Chapter 7. Intrusion Detection and Security Baselines
Terms you need to understand
Techniques you need to master
![]() Understand the use of host-based and network-based IDS solutions and how they may be used together to secure a network.
Understand the use of host-based and network-based IDS solutions and how they may be used together to secure a network.
![]() Understand the purpose behind establishing security baselines.
Understand the purpose behind establishing security baselines.
![]() Recognize common considerations in planning for operating system, network, and application hardening.
Recognize common considerations in planning for operating system, network, and application hardening.
To secure a network, it is important to identify the normal operating parameters and be able to identify atypical variations from this baseline operational level. The first step toward minimizing the potential damage that may result from unauthorized access attempts is the detection and identification of an unauthorized intrusion.
Intrusion detection requires a detailed understanding of all operational aspects of the network, along with a means to identify variations and bring these changes to the attention of the proper responsible parties. In this chapter, you examine several forms of intrusion-detection solutions and review the requirements for establishing reasonable baseline standards.
Intrusion Detection
An intrusion includes any unauthorized resource access attempt within a secured network. Although it is possible for human monitoring to identify real-time intrusion events within small tightly controlled networks, it is more likely that a human administrator will monitor alerts and notifications generated by intrusion-detection systems (IDSs). These software and hardware agents monitor network traffic for patterns that may indicate an attempt at intrusion, called an attack signature, or may monitor server-side logs for improper activity or unauthorized access.
Both passive and active forms of IDS exist:
• A passive IDS solution is intended to detect an instrusion, log the event, and potentially raise some form of alert.
• An active IDS solution acts to terminate or deny an intrustion attempt by changing firewall or IPsec policy settings automatically before logging the event and raising an alert for human operators.
Both active and passive IDSs must first identify an intrusion before altering the network configuration (in an active system), logging the event, and raising an alert. The sections that follow examine some common mechanisms for intrusion detection.
Methods of Intrusion Detection
Intrusion detection may be managed by two basic methods: knowledge-based and behavior-based detection. Knowledge-based detection relies on the identification of known attack signatures and events that should never occur within a network. Behavior-based detection involves the use of established patterns of use and baseline operation to identify variations that may identify unauthorized access attempts.
Knowledge-Based IDS
The most common form of IDS detection involves knowledge-based (also termed signature-based) identification of improper, unauthorized, or incorrect access and use of network resources. Identification of known attack signatures allows for few false alarms; a known attack pattern is almost always a good sign of a danger to the network. Because the signature identifies a known method of attack, detailed planning may be made beforehand for countering and recovering from the attack.
Knowledge-based IDSs may also monitor for patterns of access that have been established as never being appropriate within the monitored network. An example of this might include communications directed at common ports used by services such as FTP or web servers running on workstation systems. Details of individual network transactions can be identified by examining the transacted data packets (also called “sniffing” the packets). Figure 7.1 illustrates data evaluation using a human-readable packet-sniffing application.
Figure 7.1. An example of packet-level identification of port and protocol access using the Ethereal packet sniffer.

Knowledge-based IDS has several limitations, including the following:
• Maintenance of the knowledge library to include newly identified signatures can become a complex and time-consuming task.
• Knowledge-based detection of internal misuse is difficult because most misuse involves an improper use of a normal form of access or priviledge.
• As new exploits are identified, it will take some time before an identified signature for the attack can be prepared and distributed. During this time, knowledge-based IDSs cannot identify attacks of the new type.
• Knowledge-based IDS is closely tied to the technologies in use within a particular network. As new technologies are integrated, or evolutionary changes are made to the network environment, knowledge-based systems may be unable to provide support for all potential avenues of attack created by the changes.
Behavior-Based IDS
One of the most common methods to detect a compromised workstation involves a user noticing an unusual pattern of behavior, such as a continually operating hard drive or a significantly slowed level of performance. Through the detection of anomalies from normal patterns of operation, it becomes possible to identify new threats that may bypass knowledge-based IDSs. Because this method detects anomalies, it is also called statistical anomaly detection. Highly secure environments might use complex patterns of behavior analysis, in some cases learning individual patterns of use common to each user profile, so that variations can be identified.
Behavior-based IDSs provide the following advantages over knowledge-based IDSs:
• Better able to identify new forms of vulnerability
• More flexible as network evolution occurs
• Can be used to identify internal misuse by recognizing actions outside of normal access patterns or authorized events occurring outside of normal profile usage, such as the access of protected files during off-hours
Although more flexible than knowledge-based intrusion detection, behavior-based detection has several limitations, including the following:
• High incidence of false alarms. Because anything falling outside of the established behavior profile is considered a potential sign of attack, any action that varies from the norm may generate an alert.
• Behavior profiles must be regularly updated to include changes in technology, network configuration, and changes to business practices that may affect the normal order of operations. In systems that maintain detailed user access profiles, even a simple promotion within the business structure might require administrative action to update the use profile of the user involved.
• Because behavior profiles must be periodically updated, behavior-based intrusion detection might not identify threats during the update cycle and might even identify an ongoing attack pattern as part of the normal pattern of use, creating a potential area for later exploitation.
Intrusion-Detection Sources
Whether knowledge-based or behavior-based, intrusion detection relies on the ability to monitor activity, identify potential risks, and alert the appropriate responsible parties. Monitoring might be performed on the network itself or on a host system, based on the security requirements mandated by business requirements.
Network-Based IDS
Network-based IDS (NIDS) solutions monitor all network traffic to identify signatures within the network packets that may indicate an attack, including the following:
• String signatures—Used to identify text strings that are used in common attacks, such as the code transmitted by Code Red infected systems
• Port signatures—Used to identify traffic directed to ports of common services not running on the identified host or on ports used by well-known exploits such as the Blade Runner and SubSeven Trojan horse services
• Header signatures—Used to detect the presence of conflicting or inappropriate packet headers, such as the SYN packets that might indicate a flood attack
NIDS solutions are designed to catch attacks in progress within the network, not just on individual machines or the boundary between private and public networks.
Table 7.1 details some of the strengths and weaknesses of NIDS solutions.
Table 7.1. Strengths and Weaknesses of NIDS Solutions

When deploying a NIDS, you must decide how many sensors you need and where to place them. When planning, you should consider the priority of each sensor and deploy accordingly within your budgetary or bandwidth constraints. Evaluate the organization’s business model and determine the importance of each server. Sensor placement should then be based on this determination. If a sensor is placed before the firewall, it tends to generate a lot of useless events that will have to be sorted through.
Host-Based IDS
Users often bring in outside devices that can easily affect the environment; many times, this is the port of entry for malware. In addition, one of the greatest threats to an organization is from trusted insiders. A host intrusion-detection system (HIDS) can help as a line of defense against this type of threat.
HIDS solutions involve processes running on a host and monitoring event and applications logs, port access, and other running processes to identify signatures or behaviors that indicate an attack or unauthorized access attempt. Some HIDS solutions involve the deployment of individual client applications on each host, which relay their findings to a central IDS server responsible for compiling the data to identify distributed trends.
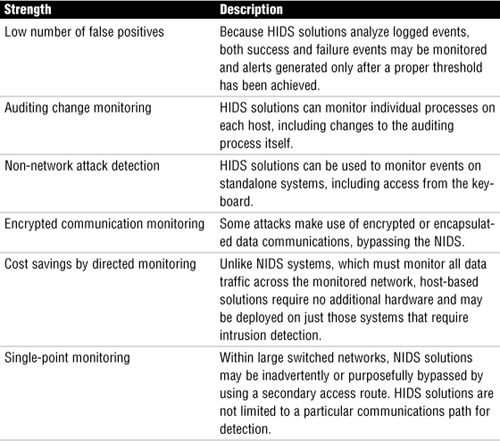
Table 7.2 details some of the strengths and weaknesses of HIDS solutions.
Table 7.2. Strengths and Weaknesses of HIDS

To plan the use of intrusion-detection systems for infrastructure protection, you need to be aware that the cost of implementation can depend on the size of your network and the number of individual computers to be monitored. In addition, the systems will require signature updates, and sometimes the system might incorrectly flag legitimate requests as security breaches or fail to detect something it should. These types of errors can be categorized as follows:
• False positive error—Occurs when the intrusion-detection system detects a legitimate action as a possible intrusion.
• False negative error—Occurs when the intrusion-detection system allows an intrusive action to pass as nonintrusive behavior.
• Subversion error—Occurs when the intrusion-detection system is modified by an intruder to cause false negatives or fooling the system over time by executing small individual steps that by themselves don’t mean much, but when combined can amount to an attack.
In most network deployment scenarios, a layered approach is required to provide protection against all forms of attack. User training, HIDS and NIDS solutions, and the hardening of services and systems to exclude known vulnerabilities will together form a unified solution to many developing security requirements.
Honeypots and Honeynets
Honeypots are often used to identify the level of aggressive attention directed at a network and to study and learn from an attacker’s common methods of attack. Honeypots are systems configured to simulate one or more services within an organization’s network and left exposed to network access. When attackers access a honeypot system, their activities are logged and monitored by other processes, so that the attacker’s actions and methods may be later reviewed in detail, while the honeypot distracts the attacker from valid network resources. Honeypots might be simple targets exposed for identification of vulnerability exposure, or might interact with the attacker to extend access time and allow tracking and logging of an attacker’s activities to build better attack profile data.
Honeynets are collections of honeypot systems interconnected to create functional-appearing networks that may be used to study an attacker’s behavior within the network. Honeynets make use of specialized software agents to create normal-seeming network traffic. Honeynets and honeypots may be used to distract attackers from valid network content, to study the attacker’s methods, and to provide early warning of attack attempts that may later be waged against the more secured portions of the network. Padded cells take a different approach. Instead of trying to attract attackers with tempting data, When an IDS detects an attacker, the attacker may then be transparently transferred to a padded cell host. This is a seamless transfer to a simulated environment, where harm cannot be done.
Incident Handling
When IDS solutions alert responsible parties to a successful or ongoing attack attempt, it is important to have previously established, documented plans for incident response. Several forms of response can be derived from analysis and identification of attack attempts, including the following:
• Deflection—Redirecting or misdirecting an attacker to secured segmented areas, allowing them to assume they have been successful, while preventing access to secured resources. Honeypots, padded cells and honeynets are examples of deflection solutions.
• Countermeasures—Intrusion-countermeasure equipment (ICE) may be used in some scenarios to provide automatic response in the event of intrustion detection. ICE agents may automatically lock down a network or increase access security to critical resources in the event of an alert; however, false positives could create problems for legitimate users in such a scenario.
• Detection—After identification of an attack, forensics analysis of affected systems can yield information that identifies the attacker. This information may then be used to direct the attention of the proper authorities to the source of the attack.
• Analysis—Collection and analysis of log files allows the identification of the type and methods of attack used and may provide details useful in identifying the attacker for law enforcement.
Later analysis of successful intrusions should be used to harden systems against later attempts that use the same methodology. Planning should include access restrictions and attempts to make the network appear less desirable to potential attackers.
Security Baselines
To identify atypical behavior, you must first identify what identifies typical behavior of both network and application processes. The measure of normal activity is known as a baseline. Baselines must be regularly updated as networks and deployed technology changes. Security monitoring during baselining is important because an ongoing attack during the baselining process could be registered as the normal level of activity. The sections that follow examine mechanisms for identifying vulnerabilities and hardening vulnerable systems revealed during this process.
Vulnerability Assessment
Metrics for security baselines and hardening efforts rely on identification of vulnerability and risk within the extended network enterprise. It is necessary to have some mechanism for measuring vulnerability to determine whether a baseline has been met or if a new security measure has been effective.
Dealing with Risk
An enterprise relies on the identification of key assets and resources, enumeration of the risk factors associated with each, and the requirements for each. Before any baseline can be established, beyond those developed by regulatory bodies outside of the business entity, a risk assessment must be conducted to identify existing risks and potential mitigation mechanisms.
A risk, once identified, can be dealt with in several ways:
• Accepted—Some risks cannot be addressed within a reasonable time or cost constraint and may be accepted, along with proper documentation as to the reasons why the risk is acceptable.
• Transferred—A risk may be transferred, such as when the risk of equipment loss is covered by a full-replacement insurance policy.
• Eliminated—Some risks can be eliminated through a change in the technology, policy, or mechanism of employment. For example, the risk of “war dialing” attacks can be eliminated by removing legacy dial-up telephony modem devices.
• Mitigated—Most risks fall into this response area, where the application of additional effort may reduce the risk to a level documented as acceptable.
Identifying Vulnerability
Many risks to enterprise networks relate to vulnerabilities present in system and service configurations and to network and user logon weaknesses. For the exam, you should be familiar with some of the more common tools used to conduct vulnerability assessments, including the following:
• Port scanners—This software utility will scan a single machine or a range of IP addresses, checking for a response on service ports. A response on port 80, for example, may reveal the operation of an HTTP host. Port scanners are useful in creating an inventory of services hosted on networked systems. When applied to test ports on a single system, this is termed a port scan, whereas a scan across multiple hosts is referred to as a port sweep.
• Vulnerability scanners—This software utility will scan a range of IP addresses, testing for the presence of known vulnerabilities in software configuration and accessible services. Unlike port scanners, which only test for the availability of services, vulnerability scanners may check for the particular version or patch level of a service to determine its level of vulnerability.
• Protocol analyzers—This software utility is used on a hub, a switch supervisory port, or in line with network connectivity to allow the analysis of network communications. Individual protocols, specific endpoints, or sequential access attempts may be identified using this utility, which is often referred to as a packet sniffer.
• Network mappers—Another software utility used to conduct network assessments over a range of IP addresses, the network mapper compiles a listing of all systems, devices, and network hardware present within a network segement. This information can be used to identify simple points of failure, to conduct a network inventory, and to create graphical details suitable for reporting on network configurations.
• Password crackers—This software utility allows direct testing of user logon password strength by conducting a brute-force password test using dictionary terms, specialized lexicons, or mandatory complexity guidelines. Password crackers should provide only the relative strength of a password, rather than the password itself, to avoid weakening logon responsibility under evidentiary discovery actions.
Penetration Testing
In some cases, vulnerability assessments may be complemented by directed efforts to exploit vulnerabilities in an attempt to gain access to networked resources. These are, in essence, “friendly” attacks against a network to test the security measures put into place. Such attacks are referred to a penetration tests or simply pen tests, and may cause some disruption to network operations as a result of the actual penetration efforts conducted. Penetration tests can also mask legitimate attacks by generating false data in IDS systems, concealing aggression that is otherwise unrelated to the offically sanctioned penetration test. Some tools use passive OS fingerprinting. A passive attack attempts to passively monitor data being sent between two parties, and does not insert data into the data stream.
Hardening
When establishing operational baselines, it is important to harden all technologies against as many possible avenues of attack as possible. The three basic areas of hardening are
• Operating system—Security of the operating system, including domain architecture and user logon access planning
• Network—Security of the network through hardware implementations such as firewall and NAT devices and logical security involving access control over distributed resources
• Application—Security of applications and services such as domain name system (DNS), Dynamic Host Configuration Protocol (DHCP), and Web servers, and user client-side applications and integration suites
The following sections describe each area of hardening in greater detail.
Operating System Hardening
Hardening of the operating system includes planning against both accidental and directed attacks, such as the use of fault-tolerant hardware and software solutions. In addition, it is important to implement an effective system for file-level security, including encrypted file support and secured file system selection that allows the proper level of access control. For example, the Microsoft New Technology File System (NTFS) allows file-level access control, whereas most File Allocation Table (FAT)-based file systems allow only share-level access control.
It is also imperative to include regular update reviews for all deployed operating systems, to address newly identified exploits and apply security patches, hotfixes, and service packs. Many automated attacks make use of common vulnerabilities, often ones for which patches and hotfixes are already available but not yet applied. Failure to update applications on a regular basis or to update auditing can result in an unsecure solution that provides an attacker access to additional resources throughout an organization’s network.
IP Security (IPsec) and public key infrastructure (PKI) implementations must also be properly configured and updated to maintain key and ticket stores. Some systems may be hardened to include specific levels of access, gaining the C2 security rating required by many government deployment scenarios. (Mentioned in Chapter 5, “Access Control and Authentication Basics,” the Trusted Computer System Evaluation Criteria (TCSEC) rating of C2 indicates a discretionary access control environment with additional requirements such as individual logon accounts and access logging.)
Operating system hardening includes configuring log files and auditing, changing default administrator account names and default passwords, and the institution of account lockout and password policies to guarantee strong passwords that can resist brute-force attacks. File-level security and access control mechanisms serve to isolate access attempts within the operating system environment. Make sure to understand the principle of least privilege addressed in Chapter 5.
Network Hardening
Network hardening involves access restrictions to network shares and services, updates to security hardware and software, and disabling unnecessary protocol support and services. In homogenous networks, it might be possible to terminate support for AppleTalk, IPX/SPX, or other forms of unused network communications protocols. Firewall and Network Address Translation (NAT) software and hardware solutions will provide the first layer of defense against unauthorized access attempts. Ensuring updates to system firmware also helps to address emergent hardware-related vulnerabilities.
Mapping avenues of access is critical in hardening a network. This process is a part of the site survey that should be performed for any network, especially those that involve public areas where a simple connection through a workstation might link the protected internal network directly to a public broadband connection. Wireless networks also create significant avenues for unsecure access to a secured network. A user who configures a PC card on his workstation to allow synchronization of their 802.11-compliant wireless PDA may have inadvertently bypassed all security surrounding an organization’s network.
As with operating system hardening, default configurations and passwords must be changed in network hardware such as routers and managed network devices. Routing hardware must also be maintained in a current state by regularly reviewing applied firmware updates and applying those that are required for the network configuration and hardware solutions in use.
If a centralized access control system is used, such as those found in Windows and Novell networks, resource access and restrictions may be assigned to groups, and users granted membership to those groups. By properly configuring access control lists, resource access may be made to authorized parties while also limiting potential avenues of unauthorized access.
Network hardening practices also include configuring network devices and firewalls to exclude unsecure protocols, such as raw Telnet sessions that transfer logon and session details in plain-text format.
Application Hardening
Each application and service that may be installed within a network must also be considered when planning security for an organization. Applications must be maintained in an updated state through the regular review of hotfixes, patches, and service packs. Many applications, such as antivirus software, require regular updates to provide protection against newly emerging threats. Default application administration accounts, standard passwords, and common services installed by default should also be reviewed and changed or disabled as required.
Web Services
Access restrictions to Internet and intranet web services may be required to ensure proper authentication for nonpublic sites, while anonymous access may be required for other pages. Access control may be accomplished at the operating system or application level, with many sites including a requirement for regular update of Secure Sockets Layer (SSL) certifications for secured communications.
Regular log review is critical for web servers, to ensure that submitted URL values are not used to exploit unpatched buffer overruns or to initiate other forms of common exploits. Many web servers may also be integrated with security add-ins provided to restrict those URLs that may be meaningfully submitted, filtering out any that do not meet the defined criteria. Microsoft’s URLScan for the Internet Information Services (IIS) web service is one such filtering add-in.
Email Services
Email servers require network access to transfer Simple Mail Transfer Protocol (SMTP) traffic. Email is often used to transport executable agents, including Trojan horses and other forms of viral software. Email servers may require transport through firewall solutions to allow remote Post Office Protocol 3 (POP3) or Internet Message Access Protocol (IMAP) access or may require integration with VPN solutions to provide secure connections for remote users. User authentication is also of key importance, especially when email and calendaring solutions allow delegated review and manipulation. Inadequate hardware may be attacked through mail bombs and other types of attack meant to overwhelm the server’s ability to transact mail messages. Email service hardening also includes preventing SMTP relay from being used by spammers and limiting attachment and total storage per user to prevent denial-of-service attacks using large file attachments.
FTP Services
File Transfer Protocol (FTP) servers are used to provide file upload and download to users, whether through anonymous or authenticated connection. Because of limitations in the protocol, unless an encapsulation scheme is used between the client and host systems, the logon and password details are passed in clear text and may be subject to interception by packet sniffing. Unauthorized parties may also use FTP servers that allow anonymous access to share files of questionable or undesirable content, while also consuming network bandwidth and server processing resources.
DNS Services
DNS servers responsible for name resolution may be subject to many forms of attack, including attempts at DoS attacks intended to prevent proper name resolution for key corporate holdings. Planning to harden DNS server solutions should include redundant hardware and software solutions and regular backups to protect against loss of name registrations. Technologies that allow dynamic updates must also include access control and authentication to ensure that registrations are valid. Unauthorized zone transfers should also be restricted to prevent DNS poisoning attacks.
NNTP Services
Network News Transfer Protocol (NNTP) servers providing user access to newsgroup posts raise many of the same security considerations risks as email servers. Access control for newsgroups may be somewhat more complex, with moderated groups allowing public anonymous submission (and authenticated access required for post approval). Heavily loaded servers may be attacked to perform a DoS, and detailed user account information in public newsgroup posting stores like those of the AOL and MSN communities may be exploited in many ways.
File and Print Services
User file-storage solutions often come under attack when unauthorized access attempts provide avenues for manipulation. Files may be corrupted, modified, deleted, or manipulated in many other ways. Access control through proper restriction of file and share permissions is necessary, coupled with access auditing and user authentication schemes to ensure proper access. Network file shares are not secure until you remove default access permissions.
Distributed file system and encrypted file system solutions may require bandwidth planning and proper user authentication to allow even basic access. Security planning for these solutions may also include placing user access authenticating servers close to the file servers to decrease delays created by authentication traffic.
Print servers also pose several risks, including possible security breaches in the event that unauthorized parties access cached print jobs. DoS attacks may be used to disrupt normal methods of business, and network-connected printers require authentication of access to prevent attackers from generating printed memos, invoices, or any other manner of printed materials.
DHCP Services
Dynamic Host Configuration Protocol (DHCP) servers share many of the same security problems associated with other network services, such as DNS servers. DHCP servers may be overwhelmed by lease requests if bandwidth and processing resources are insufficient. This can be worsened by the use of DHCP proxy systems relaying lease requests from widely deployed subnets. Scope address pools may also be overcome if lease duration is insufficient, and short lease duration may increase request traffic. If the operating system in use does not support DHCP server authentication, attackers may also configure their own DHCP servers within a subnet, taking control of the network settings of clients and obtaining leases from these rogue servers. Planning for DHCP security must include regular review of networks for unauthorized DHCP servers.
Data Repositories
Data repositories of any type might require specialized security considerations, based on the bandwidth and processing resources required to prevent DoS attacks, removal of default password and administration accounts such as the SQL default sa account and security of replication traffic to prevent exposure of access credentials to packet sniffing. Placement of authentication, name resolution, and data stores within secured and partially secured zones such as an organization’s DMZ may require the use of secured VPN connections or the establishment of highly secured bastion hosts. Role-based access control may be used to improve security, and the elimination of unneeded connection libraries and character sets may help to alleviate common exploits.
Take care to include data repositories beyond the obvious file, email, and database stores. Hardening efforts must also address security of the storage and backup of storage area networks (SANs), network access server (NAS) configurations, and directory services such as Microsoft Active Directory and Novell eDirectory.
Exam Prep Questions
1. Which of the following IDS forms uses known attack signatures to identify unauthorized access attempts?
![]() A. Knowledge-based IDS
A. Knowledge-based IDS
![]() B. Behavior-based IDS
B. Behavior-based IDS
![]() C. Network-based IDS
C. Network-based IDS
2. Which of the following IDS forms is subject to common false-positive attack indications?
![]() A. Knowledge-based IDS
A. Knowledge-based IDS
![]() B. Behavior-based IDS
B. Behavior-based IDS
![]() C. Network-based IDS
C. Network-based IDS
![]() D. Host-based IDS
D. Host-based IDS
3. A denial-of-service attack is being waged against the company’s web server using a large external botnet. Which of the following IDS solutions could enhance the attack’s effect?
![]() A. Host-based
A. Host-based
![]() B. Application protocol-based
B. Application protocol-based
![]() C. Behavior-based
C. Behavior-based
![]() D. Network-based
D. Network-based
4. Which of the following IDS forms are relatively platform independent? (Select two correct answers.)
![]() A. Knowledge-based IDS
A. Knowledge-based IDS
![]() B. Behavior-based IDS
B. Behavior-based IDS
![]() C. Network-based IDS
C. Network-based IDS
![]() D. Host-based IDS
D. Host-based IDS
5. You have deployed a packet-monitoring system to sniff packets passing through an organization’s DMZ. Which of the following types of IDS is this solution?
![]() A. Knowledge-based IDS
A. Knowledge-based IDS
![]() B. Behavior-based IDS
B. Behavior-based IDS
![]() C. Network-based IDS
C. Network-based IDS
![]() D. Host-based IDS
D. Host-based IDS
6. You have installed a custom monitoring service on the web server that reviews web service logs to watch for the URLs used by the Code Red worm to propagate itself. When this custom service detects an attack, it raises an alert via email. Which of the following types of IDS is this solution? (Select two correct answers.)
![]() A. Knowledge-based IDS
A. Knowledge-based IDS
![]() B. Behavior-based IDS
B. Behavior-based IDS
![]() C. Network-based IDS
C. Network-based IDS
![]() D. Host-based IDS
D. Host-based IDS
7. Which of the following describes a host configured to expose a specific service to a public network, while hardening all other resource access to restrict access within an organization’s secure network?
![]() A. Honeypot
A. Honeypot
![]() B. Honeynet
B. Honeynet
![]() C. Bastion
C. Bastion
![]() D. War driving
D. War driving
8. Acquiring insurance to cover the costs of potential lost data is an example of which risk-management strategy?
![]() A. Accepting the risk
A. Accepting the risk
![]() B. Eliminating the risk
B. Eliminating the risk
![]() C. Mitigating the risk
C. Mitigating the risk
![]() D. Transferring the risk
D. Transferring the risk
9. You have configured your web server to use Windows partitions and the Microsoft System Update Service (SUS) to regularly apply new hotfixes and patches. Which of the follow forms of hardening is specified in this solution?
![]() A. Application
A. Application
![]() B. Baseline
B. Baseline
![]() C. Operating system
C. Operating system
![]() D. Network
D. Network
10. Which of the following servers may be overcome by a denial-of-service type of attack? (Select all that apply.)
![]() A. Web servers
A. Web servers
![]() B. FTP servers
B. FTP servers
![]() C. DNS servers
C. DNS servers
![]() D. NNTP servers
D. NNTP servers
![]() E. DNS servers
E. DNS servers
Answers to Exam Prep Questions
1. A. Knowledge-based IDS solutions use known attack signatures to identify network attacks. Answer B is incorrect because behavior-based IDS solutions measure access patterns against known baselines to identify attacks. Answers C and D are incorrect because either might include knowledge-based or behavior-based IDS solutions, and so neither is the best answer here.
2. B. Behavior-based IDS solutions measure patterns of access against known security baselines. As a result, any variation from the previous baseline may be detected as a possible attack. Answer A is incorrect because knowledge-based IDS solutions use known attack signatures to identify attacks and so are not often subject to false positives. Answers C and D are incorrect because either might include knowledge-based or behavior-based IDS solutions, and so neither is the best answer here.
3. A. Because host-based IDS solutions use the same resources that are being attacked, they can enhance denial-of-service attempts by consuming additional resources for each identified intrusion event. Answer B is incorrect because an application protocol-based detection system would generally operate away from the web server itself, residing in the middleware layer to monitor protocol use between service elements. Answer C is incorrect because any of the solutions may be behavior-based, and it is likely that the successful identification of a DoS attack would be behavior-based. Answer D is incorrect because a NIDS solution would not impact the service or resource performance of the separate host under attack.
4. B, C. Behavior-based IDS solutions and network-based solutions operate on patterns of access and data packet transfer to identify attacks. As a result, both can evolve to meet changes in network technologies in use. Answers A and D are incorrect because knowledge-based IDS solutions must be able to identify known attack signatures directed at the protected technologies, and host-based IDS solutions involve client agents running on the monitored hosts, and so both are strongly affected by changes to the protected technologies.
5. C. This is a common NIDS solution, where packet data is monitored for unauthorized access patterns. Answers A and B are incorrect because the proposed solution might make use of either knowledge-based or behavior-based IDS, and so neither is the best answer here. Answer D is incorrect because a HIDS solution would use client agents operating on the monitored hosts rather than sniffing the network traffic.
6. A, D. This solution describes a host-based solution identifying a known attack signature. Answer B is incorrect because no baselining is required for this solution. Answer C is incorrect because the agent does not attempt to capture packet data; it only reviews the web service logs on the local system.
7. C. A bastion host exposes a service or port while protecting against other forms of exploit. Answers A and B are incorrect because honeypots and honeynets are used to distract attackers or to monitor their access methods. Answer D is incorrect because war driving refers to driving around with a wireless card in promiscuous mode, attempting to detect open wireless access points.
8. D. Obtaining insurance to cover the cost of a potential exposure is an example of transferring an identified risk without reduction. Answer A is incorrect because the risk has not simply been accepted. Answer B is incorrect because the risk remains; only the costs have been addressed by this solution. Answer C is incorrect because the level of risk remains the same.
9. C. Selecting a secure file system such as NTFS and regularly applying operating system updates are examples of operating system hardening. Answer A is incorrect because application hardening involves the security of user applications and services. Answer D is incorrect because network hardening involves the security of network access. Answer B is incorrect because a baseline establishes the normal operating levels of a network and is not itself hardened.
10. A, B, C, D, and E. All of these services may be overcome by a DoS attack if the attacker can overload the available processing and bandwidth resources available to each. When multiple services are loaded onto a single system, this problem can be compounded.
Additional Reading and Resources
1. Jones, Andy and Debi Ashenden. Risk Management for Computer Security: Protecting Your Network and Information Assets. Butterworth-Heinemann, 2005.
2. Stein, Lincoln D. and John N. Stewart. The World Wide Web Security FAQ: http://www.w3.org/Security/Faq/
3. SANS Information Security Reading Room: http://www.sans.org/reading_room/
4. CERT Incident Reporting Guidelines: http://www.cert.org/tech_tips/incident_reporting.html
5. US-CERT OVAL: http://www.us-cert.gov/oval.html
