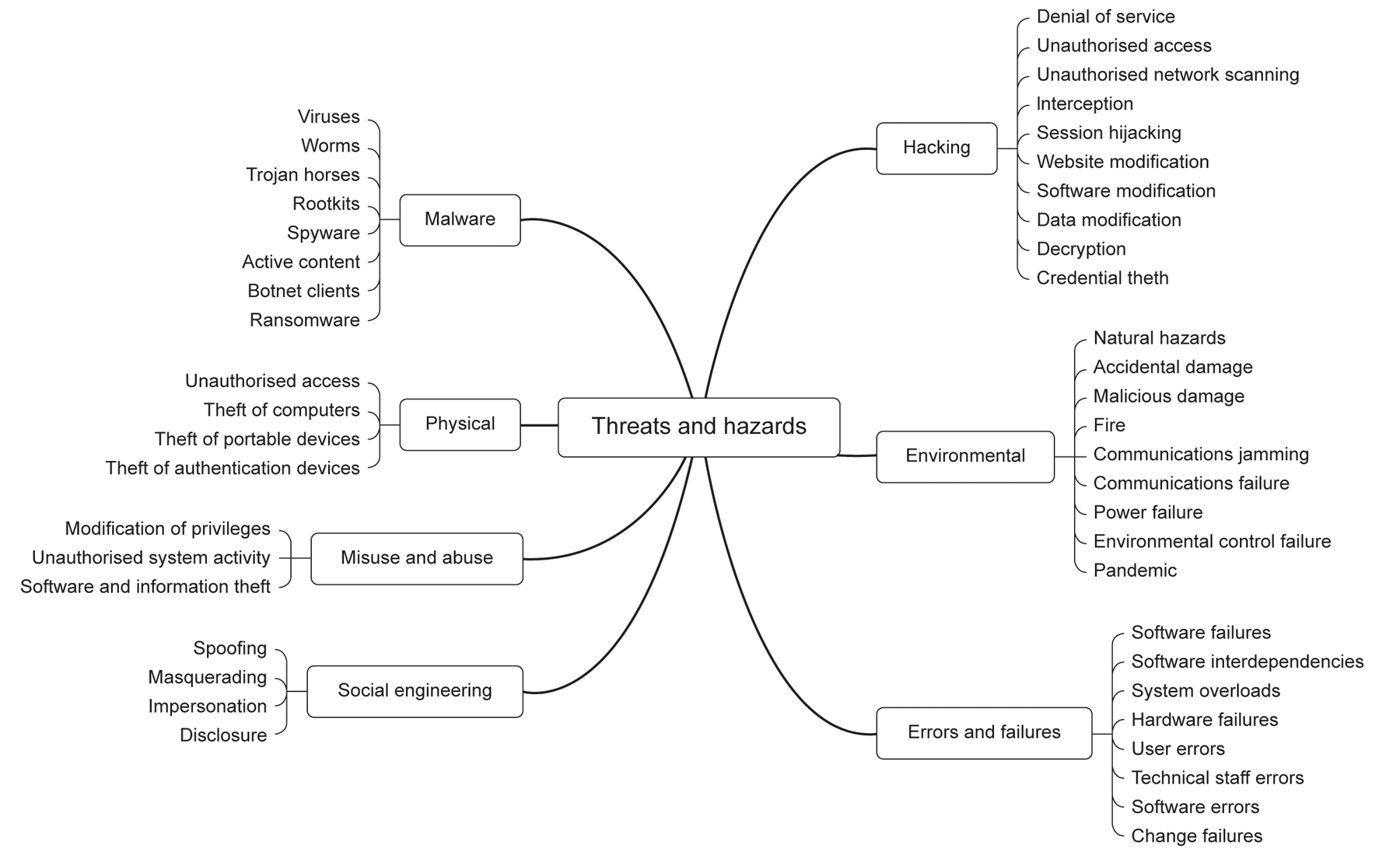
APPENDIX B – TYPICAL THREATS AND HAZARDS
Threats and hazards cause impacts or consequences to occur on one or more assets by taking advantage of one or more vulnerabilities. The list in Figure B.1 may not be exhaustive, but should provide a starting point.
MALICIOUS INTRUSION (HACKING)
Hacking is a generic term applied to many forms of unpleasant behaviour, although it began as a description of what people did in order to find out how computers worked and how to improve their performance. Hacking almost invariably results in a breach of confidentiality, integrity or availability as hackers use software tools to intercept and decrypt legitimate information, and either steal it, change it or deny access to it in some way.
Since the introduction of the Computer Misuse Act in 1990, hacking has been treated as a crime, since it invariably involves accessing a computer without the owner’s permission to do so.
Denial of service
Occasionally, hacking is used to deliver so-called DoS attacks, designed to prevent legitimate access to systems, often to make a political point or as revenge for a perceived or real injustice. Associated with hackers are so-called ‘hacktivists’ who sometimes deface website pages or mount DoS attacks. Their attacks follow no set pattern or target, but the end result becomes an availability issue not only for the organisation hosting the targeted website, but also potentially for its users.
Unauthorised access
Most people think of hackers as working from outside the organisation, and although this may be generally correct, there is no reason why someone within the organisation should not be considered a hacker, since their ability to access information from within is much easier than for someone on the outside. It is not unknown for criminal gangs to ‘plant’ well-trained technical staff and security specialists inside target organisations in order to steal information or systems hardware, and such people might be sufficiently well resourced to evade detection during the recruitment process.
As with hacking, following the introduction of the Computer Misuse Act in 1990, the unauthorised access of someone else’s computer became a criminal offence, since it invariably involves accessing a computer without the owner’s permission to do so, and unauthorised use from within an organisation can be considered an offence under the Act just as it can from an external attack.
Unauthorised access to systems and information is not restricted to criminal hackers, and although most prosecutions have been for activities that one would consider unsociable, even people who are supposed to be beyond reproach have been prosecuted for offences under the Act – some years ago an ex-police superintendent was convicted of using the Police National Computer System to acquire information about his ex-wife’s new partner.
Unauthorised network scanning
Likewise, once hackers penetrate unsecured wireless networks, they will invariably carry out a scan of systems, and both wired and wireless networks, as part of obtaining information that will aid them in attaining their targets.
Once connected to an organisation’s internal network, hackers will invariably try to steal user credentials such as user IDs and passwords and, if they can also steal cryptographic keys, they may be able to decrypt information they recover from systems.
Interception
Hackers should not be viewed as unsophisticated individuals. Very often, they are extremely experienced, equipped with highly sophisticated tools and often financially funded by criminal enterprises, allowing them to intercept wireless and wired network traffic, especially in organisations that promote the wider use of Wi-Fi within their premises. Apart from intercepting wireless traffic, hackers may also introduce their own wireless access points in an attempt to lure unsuspecting users onto insecure networks.
Session hijacking
When a user establishes an internet connection to another computer, the remote computer invariably places a cookie on the user’s computer, which permits continuity of the session without the need for the user to re-authenticate at every new request or transaction. This is sometimes known as a ‘magic cookie’, and if an attacker can obtain this, he can then hijack the user’s session and masquerade as the legitimate user.
Session hijacking is quite a complex process and requires an attacker with considerable skill and motivation.
Website modification
Website modification is frequently an attack carried out as revenge for a perceived injustice or to demonstrate an attacker’s technical expertise. Weaknesses in the website code allow skilled attackers to take control either of the website page or even the entire website in order to substitute information of their own choosing. Individuals and groups of hackers have carried out this type of attack on numerous occasions, sometimes to the great embarrassment of governments and businesses alike.
Software modification
Attackers who wish to carry out attacks on a large number of prospective targets will often modify existing software by adding their own malicious code – malware – and offer the software through spam emails or other means. The malware might cause a number of different results – for example, to turn the target user’s computer into a botnet client or to steal personal information.
Data modification
Attackers who access websites and visibly change the web pages are just one side of the coin. Instead of changing something obvious, such as the website owner’s identity, they might modify other data on the website, which might not be so obvious and might provide a visitor with incorrect or misleading information, often inserting links to other websites containing malware or where the user’s security credentials can be obtained.
Decryption
The unauthorised decryption of encrypted information is a threat that is used in combination with, for example, the theft of business information and the theft of cryptographic keys or the brute-force attacking of encrypted information. An example of this is in cases where an attacker will intercept and record encrypted wireless network traffic over a period of time, and either decrypt it having acquired or guessed the correct key, or will subject it to a lengthy attack in order to recover the key, after which further traffic could be decrypted ‘on the fly’.
Credential theft
The theft of user credentials permits an attacker to carry out spoofing, masquerading or impersonation attacks against targets. User credentials may be as simple as user ID and password combinations gathered from social engineering or phishing activities. In many cases, attackers will not use the credentials themselves, but will sell them on in bulk to criminal gangs.
ENVIRONMENTAL THREATS
Environmental threats are almost always concerned with availability, since they affect the environment in which a system or information resides. Those impacts or consequences that occur as a result of natural events – for example, severe weather – are often referred to as hazards in order to distinguish their motivation from those of malicious threats.
Severe weather can knock out power and communications networks, denying us electronic access to our information, and can also have an adverse effect on communications networks that remain operational, since many people stay at home during adverse weather, which increases the load on the internet and delays access to information.
Natural hazards can also include pandemics, in which a large number of key staff may be taken ill and unable to work, resulting in an impact to service delivery, for example. In the case of the coronavirus pandemic in 2020, large numbers of people were encouraged to work from home where possible, and others who were unable to work because their workplaces were closed also stayed at home. This greatly increased the ‘normal’ load on broadband and mobile networks, and as a consequence overloaded many organisations’ websites.
Accidental and malicious physical damage
While physical damage might not at first appear to be a threat to information, instances of accidental damage to underground communications cables is quite commonplace, and in recent years thieves have targeted copper cables for their scrap value. Either instance may well result in an enforced denial of access unless the communications service providers are able to install a fully redundant infrastructure.
A typical example of this was in April 2009, when a tunnel-boring machine managed to directly drill into a tunnel near Ilford that carries communications cables. The cables were wrapped around the machine and pulled out in both directions.
It is also commonplace for thieves to mistakenly target fibre-optic cables instead of copper cables, the impact of which can be even more severe, since fibre-optic cables tend to carry significantly greater quantities of traffic.
Fire
Fire is another serious hazard. Although much information can be backed-up in alternative locations, some cannot. Take, for example, the fire in May 2014 at the Glasgow School of Art, in which many students’ entire final year work was destroyed. Either the smoke or the water used in extinguishing the fire may have ruined even work that was not actually destroyed by the flames. Ironically, during the restoration work following the fire, another fire broke out in June 2018, almost totally destroying the Mackintosh building. Art is a form of information that is often overlooked, and in many cases is very fragile and irreplaceable.
Communications jamming or deliberate interference
Communications jamming or deliberate interference is a less common form of threat to information, but can be highly successful if deployed in a very specific location, and it is an unfortunate fact of life that much of this cannot legally be prevented, since wireless networks operated in unlicenced bands of the radio spectrum.
Many of these hazards affect a wide geographic area, and can cause serious disruption to multiple organisations rather than to a specific organisation or system.
Communications failures
Failures in communications networks can have considerable adverse consequences in the area of availability. Their causes are varied, ranging from accidental damage by utility companies digging up underground cables, and cable theft, especially for the copper content in many cables, to utility failures in and between communications centres, and severe weather, which can quickly disrupt both wired and wireless traffic.
Power failures
Fortunately in the UK generally, wide-area power failures are relatively uncommon, since the national grid is extremely robust. However, localised power failures are more frequent due to the nature of network design, since the level of resilience decreases at the lower levels of the network.
In some countries, however, power failures over wide areas are commonplace and regularly restrict the availability of access to information sources.
ERRORS AND FAILURES
Errors and failures fall neatly into two categories – those made by users and technical staff, and those things that simply fail. Neither form is regarded as being malevolent, even though some user and technical errors are caused by lack of attention or poor training. Despite the view of many technicians that both hardware and software is designed to cause them grief, there is no evidence to suggest that this is actually the case. Examples of error threats are discussed below.
Software failures
Software failures are relatively uncommon, since most software is tested exhaustively before it is distributed and manufacturers usually fix bugs very quickly, as customer satisfaction is normally high on their list of priorities. Software failures are more common when two applications, normally from different manufacturers and which usually work well together, cease to function in the expected manner, usually when one or the other has been updated without robust interdependency testing.
Software interdependencies
As organisations’ information infrastructures become increasingly complex, the interdependencies between software applications grow exponentially, and it sometimes only takes a minor change in one to cause a serious downstream problem in one or more others, hence the need for full regression testing becomes of prime importance.
In 2012, a UK mobile telecoms provider began the rollout of a new customer database and, despite their best efforts to verify the software before rollout, the software failed under load and almost half of their 22 million customers were without service for several hours. There have also been numerous examples in recent years of high street banks updating their software, only to find that failures have locked customers out of their online accounts and prevented scheduled transactions from taking place.
System overloads
System overloads are far more frequent, and it is often the case that websites are unable to cope with sudden increases in demand for sales or services. In May 2014, the Ticketmaster website selling tickets for the 2014 Commonwealth Games in Glasgow put an additional 100,000 tickets on sale, and suffered a major overload problem resulting in people unable to access the site and people who thought they had obtained tickets but had not.
During the 2020 coronavirus pandemic, people were encouraged to use online shopping rather than visit supermarkets. This resulted in the main food retail organisations experiencing major overloads on their websites.
Hardware failures
Hardware failures are much more common than either of the previous examples. Although systems hardware has become increasingly reliable in recent years, failures do still occur and, unless the organisation has invested in resilient systems, duplication of key elements or DR, customers can find themselves unable to access the services they require, resulting in delays, frustration and ultimately bad press for the organisation concerned.
User errors
Errors made by users form a significant threat to information, since it is very easy using commonly available office applications to change files or filenames, either deliberately or accidentally, to delete files or to change file contents, all with no means of control, and users frequently do not realise their mistakes until long after the event.
Although backup and restore processes should address this, sometimes the backup media has been damaged or overwritten, and also the user may be reluctant to admit their mistake and request the restore of a file.
This type of failure especially affects shared storage resources, including both internal shared drives and external cloud services, where any one of the users sharing the storage facility can inadvertently or deliberately delete or modify files.
Technical staff errors
In theory, technical staff errors should be less frequent than user errors, since technical staff should have received appropriate training for their role. However, mistakes can and do occur, and it is an unfortunate fact that technical staff may well have greater system access privileges, and can do more damage with a single keystroke or mouse click than an ordinary user can.
Internal and external software errors
Generally, all software applications that are used by both large and small organisations have been thoroughly tested for functionality prior to their release, so failures are relatively uncommon but still can and do happen. More prevalent (and potentially more dangerous) in computational software, errors can at best lead to poor decision-making, and at worst could have life-threatening consequences if, for example, an application recommended the dosage of a drug to be significantly greater than would be safe.
Change failures
Change failures are often identical to technical staff errors, in that changes are incorrectly made to systems, applications and information. However, the other option here is that changes might have been incorrectly specified, with the possible result that the change either simply did not work as expected, or that the change made matters worse.
This particular type of threat reinforces the need for thorough testing following a change and also, later in the information risk management process, to examine the results of risk treatment to verify that it has been effective and that it has not introduced additional problems.
SOCIAL ENGINEERING
Social engineering is a technique used by hackers and other ne’er-do-wells to acquire information, generally about access to systems (both electronic and physical) so that their hacking activities are simplified. Social engineering comes in several forms – not only the traditional approach where a hacker attempts to engage with a user by conversation (usually over the telephone or by email), but also by disguising malware as legitimate software and web links and by copying the style, naming conventions and language of a target organisation. For example, they may send a user an email that appears to originate from their bank, but in which embedded web links take the user to the hacker’s own website. Examples of social engineering threats are discussed below.
Spoofing, masquerading or impersonation
Spoofing, masquerading or impersonation is a very common approach to social engineering. It is often achieved by electronic means, in which an email that purports to come from an organisation with whom the subject may have had dealings is sent to a number of recipients, but in fact may lead them to carry out an action that captures some of their personal information. Alternatively, it may take them to a website containing (usually false) offers of goods or services, or may infect their computer with malware (see a more detailed description in the Malware section).
Phishing is the act of trying to conduct a scam of some kind by contacting people, usually by text message or email, and either offering them something (frequently at a ridiculously low price) or telling them that they owe money in some way. The recipient clicks on a link in the message and is taken to the scammer’s website where they are relieved of their money. Phishing can either be used in the context described above, or as ‘spear phishing’, in which specific individuals are targeted rather than the general population.
Spoofing, masquerading or impersonation by phishing may also take a more personal approach, in which direct contact is made to the victim inviting them to take some action or other, again usually with unfortunate consequences.
Whatever the method used, the main objective is usually to obtain information that can be used to commit crime – to steal money or to order goods and services to be paid for by another person.
Spam
Spam is a technique frequently used to carry out phishing attacks, by enticing the target to click on a malicious web link or to provide information to the attacker. Many internet service providers (ISPs) use sophisticated systems to detect known spam email and to quarantine it in a ‘spam folder’, which the user can then examine and decide whether or not the message is genuine.
Attackers who make use of spam do not care if 99 per cent of their messages are trapped and deleted in this way, since the remainder will reach their destination, and a percentage of these will still result in a successful attack.
Disclosure
Disclosure of information is generally accidental in nature, and most social engineering is designed to fool the target into disclosing personal or sensitive information without realising that they have done so.
A typical example of this might be where the attacker calls the target on the telephone and purporting to be their bank requests the first and third digits of their security PIN for identification. They then might say there was noise on the line and ask for the second and fourth digits, thus gaining the full PIN.
Most social engineering attacks rely on the fact that target individuals have a fundamental belief that they are either talking to or exchanging information with a genuine organisation.
MISUSE AND ABUSE
Whereas hacking is usually deemed to originate from outside an organisation, misuse normally originates from within. The net result may well be the same for either approach but, in the case of misuse, the internal user or technician has the added advantage of already being on the right side of the organisation’s firewall and security systems, may have access to the required passwords and have suitable access privileges. For this reason, threats from internal attackers potentially present significantly greater levels of likelihood of success than those of external attackers. Examples of misuse threats include the following scenarios.
Modification of system access privileges
Whenever hackers succeed in penetrating a network, one of their first actions will be the modification of system access privileges so that they can explore systems and steal or change information. Naturally, this is much more easily accomplished if the attacker is already within the organisation – actually connected to the network. Systems administrators are generally well placed to undertake this kind of activity, and this frequently takes place as a result of poor control of passwords and the reluctance to change default user IDs and passwords on new systems.
Unauthorised systems activity
Misuse itself can cover a variety of activities, and includes unauthorised system activity, in which users probe systems on an organisation’s network to find out what information or software is available to them. It can involve the abuse of other privileges, such as the ability to send email using the organisation’s domain name, or, more commonly, abuse the availability of the internet to download material such as pornography, pirated software, music and films. Inappropriate use of the organisation’s internet connectivity can also result in the organisation becoming infected by malware.
Software theft and business information theft
Misuse can also cover the sending of proprietary information to persons outside the organisation, including the theft of the organisation’s software, the use of the organisation’s facilities to run a business and the posting of derogatory or abusive comments on social networking websites.
Finally, a form of misuse that has hit the headlines is that of confidential information or laptop computers containing confidential information being left unattended – in taxis or on trains, for example. In 2008, secret government documents detailing the UK’s policies towards fighting global terrorist funding, drugs trafficking and money laundering were discovered on a London-bound train and handed to a national newspaper – and there have also been numerous reports of government security officials having unencrypted laptops stolen from vehicles.
PHYSICAL THREATS
Many physical threats are also carried out by employees – many will have access to systems and equipment that they can easily remove from the organisation’s premises without the fear of discovery, whereas an external attacker would have to pass through the organisation’s layers of physical security in order to do so.
While unauthorised access to an organisation’s premises in itself is not really a threat, it is what an intruder could achieve once within the perimeter that should concern us. The problem is compounded in cases where a legitimate visitor is left unattended in an organisation’s premises and is able to wander at will within a supposedly secure environment.
Theft of computers and portable devices
Desktop computers are quite difficult to steal, but laptops, tablet computers and smartphones are relatively easy to slip into a briefcase or pocket and be taken from a building before the alarm can be raised. However, even the theft of larger computers and racks of servers has been known, and criminal gangs have stolen significant numbers of high-end systems and networking equipment to sell on the black market. With any of these systems, laptops, tablets or smartphones go the information they hold and quite possibly also details of access permissions to other systems or services.
Theft of authentication devices
The theft of authentication devices is less common, but used in conjunction with a user ID and password or PIN, may allow an attacker easy access to systems, often over the internet, so that no physical presence on the organisation’s premises is necessary.
MALWARE
The term ‘malware’ is used to refer to any form of malicious software that can be used to attack an information system. Examples of malware include software entities that result in the collection of, damage to or removal of information. Such software is almost always concealed from the user, often self-replicating – attaching itself to an executable program – and can spread to other systems when the user unwittingly activates it.
Some malware makes no attempt to conceal its existence, but appears to the user as legitimate software. Its purpose, however, is usually very similar in that it may collect, damage or remove information when the user activates what they believe is a legitimate program. Examples of malware include the methods discussed below.
Viruses
Viruses must always be attached to another piece of software or data – often legitimate – and may be activated by the user opening an email attachment or executing a program to which the virus has been attached. In the early days of computer viruses, most were harmless, but gradually they have been developed to become highly sophisticated and malevolent. Some will encrypt a user’s hard drive so that it can no longer be accessed, and the user will subsequently receive a ransom demand for money to unlock the encryption. Other users will simply have their personal information stolen.
Worms are very similar to viruses in terms of what they are designed to achieve, but do so in a rather different way. Worms do not require other software or data to spread, seeking out other targets over networks to which they are connected – and they can do so extremely quickly. In 2003, the Slammer worm is reputed to have infected 75,000 computers within 10 minutes.
Back doors
Back doors provide a means for an attacker to access the computer and use it for their own purposes without the need to undergo any authentication checks. Back doors can be used to turn the computer into a ‘botnet client’ that can be used under remote control by an attacker to send out spam email or to launch a distributed denial of service (DDoS) attack.
Trojan horses
Trojan horses are much more successful than any other method of attacking a target. These are often disguised as legitimate software or hidden inside compromised files, which users are lured into downloading and/or running. They successfully avoid security countermeasures because users having accounts with administrator privileges allow the Trojan to run.
Another highly successful means of infection is by the use of compromised websites. Trojans can download themselves without the user needing to click on any links on the web page, and the simple act of visiting an infected web page can be sufficient. An increasing number of criminal organisations are making full use of sophisticated Trojans to attack target systems in order to capture information.
Rootkits
Rootkits are more complex software applications that hijack the user’s operating system and make themselves invisible both to the user and to any security software. They frequently still perform all operations that the user has requested, but they can also make duplicate copies of sensitive information such as user IDs, passwords and account details and then transmit them to another computer. Rootkits are often used to enable financial fraud or identity theft.
Spyware
Spyware is a common example of the use of cookies by websites, some of which are designed to be persistent and to track and report the user’s web usage back to a third party without the user’s knowledge. Some spyware can log the user’s keystrokes and search for specific information such as bank account login credentials. Other versions have been known to install software that dials premium rate telephone numbers on those computers that are still connected to modems in order to generate revenue for the attackers. Spyware can also be installed by software that performs a legitimate service such as freeware.
Active content is the mechanism by which Trojan horses can be downloaded to a computer through its internet browser. Modern web applications use active code to perform complex tasks within the web page to improve the user’s experience. There is no doubt that they are extremely good at achieving this, but they are also ideal for installing malware on a target computer. Failure to set the appropriate level of security in the browser will allow the compromised code to be installed and to run itself on the target without the user’s knowledge.
An example of this type of attack is where a banner advert runs on a well-known, usually reliable and frequently visited website, in which the Hypertext Markup Language (HTML) code for the banner has been supplied by a third-party advertiser. The attacker adds the Trojan horse software into the banner HTML code and people view the website thinking it trustworthy because of the reputation of the organisation, little realising that the advert is infecting their computer. The payload can be any of the forms of malware described earlier in this section.
Botnet clients
Botnet clients are systems that have been infected with a particular form of malware that allows a botnet controller to make use of the resource for whatever purpose they have in mind. This might be in order to mount a phishing attack to gain information, to send out large quantities of spam with much the same aim in view or to mount a DoS attack on one or more websites.
Ransomware
Ransomware is simply another variety of Trojan that downloads onto a computer and generally encrypts user files or the entire hard drive. The malware then notifies the user that their machine can be unlocked after paying a ransom fee.
A particular example of ransomware was that of the WannaCry attack that took place across 150 countries in 2017. It was designed to exploit a vulnerability in the Windows operating system, having been allegedly originally created by the United States National Security Agency and leaked by a hacking group.
It is reputed to have affected 230,000 computers globally – including a third of hospital trusts in the UK, and costing the National Health Service as much as £92 million. Users were locked out of their systems and the ransom being demanded by payment in Bitcoin.