A useful construct for describing the various types of IOCs and IOAs that an adversary can leverage and their ability to modify them during an attack is the pyramid of pain. This construct, developed by David Bianco, describes the relationship between the IOCs, IOAs, and TTPs that an attacker makes available through observations by the defender and the attacker's ability to change those indicators. The following diagram shows the relationship to the various indicators and the work effort necessary to modify them in order to bypass security controls:
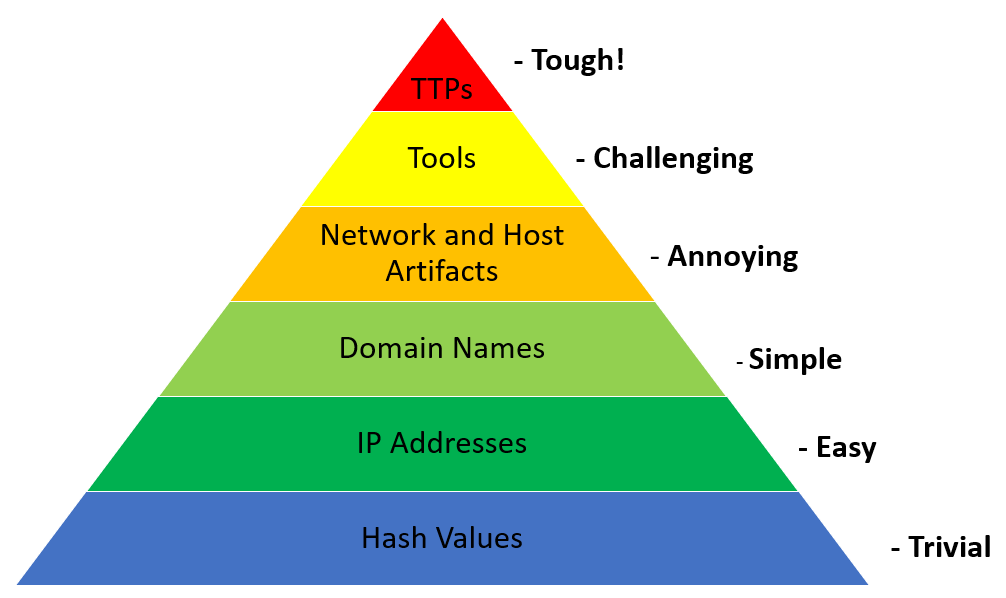
For example, an attacker may have crafted a piece of malware that spreads through lateral movement via the Windows SMB protocol. To bypass traditional signature-based malware prevention tools, the attacker uses a polymorphic virus that changes its hash every time it is installed. This change allows the piece of malware to bypass this control. Other indicators such as network or host artifacts are harder to change for the attacker and, as a result, responders have a greater chance of successfully stopping an attack by aligning their security controls at the top layers of the pyramid.
From a threat intelligence perspective, the pyramid of pain allows responders to align threat intelligence requirements with what would be useful from a long-term strategy. Having detailed information and intelligence about the TTPs in use by threat actors will provide more insight into how the threat actor operates. Lower-level indicators such as the IP addresses of C2 servers are useful, but responders do need to understand that these can easily be changed by the adversary.
