
When you share files with others or connect your iMac to the Internet or a network, you expose it to threats. To keep your iMac and your data safe, you must understand these threats, install and use antivirus software, turn off automatic login, and set up the Mac OS X firewall.
Understanding Threats to Your iMac and Your Data 312
Install Antivirus Software 314
Scan Your iMac for Viruses 316
Turn Off Automatic Login 318
Increase the Security of the Mac OS X Firewall 320
Recognize and Avoid Phishing Attacks 322
To keep your iMac and your data safe, you should understand the main threats they face. These threats range from malevolent software to people accessing your iMac without permission, from deliberate attacks to accidental data corruption or hard-disk failure.

Viruses and Malevolent Software
Just as you expose yourself to viruses and bacteria in public, so you expose your iMac to computer viruses and malevolent software when you use the Internet or share files. Viruses and malevolent software can delete your data or corrupt your iMac's operating system or applications, so you must protect the iMac with antivirus software.

Unauthorized People Accessing Your iMac
Anyone who can log in to your iMac in person or across the Internet can attack your data. For example, an intruder can copy your files, steal them, or simply delete them. To ensure that each user must log in to the iMac, always log out when you have finished using the computer, and turn off automatic login.

When your iMac is connected to a network or the Internet, it needs protection from possible attacks from other computers. Mac OS X includes a powerful firewall that can protect your iMac against many threats, but you may need to turn it on and change its configuration to enjoy full protection.

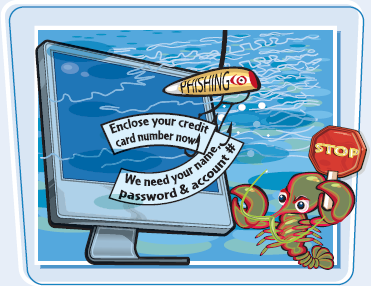
Be on your guard against phishing attacks, attacks in which a phisher attempts to make you divulge valuable information such as bank account login names, passwords, or credit card numbers. Most phishing takes place via e-mail, but phishers also use instant messaging and telephones to persuade people to give up information against their interests.
Power Outages and Hardware Failures
To protect your iMac from power outages or electric surges, give it power through an uninterruptible power supply (UPS) or a surge suppressor instead of directly from a socket. A UPS uses a battery to provide steady, conditioned power to your iMac and enable you to save files and shut down when a power outage occurs. To protect your data against hardware failure, back up your data as explained in Chapter 15.

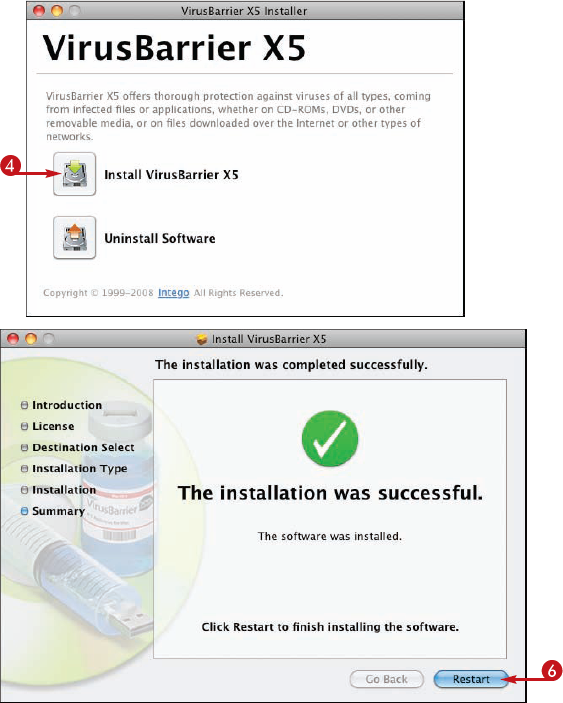
Malevolent hackers on the Internet target Macs as well as Windows PCs, so you must protect your iMac by installing and running antivirus software. This section shows you how to install VirusBarrier, a widely used antivirus package, and keep it updated.

Install Antivirus Software

Note
If you have an Internet connection, buy your antivirus software online and download it. That way, you get the latest version.





After the restart, the antivirus software runs automatically to protect your iMac.
Keep Your Antivirus Software Up-to-Date


A dialog opens telling you whether updates are available.

The dialog closes.
If updates are available, the NetUpdate window shows the updates in boldface.


NetUpdate downloads and installs the updates.


Tip
Which antivirus software shall I get for my iMac?
Widely used antivirus software includes VirusBarrier from Intego and Norton Antivirus for Mac or Norton Internet Security for Mac from Symantec. Intego offers a 30-day trial version of VirusBarrier, so you can evaluate the software before you buy it. If you prefer not to pay and are prepared to put a little more effort into setup, look at ClamXav (www.clamxav.com).

What features should I look for in antivirus software?
The main feature to look for is protection against malevolent software. This includes viruses, Trojan-horse programs that hide harm in a program that seems helpful, and rootkits, which try to build secret entry points into your computer. Protection against spyware programs, phishing messages, and infected Web sites are useful too.

After installing antivirus software as described on the previous two pages, you should run a full scan of your Mac. This section shows you how to run a scan using VirusBarrier from Intego.

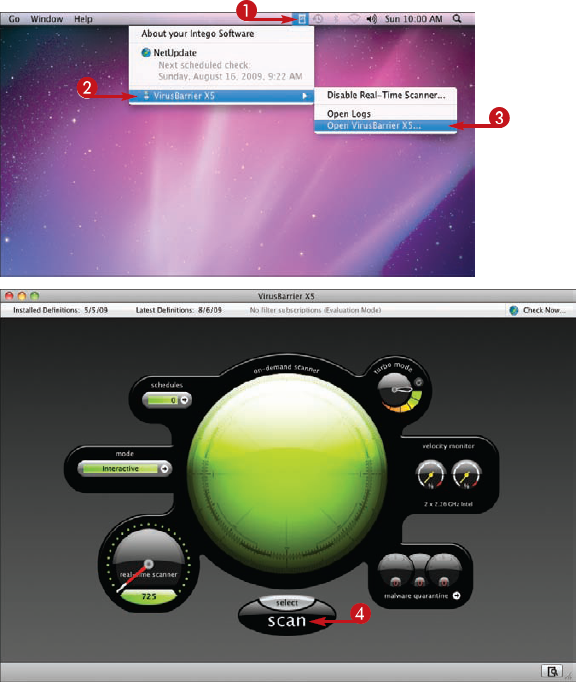
Scan Your iMac for Viruses


The submenu opens.

The VirusBarrier X5 window opens.

VirusBarrier counts the files and then scans them.
The green light indicates all is well.
The light turns red when VirusBarrier finds an infected file.
A VirusBarrier dialog opens showing a list of infected files.






After you click a button, VirusBarrier removes the file from the list.
When you have dealt with all the infected files, the dialog closes.


Tip
What happens when I place an infected file in quarantine?
Placing a file in quarantine puts it in a secure area so that you can review it later. Quarantine prevents the infected file from damaging your iMac but does not remove the infection. Click Malware Quarantine to open the quarantine area. Click the file you want to deal with and click the appropriate action button: Repair, Scan, Consider Safe, or Delete from Disk.

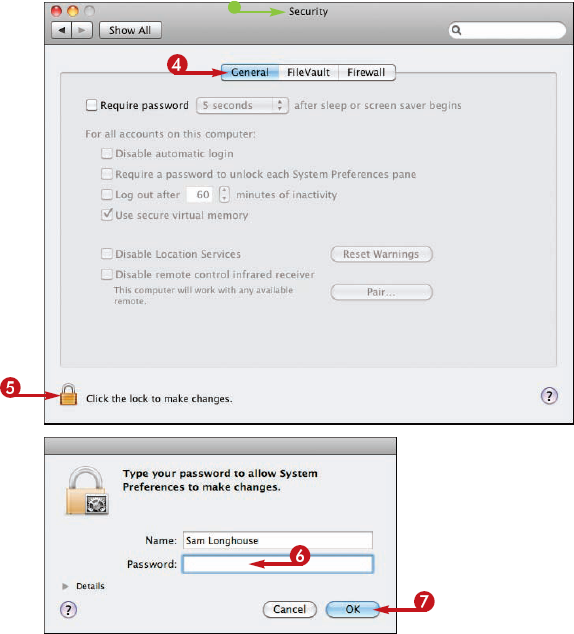
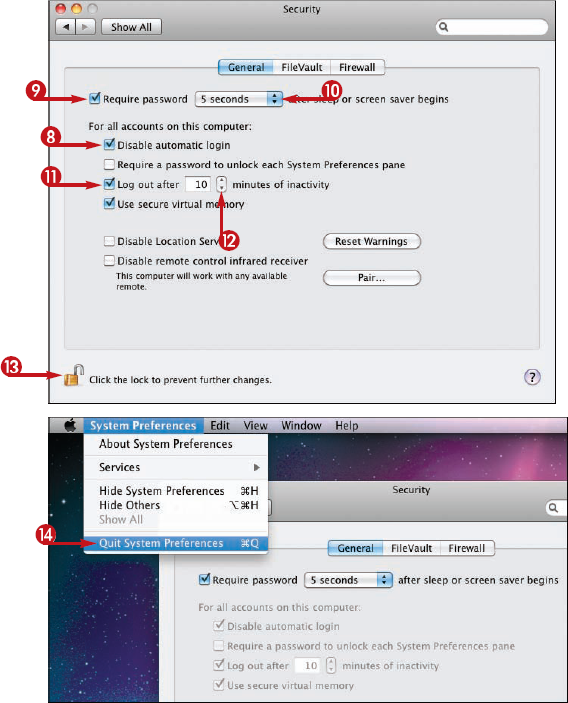
When you install Mac OS X from scratch, Installer sets up your iMac with automatic login for the administrator account you first create. Automatic login is convenient when you are the only person who uses your iMac, but you can make your iMac more secure by turning off automatic login so each user must log in.


The Apple menu opens.

The System Preferences window opens.



The General pane appears.

The Authenticate dialog opens.


The Authenticate dialog closes.
Mac OS X enables the preferences (








Tip
Are there other options for tightening my iMac's security?
In Accounts preferences, click Login Options. You can then click Name and password (

A firewall protects your iMac from unauthorized access by other computers on your network or on the Internet. Your Internet router likely has its own firewall to keep Internet threats out of your network, but Mac OS X also includes a built-in firewall to give your iMac even greater protection.

Increase the Security of the Mac OS X Firewall

The Apple menu opens.

The System Preferences window opens.



The Firewall pane appears.

The Authenticate dialog opens.


The Authenticate dialog closes.


The firewall starts, and "Firewall: On" appears.

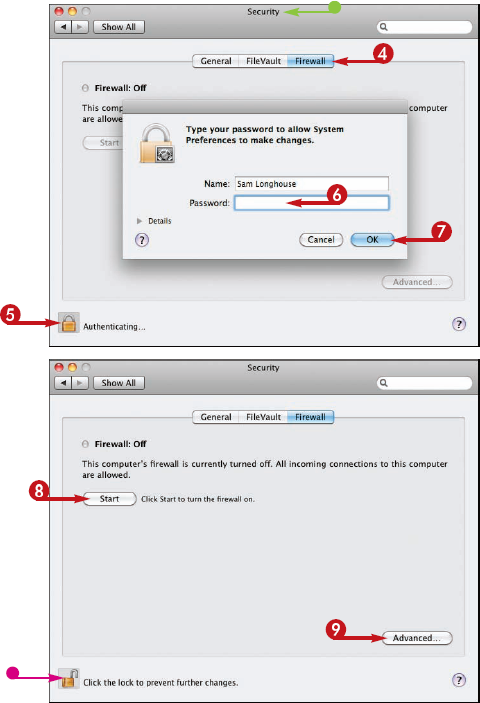





Mac OS X adds the application to the list.





Tip
When should I use the Block all incoming connections option?
Click Block all incoming connections when you need to tighten security as much as possible. The usual reason for blocking all connections is connecting your iMac to a network that you cannot trust, such as a public wireless network. This option is more widely used with MacBooks than with desktop Macs.
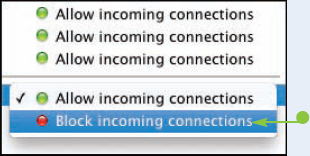
Can I block incoming connections only to a specific application?
To block incoming connections only to a specific application, add that application to the list in the Advanced dialog as described on this page. Then click the application's Allow incoming connections button in the list and click Block incoming connections (
Phishing is an attack in which someone tries to make you provide valuable information such as bank account login names, passwords, or credit card numbers. After acquiring this information, the phisher either uses it directly — for example, withdrawing money from your bank account — or sells it to criminals.

Recognize and Avoid Phishing Attacks
Recognize a Phishing E-mail Message







Note
Phishers frequently target eBay customers. Genuine eBay messages always address you by your member name and include the actual name you have given eBay.



Connect Securely to a Web Site

A Safari window opens.


Safari opens the Web site.

Note
Safari displays the padlock icon when you have connected securely to a Web site. The address of a secure connections starts with https:// rather than http://.
A dialog opens showing the details of the digital certificate that identifies the Web site.





Tip
Is it possible to make a secure connection to a dangerous Web site?
Yes. The padlock icon means only that the connection between your iMac and the Web site server is secure and cannot be read in transmission. The Web site may be safe or it may be dangerous; it is up to you to establish which.

Is a message definitely genuine if it includes my name?
Even if a message includes your name, be alert for other signs of phishing. Some phishers send customized phishing messages in the hope of ensnaring particular high-value victims. This technique is called spear-phishing. Evaluate the message's content for sense and likelihood, and remember that anything too good to be true is usually not true.

