Chapter 5: Enumeration
Enumeration is interesting. It does something that we typically don't want to happen. It makes systems behave abnormally or in a way that we wouldn't expect them to. Steve Wozniak, one of Apple's founders, said that a lot of hacking is playing with other people, you know, getting them to do strange things, and that's exactly what enumeration does for us. Enumerating is a core part of evaluating any target. An enumeration can be as simple as running a reverse DNS lookup on an IP address, or as complex as the entire OSINT process being run on a target. Enumerating a target is one of the most important steps in penetration testing. The goal of performing enumeration on a network is to gather as much information about the network as possible. This process typically looks at hosts and the services that they provide. With this information, an ethical hacker can identify and exploit vulnerabilities in the network.
Before enumerating a network, it is important to understand exactly what an enumeration is and why it's useful.
In this chapter, we'll cover the following main topics:
- What is enumeration?
- Ports and services to know about
- Enumerating via defaults
- NetBIOS enumeration
- Enumerating using SNMP
- Enumerating via LDAP
- Network time protocol
- Enumerating using SMTP
- The golden ticket – DNS
- Oh wait, there's more!
- The countermeasures
Let's get started!
What is enumeration?
This technique is usually conducted internally. While it can be done through reconnaissance, it is a slightly higher risk because we need an active connection to the target machine, which means what we're doing could be detected by a security team. When a user makes a connection to a network share, they must provide credentials. Those credentials are associated with what we refer to as an access control list (ACL). This ACL contains usernames and groups that have access and the permissions for those who access them. So, maybe we can trick the target machine into giving us that information without presenting our credentials.
We'll also look at some services. If we know of a specific service from looking at our reconnaissance and scanning techniques, we can enumerate those services to give us information that is about more than just the operating system. It's called a null session. A lot of the newer operating systems have blocked this capability. The issue is not everybody is up to date, and there's always one little machine out there nobody is tracking. Also, maybe you can't afford the latest and greatest, so creating these null sessions is a way to make an active connection and then query the services and/or shares.
When we hit a target, we extract information such as usernames and possible groups. In some cases, we also pull the groups and the users who are members of that group. If we can't do this yet, we should be able to pull the machine's name and network resources and services that may be running on that system.
Again, some of the information we might be able to pull could also include routing tables – especially if it's like a switch or a router of some sort, along with auditing services. We will also try to expose some applications. Again, we should have been able to discover applications via our scanning and reconnaissance phases, but often, the application itself can give up a lot of data. Additionally, if I can get ahold of some DNS and Simple Network Management Protocol (SNMP) information, it can make your life a living nightmare.
Now, let's discuss enumeration weak points.
Some of my favorite enumeration weak points
When it comes to enumeration, an attacker will typically look for what we call the low-hanging fruit. This means we'll look for the easiest weak points first. Here are some of the lowest fruits that attackers will target initially.
Business card
How can a business card provide a weakness? Well, think about it. What's on your business card? Your name, address, and company name. That doesn't seem to give up too much information, right? How about your email address? They might not spam you, but guess what? Most companies – because of the way Active Directory works, or any directory services – go through and create usernames (what's referred to as distinguished names), which would be a way of logging into the network. We typically think of logging in as being domainusername (gothambwayne). Most directory services technologies will also accept [email protected]. It uses the same naming syntax that is associated with email.
As an attacker or hacker, I need at least two pieces of information to come for you: a login name and a password. If you hand me a business card and you were able to log into your system using that same email address, I just got 50% of your information. I probably don't need a business card, because I can get your email address off your company's website. Scared yet?
Windows groups
As we mentioned previously, these groups are created and maintained by your IT department and have been given security identifiers (SIDS). They contain other objects such as the user accounts themselves, or SIDS.
When a user tries to gain access to a resource, they present their credential. This credential is then looked at by the file server, which says, Let me check if you're a member of a group that has access or have been given explicit access. In this case, let me look and see if the group "marketing folks" have access to this file or resource. I can, therefore, enumerate a Windows group and say, Okay, which user accounts are a member of this "marketing folks" group? Again, I can end up enumerating everybody in every department at your organization.
Default passwords
Default passwords are one of my biggest pet peeves. I get it – technology is moving extremely fast, and a lot of times, we just don't think things through. This is one of those things I wish I could get across to everyone, including home users. We go and purchase the latest and greatest router and, according to their instructions, we hit one button and it auto-configures. With one click, we're on the internet, and we're safe. Well, probably not. So many devices today come with default passwords. It's very easy to log into the system to enumerate it just by using those passwords if no one's changed them.
There are websites dedicated to storing default passwords. It's nothing nefarious, it's just very convenient, especially for an IT guy who walks in and goes, Well, SMC switch, I wonder what the default admin password is on this one because I need to log in.
Next, let's discuss the ports and services you'll need to know about.
Ports and services to know about
Let's consider the ports and services you will want to be familiar with:
- Most of the DNS information that goes across the network is going to be using port 53.
- Simple Mail Transfer Protocol (SMTP) typically uses port 25.
- Microsoft RPC endpoints use TCP 135.
- The global catalog service, which is a stripped-down version of Active Directory that users and applications take advantage of all the time, queries port 3286.
- The NetBIOS naming service, which is typically the computer name to an IP address, uses port 137, both TCP and UDP.
- LDAP or LDP is the protocol used by Active Directory, Open Directory, and all the different directory services out there. It uses TCP and UDP port 389.
- SMB, which is our server message block over NetBIOS, is what creates shared resources or shared folders, and it uses TCP 139 to make connections.
- We also have SNMP, which uses UDP 161. The other SMB technology that it can use is TCP, which is going to be associated with port 445 on TCP.
Note
It's important to know about these services and the ports they operate on. You need to understand or memorize some of the ports and services that different technologies utilize for your exam.
All these services are utilized in day-to-day operations on the network. You could go through and block all these ports if you'd like, but that system isn't doing much online. A good analogy for this is saying, I understand the risks of driving on the freeway; I have a higher chance of getting in a car accident. However, I accept those risks, knowing the flaws and possible situations that can take place. I'm going to prepare myself for that – I'm going to be more aware of the road around me, how fast I'm going, how far ahead the car is in front of me, which exits are coming up, and avoid distractions. If you think in terms of normal network traffic, the issue with these ports is that you need to be monitoring the traffic on them. This is because anything you're not expecting is going to throw a flag in the air, stating that something may be going on in your network.
Enumerating via defaults
This subject drives me bonkers; it makes me want to pull out my hair, thinking about how naive people are out there. In 2015, CNN released a study showing 90% of the credit card readers out there use the same password. It's the default one – it's either 166816 or z 66816. Now… don't rush to your bank or ATM to see if that password works. That's not our purpose. The point is, there are these types of vulnerabilities.
This is our biggest security issue because defaults exist everywhere. I love the phrase complacency will be your downfall. I know we have tons of devices and technology out there being thrown at us – servers, desktops, routers, tablets, phones, switches, Wi-Fi, and so on. The demand is always there in getting it set up and getting it done fast. Sometimes, we have the issue where devices get deployed with our default passwords or default user accounts. Every device out there has them because you must go through and set it up.
Never leave the default user accounts or passwords in place! Never! Don't assume or say it's just a small device, it's just my cell phone, it's just a tablet my kid plays on, or it's just my home router.
A friend of mine (ok, maybe it was me or maybe it wasn't) was doing a lot of traveling and while visiting a small town where some family lived, they went to the local convenience store to withdraw some cash. Once they were in front of the ATM, they noticed that instead of a normal ATM screen, it was asking for a password, and they hadn't put their debit card in yet.
They tried some known default codes, first typing in 1234. They got an error and then typed in 0000 and got another error. They tried 1212 and to their surprise, they were presented with the administrative screen of the ATM. They could get into the setup and do config testing. Out of curiosity, they selected tests. They were presented with another menu that invited them to test a receipt, meaning print a receipt. They could also test a cash distribution. Yeah, that would have issued cash to my friend. Being an ethical hacker who just likes to see how things work, they went over to the front counter person and told them about it. They disconnected the plug and powered it back up, and the ATM started running correctly.
So, either somebody had just serviced the ATM and didn't completely exit out or there was a glitch. But again, think about the defaults being used here and the vulnerabilities that can be presented.
NetBIOS enumeration
What is NetBIOS? Well, let's put our memory caps on and take a trip down memory lane. NetBIOS has been around for some time and is often mistaken as a protocol. It stands for Network Basic Input Output System, and it's technically a program that allows applications on different systems to talk to each other over LAN.
Warning
Some of the things you see, especially when it comes to NetBIOS, might be a little outdated. We'll talk about why we still cover it, why we still talk about it, and why it's relevant today.
It was created by IBM back in the old days. IBM kind of left it behind and Microsoft adopted it. Since then, NetBIOS has become an industry standard. It's used on Ethernet, and if you're old school, it's also used in Token Ring. If you are familiar with Token Ring, I'm not referencing anything about hobbits… NetBIOS is used inside of the options when we are inside Windows. If we go into the network settings for a network interface, it's under the clients for Microsoft networks. In there, you'll see an option that says file and print services, which is where we can turn things off and on.
Note
Remember, not only is it important to know what applications are on your machines, but also what users can run from even a thumb drive.
Some of these things won't work on newer operating systems, such as Windows 7 and higher. However, from my experience, there's always a system on the network that's not up to date, or one they had no reason to update.
Some of the commands you can use to enumerate NetBIOS include using the built-in utility in every single Windows system, called nbtstat.exe, using the nbtstat -A <target-ip-address> command. This will display the services running on the target, as well as group memberships and domain information.
Note
For the detailed functions of nbtstat, simply type nbtstat into Command Prompt:
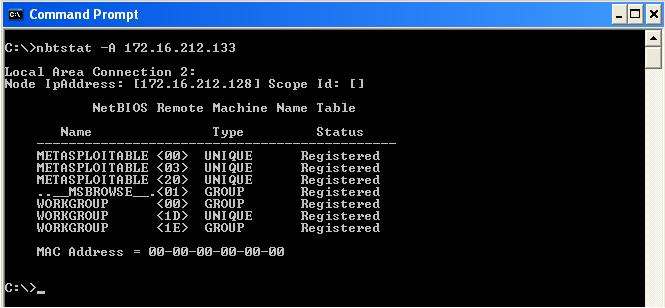
Figure 5.1 – Results of the nbtstat command
Next, we'll learn how to enumerate with SNMP.
Enumerating using SNMP
What could go wrong? Well, quite a bit. Little things make big things happen.
SNMP has been around for a long time and has gone through several version changes. We'll go through and look at what SNMP is and why administrators enable it. While it makes our lives easier, any time we talk about ease of use, remember the technology triangle. Once we implement heavier in terms of ease of use, or from the GUI perspective, we lose security.
What is SNMP? It stands for Simple Network Management Protocol. It's exactly what it sounds like – a protocol that runs the application layer and allows us to manage different devices. Now, whether they're routers, switches, firewalls, wireless access points, or even servers, they report back to a centralized location so that we can, as its name implies, manage devices:

Figure 5.2 – SNMP clients gather performance intel and report back to a centralized reporting point
So, again, an administrator can see what's going on. If a CPU is overloaded on a particular router, if server memory is being over-utilized, and so on, the administrator needs to be warned about these things. Besides devices, a lot of operating systems, including both Windows and Linux, support the SNMP protocol. Typically, we install an agent on these devices, and they report back to a management console. The Management Console, or management station, will then send out requests to the agents to retrieve certain information you've plugged in and are trying to monitor.
The agents we install on our components and the management software program are going to talk to each other, but we don't want them to just talk arbitrarily. There's a little bit of security that's implemented with SNMP, but not enough as far as the security is concerned, or the lack thereof. It all depends on the version of SNMP you're running. Version one is very simple, basic, and extremely vulnerable to SNMP enumeration. They then released version two, which was the same as version one, except they added some additional components and enhancements to it. Still, it is not very secure.
The reason SNMP has a bad rap about not being secure is because the two communication channels that are used between the agent and the management software use two different types of passwords. One of them has read access, while the other one has read and write access. Now, here's where the issue comes into play. For the public, which has read access, meaning my software can go out and read information and pull CPU information and whole memory information, the default password is public. Now, that was slick, wasn't it? And you'll never guess what the private password is. Sometimes, we refer to these passwords as just community strings.
For most of the devices we're monitoring, IT guys have come up with an administrative username and password or possibly even, say, a switch, a router, or a wireless access point. They must link it up and say, Only these users are allowed through, or these computers are allowed through, which means information is being stored somewhere on that box and SNMP is designed to extrapolate that.
They then came out with version three, which is the latest version of the protocol. There's a lot of emphasis being placed on the area of authentication and privacy. So, we can select or specify restricted user access. We can also encrypt data on the fly. This does require more complexity because we must configure it to do these things, which is the other issue we have to kind of fight here. After all, some security holes can be created.
A very common issue I see out there is many IT guys going off and purchasing the device that supports SNMP. What they don't realize is that, by default, versions one and two have backward compatibility enabled. If you must do this, disable versions one and two unless you don't mind somebody pulling off information. Now, you may be thinking, what type of information could they pull off a device like this? Well, they can pull off quite a bit. They can look at enough information that puts your network at risk. They could very easily use it to grab the routing tables of routers; they can change your configurations if the defaults are in place because the private community string gives it the right permissions. If it's a host machine, they could also look at file shares, ARP tables, and traffic statistics.
We can use Management Information Base (MIB) here, a virtualized database that provides descriptions of the network objects that can be managed through SNMP. It's done hierarchically and each of the objects in the MIBs is dressed in what they refer to as OIDs. OID is short for object identifier. It is a numeric name that's given to objects inside of the MIB so that it can uniquely identify the objects that are present within the hierarchy. It's used by SNMP to convert the OIDs into plain human language.
Microsoft has a list of MIBs they include on the server platform. The most utilized is for DHCP. It monitors traffic between a DHCP server and the clients. There's one for WINS, which is being deprecated at the time of writing. There's one for hosts, which helps you monitor the resources, CPU, network cards, memory, and hard drives on host resources. We also have the LNMIB, which contains the different types of objects for workstation and server services.
Enumerating via LDAP
So, what is LDAP? The reason why it sounds familiar to us is because we use it as a database to store user account information and object information about our network. Microsoft utilizes it in Active Directory. Novell e-directory also utilizes it and, of course, Apple uses Open Directory. Now, this is the technology that contains or stores our user accounts and our computer accounts. From an Active Directory perspective, it contains/stores everything that's involved in our Microsoft platform.
Some people think Microsoft stole this technology from Novell, but LDAP is an open standard. Novell followed it first with e-directory. Microsoft then followed up behind them by using their implementation, called Active Directory. Because these are open standards, there's a lot of similarity between the names and the syntax being utilized.
Now, full disclosure here... I'm not a big fan of Apple, but Apple's Open Directory is also another implementation of LDAP. They're using LDAP there, which includes an Apple password server, and they also use Kerberos 5. Technically, it's a form of what we refer to as open LDAP, an open source implementation of LDAP. It's platform-independent. Linux, Solaris, Microsoft, HP, HP UX, and Android use LDAP.
Understanding LDAP
Let's look at what's behind LDAP. There are what's referred to as Directory System Attendant (DSA) ports. It's what the client uses to start an LDAP session by connecting to an LDAP server. By default, this port is on TCP and UDP 389. If by chance, they're using SSL, they are technically using LDAP, which is utilized on port 636.
There's another service called the global catalog, which is simply a smaller or a stripped-down version of the full database. When you open an email client such as Outlook and hit I'd like to create a new email and you hit the To box, Outlook queries – via exchange – the global catalog server and extrapolates some of the basic information, such as the username and email address.
By default, those ports are set to communicate on TCP and UDP 3268. Again, if you're using any type of encryption, it's done on port 3269.
The structure is technically based on what's referred to as the X 500 model, which has been around for ages. What we mean here is that this database, since it's based on this model, has what's referred to as classes.
Classes
Classes are a way of looking at objects. For example, I can have a class that represents users, have another class that represents groups, and another class that represents computers. See where I'm going here? Classes represent objects. Each of those classes has its own set of attributes. For example, in the user class, the attributes would include first name, last name, city, state, and ZIP code. These classes, attributes, and objects can be found inside of an LDAP environment by using what we refer to as a unique identifier or distinguished name.
A distinguished name is very distinctive; every object must be its own entity; you can't have duplicating objects. So, in the case of a user whose name is Bruce Wayne, who belongs to a Gotham.com domain, his distinguished name or unique identifier would be listed as cn=Bruce Wayne,dc=gotham,dc=com. Within the distinguished name, cn stands for Common Name, and dc stands for Domain Component. You'll often see ou as well in here, which stands for Organizational Unit. So, that would be represented as gotham.com or Gotham City, if the last dc was equal to city. You must understand distinguished names, especially if you start enumerating to find out where they're located.
What can we learn from LDAP?
There's a lot because you can mostly query an LDAP server anonymously.
Note
Good IT guys ensure you can't anonymously hit the domain controller, but when you think about the domain controllers, they are there to ask for authentication. So, typically, anonymity is allowed.
Some of the things we can find out would include group names. When we see these group names, we could extrapolate users that are a member of that group. I can even pull up individual users. Now, because I can pull up these names, I should also be able to check the account information, such as the other attributes that are associated with these objects, the city's state, ZIP code, login hours, and password reset thresholds. Again, most attributes can be looked at very easily.
We can also look at system names, which is where I come back to naming your systems – making sure you don't give away what they are. I know I've shown you my environment where I have Batcave DC1; you can tell it's a domain controller. However, if mine was an actual production environment for a company, I would never do something like that. However, still enumerating through LDAP, I can easily determine which box is a domain controller.
With tools such as JXplore and Hyena (Figure 5.3), I can pull up the Active Directory schema (the layout, though you can think of it as an Excel spreadsheet that lays out attributes and classes). I should not only see the schema, but also the classes. Therefore, I should be able to drill into user accounts, group accounts, server names, and more:

Figure 5.3 – Results from Hyena regarding an Active Directory infrastructure
We'll discuss Network Time Protocol next.
Network Time Protocol
Okay; guess what? We can enumerate using time! There's a protocol out there that our computers use to synchronize the time between each other. It's called Network Time Protocol (NTP). Now, you may be thinking, Dale, you cannot possibly have a quote about this. Well, guess again. Cindy Lauper said, If you're lost, you can look and you will find me, time after time. When it comes to hacking, the things that you don't expect end up giving up information.
NTP is a protocol that we use for synchronizing our clocks between all the systems in a LAN network. This has been around for decades, having been developed in 1981 by David Mills. In a domain, one of the most important settings will be time, and all the computers in the domain need to be within a certain timeframe. For example, in the Microsoft world, the computers or the desktops themselves can't be more than 5 minutes out of sync. Now, technically, domain controllers use NTP with what they refer to as UTC, which is Coordinated Universal Time.
UTC is independent of time zones and enables NTP to be used anywhere in the world, regardless of time zone settings. That's why they're able to keep up, whether you're in Mountain Standard Time or Eastern Time and so on. In a typical Microsoft environment, there's going to be one computer that is flagged as the NTP server for the entire domain. It's referred to as a PDC emulator, which is also known as one of the most flexible single master operations (FSMO) roles. This is the machine that oversees time, and it gets its time from the BIOS clock, which is the default. A best practice of Microsoft is to get the PDC emulator server to synchronize with an atomic clock on the internet. Now, all this communication is taking place on a specific port, and that is port UDP number 123. This port needs to make sure that it's open so that all the domain controllers will synchronize themselves with the PDC emulator and that all the domain member's servers and domain workstations are synchronized with one of the domain controllers.
You need to ensure that port 123 on UDP is accessible. In a domain, time synchronization takes place when the Windows time server turns on during system startup and, every now and then, as the system is running. NTP itself is extremely accurate. And when I say extremely accurate, it depends on the network that it's synchronizing across. If it's a private network, it can synchronize the machines to be within 200 microseconds of each other. And in a public network, it does slow down a bit to under 10 milliseconds.
Now, these computers, which are talking to each other to synchronize their time, open them up for enumeration. So, what can we learn from NTP? Well, we can do a lot of things, including pulling a list of hosts off an NTP server because they're all reporting into the NTP server to make sure they're synchronized. There will be some residual information listing hostnames and with those, we should also be able to get IP addresses listed. We may even be able to pull off system names and we will even see operating systems being displayed.
With basic NTP commands, we should be able to trace the chain of NTP servers, as well as query the NTP daemon and its current state, and monitor the NTP daemon. NTP attacks are primarily Denial of Service (DoS) based to wreak havoc on an organization.
Enumerating using SMTP
Who would think a simple protocol that we use in day-to-day life, such as SMTP, could reveal so much about a network? A famous T-shirt went around at Blackhat several years ago. Most people didn't understand the meaning. It simply said I read your email.:

Figure 5.4 – I read your email T-shirt from Blackhat
That's so true. Normally, email is transmitted in clear text, meaning that messages are readable. As email servers communicate with each other, they also transmit information via the SMTP protocol, which can be used to further enumerate your network.
The purpose of this is not necessarily to read people's emails, even though that could give up a lot of information. It's more about looking at what we refer to as the headers of the email, which is the information that gets attached to the beginning of the email during transit, which exposes quite a bit.
So, what is SMTP? It's simply a protocol we use for delivering emails between email servers and across the internet. It utilizes a process referred to as store and forward, which means that the SMTP protocol moves your email on and across the networks. It uses DNS to look up a specific type of record, called an MX record, to identify the server it needs to forward or store the email in. It also works closely with Mail Transfer Agents (MTAs) to ensure it sends the email to the right computer and email inbox. SMTP directs how your email moves from your computer's MTA to an MTA of another computer or even several computers.
I know this is a bit confusing but because all of this happens in the background, we don't have to worry about it. Once the email gets inside our network infrastructure, we typically use other types of protocols. For example, we might use POP, IMAP, or MAPI to deliver the emails internally. However, externally, out on the internet, SMTP is the big bad boy of the block. SMTP uses a couple of ports, including port 25 and port 587 for submission.
Some commands take place between the servers to communicate and deliver emails. There is a set of codes that help simplify those communications. When you send an email message out, it gets converted into strings of text that are separated by these code words (their numbers), which identify the purpose of each of the sections being transmitted.
Typically, only other SMTP servers understand what those commands are as the message travels toward its destination. Sometimes, it passes through several computers, as well as their individual MTAs. It may also be stored briefly before moving on to the next computer within that path.
Some of those commands include specifying the email address of the sender. This command also tells the SMTP server that a new email is starting and makes these SMTP servers reset all their states and buffers. There's also a receipt to the recipient of the email. There's also the command data, which starts transferring the email message itself. It will typically receive the attachments and the body text. Once the SMTP server sends the email across, it waits for a specific code to verify that the destination server received it. This verification is typically done with an acceptance code called a 250 reply code, which means everything is okay. There's also a verifier, which asks the server to confirm or verify that a specific username or mailbox exists.
If you're starting to think like I've been trying to teach you to think, think about how that command can be useful to you. One of these commands can be used to probe for login names on servers, as well as possible groups.
Servers that ignore the verify command will usually send some type of reply, but they will not send information the client is looking or asking for. The fact remains that either a yes or a no gives me quite a bit of data.
We also have the expanded command, which is like the verify command, except for in the case of a mailing list, it shows the members of that mailing list. The SMTP expand command causes a sent mail to expand to all the recipients and makes sure each of those recipients gets one of those email messages that were initially in the data section.
Knowing that, what could we possibly learn from SMTP? Well, we can download a list of names off the internet. This list could have been utilized to verify what users are valid within the network and which ones are not. This is how a lot of spammers clean up their spam lists. It can also help me expose a possible target, making sure that it's a valid login name.
Next, we'll discuss DNS enumeration.
The golden ticket – DNS
When it comes to enumeration, one of the most revealing things you can do is get a hold of all the computer names and IP addresses on the network in one shot. We can do that with DNS enumeration. DNS is responsible for turning names into IP addresses. What's in a name?, William Shakespeare would ask. Well, in this case, everything, because what DNS holds for me can reveal a ton of information. I can see server names, what services are being offered up, and I can identify domain controllers if I need to, as well as websites or SQL servers.
Most of the network connectivity that takes place there, as far as computers figuring out where things are located goes, is handled by DNS. If I can enumerate that, I can pull a plethora of information:
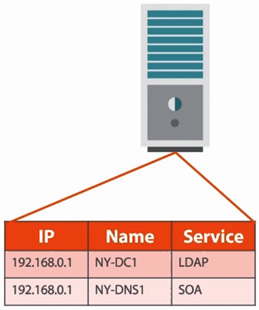
Figure 5.5 – DNS records associated with the services that are installed
As you can see, we have 192.168.0.1, which is resolved to the computer name of NYC-DC1. It happens to be running LDAP. What that tells me is that when I'm trying to log into a domain environment, I need to find an LDAP server. It also tells me that the LDAP server is equal to NY-DC1, which is equal to an IP address, and I can make the connection. In the case of the bottom entry, 192.168.0.2, this tells me that's a server whose name is NY-DNS1, which is my Start of Authority (SoA).
With enumeration, we can go through and look up the records and identify what records are registered with which computers. We can also do something called cache snooping. Cache snooping is where the DNS server resolves names to IP addresses for client machines. For example, if I say I'd like to go to www.yahoo.com, I can submit that entry to my DNS server and it will go and resolve that, get an IP address, and submit it back to me. That information is stored inside the cache memory of my computer. If I can snoop that cache, especially for an internal DNS server, I can see what computer names have been resolved by this box. We can also use a Google lookup. If I can enumerate via Google's DNS servers, I might be able to find out a lot about your infrastructure, especially if you have subdomains.
Reverse lookups
We also have reverse lookup capabilities. When normal name resolution takes place, we have a name. I'm trying to go to yahoo.com, and in return, I get an IP address from the DNS server. Reverse lookup is the opposite, where we have an IP and I want to know what name is associated with that IP address. I have an IP address of 192.168.0.1, but I have no idea what the computer name is. This reverse lookup is done with what's referred to as a pointer record, and we can do this against either IPv4 or IPv6 addresses. We can also do zone walking. Zone walking isn't difficult to understand. This is a technique that helps us reveal internal records if the zone is not properly configured. We can ask, what subdomains do you have behind you? This can help us map network hosts by enumerating the contents of the zone.
Zone transfers
This is the big bad boy. If I can do this with your DNS servers, look out – I'm going to be in heaven. When I teach the Microsoft Server platform, I talk about how to set up a DNS server. One of the things that we do is set up the one DNS server to replicate only with a secondary DNS server. We want to make sure that it only replicates with that second DNS server. The reason behind this is that, if it's not set up correctly, an attacker will attempt to contact your DNS server and say, Hey, would you please replicate with me and tell me who you've got because I don't have anybody in my database? Now, I have a complete record and map of your environment, including MX records, hostnames, and all kinds of other records. This can help me do something later called DNS poisoning, where I'm going to put invalid records into your DNS zone.
DNS records
So, what's behind DNS? Well, we know that it's a database itself that contains computer names and their IP addresses. It operates on port UDP 53, as well as TCP 53. Typically, we use UDP port 53 for doing standard lookups such as Hey, I need yahoo.com's IP address, where zone transfers are typically done through TCP port 53. The reason why we use UDP is because it's a much faster resolution. We'll look at some of the records in detail next.
A records
So far, we have mentioned that the database itself consists of multiple records that point to IP addresses, the names these records help identify, and, in some cases, the services that are running. One of those records is an A record, or as the Canadians would say, a record, eh? This is simply just a hostname being resolved to an IP address.
AAAA records
These are the same things as A records, except instead of pointing to IPv4 addresses, they point to IPv6 records.
Side Note
The Fonz is a big fan of AAAA records. AAAAAAAY! Okay, for you young ones out there, if you don't know what that reference was, go Google it – Happy Days, The Fonz.
CNAME records
A CNAME record is an alias that points to another A record. So, for example, my A record or AAAA record could be batcave and pointing to an IP address, but maybe I have another name for that same computer, which I'm going to call www. So, whether somebody types in www or batcave, they will go to the same IP address/location. So, a CNAME record points to the A record reference.
MX records
Then, we have MX records. No, not motocross. These are mail exchange records. This helps us identify the server/servers that oversee sending and receiving emails.
NS records
We also have NS, which are name servers. Hey, name servers! If an attacker can find those records, they would be the IPs of the DNS servers that I'd want to try to enumerate with. This is a major score here.
SOA records
We also have SOA, which is the primary DNS server. This would be another record I would want to get a hold of and see if I could do a zone transfer with.
PTR records
We also have PTR records, also known as pointer records. Again, this is the reverse lookup, so if we only have an IP address and we don't know the computer name, or we don't know what the hostname is, if I can do a reverse lookup, I'll be able to extrapolate that information.
SRV records
Then, we have something called SRV records, or service records. These service records record what services are running on which machines. For example, in a Microsoft Exchange environment, if I open Outlook, create a new email, and hit my little To button, I will see the big list of email addresses for my company:
Figure 5.6 – Global Address Book populated by a Global Catalog Server
Well, what happened is that my computer went and looked at the DNS to find a computer on the network that offers the global catalog service. It identifies, contacts, resolves, and gives me back email address information.
Sum it up
So, what can we learn from DNS? Folks, it's the mother lode – it's the secret treasure of enumeration. This is because, in one fell swoop, I can find out every single computer name on your network, their IP addresses, and the services they're running, which all help me determine which vulnerabilities might be out there that I could use as a point of entry. Now, we can also pick up, as I mentioned previously, the server names and workstations. Believe it or not, sometimes, IT guys use their workstations to, for example, monitor network traffic. I want to know what that box is, hopefully so that I can avoid it. I should also be able to see which services are running on which servers. Again, I can find an LDAP server, which would be my domain controller, so I can find a global catalog server or a Kerberos server. Once I have a list of all your domain controllers, I'm going to go back (remember when we talked about doing NetBIOS enumeration?), where maybe I can discover what OS is being used. If it's a 2012 server, I'm going to get giddy inside because that's an older OS that's probably not patched or Microsoft stopped supporting it.
Oh wait, there's more!
There are more ways we can enumerate; it's not limited to just the Windows platform. They work on almost all devices; none are safe. It cracks me up when friends and family members tell me how they feel safe because they don't run Windows, and that they're running Linux or a version of Unix. But here's the dirty secret; if it deals with a protocol, you are not secure! You are dead wrong if you think any operating system or device is safe. There are different ways to attack all types of boxes, whether it's a Linux box, a Unix box, a Cisco router, and so on. In one of their old marketing campaigns, Apple bragged that they were virus-free—they don't get malware. Today, they know better. In Golden Eye, a 1995 spy film, a hacker named Boris Grishenko would scream, I'm invincible! whenever he was onto something. Toward the end of the movie – spoiler alert – something unpleasant happens to him. The same applies to some of these operating systems today, giving us a sense of invincibility.
IPsec
IPsec is a commonly implemented technology for gateway-to-gateway, LAN-to-LAN, and even VPN-based enterprises. Most of the IPsec-based VPNs use the Internet Security Association Key Management Protocol (ISAKMP). It's used to establish, negotiate, modify, and delete SAs, as well as the cryptographic keys in a VPN environment.
So, what does it need from a hacking perspective? Well, this is simple. An attacker can perform a simple direct scan for the ISAKMP protocol, which uses UDP port 500. We could use tools such as Nmap here.
VoIP enumeration
This is an interesting enumeration. VoIP is replacing most of the traditional telephone services in both corporate and home environments. The overall concept here is that VoIP is utilizing your network or internet access, and it does so through Session Initiation Protocol (SIP), one of the protocols that VoIP uses to perform voice calls, video calls, and so on.
SIP uses UDP or TCP ports 2000, 2001, 5050, and 5061. There are several tools out there that you can use to enumerate VoIP. Metasploit has some built-in tools. There are also tools such as SIPvicious, an auditing tool that can be used to scan phone systems by performing an invite scan. And, of course, the attacker could then combine this invite scan with a call command to determine the weak passwords that are used to connect to a particular phone host or a PBX network. Another popular tool out there is svmap, a free, open source scanner we use to identify different SIP devices and PBX servers on a particular network.
If you think outside the box and think about these different VoIP solutions and the information they may communicate across the internet, you might look at doing some Google hacking.
Enumerating with Remote Procedure Call (RPC)
RPC is a technology we use to create distributed client-server programs. It allows the client and the server to communicate via these programs.
You can fire up Kali if you want and use Nmap. The command that you would use would be nmap -p 135. Then, you would specify the target machine. In our case, it would be 192.168.01-254. If you suspect a particular target machine, you could just type in the full IP address of the target machine.
The countermeasures
Countermeasures are designed to protect a network or system from an attack by either preventing the attack from happening or detecting when it has happened. This enables security professionals to take corrective action to ensure their systems remain secure. Countermeasures must be taken seriously because once an attacker has enumerated a network, penetrating the system becomes significantly easier.
Defaults and NetBIOS
When it comes to defaults, we're talking about default settings – whether it's the default settings for NetBIOS, your wireless access point, or SQL database defaults. The rule is: do not create a security hole by leaving default username and passwords or default settings in place. Change them. For example, I get into my servers via remote desktop all the time, but I don't use the default ports. I've changed them up. Likewise, be aware of your ports. Of course, you can't change some of them. I can't change the DNS port unless I implement something such as a socket pool, a feature of the Windows Server platform that randomizes the ports, but that's another book.
Also, if you don't want shares to be accessible to users on a particular box, then turn off your Server Message Block (SMB). Now, you wouldn't want to do that to a file server.
SNMP
As far as countermeasures go for SNMP, remember that this is the protocol that allows us to monitor and manage network devices as well as servers. If you don't need it, turn it off. If you're going to have it turned on, make sure that you at least start using version 3 because it has better security associated with it.
Another thing you can do from the Windows Server platform is use a group policy, which allows us to control settings on servers. I would also look at the additional restrictions for anonymous connections. If you have any older servers, have them locked down (for the love of Pete, update them). Also, block port 161, both TCP and UDP.
Alternatively, if you still need to use SNMP, go to your firewall rules and allow 161 to be opened, but only to specific machines, which would maybe be your monitoring server. This also goes back to the aspect of when it comes to SNMP, don't install the agent on a device you will not use it on. You don't necessarily need to monitor every single device. If you are going to turn it on, one of the things you may want to look at is implementing IPsec filtering, which encrypts the traffic going back and forth between the agent and the server monitor. And of course, be very careful about any quick-fix solutions by vendors saying that you need to open a null session because null sessions can be extremely dangerous.
LDAP
LDAP is the protocol that we use to authenticate users and store user accounts and objects in Active Directory, at least from Microsoft's perspective. Other LDAP services include open LDAP and several others, but they all use the same protocol.
One of the things you want to do is separate the email address from login names. While you're at it, don't use the default, which is typically the login name, which is their email address. Why? Because, as an attacker, I will go to your website and see if you list email addresses for some of your company officers or employees. I will then go through and try those as login names within your network. It's shocking how many companies still use an email address schema for logins.
Note
If you're not sure about this one, throw your three-finger salute on your computer (Ctrl + Alt + Delete) and log off. Now, if my login name is normally Bwayne and my domain is gotham.com, odds are that if I use [email protected] instead for my login in and it works, you might want to rethink your Active Directory environment!
Now, you may also need to remember that LDAP traffic is unsecured when it goes across the wire. So, we may want to look at using SSL to encrypt our traffic. Another thing that I'm a big fan of is encrypted drives that store the LDAP database using BitLocker, which is a great solution. Full disk encryption, or another drive encryption technology, is a great idea to ensure that if somebody does get physical access to it, they cannot access the information. And hey, BitLocker is free! #BonusPoints.
Network Time Protocol (NTP)
All the computers on the network get their time from a centralized location. This depends on whether you're using a Windows product or possibly a Cisco router as your NTP server or Juniper device because Windows doesn't use the NTP protocol. This means it's not susceptible to the NTP vulnerabilities that are out there, but it has its own problems.
When it comes to NTP, make sure you watch your ports. Remember that the default port is 123, which is easy to remember. You also need to understand what software is installed or what patches have been applied, especially to these hardware devices. Sometimes, we install software, and it opens ports without our knowledge because maybe they need to use an NTP protocol. And of course, use those commands that we talked about to check your own NTP Master so that you understand what information is being exposed.
Simple Mail Transfer Protocol (SMTP)
One of the things we want to do is ensure we have disabled open relays. For most of the email servers out there, the open relays are already turned off. It's kind of funny because back in the old days, they were turned on, to make it easy for you. But if you are familiar with the technology triangle, when we make things easier, we end up opening more security holes. Also, drop unknown recipients. Again, most of the products out there that handle email will do reverse lookups. They will look at the header of the email, which always states the IP address of where it came from, and it'll do a reverse lookup to DNS. And if it doesn't match up, it'll drop it out of there.
DNS
DNS is our name server – it's what resolves a computer name to an IP address. So, first, we want to configure DNS zone transfers to be sent to specific or explicit servers. Also, make sure the hostnames of computers you don't want to be visible to the outside world are not referenced to an IP address in your DNS zone files.
When you check the DNS zone files – that is, you know what names are listed within the database – make sure that you check both internal and external DNS servers. I've seen situations where IT guys have taken the internal database and just simply copied it into the external DNS server to make things easy for themselves.
For the love of Pete, there's a DNS record out there called a HINFO record that specifies the server's type of CPU and operating system. It was designed initially so that applications such as FTP could use special processes when they were communicating with the servers of a known CPU or operating system. But think about that one for a second. If it's a file that's accessible from the outside telling you the server's name and operating system, you're not going to have a very good day.
Summary
In this chapter, we covered a lot of ways to enumerate a targeted network. Some of these methods are caused just by the way networks and the internet are designed to work. From protocols such as LDAP and NTP to services such as NetBIOS and DNS, there's a lot to watch out for. Again, remember what I taught you earlier: you can't stop attackers – you can only slow them down. Don't get discouraged by not being able to stop some of these issues. Instead, be aware of them and monitor them closely.
In the next chapter, we'll look at how attackers find vulnerabilities on our infrastructure and how we can be one step ahead of them by using the same techniques to keep our systems up and secure.
Questions
As we conclude, here is a list of questions for you to test your knowledge regarding this chapter's material. You will find the answers in the Assessments section of the Appendix:
- Which of the following best describes enumeration?
- User and machine name identification
- Cracking passwords
- Recognizing routers and firewalls
- Active network system recognition
- Which function is performed by SMTP?
- Transmitting status information
- Network equipment monitoring
- File transfer
- Sending email messages
- To view NetBIOS information, what command should you use?
- Nmap
- netstat
- nbtstat
- telnet
- __________ is used to synchronize clocks on a network.
- SAM
- NTP
- NetBIOS
- FTP
