Chapter 3: Reconnaissance – A Deeper Dive
Did you know that most organizations give away intel for free! I know, right?! During the reconnaissance stage, it's important to know that by virtue of the internet being the internet, there's so much data freely available online that it makes the job of an attack extremely easy. This type of intel is often referred to as open source intelligence, or, if you want to sound like the cool kids, you say OSINT.
In this chapter, we'll cover the following topics:
- Investigating the target's website
- The Wayback Machine
- What organizations give away for free
- Employees – the weakest link
- Reconnaissance countermeasures
Investigating the target's website
Let's look at how to conduct reconnaissance on a target's website and how we can make use of other research sites. When you're doing reconnaissance, the target website is often where you'll land after a quick online search. That's where you'll learn the business's exact functions, location, contact information, clients, who the leadership team is, and sometimes, way more than that. You'll want to pay close attention to everything on the website.

Figure 3.1 – Investigating a website
In Figure 3.1, we can see a couple of pieces of information on this main page. First, on the left side, they've provided information on how to set up Microsoft Outlook with their particular email product. I already clicked through and saw how to set up via Microsoft Exchange 2003, where they also gave me the Simple Mail Transfer Protocol (SMTP) servers they utilize. Later, I'll describe how we can use that information to do banner grabs to identify the email server.
We can also see that they use remote assistance software. When you see that an organization utilizes third-party software, it's a good idea to do some vulnerability research to find out whether there are any issues with that product that could get you into the target's system. There are also links everywhere on the page – for example, the Help for Sending Email link highlighted in Figure 3.1. Explore all the links. They may have helpful information.
This company got bought out by another company (you can see that they've linked to the letter they mailed to all their current customers). Read that letter – it may discuss any new platforms they're utilizing.
Let's look at another target site in Figure 3.2. First, look at all the posts they've linked to – for example, Business Connectivity: Big Data is Everywhere. Some of their additional posts might be valuable to us; they might discuss details about the history of the company and other information we want to know. Even if it's historical, it may give us a clue for how we approach the phases after reconnaissance.

Figure 3.2 – Investigating another target site
This company has given us a lot of valuable information. They provided direct links to their Facebook and Twitter accounts. They have a chat service listed here. If you see something like that, find out what chat service they're utilizing and do vulnerability research on it.
Check the bottom of the page – and I mean the very bottom. People tend to overlook the legal imprint and privacy policy, but you should take note of it if it's there. Websites also typically name their web designer at the bottom, as we see in Figure 3.2. Do some research on that company because they could be hosting multiple targets we may want to exploit.
Look at links to form-based pages, like a contact or support page. In Figure 3.3, since this is an email-based form, it could show the information they don't intend for anyone to see. View the page's source information/code to see the HTML, ASPX, or whatever it is they're using:

Figure 3.3 – Email-based page
Inside that code, we might see some identifying comments that developers typically insert for their own memory. You'd be amazed at what we find inside of the page source code, as you don't see it in the web page itself. It's hidden – at least, hidden to the average user.
Many companies post things they think are completely innocuous, but a hacker looks at information differently from how a consumer does. For example, most companies have a page titled About our staff. Sometimes, they have links to their employees' emails, or they have photos of them and links to their social media accounts. Social media accounts will be particularly important because sometimes people share too much when they think no one is looking. They might even share details about their work projects. Therefore, it is important to do your due diligence when looking into employees (I'll show you how to do that later).
Some sites have dedicated forums or even internet relay chat (IRC) (especially if we're looking at an organization with a lot of nerds, as you see on HackThisSite.org). Look at what people are talking about. If they have IRC statistics or quotes, look at those. We could start a social engineering attack by contacting somebody in this company and saying something like, "Hey, what's it like working there? I'm thinking about applying."
To really dig into the website, ethical hackers often use a program called HTTrack (https://www.httrack.com/). It downloads a copy of any given website to your hard drive, including some of the backend code. Just think about the possibilities there. Using HTTrack, we can see exactly how this page is laid out, which might give us more information, such as whether they're saving their images to a different location. This is a very easy program to run. Simply create a project, categorize it, and assign a folder on your hard drive for it to download to.
Figure 3.4 – HTTrack website copier
As you can see in Figure 3.5, you have the option to Download web site(s), as well as the option to Download web site(s) + questions, which means you get to decide whether to download its associated links. Or, you could download the site into separate files. There is even an option that finds and downloads all ZIP files on a site:

Figure 3.5 – HTTrack, downloading the site
There are plenty of options that we can configure to get exactly the information we need (just click Set options…). For example, what do we want to scan for? By default, the program looks for images and CSS pages. Note that we're probably not interested in advertisements, so we can exclude them from the download.
Another thing that's important to remember is to change your browser ID and accept cookies.
Make them think a different browser is hitting their server (this option is under Browser ID). Throw them off the trail. Make it seem like you're using a Linux box even though you're running a Microsoft box. If you're going through this with me, download the site (HackThisSite.org).
In the past, I've found Microsoft Excel spreadsheets on a site. I have even found password files. Regardless of whether you find those kinds of files, it's important to have a good understanding of how the target's site is laid out.
Another tool we can use to map out this system and possibly even expose things is a link extractor utility. This utility usually goes through a given website and tries to extract both internal and external URLs for it. To find one that works for you, you can just search Google for link extractor. In Figure 3.6, I'm using the one at Webmaster-Toolkit (https://webmasterstoolkit.com/). All you have to do is type in the web address of the site you're targeting and hit Extract the Links. Seeing all the different links used on this website could help us figure out the server infrastructure. Some of the links could even provide other ways into the environment.

Figure 3.6 – Using the Link Extractor tool from the webmaster toolkit
After extracting the links, the result is as follows:
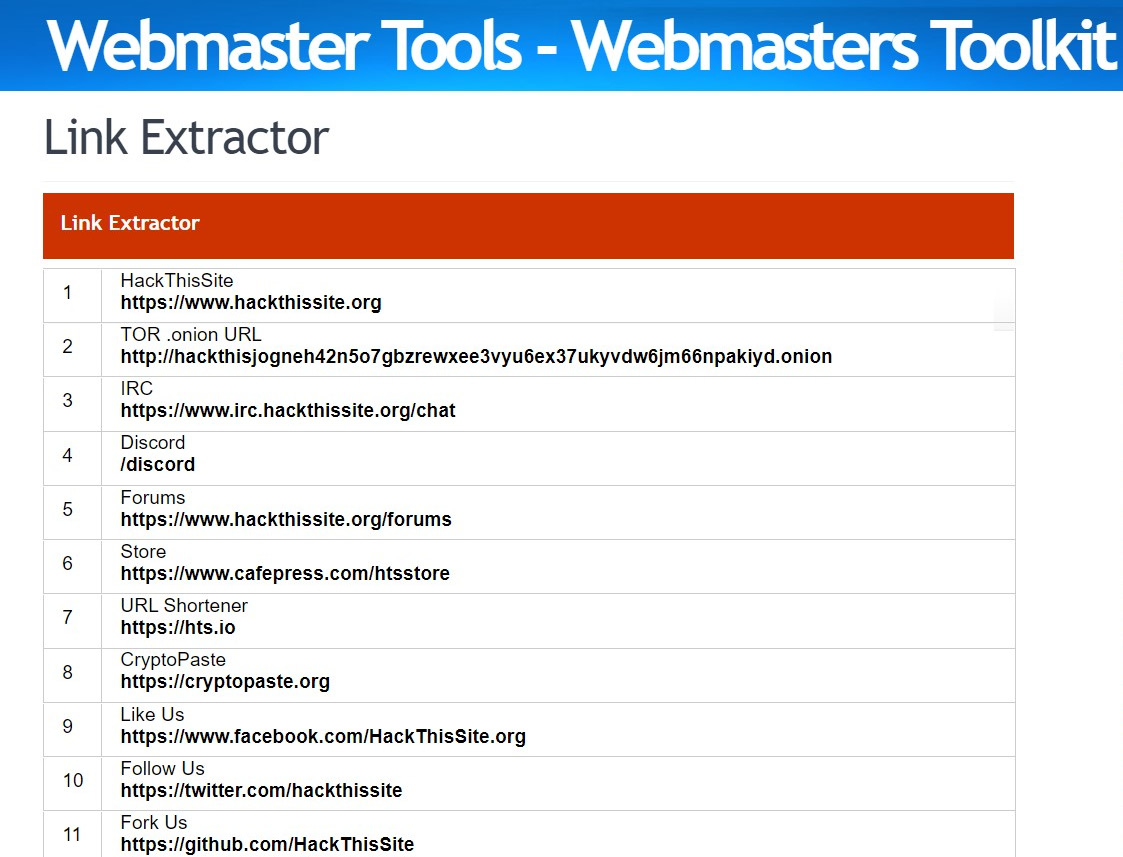
Figure 3.7 – Result of the link search
When looking at these results, make sure to check whether they expose anything, for example, extranet.wayneenterprises.com or maybe mail.wayneenterprises.com. The famous keywords to look for are email or restricted. I'm sure you can think of a few others on your own as well.
Advanced DNS tricks
Let's go a little deeper into nslookup.io. One type of DNS record is called an SOA, or Start of Authority. An SOA stores a record or information that's important about a domain or a zone containing adminstrative information that could be helpful to you.
Follow these steps:
- Just like before, type set type=soa. This type looks for the authoritative server.
- Enter the target URL (in our example, this will be hackthissite.org).
- Exit nslookup. The screen should look like the following:

Figure 3.8 – nslookup, looking for the authoritative server
- Ping the URL that was identified as the SOA to get the IP address (ns1.hackthissite.org).
- Once you've got the IP address, go back into nslookup and change the DNS server you're using with the server [IP address of SOA] command. That means that nslookup will use this DNS server to do the resolution.
- Next, change the type to find any address by typing set type=any.
- Type ls -d [target site or hackthissite.org].
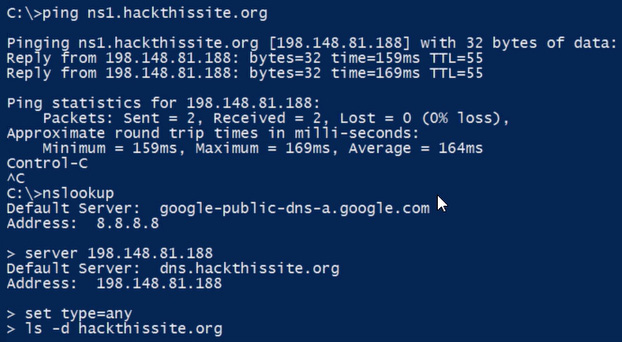
Figure 3.9 – nslookup, finding any site by type
- That final step will execute what is referred to as a zone transfer, which will tell the authoritative DNS server to send us a list of every single computer name or DNS name linked to an IP address. It shows the MX records and the A records. It shows whether there's a www or an FTP (maybe it's FTP1 or FTP2). This is a very easy way to pull all the server names out. Again, all we're doing is executing a normal, expected command against their own DNS server. Most secured DNS servers today only allow zone transfers to take place between specific IP addresses or computer names. However, don't think that will totally protect you – I could easily spoof the IP or computer name.
- Let's set the type back to return the mail server information (set type=mx). Take a look at the MX preference number. This number represents the order in which the server responds (the lower the number, the higher the priority).

Figure 3.10 – nslookup, looking for mail server information
In the preceding example, I am looking at MX records for HackThisSite.org again. From this results list, we can see that their primary mail server is ASPMX.L.GOOGLE.COM. We can also see that they've got a couple of redundant servers here (the lower priority GOOGLEMAIL servers). Often, when you perform a zone transfer, you're able to see the TTL (time to live). If the TTL is set too long, such as 3600 (which is 1 hour), we could poison their DNS.
What does it mean to poison their DNS? It means that I change the IP address (or hostname) to direct you away from legitimate servers and toward fake ones.
Let me demonstrate with an example. The equivalent in an attack scenario would be to do this to their server to infect their DNS. First, I'll play with a file on my system.
Let's go into my Windows directory, System32driversetc, and open in Windows Notepad a file in there called HOSTS. All computers look at this file (HOSTS) before they move on to sending a request to their DNS servers. I'm going to emulate a DNS poison attack using this file (technically, this is a DNS poison attack, but most of the later Windows operating systems set this file as read only, so it's only the administrator who can do modifications). I'm going to take the IP address of yahoo.com and make it equal to google.com. If I saved this file, every time I tried to go to google.com, my computer would go to this IP address (Yahoo's):

Figure 3.11 – Changing the IP address of Yahoo to Google's
The concept of poisoning a DNS is to redirect any traffic to an alternate IP address (at least for a little while). For example, I would make it so that every time an employee tries to access Citibank, they go to my IP address, where I would have a website very similar to Citibank's that prompts the user to enter their username and password. Then I would forward the user to the real Citibank site after capturing their login information (insert evil laugh).
All this research will be vital when you're working on a penetration test for an organization. Remember that for each of these sources, you need to look at them from a hacker's perspective – not from the perspective of a normal end user.
Netcraft
There are several tools out there that can help you with reconnaissance and footprinting. Sam Spade is one that's talked about a lot:
Figure 3.12 – Sam Spade
It's an application that adds a graphical user interface (GUI) to a lot of the reconnaissance tools we've been talking about thus far. While people use it as a vulnerability scanner to help secure their systems, attackers also frequently use it to find vulnerabilities.
While Sam Spade is an application that can be traced back to you (by IP), Netcraft is an online tool that looks at public-facing sites and helps to discover external servers. In some cases, it also looks at operating systems and even applications that are running on those servers via a banner grab. This last part is what usually scares people the most when they learn about NetCraft. Try it out for yourself at https://www.netcraft.com/.
A banner grab is simply identifying a system by looking at what ports are open and how the system responds to a request to said ports. A Windows server responds to a request on port 80 a little differently than a Linux box. Those differences are what help services (and some tools) to identify the target system.
Netcraft is intended to secure an environment by exposing any problems or vulnerabilities and then fixing them. As an attacker, this is something I will make use of. Netcraft has a variety of services that are focused on helping you secure your environment, but its primary use for us is in finding out the web server a site is using.
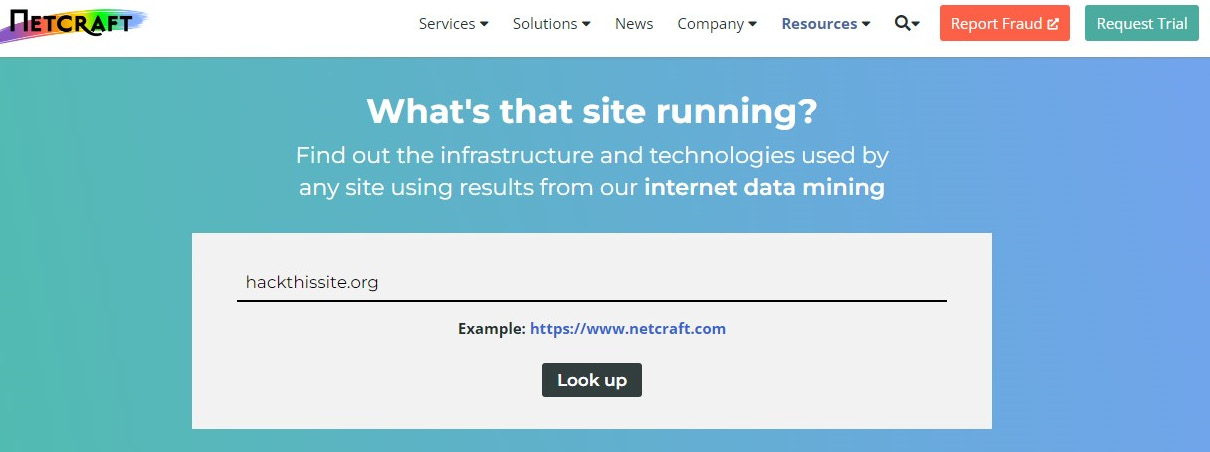
Figure 3.13 – Finding out the web server of a site using Netcraft
Let's pull up Netcraft and try it on our favorite – HackThisSite.org. You can see they give us quite a bit of background information here:
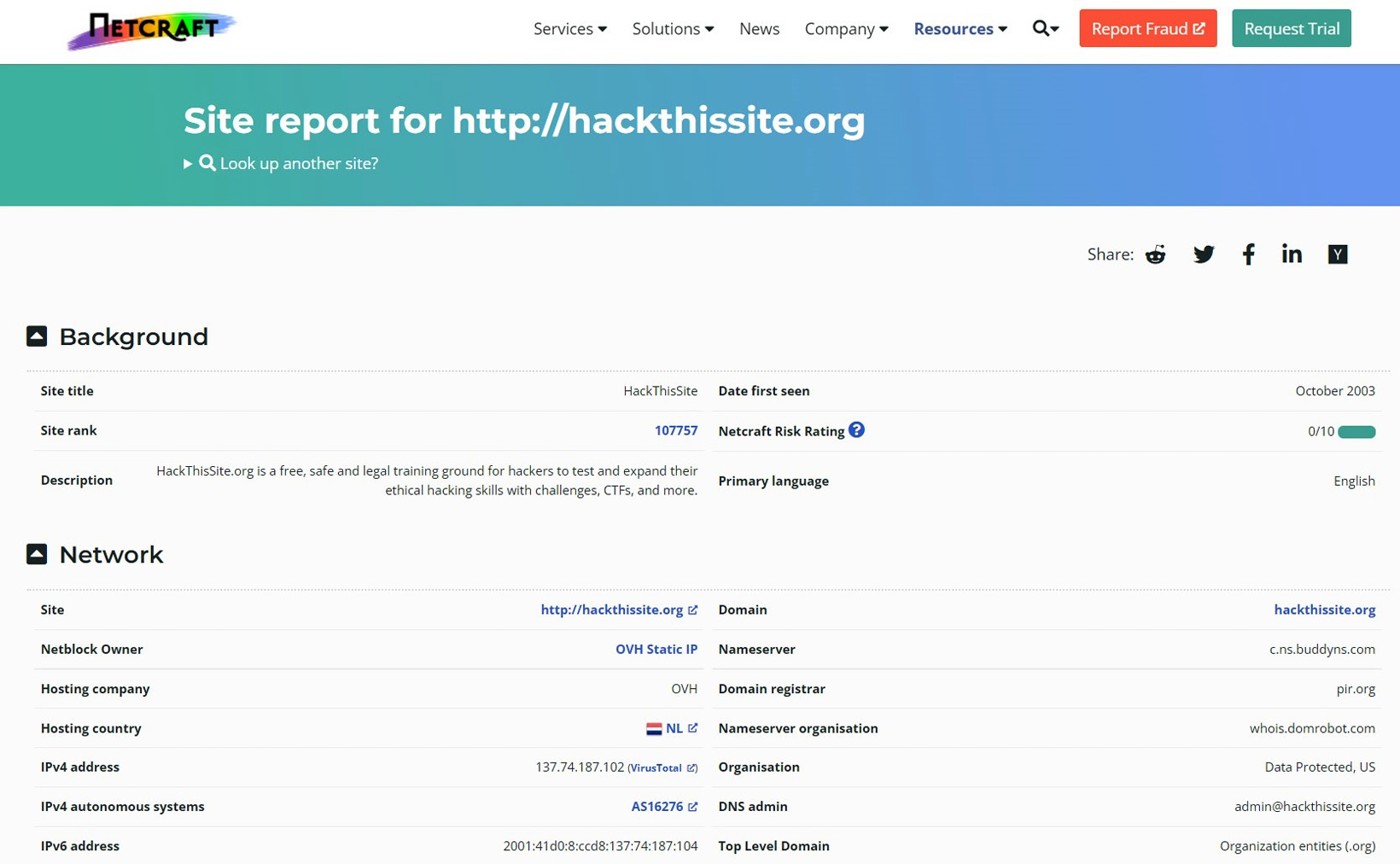
Figure 3.14 – Trying Netcraft on HackThisSite.org
It has extracted some keywords that they utilize. It's given us the site's IP address, including its IPv6 address and the domain registrar. We can also see the hosting history, which shows us that they are using a load balancer based off FreeBSD, which (if not patched properly) could be a great target. Netcraft also shows us their web tracks and the server-side technologies they're using, such as PHP, SSL, JavaScript, and CSS.

Figure 3.15 – Web tracks shown by Netcraft
More information is shown in the following screenshot:

Figure 3.16 – More information
What are they using to see which web browser their users are utilizing to access their website? As you can see, we can learn a lot of information with this tool.
When I test it with my old site (utahwisp.com), it gives us the site's hosting history, including the IP address, web server, and operating system. If you are conducting a penetration test on your organization's infrastructure, this will be quite useful because it's great at pulling up what server and web server service you're using:
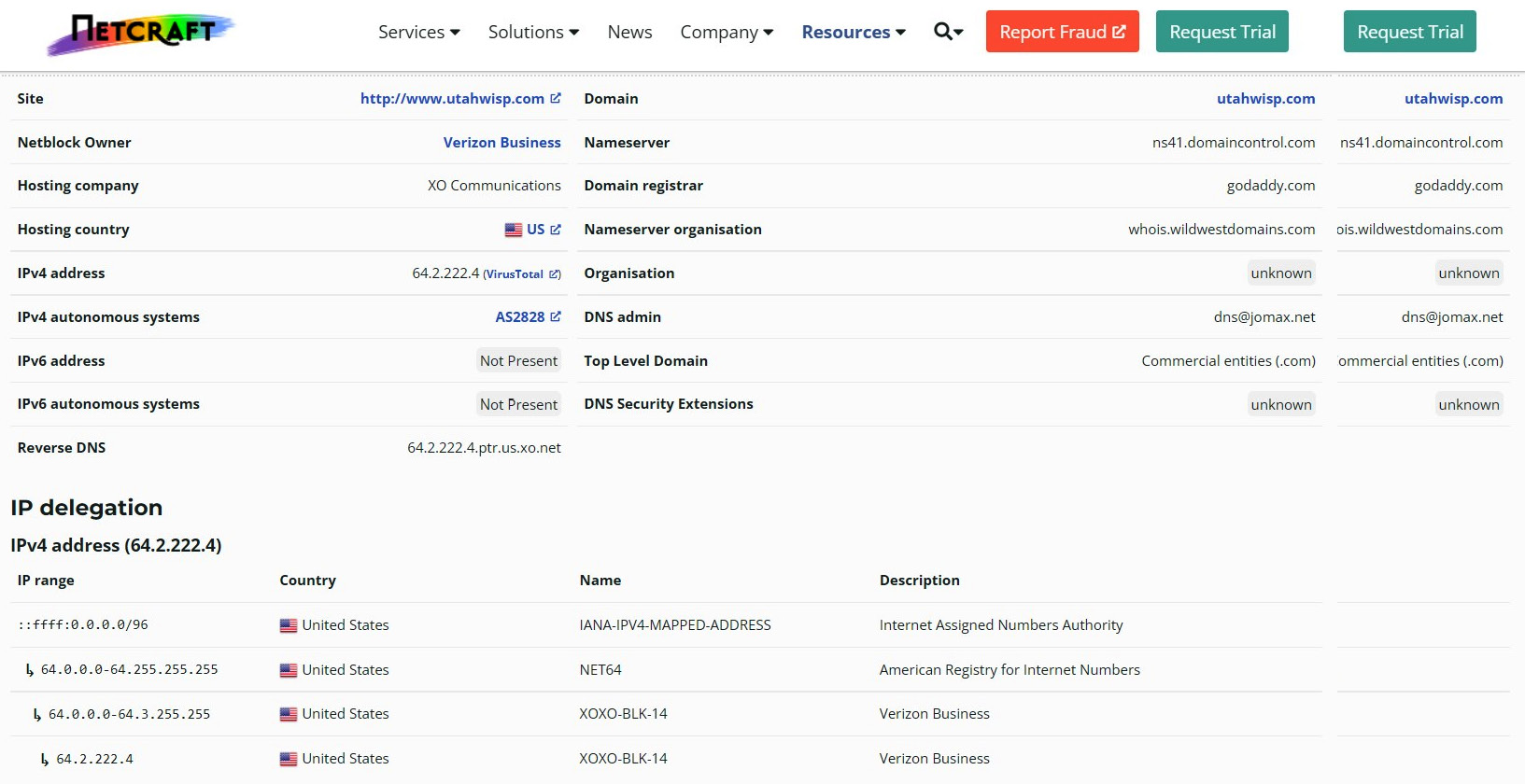
Figure 3.17 – Testing utahwisp.com
One other nice thing about Netcraft is that it shows you a Netcraft risk rating. Zero out of 10 is a great rating for security, but that doesn't mean it's not hackable. Obviously, them revealing this information exposes quite a bit to an attacker. There are a lot of tools created for legitimate purposes, such as Netcraft, that attackers can capitalize on just by shifting their perspective.
The Wayback Machine
At this point, the internet has been around for quite some time, and there are a number of retired web pages and websites. The Wayback Machine (https://archive.org/web/web.php) allows us to view previous versions of websites that may not even exist anymore. Think of it as the archive of the internet. Once we find the older version of our target site, we can scan for historical data that people didn't mean to expose. Now, before I got my start in security, I had no idea this tool was out there, but it's really interesting to use for fun as well (you know, like showing your kids what Amazon used to look like):

Figure 3.18 – The Wayback Machine home page
You can see here that they have saved over 456 billion web pages. The Wayback Machine goes through websites and detects any changes – if it detects a change, it makes a note and caches that information. As an example, I'll use my old company's website. The site is no longer being maintained, but you can see there was some activity in 2003. There is one snapshot of my site from January 10, 2003:

Figure 3.19 – The Wayback Machine change history of utahwisp.com
In the snapshot, you can see my web development skills. My prowess was considerable. This is back in the days when we used Notepad. I think by then I'd moved up to HotDog, which was one of the first WYSIWYG environments for web design.
What can we find here that would be useful for our purposes? We can find the purpose and messaging of the organization, where it's located, contact information, such as a cell phone number, and information about the email options available, including a login page. Note that this is just an example – your target will still be operational, so a lot of the infrastructure is probably still in place:
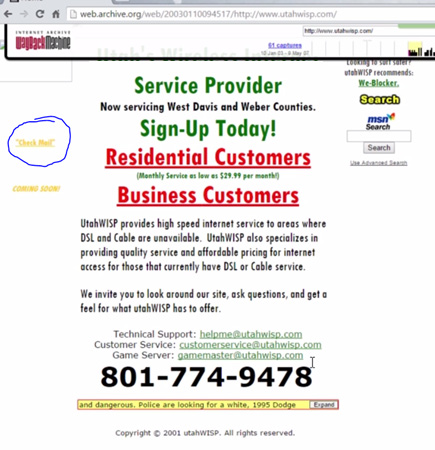
Figure 3.20 – More information from Wayback Machine
When companies first built their web pages (especially back in the day), they listed all kinds of information. They didn't think it was a security risk. That means, if we go back and look at previous versions of their website, it could expose quite a bit, for example, employee or leadership personal information. There may even be a press release section where they announced that they're moving to Microsoft Server 2000 and looking toward moving to 2008. Even when people think they've removed historical information from a website, there's always a record of it somewhere.
What organizations give away for free
When I was about 25 years old, there was a radio station, The Q, in the city where I lived that was holding a big contest that included giving away a big prize package. They would hide this big wooden Q every day, which was about a foot by a foot in depth and in height (30 x 30 cm) and about 2 inches (5 cm) thick, and give out clues for where to find it. If you found the Q, you won a prize package that could include a couple of four-wheelers, a trip to Hawaii, TVs, tons of stuff.
I was tracking the clues that they gave out each day, and I thought I knew where it was, so I looked around for hours in this huge park. After about three or four hours, I gave up. It turned out that I was about 25 feet (8 meters) away from it when I gave up. I still regret that today. It's the same thing here with reconnaissance – you've got to look everywhere, despite the massive amounts of information that become available to you.
The more you try to find out about your target, the more you're going to find. Victor Hugo, the famous author of Les Miserables, once said, "Perseverance, secret of all triumphs" – this is especially true for reconnaissance.
In this section, we'll look at what else you can find out about your target. We'll look into the information they're publishing that can be useful for us as ethical hackers. That includes job sites, promotional materials, social media, and email.
Job sites
Job sites give us so much information. I'm not just talking about standard job sites – we'll also get information from company-run job sites, including the career pages included on the corporate website.
When we start looking at a well-known job site, we start searching by job title or technologies. Companies might inadvertently expose the different technologies they're using when they advertise for specific jobs, even if it's for a temporary project. I'll be doing these very specific searches since I'm not actually going to target a company, but you will also want to look at all the job vacancies that your target organization has advertised online.
Remember that you are not looking at this as a potential employee or the employer. Look at it through the eyes of an attacker.
I'll use Monster (https://www.monster.com/) as an example. Start by looking for some technical positions, such as systems engineer. In the following example, based on the qualifications they're looking for, we can see that they're using Microsoft Active Directory, Windows Server 2008, VMware, and Hyper-V.
They're also looking for someone with knowledge of Cisco, which means we can infer what kind of routers and switches they're probably utilizing. They also mention the SolarWinds and Spotlight monitoring tools, so now we know what type of monitoring tools they're using internally. Once you get this information, you'll want to investigate the architecture of each component and see whether there are any vulnerabilities, or better yet, you might see any security systems that you'll need to avoid.

Figure 3.21 – Job requirement for a systems engineer
Let's try searching a different way – by keyword. Find people who are looking for someone who knows something about some outdated servers. Let's go with server 2003, for example.
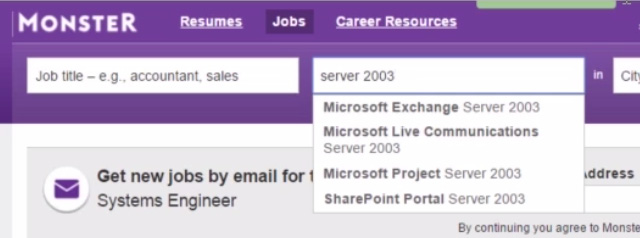
Figure 3.22 – Searching with the "server 2003" keyword on Monster
Once again, we'll look at a recruiting agency's job posting. They request experience working with Microsoft SharePoint 2010 authentication and permissions models, as well as administering SQL. So, there we have information about the backend. They are also looking for someone with experience with Visual Studio .NET, and it looks like they have both intranet and internet portals that are being hosted by SharePoint. All these systems are way outdated, and it would surprise you how many organizations out there are still running systems this old. If they weren't, I wouldn't be so busy!

Figure 3.23 – Job requirements of a SharePoint administrator
The same thing can be done by looking at other job sites, such as DICE (https://www.dice.com/), Indeed (https://www.indeed.com/), and more. Pay special attention to the jobs that your target advertises, as these will give you valuable insight into the systems they're running and their overall network architecture. You might even get a sense of what security controls they have in place. For example, what type of intrusion detection system (IDS) do they have installed?
Can you see now why job sites make me all giddy inside? They can give us a plethora of information, and this makes our job so easy.
Marketing and customer support
We can learn so much just by looking at the organization's social networking profile. As demonstrated in the previous section, recruiters and job sites can provide valuable information, such as the platforms or systems the target is using. We can also take note of how they support their users because that can be important for a social engineering attack. For example, I could call a random employee: "Hey Jim, this is Fred in the IT department. I just reset your account, and I need to make sure that your password is going to work correctly and log you in. What's your password, really quick?"
If the user support is done via email, I can spoof an email and make it look like it's coming from their IT department. Or better yet, a CEO fraud email attack, where an attacker (after reconning a company) poses as an executive, creates an emergency issue, and requests money from someone in accounting or their assistant to be transferred to a specific account. We can also look at the user surveys the target puts out to collect feedback, as the questions they ask might give us an insight into their business strategies.
If we start looking at the products they're promoting, that should also give us some information about their product specifications. To use this in practice, if I notice a particular target uses a given piece of software, I will backtrack and find out all I can about that software.
In our culture, we are sharing way too much information, both personally and from a business perspective. Social networking environments such as Twitter, Facebook, LinkedIn, and even Google+ are now used for marketing and personal purposes. This combination can expose information with very tangible consequences. Hopefully, if you're reading this, you understand that if you post something, you can't take it back, and it doesn't matter if you delete it immediately. We've seen thousands of people lose their jobs because of the things that they've posted online. Likewise, we've also seen a lot of companies lose money because of this.
Let's look at some of the different methods we can use to mine these social sites for our target's data. Obviously, start by looking around (from an attacker's perspective) and see what you can find. Look at their previous posts. Look at photos being uploaded or posted. Check out employees' personal sites. It's shocking how few people put controls on their websites.
Financial and competitive analysis data
Businesses often conduct competitive analyses to assess their competitors or to figure out their market strategy. As attackers, we can use services that are intended for business analysis for somewhat more nefarious purposes.
There are many sites out there we could use, but I'm going to focus on some of the more popular ones, such as Yahoo Finance, Google Finance, CNN, MSNBC, MarketWatch, The Wall Street Transcript, and more. Several of them provide information such as the market value of a company's shares, the company profile, and its major competitors. All this information may be helpful in future penetration testing, especially for social engineering attacks.
You can get this information through tools that allow for competitor analysis, or by setting up email alerts for updates to a specific company's profile. For example, if Microsoft posts something about the new HoloLens, or if Google posts something about ending Gmail, you obviously want to be notified about this kind of information. You'll have to register for those services, but it's a good way of monitoring what's going on with the company.
Competitive analysis tools allow businesses to discover information about competitors.
Attackers utilize these services to find out basic company information, such as when and how it was founded, or its leadership, location, and products. Many of these tools don't just provide analysis of competitors; they might also provide analyses of their products, their customer base, their suppliers, and more. They use the same techniques that we've already gone over to gather that information. They then charge money for it and give you a nice formatted report with patents, trademarks, catalogs, customers, vendor interviews, press releases, annual reports, and more. They basically go out and do all the spying for you, and there's nothing illegal about that.
Employees – the weakest link
Have you ever lost something and it ended up being right in front of you? This usually happens with my glasses. I'll be looking everywhere for them and running around the house saying, "Anybody seen my glasses?" And my wife will turn to me and say, "They're on top of your head."
It's the same concept with different reconnaissance techniques. Some of the data that we gather in the reconnaissance phase is incredibly easy to find. In fact, a lot of the information can be found through online services that we're probably already using:
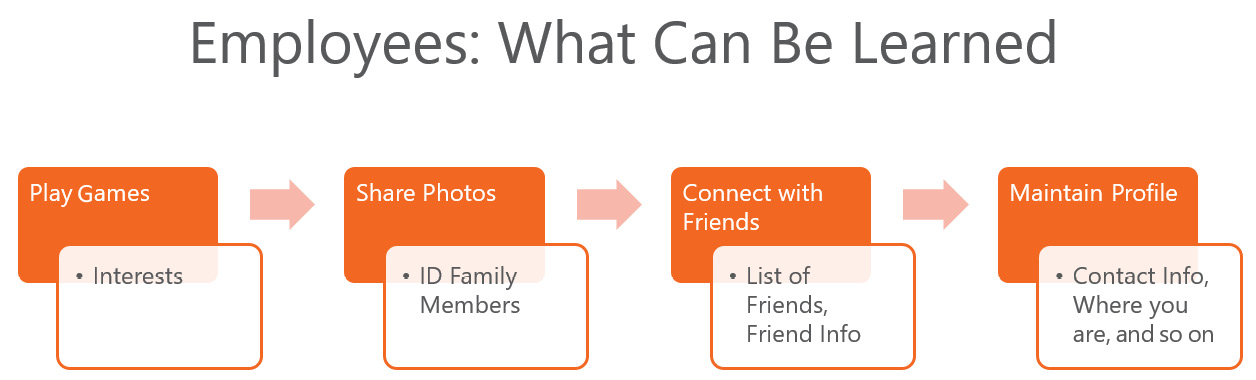
Figure 3.24 – Online services where information can be gathered
The employee side is where things get scary. For example, if an employee plays games, that may show us their interests and hobbies (not that I think that somebody sits at home with a hammer and crushes candy). This information provides us with a good sense of what people are familiar with, which could help us out with passwords in the future.
To take it to the next level, you can create a fake persona and start interacting with the target. For example, if you're a big fan of a particular gaming console, you could try to get into the forums where they're talking about doing repairs. You could even ask your target a few questions to start and build a relationship. This is a small taste of what social engineering is – another method for us to gather information.
What photos are they sharing? From these photos, we could find out some things: who their family members are; where the picture was taken; if they go to that place frequently. Today, smartphones even tag photos with GPS (Global Positioning System) coordinates, making it much easier to find out where someone is. We can glean even more information from the backgrounds of the photos – this could be their street address, a sports league they're in, or the school their kids attend. I know that's a little family-related, but it can be dangerous. I'm very protective about families and I hope you guys can recognize the problem with posting seemingly harmless information about your kids.
Employees might post pictures of them at the local bar on the weekends, revealing where they go to hang out with friends. Now, we know where to go to meet people that work for that organization.
Who are they connected to in their friend list? This could give us some potential additional targets. But more often, it's important for answering security questions. One of the security questions we get all the time when trying to reset a password is, Who was your childhood best friend? We might be able to figure that out just from interactions on social media. If that doesn't work, we could deploy a minor social engineering attack. For example, if I see that Bruce Wayne is friends with Clark Kent, I could send Bruce Wayne a spoofed email from Clark Kent asking about additional information that I might need for an attack.
Does the target often post their location or what they're doing? For example, Bruce Wayne says he's going to Metropolis this week. For us, the attackers, that means he's out of Gotham City, and the banks are wide open for me to rob because he's not there to protect them. Did the target post their phone number on their profile? Do they have strict privacy settings in place?
Think of security this way: I could be the safest driver in the world, but a drunk driver could still crash into me. Likewise, I can do everything I can to block people from getting to my information, but my best friend might have a profile that's wide open. If we've interacted online, that could expose some additional information about me, like my friends or hometown.
According to Tech Crunch, approximately 2 billion users log in to Facebook every month. That's around 1.3 billion logins daily:
https://techcrunch.com/2017/06/27/facebook-2-billion-users/
Over 300 million photos are uploaded daily. And when people go to Facebook, they spend 20 minutes per visit, on average. Facebook is an inextricable part of daily life. This means this site is not only valuable for reconnaissance, but is also useful for the attack stage. There are as many as 85 million fake profiles.
Let's look at some of the information we can extrapolate out of a Facebook page – John Wayne's to be precise. I've found his Facebook page, and he's been doing some posting, which is kind of bizarre:

Figure 3.25 – Facebook page of John Wayne
People will put all kinds of personal information on their Facebook pages because we're often unaware that seemingly trivial data can be very revealing in the wrong hands. From these pages, and specifically from John Wayne's page, we know his personal website, when he went on a business trip, what airline he likes, his birthday, his personal achievements, his parents' names, where he's lived, his pets' names, his high school, hobbies, and more. We can find out who his friends are based on who posts comments on his photos. When he's tagged in a photo, we can look at the buildings in the background to see whether we can identify where he is. Is his car in the picture? Can you see a license plate number? He posted a picture of him and his daughter, so now we know her name and roughly when she was born.
As you can see, people tend to put a lot of information online – even for deceased celebrities. What does that say about their interest in sharing personal data on the internet?
LinkedIn, designed for business relationships, is also a popular social media platform. It has approximately 13 million companies currently listed and a total of 467 million users. Let's go over what we could discover with LinkedIn.
The key information you should record in your Target Information Profile (TIP) from LinkedIn is as follows:
- Current and past employment data
- Educational information, certifications, and skills
- Personal interests, contact information, and location
- Notable connections and groups they may be a part of
For example, you can look at the technical skills listed, see where the target got their education, and investigate that particular program for more details about their abilities. As mentioned before in the Job sites section, we're able to see what type of platforms the target is used to working with, which may give us a sense of what their current employer is using (if that's what we're going after). Don't ignore the groups that people join – we're often able to see what someone is struggling with because people tend to join groups to help them with specific projects or issues they've encountered.
We will also be able to gather more information if we are connected to the person. In some cases, people will accept LinkedIn connection requests just to build their professional network. Because this is a professional platform where people don't generally share very personal thoughts, even fewer are concerned about the information they may expose through this site.
Let me show you an example using my own profile:
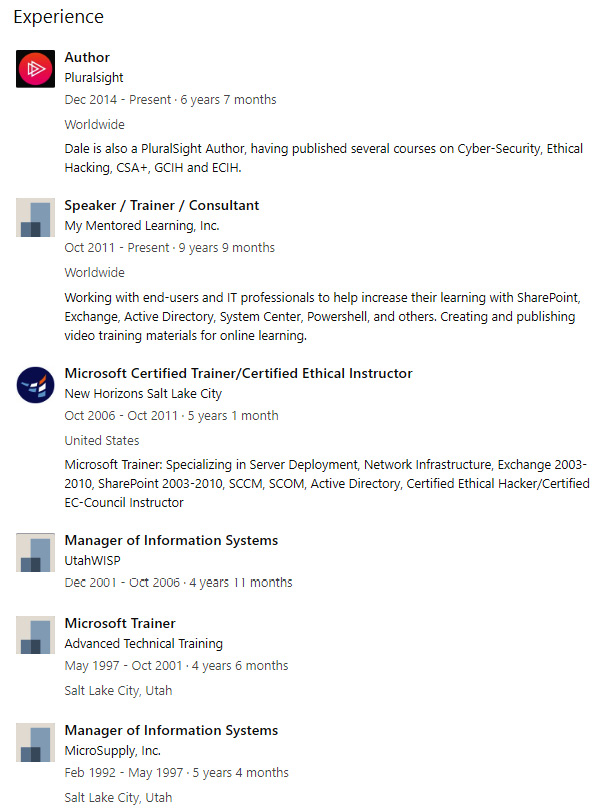
Figure 3.26 – A LinkedIn page showing the Experience section
In some cases, you can estimate the network infrastructure of a person's current employer based on their past experiences. As we go through this profile, you can see here that I worked for My Mentored Learning, Inc. That's my existing company that I use when I go out and teach. We also have New Horizons out of Salt Lake City. There's UtahWISP and Advanced Technical Training (another training center). Look especially at the certifications that I've listed in Figure 3.27. I'd say right away that this person knows something about Microsoft Servers, Exchange, SharePoint, and Systems Center. In a real-life scenario, you could infer that I'm also using that experience (and potentially those specific technologies) in my current job.
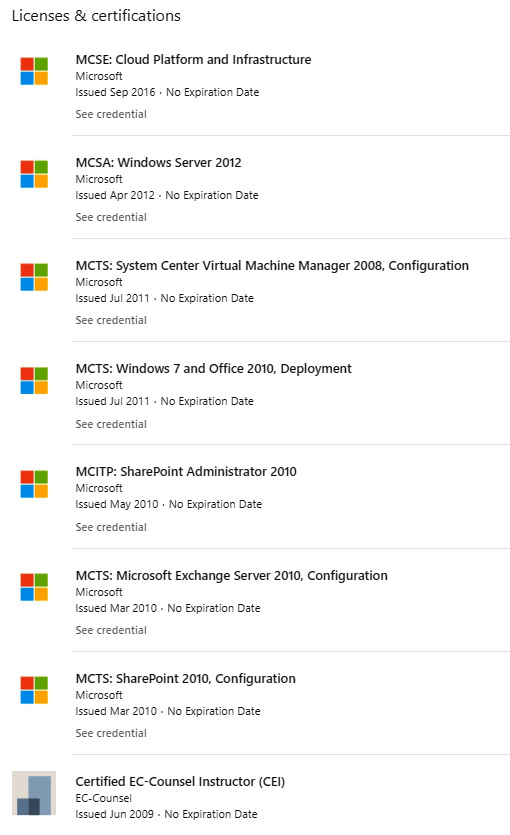
Figure 3.27 – Licenses & certifications section
Researching people
By now, you know how employees might provide valuable information for our reconnaissance. That could be because they share too much on social media, their skills, and past employment history, or maybe one of them is the vulnerability we want to target with a social engineering attack.
Overall, we are trying to create a profile of each person. Even seemingly innocuous information may be helpful because people often base their passwords on things that they reveal online. Look for information such as job title, hobbies, whether they're involved in any type of charitable work, or anything that may be of interest. We also want to try to collect things such as phone numbers, home addresses, email addresses, and possibly bank or credit card details.
To find those things, most people will use third-party products. There are obvious sources, such as personal blogs or social media, but there are also dedicated online search products for finding this type of information. These include sites such as PeopleLookup (https://www.peoplelookup.com/), AnyWho (https://www.anywho.com/whitepages), and CheckPeople (https://www.checkpeople.com/).

Figure 3.28 – Looking up people on PeopleSmart
I used myself as an example and searched with PeopleSmart. All I had to do was enter my name and the city of Salt Lake City, Utah, and hit Search. These types of websites search public records, as well as court records, and make them accessible to the average person. It's all already out there, but they've made it easy for us to get a hold of it. Note that most of these are paid services and require a little more information. But even with the free version, I can see my old phone number and address. You may want to take this to the next level by finding the addresses on Google Maps so you understand where this person lives. Again, the purpose of this is to give you some hints and details that you will add to your database of information or your TIP.
Pro-Tip
Many of these search engines, such as Google and Yahoo, will provide notifications on updates. If someone changes something on that website, you could be notified of those updates. Trust me – attackers are already doing that to see when you post a new job.
Social engineering
I define hacking as getting a device to do something outside of what it was designed to do. That's exactly what social engineering attacks accomplish, or, as I like to call it, human hacking.
By default, humans are not designed to give up personal information. We know it's wrong, but we continue exposing information about ourselves because people or services convince us that we should somehow trust them (this is called gaining the target's confidence).
Information
A McAfee documentary (https://www.youtube.com/watch?v=yzU82Ul96pU) from a few years ago perfectly illustrates the power of social engineering. It describes one of the most famous social engineering attacks that targeted a woman based solely on the fact that she visited a genealogy website. A group of people pretended to be related to her and preyed on her emotions (a hallmark of social engineering). They claimed that they were trying to escape a bad situation and needed money to do so. She ended up giving them over $500,000. Ultimately, this was revealed by a gray hat hacker who investigated the extent of the damage by hacking her again to see how the attackers had targeted her (https://www.youtube.com/watch?v=F9GylhWsVc8).
So, how is this typically done? One of the most basic methods is dumpster diving. Surprisingly, this is what it sounds like. You can find a lot of information about someone in their trash can. A great example of this was back in the days when Microsoft was under investigation by the US Department of Justice about how they were implementing Internet Explorer. You can read about it at http://www.newsweek.com/diving-bills-trash-161599. Sun Microsystems hired people to go and dumpster dive at Microsoft's location. Because trash is not considered company property, they pulled out some reports showing some of Microsoft's questionable behavior.
We can also eavesdrop on a target. Eavesdropping could include physical listening (like when you listen to the person in the cubicle next to you), digital eavesdropping (via email, for example), or so-called shoulder surfing (secretly watching what people are doing).
I try to protect against the latter as much as I can. In fact, my wife thinks I'm crazy because whenever I'm out and about and have to swipe my debit card, before I type in my PIN code, I physically turn around and make sure no one is trying to shoulder surf. There are also digital methods of shoulder surfing – where people use their cell phones to capture images. I'm very suspicious of people who are on their cell phones that are right behind me in a checkout line because, even if they have the phone up to their ear, their camera could be recording my PIN. The same principle can apply to passwords, so be mindful of typing your password into your phone in a public place.
Eavesdropping can also be dangerous because it may allow people to more convincingly impersonate an employee of an organization that you are legitimately involved with. Perhaps you take a phone call in your local grocery store, and you're complaining about your bank, Citibank. A scammer might hear you and then call you up and say that Citibank has an issue and is calling people up asking them to confirm their identities. In that way, they're using minor details about you to get you to reveal potentially valuable information about yourself or someone you know.
You've got mail = I've got you!
Another great tool for gathering intelligence is email. We can track when an email has been read, if it has been forwarded, the time spent reading it, any links visited, the types of servers being used, the OS the recipient is using, and more. There's a lot of information embedded in emails.
Let me give you an example:

Figure 3.29 – Information embedded in an email
This is an email header I got from Thrifty Car Rental – a typical email advertisement about some upcoming car rental stuff. Look at this header information – it's available for every email. Back in the old days when we didn't have Outlook, a lot of this technical information was listed at the beginning of all your emails. Now it's hidden, but you can still expose it by looking at advanced headings (typically).
From the header alone, we can see who the email was sent to, the date and time that it was sent, the server it came from, the sender's IP address, and even the authentication system being used by the sender. That means if we want to obtain the name of one of Thrifty's email servers, all we have to do is sign up for emails from them.
There are several tools that we can use to gather information from emails that are completely invisible to email recipients. Email Lookup (https://www.ipaddresslocation.org/) by IPAddresslocation.org scans the headers for you. If you want to track what's going on with a particular piece of email, you can use eMailTrackerPro (http://www.emailtrackerpro.com/). It will show you a map of the likely location of the sender and some WHOIS information. PoliteMail (https://www.politemail.com/) is a tool you can use with Outlook. It creates a map that shows all the different email servers that a particular email hopped through.
DidTheyReadIt (http://www.didtheyreadit.com/) is another application or tool that you can use to find out whether an email recipient read an email or whether they just deleted it right away. ReadNotify (https://www.readnotify.com/) can tell you when your email is opened, if it was reopened, if the recipient forwarded it to somebody else, and if so, who it was forwarded to. This one also has a nice GUI.
These kinds of services are especially popular in the sales and marketing sector – they want to know when you've opened a message, clicked a link in it, and even how long you spent reading it. If you're working for a company, the marketing team may already have access to these tools.
Today, based on reverse lookup, most email servers drop an email if they believe a header has been forged. When an email comes in, the server asks, What's the name of the email server this came from, and what's the IP address in the header. Then it does a reverse lookup to see whether those are still true statements because most of the time, when someone is forging a header or spoofing the email address, that information won't match up and your email server will drop it. Using these types of tools helps security professionals to see whether their email systems are susceptible to different types of reconnaissance.
A great example of this is, as I mentioned previously, countless corporations falling victim to CEO fraud emails. Attackers spoofed corporate email accounts and impersonated executives to fool employees in accounting or HR into executing unauthorized wire transfers or sending out confidential tax information, as seen in this article:
https://krebsonsecurity.com/2016/04/fbi-2-3-billion-lost-to-ceo-email-scams/
Reconnaissance countermeasures
One of my favorite movies is The Hunt for Red October. When the torpedoes are coming in, Sean Connery yells, "Release the countermeasures!" And this is exactly what we need to do here. We need to understand the countermeasures for reconnaissance and what we need to be looking for when performing penetration tests (pen tests). You might know GI Joe's famous quote, "Knowing is half the battle." This also applies to us. Knowing what you are exposing and knowing what the attacker is capable of is half the battle.
In this section, I'll show you how to put your shields up and implement those countermeasures, as well as some best practices for reconnaissance. I'll also show you how to set up for a pen test and the actual workflow of what you should be tracking when doing reconnaissance.
Countermeasures
So, how do you defend yourself against the kind of reconnaissance techniques we reviewed earlier?
The first thing you need to do is make sure you have configured your routers to not respond to certain types of traffic. In other words, ensure they don't identify themselves.
Here's a fun exercise. What's the default SSID (Service Set Identifier) on the Linksys router? Oh, that's right, it's Linksys. What I like to do is take that Linksys router and change the SSID to D-Link – because that's the default broadcast for a D-Link router. That's misdirection. When an attacker comes, they're going to try to launch D-Link attacks at my router and not ones for Linksys. So, please, configure your routers to not give out information they shouldn't be.
Here are a few tips for protecting yourself:
- Make sure that you use some kind of IDS.
- When you deploy your web servers, don't leave them with the default configurations/settings.
- Get rid of powered by… because it can give away too much information (you saw that earlier when we went through Google hacking techniques).
- Enforce security policies. That includes training employees to adhere to the policies so they don't respond to someone calling them up and saying, "Hey, this is Billy Bob down at the IT department, I need to reset your password – can you tell me what it is currently?"
- Implement (and enforce) security policies on servers. Just having them and not enforcing them is like a parent threatening to ground a kid and not following through.
- Do some reconnaissance on yourself.
- Close unused ports, and if you do have open ports, whitelist them.
- Disable unnecessary services on web servers. Microsoft has a Best Practice Analyzer (BPA) tool that will go through and tell you what services aren't needed that you have turned on based on the role of that server.
- Prevent search engines from caching. There's a file you can create called a robot.txt file. This file tells Google which folders and files not to crawl or index. The only downside to this is that (you're going to laugh at this one) I can use Google to find websites that have robot.txt files in them.
- Disable directory listings in order to prevent people from learning the OS or doing directory traversal.
- Configure the internal and external DNS (separately):
- For example, if your public-facing site is gotham.com, make sure your internal DNS environment is not also gotham.com.
- Restrict input types (such as pipes, commas, and colons). This will be even clearer if you watch videos on SQL injection, as restricting your input types is what's going to save your bacon.
- Avoid cross-linking on your site (linking to other pages within your website). That just helps Google.
- Always remember – humans are the weakest link. In fact, my favorite quote is, "There is no patch for human stupidity." There was a report that the IRS started a big push to train all their employees on how to avoid social engineering attacks. Within 30 days, they pen tested them, and 65% of their employees gave up their information. Train your employees and help them set up encryption or stronger passwords. Send out updates through an organizational newsletter if you've got one. It pays off.
Now, I know that reconnaissance can be overwhelming as far as remembering what to look for, so I've got a great solution for you. Wander over to the OSINT Framework (https://osintframework.com/). As its name implies (Open Source Intel), this site will help you cover all your bases during your research by using open source (or publicly available) intel. Plus, it might give you some other ideas of where to find more intel on your target:
Figure 3.30 – OSINT Framework
With that, we have come to the end of this chapter. Congratulations on completing it successfully.
Summary
Our quest led us to investigate how attackers gather information from their target's website to know the target's exact business functions, important contact information, clients and partners, the management team, and so on. We learned how to use WHOIS, the command-line interface, ping and DNS, and SOA to gather information. We learned about more tools that help with reconnaissance and footprinting, such as Sam Spade, Netcraft, and the Wayback Machine.
We saw how what the information organizations give away for free can reveal a ton of vulnerabilities. So do job sites, marketing materials, customer support, social networking profiles, and financial and competitive analysis data.
We also discussed employees as the weakest link. Their hobbies, the things they share or post online, the places they go to after work, what they buy, and more all give attackers the clues they need. We then discussed how attackers use these clues to join the groups their targets frequent, befriend them or their friends on Facebook, connect on LinkedIn, and/or find a way to socially engineer them.
In the People search section, we learned how to profile people using third-party products such as PeopleLookUp, Anywho, and CheckPeople.
Now that we've done some reconnaissance, our next step is to start scanning the networks we've discovered. We'll do this to find live targets and understand the infrastructure of the target organization. Scanning is done via various techniques – some passive, and others active.
Questions
As we conclude, here is a list of questions for you to test your knowledge regarding this chapter's material. You will find the answers in the Assessments section of the Appendix:
- Which information may be gathered using nslookup?
- A DNS server location
- Hostnames and IP addresses
- WHOIS intel
- A nameserver and operating systems
- Which of the following is the most accurate description of footprinting?
- Investigating a target
- Enumeration of services
- Discovery of services
- Dialogue with people
- Which record will disclose details about a domain's mail server?
- Q
- MS
- MX
- A
- What alternative options do you have if you can't collect enough information from a target directly?
- Social engineering
- EDGAR
- Competitive analysis
- Scanning
