In This Chapter
Surprising places to look for evidence
Tools for extracting evidence from nonstandard devices
The future of data storage
You probably don't realize just how much computers have changed the way you live. Few activities you perform during the course of your day do not have some form of electronic footprint somehow associated with them. Unless you shun electronic devices and electricity in general, chances are good that a generous portion of your activities can be re-created by someone who has the right equipment and motivation.
Your digital alarm clock and electricity meter indicate exactly when you wake up, your computer logs the information you look up and when, and your home security system records when you leave or enter your house. Your car indicates how fast you drive, how many miles per gallon your car reaches, how far you can go until you run out of gas, and your GPS location. A computer cash register logs your debit card transaction, as does your bank's computer. Cameras located on the roadway record the time you pass by; if you use a toll road, your wireless toll card dutifully deducts the correct amount from your account.
In this chapter, we take a look at all the places you can extract forensic evidence.
The days of using a tape cassette for answering machines have mostly gone the way of the dodo bird (a few people still use them). To analyze a digital answering machines with no tape cassette, you had to access the storage microchips or recording audio from the speakers or by way of replay. Both extraction methods left something to be desired.
A modern-day answering machine is nothing more than a digital audio recorder connected to a phone line with telephone functionality.
These modern-day answering machines are shipped with USB connections so that your computer can access the storage area of the answering machine to store or retrieve messages.
Because the typical USB-enabled answering machine is considered a storage device by your desktop computer, the use of an answering machine to hide data isn't so far-fetched. As the forensic examiner, you can now use the FTK or EnCase forensic tool to acquire and image the answering machine just like you would with a regular computer storage device. One key marker to look for on the desktop computer is one or more link files that point to another storage device. If you see link files on the suspect computer and notice an answering machine sitting close by, it may be time to examine that answering machine a bit closer. Link files are covered in much more detail in Chapter 11.
Home entertainment digital video recorder (DVR) equipment can track the programs you watch, but the real reason to examine DVR equipment is that it can store files as an external hard drive to your desktop computer.
DVR technology isn't used only in convenience stores but also in camera systems on roadways, hotels, restaurants, airports, railway stations, bridges, supermarkets, schools, and just about any other place where people visit or congregate.
Most camera storage devices are now digital, and you can extract data from them. Figure 14-1 shows a standard DVR device that is essentially a computer dedicated to video recording. The video is saved in a readable format by the DVR, which allows the user to save and play back the video recordings.
Most DVR devices use a storage device to save the video files, and you can image the storage devices in the same way you image regular desktop computer storage devices.
You can extract information from a DVR in two ways:
If you're lucky: The video formats are fairly standard (such as AVI or MPEG) and you can play the video on any standard video player.
If you aren't so lucky: If you're working with a proprietary format, the best option is to clone the original storage device and use the cloned storage device to use the device's own player or similar model to view the videos without risking damage to the original storage device.
Note
Always check with the manufacturer to see what action it recommends. It might even have software to help you view or extract the video.
The newest version of EnCase can now interpret TiVo file systems 1 and 2.
Most home security systems rely on a small computer system with a minimal operating system and few hardware resources (similar to a mobile phone). These systems use storage spaces to store logs, security codes, and configuration settings. If the system is capable, the logging function can show activation and deactivation of the system and indicate which code was used. If each person uses a separate code, you can easily figure out who accessed the alarm system.
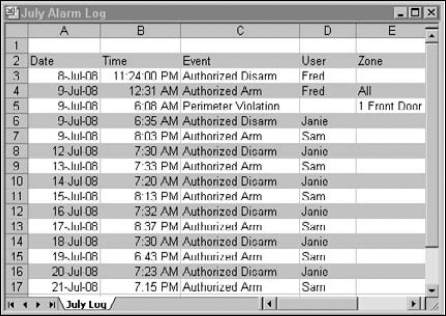
Home security systems can also be programmed to remotely perform a number of tasks, such as activate and deactivate at certain time intervals, create new codes, and even shut down certain zones while leaving others on. You can see these types of activity if you view the logs, but you have to know to look there. When you run across a crime scene that indicates no forced entry or tripping of the alarm, one of your first stops must be the alarm system logs to see what happened. The results may answer a few questions or, at worst, create more! Figure 14-2 shows some typical information that can be extracted from alarm system logs. Most alarm panels have a menu system from which you can view events on the system panel and other, more sophisticated alarm panels can download the information to your computer. Check with the alarm manufacturer to see whether the alarm panel you're working with can download log data.
Note
If the security system is monitored or connected to a central alarm company, the possibility of your finding data increases dramatically because the security system is connected to systems with logging and recording capability. Additionally, some alarm systems have built-in speakers and microphones so that the operators can communicate with you, which means that they can listen and record whatever information is transmitted over that microphone, especially if the alarm has been tripped.
With the advent of GPS technology, tracking a vehicle has never been easier. In case after case, law enforcement has used GPS technology to catch people who aren't exactly telling the truth. The conversation goes something like this:
Police officer: Where were you on the night of July 5, 2008 at 9 p.m.?
Suspect: I was at Leo's Bar on 5th Street.
Police officer: That's funny because your car was parked outside City National Bank on the other side of town while the bank was being robbed at that time.
GPS technology is rather simple in concept: A receiver uses satellite signals to establish a car's position to within several meters. The implementation becomes a bit more complex, though when you add satellites, atmospheric interference, and multipath effects (radio waves essentially bouncing off big objects and throwing off the GPS calculations). The system relies on a group of 24 orbiting satellites.
This capability ensures that a trusted third party can verify, with reasonable accuracy, exactly where that receiver was and at what time. You can find out exactly where a particular car was at a particular time.
GPS devices are available in two different forms:
Handheld or dashboard-mounted unit: Can be purchased at your local shopping mall or sporting goods store. The most popular consumer GPS brand is now Garmin, shown in Figure 14-3. This device is usually the size of a paperback book or mobile phone.
Original equipment manufacturer (OEM) unit: Usually embedded in vehicles, truck fleets, aircraft, and many other applications by the manufacturer. An OEM-type GPS receiver is shown in Figure 14-4. This device is typically about the size of a large mailing stamp.
If the times and locations on the GPS receiver don't comprise enough information to satisfy an investigator, the newest GPS devices are capable of data storage, have MP3 players built in, and interface or pair with mobile phones by way of Bluetooth or direct connection.
With all this information on the GPS device and the ability to connect by way of USB or Bluetooth, you can forensically acquire and image GPS devices quite easily to extract useful data. Because desktop computers consider the devices to be storage devices, the forensic process works the same way as imaging a desktop computer or mobile phone. If you're dealing with a GPS device paired with a mobile phone, the type of information passed to the GPS can include call lists, text messages, and even phone book data, which links the GPS with the user of the mobile phone and vice versa.
In radio frequency identification (RFID), very small and very low-power transmitters are used to interface with a type of receiver or interrogator to identify a person or an object. In its simplest form, the RFID transmitter sends a radio frequency signal encoded with an identification number that is then received by the RFID reader or receiver. After the reader receives the encoded signal, the reader converts the signal to digital and passes it along to whichever process or device it's connected to.
Most people have heard of RFID technology in the context of supermarket inventory control; however, RFID technology is finding its way into many other areas, such as
Fuel stations: Just drive right up, wave your RFID card at the pump, and start pumping fuel.
Vending machines: Using your RFID debit card or key fob, you can pluck a snack or a drink from a vending machine and it deducts the cost directly from your bank account.
Supermarket checkout lines: After the cost of all your groceries is totaled, you just tap the RFID card on the reader and your transaction is complete.
Your pets: Implant RFID technology into Fluffy or Rover, and easily identify the pet if later it gets lost or stolen. People with high-value animals are literally flocking (no pun intended) to this technology because it makes identifying stolen or lost animals so easy.
Casinos: RFID in betting chips lets casinos track them on the floor and study customer betting habits.
Identification systems: RFID tags are being inserted into all forms of identification systems, such as employee badges, passports, student badges, and even human beings.
In every case of RFID, the technology is designed to leave a digital trail. From the forensic point of view, you can re-create the movements and actions of a person by simply extracting this information from the RFID reader or interrogator. For example, a casino using RFID chips can literally track a chip's movement and track whoever is carrying that chip from table to table to re-create that journey based on the data that's stored. Another example often touted by security firms is the ability to watch security guards make their rounds in real time as the RFID tags sequentially check in at predetermined points!
Warning
Because the RFID system involves the use of radio frequency waves, anyone with the right type of receiver can intercept RFID signals. Also, RFID cloning devices already exist, so just because the data shows that the RFID device was nearby at that time, you should always find a way corroborate that evidence.
Not to be left out, mobile phone manufacturers are beginning to produce RFID-capable mobile phones that will more than likely become electronic wallets or billfolds. The classic example that mobile phone companies use to promote RFID is that you only have to put your phone next to a Broadway show advertisement and confirm the number of tickets you want to purchase, and the RFID system (plus the mobile phone wireless connection) handle the transaction. This situation may not happen tomorrow or next week, but the future is arriving fast. (Just remember not to lean on a glass display and accidentally order a dozen tickets to a show!)
The modern-day copier in your office is a wonder of office technology. Figure 14-5 shows a model. It can not only make copies but also act as a network printer, network storage device, and fax — it can even archive every single copy ever made on it.
This capability is due in large part to the transition from analog to digital technology. In short, a copier is essentially a low-end computer with a scanner attached to its top. The key to extracting the information in a copier is its storage device, which is often a hard drive.
From the forensic point of view, you have access to the data stored within the copier via any access point, which might be a network port, a USB port, or a wireless access point (WAP), depending on the forensic tool you use. The most direct method of extracting data from the storage device is to simply take apart the copier and physically extract the storage device. Any computer forensic software now on the market can do an extraction and then image the contents. The problem becomes how to read the data.
Some copier manufacturers use proprietary methods to save their data; the file systems they use may not be recognized by any forensic tools. Network copiers tend to use file systems that are recognizable to the network, such as FAT or NTFS, and some still use MS-DOS. You might have to look at the data found on the storage device in a different way than you normally would — simply clicking buttons in your forensic software manner doesn't work. You might even have to use a hex editor (gasp!) to view file headers to figure out exactly which type of file you have. (Chapter 11 covers file headers in much more detail.) The problem with nonstandard file systems is that you have to dig through raw data to make sense of how the company organized its file system for its copier. Contacting the manufacturer is always a good idea at this point because it can help you immeasurably in technical expertise and in saving time.
If a copier uses a proprietary system to archive copies, your best option is to contact the copier manufacturer for advice, and possibly the software manufacturer to extract the copier images. We can't stress enough how useful a copier examination can be for finding evidence. Beyond the scope of this book, but within the realm of computer security forensics, copiers are becoming a frequent place for hackers to plant rootkits and "back doors" into networks because most copiers aren't as well protected as desktop computers.
The next hurdle for forensic scientists to conquer is the issue of extremely large storage devices, on the order of terabytes, or TB (1000 gigabytes), and petabytes (1000 terabytes). With storage devices measuring 500 gigabytes (GB) on store shelves now, the possibility of working with terabytes of information isn't as remote as it might seem. The problem that forensic scientists need to resolve is how to acquire and analyze extremely large storage areas in a timely fashion. The question becomes "How do you find a digital needle in a 2TB database haystack without the process taking weeks or months?
The trend in computing power is for devices to become smaller while also becoming more portable. Almost any device you can think of now will eventually have some form of computing and storage ability. For example, some refrigerators made by Frigidaire are equipped with a flat-screen monitor and computer. Home entertainment systems can correlate what you watch and even recommend shows that fit your tastes! These trends, plus lots of other anecdotal evidence, appear to show that computer forensic investigators will have plenty of data to parse when looking for evidence of who, what, when, where, why, and how. The trick will be to keep computer forensic tools — and computer forensic analysts' training — up-to-date.