Chapter 11: Hacking Wireless Networks
This is a topic I'm passionate about and have a vast background and experience with. In 2001, right after 9/11, I became unemployed. I live in a rural community in northern Utah, and we didn't have a high-speed internet service. I saw a need so decided to start up my own ISP service.
I rented space off the city water tower that can be seen for miles. Since there was no affordable high-speed internet, I decided to offer this service. So, I put two T1 lines into my garage and converted my garage from a standard garage to an office in a server room environment. I put an antenna on top of my roof, pointed it towards the water tower, and then put an array of antennas and access points (APs) on top of the water tower.
The company grew quite fast; it was one of the fastest-growing ISP services in the Mountain West area. We grew it to 600 customers; we got so busy that we ended up having to expand our service and we had to find another cell tower.
The thing about wireless is that a line of sight is critical for a strong signal. A lot of our customers couldn't get access to the internet because they didn't have a line of sight. In the case of the water tower in Syracuse, we put up several different sector-based antennas. We went and added tons of these as the company grew, including an omnidirectional antenna (we'll discuss why omnidirectional is technically not as powerful as sector-based antennas). As the company grew, we added that second tower and put in sector-based antennas as well. We were able to cover an 18 to 20 mile stretch of homes in this rapidly growing area.
After growing this company, I sold it because I saw the writing on the wall; we were finally getting Comcast, which at the time was Qwest, but I think is now CenturyLink. They're doing quite well because we have these new subdivisions popping up and the commercial ISPs can't get out there fast enough.
Kevin Mitnick, a famous hacker, says, New security loopholes are constantly popping up because of wireless networking. The cat-and-mouse game between hackers and system administrators is still in full swing. Just when you think it's safe to get back on the wireless network, we get another issue popping up. Hopefully, as you work your way through this chapter, you'll feel more prepared to deal with the rapidly growing wireless environment.
In this chapter we will cover the following topics:
- The wireless network and its types
- The right encryption can help
- A plethora of attack vectors
- Methodology of wireless hacking
- Hacking Bluetooth
- Countermeasures
Let's begin by discussing insights into the wireless world.
The wireless network and its types
The wireless environment is constantly evolving. As such, let's begin by defining some key terms you will need to know. You've probably heard some of these terms before, but let's review some of them and what the acronyms stand for.
Frequency hopping spread spectrum
Frequency hopping spread spectrum (FHSS) was invented by Hedy Lamarr. She was not only a famous Silver Screen actress but also very intelligent. In fact, she was an inventor. It's kind of funny to watch the documentary about her. She was so beautiful that a lot of men—you must think of the time when she was around—didn't take her seriously as far as some of her inventions were concerned.
FHSS was accomplished by manipulating radio frequencies at irregular intervals between transmissions and receptions, hence hopping.
Her invention also formed an unbreakable code because it was hopping around so nobody could listen in, meaning that classified messages could be transmitted without being intercepted. Typically, FHSS operates within the 900 MHz to 2.4 GHz range.
A variation of FHSS is called adaptive frequency hopping (AFH), which is also known as Bluetooth.
With any type of spread spectrum technology, if you have a lot of devices communicating on the exact same channel, that equals degradation of signal. So, what Hedy Lamarr did is create this technology that allows the channel or the transmission to jump between the different channels. You do this with a hop sequence.
It's extremely difficult for anybody to intercept this traffic. In fact, by looking at this information or looking at a frequency hopping environment with a spectrum analyzer, it just looks like interference. Obviously, the receiving and the sending antennas must be on the same hop count, so they know which channel they are hopping to and the next data packet transmission.
The problem with FHSS is its speed limitation. It is limited to 3 MB. I know you're thinking… That's slow! Well, I know, but back in my day, we offered high-speed internet up to 512 KB and people thought that was blazing fast. They paid me $69 a month for it. It was great. My slowest speed was about 128 KB, and I charged $19.99.
Direct sequence spread spectrum
Direct sequence spread spectrum (DSSS) is probably the most popular one. It has the same channels and the same frequencies, but you must select which channel both the sending and the receiving antennas are going to be on, and they stay there, which obviously makes it easier for someone to intercept traffic.
Because of how the channels overlay with each other, it can also create interference. You could also end up with interference from other wireless devices, such as cordless phones, microwaves, and even fluorescent lamps because they all cause interference.
With these channels, people ask how I select a channel that won't interfere with another channel? Well, believe it or not, there are three sweet spots. Channel 1 does not interfere with Channel 6, and it's the same between 6 and 11. There's a separation. Some people might think, Well, five would be okay because 5 doesn't necessarily interfere with 1. Well, technically, in the spectrum analyzer, that's not a clean separation.
Basic service set identifier
The basic service set identifier (BSSID) consists of the MAC address of the AP that has associated it with a basic service set (BSS). This is often confused with the service set identifier (SSID). Generally, users are unaware of the BSS to which they belong. When a user moves a device, the BSS used by the device could change because of a variation in the range covered by the AP, but this change may not affect the connectivity of the wireless device.
Now, the BSSID, as I mentioned before, deals with the MAC address of that device. What happens is that the BSS address gets incremented, and that is broadcasted and used for communication in the air. If you've got a wireless network that is broadcasting on multiple bandwidths, such as g, n, ac, or ax, it gets incremented again and again so it can be used for each one of those bands.
Even though you're connected to the same SSID that is supported by several APs, a device needs to know which AP to return its packets to.
If you use some type of packet capturing tool, you should be able to see the wireless MAC address floating around in the air, which should flag your hacking senses as an issue for wireless networks. You can also see the APs broadcast in the BSSIDs. This is probably more information than you really need to know; it's just information that is floating around in my head.
SSID
This is what everybody's familiar with when it comes to wireless, right? It's the network name; it can be up to 32 characters in length and it is attached to every single wireless packet that goes out onto the air. This is how you can have multiple APs transmitting data to different systems but dropping just as we see with a normal network environment. If the packet is not destined for that network, it gets dropped—it's the same concept, we just use this SSID because in the air, there's other information floating around, or maybe it's not information, just interference.
Global System for Mobile Communications
The Global System for Mobile Communications (GSM) is an open and digital cellular technology used for mobile communication. It uses four different frequency bandwidths: 850 MHz, 900 MHz, 1,800 MHz, and 1,900 MHz.
Hotspot
These are places where wireless networks are available for public use. Hotspots refer to areas with Wi-Fi availability, where users can enable Wi-Fi on their devices and connect to the internet.
Association
This simply refers to the process of connecting a wireless device to an AP.
MIMO-OFDM
This method affects the spectral efficiency of 4G and 5G wireless communication services. The use of MIMO-OFDM reduces interference and improves the reliability of the channel.
The disadvantages of Wi-Fi
Let's start with the negatives since they are the most significant concerns for us as wireless security experts. From a security perspective, the following are the biggest issues for us with Wi-Fi:
- Upgrades: One disadvantage is, obviously, upgrades. When they come out with a new speed, we're upgrading equipment like crazy, not only at the AP level but also on the devices. Then, we have to worry about whether they're backward compatible, and of course, backward compatibility always means that we have a security risk involved.
- Interference: Not interference from other APs, although that is a concern, but interference from other devices that have nothing to do with wireless networks. Electrical devices can interfere (for example, fluorescent lights, desk fans, and microwaves). Bluetooth devices can interfere, as can cordless phones and anything else that is kind of wireless itself, as well as anything that operates at the same signal level as your wireless devices.
- Public access: Isn't public access an advantage? Well, they want to make it seem that way because I can go down to McDonald's and jump onto the Wi-Fi. In fact, I happened to visit my local Walmart the other day and they had a sticker on the front door that said, Free Wi-Fi at our store. It seems like a good idea to most, but in my mind, I was thinking, This is not good!
You've probably heard this before, but I'll say it again. Please, do yourself a favor: if you see an AP that says, Free Wi-Fi, don't get on it! Most of the time, those are rogue APs, (Figure 11.1), or an attacker trying to get you to hook into their AP. Once you do it, the attacker becomes a man in the middle who can attack you. Isn't that nice of them to give you free Wi-Fi and all they get in exchange is your bank account details?

Figure 11.1 – A Wi-Fi Pineapple from Hak5, a rogue AP
Okay, now that I've most likely let you down and you don't want to use Wi-Fi anymore, let's get to the shiny side of things here.
The advantages of Wi-Fi
Here's a list of the advantages Wi-Fi has to offer:
- Installation: One of the biggest advantages is installation. Put a box up here and I've got access anywhere I want to go; I no longer rely on an Ethernet cable running through a wall or having to reroute cabling for somebody who wants to move their desk in the office. Or, if I buy the next building to expand our business, I don't have to worry about running cables across.
- Easy connectivity: Almost everybody knows how to hook into a Wi-Fi access point or network, but give somebody a crimping tool and some cable and watch the confused look on their face. It's very easy to add devices.
- Mobility: Being able to move around is one of my favorite advantages. As I said before, with installation, I don't have to worry about wanting to move from one room to another, especially in my home. If I want to go out on the back patio and just relax, I can take my laptop with me and sit wherever I want and still be connected.
Types of Wi-Fi networks
Types of Wi-Fi? Isn't it just all wireless? No, not really. Matter of fact, here's where we're going to play around with some terms because, today, we use terms such as APs. These are the different types of Wi-Fi:
- Extension to networks: The first type of Wi-Fi is the extension to networks. What this means initially is APs, which I have emphasized because whenever we say APs, we have this tendency to think of the little Cisco or Linksys, or the D-Link product, for example. We envision these devices as not only APs but also switches and routers. But you can purchase an AP designed to be a bridge to wireless folks, so they gain access to the wired network.
- LAN networks: Another type is to have extension networks designed to communicate with each other. We refer to these as LAN-to-LAN networks and often see this being done between buildings.
- Multiple access point network: This is where we have multiple APs representing the same BSSID. So, no matter where you go within the building or the environment, your traffic is directed back to the same network. To appropriately deploy these, you need to make sure the APs overlap each other as far as coverage is concerned. This makes it so the user can move around or roam between the two connections, never losing connectivity.
- Cellular access networks: This is where we use cellular service to provide access to the internet. Our phones become cellular hotspots and turn into full APs for us so when we're at the airport or out and about, we can turn on the hotspot access on our phone and connect a laptop, tablet, or another type of device to it.
Different Wi-Fi technologies
It all started with the 802.11 family, as explained here:
- 802.11 (Wi-Fi): This standard applies to WLANs and uses FHSS or DSSS as the frequency-hopping spectrum. It was developed to operate on the 2.4 GHz ISM band and supported speeds of 1 Mbps – 2 Mbps. Compared to the speeds we have now, it would take longer to download files and cause challenges with group video calls, online gaming, and streaming.
- 802.11a: This was the first standard to use the 5 GHz range, which allowed faster speeds (up to 54 Mbps) but was really limited by its range. It also was the first time we saw OFDM being used. We mostly saw these used in the business world as the devices weren't cheap.
- 802.11b: This used only DSSS on the 2.4 GHz band and could achieve speeds of 11 Mbps. It was better at penetrating obstacles for a wider coverage area, but its downside was interference caused by other devices such as microwaves, cordless phones, and Bluetooth devices.
- 802.11g: The developers took the best qualities of 802.11a and 802.11b to create the 802.11g standard. It supports a networking bandwidth up to 54 Mbps and operates under the 2.4 GHz band. The devices using this standard are only capable of tapping into the standard under which they operate, which means an 802.11b computer connected to an 802.11g AP can only go as fast as what the b standard allows. On the flip side, a g device connected to a b AP will only go as fast as what the AP offers.
- 802.11n: Wireless-N was developed in 2009 to improve speed and reliability, and extend the range of wireless transmissions. It was the first standard to use multiple-input, multiple-output (MIMO) technology. MIMO products use a series of antennas to receive more data from one device at a time, which results in faster data transmissions. In addition, it was the first to allow the usage of two radio frequencies – 2.4 GHz and 5 GHz. The use of both frequencies makes the 802.11n standard compatible with 802.11a/b/g devices. With all its improved functionalities, 802.11n supported bandwidth speeds up to 600 Mbps and had a theoretical range of 230 ft indoors, which is a huge upgrade from the previous standards.
- 802.11ac: The fifth generation of Wi-Fi was developed to reduce interference in the 2.4 GHz band; it was developed to operate under the 5 GHz band. Most of these devices are advertised as dual-band – but the real deal is that vendors incorporated Wireless-N technology to make ac products compatible with the 2.4 GHz band. It was also the first to use downlink multi-user MIMO (DL MU-MIMO). It took Wireless-N MIMO technology one step further to increase data transmission even more. DL MU-MIMO allows wireless routers to transmit information to multiple devices at the same time, improving bandwidth speeds and reducing latency. With the help of Wireless-N technology, 802.11ac is compatible with 802.11a/b/g/n.
- 802.11ax (Wi-Fi 6): The new kid on the block. It's designed to deliver faster speeds, support more devices simultaneously, decrease latency, improve security, and increase bandwidth. To do so, it includes technologies such as OFDM, MU-MIMO, and 1024-QAM. With all of its improvements, it has a theoretical maximum speed of 14 Gbps. In addition, it operates on the 2.4 and 5 GHz bands, which hasn't been done since 802.11n. This allows it to be compatible with 802.11a/b/g/n/ac. In 2021, Wi-Fi 6 will have a subcategory known as Wi-Fi 6E (Wi-Fi 6 Extended). The FCC has made the 6 GHz frequency available, thanks to Facebook and Google championing the release of another frequency to be opened for public use. Wi-Fi 6E devices will be able to operate on the 2.4, 5, and 6 GHz frequencies. As a result, compatible Wi-Fi devices will benefit from less congested frequency bands.
There are other 802.11 technologies out there, but these are the ones you should focus on.
Wi-Fi authentication modes
This has nothing to do with the type of encryption we're going to be utilizing. When IEEE released the 802.11 standards, they defined two different methods wireless devices could use to authenticate to a wireless access point (WAP) before actual network communication would take place:
- Open System Authentication (OSA): For OSA to work, the SSID of the computer should match the SSID of the WAP. First, the computer or the device sends out a probe request looking to see whether there's an AP out there with that SSID. The AP then responds with a probe response. Next, the system, computer, or device sends a request for authentication. The AP generates an authentication code, usually random, and sends it back in an open system authentication response. At this point, the device accepts that authentication code and sends an association request. Then, the AP responds with an association response, and the system becomes a part of the network as long as the session continues and the computer remains within the range of the original APs.
- Shared key: To connect, a computer sends a request for authentication to an AP. A sequence of characters, called a challenge text, is generated by the AP. The computer then encrypts the challenge text with its Wired Equivalent Privacy (WEP) key and transmits the message back. The AP then decrypts the message and compares it to the result of the original challenge text. If there are no discrepancies, the AP sends an authentication code. The computer or the device is then able to hook into the network so long as the session stays open or if the device remains within range of the original AP. The shared key may look familiar to you because it's utilized primarily for WEP.
So, guess what? It's time to play wireless threats, and the top-dollar question is, which authentication process is the least secure? Is it OSA or shared key? If you selected OSA, you would be wrong. Shared key is the least secure mechanism. The reason behind this is because the shared key is shared, it's transmitted.
Even though OSA sounds like it's worse, we'll use other types of mechanisms to secure the network.
Chalking – ways to identify Wi-Fi networks
Here are some different ways we can identify Wi-Fi networks. To discover them, we can use one of the following methods:
- Warwalking: This is where we have a mobile device with us and we simply walk around a building, and it picks up APs and records information for us.
- Warflying: This is a relatively new concept and, with drones, it'll get even more popular. However, back in my day, they used model rockets, like the ones kids shoot and watch go up in the air. Well, some kids attached a WAP to one of them and shot it up. They picked up like a 15-mile range of WAPs as it went up and came back down.
- Wardriving: Wardriving, as the name suggests, is searching for wireless networks while in a moving vehicle.
So, after we've identified those networks, we want to make sure we can share this information. This is where warchalking came into play. Again, this may be a little bit of a deprecated technology or concept because of what we've done in the digital age; most of the stuff now is online. But it got its start back in 2002 by a gentleman by the name of Matt Jones, and it was inspired by the Great Depression and the homeless community.
When the homeless traveled, they communicated by leaving behind different marks that represented different things so other homeless travelers would know. For example, that it was okay to sleep someplace, that there was a doctor that would help them, or a policeman nearby who kept an eye out. They would make these marks these using chalk or coal to the Brotherhood. Well, guess what? It's still being utilized today, but with Wi-Fi networks; we use different symbols to identify them.
Let's start off by showing you what an open and closed node symbol would look like.
I bet you can't figure out which one's which (Figure 11.2):

Figure 11.2 – Open and closed nodes
Open means it's typically free, while closed means it's somehow locked down.
If it's locked down, we need to identify the encryption that's used. So, either it's a WEP encryption or a paid service. We typically list the speeds with the node identification at the bottom, and we would normally see the SSID above the representation of the node. If by chance they were doing any type of filtering, we would also use this symbol to identify that in this case here, it's a MAC filtered node.
What's funny is that whenever I teach this concept, people say, Dale, I've never seen any of these symbols around. Well, the problem is you haven't been looking for them.
Let me show you. So, what do you have here? You have an open node that's anywhere from 1 to 5 Mb, and its SSID is KYNANCE (Figure 11.3):

Figure 11.3 – Open node
Now, next time you run into some kids (especially my grandkids) with laptops or tablets, you might want to be careful or pay attention to what they're drawing (Figure 11.4):

Figure 11.4 – Kids with tablets
Antenna types
You may be familiar with only one or two of these, so, I want to make sure you understand them. It's amazing! After you study wireless, you'll start looking around as you drive, you'll start to see antennas that you never realized were there before, and they pop up in the strangest of places.
What you're trying to accomplish will determine the type of antenna you want to use.
Omnidirectional antenna
An omnidirectional antenna is a traditional one; everybody knows about it. You have seen something that looks just like these (Figure 11.5). The one on the left is a commercial-grade AP that we install on top of a mast, and the thick one on the right is what we usually see on the back of our AP.

Figure 11.5 – Omnidirectional antenna
Omnidirectional means the signal is transmitted 360 degrees and, by default, it's broadcasted out horizontally, meaning that our beam width starts at the antenna and moves in a horizontal direction (Figure 11.6):

Figure 11.6 – Omnidirectional antenna 360°
We know the signal goes out in a 360-degree pattern. Instead, if I take that antenna and encase it with something highly reflective, that's where we get sector-based antennas. Most of the time, it's just sheet metal. That sheet metal takes the signal that hits it, reflects it, and pushes behind the signal that's already going in that other direction and amplifies (Figure 11.7). It's kind of a cool concept when you think about it—something so simple.

Figure 11.7 – Sheet metal amplification
Parabolic grid antenna
This is what a parabolic grid antenna looks like (Figure 11.8):

Figure 11.8 – Parabolic antenna
You may have seen these quite often. You have your transmitting element in the center and the grid portion is pushing as well as receiving, almost like a big satellite dish receiving the signal and focusing it back to that center arm.
These are also more powerful than omnidirectional antennas and they're typically used for long distances, such as 10 miles or more.
Yagi antenna
This is what a Yagi antenna looks like (Figure 11.9):

Figure 11.9 – Yagi antenna (by Tennen-Gas – own work, CC BY-SA 3.0)
This is used for extremely focused connectivity. With a parabolic antenna, you can be within a couple of degrees and pick up the signal, but with a Yagi antenna, you must be exactly on. Again, this type of antenna is for great distances.
Now that we understand more about wireless signals, let's discuss next how to encrypt those signals more securely.
The right encryption can help
Now that we've deployed our wireless environment, how do we make sure things are still secure? Well, once we've identified our weakness, we'll have strength, and that's when we get dangerous. It's so true because knowing is half the battle. Understanding where your weaknesses are helps to strengthen you.
WEP encryption
Believe it or not, WEP encryption is still heavily used. But, let's not even pretend here, WEP stands for Wired Equivalent Privacy, but it's not. That was the initial goal, and we'll discuss why they didn't achieve it when they implemented or had this ratified.
It was designed to protect us from digital eavesdropping and to help make sure our data was protected.
It also was there to help make sure we prevented anybody from getting on the network via Wi-Fi without being authorized to do so.
To prevent unauthorized access and eavesdropping, it uses a key. The key is the problem because it is used to encrypt the packets before transmission. However, this key is shared, making it kind of a nightmare for us.
So, what happened? First, when they came up with WEP, it was not reviewed by any academia or any type of public review for any type of input, nor were any cryptologists able to review this technology. Back in the day, they were so desperate to get some type of encryption, the result was like people threw things together hoping they would work. As I just mentioned, one of its biggest downfalls is the pre-shared key issue.
One of the reasons it wasn't strong was because of the issue they had with US restrictions on the export of various cryptography technologies. This led to manufacturers restricting their devices to only 64-bit encryption, but WEP only used a 40-bit key. When the restrictions were lifted, it was increased to 128-bit, but again, WEP ended up only using a 104-bit key size. And, even though they came out with 256-bit WEP encryption, which only uses a 232-bit key size, 128-bit remains one of those common implementations today.
The other issue is the fact that WEP used the RC4 algorithm for its encryption. The problem is that RC4 is designed for randomized keys to be encrypted, but WEP is not random at all. You create one shared key, and it's the same for everybody. The result is that WEP can be cracked if enough traffic can be intercepted.
I'm not here to say that WEP is totally useless; I would much rather use WEP than nothing at all. But please, if you're using it anywhere, turn it off. Or, if you're not going to turn it off, let me know the address of your AP. I think I'd like to come to visit you!
Wi-Fi Protected Access
Wi-Fi Protected Access (WPA) is like WEP all grown up, with its big boy pants on. Well, it has given us better protection than we experienced with WEP. It was formally adopted back in 2003, which was about a year before WEP was officially retired. So, it was designed to patch the issues we had with WEP.
The most common WPA configuration is using a WPA pre-shared key (PSK). These keys are 256 bits, which is much stronger than the 64-bit and 128-bit keys we saw with WEP.
One of the biggest changes in implementing WPA included a message integrity check (MIC). What we mean by that, in non-geek terms, is the ability to check to see if an attacker had captured or altered the packets as it was passing from the AP to the client.
We do that with the Temporal Key Integrity Protocol (TKIP). What's TKIP? Well, under TKIP, a client starts with a 128-bit temporal key that is then combined with the client's MAC address. Once the TKIP has been created, it wraps itself around WEP because that's all WPA is—fixing WEP—and then unique encryption keys are created for each wireless frame, creating a more secure network connection.
However, despite the improvement WPA gives us over WEP, the ghost of WEP still haunts WPA. The cool thing about WPA back in the day is it didn't require you to go off and buy new hardware. It was simply a firmware upgrade on the networking devices. But here's the downside to it: because it had to recycle certain elements used in WEP, it ended up creating exploits. In fact, today, WPA by itself is not considered secure, just like WEP.
WPA2
Then, along came our big brother, WPA2, which created much stronger protection for us.
WPA comes in two different types.
WPA-Personal
The first type of WPA is referred to as WPA-Personal. It uses a PSK, a 256-bit key for encryption, and the encryption is based on anywhere from 8 to 63 ASCII characters.
You have probably set up an AP before where you've gone through and created a passcode or a passphrase for your wireless network. Well, it's those characters that are used to help create that 256-bit key.
If you think you're safe because you are using WPA2, think again, because some of the same vulnerabilities that were the big hole in WPA armor exist with WPA2.
If on your Wi-Fi routers you're using Wi-Fi Protected Setup (WPS), it's that little button. All you must do is hit this button and you'll get your device to hook right up. WPS is burnt into the firmware, it doesn't change or rotate, and it's a code.
I could still try to break into your WPA2 network by using brute force attacks and it could take anywhere from several hours to a couple of days, maybe even a week. However, if I go after your WPS, this vulnerability can be hacked by some software called Reaver. I can crack that in anywhere from 2 to 14 hours depending on my system. So, if you can, try to disable WPS.
WPA2-Enterprise
This other flavor of WPA2 is referred to as WPA2-Enterprise. WPA2-Enterprise addresses the concerns regarding the distribution and management of those static passphrases. It's the control access on a per-account basis by tying into some type of authentication service. Those are typically handled by either the Extensible Authentication Protocol (EAP) or the Remote Authentication Dial-In User Service (RADIUS).
This mode requires credentials such as a user's name, a certificate, and maybe a one-time password. The authentication occurs between the station and this centralized authenticating server.
The AP or the wireless controller simply monitors the connection and directs the authentication packets to the authentication server. Typically, this is going to be a RADIUS box.
This is all based on the enterprise environment, using the Advanced Encryption Standard (AES) with the Cipher Block Chaining MAC Protocol (CCMP), which is extremely strong compared to Rivest Cipher 4 (RC4).
WPA3
Let's take a look at advances that have been made in our newest WPA version. WPA3 has capabilities necessary to support various deployment sizes that range from large corporate network environments down to a simple home network.
It uses encryption algorithms such as AES and TKIP, which help to ensure cryptographic consistency, and it has enhanced network resilience by using protected management frames (PMF) to deliver a strong defense against eavesdropping and forging attacks. It rejects outdated legacy protocols. Some pretty cool stuff – and it's about time.
How it relates to WPA 2
First, WPA3's encryption/authentication security protocol is stronger and builds upon the security protocols in WP2. In this new version, there have been advancements that provide cutting-edge features to simplify Wi-Fi security. One of the reasons it's stronger is that it can be used to implement a layered security strategy that can protect all aspects of a Wi-Fi network. WPA2 was not able to protect users' passwords through the use of an offline dictionary attack if someone had enough time and processing power. Attackers would have to gain access to the password through a brute force attack by checking all possible combinations. In WPA3, passwords are encrypted through an improved key handshake protocol. The Dragonfly handshake/Society of Automotive Engineers (SAE) protocol is mandatory for WPA3 certification, and this reduces the risk of a dictionary attack.
It's important to note that the new authentication process requires devices to be in close physical proximity to the router, which means that your neighbor can't hack your wireless network if they aren't close to your house.
Just like WPA2, WPA3 also comes in two operation modes (Personal and Enterprise). If you have a device that doesn't support WPA3, the network will stay in WPA2 mode.
Weak initialization vectors
So, if things are encrypted, how do we break that encryption? Well, that's going to depend on the type of encryption you're using. When it comes to WEP, one of the biggest issues we have is the feeble initialization vectors (IVs) that are out there.
First is the fact that WEP uses RC4. While RC4 itself isn't weak, the problem is how WEP uses RC4. It utilizes it using a key scheduling algorithm (KSA) to create the IV and it is added to the base key.
Unfortunately, the first few bits are clear text, so it becomes very easy to predict what the IVs are going to be. Therefore, if I intercept enough traffic with WEP, I'll be able to figure out what your key is.
The other issue is the IVs are not explicit. They're reused over and over on your devices. So, if you get one key, you have everything. It's like one ring to rule them all.
Another weakness in the IV is the IV itself is appended to the beginning of the security key, which makes it vulnerable to Fluher, Mantin, and Shamir (FMS) attacks. It takes advantage of the weaknesses in the RC4 key scheduling algorithm to reconstruct the messages to determine what the key is, and we do this with simple scripts. It's so simple. In fact, a lot of the tools we use for hacking wireless networks, such as Aircrack-ng and AirSnort, can exploit this type of weakness.
Another weakness in the IV is the fact there's no way to detect that the message has been tampered with. There might be some other methods, such as check values, that can look at the message integrity, but they have their own drawbacks as well.
One of the most critical weaknesses is probably the use of short IVs. Basically, within a few hours of traffic—I can simulate the traffic to speed the timeframe up—the same IV will repeat itself. And, I can see those repeats using sniffing tools, capture the encrypted packets with the same key, and then use a tool such as Aircrack-ng or WEPCrack to decrypt the weak IV, which would then give me the base key. Again, the base key is the base key for everyone. So, knowing that these IVs exist, it's very easy to crack WEP.
Now, because WPA is basically a grownup version of WEP, it does make it a little bit tougher, but I can still brute force attack it if I'm able to capture enough packets.
The same applies to doing an offline attack. To implement this, we must be near the AP—only for a matter of seconds—to capture the WPA and the WPA2 authentication handshake. By capturing the right number of packets, we can then try to crack this offline.
The biggest advantage an attacker has is time. As an attacker, I don't have to sit there and be on your network consistently.
If you want to get tricky, we can do something called a de-authentication attack. With this, I'll find an active client and force them off or disconnect them from the AP. I'll then use some of my tools to capture the authentication packet when the client tries to reconnect to the AP, which normally happens within just a few seconds of it being disconnected. That authentication packet includes the Pairwise Master Key (PMK), which I can then brute force or dictionary attack to recover the WPA key. And, just like WEP, we can brute force the WPA keys.
Some of the tools we utilize for this process include Aircrack-ng, KisMAC, and Reaver, which grabs the WPS.
Security measures
Okay, it sounds like we should just never use Wi-Fi now. Well, no, that's not really what I'm saying, because we can do some things to defend ourselves against cracking on wireless.
Again, there is nothing that is completely secure but knowing what your risks are helps to make you stronger or safer. So, let's talk about how implementing some very basic things can beef up your security. Most people have the tendency of overlooking them, yet they can help you in securing your wireless network.
If you make the passphrases in WPA complicated, make them long as well. Get a passphrase with 20 characters, if not longer. Don't use real words that can be found in a dictionary.
Lastly, look at the client settings. Use WPA2 with AES and cipher block chaining (CCM) encryption only. Also, when it comes to the client settings for the validation server, make sure you use a specific server address.
Next, let's discuss threats from wireless technology.
A plethora of attack vectors
Wireless is a great technology. So, how do we evaluate the threats, or the possibility of threats, that we expose our networks to?
Let's look at some of the integrity attacks you could be a victim of. They can be summed up in several different categories.
Access control attacks
These types of attacks are designed to gain access to your network without your wireless security solutions detecting them or being able to bypass them altogether:
- Wardriving – This is basically driving around and using a device to search for the web beacons; these are little packets in the air that make it so your authorized devices know they're in range of your SSID. I personally use PassMark's WirelessMon, but other tools include Kismet, inSSIDer, and the classic NetStumbler.
- Rogue APs – We'll dive into this one a little later, but, for now, let's just describe them as unauthorized APs that a hacker brings into your environment.
- MAC spoofing – MAC spoofing occurs when an attacker searches a network for legitimate MAC addresses and then seeks to access and take control.
- AP misconfiguration – Yep, it's an AP that is configured incorrectly, either by the lack of knowledge or failing to configure something, for example, by using default settings.
- Ad-Hoc connection – This is again a way for an attacker to connect directly with your devices without an AP and then piggyback off your connection into your network, kind of like a NAT connection of sort.
- Promiscuous mode client – Attackers take advantage of the fact that your device will connect to the strongest signal, which could be their fake AP, and then forward your requests to the real AP; this is like an evil twin attack.
- Client misconfiguration – Remember the AP misconfiguration we just talked about? Same concept here, but on the client device instead.
- Unauthorized connection – These are unauthorized clients that connect to your APs. An attacker can gain access to your network through your APs if the security is weak.
Integrity attacks
Let's look at some of the integrity attacks you could be a victim of. They can be summed up in several different categories:
- Data frame injection – This is where we construct and send out forged wireless frames on the network.
- WEP injection – If you've been around wireless at all, you probably understand what this is. Basically, we construct and distribute forged WEP encryption keys.
- Bit flipping attack – This is where the attacker sniffs a frame on the wireless network. The attacker transmits the modified frame, and the AP accepts the modified frame, but when the destination receiver goes to decapsulate the frame, the checksum fails, and the receiver generates a predictable Internet Control Message Protocol (ICMP) error. The attacker simply sniffs the network LAN looking for the encryption error and, upon receiving the message of the error, the attacker can derive the keystream, which is the same thing we do with the IV replay attack.
- Data replay – This is where we simply capture the data frames and replay the frames later.
- RADIUS replay – This is where we capture the communication channel between the AP and the authentication server. Remember we talked about RADIUS servers? We can later replay that interaction to see if we can gain access.
- Wireless network viruses – Believe it or not, these are wireless network viruses. These aren't viruses that target computers and nodes; they target APs. One of the most popular ones is called Chameleon. When it attacks an AP, it doesn't affect how it works. Instead, it is able to collect and report the credentials of all other Wi-Fi users who are connected to it, and it can spread to other APs outside your wireless infrastructure. So yeah, your neighbor's AP could infect your AP.
Confidentiality attacks
These attacks are designed to intercept sensitive data. I told you it was going to get scary! These attacks include the following:
- Eavesdropping – This is where we're going to capture and look at traffic to see if we can obtain any type of potentially sensitive information.
- Traffic analysis – This can tell us quite a bit about the network infrastructure.
- Cracking WEP – This is another confidentiality attack. Just by capturing data, we can try to recover the WEP key using either brute force or an FMS cryptanalysis.
- Evil twin AP – This is probably the most notorious. Here, you basically pose as an authorized AP by using the same SSID, and hopefully, users hook into your AP mistakenly.
- Honeypot AP – This is simply where an AP SSID is set up to be the same as a legitimate AP.
- Session hijacking – This is very similar to what we see with the wired network, but it's where we manipulate the network, so the attacker's host appears to be the desired destination.
- Masquerading – Is this where we run around the office in a costume? No, this is where you pretend to be an authorized user to gain access to a system.
- Man-in-the-middle attack – This is simply a network, but instead of wires, we use wireless. If you're not familiar with the concept of man-in-the-middle, I recommend looking up the chapter on sniffing.
Availability attacks
These attacks include the following:
- AP theft – Yep, that will stop you and your users from having network access.
- Disassociation attack – This is another type of availability attack, and it is where we basically go and destroy the connection between the client and the AP and make the AP totally unavailable.
- EAP failures – In this case, we look at valid 802.1x EAP exchanges and then send the client a forged EAP failure message. Again, they would disassociate.
- Beacon flooding – Here, in order to take away the availability of the AP, the attacker generates hundreds or thousands of counterfeit 802.11 beacons and distributes them in the air, making it harder for the client to find a legitimate AP.
- Denial-of-Service attack (DoS) – If I send forged authentications or associations from random MACs, I'll end up doing an authorization flood, and you are going to have a very bad day!
- Deauthentication flood – This is where we flood clients instead of the AP with forged deauthentication or deassociation to disconnect them from the AP.
- Routing attacks – This is where we mess up the routing tables or even try to poison the routes and distribute that information throughout the network via the AP.
- Authentication flood – The attacker sends your AP so many fake authentication packets with random MAC that your AP's association table fills up, kind of like a MAC flood. Cool, huh?
- ARP poisoning – This is the same thing we do on the wired network. It's also one of our first steps in performing the man-in-the-middle attack.
- Power saving attack – APs will buffer all inbound data for a client that is in sleep mode until the client pulls the AP for its data when it wakes up. By spoofing the polling message on behalf of the client, an attacker can cause the AP to discard the client's packets while it is asleep, which basically causes a DoS.
- TKIP MIC exploit – This is basically where we, as an attacker, generate a bunch of TKIP data that exceeds the target's MIC error threshold. By exceeding that threshold, we shut down the AP.
Authentication attacks
The goal of authentication attacks is to steal the identities of Wi-Fi clients, their personal information, and their login credentials, so that the attackers can get into network resources without permission:
- PSK cracking – Using tools such as KisMAC or coWPAtty, we can recover WPA PSK data from the key handshake frames.
- Lightweight EAP (LEAP) cracking – Attackers can use dictionary attacks to recover user credentials from LEAP packets.
- VPN cracking – Tools such as Anger or THC-PPTP bruter can access users' credentials or IPSec pre-shared keys (PSK) via a brute-force attack.
- Domain login cracking – Here we can use a password cracking tool like John the Ripper to crack passwords and gain acces.
- Key reinstallation attack – Attackers prey on the four-way handshake of WPA2 to gain access.
- Identity theft – This is one of my favorites. It is where we capture users' identities from clear text 802.11x ID response packets.
- Shared key guessing – Remember WEP? Well, cracking WEP using the vendor default WEP key is a classic example of this one, or just outright cracking the WEP key.
- Password assumption – Here, the attacker captures identities; they continually attempt using 802.1X authentication to try to guess the user's password.
- Application login theft – This is another one of my favorites. It is where we capture users' credentials from cleartext application protocols. Most of us use the same password for the application as our login credentials, as well as to gain access to our wireless network. You didn't think about that one, did you?
Attacks on the APs
Let's look at some of the possible AP attacks:
- Rogue AP attack – A rogue AP is simply a device that isn't sanctioned by an administrator but is operating on the network.
Sometimes, these rogue APs are deployed by employees who just want better reception. But from the attacker's perspective, they set up a rogue AP and place it near the target network. When the user turns their computer on, the rogue AP offers up a connection to the user's wireless network interface controller (WNIC).
If the user connects to the rogue AP as the legitimate AP, it's going to try to authenticate itself, and therefore, the rogue AP picks up that whole communication channel.
- Unauthorized association – The attacker installs a soft AP, which is an AP program that runs via software and turns the laptop into an AP. Now, if successful, other machines might hook into that AP, and the attacker would be able to capture that information.
- Honeypot AP attacks – This is where the attacker creates an AP that has the same type of SSIDs as some of these retail locations, and because the signal may be stronger because I'm sitting next to you, you'll connect to me.
- AP MAC spoofing – I'm sure you can figure out what this is. We have our network infrastructure, we have our wireless systems running, and the attacker just simply comes in and spoofs the MAC address of an AP in the hope that somebody hooks up to them. Now, let's see, when would this also come into play? Let's say that you're on a transportation device that flies through the air, and they happen to provide wireless internet on your transportation device. Most of these are paid services and a legitimate user might log in with their laptop, and most of the access is controlled by MAC addresses, so the AP says, Oh, yes, I allow this particular MAC address onto the network.
Somebody who may be curious—not saying I may or may not have done this before—but an attacker could simply duplicate the MAC address and be allowed access to the network. I know you're already thinking, I'd better look to see if Dale's on my flight!
Attacks on clients
These are simple, and we'll start off with the most basic:
- DoS – Under normal circumstances, we have our systems that are hooked up to our WAPs. To just totally mess up the network infrastructure, the attacker might send a deauthentication packet to the node, which basically shuts off its wireless—no longer associated with the AP. It's a simple attack.
- Ad hoc attack – A lot of devices, such as laptops, have both Wi-Fi and Ethernet cabling built into them. So, a user comes in and, for better communication on the network, they click into their RJ45 connection. Ad hoc means a one-to-one relationship, so the attacker simply comes in and creates an ad hoc connection to your laptop and then can pass through and gain access to the network. So, Super Dale rule number 583 reads, Turn off your Wi-Fi if you're hooked in through Ethernet.
- Jamming – Traffic jam? No. How about a paper jam? No. How about jamming with your favorite band? Yes, that's me with Collective Soul. However, the jamming we're talking about here is where we have a WAP, and we deny services. I sometimes wish I had a mobile jammer that I could turn on in the movie theater for those youngsters who talk on their phones or text during the movie. Yes, you can buy a device like this off the internet.
Jamming is extremely popular, especially when it comes to dealing with criminal activities. This is a jammer that does several frequencies including, not only cell but Wi-Fi, Bluetooth—everything (Figure 11.10):

Figure 11.10 – Using a Wi-Fi Pineapple as a jammer
Next, let's talk about the methods we use in wireless hacking.
Methodology of wireless hacking
Believe it or not, there is a methodology when it comes to hacking wireless networks.
Step 1: Wi-Fi discovery
This is the first step in the methodology of hacking wireless networks. We always look at this the same way we do with standard networks—that we need to first see what's going on around the environment itself. If you remember, one of the first steps is the process of footprinting or reconnaissance. All we're doing is looking around.
I like to refer to this process as a looky-loo. If you're not familiar with that term, I'll give you a description. In my state it just so happens if you're driving down the freeway and there's an accident on the other side and you can't see it, you're required to slow down and see if you can see what's going on, thereby slowing down traffic on the opposite side, which is nothing but totally frustrating and creates some road rage. We refer to those folks as looky-loos.
If you remember, when it comes to footprinting, this is simply where we're trying to locate and understand the network itself. We do that in a couple of different ways:
- Passive method – This is one of the ways you can use it. Passive is just sniffing the airwaves, seeing what's there. We're not hitting anybody or trying to connect with any AP, we're just looking at the airwaves themselves.
- Active method – This is obviously a little bit more intrusive. I could send out a probe request with an SSID to see if an AP responds.
Either way, to accomplish footprinting, you'll need a couple of things. You'll need applications, including desktop applications, and some of the newer ones based on mobile.
Some of the more common desktop applications include Insider, which is an open source, multi-platform Wi-Fi scanning software. It gives the attacker information such as the proper channeling of wireless networks, signal strength if the AP is filtered, and of course, we can export the Wi-Fi GPS data out to an XML file that we can then use inside Google Earth.
Another product out there is called NetSurveyor. This is a network discovery tool used to find WAPs in real time. It's a little bit more GUI as far as its interface is concerned, so it's a little prettier.
WiGLE.net is one of my favorites. It is an open platform and a website for collecting information about different wireless hotspots around the world. It started back in 2000, and by 2013, it had over 170 million recorded Wi-Fi networks in its database. Out of that 170 million, 105 million have GPS coordinates.
We also have Kismet. This is a layer 2 wireless network detector, sniffer, and IDS environment. There are probably more by now; it's like they're coming out daily.
Step 2: Wireless traffic analysis
After discovering our wireless networks, and using our GPS mapping to get their locations, the next step is doing wireless traffic analysis and determining any vulnerabilities that may be in the network. Tools such as PRTG Network Monitor (https://www.paessler.com/howto-free-network-monitoring) and Microsoft's Wi-Fi Analyzer and Scanner (https://www.microsoft.com/en-us/p/wifi-analyzer-and-scanner/9nblggh5qk8q) are great solutions, and there are also several tools available on the mobile apps stores.
We're going to do this in a couple of different ways. The first thing we'll do is look for vulnerabilities. This can be done just like we normally do on our wired networks. Again, our whole purpose is to determine an appropriate strategy for attacking the network.
The other thing you need to remember, and I've mentioned it a couple of times, is this is wireless, so traffic itself is just flowing through the air and it isn't serialized, which makes it extremely easy to sniff and analyze the packets.
Step 3: In-depth reconnaissance
The next step of the attack is doing a little bit more in-depth reconnaissance. We'll be looking for SSIDs, whether they're hidden or being broadcasted. We'll also look at APs—like how many there are, the encryption being utilized, as well as the authentication they're trying to use.
Why do we need to know how many APs they have? Well, two-fold. First, it gives us a layout of the network infrastructure itself. However, more importantly, I'm going to be looking to see if all the APs have been patched. Often, when companies have multiple APs, they may do firmware upgrades for one or two, but they may forget one, and that could be my door into their network.
There are more cool tools out there that will help us to determine all these reconnaissance requirements or issues. Those include things we've already seen including Wireshark; because packets are going through the network, Wireshark can sniff that out.
We also have some very specific products out there for wireless including AirMagnet, OmniPeek, and AirSnort.
Step 4: Launching the attack
Are you ready to start launching the attack? Well, for us to accomplish this, we can use probably one of the most powerful tools out there, Aircrack-ng. It's not just a simple application, it's a suite of applications designed to target the wireless environment. By suite, I mean, there are several different products inside the product. It's open source, and what's cool is it's free. It's done through the GNU General Public License.
As we said, Aircrack-ng is made up of several utilities. The ones you should be aware of for your exam would be the following:
- Aircrack-ng itself. This is the standard WEP, WPA, and WPA2-PSK cracking tool.
- We also have Aireplay-ng, designed to create traffic and fake authentication packets, as well as ARP request injections.
- There's also Easside-ng, a nifty little tool that allows you to communicate via WEP encryption with an AP without knowing the WEP key.
- Other tools include Airodump-ng, a utility used for packet capturing. It also can link in with a GPS receiver if you have one hooked up.
- I bet you can't guess what Airmon-ng does? Yep, we use it to enable the wireless NIC card to start monitoring the wireless interface and looking for different APs.
Now, you may never use some of these programs within the Aircrack-ng suite. I just want you to understand that, because it has so many utilities inside of it, you could say it's a sweet suite.
Step 5: Cracking the encryption
Once we have the SSID, the next thing we need to do is look at cracking the encryption. Now, as an attacker who may have gotten unauthorized access to the target network by doing things such as placing rogue APs, evil twins, and finding out what the hidden SSIDs are, the next step is to crack the security that's stopping us.
How we achieve this totally depends on the encryption that's being utilized, and there are many tools based on our requirements. We obviously know about Aircrack-ng and its suite of tools. On the macOS platform, we have something called KisMAC that is basically a playoff of Kismet, which is designed to run on a Linux environment.
We also know about Kali Linux, which has a plethora of tools. We've just talked about Aircrack-ng, but it has a ton of tools as far as wireless cracking is concerned.
It also has KillerBee, Blueport, BlueRanger, RedFang, and WiFiHoney – we could spend hours going over that information. And, of course, if you're on the Windows platform, good old Cain and Abel also can do some cracking for us.
Let's discuss Bluetooth next.
Hacking Bluetooth
Bluetooth is not normally something we would consider an attack vector, but it really is. It's a technology that allows for devices to share data over somewhat short distances. We're about to look at how Bluetooth works, the security mechanisms it has, the threats it provides or creates, and, of course, it can't be complete unless we talk about tools and attacks. Cheer up and let's get going!
I know by now your little brain is overloaded with tons of acronyms and terms, but you must make room for some new ones, especially when it comes to Bluetooth:
- Bluejacking – This is sending messages via Bluetooth from one device to another without the consent of the user. It's like spam. It's relatively harmless. The attacker can't access any information or intercept messages, but they can use Bluejacking as a way of social engineering a target to do something on the phone because a message told them to do it thinking it's an official thing. For example, Turn on your Wi-Fi and hook into this access point. It's annoying getting a ton of Bluejack messages.
- Bluesmacking – This is a DoS attack that causes a buffer overflow. It does it through a ping of death through ICMP packets being sent to the Bluetooth device.
- Bluesnarfing – Bluesnarfing is more dangerous than Bluejacking because it enables the hacker access to part of your data. The attacker uses customized software to request information from the device via Bluetooth push profile in this type of attack. The attack can be carried out in stealth mode against the device; however, this is unlikely due to the time required to determine the device's name.
- Blueprinting – Can you guess what it does? Hang on, I know you're thinking, It has something to do with printers, right? No. Blueprinting is simply a footprinting method. Now can you see the correlation between blueprinting and footprinting? This method allows the attacker to find out the model and make of the device they're going after.
- Bluebugging – This is when the attacker can gain remote access to the target Bluetooth-enabled device without the victim being aware of it, and it gives them full access to the 80 level commands of the device, meaning they would have read-write access to text messages and their phonebook or contacts. Bluebugging was developed after the onset of Bluejacking and Bluesnarfing. It's just on steroids.
You might want to make sure you have a couple of these terms at your fingertips for your immediate future, particularly, Bluesmacking, Bluejacking, and Bluesnarfing.
More about Bluetooth
Besides using frequency hopping as a security mechanism, remember both the master and slave must know the hop sequence; we have the PSK that's exchanged at pairing.
With Bluetooth, we have three different modes:
- Discoverable mode – This is the mode most people are used to. When you try to pair up a device, you make it discoverable, which means that it will respond to any inquiries that are made to that device. This mode should only be turned on while making the connection for the first time. Upon saving the connection, the two devices will remember each other and, therefore, the discoverable mode isn't necessary at a later point.
- Limited mode – This mode is exactly what it sounds like—only responding for a limited time. Most of our phones today, when we make them discoverable, have a timeout. My phone has 2 minutes before it becomes non-discoverable.
- Non-discoverable mode – This mode prevents the device from appearing on anybody's lists of available Bluetooth devices in the area. However, it's still available or visible to devices it has paired with previously.
There are two pairing modes that are available as well:
- Non-pairing – This is the first one and, just like the name sounds, the device itself rejects any pairing requests made by any device.
- Pairing – With this, the device accepts a pairing request upon receiving and establishing the connection with the pairing request device.
Eavesdropping and impersonation
What we mean by this is we allow an attacker to intercept or listen in or on communications between two or more devices. Now, here's where the frequency hopping comes into play; it makes it a little bit more difficult for us to listen in since it's hopping around. If I can figure out the frequency hopping algorithm you're using, or the hops sequence, I can simply listen in. In fact, to just circumvent the frequency hopping algorithm, all I have to do is use another Bluetooth listening device that's modified to listen to all frequencies. And I bet you'll guess that I got a tool for that, right? It turns the device into a sniffer for Bluetooth.
Person-in-the-middle attack
We need to be concerned about person-in-the-middle (PITM) attacks. Whoa, wait, I thought it was a man-in-the-middle attack? Well, it's basically the same thing, where the attacker who already has the link keys of the two Bluetooth devices can intercept the communication and initiate new communications to both devices posing as each other. With Bluetooth, there must be a master and a slave. Typically, your phone would be the master, your headset would be the slave, and that creates what they refer to as a piconet. Did I hear you say, Oh, come on, Dale, you're making things up now? Well, that's what we call it, it's an ad hoc network. By doing a person-in-the-middle attack, we end up creating two piconets since both devices are considered slaves and masters.
Countermeasures for Bluetooth
Now that we've talked about the big scary wireless, let's talk about countermeasures, shall we? By now, you know why we need to have countermeasures. I think the Dalai Lama summed it up best when he said, Forgiveness doesn't mean forget what happened. If something is serious, and it's necessary to take countermeasures, you have to take countermeasures. Such a wise statement.
The first thing you want to do includes obvious things such as not using default pins like 1234 or 1111 and making sure your Bluetooth devices are kept in the non-discoverable mode because if an attacker can't see it, they won't connect to it. Better yet, if you don't need it, turn it off. I only have my Bluetooth on when I feel like I'm in my safe zone, which is getting smaller and smaller all the time.
Also, check your paired devices to make sure there's nothing random suddenly showing up as a device that you've paired with, and don't accept any unexpected requests. If your device supports it, make sure you implement linking encryption on all connections.
The six layers of wire security
Every time I hear six layers, I always think of the Six Degrees of Kevin Bacon (oracleofbacon.org), and I'm sure if I start with APs within six layers, I'll be able to get to Kevin Bacon, but let's talk about wireless security here:
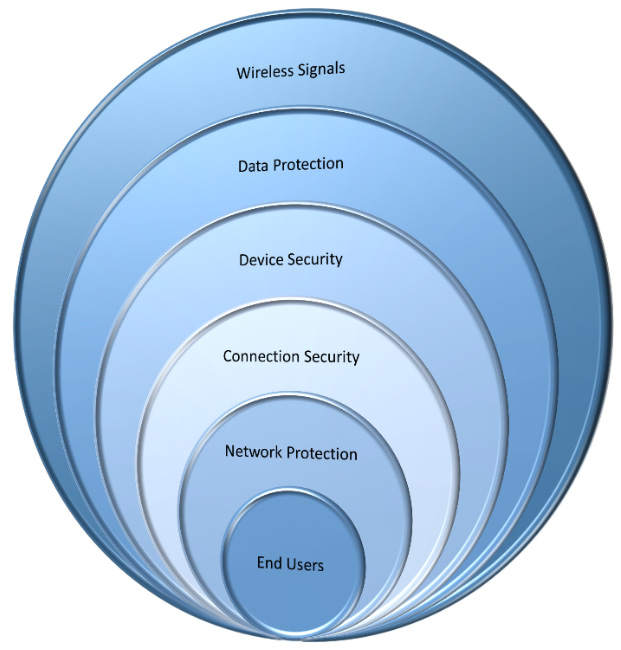
Figure 11.11 – The six layers of wireless security
Let's briefly discuss these layers:
- First layer: Wireless signals
In wireless networks, the continuous monitoring and managing of the RF spectrum within your environment helps to identify threats and makes you aware of its capabilities. You may want to invest in something like an IDS system or even in a wireless intrusion detection system (WIDS). Previously, I discussed how to limit the length of the transmission of your wireless network by using a reflector of some sort.
I've also heard of users removing antennas from APs. Just because the antenna isn't physically attached, doesn't mean the AP doesn't continue to operate. It just gives it a stronger signal. If the signal is going too far, do yourself a favor: try taking the antenna off and looking at its transmission distance.
- Second layer: Data protection
This is another layer within wireless security. Obviously, we've talked about the use of WPA2 and, yes, these encryption algorithms should help to protect your data during transmission. Again, it's not foolproof because of weaknesses and other subsystems.
- Third layer: Device security
This is another layer, not only the physical layer of the device but also making sure that the device is up to date via patch management and scanning these devices for vulnerabilities. When I say scanning for vulnerabilities, I'm not necessarily saying hitting the device itself but doing research to see if there are any vulnerabilities that have been listed by the manufacturer or third parties.
- Fourth layer: Connection security
Connection security per frame, or packet authentication, provides protection against man-in-the-middle attacks. It makes it almost impossible to accomplish. It does not allow the attacker to sniff data when two authorized users are communicating with each other. I would also look at centralizing the encryption method. Obviously, the centralization of this encryption, like a RADIUS server, requires additional security on the backend.
- Fifth layer: Network protection
This means strong authentication ensures that only authorized users can access the network and its resources. When we say strong authentication, we're not only talking about the encryption and authentication mechanisms, but we're also talking about how long the passcodes or passphrases are. Weaknesses at that level make us extremely vulnerable.
- Sixth layer: End users
I know it's hard to wrap your head around it, but believe it or not, if an attacker is able to associate with an AP, the personal firewalls installed on the end user's system on Wi-Fi networks can prevent attackers from gaining access to files.
Moving onto countermeasures next!
Countermeasures
Typically, this is where we have the most control as security professionals.
When it comes to wireless, do yourself a favor and change the default SSID. In fact, this might be a great opportunity to practice something I always talk about, and that is misdirection. For example, if I have a D-Link router, I know the default SSID is called D-Link. I'll switch it to Linksys or Tsunami, a different manufacturer, because when the attacker is wardriving through my neighborhood or a business environment and he sees D-Link, he'll throw D-Link attacks or vulnerabilities at that device, which obviously won't work.
Disable SSID broadcasting
Again, this will not stop an attacker, but that's not your job because that job is impossible. Your job is to slow them down. The attacker dared to be looking for a hidden SSID.
Disable remote login and wireless administration to the device
The last thing you want is for the attacker to be able to gain access to the device wirelessly. Let's make it a little bit harder for them. Make it so you have to be on the physical wired network to manage this device.
Enable MAC filtering
This is very similar to disabling the SSID broadcasting. It's not necessarily going to stop them, but it is going to slow them down. In fact, if I slow them down enough, I will hopefully discourage them
Update drivers on Wi-Fi devices
Make sure you update drivers on all the Wi-Fi devices. Again, I go back to how we are all so much aware of updating our applications, especially on our mobile devices, or we update our OS on the famous Patch Tuesday for Microsoft, right? But, I always ask people, When was the last time you updated the firmware or the drivers on the Wi-Fi devices? This should be done at a minimum of at least once a year; I would preferably see this on a task list, to be done every quarter.
Create a centralized authentication server
We've already talked about creating a centralized authentication server. Remember our RADIUS server? That's also going to require some best practices regarding locking it down.
Secure Wi-Fi devices
You may not have thought of this, but guess what? If you're not using it, turn it off, please. Just because you can be wireless doesn't mean you have to have it turned on.
Best practices for the SSID settings
Let's discuss some of the best practices when using SSID settings.
Change and hide the SSID
We've mentioned changing the default SSID and hiding it. This is also known as SSID cloaking. I once read an article on the internet that listed three reasons why hiding your wireless SSID was a bad idea. One of the three reasons was that hiding your wireless SSID tempts bad guys. Guess what? You're already tempting them by having a wireless network. We can also argue whether it's a waste of time because as we've seen, we can detect those, but that does require a different level of attacker.
Also, when you name your SSID, please, for the love of Pete, don't use anything identifiable such as the company name, address, or your last name, for example. At that point, you're just making things almost too easy.
Use a firewall or a packet filter
As far as layout is concerned, you should also make sure you place a firewall or a packet filter between the AP and the corporate network.
Encryption
Other encryption technologies we can use with wireless include, for example, IPsec for wireless, or setting up VPN tunnels between wireless users and APs—anything to slow the attacker down.
Now, I do need to probably give you a caveat here and that is, every time we add additional protections to our systems, we end up affecting performance, as well as creating some complexity. And as you probably know, anytime we hear the word complexity, we must associate it with the possibility of additional security holes being made. It takes a very vigilant IT security professional to keep up on all of this. But hey, that's what you're here for, right?
Summary
In this chapter, we discussed the various wireless network environments we experience. We shared insights into the evolution of wireless and wireless networking. We discussed the great advantages and some of the disadvantages of wireless networks. We shared insights into what makes wireless networks vulnerable to security issues and some countermeasures we can do to better protect ourselves from threats we face. We discussed the methodology of hacking wireless and Bluetooth devices.
In the next chapter, we will learn about hacking mobile platforms.
Questions
As we conclude, here is a list of questions for you to test your knowledge regarding this chapter's material. You will find the answers in the Assessments section of the Appendix:
- Which of the following best describes a wireless hacking attack's evil twin?
- An attacker creates an access point for clients to connect to within a network range.
- Attackers create a system with the same MAC as a legitimate target.
- On a wireless network, an attacker sets up an authentication.
- An attacker logs in with the same username and password as a legitimate user.
- A WEP-encrypted access point has been located by a team. To crack WEP, what is required to perform a fake authentication to the AP? (Select two.)
- The access point's MAC address
- The SSID
- A replay of an authentication packet that was captured
- The wireless access point's IP address
- Which of the following statements about wireless security is correct?
- WPA2 is a superior encryption option to WEP.
- WEP is a superior encryption option to WPA2.
- The use of MAC filtering and cloaking the SSID eliminates the requirement for encryption.
- Increasing the SSID's length to its maximum improves the system's security.
- Which wireless standard uses MIMO antenna technology to reach high data transmission speeds?
- 802.11g
- 802.11b
- 802.16
- 802.11n
