CHAPTER 13
NETWORK PROTECTION SYSTEMS
After reading this chapter and completing the activities, you will be able to:
![]() Explain how routers are used as network protection systems
Explain how routers are used as network protection systems
![]() Describe firewall technology and tools for configuring firewalls and routers
Describe firewall technology and tools for configuring firewalls and routers
![]() Describe intrusion detection and prevention systems and Web-filtering technology
Describe intrusion detection and prevention systems and Web-filtering technology
![]() Explain the purpose of honeypots
Explain the purpose of honeypots
Hackers have many tools at their disposal to attack a network. You have seen how port scanning and enumeration make it possible for attackers to determine the services running on computers and gain access to network resources. In this chapter, you look at network protection systems that can be used to reduce exposure to these attacks and reduce their occurrence.
Routers, hardware and software firewalls, Web filtering, intrusion detection and prevention systems, and honeypots are covered in this chapter. A network protection system can also include a security incident response team, which is a team of people with the responsibility of protecting a large network.
UNDERSTANDING ROUTERS
To protect a network from attack, security professionals must know how to use network protection systems, such as routers, firewalls, intrusion detection and prevention systems, Web filtering, and honeypots. For the purposes of this book, a network protection system is simply any device or system designed to protect a network. The term security appliance is also used in this field. It’s a single device combining two or more network protection functions, such as those performed by routers, firewalls, intrusion detection and prevention systems, VPNs, Web-filtering systems, and malware detection and filtering systems. For instance, modern Cisco routers can perform firewall functions, address translation (Network Address Translation and Port Address Translation), and intrusion prevention in addition to their router function. As hardware technology gets more powerful, security appliances can perform the same functions that once required using several dedicated systems. They also reduce administrative effort because multiple network protection functions are managed via a common interface. In this section, you start learning about network protection systems by seeing how routers are used to reduce network attacks.
Understanding Routing Protocols
Routers, which operate at the Network layer of the OSI model, are hardware devices used to send packets to different network segments. Their main purposes are to reduce broadcast traffic passing over a network and choose the best path for moving packets. For example, if Router A in Spain wants to send a packet to Router B in Iowa, the packet can probably take several paths. Routers use routing protocols in this best-path decision-making process that function in the following ways:
![]() Link-state routing protocol—A router using a link-state routing protocol sends link-state advertisements to other routers; these advertisements identify the network topology and any changes or paths discovered recently on the network. For example, if a new router or path becomes available for a packet, this information is sent to all other routers participating in the network. This method is efficient because only new information is sent over the network. An example of a link-state routing protocol is Open Shortest Path First (OSPF).
Link-state routing protocol—A router using a link-state routing protocol sends link-state advertisements to other routers; these advertisements identify the network topology and any changes or paths discovered recently on the network. For example, if a new router or path becomes available for a packet, this information is sent to all other routers participating in the network. This method is efficient because only new information is sent over the network. An example of a link-state routing protocol is Open Shortest Path First (OSPF).
![]() Distance-vector routing protocol—If a router is using a distance-vector routing protocol, it passes its routing table (containing all possible paths it has discovered) to all routers participating on the network. These neighbor routers then forward the routing table to their neighbors. If a router learns one new path, it sends the entire routing table, which isn’t as efficient as a link-state routing protocol. An example of a distance-vector routing protocol is Routing Internet Protocol Version 2 (RIPv2).
Distance-vector routing protocol—If a router is using a distance-vector routing protocol, it passes its routing table (containing all possible paths it has discovered) to all routers participating on the network. These neighbor routers then forward the routing table to their neighbors. If a router learns one new path, it sends the entire routing table, which isn’t as efficient as a link-state routing protocol. An example of a distance-vector routing protocol is Routing Internet Protocol Version 2 (RIPv2).
![]() Path-vector routing protocol—A path-vector routing protocol uses dynamically updated paths or routing tables to transmit packets from one autonomous network to another. It isn’t used on LANs because it’s used mainly by ISPs and large organizations with multiple Internet connections to other ISPs and organizations. The main path-vector routing protocol is Border Gateway Protocol (BGP), a routing protocol that an ISP uses to transmit packets to their destinations on the Internet.
Path-vector routing protocol—A path-vector routing protocol uses dynamically updated paths or routing tables to transmit packets from one autonomous network to another. It isn’t used on LANs because it’s used mainly by ISPs and large organizations with multiple Internet connections to other ISPs and organizations. The main path-vector routing protocol is Border Gateway Protocol (BGP), a routing protocol that an ISP uses to transmit packets to their destinations on the Internet.
BGP does have some security vulnerabilities. For example, attackers might hijack IP space belonging to another ISP by injecting a malicious BGP routing advertisement for a network prefix they don’t own. This type of attack happened in summer 2008, when the IP space for YouTube.com was hijacked by an ISP in Pakistan, causing YouTube.com to be completely unreachable. For more information about this BGP hijacking event, visit www.ripe.net/news/study-youtube-hijacking.html.
Tip
For more information on routing protocols, see CCNA Guide to Cisco Networking Fundamentals, Fourth Edition (Kelly Cannon, Kelly Caudle, and Anthony V. Chiarella, Course Technology, Cengage Learning, 2009, ISBN 1418837059).
As a security professional, your main concern is confirming that a router filters certain traffic, not designing a router infrastructure and determining the routing protocol an organization uses. The following section explains how a Cisco router is configured to filter traffic.
Understanding Basic Hardware Routers
In this section, Cisco routers are used as an example because they’re widely used; millions of Cisco routers are used by companies around the world. Because Cisco has become such a standard among network professionals, vendors offering competitive products often design their configuration interfaces to be similar to Cisco’s. So although the information in this section can assist you in performing security tests on companies using Cisco routers in their networks, you won’t be completely lost if you see a product from a Cisco competitor, such as Juniper. The principles you learn in this chapter can be applied to other types of routers. In Activity 13.1, you visit the Cisco Web site and review some Cisco products. If you’ve never seen a router or worked with the interfaces discussed in this section, the product photographs on this site can give you an idea of what you’ll be working with as a security professional. As you learned in Chapter 9, a Cisco router is an embedded system that uses Cisco Internetwork Operating System (IOS) to function.
Activity 13.1: Visiting the Cisco Web Site
Time Required: 30 minutes
Objective: Learn more about Cisco routing products.
Description: Cisco routing products will be an important part of your job as a security professional because many companies use them. In this activity, you visit the company’s Web site and review the type of vulnerability information Cisco makes available to its customers. This information can be helpful if you’re performing a security test on a network using Cisco routers.
1. In Windows, start a Web browser, and go to www.cisco.com. On the Cisco home page, point to Products and Services in the top menu, and click Routers.
2. At the time of this writing, Cisco groups its routers into three categories. Explore the types of products available. In which category does the main router at your home or business fall? If it isn’t a Cisco product, who is the vendor?
3. Next, go to www.cisco.com/security. In the Search Security text box, type ios and click Go. Examine some recent vulnerabilities in Cisco IOS.
4. Next, go to http://nvd.nist.gov, click the Vulnerability Search Engine link, type cisco ios in the Keyword search box, and then press Enter. At the time of this writing, the CVE Vulnerability Database was much faster than the Cisco security search site, so for the remainder of this activity, you use this site.
5. Examine the search results. How many records were returned?
6. Choose a specific vulnerability with a Common Vulnerability Scoring System (CVSS) severity score of at least 7, and click the link beginning with CVE- to read the summary information. What does the flaw allow an attacker to do? For software flaws, the NVD Web site supplies links to the vendor’s Web site to find a patch or workaround. Click the link to the Cisco Web site and read the information. What does Cisco recommend?
7. Exit your Web browser and log off Windows for the next activity.
As you can see from your reading, vulnerabilities exist in Cisco IOS as they do in any OS, so security professionals must consider the type of router used when conducting a security test.
Security Bytes
At a Black Hat computer security conference, a 24-year-old researcher named Michael Lynn was instructed by Cisco not to give a presentation on vulnerabilities he found in Cisco’s Internet routers. Mr. Lynn claimed the vulnerabilities would allow hackers to take over corporate and government networks. Cisco argued that releasing his findings to the general public was illegal and that Mr. Lynn found the vulnerabilities by reverse-engineering Cisco’s product, also illegal in this country. Most technology companies don’t want vulnerabilities in their products to be released to the public until they have the chance to correct the problem themselves or they can control what information is given to the public. The issue of disclosure will be here for quite some time and will most certainly affect security testers.
Cisco Router Components
To help you understand how routers are used as network protection systems, this section describes the components of a Cisco router. Just as a system administrator must understand commands for configuring a server, Cisco router administrators must know commands for configuring a Cisco router. Many components of a Cisco router are similar to those of a computer, so the following components should seem familiar:
![]() Random access memory (RAM)—This component holds the router’s running configuration, routing tables, and buffers. If you turn off the router, the contents stored in RAM are erased. Any changes you make to a router’s configuration, such as changing the prompt displayed, are stored in RAM and aren’t permanent unless you save the configuration.
Random access memory (RAM)—This component holds the router’s running configuration, routing tables, and buffers. If you turn off the router, the contents stored in RAM are erased. Any changes you make to a router’s configuration, such as changing the prompt displayed, are stored in RAM and aren’t permanent unless you save the configuration.
![]() Nonvolatile RAM (NVRAM)—This component holds the router’s configuration file, but the information isn’t lost if the router is turned off.
Nonvolatile RAM (NVRAM)—This component holds the router’s configuration file, but the information isn’t lost if the router is turned off.
![]() Flash memory—This component holds the IOS the router is using. It’s rewriteable memory, so you can upgrade the IOS if Cisco releases a new version or the current IOS version becomes corrupted.
Flash memory—This component holds the IOS the router is using. It’s rewriteable memory, so you can upgrade the IOS if Cisco releases a new version or the current IOS version becomes corrupted.
![]() Read-only memory (ROM)—This component contains a minimal version of Cisco IOS that’s used to boot the router if flash memory gets corrupted. You can boot the router and then correct any problems with the IOS, possibly installing a new, uncorrupted version.
Read-only memory (ROM)—This component contains a minimal version of Cisco IOS that’s used to boot the router if flash memory gets corrupted. You can boot the router and then correct any problems with the IOS, possibly installing a new, uncorrupted version.
![]() Interfaces—These components are the hardware connectivity points to the router and the components you’re most concerned with. An Ethernet port, for example, is an interface that connects to a LAN and can be configured to restrict traffic from a specific IP address, subnet, or network.
Interfaces—These components are the hardware connectivity points to the router and the components you’re most concerned with. An Ethernet port, for example, is an interface that connects to a LAN and can be configured to restrict traffic from a specific IP address, subnet, or network.
As a security professional, you should know some basic Cisco commands to view information in these components. For example, to see what information is stored in RAM, a Cisco administrator uses this command (with bolded text indicating the actual command):
RouterB# show running-config
Here’s an example of the abbreviated output of this command for a production router:
Building configuration... Current configuration : 4422 bytes ! version 12.4 service timestamps debug datetime msec localtime service timestamps log datetime msec localtime no service password-encryption ! hostname R3825_2 ! boot-start-marker boot-end-marker ! card type t1 0 0 logging buffered 51200 debugging ! no aaa new-model ! resource policy ! clock timezone Hawaii-10 network-clock-participate wic 0 network-clock-select 1 T1 0/0/0 ip subnet-zero ip cef ! interface GigabitEthernet0/0 description $ETH-LAN$$ETH-SW-LAUNCH$$INTF-INFO-GE 0/0$ ip address 192.168.10.3 255.255.255.0 duplex auto speed auto media-type rj45 negotiation auto h323-gateway voip interface h323-gateway voip bind srcaddr 192.168.10.3 ! interface Serial0/0/0:23 no ip address isdn switch-type primary-ni isdn incoming-voice voice isdn bind-l3 ccm-manager no cdp enable ! ip classless ip route 0.0.0.0 0.0.0.0 192.168.10.1 ! ip http server username netdef privilege 15 secret 5 $1$pod7$ZZWTCxA9O8iBSJbd3tIlL1 ! end RouterB#
Cisco Router Configuration
Two access modes are available on a Cisco router: user mode and privileged mode. In user mode, an administrator can perform basic troubleshooting tests and list information stored on the router. In privileged mode, an administrator can perform full router configuration tasks. You can see which access mode you’re in by looking at the prompt. The router name followed by a > symbol, such as Router>, indicates that you’re in user mode. A router name followed by a # sign, such as Router#, indicates that you’re in privileged mode, also called enable mode. When first logging on to a Cisco router, you’re in user mode by default. To change to privileged mode, simply enter the enable command, which can be abbreviated as en. Usually, you have to enter a password to use this command, unless the Cisco router administrator has little experience and hasn’t specified a password.
After you’re in privileged mode, you need to enter another command for one of the following modes to configure the router:
![]() Global configuration mode—In this mode, you can configure router settings that affect overall router operation, such as changing the router’s displayed banner when a user connects from a remote host via Telnet. The banner might indicate that the router is secured or shouldn’t be accessed by unauthorized personnel. To use this mode, enter the configure terminal command at the Router# prompt. You can also enter an abbreviated command, which the Cisco command interpreter understands, as long as it’s not so short that it’s ambiguous. Therefore, config t works, too. The prompt then changes to Router (config)# to indicate global configuration mode. When using a Cisco router or switch, being aware of the prompts is critical.
Global configuration mode—In this mode, you can configure router settings that affect overall router operation, such as changing the router’s displayed banner when a user connects from a remote host via Telnet. The banner might indicate that the router is secured or shouldn’t be accessed by unauthorized personnel. To use this mode, enter the configure terminal command at the Router# prompt. You can also enter an abbreviated command, which the Cisco command interpreter understands, as long as it’s not so short that it’s ambiguous. Therefore, config t works, too. The prompt then changes to Router (config)# to indicate global configuration mode. When using a Cisco router or switch, being aware of the prompts is critical.
![]() Interface configuration mode—In this mode, you’re configuring an interface on the router, such as a serial or Fast Ethernet port. To use this mode, first enter global configuration mode (with the config t command). Next, enter the command for interface configuration mode and the interface name you want to configure, such as interface fastethernet 0/0. The prompt then changes to Router(config-if)# to indicate interface configuration mode.
Interface configuration mode—In this mode, you’re configuring an interface on the router, such as a serial or Fast Ethernet port. To use this mode, first enter global configuration mode (with the config t command). Next, enter the command for interface configuration mode and the interface name you want to configure, such as interface fastethernet 0/0. The prompt then changes to Router(config-if)# to indicate interface configuration mode.
Now that you understand the basic modes in which a Cisco router can operate, take a look at Table 13.1, which describes some common commands for viewing a Cisco router’s components. If you want to know all the commands available in global configuration mode, simply type a question mark after the Router(config)# prompt.
A Cisco administrator needs to know many other commands that aren’t covered in this book. The most critical configuration that security professionals perform is on a router’s interfaces. Packets can be filtered or evaluated on a router’s interfaces before passing to the next router or the internal network. To control the flow of traffic through a router, access lists are used, as explained in the following section.


Understanding Access Control Lists
There are several types of access control lists, but this section focuses on IP access lists. IP access lists are lists of IP addresses, subnets, or networks that are allowed or denied access through a router’s interface. On a Cisco router, an administrator can create two different types of access lists:
![]() Standard IP access lists
Standard IP access lists
![]() Extended IP access lists
Extended IP access lists
Note
Cisco refers to IP access lists as “access control lists” but refers to the specific file containing the list of commands as an “access list.”
Standard IP Access Lists
Standard IP access lists can restrict IP traffic entering or leaving a router’s interface based on only one criterion: source IP address. Figure 13.1 shows a network composed of two routers. Network 1 (10.0.0.0) is connected to a Fast Ethernet interface (FE0/0) on Router A. Router A’s serial interface (S0/1) is connected to Router B’s serial interface (S0/0). Network 2 (192.168.10.0) is connected to Router B’s Fast Ethernet interface (FE0/0), and Network 3 (173.110.0.0) is connected to Router B’s other Fast Ethernet interface (FE0/1).
Figure 13.1
Applying access lists to router interfaces

Courtesy Course Technology/Cengage Learning
A Cisco administrator who wants to restrict all traffic from Network 3 from entering Network 1 can create a standard IP access list that looks like the following:
access-list 1 deny 173.110.0.0 0.0.255.255 access-list permit any
Extended IP Access Lists
A standard IP access list is restricted to source IP addresses. So if you want to restrict a user from sending a packet to a specific IP address (destination IP address), you can’t use a standard IP access list. Extended IP access lists can restrict IP traffic entering or leaving a router’s interface based on the following criteria:
![]() Source IP address
Source IP address
![]() Destination IP address
Destination IP address
![]() Protocol type
Protocol type
![]() Application port number
Application port number
Configuring an extended IP access list is much the same as configuring a standard IP access list. A network administrator can decide which interface to apply an access list to, based on several variables. For example, a router might have an interface connecting to a T1 or DSL line. An access list can be applied to only this interface, not to another interface connected to a CAT 5 cable. Access lists are nothing more than lists; they don’t become effective until they’re applied to interfaces. A detailed discussion of the syntax of access lists is beyond the scope of this book. Because your job might include testing a network with routers, however, you should research access lists in more detail on your own or in another course. If you decide to earn a Cisco Certified Network Associate (CCNA) certification, for example, you need to know how to create, configure, and apply access lists to interfaces. The knowledge you gain from earning this certification is a good addition to your security-testing arsenal.
UNDERSTANDING FIREWALLS
Firewalls can be hardware devices with embedded OSs, as you learned in Chapter 9, or software installed on general-purpose computer systems. Firewalls serve two main purposes: controlling access to traffic entering an internal network and controlling traffic leaving an internal network. Firewalls can be installed on a network to protect a company’s internal network from dangers existing on the Internet. On large enterprise networks, firewalls can also protect internal network segments, such as those containing only application servers, from other internal network segments—for example, those containing employee workstations. For instance, a typical enterprise firewall approach is restricting the remote desktop port TCP 3389, used for remote administration of application servers, to only the system administrator network segment and allowing only ports 80 and 443 for Web traffic on the network segment containing employee workstations. In this example, clearly typical employees don’t need to administer application servers, so this approach reflects a least-privileges philosophy.
There are advantages and disadvantages of hardware and software firewalls. However, instead of making recommendations, this chapter focuses on how firewalls fit into a security strategy. Briefly, the disadvantage of hardware firewalls is that you’re locked into the firewall’s hardware, such as the number of interfaces it includes. With a software firewall, you can add NICs easily to the server running the software. A disadvantage of software firewalls is that you might have to worry about configuration problems, such as memory requirements, hard disk space requirements, number of CPUs supported, and so on. Software firewalls also rely on the OS on which they’re running. Microsoft Internet Security and Acceleration (ISA) Server, for example, is a software firewall that runs on Windows Server 2003. Another example is Iptables, included with BackTrack on this book’s online supporting files. Hardware firewalls, such as Cisco Adaptive Security Appliance (covered later in this chapter), are usually faster and can handle a larger throughput than software firewalls can.
As you have seen, a router can also be used to filter traffic entering or leaving its interface. Filtering can be set up with access lists that restrict traffic based on the source IP address, destination IP address, protocol, and port. However, a firewall is specifically designed as a network protection system and has more security features than a router.
Understanding Firewall Technology
You have seen numerous methods that attackers use to scan a network and launch exploits. Firewalls can help reduce these attacks by using several technologies:
![]() Network Address Translation
Network Address Translation
![]() Access lists
Access lists
![]() Packet filtering
Packet filtering
![]() Stateful packet inspection
Stateful packet inspection
![]() Application layer inspection
Application layer inspection
Network Address Translation
The most basic security feature of a firewall is Network Address Translation (NAT). One job of a security professional is to hide the internal network from outsiders. With NAT, internal private IP addresses are mapped to public external IP addresses, hiding the internal infrastructure from unauthorized personnel. For example, a user with a private IP address of 10.1.1.15 has her address mapped to an external IP address of 193.145.85.200. The outside world sees only the external IP address and doesn’t know the internal IP addresses the company uses.
After hackers know a computer or server’s IP address, they scan that system for open or vulnerable ports. Hiding IP addresses from hackers can help prevent these scans from being successful. To accommodate the many addresses that need to be mapped, many organizations use Port Address Translation (PAT), which is derived from NAT. It allows mapping thousands of internal IP addresses to one external IP address.
Access Lists
As discussed in the section on routers, access lists are used to filter traffic based on source IP address, destination IP address, and ports or services. Firewalls also use this technology, as you see later in the section on the Cisco Adaptive Security Appliance firewall. After you understand how to create an access list on a router, creating one on a firewall is a similar process.
Packet Filtering
Another basic security function a firewall performs is packet filtering. Packet filters screen packets based on information in the packet header, such as the following:
![]() Protocol type
Protocol type
![]() IP address
IP address
![]() TCP/UDP port
TCP/UDP port
Stateful Packet Inspection
Firewalls usually take the basic filtering a router does a step further by performing stateful packet inspection (SPI). Stateful packet filters record session-specific information about a network connection, including the ports a client uses, in a file called a state table. Table 13.2 is an example of a state table.
In this state table, several internal hosts using private IP addresses have established connections to external IP addresses. One host has established a Telnet session (port 23), two hosts have established HTTP connections (port 80), and one host has established a connection to an e-mail server (port 25). This state table is a way for the firewall to track the state of connections, based on what kind of traffic is expected in a two-way session. Port scans relying on spoofing or sending packets after a three-way handshake are made ineffective if the firewall uses a state table. If a hacker attempts to send (spoof) a SYN/ACK packet from an IP address not in the state table, the packet is dropped. As you learned in previous chapters, a SYN/ACK packet is sent only after a SYN packet has been received.
Table 13.2 State table example

Stateful packet filters recognize types of anomalies that most routers ignore, such as hundreds or thousands of SYN/ACK packets being sent to a computer, even though the computer hasn’t sent out any SYN packets. Because stateless packet filters handle each packet separately, they aren’t resistant to spoofing or DoS attacks.
Application Layer Inspection
An application-aware firewall inspects network traffic at a higher level in the OSI model than a traditional stateful packet inspection firewall does. SPI ensures that a packet’s source, destination, and port are expected before forwarding the packet, but a firewall performing application layer inspection also makes sure that the network traffic’s application protocol is the type allowed by a rule. For example, many Trojans get past firewalls by launching a reverse shell that originates from the compromised system and connects to a remote system the hacker controls. This reverse shell is the hacker’s secure command-and-control tunnel, and it’s usually disguised by using a commonly allowed outbound port, such as port 80. The hacker-controlled channel then penetrates from inside the network to outside over the allowed outbound port. Workstations use port 80 outbound for Web browsing via HTTP, an application protocol. If the reverse shell uses Telnet or SSH application protocols, however, an application-aware firewall can prevent the reverse shell from being used on a port reserved for HTTP traffic. Some application-aware firewalls act as a proxy for all connections, thus serving as a safety net for servers or clients (or both), depending on what the firewall is protecting. If an application-aware firewall is protecting a Web server, for example, it prevents buffer overflows that target a specific application protocol, such as the ISAPI vulnerability in IIS Web server software.
Implementing a Firewall
Placing a firewall between a company’s internal network and the Internet can be dangerous because if hackers compromise the firewall, they have complete access to the internal network. To reduce this risk, most enterprise firewall topologies use a demilitarized zone, discussed in the following section, to add a layer of defense.
Demilitarized Zone
A demilitarized zone (DMZ) is a small network containing resources that a company wants to make available to Internet users; this setup helps maintain security on the company’s internal network. A DMZ sits between the Internet and the internal network and is sometimes referred to as a “perimeter network.” Figure 13.2 shows how outside users can access the e-mail and Web servers in the DMZ, but the internal network is protected from these outside Internet users.
Note that Internet users can access the DMZ without going through the firewall. A better security strategy is placing an additional firewall in the network setup (see Figure 13.3).
Figure 13.2
A DMZ protecting an internal network

Courtesy Course Technology/Cengage Learning
Figure 13.3
An additional firewall used to protect the DMZ

Courtesy Course Technology/Cengage Learning
For users to access the internal network from the Internet, they need to pass through two firewalls. This setup is probably the most common design for an enterprise firewall topology.
Understanding the Cisco Adaptive Security Appliance Firewall
A good way to learn how a firewall operates is to look at the configuration of one of the most widely used firewalls: the Cisco Adaptive Security Appliance (ASA) firewall. Cisco ASA has replaced the Cisco PIX firewall and added advanced modular features, such as intrusion detection and prevention and more sophisticated application layer inspection. In the following sections, you view some configuration commands for an ASA firewall to get an idea of what security professionals need to know.
Note
Cisco has classes and books on configuring ASA, so the information in this section is just the tip of the iceberg.
Configuring the ASA Firewall
After logging on to an ASA firewall via SSH, you see a logon prompt that’s similar to the prompt for logging on to a Cisco router:
If you are not authorized to be in this XYZ Hawaii network device, log out immediately! Username: admin Password: ********
In this example, the administrator created a banner warning that anyone attempting to connect must be authorized before continuing. This banner might seem like a waste of time, but it serves a legal purpose. If the banner had said “Welcome, please log on,” intruders might not be prosecuted if they hack into your network. The U.S. legal system has already dropped charges against hackers who entered sites with the word “Welcome” in banners.
After you log on with the correct password, the firewall displays the following information:
Type help or '?' for a list of available commands. ciscoasa>
The prompt is the same one you saw when logging on to a Cisco router—the router name followed by a > symbol—so you know you’re in user mode. To enter privileged mode, you enter the same enable (en, in this example) command used for a Cisco router and are then prompted to enter a password:
ciscoasa> en Password: ********
After entering the correct password, you’re placed in privileged mode, indicated by the # prompt. Entering the ? character reveals more commands available in privileged mode. Next, to enter configuration mode in ASA, you use the same command as on a Cisco router: configure terminal or configure t.
Next, look at how the firewall uses access lists to filter traffic. The following access list named PERMITTED_TRAFFIC shows the specific VPN connections to several wiring closets:
ciscoasa(config)# show run access-list access-list PERMITTED_TRAFFIC remark VPN-CONC1 TO TERMINAL CLOSET1B access-list PERMITTED_TRAFFIC extended permit ip host 10.13.61.98 host 10.13.61.18 access-list PERMITTED_TRAFFIC remark VPN-CONC2 TO TERMINAL CLOSET1B access-list PERMITTED_TRAFFIC extended permit ip host 10.13.61.99 host 10.13.61.19 access-list PERMITTED_TRAFFIC remark VPN-CONC3 TO TERMINAL CLOSET1B access-list PERMITTED_TRAFFIC extended permit ip host 10.13.61.100 host 10.13.61.20 access-list NONE extended deny ip any any log access-list CAP-ACL extended permit ip any any
Next, look at the object group listing in the ASA configuration. An object group is a way to organize hosts, networks, services, protocols, or ICMP types into groups so that a firewall rule can be applied to all objects at once, instead of one at a time. In this example, several hosts are members of the VIRTUAL_TERMINALS object group:
ciscoasa# show run object-group object-group network VIRTUAL_TERMINALS network-object host 10.11.11.67 network-object host 10.11.11.68 network-object host 10.11.11.69
In the following example, notice the object group for networks. It’s called AD_SERVERS, a name the firewall administrator chose to represent Active Directory servers. Currently, there’s only one host in the group, but the firewall administrator might expand it when more Active Directory servers are added. Next is the object group for services, which is organized as AD_TCP and AD_UDP. In Chapter 8, you learned which ports must be open on a firewall for domain controller Active Directory services to function, so the ports listed in this example should look familiar.
object-group network AD_SERVERS network-object host 10.0.0.25 object-group service AD_TCP tcp port-object eq domain port-object eq 88 port-object eq 135 port-object eq ldap port-object eq 445 port-object eq 1026 object-group service AD_UDP udp port-object eq domain port-object eq 88 port-object eq ntp port-object eq 389
Finally, the application services that should be allowed through the firewall are organized in the APP_SERVICES object group. Notice that Web (WWW, HTTPS), FTP (FTP, FTP-data), e-mail (POP3, SMTP), and file sharing (port 445) are allowed:
object-group service APP_SERVICES tcp port-object eq ftp-data port-object eq ftp port-object eq smtp port-object eq www port-object eq pop3 port-object eq https port-object eq 445
Using Configuration and Risk Analysis Tools for Firewalls and Routers
As you learned in Chapter 8, patching systems is only one part of protecting them from compromise. You must also configure them securely. Fortunately, plenty of resources are available for this task. One of the best Web sites for finding configuration benchmarks and configuration assessment tools for Cisco routers and firewalls is the Center for Internet Security (CIS, www.cisecurity.org). A benchmark is an industry consensus of best configuration practices on the hows (using step-by-step guidance) and whys (explaining the reasons for taking these steps) of securing a Cisco router or firewall. For Cisco routers, use the CIS Cisco IOS Benchmark; the most recent version is currently 2.2. For Cisco ASA firewalls, use the CIS Benchmark for Cisco Firewall Devices, version 2.0. Reviewing all the configuration steps in these benchmarks can take quite a bit of time, however. For this reason, CIS offers a useful tool called Router Audit Tool (RAT) that’s faster and easier to use. RAT versions are available for both *nix and Windows systems. If you have time and access to a lab with a Cisco router or firewall, download the RAT tool and run it on your Windows or BackTrack system.
A commercial tool worth mentioning is RedSeal (www.redseal.net), a unique network risk analysis and mapping tool. Like the CIS RAT tool, RedSeal can identify configuration vulnerabilities in routers or firewalls, but it also generates professional-looking reports that can be customized with your company logo, for example. In addition to analyzing configuration files from routers and firewalls, RedSeal can analyze IPSs as well as OS vulnerability scans of a network to produce a detailed analysis and mapping. Figure 13.4 shows the network risk map that’s generated when you enter Cisco router and firewall configuration files and Nessus scans in RedSeal. It analyzes the configurations of all devices on the network to identify what access is allowed. In considering the architecture to use for network protection, access is determined by combining the rules and ACLs in each device along a network path. The thicker lines in Figure 13.4 represent every subnet that can access a network’s data center. To see details of an allowed path, simply click the corresponding line.
RedSeal is unique in that it shows a graphical representation of vulnerabilities discovered in the context of the network on which they’re found. A RedSeal report and map can be especially useful in conveying information to senior management; the graphical format is easier to understand than pages of wordy reports. (Remember the old adage: A picture is worth a thousand words.) For representing a network’s security status, RedSeal is a handy tool.
Figure 13.4
The RedSeal network risk map
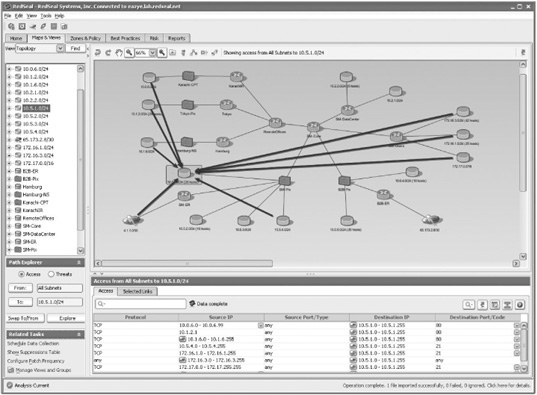
Courtesy Course Technology/Cengage Learning
UNDERSTANDING INTRUSION DETECTION AND PREVENTION SYSTEMS
Intrusion detection systems (IDSs) monitor network devices so that security administrators can identify attacks in progress and stop them. For example, for users to be able to access a Web server, a firewall must allow port 80 to be open. Unfortunately, opening this port can also allow a hacker to attack the Web server. An IDS examines the traffic traversing the connection to port 80 and compares it with known exploits, similar to virus software using a signature file to identify viruses. If an attacker attempts to exploit a known vulnerability in the Web server, the IDS sends an alert of the attack so that the Web server administrator can take action. Intrusion prevention systems (IPSs) are similar to IDSs, but they take the additional step of performing some sort of action to prevent the intrusion, instead of just alerting administrators of the attack. The following section describes two types of intrusion detection and prevention systems: network-based and host-based.
Network-Based and Host-Based IDSs and IPSs
Network-based IDSs/IPSs monitor activity on network segments. Essentially, they sniff traffic as it flows over the network and alert a security administrator when something suspicious occurs. Some of these systems can also block traffic. Host-based IDSs/IPSs are most often used to protect a critical network server or database server, although they can also run on workstations. The IDS or IPS software is installed on the system you’re attempting to protect, just like installing antivirus software on your desktop system.
IDSs can also be categorized by how they react when they detect suspicious behavior. Systems that don’t take any action to stop or prevent an activity are called passive systems. They do, of course, send an alert and log the activity, much like an underpaid security guard at a shopping mall witnessing an armed robbery. Active systems also log events and send alerts, but they can also interoperate with routers and firewalls. For example, an active IDS can send an access list to a router that closes an interface to prevent attackers from damaging the network. Some active IDSs send spoofed reset packets that fool the TCP/IP stacks of both the victim and attacker into tearing down the malicious connection.
Of course, the time from the start of an attack to the time it compromises a system can be mere milliseconds, too fast for a human to take action. For this reason, vendors have started focusing their marketing efforts on IPSs. There’s a difference between an active IDS and a true IPS. A true network-based IPS is installed inline to the network infrastructure, meaning traffic has to pass through the IPS before going into or out of the network. An active IDS just sniffs traffic and can be turned off or unplugged from the network without affecting network connectivity. Because an IPS is inline, generally it’s more capable of stopping malicious traffic than an active IDS is, especially against UDP-based attacks. Many current IDSs include IPS features and often have optional modules, such as malware detection and Web filtering. In addition, host-based IPSs are available; they operate at the OS (or kernel) level and intercept traffic that’s not allowed by the host policy. Because host-based IPSs share resources with the OS they run on, they can slow down performance if the hardware isn’t adequate.
Network-based IDSs and IPSs can be further categorized by the way they detect attacks: signatures or anomalies. Most of these systems detect malicious activity by using a database of known attack signatures. Anomaly detectors, on the other hand, use a baseline of normal activity and then send an alert if the activity deviates significantly from this baseline.
Table 13.3 lists some of the many IDSs and IPSs on the market. A recent trend is for IDS manufacturers to offer IPS functionality as an option in most of their IDS products—hence the tendency to use the IDS and IPS terms together. Spend some time visiting the Web sites listed in the table to learn more about these products. IDSs and IPSs play an important role in defending against network attacks. When combined with routers and firewall technology, they can help you protect the network you’ve been asked to secure.
Table 13.3 Intrusion detection and prevention systems

Web Filtering
Statistically speaking, firewalls and IPSs do a good job of protecting a network from attacks from the Internet. Hackers know the statistics, so recently they’ve been using a new way into the network that doesn’t require breaching the network’s hardened perimeter defenses. This new way in is out—that is, using the least restricted pathway through a firewall, which on most networks is the outbound rules. How does this attack method work?
Attackers target the devices that are usually allowed access out of the network automatically: user workstations. If they can get an internal user to visit a bogus Web site or install malicious code from an e-mail attachment, they don’t need to break through the firewall. After Trojan code is installed on a user’s workstation, attackers can control the Trojan remotely with commands that might seem to be normal traffic. They can take advantage of this compromise to expand through the network by running network scans from the compromised workstation, cracking system passwords, and exploiting vulnerabilities they discover on other systems. Firewall application layer inspection might not detect this kind of attack, especially if attackers hide the command-and-control activity inside HTTP and HTTPS traffic. In this situation, Web filtering can be used to detect users’ attempts to access malicious Web sites and block these attempts, and some Web-filtering systems can actually block malicious code before it gets to a user’s workstation or before it has a chance to connect to an attacker’s control system outside the network.
Organized cybercriminals often try to hack busy Web sites that have the best chance of infecting thousands of Web site visitors with their malicious code. These types of mass compromises are used to initiate drive-by downloads, in which Web site visitors download malicious code without their knowledge. Usually the drive-by download exploits a security flaw in the browser or a third-party application, such as Adobe Reader or Apple QuickTime. Because malicious Web sites and code change daily, Web-filtering system providers need to update their signatures and databases of malicious Web sites constantly. Examples of vendors offering Web-filtering products on a subscription basis are Websense (www.websense.com) and Blue Coat (www.bluecoat.com).
Security Incident Response Teams
The IDSs, IPSs, and honeypots (discussed in the next section) that help keep a network secure require administrative expertise to set up, run, and maintain. When a security event happens, usually administrators have to clean up the mess and then make a report to management or the legal department or work with law enforcement. For large organizations that have sensitive or critical data, normal administrative expertise isn’t enough to follow up and do damage assessment, risk remediation, and legal consultation. For these types of organizations, you might need to recommend using a security incident response team (SIRT). Some organizations need a permanent team whose members are responsible solely for security-response functions. Other organizations might better spend their resources setting up an ad hoc team, with members who normally have other roles and are called in response to a specific incident. You can find more information on forming SIRTs at www.cert.org.
UNDERSTANDING HONEYPOTS
A honeypot is a computer placed on the network perimeter that contains information or data intended to lure and then trap hackers. The main goal is to distract hackers from attacking legitimate network resources. A security professional configures the computer to have vulnerabilities so that hackers spend time trying to exploit these vulnerabilities. Another goal of a honeypot is to have hackers connect to the “phony” computer long enough to be traced, as in movies when the FBI wants a criminal to stay on the phone long enough to trace his or her location. In addition, a honeypot can serve as an excellent data collector and early warning system to help characterize new attacks and threats; this information makes it easier for security professionals to defend networks against them.
For more information on honeypots, visit www.honeynet.org. This Web site offers exercises and challenges that encourage user participation, contains white papers on honeypots, and includes workshop presentations describing the Honeynet Project. If you decide to participate in any exercises, you might want to use a computer lab isolated from any production servers or networks. A test computer should be used because of the possibility of virus infection or data corruption.
How Honeypots Work
If attackers can get to your internal network, they can create havoc. A honeypot appears to have important data or sensitive information stored on it. For example, it could store fake financial data that tempts hackers into attempting to browse through the data. The government and private industry have used honeypots to lure attackers into network areas away from the real data for many years. Basically, the belief is that if hackers discover a vulnerability in a system, they’ll spend time exploiting the vulnerability and stop looking for other areas to exploit and access a company’s resources.
Honeypots also enable security professionals to collect data on attackers. In this way, the hunter becomes the hunted. Both commercial and open-source honeypots are available, and Tables 13.4 and 13.5 show some products available for security professionals.
Table 13.4 Commercial honeypots
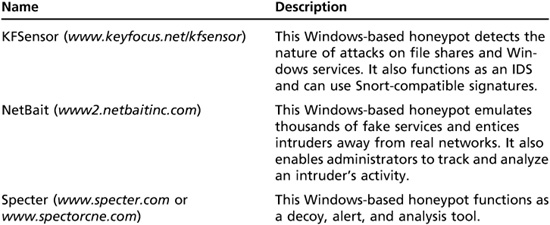
Table 13.5 Open-source honeypots

The good news is that creating a honeypot without dedicating a powerful server to the task is possible now. Virtual honeypots are created by using a programming language rather than configuring a physical device. You can download free open-source code and install it on a *nix or Windows computer. In Activity 13.2, you examine one of these products: Honeyd, created and maintained by Niels Provos.
Activity 13.2: Examining an Open-Source Virtual Honeypot
Time Required: 30 minutes
Objective: Learn about Honeyd, an open-source virtual honeypot.
Description: As a security professional, you might need to set up a honeypot to help reduce your network’s attack surface. With virtual honeypots, you don’t need to dedicate physical resources to a honeypot. In this activity, you look at an open-source virtual honeypot called Honeyd.
1. Start a Web browser, if necessary, and go to www.honeyd.org.
2. On the main Developments of the Honeyd Virtual Honeypot Web page, read the information. Then click the General Information link in the Honeyd Resources menu on the left. Review the Overview, Features, Subsystem Virtualization, and Internet in the Box sections to become more familiar with Honeyd’s capabilities.
3. In the Honeyd Resources menu, click the Sample Configurations link. Read the information on configurations to get an idea of how some different honeypots work.
4. Exit your Web browser.
If time permits, you might want to download the Honeyd program from www.honeyd.org and install it on a Linux system. You might also want to set up a lab and get some practice using the program, which does an excellent job of tracking hackers who are attempting to access resources on a network. It can even trick Nmap into believing it has detected the OS running on a system. For example, you can create templates that emulate whatever OS you want the attacker to believe is running on a particular IP address.
Honeyd monitors all unused IP addresses on a network and assumes that anyone else monitoring these addresses is a malicious user. After all, why would anyone monitor an IP address that’s not being used? Honeyd generates an alert and indicates what the attacker is attempting to do. For more information on using this program, visit www.securityfocus.com/infocus/1659.
CHAPTER SUMMARY
![]() Security professionals can use a variety of network protection systems to protect a network, such as routers, firewalls, intrusion detection and prevention systems, Web filters, honeypots, and security appliances, which combine multiple network protection functions on one device.
Security professionals can use a variety of network protection systems to protect a network, such as routers, firewalls, intrusion detection and prevention systems, Web filters, honeypots, and security appliances, which combine multiple network protection functions on one device.
![]() Routers use access lists to accept or deny traffic through their interfaces. On Cisco routers, access lists can be used to filter traffic entering and leaving a network. Access lists are applied to interfaces on the router.
Routers use access lists to accept or deny traffic through their interfaces. On Cisco routers, access lists can be used to filter traffic entering and leaving a network. Access lists are applied to interfaces on the router.
![]() Firewalls can be hardware or software and are used to control traffic entering and leaving a network. Cisco ASA is one of the most widely used firewalls. Firewalls can also be used to protect internal network segments and prevent attackers from initiating command-and-control data, such as a reverse shell, from inside the network.
Firewalls can be hardware or software and are used to control traffic entering and leaving a network. Cisco ASA is one of the most widely used firewalls. Firewalls can also be used to protect internal network segments and prevent attackers from initiating command-and-control data, such as a reverse shell, from inside the network.
![]() Firewalls use NAT, packet filtering, access control lists, stateful packet inspection, and application layer inspection to filter incoming and outgoing network traffic.
Firewalls use NAT, packet filtering, access control lists, stateful packet inspection, and application layer inspection to filter incoming and outgoing network traffic.
![]() A DMZ is a small network containing resources that sits between the Internet and the internal network, sometimes referred to as a “perimeter network.” It’s used when a company wants to make resources available to Internet users yet keep the company’s internal network secure.
A DMZ is a small network containing resources that sits between the Internet and the internal network, sometimes referred to as a “perimeter network.” It’s used when a company wants to make resources available to Internet users yet keep the company’s internal network secure.
![]() Intrusion detection systems monitor network traffic so that administrators can identify attacks occurring on a network. For example, a computer receiving thousands of SYN packets over a short period might indicate that an intruder is scanning the network.
Intrusion detection systems monitor network traffic so that administrators can identify attacks occurring on a network. For example, a computer receiving thousands of SYN packets over a short period might indicate that an intruder is scanning the network.
![]() Network-based IDSs monitor activity on network segments, whereas host-based IDSs are used to protect a critical network server or database server.
Network-based IDSs monitor activity on network segments, whereas host-based IDSs are used to protect a critical network server or database server.
![]() Passive IDSs don’t take any action or prevent an activity from continuing to occur; they simply alert the administrator and log the activity. Active IDSs log and send alerts but also interoperate with routers and firewalls and can close a port or a router interface if they detect possible intrusions.
Passive IDSs don’t take any action or prevent an activity from continuing to occur; they simply alert the administrator and log the activity. Active IDSs log and send alerts but also interoperate with routers and firewalls and can close a port or a router interface if they detect possible intrusions.
![]() Like IDSs, intrusion prevention systems (IPSs) detect malicious activity. However, IPSs are placed inline to the network infrastructure (network-based IPSs) or on the host (host-based IPSs) and can block or prevent malicious activity. Many IDS vendors now offer products with some sort of IPS functionality.
Like IDSs, intrusion prevention systems (IPSs) detect malicious activity. However, IPSs are placed inline to the network infrastructure (network-based IPSs) or on the host (host-based IPSs) and can block or prevent malicious activity. Many IDS vendors now offer products with some sort of IPS functionality.
![]() Anomaly detectors detect network activity that varies from a set baseline and send alerts.
Anomaly detectors detect network activity that varies from a set baseline and send alerts.
![]() Configuring routers and firewalls securely is easier with benchmark tools, such as the free tools available at the CIS Web site. Commercial tools, such as Red-Seal, are helpful in analyzing and mapping network risks.
Configuring routers and firewalls securely is easier with benchmark tools, such as the free tools available at the CIS Web site. Commercial tools, such as Red-Seal, are helpful in analyzing and mapping network risks.
![]() Web filtering is a technology that can block Web sites containing malicious code, such as those used in drive-by download attacks. Because Web sites change often, using a subscription service to update Web-filtering signatures and databases is a good protective measure.
Web filtering is a technology that can block Web sites containing malicious code, such as those used in drive-by download attacks. Because Web sites change often, using a subscription service to update Web-filtering signatures and databases is a good protective measure.
![]() Large organizations might need to form a security incident response team (SIRT) made up of experts with the skills and training to respond to network security incidents.
Large organizations might need to form a security incident response team (SIRT) made up of experts with the skills and training to respond to network security incidents.
![]() Honeypots are physical or virtual computers containing bogus information and vulnerabilities, designed to lure hackers away from legitimate network resources and entice them to spend time exploiting the honeypot’s vulnerabilities.
Honeypots are physical or virtual computers containing bogus information and vulnerabilities, designed to lure hackers away from legitimate network resources and entice them to spend time exploiting the honeypot’s vulnerabilities.
