Chapter 5. Access Control and Authentication Basics
Terms you need to understand
![]() Mandatory access control (MAC)
Mandatory access control (MAC)
![]() Discretionary access control (DAC)
Discretionary access control (DAC)
![]() Role-based access control (RBAC)
Role-based access control (RBAC)
![]() Challenge-Handshake Authentication Protocol (CHAP)
Challenge-Handshake Authentication Protocol (CHAP)
Techniques you need to master
![]() Be able to recognize the forms of access control (MAC/DAC/RBAC).
Be able to recognize the forms of access control (MAC/DAC/RBAC).
![]() Understand the process of authentication and the various forms of authentication available.
Understand the process of authentication and the various forms of authentication available.
![]() Be able to recognize asymmetric and symmetric encryption methods.
Be able to recognize asymmetric and symmetric encryption methods.
![]() Explain the strengths and vulnerabilities of various physical security zones and devices.
Explain the strengths and vulnerabilities of various physical security zones and devices.
The concept of security within the network environment includes aspects drawn from all operating systems, application software packages, hardware solutions, and networking configurations present within the network to be secured, and from within any network-sharing connectivity directly or indirectly with the network to be secured. For the Security+ exam, you need to develop the broadest set of skills possible, gaining experience from the most specific to the most general of security concepts. Awareness of emerging threats is essential to testing success.
This chapter and Chapter 6, “Securing Communications,” provide an overview of general concepts you should familiarize yourself with. This chapter focuses on access control mechanisms and methods for secure network authentication and physical access. A general knowledge of network terminology will aid in understanding these concepts. As a prospective security professional, you should also take every opportunity you may find to expand your skill base beyond these. The practice of a security professional is never an end unto itself, but rather a never-ending path threaded through constant change and ever-evolving possibility.
Access Control
This section examines the methods for controlling access to network resources. Planning for access control may affect the methods used in the authentication process examined later in this chapter. For example, if there will be a need only for anonymous access to a public read-only HTML document, the simple access control mandates eliminate the need for a complex authentication process.
Access control generally refers to the process of making resources available to accounts that should have access, while limiting that access to only what is required. The forms of access control you need to know include the following:
• Mandatory access control (MAC)
• Discretionary access control (DAC)
• Role-based access control (RBAC)
We discuss these types of access control and access control best practices in the following sections. These methods and best practices are based on security criteria set by various efforts. Trusted Computer System Evaluation (TCSEC) and Information Technology Security Evaluation Criteria (ITSEC) are major security criteria efforts. The Common Criteria is based on both TCSEC and ITSEC.
Mandatory Access Control
The most basic form of access control involves the assignment of labels to resources and accounts. If the labels on the account and resource do not match, the resource remains unavailable in a nondiscretionary manner. This type of access control is called mandatory access control (MAC, also referred to as multilevel access control) and is often used within governmental systems where resources and access may be granted based on categorical assignment such as classified, secret, or top secret. Mandatory access control applies to all resources within the network and does not allow users to extend access rights by proxy.
Discretionary Access Control
A slightly more complex system of access control involves the restriction of access for each resource in a discretionary manner. DAC scenarios allow individual resources to be made available or secured from access individually. Access rights are configured at the discretion of accounts with authority over each resource, including the ability to extend administrative rights through the same mechanism. In DAC a subject has complete control over the objects that it owns. The owner assigns security levels based on objects and subjects.
Role-Based Access Control
In an RBAC scenario, access rights are first assigned to roles, and accounts are then assigned these roles without direct assignment of resource access rights. This solution provides the greatest level of scalability within large enterprise scenarios, where the explicit granting of rights to each individual account could rapidly overwhelm administrative staff, and the potential for accidental grant of unauthorized permissions increases.
RBAC combines direct access aspects of MAC and varying access rights based on role membership. Delegation of administration over rights granted through RBAC is itself managed by specialized administration roles, rather than though ownership or direct control over the individual resources as in DAC solutions.
Access Control Best Practices
Along with the previously mentioned “less-is-more” stance for access control, a number of other best practices exist. You should be familiar with the following:
• Implicit deny—An access control practice wherein resource availability is restricted to only those logons explicitly granted access, remaining unavailable even when not explicitly denied access. This practice is used commonly in Cisco networks, where most ACLs have a default setting of “implicit deny.” This ensures that when access is not explicitly granted, it is automatically denied by default.
• Least privilege—An access control practice wherein a logon is provided only the bare minimum access to resources required to perform its tasks. Whenever confronted by a solution involving the determination of proper levels of access, remember the phrase “less is more.” This is a convenient reminder of the security practice known as the principle of least privilege, where an account is granted no more access rights than the bare minimum needed to perform assigned tasks.
• Separation of duties—An access control practice involving both the separation of logons, such as day-to-day and admin accounts both assigned to the same network admin, and the separation of roles, such as security assignment and compliance audit procedures. Separation of account functionality protects the network by ensuring that an inadvertent malware execution during normal daily operations cannot then attack the network with full administrative privileges. Separation of role duties ensures that validation is maintained apart from execution, protecting the network against fraudulent actions or incomplete execution of security mandates.
The User Access Control (UAC) technology used by the Microsoft Vista operating system ensures that software applications cannot perform privileged access without additional authorization from the user. Within the Microsoft environment, lesser accounts may perform privileged processes using the “run as” option to specify the explicit use of a privileged account.
• Expiration—An access control practice to expire passwords on a regular basis, protecting against brute-force password guessing attacks, and to expire accounts not used after a certain period of time. Unused accounts often retain weak passwords used in initial assignment and may be more susceptible to password-guessing routines.
• Job rotation—As an extension of the separation of duties, rotating administrative users between roles both improves awareness of the mandates of each role, while also ensuring that fraudulent activity cannot be sustained. This is also the reason that users with administrative access may be required take vacations, allowing other administrators to review standard operating practices in place.
Authentication
Before authorization may occur for anything other than anonymous access to wholly public resources, the identity of the account attempting to access a resource must first be determined. This process is known as authentication. The most well-known form of authentication is the use of a logon account identifier and password combination to access controlled resources. Access is not possible without both parts required for account authentication, so a level of protection is provided.
The relative strength of an authentication system involves the difficulty involved in falsifying or circumventing its process. Anonymous or open access represents the weakest possible form of authentication, whereas the requirement for both a logon identifier and password combination may be considered the most basic of actual account verification. The highest levels of authentication may involve not only account logon, but also if the logon is occurring from specific network addresses or whether a security token such as an access smart card is present.
In theory, the strongest security would be offered by identifying biometric keys unique to a particular user’s person or physical body, such as fingerprints and retinal or iris patterns, combined with other authentication methods involving access passwords or token-based security requiring the possession of a physical smart card key.
Obviously, the needs for authentication are going to be relative to the value assigned to a particular resource’s security. Additional authentication layers required for access increase both the administrative overhead necessary for management and the difficulty users will have trying to access needed resources. Consider, for example, the differences in authentication requirements for access to a high-security solution such as the Federal Reserve’s banking network as opposed to those needed to access an unprivileged local account in a public kiosk.
In the first scenario, to establish authentication for rightful access, the use of a combination of biometric, token-based, and password-form access methods may be mandatory. You may also use these access methods with even more complex forms of authentication, such as the use of dedicated lines of communication, time-of-day restrictions, synchronized shifting-key hardware encryption devices, and redundant-path comparison. You would use these to ensure that each account attempting to make a transaction is properly identified. In the second scenario, authentication might be as simple as an automatic anonymous guest logon shared by all visitors.
Each mechanism for authentication provides different levels of identification, security over data during the authentication exchange, and suitability to different access methods such as wireless or dial-up network access. We will now examine several forms of authentication you should be familiar with for the exam.
Kerberos Authentication
The most basic aspects of authentication within a completely isolated network include only the need to determine the identity of an account. If a network is physically or logically accessible to external parties that might seek to sniff (capture and examine) data being transacted between systems, the problem arises as to how to keep the authentication keys themselves safe.
Here is an example: A basic File Transfer Protocol (FTP) access session involves the client sending a logon identifier and a password to the FTP server, which accepts or rejects this access. The logon identifier and password, by default, are sent in plain-text form, readable by any agent with access to the data as it is transmitted from the client to the server. An unauthorized party, pretending to be the authorized user, might use this information later to gain access to the server.
To avoid sending the actual logon information across an unsecured network, one solution is the symmetric-key authentication protocol known as Kerberos (created by the Athena project at MIT). A symmetric key means that both the client and server must agree to use a single key in both the encryption and decryption processes (see Figure 5.1). Kerberos is primarily a UDP protocol, although it falls back to TCP for large Kerberos tickets. Kerberos clients send UDP and TCP packets on port 88 and receive replies from the Kerberos servers. Port 88 is the standard port for Kerberos 5. You may also find references to ports 749 and 750 used by earlier versions of Kerberos.
Figure 5.1. Example of a symmetric-key encrypted data transfer.
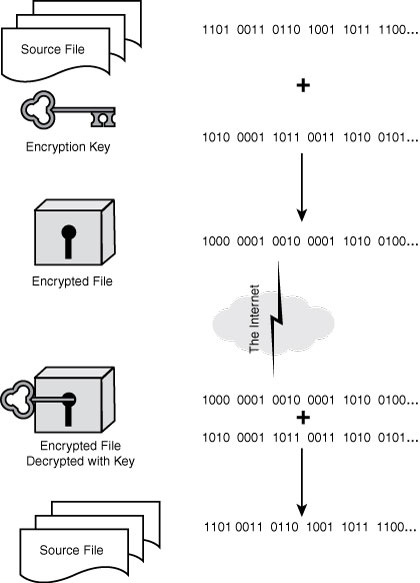
In Kerberos authentication, a client sends its authentication details not to the target server, but rather to a Key Distribution Center (KDC), as follows:
1. The client first contacts a certification authority (CA).
2. The CA creates a time-stamped session key with a limited duration (by default, eight hours) using the client’s key and a randomly generated key that includes the identification of the target service.
3. This information is sent back to the client in the form of a Ticket-Granting Ticket (TGT).
4. The client then submits the TGT to a Ticket-Granting Server (TGS).
5. This server then generates a time-stamped key encrypted with the service’s key and returns both to the client.
6. The client then uses its key to decrypt its ticket, contacts the server, and offers the encrypted ticket to the service.
7. The service uses its key to decrypt the ticket and verify that the time stamps match and the ticket remains valid.
8. The service contacts the KDC and receives a time-stamped session keyed ticket that it returns to the client.
9. The client then decrypts the keyed ticket using its key. When both agree that the other is the proper account and that the keys are within their valid lifetime, communication occurs.
The short lifespan of a ticket ensures that if someone attempts to intercept the encrypted data to try to break its keys, the key will have changed before he or she can reasonably be able to break the key using cryptographic algorithms. The handshaking between the client and the KDC and between the service and the KDC provides verification that the current session is valid, without requiring the transmission of logons or passwords between client and service.
The strengths of Kerberos authentication come from its time-synchronized connections and the use of registered client and service keys within the KDC. These also create some drawbacks, such as the need to use a standard time base for all systems involved, and difficulties that can result if the KDC is unavailable or the cached client and service credentials were accessed directly from the granting servers. An important advantage of time-stamped credentials is that they help prevent spoofing and replay attacks.
Mutual Authentication
Kerberos 5 includes support for a process known as mutual authentication, in which both client and server verify that the computer with which they are communicating is the proper system. This process helps to prevent man-in-the-middle attacks, where an unauthorized party intercepts communications between two systems and pretends to be each to the other, passing some data intact, modifying other data, or inserting entirely new sets of values to accomplish desired tasks. (Chapter 3, “Infrastructure Basics,” covers man-in-the-middle attacks in more detail.)
In mutual authentication, one system creates a challenge code based on a random number and then sends this code to the other system. The receiving system generates a response code using the original challenge code and creates a challenge code of its own, sending both back to the originating system. The originating system verifies the response code as a value and returns its own response code to the second system, generated from the challenge code returned with the first response code. After the second system has verified its returned response code, it notifies the originating system, and both systems consider themselves mutually authenticated.
Challenge-Handshake Authentication Protocol
The Challenge-Handshake Authentication Protocol (CHAP) can be used to provide on-demand authentication within an ongoing data transmission. CHAP is an improvement over Password Authentication Protocol (PAP). PAP is a basic form of authentication during which the username and password are transmitted unencrypted. CHAP uses a one-way hashing function that first involves a service requesting a CHAP response from the client. The client creates a hashed value that is derived using the message digest (MD5) hashing algorithm and sends this value to the service, which also calculates the expected value itself. The server, referred to as the authenticator, compares these two values. If they match, the transmission continues. This process is repeated at random intervals during a session of data transaction.CHAP functions over Point-to-Point Protocol (PPP) connections. PPP is a protocol for communicating between two points using a serial interface, providing service at the second layer of the OSI model: the data-link layer. PPP can handle both synchronous and asynchronous connections.
Occasionally, you might find Shiva Password Authentication Protocol (SPAP) implemented. SPAP was designed by Shiva and is an older, two-way reversible encryption protocol that encrypts the password data sent between client and server. A computer running Windows XP Professional, when connecting to a Shiva LAN Rover, uses SPAP, as does a Shiva client that connects to a server running Routing and Remote Access. This form of authentication is more secure than plaintext but less secure than CHAP or MS-CHAP.
Terminal Access Controller Access Control System Plus
The Terminal Access Controller Access Control System Plus (TACACS+) remote-access control system, which provides authentication, accounting, and access control, relies on a central server to provide access over network resources, including services, file storage, and network routing hardware. TACACS+ is a replacement for the older TACACS and is not backward compatible with the legacy TACACS standard made popular over Telnet connectivity originally developed for UNIX systems. TACACS+ is similar to Remote Authentication Dial-In User Service (RADIUS), but relies on Transmission Control Protocol (TCP) rather than RADIUS’s User Datagram Protocol (UDP) transport developed originally for modem-based connectivity access control.
Remote Authentication Dial-In User Service
The RADIUS remote-access control system provides authentication and access control within an enterprise network using UDP transport to a central network access server, which in turn provides credentials for access to resources within an extended enterprise. Developed originally for use in dial-up connectivity over telephonic modems, you might still find RADIUS servers in larger enterprises where logons must span resources located in multiple logon realms.
IEEE 802.1x
The IEEE 802.1x standard for wireless, port-based access control can be used to provide authentication and access control but is often paired with a RADIUS service to facilitate enterprisewide access management. Because of the broadcast nature of wireless connectivity, additional transport security is often used in conjunction with 802.1x authentication to secure communications between the mobile device and the secured network. Internet Protocol Security (IPsec) is another common protocol used in conjunction with IEEE 802.1x to provide this functionality.
Certificates
One of the most rigorous forms of authentication involves the use of digital certificates within a public key infrastructure (PKI) to establish encrypted communication streams through unsecured networks. Public key systems use an asymmetric cryptographic process in which the encryption and decryption keys are not the same as in a symmetric cryptographic process like that used in Kerberos authentication.
In public key encryption, a public and private key are generated by a CA, and these keys are returned to the client in the form of digital certificates. The public key is given to those who need to encrypt data and send it to the client. The client then decrypts the data using its private key that only the client has. The public key is used to encrypt a message, and the private key is used to decrypt the results.
A registration authority (RA) provides authentication to the CA of the validity of a client’s certificate request. One of the most commonly used certification and registration authorities is VeriSign, a vendor specializing in the issuance of X.509 certificates for secure website connections.
Username and Password
The most commonform of authentication combines a username and a password or pass-phrase. If both match values are stored within a locally stored table, the user is authenticated for a connection. Password strength is a measure of the difficulty involved in guessing or breaking the password through cryptographic techniques or library-based automated testing of alternative values.
A weak password might be very short or only use alphanumeric characters, making decryption simple. A weak password can also be one that is easily guessed by someone profiling the user, such as a birthday, nickname, address, name of a pet or relative, or a common word such as God, love, money, or password. Password policy is discussed in greater detail in Chapter 4, “Infrastructure Security and Controls.” Make sure that you are familiar with the details presented there, too.
Tokens
One of the best methods of authentication involves the use of a token, which may either be a physical device or a one-time password issued to the user. Tokens include solutions such as a chip-integrated smart card or a digital token such as RSA Security’s SecurID tokens. Without the proper token, access is denied. Because the token is unique and granted only to the user, it is harder to pretend to be (spoof) the properly authorized user. Digital tokens are typically used only one time so that they cannot be captured and reused later by an unauthorized party. Chapter 4 includes details on logical tokens that you should be familiar with.
Biometrics
The most unique quality of a user is his or her unique physical characteristics, such a fingerprints, retinal patterns, iris patterns, facial blood-vessel patterns, bone structure, and other forms of specific unique biophysical qualities. Other values may be used, such as voice-pattern recognition or high-resolution cardiac patterns; but because these may change based on illness or exertion, they can be somewhat less dependable.
New systems are becoming available to allow authentication users by their body measurements (biometrics), which are compared to values stored within a local table to provide authentication only if the biometric values match. Another alternative is to store biometric data on smart card tokens. Under this scenario, users must be authenticated within a widely distributed scheme where transactions against a central server storing large and complex biometric values might be difficult. Table 5.1 describes the most common biometrics methods.
Table 5.1. Biometric Technologies

Biometric devices are susceptible to false acceptance and false rejection rates. The false acceptance rate (FAR) is a measure of the likelihood that the access system will wrongly accept an access attempt—in other words, allow access to an unauthorized user. The false rejection rate (FRR) is the percentage of identification instances in which false rejection occurs. In false rejection, the system fails to recognize an authorized person and rejects that person as unauthorized.
Multifactor Authentication
The best possible authentication solution combines multiple other methods. One example of a multifactor solution is the use of a smart card token that stores biometric values that are compared to those of the user, who might also be asked to enter a valid password. The difficulty involved in gaining unauthorized access increases as more types of authentication are used, although the difficulty for users wanting to authenticate themselves is also increased similarly. Administrative overhead and cost of support also increase with the complexity of the authentication scheme, so a solution should be reasonable based on the sensitivity of data being secured.
Single Sign-On
Distributed enterprise networks often include many different resources, each of which may require a different mechanism for authentication and access control. To reduce user support and authentication complexity, a single sign-on (SSO) capable of granting access to all services is desirable. SSO solutions may use a central directory service, such as Microsoft Active Directory or Novell eDirectory service, or may sequester services behind a series of proxy applications as in the service-oriented architecture (SOA) approach. In the SOA network environment, the client-facing proxy application provides a standard mechanism for interacting with each service, handling specialized logon, authentication, and access control functions “behind the scenes” out of sight of the consuming user or service.
Identity Proofing
Identity proofing is an organizational process that binds users to authentication methods. Identity proofing gives the organization assurance that the user performing an authentication is the legitimate user. Identity proofing is the main component of authentication life cycle management. The first link in the chain of trust is established when a person is issued a credential establishing identity or privileges. It must provide a firm assurance that persons are who they say they are. This technique can include integrated biometrics or online database validation. Identity proofing comes in a variety of forms. A poorly identity-proofed smart card provides less identity assurance than an effectively identity-proofed password. Authenticators include smart cards, biometrics, and one-time password (OTP) devices. Identity proofing is especially important in emergency access (for example, when users forget their hardware token).
Operating System Hardening
In security terms, hardening a system refers to reducing its security exposure and strengthening its defenses against unauthorized access attempts and other forms of malicious attention. A “soft” system is one that is installed with default configurations or unnecessary services, or one that is not maintained to include emerging security updates. There is no such thing as a “completely safe” system, so the process of hardening reflects attention to security thresholds.
Nonessential Services and Protocols
Systems installed in default configurations often include many unnecessary services that are configured automatically. These provide many potential avenues for unauthorized access to a system or network. Many services have known vulnerabilities that require specific action to make them more secure, or ones that might just impair system function by causing additional processing overhead. Default configurations also allow for unauthorized access and exploitation.
Common default-configuration exploits include both services such as anonymous-access FTP servers and network protocols such as the Simple Network Management Protocol (SNMP). Others may exploit vendor-supplied default logon/password combinations, such as the Oracle Db default admin: scott/tiger.
Patch Management
Many vendors provide regular updates for installed products, managed through automated deployment tools or by manual update procedures carried out by a system user. Regular maintenance is required to meet emerging security threats, whether applying an updated RPM (Redhat Package Manager, a file format used to distribute Linux applications and update packages) by hand or through fully automated “call home for updates” options like those found in many commercial operating systems and applications.
Because of the emergence of blended-threat malware, which targets multiple vulnerabilities within a single attack, all major operating systems and application solutions must be considered in system hardening plans. Automated reverse-engineering of newly released patches has significantly reduced the time from an update’s initial release until its first exploits are seen in the wild, down from months to hours before unpatched applications can be targeted.
Types of updates you should be familiar with include the following:
• Hotfixes—Typically, small and specific-purpose updates that alter the behavior of installed applications in a limited manner. These are the most common type of update.
• Service packs—Major revisions of functionality or service operation in an installed application. Service packs are the least common type of update, often requiring extensive testing to ensure against service failure in integrated network environments before application. Service packs are usually cumulative, including all prior service packs, hotfixes, and patches.
• Patches—Like hotfixes, patches are usually focused updates that affect installed applications. Patches are generally used to add new functionality, update existing code operation, or to extend existing application capabilities.
Security Settings
To establish effective security baselines, enterprise network security management requires a measure of commonality between systems. Mandatory settings, standard application suites, and initial setup configuration details all factor into the security stance of an enterprise network.
Types of configuration settings you should be familiar with include the following:
• Group policies—Collections of configuration settings applied to a system based on computer or user group membership, which may influence the level, type, and extent of access provided.
• Security templates—Sets of configurations that reflect a particular role or standard established through industry standards or within an organization, assigned to fulfill a particular purpose. Examples include a “minimum-access” configuration template assigned to limited-access kiosk systems, whereas a “high-security” template could be assigned to systems requiring more stringent logon and access control mechanisms.
• Configuration baselines—Many industries must meet specific criteria, established as a baseline measure of security. An example of this is the health-care industry, which has a lengthy set of requirements for information technology specified in the Health Insurance Portability and Accountability Act (HIPAA) security standards. Unless the mandated security baseline is met, penalties and fines could be assessed. Security baselines are often established by governmental mandate, regulatory bodies, or industry representatives, such as the PCI requirements established by the credit card industry for businesses collecting and transacting credit information.
Physical Access Security Methods
When planning security for network scenarios, many organizations overlook physical security. In many smaller organizations, the servers, routers, and patch panels are placed as a matter of convenience because of space restrictions. This can cause security issues. Speaking from experience, this equipment ends up in the oddest places, such as in the coat closet by the receptionist’s desk in the lobby, in the room with the copy machine, or in a storage room with a backdoor exit that’s unlocked most of the time. Securing physical access and ensuring that access requires proper authentication is necessary to avoid accidental exposure of sensitive data to attackers performing physical profiling of a target organization.
When planning physical security, you must consider events such as natural and man-made disasters. If you have space constraints and put the servers in a room with the water heater, how will you deal with the consequences when the water heater springs a leak? How soon will your network be back up and running? If your building is in a flood zone and the most important equipment is in the lowest spot in the building, you need to be prepared when heavy rains come. Man-made disasters can be as simple as a clumsy technician spilling his soda into the most important piece of equipment you have. Many times, these types of scenarios are overlooked until it is too late.
Physical access to a system creates many avenues for a breach in security, for several reasons. Many tools may be used to extract password and account information that can then be used to access secured network resources. Given the ability to reboot a system and load software from a floppy disk, attackers may be able to access data or implant Trojan horses and other applications intended to weaken or compromise network security. Unsecured equipment is also vulnerable to social engineering attacks. It is much easier for an attacker to walk into a reception area, say she is there to do some work on the server, and get access to that server in the closet in the front lobby than to get into a physically secured area with a guest sign-in and sign-out sheet. As mentioned earlier, weak physical controls can also amplify the effects of natural and man-made disasters.
Physical security controls parallel the data controls. Mandatory physical access controls are commonly found in government facilities and military installations, where users are closely monitored and very restricted. Because they are being monitored by security personnel and devices, users cannot modify entry methods or let others in. Discretionary physical control to a building or room is delegated to parties responsible for that building or room. In role-based access methods for physical control, groups of people who have common access needs are predetermined, and access to different locations is allowed with the same key or swipe card. Users in this model generally have some security training and are often allowed to grant access to others by serving as an escort or by issuing a guest badge. The security department coordinates the secure setup of the facility and surrounding areas, identifies the groups allowed to enter various areas, and allows them access based on their group membership.
When physical security is considered, the most obvious element to control is physical access to systems and resources. Your goal is to allow only trusted use of these resources via positive identification that the entity accessing the systems is someone or something that has permission to do so based on the security model you have chosen. When planning for access control, you pay attention not only to direct physical contact with hosts and network hardware but also to line-of-sight access, which means you need to place systems in such a way that you don’t allow an attacker with a telescope or binoculars to spy on typed passwords. You also need to consider areas covered by wireless device transmissions, which may be detected at far greater distances than are useful for two-way network connectivity. Even the location of systems in low-traffic, public, or unmonitored areas may pose security risks.
This section covers physical access control, including barriers, facilities, and environments. Social engineering and user education are also covered.
Physical Barriers
Access might be controlled by physically securing a system within a locked room or cabinet; attaching the system to fixed, nonmovable furniture using locking cables or restraints; and locking the case itself to prevent the removal of key components. Nonstandard case screws are also available to add another layer of security for publicly accessible terminals. Other secured-area considerations include ensuring that air ducts, drop ceilings, and raised floors do not provide unauthorized avenues for physical access. You can have the most secure lock on the door with biometric devices for identification, but if the walls don’t go up all the way and ceiling tiles can be removed to access rooms with sensitive equipment in them, someone can easily walk off with equipment and sensitive data.
Frosted or painted glass can be used to eliminate direct visual observation of user actions, and very high-security scenarios may mandate the use of electromagnetic shielding to prevent remote monitoring of emissions generated by video monitors, network switching, and system operation. In addition, many modems and network hardware solutions use raw, transmitted data to illuminate activity indicator lights. Direct observation of these may enable an attacker to remotely eavesdrop on transmitted data using a telescope.
Security guards, surveillance cameras, motion detectors, limited-access zones, token-based and biometric access requirements for restricted areas, and many other considerations may be involved in access control planning. In addition, users must be educated about each measure taken, to prevent circumvention to improve ease of normal access. A single propped-open door, a system left logged in when the administrator is away from her desk, or a paper with sensitive data on it thrown in the garbage could undo many layers of protection.
Facilities
Because a physical security plan should start with examining the perimeter of the building, this section discusses the various methods used to secure your facilities from the outside of the building.
Buildings that house sensitive information and systems usually have an area of cleared land surrounding them. This area is referred to as no-man’s land. The purpose of this area is to eliminate the possibility of an intruder hiding in the bushes or behind another building. Intruders often piggyback their way into a building, meaning they wait for someone with proper access to enter the building and then enter behind before the door closes. Depending on the company policy, the time of day, or the employee, these intruders may never be questioned or escorted out. Having a clear area in the main facility can keep this from happening.
Another common deterrent is a fence or similar device that surrounds the entire building. A fence keeps out unwanted vehicles and people. One factor to consider in fencing is the height. The higher the fence, the harder it is to get over. Another factor to consider is the material the fence is made of. It is much easier to remove wooden slats or cut a chain-link fence with bolt cutters than it is to drill through concrete or block. One final note: If the fence isn’t maintained or the area around it isn’t well lit, the fence can easily be compromised.
Another physical barrier is a moat. Moats surround part or all of a facility and are excellent physical barriers because they have a low profile and are not as obtrusive as fencing. In this instance, the consideration is the depth and width. As with all physical barriers, the moat must be well maintained.
Other Deterrents
You can implement the following additional security measures to help deter unauthorized access:
• Security guards and dogs—Security guards and dogs can be great deterrents to intruders. It is imperative that they are trained properly. They are often used in combination with other measures.
• External lighting and cameras—If areas are brightly lit and have cameras, they are less likely to have unauthorized access attempts.
• External and internal motion detectors—Motion detectors can alert security personnel of intruders or suspicious activity on the company’s premises. They can be based on light, sound, infrared, or ultrasonic technology. These devices must be properly configured because they are extremely sensitive and can issue false alarms if set too stringently.
• External doors and windows—Steel doors are the best deterrent, but steel-reinforced wooden doors work, too. Windows should have locking mechanisms, and building security alarms should monitor the open/closed position of all windows that could pose an entry risk.
• Mantraps—A mantrap is a holding area between two entry points that gives security personnel time to view a person before allowing him into the internal building.
• Locks—Locks must be easy to operate yet deter intruders. Besides the normal key locks, several different types can be considered. A cipher lock has a punch-code entry system. A wireless lock is opened by a receiver mechanism that reads the card when it is held close to the receiver. A swipe card lock requires a card to be inserted into the lock; many hotels use these. The factors to consider are strength, material, and cost.
• Biometrics—Physical security can also integrate biometric methods into a door-lock mechanism. Biometrics can use a variety of methods. See Table 5.1 for a review of these technologies. When using biometrics, remember that each method has its own degree of error ratios, and some methods may seem invasive to the users and may not be accepted gracefully.
• Door access systems—Door access systems include biometric access, proximity access, and coded access systems, Disability Discrimination Act (DDA) door entry systems, and modular door entry systems. The type of access used will depend on the amount of security needed.
• Video surveillance—Closed-circuit television (CCTV) is the most common method of surveillance. The picture is viewed or recorded, but not broadcast. It was originally developed as a means of security for banks. IP video surveillance uses TCP/IP for recording and monitoring.
Make sure that all users understand how these plans function and practice orderly evacuation procedures so that an emergency situation does not leave critical systems unguarded or unsecured. Smoke from a cigarette or a purposefully set flame could create an opportunity for an attacker to gain access to highly secure areas if evacuation planning does not include security considerations.
Exam Prep Questions
1. You are the network administrator responsible for selecting the access control method that will be used for a new kiosk system to be used in a local museum. The museum’s donors want to have full access to information about all items, but visitors should have access only to those items on current display. Which forms of access control are most appropriate to this requirement? (Choose two correct answers.)
![]() A. Discretionary access control
A. Discretionary access control
![]() B. Mandatory access control
B. Mandatory access control
![]() C. Role-based access control
C. Role-based access control
![]() D. Rule-based access control
D. Rule-based access control
2. Which of the following best describes identity proofing?
![]() A. Specifies the types of access attempts that cause the system to generate a record in the security event log
A. Specifies the types of access attempts that cause the system to generate a record in the security event log
![]() B. Model in which permissions are uniquely assigned to each account
B. Model in which permissions are uniquely assigned to each account
![]() C. Organizational process that binds users to authentication methods
C. Organizational process that binds users to authentication methods
![]() D. Controls how access to a computer’s processors and memory is shared
D. Controls how access to a computer’s processors and memory is shared
3. Which of the following criteria is not a common criterion to authenticate a valid access request?
![]() A. Something you have
A. Something you have
![]() B. Where you logon
B. Where you logon
![]() C. What you know
C. What you know
![]() D. Something you do
D. Something you do
![]() E. Something you are
E. Something you are
4. When reviewing user access to a service or resource, what is the order of operation?
![]() A. Access must be granted first, and then authentication occurs.
A. Access must be granted first, and then authentication occurs.
![]() B. Authentication occurs first, and then access is determined.
B. Authentication occurs first, and then access is determined.
![]() C. Authentication and access control occur separately at the same time.
C. Authentication and access control occur separately at the same time.
![]() D. A user’s access rights are determined by the method of authentication used.
D. A user’s access rights are determined by the method of authentication used.
5. Which type of authentication involves comparison of two values calculated using the message digest (MD5) hashing algorithm?
![]() A. Biometric authentication
A. Biometric authentication
![]() B. Challenge-Handshake Authentication Protocol (CHAP)
B. Challenge-Handshake Authentication Protocol (CHAP)
![]() C. Kerberos authentication
C. Kerberos authentication
![]() D. Mutual authentication
D. Mutual authentication
![]() E. Public key infrastructure (PKI)
E. Public key infrastructure (PKI)
6. Many different keys may be used to perform user authentication. Which of the following are biometric authentication types? (Choose all that apply.)
![]() A. One-use passcode
A. One-use passcode
![]() B. Voice recognition
B. Voice recognition
![]() C. Fingerprint
C. Fingerprint
![]() D. Smart card
D. Smart card
![]() E. Facial recognition
E. Facial recognition
![]() F. Iris identification
F. Iris identification
7. Which of the following is an example of the use of an asymmetric encryption method?
![]() A. Biometric authentication
A. Biometric authentication
![]() B. Challenge-Handshake Authentication Protocol (CHAP)
B. Challenge-Handshake Authentication Protocol (CHAP)
![]() C. Kerberos authentication
C. Kerberos authentication
![]() D. Username and password
D. Username and password
![]() E. Public key infrastructure (PKI)
E. Public key infrastructure (PKI)
8. You are the network administrator responsible for selecting the access control method that will be used for a new parking garage. Members of the board of directors must always be granted access, whereas other staff members should be granted access to the parking garage only when spaces are available. Visitors should be allowed access only during normal business hours. What form of access control is best for this scenario?
![]() A. Discretionary access control
A. Discretionary access control
![]() B. Mandatory access control
B. Mandatory access control
![]() C. Role-based access control
C. Role-based access control
![]() D. Rule-based access control
D. Rule-based access control
9. Which of the following might be used in multifactor authentication? (Choose all correct answers)
![]() A. Biometric authentication
A. Biometric authentication
![]() B. Challenge-Handshake Authentication Protocol (CHAP)
B. Challenge-Handshake Authentication Protocol (CHAP)
![]() C. Kerberos authentication
C. Kerberos authentication
![]() D. Username and password
D. Username and password
![]() E. Public key infrastructure (PKI)
E. Public key infrastructure (PKI)
10. You are presented with an authentication scheme in which Computer A calculates a code it sends to Computer B, Computer B returns a calculated code based on the one from Computer B and one of its own, and then Computer A returns a calculated code to computer B based on its transmitted code. What type of authentication is this?
![]() A. Biometric authentication
A. Biometric authentication
![]() B. Challenge-Handshake Authentication Protocol (CHAP)
B. Challenge-Handshake Authentication Protocol (CHAP)
![]() C. Kerberos authentication
C. Kerberos authentication
![]() D. Mutual authentication
D. Mutual authentication
![]() E. Public key infrastructure (PKI)
E. Public key infrastructure (PKI)
11. External motion detectors can use which of the following technologies? (Select all correct answers.)
![]() A. RFID
A. RFID
![]() B. Infrared
B. Infrared
![]() C. Ultrasonic
C. Ultrasonic
![]() D. Sound
D. Sound
Answers to Exam Prep Questions
1. B, C. A mandatory access control solution involving labels such as DONOR and DISPLAY would suffice for the user access assignment. A role-based access control solution involving the roles of User and Donor would also be appropriate. Answer A is incorrect because the complexity of assigning by-user access rights over each item’s files would involve a large amount of administrative overhead. Answer D is incorrect because the complexity of the requirement is not great enough to involve detailed conditional testing.
2. C. Identity proofing gives the organization assurance that the user performing an authentication is the legitimate user. Answer A is incorrect because access control entries specify the types of access attempts that cause the system to generate a record in the security event log. Answer B is incorrect because in a user-based model permissions are uniquely assigned to each account. Answer D is incorrect because a hypervisor controls how access to a computer’s processors and memory is shared.
3. B. Although rules-based access controls may restrict access to a particular address or terminal, the location does not provide authentication for the account requesting access. Answer A is incorrect because security tokens (something you have) are commonly used for authentication. Answer C is incorrect because logon/password combinations (something you know) represent the most common single-factor authentication mechanism. Answers D and E are also incorrect because both something you do (such as handwriting analysis) and something you are (biometrics) represent authentication mechanisms that interact directly with the requesting user’s person.
4. B. Before access rights can be determined, a user must first be authenticated. Answers A and C are incorrect because authentication must precede access rights determination to avoid granting an unauthorized account access rights. Answer D is incorrect because the processes of authentication and access rights determination are not explicitly dependent on one another.
5. B. The Challenge-Handshake Authentication Protocol uses two compared values created using the MD5 hashing algorithm. Answer A is incorrect because biometric authentication relies on biological patterns rather than calculated values. Answers C and D are incorrect because Kerberos and mutual authentication schemes involve time-stamped ticket-based key or time-based random code exchange rather than an MD5 calculated value. Answer E is incorrect because a PKI solution involves the use of digital certificates rather than a calculated hashed value.
6. B, C, E, and F. These are all biometric authentication types. Answers A and D are incorrect because they are token authentication types.
7. E. A PKI solution involves an asymmetric encryption scheme in which a public key is used to encrypt data and a separate private key is used to decrypt the data. Answer A is incorrect because biometric identification relies on biological patterns and not encrypted values. Answers B and C are incorrect because both CHAP and Kerberos authentication involve the use of symmetric encryption schemes, in which the same key values are used to calculate or encrypt and decrypt data by both client and service. Answer D is incorrect because the username and password are simply available values and do not involve encryption.
8. D. A rule-based access control solution would allow detailed conditional testing of the user’s account type and the time of day and day of the week to allow or deny access. Answers A and B are incorrect because both solutions do not allow for conditional testing. Answer C is also incorrect because role-based access control involves testing against role-assigned access rights, rather than by other qualities such as a test for normal working hours.
9. A, B, C, D, and E. Any combination of authentication methods may be used in a multifactor solution. Multifactor authentication just refers to solutions including more than a single type of authentication.
10. D. In mutual authentication, both computers exchange calculated values and verify a returned code based on these. Answer A is incorrect because biometric authentication involves comparisons against stored biological values. Answer B is incorrect because CHAP is service demanded and does not provide verification back to the client that the service is also authentic. Answers C and E are incorrect because Kerberos and PKI authentication involve the exchange and comparison of keys or certificates issued by a third agent (the certificate authority) rather than by direct negotiation between the two systems.
11. B, C, and D. External motion detectors can be based on light, sound, infrared, or ultrasonic technology. Answer A is incorrect because radio-frequency identification (RFID) is an automatic identification method.
Additional Reading and Resources
1. Allen, Julia H. The CERT Guide to System and Network Security Practices. Addison-Wesley, 2001.
2. Krause, Micki and Harold F. Tipton. Information Security Management Handbook, Sixth Edition. Auerbach Publications, 2007.
3. SANS Top Twenty 2007 Security Risks: http://www.sans.org/top20/
