APPENDIX A – TAXONOMIES AND DESCRIPTIONS
Taxonomies are simply ways of ordering or classifying information and can help us to understand concepts through either diagrams or written explanations. For clarity, this appendix includes both forms for the following areas:
- an overall taxonomy of information risk;
- typical impacts or consequences.
It should be noted that these are simply the author’s interpretation, and are not necessarily complete in terms of all possibilities, or to the deepest level of abstraction.
INFORMATION RISK
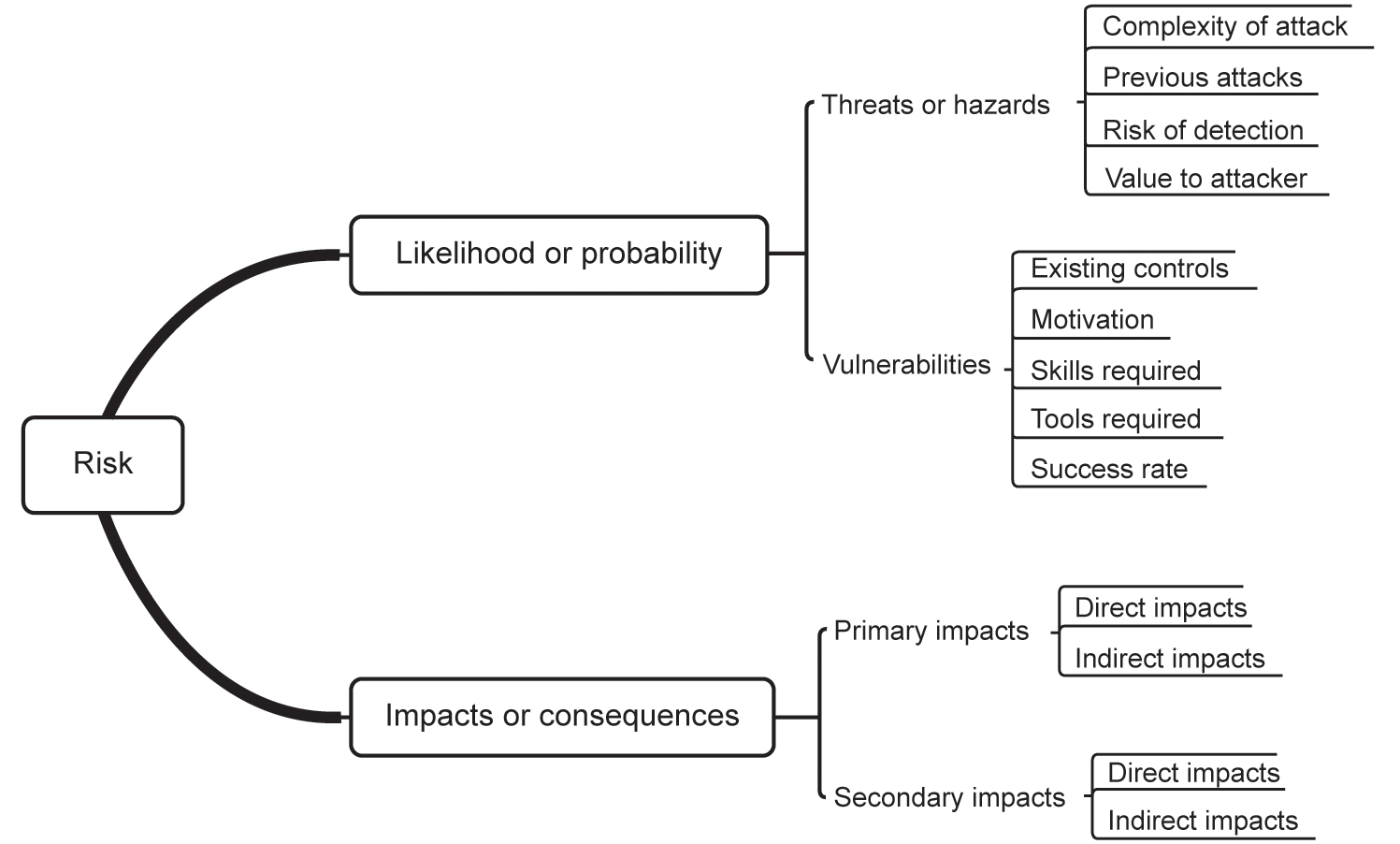
Information risk is the combination of the impact or consequence of a threat or hazard on an information asset and the likelihood or probability of its doing so. Figure A.1 illustrates the key components.
Figure A.1 An overall taxonomy of information risk
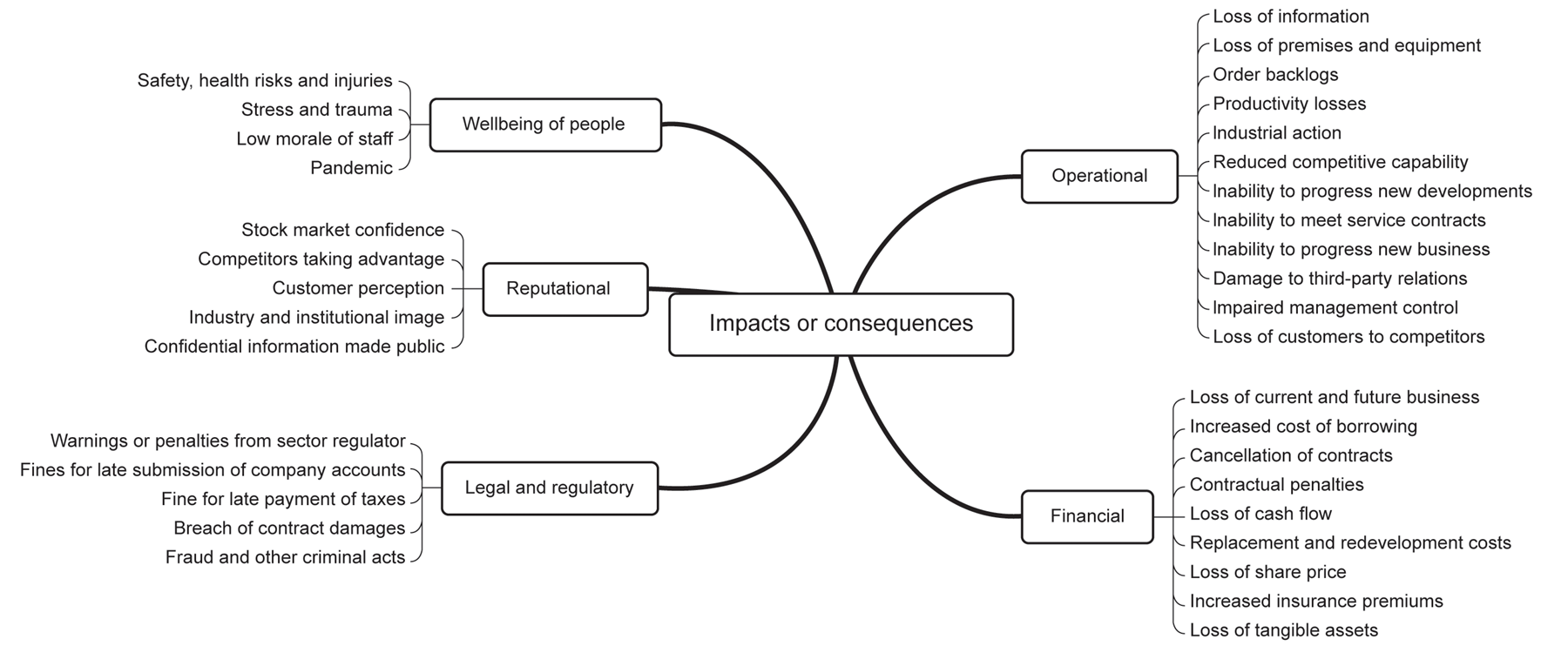
The impact or consequence of an event is the successful result of one or more threats acting upon one or more vulnerabilities of an information asset. They are categorised as follows:
- Primary impacts are those that result from the event itself, when a business function is detrimentally affected or unable to continue.
- Direct primary impacts; for example, if a customer database is hacked and personal information is stolen, the organisation will lose control of that valuable information resource.
- Indirect primary impacts; indirect impacts are those that may occur as a consequence of the direct impact. In the above example, the Information Commissioner may levy a fine against the organisation for failing to adequately protect the information.
- Secondary impacts are those that result from responding to or recovering from the event.
- Direct secondary impacts include such things as customers purchasing their products or services from another supplier.
- Indirect secondary impacts include such things as fines imposed for failing to file statutory returns on time because the information is unavailable.
The section Typical Impacts or Consequences lists and describes the various types in more detail.
Likelihood or probability
Likelihood expresses the possibility that an event may occur, but places no certainty on it doing so. Probability, on the other hand, expresses a greater degree of certainty, in that it is based on mathematical or statistical information computed by or gathered by research. The two terms are sometimes used interchangeably, but it should be remembered that likelihood is a qualitative view, whereas probability is a quantitative view.
Threats or hazards
Some threats are malevolent in origin, such as hacking and social engineering, while others are non-malevolent, such as environmental threats and simple failures.
The likelihood will be influenced by:
- The value of the information asset to an attacker – in cases where an attack is from a malevolent source, the value of the information asset to the attacker will contribute to the lengths to which the attacker will go in order to carry out the threat.
- The complexity of the attack – some threats can easily be carried out, especially where automated tools are available to the attacker. Others will require considerably more technical expertise, and are unlikely to be undertaken by so-called ‘script kiddies’.
- The risk of detection – in the case of some types of attack, the attacker must spend significant amounts of time in carrying out the attack. The risk of detection increases with time, and those attacks that can be carried out more quickly may be adopted more frequently.
- Previous attacks – those threats or hazards that are known to have already occurred will have a considerable bearing on the likelihood of an attack succeeding, since details of them may be available to an attacker.
Appendix B lists and describes various types of threats and hazards.
Vulnerabilities are weaknesses in or surrounding the information asset, which a threat might exploit in order to compromise the information asset. Vulnerabilities may be: physical, such as inefficient locks; technical, such as poorly configured firewall rules; or procedural, such as a lack of segregation of duties. They have the following contributing factors:
- Existing controls – the presence and strength of existing controls will determine the probability that an information asset will be able to resist an attack.
- The motivation of the attacker – this might be either revenge or financial gain for the attacker, or conversely it might be financial disadvantage for the information asset owner.
- The technical skills required to successfully attack on an information asset.
- The tools required in order to carry out a successful attack, many of which are freely available on the internet.
- Success rate – the previous success rate of a type of attack, if this is known.
Appendix C lists and describes various types of vulnerabilities.
TYPICAL IMPACTS OR CONSEQUENCES
Figure A.2 illustrates and describes some of the possible impacts or consequences that might arise as a result of a successful threat against an information asset.
Operational impacts
Operational impacts are generally experienced rapidly by the organisation. Most are very obvious – for example, when information to which they expect to have access is no longer available or which they can plainly see has been dramatically altered.
Very often, direct operational impacts will result in subsequent indirect financial impacts, so an inability to meet a service contract may well result in lost orders or in claims for contractual damages. Operational impacts include:
- loss of data (confidentiality, integrity and availability);
- loss of premises and equipment;
- order backlogs;
- productivity losses;
- industrial action;
- reduced competitive capability;
- inability to meet service contracts;
- inability to progress new business or developments;
- damage to third-party relations;
- impaired management control;
- loss of customers to competitors (churn).
Financial impacts
Unsurprisingly, financial impacts or consequences are normally those that gain the greatest attention within the organisation. It is frequently against a backdrop of possible financial loss that the costs of remedial actions will be compared. While this is certainly correct, it is also true for other types of impact as well.
Many of these impacts – for example, lost sales immediately following the event – will be felt very quickly, while others – for example, increased insurance premiums – may not manifest themselves until a later date, possibly some considerable time after the costs of the event have been counted.
Financial impacts may also not be as noticeable to the whole organisation – for example, staff may not be aware of the financial implications of an event at all, and have no appreciation of the position in which the organisation finds itself until they read about it in the media or find that pay increases and bonuses are reduced. Financial impacts include:
- loss of current and future business opportunities;
- increased cost of borrowing;
- cancellation of contracts;
- contractual penalties;
- loss of cash flow;
- replacement and redevelopment costs;
- loss of share price;
- increased insurance premiums;
- loss of tangible assets.
As with reputational impacts, legal and regulatory impacts can have serious repercussions on an organisation, and the handling of these is best dealt with by a specialist team within the organisation, who may communicate information regarding an event through the corporate communication department. Legal and regulatory impacts include:
- warnings or penalties from the sector regulator;
- fines for late submission of company accounts;
- fines for late payment of taxes;
- breach of contract damages;
- fraud and other criminal acts.
Reputational impacts
Reputational impacts are almost always highly detrimental to the organisation. For this reason, many organisations employ communication specialists who are skilled in countering negative publicity and putting a positive spin on any bad news. In such organisations, most staff are advised not to talk directly to the media, but to pass enquiries through to the corporate communication department. Reputational impacts include:
- stock market confidence;
- competitors taking advantage;
- customer perception;
- public perception;
- industry and institutional image;
- confidential information made public.
Wellbeing of staff and the public-at-large
Although more rare, safety incidents are generally highly visible outside the organisation, and occasionally have an effect on the public-at-large. More common, however, are any events that may have an adverse effect on the organisation’s staff, and these can also cascade into financial and operational secondary impacts. Wellbeing impacts include:
- pandemics;
- safety, health risks and injuries;
- stress and trauma;
- low morale of staff.