CHAPTER 11
HACKING WIRELESS NETWORKS
After reading this chapter and completing the activities, you will be able to:
![]() Explain wireless technology
Explain wireless technology
![]() Describe wireless networking standards
Describe wireless networking standards
![]() Describe the process of authentication
Describe the process of authentication
![]() Describe wardriving
Describe wardriving
![]() Describe wireless hacking and tools used by hackers and security professionals
Describe wireless hacking and tools used by hackers and security professionals
The term “wireless” is generally used to describe equipment and technologies operating in the radio frequency (RF) spectrum between 3 Hz and 300 GHz. Examples of wireless equipment include cell phones, AM/FM radios, wireless networking devices, and radar systems. Most wireless networking equipment operates in a smaller portion of the RF spectrum, between 2.4 GHz and 66 GHz. Wireless technology is here to stay, so securing a wireless network from attackers is a primary concern.
This chapter gives you an overview of wireless networking technology and standards, explains the process of authentication, describes wardriving, and covers some tools attackers use on wireless networks.
UNDERSTANDING WIRELESS TECHNOLOGY
For a wireless network to function, you must have the right hardware and software as well as a technology that allows electrons to travel through the air. At one time, when seeing the comic strip character Dick Tracy talk to his wristwatch, people wondered whether that would ever be possible. The idea that a phone could work without a wire connected to it astounded them, even though Alfred J. Gross had invented the walkie-talkie in 1938. In fact, the creator of Dick Tracy asked for Gross’s permission before using a wireless wristwatch in his comics. (To read more about Al Gross, visit www.retrocom.com.) In 1973, 35 years after the walkie-talkie, Martin Cooper invented the first cell phone, which weighed in at close to 2 pounds.
Wireless technology is part of your daily life. Here are some wireless devices many people use daily:
![]() Baby monitors
Baby monitors
![]() Keyless entry systems
Keyless entry systems
![]() Cordless and cell phones
Cordless and cell phones
![]() Pagers
Pagers
![]() Global positioning system (GPS) devices
Global positioning system (GPS) devices
![]() Remote controls
Remote controls
![]() Garage door openers
Garage door openers
![]() Two-way radios
Two-way radios
![]() Wireless PDAs
Wireless PDAs
Components of a Wireless Network
Any network needs certain components to work: communication devices to transmit and receive signals, protocols, and a medium for transmitting data. On a typical LAN, these components are network interface cards (NICs), TCP/IP, and an Ethernet cable (the wire serving as the connection medium). As complex as wireless networks might seem, they too have only a few basic components:
![]() Wireless network interface cards (WNICs), which transmit and receive wireless signals, and access points (APs), which are the bridge between wired and wireless networks
Wireless network interface cards (WNICs), which transmit and receive wireless signals, and access points (APs), which are the bridge between wired and wireless networks
![]() Wireless networking protocols, such as Wi-Fi Protected Access (WPA)
Wireless networking protocols, such as Wi-Fi Protected Access (WPA)
![]() A portion of the RF spectrum, which replaces wire as the connection medium
A portion of the RF spectrum, which replaces wire as the connection medium
The following sections explain how an AP and a WNIC function in a wireless network.
Access Points
An access point (AP) is a radio transceiver that connects to a network via an Ethernet cable and bridges a wireless LAN (WLAN) with a wired network. It’s possible to have a wireless network that doesn’t connect to a wired network, such as a peer-to-peer network, but this topology isn’t covered because security testers are seldom, if ever, contracted to secure a peer-to-peer wireless network. Most companies where you conduct security tests use a WLAN that connects to the company’s wired network topology.
An AP is where RF channels are configured. Figure 11.1 shows the channels detected by NetStumbler (an AP-scanning program covered in “Understanding Wardriving” later in this chapter). APs are what hackers look for when they drive around with an antenna and a laptop computer scanning for access. Channels are explained in more detail later in “The 802.11 Standard.” For now, think of a channel as a range or frequency that data travels over, much like a channel on the radio.
An AP enables users to connect to a LAN with wireless technology. It can be configured to transmit and receive only within a defined area or square footage, depending on the technology. If you’re 20 miles away from an AP, you’re probably out of range.
Service Set Identifiers
A service set identifier (SSID) is the name used to identify a WLAN, much the same way a workgroup is used on a Windows network. An SSID is configured on the AP as a unique, 1-to 32-character, case-sensitive alphanumeric name. For wireless-enabled computers to access the WLAN the AP connects to, they must be configured with the same SSID as the AP. The SSID name, or “code,” is attached to each packet to identify it as belonging to that wireless network. The AP usually beacons (broadcasts) the SSID several times a second so that users who have WNICs can see a display of all WLANs within range of the AP’s signal. In Figure 11.2, the Windows Vista wireless connection manager shows SSIDs advertised by APs within range of the wireless computer. Some WNICs come with built-in wireless connection software that looks different from the Windows utility.
Figure 11.1
AP channels detected

Courtesy Course Technology/Cengage Learning
Figure 11.2
SSIDs advertised to a wireless computer
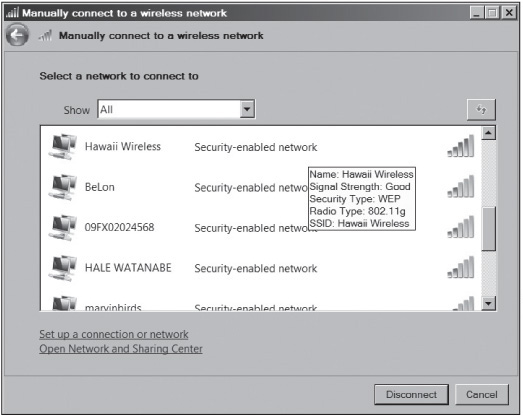
Courtesy Course Technology/Cengage Learning
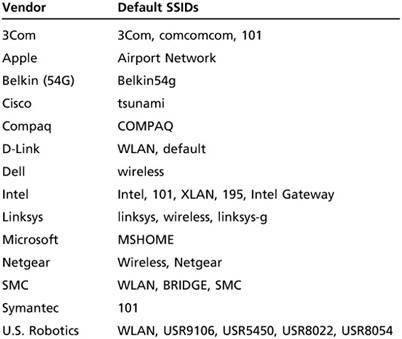
Many vendors have SSIDs set to a default value that companies never change. For example, Cisco APs use the default SSID “tsunami.” Table 11.1 shows some default SSIDs as of this writing, but this list changes often, sometimes daily. As a security professional, you must research constantly and gather information to keep abreast of changes in this industry. If an AP is configured to not provide its SSID until after authentication, wireless hackers can attempt to guess the SSID by using the information in Table 11.1. Make sure your client isn’t using a default SSID.
Activity 11.1: Finding Vulnerabilities in SSIDs
Time Required: 30 minutes
Objective: Learn how recognizing a default SSID can open the door to discovering vulnerabilities.
Description: As you learned in Chapter 6, recognizing which OS a customer or client is using is essential before you can detect vulnerabilities in a system or network. This is also true when you’re attempting to discover vulnerabilities in an AP. When conducting a security test on a WLAN, you start by looking for SSIDs advertised over the air to determine the type of AP the company is using.
1. If necessary, start your computer in Windows or boot into Linux with the BackTrack files, and start a Web browser. Go to http://nvd.nist.gov. Click the Vulnerability Search Engine link, type wireless in the search text box, and click the Search All button. Review some recent vulnerabilities with a Common Vulnerability Scoring System (CVSS) severity score of 10.0 (the highest).
2. Click the CVE link, and read the vulnerability summary information to learn more about each vulnerability. Is an exploit or attack demonstration available?
3. Choose a wireless router make and model with a CVSS score of 10.0.
4. Is the router’s default SSID listed in Table 11.1? Because router models (and URLs) change constantly, you might want to use your search skills to find the default SSID for the router make and model you selected, if it isn’t listed in Table 11.1.
5. What solution would you offer to a client using the router you selected in Step 3?
6. Leave your Web browser open for the next activity.
Configuring an Access Point
Configuring an AP varies, depending on the embedded OS supplied by the manufacturer. With most APs, users can access the software through a Web browser because the AP has an embedded OS supporting a Web server. The following example shows options for the dd-wrt Linux embedded OS that replaces the embedded OS used on hundreds of routers from Linksys, D-Link, Netgear, Belkin, Microsoft, U.S. Robotics, Dell, Buffalo, and many others. You see how an AP administrator can determine the SSID and channel and configure security (covered later in this chapter in “Understanding Authentication”). This example outlines the steps a security professional takes to access and reconfigure a wireless router running dd-wrt with the IP address 192.168.1.1:
1. After entering the IP address in a Web browser, the user is prompted for a logon name and password. If this is the user’s first time accessing the router, no password is needed. In dd-wrt, the default username is “root,” and the default password is “admin.” For security reasons, changing these credentials is essential.
2. After a successful logon, you click the Status item at the top to display the window shown in Figure 11.3. Notice the router model and CPU model listed under Router Information.
3. After clicking the Wireless tab at the top, you see the window shown in Figure 11.4. The user entered “koko” for the SSID. (Note: The default SSID for wireless routers running dd-wrt is “dd-wrt.”) The user could have changed the default name to “Cisco” to try to trick attackers into believing the router is a Cisco product; however, picking a name that’s not associated with a manufacturer or an OS might be more effective at discouraging attacks. Notice that Channel 6, the default channel for many wireless router OSs, has been selected. To improve security, you might want to disable SSID broadcasts because advertising who you are and whether you’re using encryption increases the chance of attack. In dd-wrt, disabling SSID broadcasts is easy: Just click the Disable option button.
Figure 11.3
Viewing status information in dd-wrt

Courtesy Course Technology/Cengage Learning
4. To configure security, you click the Wireless Security tab. In Figure 11.5, the user has entered a password (called a “WPA shared key” in dd-wrt) that must be supplied by the wireless computer. For example, the user of a Windows computer connecting to an AP with the SSID “koko” enters the WPA2 key in the Wireless Network properties dialog box shown in Figure 11.6.
Note
WNIC manufacturers usually supply connection management software that you can use instead of the built-in Windows utility.
If a company doesn’t change its default SSID but decides to disable SSID broadcasts, a determined intruder can use a passive wireless sniffer, such as Kismet (covered later in “Understanding Wardriving”). Unlike NetStumbler, which can pick up only broadcasted SSIDs, Kismet can detect SSIDs in WLAN client traffic. If the user didn’t assign a WLAN key or change the default administrator password to the AP, you can see how easily an attacker could access the WLAN. As a security tester, you must verify that these vulnerabilities don’t exist on a WLAN; if they do, you should recommend that the company close the holes as quickly as possible.
Figure 11.4
Basic wireless configuration in dd-wrt

Courtesy Course Technology/Cengage Learning
Figure 11.5
Configuring wireless security in dd-wrt
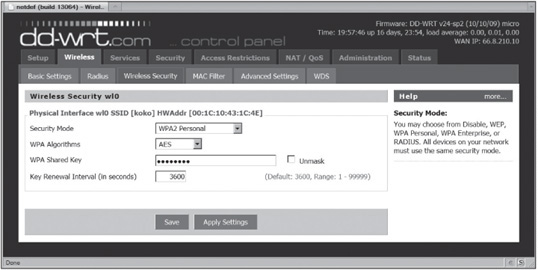
Courtesy Course Technology/Cengage Learning
Figure 11.6
Entering a WPA2 key

Courtesy Course Technology/Cengage Learning
Wireless NICs
For a computer to be able to send information over any medium, it must follow the rules for the medium it’s traversing, so the correct software and drivers for the NIC must be installed. For example, data traveling over a copper wire must follow rules for how Ethernet signals are sent over that medium. For wireless technology to work, each node or computer must have a WNIC, which converts the radio waves it receives into digital signals the computer understands.
There are many WNICs on the market, but be careful deciding which one to purchase if you’re considering using specific tools for detecting APs and decrypting WEP keys or using antennas that can cover a large distance. For instance, AirCrack NG, a program for cracking WEP encryption on a WLAN, requires using a specific chipset on a WNIC, so only certain brands of WNICs can be used.
UNDERSTANDING WIRELESS NETWORK STANDARDS
A standard is a set of rules formulated by an organization. All industries have standards, and a WLAN is no exception. Just as the Institute of Electrical and Electronics Engineers (IEEE) has standards specifying maximum cable length in an Ethernet network, there are rules to follow for wireless networks.
Working groups (WGs) of the IEEE are formed to develop new standards. After a WG has reached consensus on a proposal for a standard, the Sponsor Executive Committee must approve the proposal. Finally, after the proposal is recommended by the Standards Review Committee and approved by the IEEE Standards Board, you have a new standard.
IEEE Project 802 was developed to create LAN and WAN standards. (The first meeting was held in February 1980, so the project was given the number 802, with “80” representing the year and “2” representing the month.) WG names are also assigned numbers, such as 11 for the Wireless LAN group, and letters to denote approved projects, such as 802.11a or 802.11b. In this chapter, you learn about the 802 standards pertaining to wireless networks.
The 802.11 Standard
The first wireless technology standard, 802.11, defined specifications for wireless connectivity as 1 Mbps and 2 Mbps in a LAN. This standard applied to the Physical layer of the OSI model, which deals with wireless connectivity issues of fixed, portable, and moving stations in a local area, and the Media Access Control (MAC) sublayer of the Data Link layer. Because current 802.11 wireless networks are half-duplex (meaning only one side of the connection transmits at a time), and there’s only one pair of transmitters, collisions don’t occur. However, multiple transmitters are often nearby, so radio signals can mix and have the potential to interfere with each other (as signal collision). For this reason, carrier sense multiple access/collision avoidance (CSMA/CA) is used instead of the CSMA/CD method (collision detection, used in Ethernet).
Many definitions of terms are included in the more than 500 pages of the 802.11 standard. One important distinction is that wireless LANs don’t have an address associated with a physical location, as wired LANs do. In 802.11, an addressable unit is called a station (STA). A station is defined as a message destination and might not be a fixed location. Another distinction is made between mobile stations and portable stations. A mobile station is one that accesses the LAN while moving; a portable station is one that can move from location to location but is used only while in a fixed location.
The Basic Architecture of 802.11
802.11 uses a basic service set (BSS) as its building block. A BSS is the collection of devices (AP and stations or just stations) that make up a WLAN. A basic service area (BSA) is the coverage area an AP provides. A WLAN running in what’s called infrastructure mode always has one or more APs. An independent WLAN without an AP is called an ad-hoc network; independent stations connect in a decentralized fashion. As long as a station is within its BSA, it can communicate with other stations in the BSS. You have probably experienced losing cell phone connectivity when you’re out of range of your service area. Similarly, you can lose network connectivity if you aren’t in the WLAN’s coverage area. To connect two BSSs, 802.11 requires a distribution system (DS) as an intermediate layer. Basically, BSS 1 connects to the DS, which in turn connects to BSS 2. However, how does a station called STA 1 in BSS 1 connect to STA 2 in BSS 2? 802.11 defines an AP as a station providing access to the DS. Data moves between a BSS and the DS through the AP. This process sounds complicated, but Figure 11.7 should clear up any confusion.
IEEE 802.11 also defines the operating frequency range of 802.11. In the United States, the range is 2.4 to 2.4835 GHz. Think of the frequency as a superhighway in the sky where data travels, and this superhighway encompasses many highways (frequency bands). Each frequency band contains channels, which break up the band into smaller frequency ranges. For example, channel 1 of a frequency band ranging from 2.4 GHz to 2.4835 GHz might use the 2.401 GHz frequency, and channel 2 of this frequency band might use 2.402 GHz. The 802.11 standard defines 79 channels in the 2.4 to 2.4835 GHz range. If channels overlap, interference could occur.
Figure 11.7
Connecting two wireless remote stations

Courtesy Course Technology/Cengage Learning
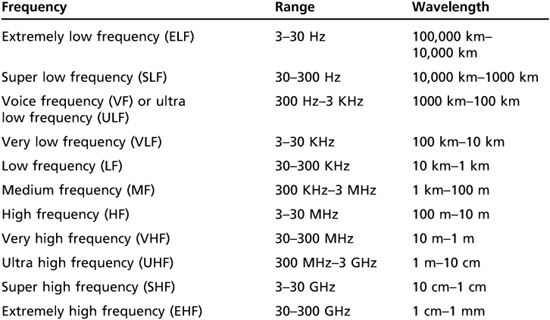
Sound travels through the air just as waves move in the ocean, and like ocean waves, a sound wave’s length is measured from the peak of one wave to the next. A sound wave’s amplitude (height) and frequency (rate at which a sound wave repeats) determine its volume and pitch. Surfers know they must wait for the next set of waves to occur and get quite accurate in determining frequency (the time it takes a set of waves to repeat). The completion of a repeating pattern of sound waves is called a cycle. For surfers, a cycle can be minutes. Sound waves, however, repeat at a much faster frequency. For example, a tuning fork vibrates at 440 hertz (Hz), or cycles per second. That’s 440 waves per second—too fast for a surfer. Different technologies use different frequencies, referred to as bands, to transmit sound. Table 11.2 lists frequency bands. For example, AM radio stations use the medium frequency (MF) band; FM radio stations and search-and-rescue stations use the very high frequency (VHF) band. The distance sound waves need to travel also determines which frequency band to use.
When you purchase a wireless router, keep in mind that many cordless phones operate at the same frequency as wireless routers, which can cause interference if the phone is close to the wireless router or AP.
An Overview of Wireless Technologies
Now that you understand the different frequencies on which radio waves can travel, take a look at the three technologies WLANs use:
![]() Infrared—Infrared light can’t be seen by the human eye. Infrared (IR) technology is restricted to a single room or line of sight because IR light can’t penetrate walls, ceilings, or floors. This technology is used for most remote controls and for syncing PDAs.
Infrared—Infrared light can’t be seen by the human eye. Infrared (IR) technology is restricted to a single room or line of sight because IR light can’t penetrate walls, ceilings, or floors. This technology is used for most remote controls and for syncing PDAs.
![]() Narrowband—Narrowband technology uses microwave radio band frequencies to transmit data. The most common uses of this technology are cordless phones and garage door openers.
Narrowband—Narrowband technology uses microwave radio band frequencies to transmit data. The most common uses of this technology are cordless phones and garage door openers.
![]() Spread spectrum—For data to be moved over radio waves, it must be modulated on the carrier signal or channel. Modulation defines how data is placed on a carrier signal. For example, spread spectrum modulation means data is spread across a large-frequency bandwidth instead of traveling across just one frequency band. In other words, a group of radio frequencies is selected, and the data is “spread” across this group. Spread spectrum, the most widely used WLAN technology, uses the following methods:
Spread spectrum—For data to be moved over radio waves, it must be modulated on the carrier signal or channel. Modulation defines how data is placed on a carrier signal. For example, spread spectrum modulation means data is spread across a large-frequency bandwidth instead of traveling across just one frequency band. In other words, a group of radio frequencies is selected, and the data is “spread” across this group. Spread spectrum, the most widely used WLAN technology, uses the following methods:
![]() Frequency-hopping spread spectrum (FHSS) : Data hops to other frequencies to avoid interference that might occur over a frequency band. This hopping from one frequency to another occurs at split-second intervals and makes it difficult for an intruder or attacker to jam the communication channel.
Frequency-hopping spread spectrum (FHSS) : Data hops to other frequencies to avoid interference that might occur over a frequency band. This hopping from one frequency to another occurs at split-second intervals and makes it difficult for an intruder or attacker to jam the communication channel.
![]() Direct sequence spread spectrum (DSSS): DSSS differs from FHSS, in that it spreads data packets simultaneously over multiple frequencies instead of hopping to other frequencies. Sub-bits are added to a packet as it travels across the frequency band and are used for recovery, in much the same way RAID-5 uses parity bits to rebuild a hard disk that crashes. Sub-bits are called “chips,” and every bit of the original message is represented by multiple bits, called the chipping code.
Direct sequence spread spectrum (DSSS): DSSS differs from FHSS, in that it spreads data packets simultaneously over multiple frequencies instead of hopping to other frequencies. Sub-bits are added to a packet as it travels across the frequency band and are used for recovery, in much the same way RAID-5 uses parity bits to rebuild a hard disk that crashes. Sub-bits are called “chips,” and every bit of the original message is represented by multiple bits, called the chipping code.
![]() Orthogonal frequency division multiplexing (OFDM) : The bandwidth is divided into a series of frequencies called tones, which allows a higher throughput (data transfer rate) than FHSS and DSSS do.
Orthogonal frequency division multiplexing (OFDM) : The bandwidth is divided into a series of frequencies called tones, which allows a higher throughput (data transfer rate) than FHSS and DSSS do.
Additional IEEE 802.11 Projects
The IEEE WG developed some additional 802.11 projects, releasing the 802.11a and 802.11b standards in October 1999. 802.11b quickly became the more widely used standard, probably because its hardware was less expensive. Also referred to as Wi-Fi, 802.11b operates in the 2.4 GHz band and increased the throughput to 11 Mbps from the 1 or 2 Mbps of the original 802.11. It allows a total of 11 separate channels to prevent overlapping signals. However, because of each channel’s bandwidth requirements, effectively only three channels (1, 6, and 11) can be combined without overlapping and creating interference. This standard also introduced Wired Equivalent Privacy (WEP), which gave many users a false sense of security that data traversing the WLAN was protected. WEP is covered later in “Understanding Authentication.”
802.11a has a different operating frequency range than 802.11 and 802.11b do; it operates in three distinct bands in the 5 GHz range. In addition, throughput was increased to 54 Mbps, much faster than 802.11b.
The 802.11g standard, released in 2003, operates in the 2.4 GHz band, too. However, because it uses a different modulation, it uses the OFDM method, which increases throughput to 54 Mbps.
The 802.11i standard introduced Wi-Fi Protected Access (WPA) in 2004, which is covered in “Understanding Authentication.” For now, just know that 802.11i corrected many security vulnerabilities in 802.11b. For security professionals, the 802.11i standard is probably the most important.
The 802.11e standard, released in 2005, had improvements to address the problem of interference. When interference is detected, the signal can jump to another frequency more quickly, improving the quality of service over 802.11b.
The 802.11n standard, finalized in 2009, operates in the same frequency (2.4 GHz band) and uses the same encoding as 802.11g. However, by using multiple antennas and wider bandwidth channels, throughput has been increased to 600 Mbps in this standard.
HiperLAN/2 is a European WLAN standard that’s not compatible with 802.11 standards, so compatibility with devices you already own is an important factor in deciding whether to purchase a HiperLAN/2 device.
Additional IEEE 802 Standards
The 802.15 standard addresses networking devices in one person’s workspace, which is called a wireless personal area network (WPAN). The maximum distance between devices is usually 10 meters. With the Bluetooth telecommunication specification, a fundamental part of the WPAN standard, you can connect portable devices, such as PDAs, cell phones, and computers, without wires. Bluetooth version 2.0 uses the 2.4 GHz band and can transmit data at speeds up to 12 Mbps. It’s not compatible with the 802.11 standards. The most recent Bluetooth version, 3.0, was released in 2009 and has moved to the 802.11 band to support speeds up to 24 Mbps. Bluetooth is more secure than a WLAN but is still vulnerable to attack. In 2005, the IEEE began work on using different technologies for the WPAN standard. ZigBee, a current example, is used for automation systems, such as smart lighting systems, temperature controls, and appliances.
The 802.16 standard covers wireless metropolitan area networks (MANs). This standard defines the Wireless MAN Air Interface for wireless MANs and addresses the limited distance available for 802.11b WLANs. The most widely used implementation of wireless MAN technology is called Worldwide Interoperability for Microwave Access (WiMAX). WiMAX is marketed as a viable alternative to so-called last-mile Internet access, which is normally provided by cable and DSL. There are mobile (802.16e) and fixed (802.16d) versions of WiMAX. A typical real-world speed of WiMAX is about 10 Mbps, quite a bit less than the theoretical 120 Mbps maximum of the 802.16 standard. Another MAN standard, 802.20, with a goal similar to mobile WiMAX is called Mobile Broadband Wireless Access (MBWA). It addresses wireless MANs for mobile users sitting in trains, subways, or cars traveling at speeds up to 150 miles per hour. The most common implementation of MBWA, iBurst, is used widely in Asia and Africa.
Table 11.3 summarizes the wireless standards in common use today but doesn’t include some wireless standards beyond the scope of this book, such as the licensed 802.11y 3.6 GHz bands, the 4.9 GHz band for U.S. public safety networks, and mobile phone wireless technologies—Evolution Data Optimized (EVDO) and Enhanced Data GSM Environment (EDGE), for example.
Activity 11.2: Visiting the IEEE 802.11 Web Site
Time Required: 30 minutes
Objective: Learn more about IEEE wireless standards.
Description: You can find a wealth of information at the IEEE Web site, and the standards are available for download. In this activity, you visit the IEEE Web site and research some standards covered in this section.
1. Start a Web browser, if necessary, and go to http://grouper.ieee.org/groups/802/, the IEEE 802 LAN/MAN Standards Committee page.
2. In the IEEE 802 GENERAL INFORMATION section, click IEEE 802 Orientation for new participants.
3. Review the PowerPoint presentation to see how the IEEE is organized and how standards are formulated.
4. Exit your Web browser.
Table 11.3 Summary of wireless standards

UNDERSTANDING AUTHENTICATION
The problem of unauthorized users accessing resources on a network is a major concern for security professionals. An organization that introduces wireless technology to the mix increases the potential for security problems. For example, if an employee installs an AP that’s not configured correctly, unauthorized users could log on to this AP after discovering the employee’s logon name and password. The 802.1X standard, discussed in the following section, addresses the issue of authentication.
The 802.1X Standard
Because there must be a method to ensure that others with wireless NICs can’t access resources on your wireless network, the 802.1X standard defines the process of authenticating and authorizing users on a network. This standard is especially useful for WLAN security when physical access control is more difficult to enforce than on wired LANs. To understand how authentication takes place on a wireless network, you review some basic concepts in the following sections.
Point-to-Point Protocol
Many ISPs use Point-to-Point Protocol (PPP) to connect dial-up or DSL users. PPP handles authentication by requiring a user to enter a valid username and password. PPP verifies that users attempting to use the link are indeed who they say they are.
Extensible Authentication Protocol
Extensible Authentication Protocol (EAP), an enhancement to PPP, was designed to allow a company to select its authentication method. For example, a company can use certificates or Kerberos authentication to authenticate a user connecting to an AP. A certificate is a record that authenticates network entities, such as a server or client. It contains X.509 information that identifies the owner, the certification authority (CA), and the owner’s public key. (For more information on certificates and keys, see Chapter 12.) You can examine an X.509 certificate by going to www.paypal.com. This Web site redirects you to the secure (HTTPS) URL, where you click the padlock icon at the right of the address bar in Internet Explorer 8, and then click View Certificates to see the certificate information shown in Figure 11.8.
The following EAP methods can be used to improve security on a wireless network:
![]() Extensible Authentication Protocol-Transport Layer Security (EAP-TLS)—This method requires assigning the client and server a digital certificate signed by a CA that both parties trust. This CA can be a commercial company that charges a fee, or a network administrator can configure a server to issue certificates. In this way, both the server and client authenticate mutually. In addition to servers requiring that clients prove they are who they say, clients also want servers to verify their identity.
Extensible Authentication Protocol-Transport Layer Security (EAP-TLS)—This method requires assigning the client and server a digital certificate signed by a CA that both parties trust. This CA can be a commercial company that charges a fee, or a network administrator can configure a server to issue certificates. In this way, both the server and client authenticate mutually. In addition to servers requiring that clients prove they are who they say, clients also want servers to verify their identity.
![]() Protected EAP—Protected EAP (PEAP) uses TLS to authenticate the server to the client but not the client to the server. With PEAP, only the server is required to have a digital certificate. (See RFC-2246 for more information on TLS.)
Protected EAP—Protected EAP (PEAP) uses TLS to authenticate the server to the client but not the client to the server. With PEAP, only the server is required to have a digital certificate. (See RFC-2246 for more information on TLS.)
![]() Microsoft PEAP—In Microsoft’s implementation of PEAP, a secure channel is created by using TLS as protection against eavesdropping.
Microsoft PEAP—In Microsoft’s implementation of PEAP, a secure channel is created by using TLS as protection against eavesdropping.
802.1X uses the following components to function:
![]() Supplicant—A supplicant is a wireless user attempting access to a WLAN.
Supplicant—A supplicant is a wireless user attempting access to a WLAN.
Figure 11.8
Viewing information about an X.509 certificate
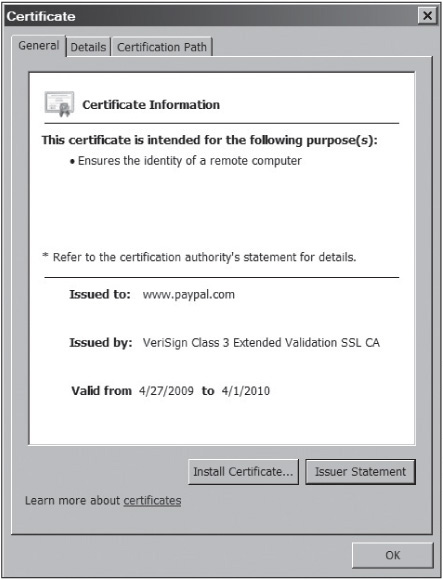
Courtesy Course Technology/Cengage Learning
![]() Authenticator—The AP functions as the entity allowing or denying the supplicant’s access.
Authenticator—The AP functions as the entity allowing or denying the supplicant’s access.
![]() Authentication server—This server, which might be a Remote Access Dial-In User Service (RADIUS) server, is used as a centralized component that authenticates the user and performs accounting functions. For example, an ISP using RADIUS can verify who logged on to the ISP service and how long the user was connected. Most RADIUS servers are *nix based, but the Microsoft implementation of RADIUS is called Internet Authentication Service (IAS).
Authentication server—This server, which might be a Remote Access Dial-In User Service (RADIUS) server, is used as a centralized component that authenticates the user and performs accounting functions. For example, an ISP using RADIUS can verify who logged on to the ISP service and how long the user was connected. Most RADIUS servers are *nix based, but the Microsoft implementation of RADIUS is called Internet Authentication Service (IAS).
Figure 11.9 shows the process of 802.1X, described in the following steps:
1. An unauthenticated client (supplicant) attempts to connect with the AP functioning as the authenticator.
Figure 11.9
A supplicant connecting to an AP and a RADIUS server

Courtesy Course Technology/Cengage Learning
2. The AP responds by enabling a port that passes only EAP packets from the supplicant to the RADIUS server on the wired network.
3. The AP blocks all other traffic until the RADIUS server authenticates the supplicant.
4. After the RADIUS server has authenticated the supplicant, it gives the supplicant access to network resources via the AP.
Until EAP and 802.1x were used on wireless LANs, a device, not a user, was authenticated on the WLAN. Therefore, if a computer was stolen from a company, the thief was able to connect to resources on the WLAN because the computer could still be authenticated. The following sections describe security features introduced in 802.11b and 802.11i.
Wired Equivalent Privacy
Wired Equivalent Privacy (WEP), part of the 802.11b standard, was developed to encrypt data traversing a wireless network. For some time, it gave many security professionals a false sense of security that wireless technology could be just as safe as wired networks. Unfortunately, WEP has been torn to shreds by security professionals, professors from major universities, and hackers who post ways to crack WEP encryption. Some argue that WEP is still better than no security at all, and when it’s combined with the security of a virtual private network (VPN), they claim that WEP works well for home users or small businesses. Still, many saw a need for a better way to protect WLANs.
Wi-Fi Protected Access
Wi-Fi Protected Access (WPA), specified in the 802.11i standard, is the replacement for WEP, which is known to have cryptographic weaknesses. WPA improves encryption by using Temporal Key Integrity Protocol (TKIP). TKIP has four enhancements that address encryption vulnerabilities in WEP:
![]() Message Integrity Check (MIC)—MIC, also called Michael, is a cryptographic message integrity code. Its main purpose is to prevent forgeries, which are packets that attackers create to look like legitimate packets. For example, an MIC uses a secret authentication key, which only the sender and receiver know, and creates a tag (message integrity code) generated from the key and message that’s sent to the receiver. The sender sends the message and tag to the receiver, who must enter the key, tag, and message in a program that verifies whether the tag created with the three input fields is equal to the tag the program should have created. You don’t need to memorize how this process takes place, but understanding that MIC corrects a known vulnerability in WEP is important.
Message Integrity Check (MIC)—MIC, also called Michael, is a cryptographic message integrity code. Its main purpose is to prevent forgeries, which are packets that attackers create to look like legitimate packets. For example, an MIC uses a secret authentication key, which only the sender and receiver know, and creates a tag (message integrity code) generated from the key and message that’s sent to the receiver. The sender sends the message and tag to the receiver, who must enter the key, tag, and message in a program that verifies whether the tag created with the three input fields is equal to the tag the program should have created. You don’t need to memorize how this process takes place, but understanding that MIC corrects a known vulnerability in WEP is important.
![]() Extended Initialization Vector (IV) with sequencing rules—This enhancement was developed to prevent replays. In a replay, an attacker records or captures a packet, saves it, and retransmits the message later. To prevent a replay from occurring, a sequence number is applied to the WEP IV field. If a packet is received with an IV equal to or less than the sequence number received earlier, the packet is discarded.
Extended Initialization Vector (IV) with sequencing rules—This enhancement was developed to prevent replays. In a replay, an attacker records or captures a packet, saves it, and retransmits the message later. To prevent a replay from occurring, a sequence number is applied to the WEP IV field. If a packet is received with an IV equal to or less than the sequence number received earlier, the packet is discarded.
![]() Per-packet key mixing—This enhancement helps defeat weak key attacks that occurred in WEP. MAC addresses are used to create an intermediate key, which prevents the same key from being used by all links.
Per-packet key mixing—This enhancement helps defeat weak key attacks that occurred in WEP. MAC addresses are used to create an intermediate key, which prevents the same key from being used by all links.
![]() Rekeying mechanism—This enhancement provides fresh keys that help prevent attacks that relied on reusing old keys. That is, if the same key is used repeatedly, someone running a program to decipher the key could likely do so after collecting a large number of packets. The same key being used repeatedly was a big problem in WEP.
Rekeying mechanism—This enhancement provides fresh keys that help prevent attacks that relied on reusing old keys. That is, if the same key is used repeatedly, someone running a program to decipher the key could likely do so after collecting a large number of packets. The same key being used repeatedly was a big problem in WEP.
WPA also added an authentication mechanism using 802.1X and EAP, which weren’t available in WEP. Because weaknesses that can be exploited have been found in TKIP, the more advanced WPA2 has replaced WPA in the official Wi-Fi standard. Stronger AES encryption (discussed in Chapter 12) is used instead of TKIP.
UNDERSTANDING WARDRIVING
It’s probably no secret that hackers use wardriving—driving around with inexpensive hardware and software that enables them to detect access points that haven’t been secured. Surprisingly, most APs have no passwords or security measures, so wardriving can be quite rewarding for hackers. As of this writing, wardriving isn’t illegal; using the resources of networks discovered with wardriving is, of course, a different story. Wardriving has now been expanded to include warflying, which is done by using an airplane wired with an antenna and the same software used in wardriving. In one test conducted by warflyers, more than 3000 APs were discovered, and two-thirds of them used no encryption. The testers used Kismet, covered later in this section, which identifies APs that attempt to “cloak” or hide their SSIDs.
How It Works
To conduct wardriving, an attacker or a security tester simply drives around with a laptop computer containing a WNIC, an antenna, and software that scans the area for SSIDs. Not all WNICs are compatible with scanning software, so you might want to look at the software requirements first before purchasing the hardware. Antenna prices vary, depending on their quality and the range they can cover. Some are as small as a cell phone’s antenna, and some are as large as a bazooka, which you might have seen in old war films. The larger ones can sometimes return results on networks miles away from the attacker. The smaller ones might require being in close proximity to the AP.
Most scanning software detects the company’s SSID, the type of security enabled, and the signal strength, indicating how close the AP is to the attacker. Because attacks against WEP are simple and attacks against WPA are possible, any 802.11 connection not using WPA2 should be considered inadequately secured. The following sections introduce some tools that many wireless hackers and security professionals use.
Security Bytes
An ethical hacker in Houston, previously employed by the county’s Technology Department, was accused of breaking into a Texas court’s wireless network. While he was conducting scans as part of his job, he noticed a vulnerability in the court’s wireless network and was concerned. He demonstrated to a county official and a local reporter how easily he could gain access to the wireless network with just a laptop computer and a WNIC. He was later charged with two counts of unauthorized access of a protected computer system and unauthorized access of a computer system used in justice administration. After a 3-day trial and 15 minutes of jury deliberation, he was acquitted. If he had been found guilty of all charges, he would have faced 10 years in prison and a $500,000 fine.
NetStumbler
NetStumbler (www.netstumbler.com) is a freeware tool written for Windows that enables you to detect WLANs using 802.11a, 802.11b, and 802.11g. It’s easy to install, but not all wireless hardware works with the software, so you must follow the directions carefully and verify that the hardware you have is compatible. NetStumbler was designed to assist security testers in the following:
![]() Verifying the WLAN configuration
Verifying the WLAN configuration
![]() Detecting other wireless networks that might be interfering with a WLAN
Detecting other wireless networks that might be interfering with a WLAN
![]() Detecting unauthorized APs that might have been placed on a WLAN
Detecting unauthorized APs that might have been placed on a WLAN
Caution
NetStumbler is also used in wardriving, but remember that in most parts of the world, using someone’s network without permission is illegal. This law includes using someone’s Internet connection without his or her knowledge or permission.
Another feature of NetStumbler is its capability to interface with a GPS, enabling a security tester or hacker to map out locations of all WLANs the software detects (see Figure 11.10).
When the program identifies an AP’s signal, it logs the SSID, MAC address of the AP, manufacturer of the AP, channel on which the signal was heard, strength of the signal, and whether encryption is enabled (but not a specific encryption type). Attackers can detect any APs within a 350-foot radius, but with a good antenna, they can locate APs a couple of miles away. For those with mechanical ability, numerous Web sites have instructions on building your own antenna with empty bean cans, potato chip cans, and the like. You can also purchase a decent antenna for about $50.
Figure 11.10
Configuring GPS settings in the Network Stumbler Options dialog box

Courtesy Course Technology/Cengage Learning
For directions on building an antenna from a potato chip can, visit www.oreillynet.com/cs/weblog/view/wlg/448.
Activity 11.3: Discovering APs with iwScanner
Time Required: 15 minutes
Objective: See what information a wireless scanner, such as iwScanner, can gather.
Description: When testing a network for vulnerabilities, don’t neglect checking for vulnerabilities in any WLANs the company has set up. iwScanner is a free Wi-Fi scanner, similar to NetStumbler, included as part of this book’s supporting files. You can verify available APs and their SSIDs. In this activity, you run iwScanner from the supporting files. If you don’t have wireless NICs or an AP, you can do the activity later where equipment is available.
1. If necessary, boot into Linux with the BackTrack files, and start the KDE desktop manager by typing startx and pressing Enter. Open a Konsole shell, and type wicd and press Enter to activate your WNIC.
2. Click the KDE start button, point to System, and click iwScanner. iwScanner begins detecting SSID broadcasts and shows the quality and frequency of AP radio signals. If you’re in an area with a lot of APs, your iwScanner window might look like Figure 11.11.
Figure 11.11
Scanning APs with iwScanner

Courtesy Course Technology/Cengage Learning
Figure 11.12
Saving iwScanner data as a NetStumbler file
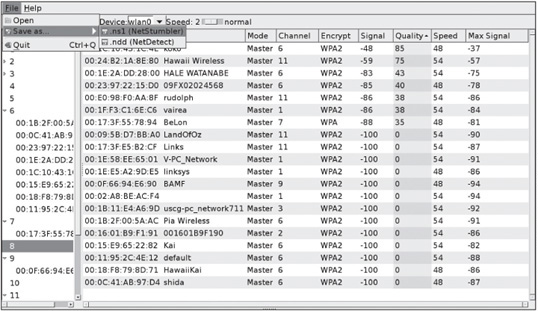
Courtesy Course Technology/Cengage Learning
3. If you’re running BackTrack from a USB flash drive or have an external USB drive, you can save your data in a NetStumbler-format file by clicking File from the menu, pointing to Save as, and clicking .ns1 (NetStumbler), as shown in Figure 11.12.
4. If you can view any SSIDs, click the right arrow next to the number 6 in the Channels column (see Figure 11.12). It’s the default channel for many APs. As you can see, many systems in this figure use channel 6, which could indicate congestion. If you discovered this information during a security test, you might suggest configuring some APs on different channels to your client.
5. Next, notice the MAC address of the AP with the SSID “Hawaii Wireless.” Start Firefox, and go to www.coffer.com/mac_find. In the MAC Address or Vendor to look for text box, type the first six characters of the MAC address (0024B2, in this example), and then click the string button. Which vendor is the Hawaii Wireless MAC address associated with? Why might this information be valuable to an attacker?
6. Click File, Exit from the iwScanner menu, and click No when prompted to save changes. Close any open windows.
Kismet
Another common product for conducting wardriving attacks is Kismet (www.kismetwireless.net), written by Mike Kershaw. This product is free and runs on Linux, BSD UNIX, Mac OS X, and even Linux PDAs. The software is advertised as being more than just a wireless network detector. Kismet is also a sniffer and an intrusion detection system (IDS, covered in Chapter 13) and can sniff 802.11b, 802.11a, 802.11g, and 802.11n traffic. It offers the following features:
![]() Wireshark- and Tcpdump-compatible data logging
Wireshark- and Tcpdump-compatible data logging
![]() Compatible with AirSnort and AirCrack (covered later in “Tools of the Trade”)
Compatible with AirSnort and AirCrack (covered later in “Tools of the Trade”)
![]() Network IP range detection
Network IP range detection
![]() Detection of hidden network SSIDs
Detection of hidden network SSIDs
![]() Graphical mapping of networks
Graphical mapping of networks
![]() Client/server architecture that allows multiple clients to view a single Kismet server at the same time
Client/server architecture that allows multiple clients to view a single Kismet server at the same time
![]() Manufacturer and model identification of APs and clients
Manufacturer and model identification of APs and clients
![]() Detection of known default AP configurations
Detection of known default AP configurations
![]() XML output
XML output
![]() Support for more than 25 card types (almost any card that supports monitor mode)
Support for more than 25 card types (almost any card that supports monitor mode)
Unlike NetStumbler and iwScanner, which rely on an AP to send out a beacon, Kismet is a passive scanner, so it can detect even hidden network SSIDs. Kismet can be used to conduct wardriving, but it can also be used to detect rogue APs on a company’s network. If you need GPS support, the BackTrack supporting files include several tools that work with Kismet, such as the GPS daemon (GPSD), GISKismet, and Kisgearth, that can come in handy for accurate AP geopositioning. When Kismet is configured to use GPSD, the output displays coordinates pinpointing the location of the AP being scanned. This coordinate data can then be fed into Google Earth to create maps.
UNDERSTANDING WIRELESS HACKING
Hacking a wireless network isn’t much different from hacking a wired LAN. Many of the port-scanning and enumeration tools you’ve learned about can be applied to wireless networks. The following sections describe some additional tools that attackers use, and you can use them to conduct security tests, too.
Tools of the Trade
A wireless hacker usually has a laptop computer, a WNIC, an antenna, sniffers (Tcpdump or Wireshark, for example), tools such as NetStumbler or Kismet, and lots of patience. After using NetStumbler or Kismet to determine the network name, SSID, MAC address of the AP, channel used, signal strength, and which type of encryption is enabled, a security tester is ready to continue testing.
Wireless routers that perform DHCP functions can pose a big security risk. If a wireless computer is issued an IP address, a subnet mask, and DNS information automatically, attackers can use all the skills they learned in hacking wired networks on the wireless network. If DHCP isn’t used, attackers simply rely on Wireshark or Tcpdump to sniff packets passing through the wireless network to gather this IP configuration information. (As a security professional, you should recommend disabling DHCP on wireless networks and assigning IP addresses to wireless stations manually.) They can then configure the WNIC with the correct IP information. What do attackers or security testers do if WEP or WPA is enabled on the AP? Several tools address this issue. AirCrack NG and WEPCrack, covered in the following sections, are what prompted organizations to replace WEP with the more secure WPA as their authentication method. However, many companies still use 802.11b with WEP enabled, and many more use 802.11b with WEP disabled.
AirCrack NG
As a security professional, your job is to protect a network and make it difficult for attackers to break in. You might like to believe you can completely prevent attackers from breaking in, but unfortunately, this goal is impossible. AirCrack NG (included on the BackTrack files or available free at www.aircrack-ng.org) is the tool most hackers use to access WEP-enabled WLANs. AirCrack NG replaced AirSnort, a product created by wireless security researchers Jeremy Bruestle and Blake Hegerle, who set out to prove that WEP encryption was faulty and easy to crack. AirSnort was the first widely used WEP-cracking program and woke up nonbelievers who thought WEP was enough protection for a WLAN. AirCrack NG took up where AirSnort (and the slightly older WEPCrack) left off. It has some useful add-ons, such as a GUI front-end called Gerix WiFi Cracker (also included as part of the BackTrack files for this book).
Note
The BackTrack files include a wide range of analysis tools for testing wireless networks.
Countermeasures for Wireless Attacks
Protecting a wireless network is a challenge for security professionals because of the inherent design flaws of wireless technology and because, to some extent, engineers are attempting to place a band-aid over a gaping chest wound. Some countermeasure techniques discussed in this section, such as using certificates on all wireless devices, are time consuming and costly. If you approach securing a wireless LAN as you would a wired LAN, you’ll have a better chance of protecting corporate data and network resources. Would you allow users to have access to network resources simply because they plugged their NICs into the company’s switch or hub? Of course not. Then why would you allow users to have access to a wireless LAN simply because they have WNICs and know the company’s SSID?
If a company must use wireless technology, your job is to make it as secure as possible. Be sure wireless users are authenticated before being able to access any network resources. Here are some additional guidelines to help secure a wireless network:
![]() Consider using anti-wardriving software to make it more difficult for attackers to discover your WLAN. In Chapter 13, you learn about honeypots, which are hosts or networks available to the public that entice hackers to attack them instead of a company’s real network. IT personnel can study how an attack is made on the honeypot, which can be useful in securing the company’s actual network. To make it more difficult for wardrivers to discover your WLAN, you can use Black Alchemy Fake AP (available free at www.blackalchemy.to/project/fakeap/). As its name implies, this program creates fake APs, which keeps war-drivers so busy trying to connect to nonexistent wireless networks that they don’t have time to discover your legitimate AP.
Consider using anti-wardriving software to make it more difficult for attackers to discover your WLAN. In Chapter 13, you learn about honeypots, which are hosts or networks available to the public that entice hackers to attack them instead of a company’s real network. IT personnel can study how an attack is made on the honeypot, which can be useful in securing the company’s actual network. To make it more difficult for wardrivers to discover your WLAN, you can use Black Alchemy Fake AP (available free at www.blackalchemy.to/project/fakeap/). As its name implies, this program creates fake APs, which keeps war-drivers so busy trying to connect to nonexistent wireless networks that they don’t have time to discover your legitimate AP.
![]() There are measures for preventing radio waves from leaving or entering a building so that wireless technology can be used only by people in the facility. One is using a certain type of paint on the walls, but this method isn’t foolproof because some radio waves can leak out if the paint isn’t applied correctly.
There are measures for preventing radio waves from leaving or entering a building so that wireless technology can be used only by people in the facility. One is using a certain type of paint on the walls, but this method isn’t foolproof because some radio waves can leak out if the paint isn’t applied correctly.
![]() Use a router to filter unauthorized MAC and IP addresses and prevent them from having network access. Unfortunately, some exploits enable attackers to spoof authorized addresses, but this measure makes exploits more difficult for typical attackers.
Use a router to filter unauthorized MAC and IP addresses and prevent them from having network access. Unfortunately, some exploits enable attackers to spoof authorized addresses, but this measure makes exploits more difficult for typical attackers.
![]() Consider using an authentication server instead of relying on a wireless device to authenticate users. A RADIUS server that can refer all users to a server running Windows Server 2008 with Active Directory can be used to authenticate wireless users attempting to access network resources. This method can also prevent an intruder from sending or receiving HTTP, DHCP, SMTP, or any network packets over the network before being authenticated.
Consider using an authentication server instead of relying on a wireless device to authenticate users. A RADIUS server that can refer all users to a server running Windows Server 2008 with Active Directory can be used to authenticate wireless users attempting to access network resources. This method can also prevent an intruder from sending or receiving HTTP, DHCP, SMTP, or any network packets over the network before being authenticated.
![]() Consider using EAP, which allows using different protocols that enhance security. For example, EAP enables using certificates for authentication, or wireless vendors can implement password-based authentication by using the EAP standard. EAP offers more options for increasing security.
Consider using EAP, which allows using different protocols that enhance security. For example, EAP enables using certificates for authentication, or wireless vendors can implement password-based authentication by using the EAP standard. EAP offers more options for increasing security.
![]() Consider placing the AP in the demilitarized zone (DMZ, covered in Chapter 13) and using a firewall in front of the company’s internal network that filters out traffic from unauthorized IP addresses.
Consider placing the AP in the demilitarized zone (DMZ, covered in Chapter 13) and using a firewall in front of the company’s internal network that filters out traffic from unauthorized IP addresses.
![]() WEP with 104-bit encryption is only marginally better than WEP with 40-bit encryption. If possible, replace WEP with WPA2 for better security, and replace hardware that can’t be upgraded to support WPA2. WEP encryption can be cracked easily with just the tools included in the BackTrack files, and researchers have shown that breaking WPA isn’t beyond a determined attacker’s abilities.
WEP with 104-bit encryption is only marginally better than WEP with 40-bit encryption. If possible, replace WEP with WPA2 for better security, and replace hardware that can’t be upgraded to support WPA2. WEP encryption can be cracked easily with just the tools included in the BackTrack files, and researchers have shown that breaking WPA isn’t beyond a determined attacker’s abilities.
![]() Assign static IP addresses to wireless clients instead of using DHCP.
Assign static IP addresses to wireless clients instead of using DHCP.
![]() Change the default SSID and disable SSID broadcasts, if possible. If you can’t disable SSID broadcasts, rename the default SSID to make it more difficult for attackers to determine the router’s manufacturer. For example, leaving the default SSID of Netgear makes it easy for an attacker to determine what router is being used. Changing its SSID to another manufacturer’s default SSID or to one not associated with any vendor might deter an attacker.
Change the default SSID and disable SSID broadcasts, if possible. If you can’t disable SSID broadcasts, rename the default SSID to make it more difficult for attackers to determine the router’s manufacturer. For example, leaving the default SSID of Netgear makes it easy for an attacker to determine what router is being used. Changing its SSID to another manufacturer’s default SSID or to one not associated with any vendor might deter an attacker.
These methods aren’t foolproof. In fact, by the time you read this book, there will be more ways to crack WPA and other security methods for protecting wireless LANs. That’s what makes the security field dynamic. There are no easy fixes. If there were, these fixes wouldn’t last long, unfortunately.
CHAPTER SUMMARY
![]() Wireless technology defines how and at what frequency data travels over the radio frequency (RF) spectrum. The term “wireless” generally describes equipment operating in the RF spectrum between 3 Hz and 300 GHz, although most wireless networking equipment operates between 2.4 GHz and 66 GHz.
Wireless technology defines how and at what frequency data travels over the radio frequency (RF) spectrum. The term “wireless” generally describes equipment operating in the RF spectrum between 3 Hz and 300 GHz, although most wireless networking equipment operates between 2.4 GHz and 66 GHz.
![]() The basic components of wireless networks are WNICs, which transmit and receive wireless signals; access points (APs), which are the bridge between wired and wireless networks; wireless networking protocols; and a portion of the RF spectrum that acts as a medium for carrying the signal.
The basic components of wireless networks are WNICs, which transmit and receive wireless signals; access points (APs), which are the bridge between wired and wireless networks; wireless networking protocols; and a portion of the RF spectrum that acts as a medium for carrying the signal.
![]() A service set identifier (SSID) is configured on the AP and used to identify a WLAN. It’s a unique, 1-to 32-character, case-sensitive alphanumeric name.
A service set identifier (SSID) is configured on the AP and used to identify a WLAN. It’s a unique, 1-to 32-character, case-sensitive alphanumeric name.
![]() IEEE’s main purpose is to create standards for LANs and WANs. 802.11 is the IEEE standard for wireless networking and includes many additional standards that address security and authentication.
IEEE’s main purpose is to create standards for LANs and WANs. 802.11 is the IEEE standard for wireless networking and includes many additional standards that address security and authentication.
![]() A BSS is the collection of all devices (APs and stations) that make up a WLAN. A BSA is the wireless coverage area that an AP provides to stations in a WLAN running in infrastructure mode. Although infrastructure mode is the most common in WLANs, independent stations can also establish an ad-hoc decentralized network that doesn’t require an AP.
A BSS is the collection of all devices (APs and stations) that make up a WLAN. A BSA is the wireless coverage area that an AP provides to stations in a WLAN running in infrastructure mode. Although infrastructure mode is the most common in WLANs, independent stations can also establish an ad-hoc decentralized network that doesn’t require an AP.
![]() WLANs use three technologies: infrared, narrowband, and spread spectrum. For data to be moved over radio waves, it must be modulated on the carrier signal or channel. The most common modulation methods for spread spectrum are DSSS, FHSS, and OFDM.
WLANs use three technologies: infrared, narrowband, and spread spectrum. For data to be moved over radio waves, it must be modulated on the carrier signal or channel. The most common modulation methods for spread spectrum are DSSS, FHSS, and OFDM.
![]() Bluetooth is the most popular form of WPAN technology (802.15 standard), which usually has a more limited range than a typical WLAN. On the other end of the spectrum is a MAN (802.16 standard), which has a much larger coverage area than a WLAN. WiMAX is the most common implementation of a wireless MAN.
Bluetooth is the most popular form of WPAN technology (802.15 standard), which usually has a more limited range than a typical WLAN. On the other end of the spectrum is a MAN (802.16 standard), which has a much larger coverage area than a WLAN. WiMAX is the most common implementation of a wireless MAN.
![]() WEP, WPA and WPA2 are wireless encryption standards used to protect WLANS from unauthorized access and eavesdropping. WEP is easy to crack, WPA is harder to crack, and WPA2 is the most secure of these three.
WEP, WPA and WPA2 are wireless encryption standards used to protect WLANS from unauthorized access and eavesdropping. WEP is easy to crack, WPA is harder to crack, and WPA2 is the most secure of these three.
![]() Authentication is usually used in combination with wireless encryption standards to ensure that access to a WLAN is authorized. 802.1x is an example of WLAN authentication and has three components: the supplicant, a wireless user attempting access to a WLAN; the authenticator, the AP that allows or denies a supplicant’s access; and the authentication server, such as a RADIUS server.
Authentication is usually used in combination with wireless encryption standards to ensure that access to a WLAN is authorized. 802.1x is an example of WLAN authentication and has three components: the supplicant, a wireless user attempting access to a WLAN; the authenticator, the AP that allows or denies a supplicant’s access; and the authentication server, such as a RADIUS server.
![]() Wardriving and warflying involve driving in a car or flying in a plane with a laptop computer, a WNIC, an antenna, and software that scans for available APs.
Wardriving and warflying involve driving in a car or flying in a plane with a laptop computer, a WNIC, an antenna, and software that scans for available APs.
![]() WLANs can be attacked with many of the same tools used for hacking wired LANs. For example, a sniffer such as Wireshark can also be used to scan WLANs for logon and password information. Specialized wireless tools include NetStumbler and iwScanner, which can survey APs as part of a wardriving scan, and Kismet, a sophisticated multipurpose wireless tool that can detect hidden network SSIDs.
WLANs can be attacked with many of the same tools used for hacking wired LANs. For example, a sniffer such as Wireshark can also be used to scan WLANs for logon and password information. Specialized wireless tools include NetStumbler and iwScanner, which can survey APs as part of a wardriving scan, and Kismet, a sophisticated multipurpose wireless tool that can detect hidden network SSIDs.
![]() Some methods for protecting a wireless network are disabling SSID broadcasts, renaming default SSIDs, using an authentication server, placing the AP in the DMZ, using EAP, upgrading to WPA2, assigning static IP addresses to wireless clients, and using a router to filter unauthorized MAC and IP addresses and prevent them from having network access.
Some methods for protecting a wireless network are disabling SSID broadcasts, renaming default SSIDs, using an authentication server, placing the AP in the DMZ, using EAP, upgrading to WPA2, assigning static IP addresses to wireless clients, and using a router to filter unauthorized MAC and IP addresses and prevent them from having network access.
