Employment and Social Media
This chapter discusses how social media can be used by individuals to find job opportunities, and by organizations to find potential candidates for employment. Throughout this chapter, we will discuss possible risks related to these endeavors, and how to minimize them. This includes password security, settings in LinkedIn, and legal issues related to using social media to find employment or candidates.
Keywords
Social networking; social media; communications; privacy; security; employment; branding
Information in This Chapter:
• Using Social Media to Find Employees
• Using Social Media to Find Employment
• Limiting Personal Information
Employment and social media
If you’ve looked in the want ads of your local newspaper, you might notice fewer jobs being advertised. While times are tough during an economic downturn, this doesn’t mean there aren’t any jobs. You may just be looking in the wrong places. According to a survey by Pew Internet & American Life Project, as of May 2013, 72% of adults on the Internet use social networking sites, so it should come as no surprise that this has also become the new landscape of a job hunt. Human resource professionals and hiring managers are looking for quality applicants online, where many candidates are finding success in locating available positions in their fields.
As we saw in the last chapter, the number of people using traditional news sources is declining, while the number of people using social media for information is increasing. More and more, businesses are tapping into using social networking and other online resources to advertise positions. Positions may be advertised on corporate Web sites, online databases called job banks, and online communities for posting classifieds like Kijii (www.kijii.ca, www.kijii.it, etc.), eBay Classifieds (www.ebayclassifieds.com), and Craigslist (www.craigslist.org). They may also be found using any number of social media sites like Twitter, Facebook, and LinkedIn.
Using social media to find employees
Looking for employees online has become a common process for many companies. If you’re looking for people with a specific skill set, experience, or education, it’s as easy to search for that person as it is to shop for anything else online. Not only does it allow employers to find new talent, but it gives them the ability to view information on a person prior to contacting them with a job offer.
In 2012, Jobvite (www.jobvite.com) conducted a survey of professionals in Human Resources and recruiting and found that 92% of American companies are using social media to find potential employees. When asking them which social networks are being used to find employees, they found:
• 93% used LinkedIn (www.linkedin.com)
• 66% used Facebook (www.facebook.com)
• 54% used Twitter (www.twitter.com)
The fact these three sites are primarily used should come as no surprise. As LinkedIn is used for business social networking and allows users to post information as an online resume, it has the perfect design for finding the candidate you want. The survey found that almost half of employers using social media to find candidates found more people to choose from than traditional methods, and that the quality of those candidates were an improvement. When fishing for talent, you want a big pool, and these three are currently the major sites people use for social media.
Using social media to find employees has a good record of achieving results. The survey found that 73% of employers were successful in hiring someone through social media. Of those hired, 89% were found on LinkedIn, 25% through Facebook, and 15% on Twitter. Being that so many organizations successfully use social media, it’s in your company’s best interest to pursue this as a method of finding employees.
There are a number of ways to find potential employees using social media. LinkedIn Recruiter (http://talent.linkedin.com/Recruiter) is a tool that is specifically designed for finding candidates who have setup a profile on LinkedIn’s site. The tool allows you or your Human Resources department to find candidates on LinkedIn. This means you don’t necessarily need to hire an outside headhunting firm to find potential employees on your behalf.
Even if you don’t use the tool, LinkedIn allows you to search people’s profiles. If you go to LinkedIn and type keywords describing a position you’re looking to fill into the search field, the results returned will be a listing of people with those attributes mentioned in their profiles. If you want to narrow down your search even further, click on the Advanced link beside the search field, and you can search for people by a combination of criteria like location, industry, title, company and other criteria.
LinkedIn allows organizations to create their own company pages, and gives them the opportunity to post job openings. These available positions will then be suggested to people who have skills related to your advertised job. In seeing these available jobs, even if a person isn’t looking they may be intrigued by an opening with your company.
One of the simplest ways of finding candidates is to create a page on your existing Web site, and then advertise the position on social media. The Web page describes the details of the job, but you advertise by tweeting the link to it on Twitter, and posting comments on Facebook and LinkedIn. You should also take advantage of your employees’ social networking and encourage them to advertise a link to the job, as this can reach an even greater number of potential applicants.
Another method of using social media to attract candidates is to create a video that promotes your company and tells people why they would want to work there. By uploading the video to YouTube, it can reach a wide audience, and you can reach even more people by posting links to it on LinkedIn, Facebook, and Twitter. To make a job ad more interactive then a textual advertisement, you could also create a video that tells people about important job openings in your organization.
While advertising an existing job can attract people who are actively seeking employment, you should also try and find passive candidates. A passive candidate is someone who isn’t aggressively looking for another job, but might consider it if he or she were asked. If you find someone who peaks your interest, offer the job. You may be pleasantly surprised.
Candidate screening
The percentage of businesses that screen candidates and do background checks through social networking is a minority, but it is debatable whether this will increase or decrease in the years to come. As we’ll see in this section, existing and new legislation, potential lawsuits, lack of verifiable data, and privacy concerns have caused hiring managers and Human Resource professionals to stop using social media to screen applicants. However, although a minority, there are still a large number of employers who research a potential employee’s social media activity to determine whether he or she matches what a business is looking for in an employee.
According to a 2012 survey conducted by Harris Interactive for CareerBuilder (www.careerbuilder.com), 37% of hiring managers and Human Resource professionals used social media to research job candidates, and of those who didn’t 11% were planning to. In screening candidates this way, there were a number of things employers were looking for when doing their research:
• 65% were looking to see if a person conducted himself or herself professionally
• 51% were trying to determine if the person was a good fit for the company
• 45% were doing research on the person’s qualifications
Acquiring this information through social networking sites may be done in a variety of ways. A simple method involves using search engines like Google, or (as we’ll discuss later in this chapter and Chapter 10) those that do deep Web searches that search public records not normally indexed by standard search engines. Using these tools, you can find a considerable amount of information including that found on social networking sites. Of course, the easiest way is to visit social media sites and view the person’s profile pages and posts. If a candidate hasn’t set his or her privacy settings to limit access to information, then everyone can see it.
When screening a candidate you don’t know, mistakes can be made. It’s important to remember that there is a lot of false information on the Internet, so you can be mislead by what you read. Also, if the applicant has never had an interview, then the employer would never know what he or she looks like. As such, they wouldn’t be able to recognize any photos on the site, and could easily mistake another person with the same name for the applicant.
The 2012 survey, CareerBuilder found that 15% of the companies didn’t research candidates using social media because their organization prohibited it. They have this policy for good reasons. A 2011 survey by the Society for Human Resource Management provided a breakdown of the rationale of companies who don’t use social media for screening, and included the following reasons:
• 66% were concerned about legal risks related to finding information about a protected status
• 48% were concerned about the ability to verify the information found on a person’s social networking page
• 45% were concerned that information about the candidate might not be relevant to the person’s potential or performance on the job
• 34% recognized that all of the candidates might not have information on these sites
• 33% were concerned that information they found about a candidate might not be relevant as to whether they were a good fit for the company
Screening applicants with social media could make a company vulnerable to lawsuits. If a site showed a candidates race, religion, gender, sexual orientation, disability, or something else protected by existing legislation, it’s possible that the organization could be sued for discrimination when not offering employment. The company would then need to prove that the information didn’t influence their decision not to hire the person. On the other hand, if there was something on a site indicating a propensity for violence or some other criminal behavior, you could be at risk of a negligent hiring lawsuit since the information was available but you did nothing. A good way to avoid this problem is to hire a third party to do the screening, specifying that you want to receive only the information that you indicate.
Asking for a prospective or current employee’s password
Over the past few years, there has been a growing trend for employers to demand the usernames and passwords for any social media sites their employees belong to, and for candidates to provide these credentials as a condition of employment. It has even extended to universities and colleges demanding this information from current students, and those applying to the schools. The demand to violate their privacy is simple: if you want to be here, we want to see what’s on your social media sites.
One highly publicized case is that of Kimberly Hester, a teacher’s aide from Frank Squires Elementary School in Cassopolis, Michigan. A parent complained to the school about a photo on Hester’s Facebook account, which showed a pair of jeans bunched around her coworker’s ankles. It showed no nudity, and only showed the jeans around the ankles. Hester and the coworker were called into separate meetings with the school principal, Peter Bennett, and the school’s district superintendent, Robert Colby. During the meeting with Hester, the two men produced 32 pages of comments her coworker had made with Facebook friends and family, and had circled comments they felt were inappropriate.
The hysteria of the traveling pants did not end there. They wanted Hester’s username and password, so they could review her account. Hester refused, and she and the coworker (who eventually resigned) was given a five-day suspension. Hester fought the action, and was assigned as an aide to a class run by Colby’s wife, told to do 47 online courses dealing with topics like fire extinguisher safety, and prohibited from talking to coworkers or to bring her cell phone on school grounds. Ultimately, she was put on unpaid leave as the union and school district argued her case. Once an arbitration process is completed, a lawyer provided by the union has plans to take the case to Federal court.
Unfortunately, there are reports throughout the world of employers demanding such information from their employees, and candidates who are hoping to gain employment. As many people are fearful of losing their job in a recession or desperately want to get a job, many of those asked will begrudging provide the information, even though it means violating the terms of service most social media sites have. Many sites including Facebook have a security rule about not sharing your password with others, meaning that the employer is forcing the person to break these rules.
If you’re concerned about your employer asking you to reveal a username and password to a personal social media site, you would do well to review any existing corporate policies involving password security. Many organizations have policies related to technology. These are often created by an IT department, and specify that you are not allowed to share passwords with other people. The rule exists to keep passwords secure, so employees don’t share accounts with coworkers, and (as we’ll discuss in Chapter 7) to prevent social engineering. If your company has such a policy, then it probably isn’t specific as to what passwords are okay to share, and which ones aren’t. As such, you could try refusing to provide the password on the basis that it violates an existing corporate policy of not sharing passwords.
For employers thinking of requesting this information, you should be concerned about violating an employee’s privacy. Such demands have an effect on morale, and will probably damage any positive relationship a manager has with his or her employees. Also, it may have an impact on security of internal passwords. After all, if an employer doesn’t care about an employee’s personal password security, the employee may feel the same about the corporate passwords he or she uses. Of utmost importance however, employers should also be concerned whether existing laws or pending legislation will make your demands for a social media user’s credentials illegal.
Legal issues
If you’re lucky, you may live in an area where there is legislation protecting your rights to privacy, so you’re not required to provide your password to an employer. In California, Assembly Bill 1844 prohibits employers from requiring employees and job candidates to disclose their login credentials to social media sites, demand access to personal social media in the employer’s presence, or provide any information on personal social media content. If you refuse an employer’s demands under this bill, you cannot be disciplined or fired.
Another piece of legislation to protect social media users in California is Senate Bill 1349, which protects students and prospective students. Those enrolled or applying to postsecondary institutions can’t be asked to provide their usernames, passwords, and other information related to social media. In doing so, colleges and universities can’t demand that applicants and current students provide access to social networking accounts as a condition of being a student.
However, while this directly addresses demands to provide your user credentials, it does not address other methods of accessing data. There are a number of tools available on the Internet that can be used to perform background checks of people by searching publicly available information and public records. One such tool is BeenVerified (www.beenverified.com), which enables you to perform online background checks, and also offers an app for iPhone. In using this tool, it will look up information collected from thousands of public records and other sources available to the public, and allow you to view links to sites where the target of your search is mentioned. The results that are displayed can include information from social networking sites, photos, property records, criminal records, and personal information like current and previous addresses, phone numbers, and so on. The results may require some analysis, as more than one person with the same name may be returned.
Such tools and services that provide background checks have come under the scrutiny of the Federal Trade Commission (FTC), which enforces the Federal Credit Reporting Act (FCRA). This Act regulates how consumer information is collected, disseminated, and used. Under the Act, any company that provides a service of assembling and evaluating consumer report information for third parties is considered consumer reporting agency. Businesses that use reports by these agencies for such things as employment, credit, insurance, tenant screening, and checking qualifications for scholarships or educational programs are subject to the terms of the FCRA. For these reasons, the FTC has charged a number of companies for violating the FCRA, including those that offer apps or services for performing background checks and screening.
Complaints have been made against BeenVerified, and similar sites. In 2012, an online privacy service named Albine (www.albine.com) complained to the FTC that BeenVerified did not remove information when requested. Like many online sites that could be used for background checks, BeenVerified has an option to opt-out of information appearing through the searches. While it was initially removed, Albine found that it later appeared in searches. Albine itself provides a subscription service to have information removed from searches on such sites.
In June 2012, another site that collects and sells personal data to employers and recruiters was fined by the FTC. The FTC alleged that Spokeo (www.spokeo.com) posted fake endorsements for their services that were created by their own employees, and didn’t follow the steps required to protect consumers under the FCRA. The case was settled with Spokeo agreeing to pay $800,000.
Under the FCRA, consumers have the right to dispute inaccurate or incomplete information. As such, when requested, the provider of the information has to show you what information they have on you and give you the opportunity to dispute it. If there is any information that is inaccurate, incomplete or unverifiable, the agency who obtained the information has to correct it. Such agencies also can’t report on outdated information that’s negative. For example, if you went bankrupt, after 10 years the company could not disclose any information regarding the bankruptcy. In cases of credit reports, the act allows you the right to know your credit score.
Another important feature of the Act is that if the employer is running a background check on you, they must get your permission prior to doing so. This is needed when background checks are done for any employment decisions, including hiring, retention, promotion, or reassignment. The employer must tell you that the information from the consumer report may affect decisions made about the person’s employment, and has to be provided in writing. If the report may be used throughout the person’s employment, the employer must clearly provide this fact to the employee or candidate. The applicant or employee must then provide written permission for the check to be done. Upon getting this information, the employer needs to inform the consumer reporting agency that they have complied with the FCRA requirements, notified the candidate or employee being checked, and will not discriminate against them or misuse the information.
Using social media to find employment
Seeking employment can be more work than the actual job you find. It’s frustrating, time consuming, and occasionally disheartening. A problem people face when looking for a work is that they’re used to the traditional process of looking in the want ads of a newspaper, but the Internet has changed all that. As we’ve mentioned, today those jobs may be posted on Web sites, searchable in databases, or advertised through social media. However, social media isn’t just for employers to find candidates. You can harness the same tools to find employment regardless of whether you’re actively seeking work or waiting for an offer to come to you.
As with many things, the importance of being noticed is location, location, location. You want to be where the recruiters are looking, so you should start by having accounts on the major social media sites. As we discussed earlier, recruiters seek employees on LinkedIn, Facebook, and Twitter. While we’ll discuss LinkedIn in greater detail later in this chapter, for now remember that these will be your focal points in social media. They will provide connections to other people who can let you know of jobs that are available, promote yourself to potential employers, and enable you to be noticed by recruiters.
As we’ve seen from the previous sections, thinking that the first impression you make on an employer is during an interview may be wrong. In the age of social media, an employer can form an opinion by looking at a person’s online activities. They could be looking at how you’re presenting yourself, the photos you’re putting up, and the comments you’re making. As such, when posting content, you will want to keep this in mind and conduct yourself accordingly.
You should also consider other ways to get yourself noticed, and showcase your abilities. For example, writing a blog allows potential employers to see your communication skills, interests, knowledge of topics related to your field, and makes you memorable. Another way to advertise your skills and interest in a job is by posting a video on YouTube. The video could simply be a short clip of yourself talking about the type of job you’re looking for, and why someone should hire you. It will allow employers to put a face to your name, and give you the opportunity to sell yourself. With any content outside of your social networks, you should publish links to the video and new blog entries so more people will have a chance to view them.
In using social media to promote yourself and find work, don’t feel that you have to spread yourself thin. You don’t need to setup accounts on every social networking site you hear about. It’s better to have a few good profile pages, than try and use an overabundance of social media poorly.
As we’ll discuss later in this chapter, sites like LinkedIn allow you to search for jobs on their site, allowing you to find positions you’re interested in within a specified area. If there’s a particular company you’re interested in, you can also search for that business and view information about it and any advertised positions they may have available. Without using social media in your job search, you’re missing out on these potential sources of employment.
Getting referrals
You’ve probably heard the adage about how “it’s not what you know, it’s who you know” that gets you a job. Although we’ve all worked with a few people that may give the first part some credence, it’s the later part that’s a proven fact. Having someone referring you to an employer is a major asset to getting a job. If someone within the company can suggest you for a job, it can increase your chances of getting offered a job and being hired.
Since there are so many adults who use social networking, it’s fairly easy to find people in the same industry as you or employed where you’d like to work. By adding them as a connection in LinkedIn, following them on Twitter, and making friends with them on Facebook, you improve your chances of hearing when a job’s available or having them recommend you. In saying this, I am not recommending a sleazy tactic where you fake interest in people. What I am suggesting is rather than limiting yourself to having Facebook “friends” you met socially or to play games, make more career-related contacts. If I’m in the same industry as you, and we have similar interests, it makes sense to make you part of my network. If I like your previous tweets, I should follow you on Twitter. After all, if you talk about things I should know, it’s to my benefit to listen. Also, getting to know people at a company you think you want to work at may provide you with information that shows you really don’t want to work there.
Subscribing to blogs, following tweets, and listening to what’s being said by the corporate and personal accounts of a business and its employees is beneficial in other ways. During an interview, you’ll have better insight into the business, its products, and the direction it’s taking with various projects. Reviewing what a company is talking about gives you the ability to reiterate this information during the interview process, showing that you’re a knowledgeable candidate with great interest in the company.
Even though you’re the one looking for work, making these connections can also be of benefit to the other person. In fact, it can be money in their pocket. Because candidates who are vetted through existing employees have been found to be high-quality ones after being hired, many companies offer referral bonuses to employees. According to the Jobvite survey, 65% of companies encourage employees to refer potential candidates, with one-third of them offering a bonus of over $1000.
Branding yourself
In the previous chapter, we discussed the importance of branding. When it comes to finding employment, it’s important to remember that you are the brand being marketed. How you present yourself in different social media will have an impact on how potential employers will see you.
When looking at online profiles, a potential employer will look for things that make you shine in a positive light, and stand out from others who applied. Just as when branding a company, you want to brand yourself to inspire trust, reliability and instill confidence. The 2012 CareerBuilder survey found that 29% of employers found something on a candidate’s online profile that caused them to hire the person. There are a number of things employers look for in a good candidate:
• 58% felt they got a good feel for the person’s personality through the profile
• 55% found the person put across a professional image
• 54% found the person’s background information supported their professional qualifications
• 51% felt the person was well rounded and showed a range of interests
• 49% found the person had great communication skills
• 44% felt the person was creative
• 34% found great references had been posted about the person by other people
When looking for employment, you are marketing yourself, so you should design your online profiles to match how you want employers to perceive you. In crafting your profile pages, you’re trying to make employers remember you and want to interact with you. In saying this, it doesn’t mean to create a false persona. After all, if you’re trying to portray yourself as something you’re not, eventually the real you will come out and people will see behind the facade. You also don’t want to create a false representation of yourself because you want to work with people who like you for you. Much of your life will be spent with the people you work with, so you want them to accept you for who you are. In branding yourself, you want to show the best parts of yourself.
Although the belief of anonymity on the Internet is fading slightly, many people tend to lack self-censorship on their profiles and posts. Something they might not say in real life somehow manages to get tweeted or blurted into comment. These are things that can be held against you when looking for work. In the previously mentioned survey by CareerBuilder, 34% of the managers and Human Resource professionals researching candidates found reasons not to hire a person. These reasons included:
• 49% found photos and information that was provocative or inappropriate
• 45% found comments or photos that dealt with the candidate drinking or using drugs
• 35% found the person had poor communication skills
• 33% found the person had bad-mouthed previous employers
• 28% made comments against a race, gender, religion, or something else that could be considered discriminatory
If an employer screened you by looking at your social networking sites and didn’t like what they found, chances are you’d never know. In the 2011 survey by the Society for Human Resource Management, 73% of the companies who used social media to screen job applications never gave the candidate a chance to explain any questionable material. Because of this, you should check whether there’s any questionable material on your sites before they do.
At this point, you may be thinking of all the possible places you or someone else may have posted the wrong thing. After all, there’s probably a silly photo or two, but this isn’t the kind of things most employers or someone thinking of recommending you for a job would be concerned about. What would be a problem would be things like vulgar jokes, photos from parties where you appear drunk, or angry comments you made about the boss or a bad day at work. If there is anything like that on your profile pages, then it’s time for damage control.
Since the Internet is decidedly very big, the first thing is to decide where you’ll focus your efforts. The surveys we discussed help with this. The 2012 Jobvite survey showed that recruiters are primarily using LinkedIn, followed respectively by Facebook and Twitter when searching for new talent. The 2012 CareerBuilder site showed 65% of employers use Facebook, 63% use LinkedIn, and 16% use Twitter when researching a person for a job. These are the major social networking sites, so you should focus your efforts on cleaning up anything of concern.
What you need to do next is decide what you want on your pages. The comments and other content should be things you’d feel comfortable having a future employer or coworkers seeing. A good piece of advice is never have anything on your profile pages that you wouldn’t want your mother to look at. If you’d be embarrassed by it, then you should edit and delete. Another good method is to look at the photo or comment, and imagine it on a billboard at the side of a highway. Is it something you wouldn’t want to be seen in public? If so, get rid of it.
How you convey and type a message is also important. Employers look for good communication skills, and your abilities will be seen with every post and tweet. In the 2012 Jobvite survey, it was found that 54% of recruiters had a negative reaction to grammar and spelling mistakes, and 61% disliked profanity. Cleaning up what you say is important to how employers perceive you.
In pruning anything damaging from your profiles, you should put it into the context of the organizations to which you’re applying. For example, there’s nothing wrong with saying that you think a particular soft drink is the best you’d ever tasted, unless you’re applying to their competitor. It is a bad idea to make comments or jokes that place one company over another in the industry you’re seeking employment. Similarly, you want to make sure that you don’t go against the basic philosophies of an organization you’re applying to. If you’re applying to oil companies, tweeting that you’re against fossil fuels may not be your best move. Most importantly, remember there are comments no employer wants to see. As mentioned earlier, you want to avoid bashing your boss online, since possible future employers will wonder if you’ll do the same to them. When in doubt, try and look at your profile objectively, and ask “Would I recommend this person?”
By this point, you’ve probably realized that LinkedIn can be an essential resource for seeking employment. According to Pew Internet & American Life Project, as of August 2012, 20% of adults on the Internet say they use LinkedIn, which accounts for why a majority of recruiters use it as a primary social media resource for finding candidates who are actively and passively seeking employment.
After creating an account, you can create a profile page that lists the features of yourself that make you marketable. This includes:
• Contact information, inclusive to a Twitter account, Web site, Facebook page, email, blog, etc.
• Work and volunteer experience
• Skills and expertise, where people can endorse you as having proficiency
• Certifications and education
• Other information, such as publications, awards, and so on
In completing these sections, it’s important to be honest. Aside from ethical reasons, lying can get you in serious trouble later. If you were hired by a company and they later discovered you’d falsified your qualifications, you could (and probably would) be fired.
Completing the jobs sections on your profile is important, because not only do employers use it to review your skills, but LinkedIn will use it to suggest available jobs. After logging into LinkedIn, you’ll see a section on the right-hand side of the home page listing jobs you might be interested in, and you’ll receive a summary of them sent to you via email. A complete profile will provide you with more potential job opportunities.
By complete, I also mean to fill out the summary field that’s located at the bottom of your profile page. While you could enter any information you wanted, the box is generally used to provide a brief summary of yourself and goals you might have. If you’re fresh out of school or changing fields, you may not have anything in your job history related to a new profession. Using the summary box, you could include this information by writing a concise overview of your new or transferable skills.
Because the people you add as contacts will be used to suggest jobs within your social network, it is a good idea to extend this network by joining groups. LinkedIn groups connect you to a wider scope of people, allowing more people to know of you, which results in increased traffic to your profile. To find groups related to your job interests and skills, you can use the Groups menu at the top of LinkedIn’s pages to view suggested groups related to your information, view groups you belong to, browse a directory of groups, or even create a new one.
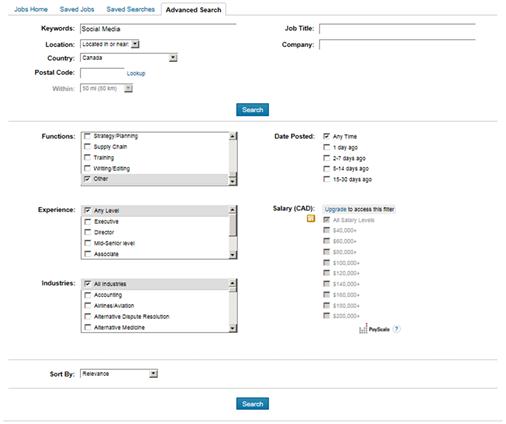
To search for jobs, you can click on the Jobs menu at the top of the page, and a page will appear providing a longer listing of available jobs related to your skills, those found within the network of people you’ve added as contacts, and a search feature. By entering titles, skills or companies of interest into the search field, a list of potential employers is returned. By clicking the “Advanced Search” link, it will expand to show additional criteria for your search, allowing you to narrow it down by country, zip code, industry, job functions, and (if you have a premium account) salary range. As seen in Figure 3.1, clicking the link for more options provides even more criteria to narrow your search results.
Using the search features may require some playing around. Depending on the criteria you enter, you may see a flood of results or filter out a lot of possible jobs. For example, if you selected only jobs posted in the last day, you will miss any opportunities posted 2 days ago. Because of the different methods available to find opportunities, the more you work with LinkedIn’s features, the better chance you’ll find your dream job.
Endorsements and recommendations
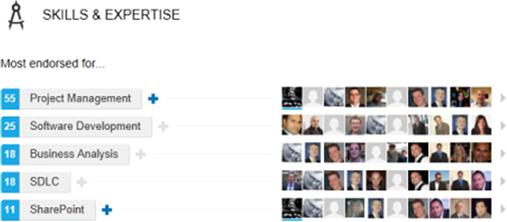
After entering your skills and experience into a profile, you can acquire endorsements from connections to verify that you have expertise in those areas. For example, if you said you were skilled at speaking another language, a connection who knew you were fluent could then provide an endorsement. As seen in Figure 3.2, your contacts can quickly endorse your expertise by simply clicking the plus sign beside a skill you’ve added.
When adding any items in the Skills & Expertise section, it doesn’t matter if they’re mentioned in other areas (such as education or work experience). People who are searching for these skills may find your profile page in their results, and can instantly see that other LinkedIn members have confirmed your skill set.
Getting endorsements can be done by connections who visit your profile, or by requesting your contacts to endorse you. Another method is to endorse others. People you endorse will get a notification, and many will reciprocate.
Another way that your contacts can confirm you’re a good job candidate is through recommendations. By hovering your mouse over the Profile tab on the top navigation bar and clicking Recommendations, a page will appear that lists your work and educational experience, and has an “Ask to be recommended” link beneath each entry. Clicking the link allows you to send an email to contacts asking them to recommend you. If they choose to recommend you, they can essentially write a short reference letter, showing their approval of you.
Creating a custom URL on LinkedIn
When you create a LinkedIn profile, the URL automatically associated with your page can be a complex and difficult to remember. For example, when initially creating my LinkedIn profile, it was given the URL of https://ca.linkedin.com/pub/michael-cross/31/746/b21. Not exactly the user-friendly address I’d want to include on a resume or link. To remedy this, LinkedIn allows you to create a custom URL for your profile. To illustrate the results, rather than being stuck with the mishmash of letters and numbers I’d been given, I changed mine to www.linkedin.com/in/mcross1.
Making such a change not only makes your profile more recognizable and in line with your personal branding, but can help optimizing how a search engine indexes a link to your page. If you include your business or name in the URL, there is a greater chance that it will rank higher in the results when someone searches for those words. To change your URL, log onto LinkedIn and do the following:
1. Hover your mouse over your name at the top right of the screen. When the menu appears, click Settings.
2. Click on the Profile tab, at the bottom left of the screen. By default, this will already be selected.
3. Click on the link labeled Edit Your Public Profile.
4. Scroll down until you see a box labeled Your public profile URL. Click on the link that says Customize your public profile URL.
5. When the screen appears, you’ll see the base URL of www.linkedin.com followed by a box. In the box, type in the end portion of the URL you want.
A common problem is finding that the name you want may have already been taken, and you’ll need to select something a little different. However, regardless of what you choose, it should be an improvement. With some effort, you should find something close to your name, or something that relates to how you want to present yourself to potential employers or colleagues.
Getting the word out
Because there are many possible ways on LinkedIn to find or be offered a job, it can be easy to miss the obvious step of telling people you’re looking for work. Let your LinkedIn contacts, Facebook friends, and Twitter followers know about your job search. In doing so, you may find that they know about a job opening and may even recommend you for it.
If you do let people know you’re looking for work through social media, be aware of who will view any announcements that you’re seeking employment. If you’re current employer doesn’t know you’re looking for another job, the two of you may get a shock if you’ve forgotten the boss or coworkers are your Facebook friends and LinkedIn contacts. Trust me when I say, this has happened more than once to people.
Limiting personal information
When you first setup your account in LinkedIn, the information you enter on your profile page is public by default. In other words, if I stumbled across your profile page using Google, I could view everything on your profile even if I wasn’t logged onto LinkedIn. If a criminal were to view this information, they could see where you worked, schools you attended, and anything else you entered into sections of the page. This can be useful in the wrong hands to steal your identity, so you should always limit the amount of personal information showing to others.
There are many different areas in LinkedIn where you can add, remove and configure information that’s displayed to others. As potential employers and contacts will use the information that’s visible on the page to search and review your experience, there will be some areas that you’ll want everyone to see, some that you’ll only want your contacts to see, and other facts you may want to leave completely blank.
Adding too much additional information
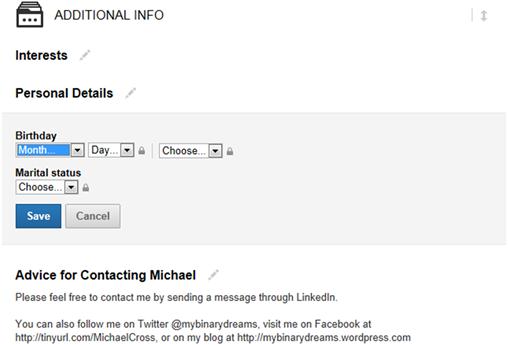
The profile page itself contains several areas that should be of concern. As seen in Figure 3.3, the Additional Info section contains fields where you can show your interests, birthday, marital status, and advice to contact you. Your birthday and marital status shouldn’t be included, as it could be used to discriminate you from being offered a position. If you do enter a birthday, avoid entering the year.
To remove personal details from showing in Additional Info area of your profile:
1. After you’ve logged on, hover your mouse over the Profile menu item on the navigation bar at the top of the screen, and click Edit Profile.
2. Scroll down to the section called Additional Info.
3. Click on the pencil icon beside Personal Details to edit that area.
4. Set the dropdown lists so they don’t show a birthday or marital status.
You should also be careful what you put in the Advice for Contacting you box, as you don’t want to include addresses, phone numbers, or other personal information that can lead to problems. LinkedIn allows members to send messages through the site; so many people invite others to use that.
As you’d imagine, you’ll find people have put some odd things that could raise eyebrows in the Interests section, so you’ll want to be careful what you add here. It’s always good to include interests that are relative to employment. Saying you have a love of eating, wine and spirits may be good if you’re a chef, but may go against you if you’re a diet consultant. Since recruiters look for well-rounded people (and in saying that, I’m not continuing the eating-related example), adding your more socially acceptable interests could also help you.
Another section to review when you edit your LinkedIn profile is the Summary section we mentioned earlier, which is found at the top of the page. The summary can be used to provide a brief description of your abilities, goals, education, and experience, but some people use this to enter contact information. You should never include your address, phone, email address, or other information in this section. While you’re essentially creating an online resume by filling out the fields on your profile page, you should remember that people can contact you by sending messages in LinkedIn. Since this is how people can contact you, you don’t need to provide anything else.
Public profiles
Your public profile is information that can appear to everyone, including those searching for you in search engines like Google or Bing. If I’m not a contact of yours or even a member on LinkedIn, I will still be able to view what you’ve allowed me to see on your public profile. As mentioned, when you first create the account, everything on the profile is public. Because it’s initially blank, this isn’t a problem, but it creates a growing risk as you fill up the profile with more and more information.
It’s up to you to limit what can be seen. Deciding what to include can be a precarious decision, because you want employers to see enough to offer you a job, but not anything that could allow someone to do such things as impersonate you, steal your identity, or apply for credit cards using the information on your page. In some cases, you may also want to limit exposure to information on your page because of the industry or position you work in. For example, you might want to prevent competitors from seeing a project you worked on, or your current position might require anonymity (as in the case of an undercover police officer). While much of what you publicize is a personal decision, there are some areas where you’ll want to limit access.
You should always make careful decisions when considering what information people are able to review browsing your public profile. To change what people are allowed to see, consider doing the following:
1. Hover your mouse over your name at the top right of the screen.
2. Click Settings on the menu that appears.
3. Click the Profile tab in the bottom-left corner of the screen.
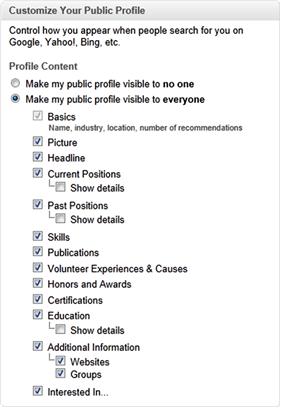
As seen in Figure 3.4, when the screen appears, there is a list of options at the right of the screen. By unchecking any boxes in the list, those areas of your profile won’t be visible to the public. At a bare minimum, you should consider unchecking the Show Details boxes under Current Positions, Past Positions, and Education. In doing so, people will be able to see jobs you’ve held and schools you’ve attended, but won’t be able to view any specifics related to them. Preventing these details from being viewed not only defends you, but may also protect your current and previous employers. The details provide information on the work you performed, and may include information on projects, procedures included in your duties, and systems used by an organization. For example, if you worked in IT, a hacker viewing the details of your job would probably see the types of servers, routers, and other systems that you have experience with and used by the employer. This could be very helpful in finding ways to compromise security.
In looking at the options available in the Customize Your Profile section, you’ll notice that the top one is Make my public profile visible to no one. Choosing this is the most secure, but will prevent anyone other than your connections from seeing your profile. If you’re actively or passively looking for work, then you would not choose this option. It is however useful if you’re not interested in a job and only using LinkedIn to connect with colleagues, access groups, or review information available through the site.
As you check and uncheck the boxes in this section, you’ll notice that your profile to the left of the box will change. The information appearing on the left side of the screen is a preview of your public profile, and allows you to see how things will appear to others as changes are made. Because changes are saved as you modify the checkboxes, you don’t need to click a “Save” button when you’re satisfied with how it looks.
Passwords
While we’ll discuss passwords in greater detail in Chapter 10, it is important to look at how passwords can be changed on sites like LinkedIn, and security issues that seem common among social media sites. Logging into LinkedIn requires two things:
For your email address, you should never post it so that others can see it on your profile page. If you do, a hacker will have half of what’s needed to logon. You should also consider creating a separate email account for social media sites, which are used for logging on and receiving email from the sites. If you have an email address displayed on social networking sites, consider creating an Outlook (https://login.live.com) or Gmail (www.gmail.com) account and displaying that on your pages.
The second part of your login is what most people associate with security, and make little effort in making secure. As we’ll discuss in Chapter 10, there are a number of tips that will reduce your chances of having an insecure password that is easily hacked. Some of these tips include changing it regularly every few months, and try and make it different from the previous version. When you do so, don’t make it easy to guess. For sites like LinkedIn, you should be aware of how to change the password:
1. After you’ve logged on, hover your mouse over your name at the top right of the screen. Click Settings on the menu that appears.
2. When the settings page appears, click on the Password Change link.
Your password may have already been compromised
On June 6, 2012, it was reported that a hacker had acquired and published the passwords of LinkedIn members on the Internet. Later that day, LinkedIn responded with an update on a blog confirming that “some of the passwords that were compromised correspond to LinkedIn accounts.” This was an understatement. The hacker had uploaded 6.5 million LinkedIn passwords and 1.5 million eHarmony passwords to a Russian hacking site.
The security breach resulted in a $5 million class-action lawsuit that was started by two LinkedIn users. The case was dismissed before going to trial, with the Judge declaring that the plaintiffs hadn’t shown they’d suffered any actual harm from the security breach. The judge further pointed out that even though they had paid for premium accounts, this was to acquire additional services and not additional security.
If you are a member of LinkedIn and have concern that your password may have been compromised, you can check by using a tool at https://lastpass.com/linkedin to determine if it was on the known list of passwords that were posted online. eHarmony users can also check using a similar tool at https://lastpass.com/eharmony. As seen in Figure 3.5, by entering your password and clicking the button, it will show you whether your password was one of the one’s compromised.
Hacking 101
In the case of LinkedIn and eHarmony’s security breach, the data the hacker uploaded was actually a list of hashed passwords. When sites and applications store your password, they generally don’t save it as the text you enter (called clear text or plaintext). Instead, an algorithm is used to encrypt the password and store it as what’s called a hash. In the case of LinkedIn, they used an outdated SHA-1 algorithm that left them vulnerable to decryption. For example, if your password was “password”, it would be saved as the following (without quotes): “5baa61e4c9b93f3f0682250b6cf8331b7ee68fd8”. While this looks pretty secure to you and I, the problem is that there are password cracking programs that use files called rainbow tables. Without diving too far into cryptographic analysis, a rainbow table is basically a list of pre-computed hashes that are used to recover the text password from a hash. Using these, the hashed passwords can be converted to text relatively quickly, allowing you to use the password to hack someone’s account.
Still sounds difficult? Let’s make it easier. Let’s say you’ve acquired a password database from the aforementioned Russian hacking site. After all, the site is easy to find since the media publicized that the passwords were uploaded there. You could then use programs like Ophcrack (http://ophcrack.sourceforge.net) that use rainbow files to quickly convert the hashes to text passwords. If you didn’t want to download the software, you could also go online and use a hash calculator like that found at http://www.xorbin.com/tools/sha1-hash-calculator, which will convert text to a hash, and vice versa. Once you’ve converted the password to text, you’re now able to go to the site, type in the text password, and logon to that person’s account.
Securing other settings on LinkedIn
While there are a wide variety of settings in LinkedIn, there are some other settings that you may want to configure. For the ones we’ll discuss here, all of them can be accessed through the Accounts & Settings page, by doing the following:
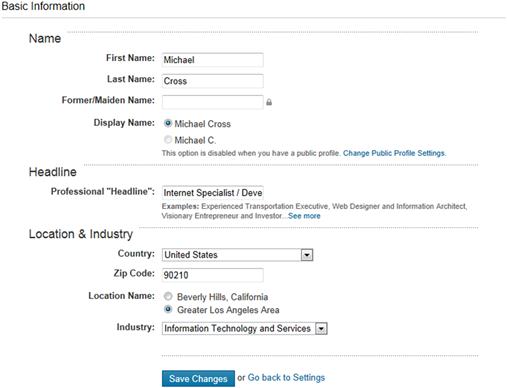
LinkedIn can show your name, location, and industry on profile pages. This may not be an issue for some people, but others may not want this information publicized on the Internet. As seen in Figure 3.6, the Basic Information page has a Display Name option, which allows you to select whether your full name is shown, or just your first name and last initial. The page also has a Location & Industry section, which LinkedIn uses to suggest jobs related to your field and location. If you don’t want people to see this information, you have a couple of options. First, you can set the Location Name option to show your city, or a larger general area. As you can see in Figure 3.6, based on my zip code of 90210 (and no, unfortunately that’s not real), I have the option of choosing “Beverly Hills, California” or “Greater Los Angeles Area.” Another option is to enter zeros in the zip code field, so that only your country is used.
To modify the settings for your name, location and industry, follow these steps:
1. Click the Profile tab in the bottom-left corner of the screen.
2. Click on Edit your name, location & industry.
3. When the screen appears, click the appropriate option to set whether your full name or just you first name and last initial appears as the name on your profile page.
4. In the Location & Industry section, click the appropriate option to set whether your Location Name will show your city or a greater geographic area.
If you travel or work from multiple computers, the information you send and receive may go over insecure or public networks. If you use LinkedIn on public computers (such as Internet café’s or business centers in hotels), or use shared Wi-Fi connections (such as in airports, restaurants, and so on), you should set LinkedIn to use secure browsing mode. When this feature is activated, your browser will use Hypertext Transfer Protocol Secure (HTTPS) when browsing LinkedIn, which provides encrypted communication and secure identification of a network’s Web servers. To modify your security settings, you should:
Employees using social media
As you can see from the previous sections, there are a lot of different security configurations that can be made for a LinkedIn account, and chances are many of your employees and coworkers haven’t used them. Many people accept default settings, meaning that anything typed into LinkedIn and other social networking sites may be available for the entire world to see. This can create a large number of security risks for individuals and your organization.
Security is a major issue for employees using social media, and a reason why many companies haven’t allowed it in the workplace. Network administrators and IT staff will go through great efforts to protect a network by configuring computers, devices and software, and implementing security measures to prevent the outside world from seeing corporate data. However, there’s nothing they can do about an employee’s failure to properly set security on a personal social media site. Even if the business uses social media, it generally isn’t an IT person who handles the Twitter, Facebook, and other accounts, so they have no control over how the accounts are configured and reconfigured. Instead of taking a proactive approach to network security, the business is suddenly forced to react to security breaches from social media.
The employee’s control over security settings on so many different social media sites creates a shift in how a company needs to address security. Rather than focusing only on the organization’s network security, the IT staff is placed in a role of having to become educators. They need to directly share recommendations on how to properly configure these accounts, or share that information with other people in the organization that train staff. Rather than manage the security of a network, computers, and other devices through configuration and software, there’s suddenly an increased need to manage it through policy.
However, the need for education goes beyond the configuration of accounts, as there’s a need for employees to know how to control information and conduct oneself online. Many organizations worry that employees could mention the company in an embarrassing way, or release internal information. It’s a valid concern, but employees aren’t the only ones working for you. Companies should also be concerned whether contractors, vendors, partners, and others related to the organization are leaking information and making embarrassing comments. After all, some vendors or contract workers may have more sensitive information than some of the people working for you, and can embarrass you just as easily.
A fine example of this is seen in an infamous mistake that was made on Twitter. James Andrews was then the Vice President of Ketchum, a public relations firm, and traveled to Memphis to do a presentation. After arriving, he tweeted the following: “True confession but i’m in one of those towns where I scratch my head and say ‘I would die if I had to live here!’.” Andrews’ presentation was to FedEx, a major client of the firm, whose headquarters is proudly located in Memphis. A FedEx employee followed Andrews on Twitter, and passed the tweet to others in the company. Ironically, Andrews was there to talk about social media, but it was FedEx who instructed him. While chastising him in their response, they informed him that a “hazard of social networking is people will read what you write.” FedEx ended their email paraphrasing the original post, by saying: “true confession: many of my peers and I don’t see much relevance between your presentation this morning and the work we do in Employee Communications.”
While the incident between Andrews and FedEx occurred in 2009, it attracted international attention and continues to be talked about years later. A company may have concerns about its own employees using social media properly, but there is no guarantee that others you do business with won’t create problems. A lapse in judgment can have far-reaching implications, involve more than just the business you’re working for, and linger for years. Although a mistake may be forgotten, mistakes in social media may never go away.
Allowing social media in the workplace
There are many good reasons why organizations haven’t allowed social media in the workplace. However, many of the arguments against social media in the workplace are the same ones that were used against allowing employees any kind of Internet access:
• It lowers productivity. After all, I don’t want my employees looking for other jobs, playing games or updating their status during company time.
• It could create a hostile work environment. If a colleague viewed or posted something offensive, it could result in harassment or workplace bullying complaints or lawsuits.
• Information could be leaked. A person could send confidential information to another person, or cause embarrassment with comments they make.
• It’s a security risk. There are all sorts of malicious programs and viruses that could infect our network.
Issues are issues regardless of the medium. Employee productivity can be lowered by goofing around on Twitter or any other Web site, just as it can by wasting time by chatting around the water cooler. If I sit at my desk for a half hour looking for another job on LinkedIn, is it any more of a waste of company time than reading want ads in a newspaper? Regardless of how it happens, employee productivity can be controlled through proper management. The same applies to many other issues. If someone is looking at porn on an adult Web site, a magazine, or by browsing Twitter accounts, the issue is that they’re violating corporate policy and conduct. Regardless of how it’s done, the fact is that they’re breaking the rules.
For other arguments dealing with technology, they are equally valid but need the same measure of unbiased consideration. There is a distinct risk that someone could leak information. However, this was just as valid a concern when email was new in the workplace, and most employees have proven they’re responsible. While problems do exist with workers sending sensitive data, making inappropriate comments, or inadvertently leaking classified information, the real problem is that it’s happening. It’s not the forum that’s an issue; it’s what’s being said.
Arguments related to the security of a network, computer, or other devices can be more complex. Computers on a network should be protected by antivirus software, and firewalls that prevent access to known security risks, such as sites known to disseminate malware and those used for social engineering (phishing). However, social media isn’t always accessed from a network computer. People will use social networks and other sites from home computers, smartphones, and other devices that aren’t constantly connected to a corporate network. Any devices owned by the company could be locked down using group policies or configurations that prevent installing software, but there’s no protection for an employee’s home computer. If possible, a company can offer an employee program that allows them to borrow and install a licensed copy of antivirus software or purchase software at a reduced price. They should at a minimum educate employees by raising awareness of common threats, make recommendations on installing the latest updates to software, suggest customized settings for social networking sites, and other information that will enhance security.
Because so many different kinds of content can be accessed with social media, the performance of a network can be bogged down by people watching videos or accessing other large files. Remember that social media is user-generated, so you’re not always dealing with content that’s been optimized for the Web, and made into a smaller size. A blog may have an incredibly large photo, or huge videos may be available to view. If a number of employees view such files, it can slow down the network. If the infrastructure of a network can’t handle so much bandwidth being used, there is always the option to block access to social networking sites during peak hours. For example, a network administrator could configure a gateway to block types of social media during work hours, but allow people to visit YouTube or others sites during lunch hours.
While many organizations have resisted social media, there is no escaping it. Employees are already using social media in their personal and professional lives, and will continue using it even if the organization they work for has no social media presence. Just because your company doesn’t allow access to social networking sites on a workstation, it doesn’t mean that you can’t tweet on your personal mobile phone or use Facebook when you get home. In other words, it’s already too late. Even if you don’t allow it in the workplace, social media is already accessible to employees.
Bibliography
1. Brenner, J. (2013, February 14). Pew Internet: Social networking (full detail). Retrieved March 10, 2012, from Pew Internet & American Life Project:<http://pewinternet.org/Commentary/2012/March/Pew-Internet-Social-Networking-full-detail.aspx>.
2. Bureau of Consumer Protection Business Center. (2012, January). Using consumer reports: What employers need to know. Retrieved March 17, 2013, from Bureau of Consumer Protection Business Center:<http://business.ftc.gov/documents/bus08-using-consumer-reports-what-employers-need-know>.
3. CareerBuilder. (2012, April 18). Thirty-seven percent of companies use social networks to research potential job candidates, according to new CareerBuilder Survey. Retrieved March 17, 2013, from CareerBuilder:<http://www.careerbuilder.ca/share/aboutus/pressreleasesdetail.aspx?id=pr691&sd=4%2F18%2F2012&ed=4%2F18%2F2099>.
4. Downey, S. (2012, May 4). Why DeleteMe is a subscription service and not a 1-time thing. Retrieved March 17, 2013, from Abine:<http://www.abine.com/blog/2012/why-deleteme-is-a-subscription-service-and-not-a-1-time-thing/>.
5. Edwards, J. (2009, January 20). Worst Twitter post ever: Ketchum exec insults fedex client on mini-blog. Retrieved April 1, 2013, from CBS Money Watch:<http://www.cbsnews.com/8301-505123_162-42740256/worst-twitter-post-ever-ketchum-exec-insults-fedex-client-on-mini-blog/>.
6. Federal Trade Commission. (n.d.). A summary of your rights under the Fair Credit Reporting Act. Retrieved March 17, 2013, from Federal Trade Commission Consumer Information:<http://www.consumer.ftc.gov/articles/pdf-0096-fair-credit-reporting-act.pdf>.
7. Jobvite. (2012, July 9). Jobvite social recruiting survey finds over 90% of employers will use social recruiting in 2012. Retrieved March 18, 2013, from Jobvite:<http://recruiting.jobvite.com/company/press-releases/2012/jobvite-social-recruiting-survey-2012/>.
8. Office of Governor Edmund G. Brown Jr. (2012, September 27). Governor Brown signs laws to protect privacy for social media users. Retrieved March 17, 2013, from Office of Governor Edmund G. Brown Jr.:<http://gov.ca.gov/news.php?id=17759>.
9. Silveira, V. (2012, June 6). An update on LinkedIn member passwords compromised. Retrieved March 12, 2013, from LinkedIn:<http://blog.linkedin.com/2012/06/06/linkedin-member-passwords-compromised/>.
10. Society for Human Resource Management. (2011, August 25). The use of social networking websites and online search engines in screening job candidates survey findings. Retrieved March 15, 2013, from Society for Human Resource Management:<http://www.shrm.org/Research/SurveyFindings/Articles/Pages/TheUseofSocialNetworkingWebsitesandOnlineSearchEnginesinScreeningJobCandidates.aspx>.
11. Taylor, L. C. (2012, April 5). Suspension over Facebook photo by U.S. teacher’s aide becomes a right-to-privacy lawsuit. Retrieved March 17, 2013, from thestar.com:<http://www.thestar.com/news/world/2012/04/05/suspension_over_facebook_photo_by_us_teachers_aide_becomes_a_righttoprivacy_lawsuit.html>.
12. Vallone, J. (2012, July 11). People search online big business, but FTC watching. Retrieved March 17, 2013, from<http://news.investors.com/technology/071112-617755-websites-gather-tons-on-people.htm?p=full>.