Chapter 16: Using Cryptography
If you're new to cryptography, let's talk about its purpose. I'm going to try to make this easy to understand, because to some folks, cryptography can be overwhelming.
Cryptography is all about protecting data, usually in the form of messages or files. This can be done by taking data and transforming it into an unreadable format, often called ciphertext. The only way to transform the ciphertext back into readable data is with a special key, which only the sender and recipient of the message have access to. This process is called encryption, and it's the basis of how cryptography works.
When you're through with this chapter, my hope is that you'll come away with an added perspective and greater depth of understanding of the essential role cryptography plays in the guarding and protecting of information and digital communication.
Here is what we'll cover in this chapter:
- Understanding cryptography
- Standards and protocols
- Countermeasures for cryptography
Let's first discuss why cryptology is important to our security efforts.
Understanding cryptography
In this section, we'll discuss why cryptology is important and some of the best cryptology tools and resources available to us. Having knowledge of the proper tools and resources will be invaluable to you as a security professional. So, let's jump in and discuss what this is all about.
Why use cryptology?
So, what does cryptography bring to the table? Well, it brings non-repudiation. This means that whoever sent a message can't later deny having altered the document. For example, "It wasn't me, Dale, I swear," to which I'll reply, "No, it was you because it was encrypted with your key."
Cryptography also brings authentication to the table. Sometimes we visit websites where it's important that we authenticate who we say we are, as well as obviously wanting to authenticate our credit card information, right? So, it's important to us, especially to those within our industry.
And, of course, confidentiality is another major factor as far as what cryptography can do for us. As far as confidentiality is concerned, we can only make certain resources available to authorized users. Now, as far as how this process works or how cryptography works, these are at a very plain or elementary level. The process goes like this.
We have plaintext; this is the text that is formatted and that we can read. Maybe it's a Word document, maybe it's an email, but it gets encrypted using an algorithm, such as the Data Encryption Standard (DES) or the Advanced Encryption Standard (AES), or even Rivest—Shamir—Adleman (RSA). After the encryption has been applied, we refer to that whole document as ciphertext. It's completely unreadable. This file is then transmitted, and on the opposite end, it just goes through the opposite process, right? The ciphertext uses the keys it's aware of to do decryption, and then it gives us the plaintext that the original sender or the resource wanted us to see.
Cryptography is an important part of keeping our information safe and secure and is used in a variety of different applications. Everything from our email to our financial information is protected by cryptography, and it's important to understand how it works.
See? I told you this would be easy.
Next, let's talk about the types of cryptography.
Types of cryptography
There's not a whole lot of talking to do on this subject because guess what? There are only two, symmetric and asymmetric:
- Symmetric cryptography is all about using the same key for both encryption and decryption. So, what we have are a sender and a recipient, and they're going to use the same key to encrypt the message they want to send back and forth. It's very fast, it's very efficient, but it also has a couple of major drawbacks:
- The first is, if you lose that key, then you've lost all access to the information that's been encrypted.
- And second, it's very difficult to manage large-scale deployments of symmetric cryptography.
- Asymmetric cryptography is just about as opposite of symmetric cryptography as you can get. Rather than using one key to do both encryption and decryption, it uses two keys, a public key and a private key:
- The first key is the public key and it's a key anybody can have access to.
- The second key is the private key, and it's meant to be known only by the owner. It should never be given to anybody else. And, the great thing about this is that, if you use a public key to encrypt information, the only way to decrypt it is by using the corresponding private key. So, even if somebody were to intercept that message, they wouldn't be able to do anything with it because they don't have access to the private key.
The other great thing about asymmetric cryptography is that it doesn't require a secure initial exchange of keys like symmetric cryptography does. So, it's a little bit more secure in that sense. It's not perfect, but it's definitely more secure.
Asymmetric also utilizes digital signatures. Digital signatures are just a way to ensure the message has not been tampered with in transit. And, the way that this works is the sender of the message will use their private key to encrypt it, and they'll send both the message and their public key to the recipient. The recipient can then use the sender's public key to decrypt the message and then they can compare it to the original message to ensure it hasn't been tampered with.
Now, it does have some cons to it. It's a little bit slower than symmetric cryptography (we're talking about half an eyeblink versus a full eyeblink), and it also requires more bandwidth. But overall, it's a much more secure way to send information. Now, nothing is foolproof, right? If I've taught you anything through this series, it's that there's always a way. When it comes to asymmetric, it is susceptible to man-in-the-middle (MITM) attacks, as well as brute-force attacks. And, unfortunately, if the private key gets lost, then there's really no way to decrypt the information that's been encrypted with it.
Let's discuss some other keys next.
GAK
The Government Access Key (GAK) is a system proposed by the United States National Security Agency (NSA) to allow government access to encrypted communications. The key would be a mathematical value that would be used to decrypt messages. The existence of such a key would make it possible for the NSA to read encrypted communications, including those between citizens and businesses, as well as between different countries.
The problem with this system is that it would require a key that is incredibly complex and difficult to generate. And, of course, the NSA would need to keep this key completely secret. If the key were to get out, then anybody could use it to read encrypted communications. Has anyone seen the 1991 movie Sneakers starring Robert Redford? Talk about a movie that predicted the future of encryption! (Homework assignment from Dale: watch this movie!).
Another problem with GAK is that it would be very difficult to implement. Any change to the encryption algorithms used by businesses and governments would need to be approved by the NSA. This would give the NSA a lot of power, and it's not clear that they could be trusted with such power.
It's also worth noting the NSA is not the only government agency interested in reading encrypted communications. The United Kingdom's Government Communications Headquarters (GCHQ) has also expressed an interest in a system that would allow them to read encrypted communications.
Let's continue to talk further about another tool for encryption next called ciphers.
Learning about ciphers
What we're talking about when it comes to ciphers is an algorithm. You can think of it as a defined series of steps that have to be performed for the encryption and decryption process to occur. Once a message or data has been encrypted using a cipher, it is considered unreadable unless, of course, whoever's receiving the data or message knows the secret key that's required to decrypt it.
Now, believe it or not, ciphers are used everywhere, not just in our emails and our data itself, but we also use them in other communication technologies, such as cell phones. This is what makes our cell phone calls more secure.
Types of ciphers
Now, I know what you're thinking: "Dale, is there only one cipher?" No, there are several different types of ciphers. We can categorize them into two different types, either classical or modern. I know, it sounds like we're going to talk about art, but we're not.
Let's look at classical and modern ciphers.
Classical ciphers
Classical ciphers are those that were developed before the invention of the computer. They include classical ciphers such as the Caesar cipher, which is a simple substitution cipher, where each letter of the alphabet is replaced with another letter according to a defined pattern. Figure 16.1 is an example of a Caesar cipher:

Figure 16.1 – Example of a Caesar cipher (a simple substitution of letters)
So, in this case here, MY VOICE IS MY PASSWORD, as you can see, gets translated to DB XGOET OL DB HALLCGKR. All we're doing is basically replacing the M with another letter, in this case, D. Notice how DB represents MY in both instances. This would help me to figure out how to decrypt this message, given enough time.
Another type of classical cipher is referred to as a transposition. In a transposition, you use what they refer to as a key. Now, depending on the transposition cipher that you're using, in this case, I'm showing you (in Figure 16.2) what they refer to as a rail fence cipher:
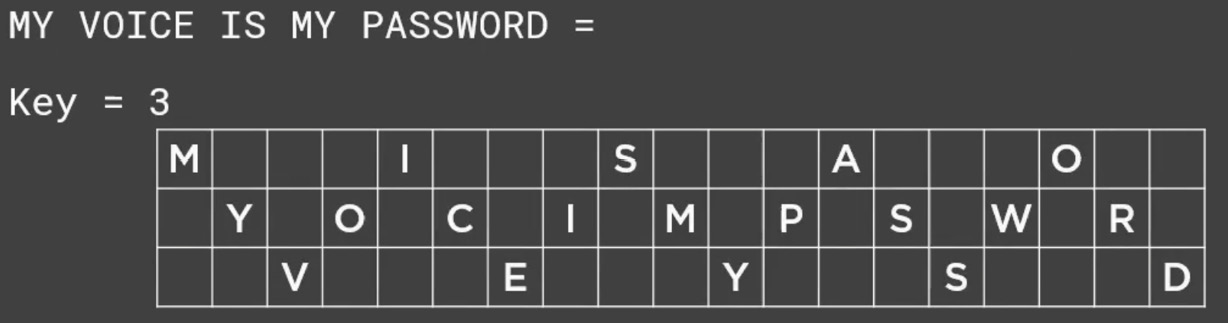
Figure 16.2 – Example of a rail fence cipher
In this case, the key is 3, which means there are three spaces between characters. You see that MY VOICE IS MY PASSWORD is spelled out in this up-and-down method, and the spaces in between are kind of ignored completely. So, the first line ends up becoming just MISAO while the next line of code would be just simply YOCIMPSWR, and the third row would just simply equal VEYSD. Now, obviously, the recipient would have to know that the key is 3 to decrypt this.
Another type of transposition cipher is a route cipher. With the route cipher, we end up taking the same data or information we're trying to encrypt. In Figure 16.3, I'm going to use the text, MY VOICE IS MY PASSWORD, and I'm going to lay it out like this:
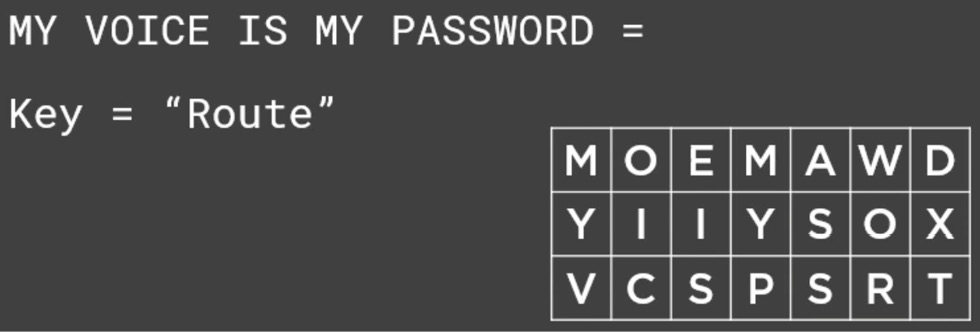
Figure 16.3 – Example of a route cipher
Can you see it all there? So, it lays the plaintext out in a grid pattern just like this, and, of course, the last two characters are just random characters. This type of cipher is determined based on the route.
Those are just some quick examples of classical ciphers.
Let's look at modern ciphers next.
Modern ciphers
You can see with the classical type how easy it would be to crack those types of ciphers. With modern ciphers, they're a little bit more difficult to try to crack manually. And typically, modern ciphers are there to provide authenticity, security, and integrity to the sender.
The types of modern ciphers you'll see are both symmetric and asymmetric. While I'm talking about it, there's a way to use both asymmetric and symmetric at the same time, but that might be going a little too deep here, so I'm just going to leave that up to you. If you want to do a little bit more research, you can look at that further.
There are also ciphers that are based on the input of data. We have what they refer to as a block cipher, and what we mean by block is the algorithm operates in groups of bits or a block of a fixed size. Most of the cryptography we see today, such as DES, AES, or even the International Data Encryption Algorithm (IDEA), are all using block-based ciphers. Now, if by chance, the block size of the data coming across is less than what is used by the cipher itself, there's some padding that helps to make sure it achieves the block size that's needed.
There are also stream ciphers. When it comes to a stream cipher, we're basically talking about a symmetric key cipher, where the plaintext digit is combined with a pseudorandom cipher digit stream, which we sometimes refer to as a keystream. In a stream cipher, each character is encrypted one at a time, and with it goes a corresponding digit of the keystream; this gives us a cyber-text digit stream.
Let's look at some other types of algorithms.
Using other algorithms
When it comes to different algorithms out there, the most common we will see are going to be DES, triple DES (3DES), AES, and RC4.
Let's discuss these next.
DES
This was created back in the 1970s by IBM. It utilizes a 64-bit block. On top of that, it only uses a 56-bit key for encryption and decryption, which is not that great. In fact, in 1999, this algorithm was cracked, especially considering the computing power we had back then was not very much. But, DES itself provided up to 72 quadrillion possible encryption keys, and we were able to crack it back in 1999. Now, because this was cracked, the US government got involved and helped. Now, obviously, to cover this vulnerability, which could be brute force-attacked very easily, we came up with triple DES, or some people might call it 3DES. The reason it's called 3DES is that it goes through and does the DES algorithm three times with three different keys.
Now, as far as how these keys are used, you have a couple of different options:
- The first option is all three of the keys are completely different or independent.
- The second option is using the K1 and K3 keys, but since they're both used for encryption, they are identical.
- And, there's a third option, which is where all three keys are the same, but that's not very secure.
The most secure would be the first option, which is where all three keys are independent.
AES
AES is kind of a fully grown adult compared to DES and 3DES. It utilizes a 128-bit block size, and its keys are 128, 192, or 256-bit in size. I bet you can't guess what they call each one of those, right? They're called AES128, AES192, and AES256. That was tricky, wasn't it? AES is a symmetric-key algorithm, created with the help of the National Institute of Standards and Technology (NIST). The government agencies use this for encrypting data that is considered unclassified.
RC4
Some folks call it Ron Rivest. Ron is the first name of the gentleman who helped create it, but the cipher is called Ron Rivest; it's Rivest Cipher 4. Now, this cipher is considered a variable key size symmetric keystream cipher. And, let's be honest, it's not that great because guess what? We use this in Wired Equivalent Privacy (WEP), which is the wireless security protocol that's been hacked very, very easily.
The reason why RC4 was vulnerable to different types of attacks was that it had what they refer to as a biased output. There is a rule that if the third byte in its original state is 0, and if the second byte doesn't equal 2, this means the second output byte is always 0. Now, this may seem complicated, but trust me, once we see patterns like this, we're able to go through and reverse engineer the cipher and crack it. And, that's what happened to WEP.
Two other algorithms that we should be familiar with are Blowfish and Twofish.
Blowfish and Twofish
The Blowfish algorithm was developed back in 1993, and I know you're thinking, "Dale, that's a long time ago." But it's quite a strong symmetric block cipher that we still use today. It uses the same key to encrypt and decrypt. It utilizes a 64-bit block, and its key is a variable key anywhere from 32 to 448 bits. This protocol was designed to replace DES and triple DES.
Now, it may be surprising to know that a lot of people still enjoy using AES, and I guess there's nothing wrong with it, but you need to know that one of the advantages of Blowfish is its speed. It breaks things down into a 64-bit block as compared to AES, which, by using a 128-bit block, allows for faster encryption and decryption.
We also have something called Twofish. This encryption was created a few years after Blowfish. It was introduced to us back in 1998, and it's relatively close to the Blowfish cipher. That's why we have a similar name here, but it encrypts data with a 128-bit block just like AES. In fact, Twofish is very similar to AES because it supports a 256-bit block, as well as a 192 or 128 key size. And, just like Blowfish, it uses a single key.
Then, there's Threefish, which was developed in 2008 and is a part of the Skein algorithm. It is a 12-round Feistel network cipher with a block size of 128 bits and a key length of 256 bits. Threefish is very fast and very secure, with a high degree of resistance to attack.
Now, another reason why both these ciphers are extremely popular is that they haven't been patented. They're open-sourced. In fact, Twofish was the algorithm that was one of the top five finalists to replace DES for the US government but, unfortunately, it didn't win. But I think it did win Ms. Congeniality. Now I'm just kidding.
So, now that we've got the most popular algorithms out of the way, in the next section, we'll talk about standards and protocols.
Standards and protocols
Let's talk about some of the most common standards we see out there. In this section, we'll talk about more algorithms, hashes, ciphers, and other cryptographic mechanisms that will assist you in securing the data and communication you help protect.
DSA
This is a federal information processing standard for creating digital signatures. How this signature standard works is that it creates a 320-bit digital signature, but the signature is also accompanied by anything from 512- to 1024-bit security. It also utilizes our private and public key technology or process.
RSA
Hey, you know what? RSA are the initials of the creators. The R is from the same Ron Rivest from RC4, as well as from two other gentlemen. The S is after Shamir, and the A is after Alderman. All three of these gentlemen worked at the Massachusetts Institute of Technology (MIT). Rivest and Shamir worked as computer scientists and Alderman was a mathematician.
Now, RSA also uses a public key encryption system and uses two large prime numbers as its basis. We see RSA as a standard in a lot of our operating systems today: Microsoft, Apple, and Sun Microsystems, as well as being utilized in networking cards, smartcards, and even what we refer to as hardware-secured phones. Now, this may make your brain hurt a little bit, but let me give you a brief synopsis of how this works:
- First, two large prime numbers are taken, and we're going to call them A and B. These two prime numbers and their product are determined by saying that C is equal to A* B, and C (in math, we'd see it this way: C=AB) and, therefore, C is referred to as the modulus.
- RSA then chooses another number called E that is less than C and relatively prime to (A-1)(B-1). What this does is it makes sure that E and A-1 x B-1 have no common factors with each other except for the number 1.
- I know, it keeps getting better because then RSA chooses another number, F, and it does this so that EF-1 is divisible by A-1 x B-1.
- Now, some of you algebra folks are following right along. But wait, there's more. The values of E and F are referred to as the public and private exponents. In using those exponents, the public key is paired with C and E to create that public key, and the private key is created by pairing C and F together.
Now, the reason why this is extremely secure is that it's considered to be extremely difficult to obtain the private key from the public key. Now, obviously, if someone can factor C into A and B, then that person could decipher the private key, but the odds of somebody trying to get a hold of those two prime numbers that are taken at random are almost impossible. So, again, a lot more secure for us.
Hashes
I'm getting hungry. I think hash browns or just some good cabbage and hash are delicious. I've got to get food off my mind here!
When it comes to hashes, what we're trying to do is come up with a way to verify that a particular document hasn't changed. We want to know it's legitimate, that it has been signed, and no one has changed or tampered with it. Now, how we do this is we take the document, and we assign a digital signature associated with it. That signature is represented by a hexadecimal code. This code tells us the document and the default for this document; if it is equal to the hexadecimal code number, we know it's legit, it's been signed, and nobody has changed it. This also applies to an executable or an email. But, if somehow the document or the executable is changed, that hash value won't work, or it won't calculate out correctly.
Message digest
When we talk about cryptography, there's something that we need to keep in mind, and that is the message digest. The message digest is also referred to as a hash value. What it does is it takes a block of data and produces a unique fingerprint or hash value of that data. This is important because when we're talking about authentication, we're talking about making sure the data has not been altered in any way. And so, this allows us to look at the message and be able to say, "Okay, this is exactly what was sent. It hasn't been changed in any way."
Another hash method is referred to as Secure Hash Algorithm 1 (SHA-1) and was introduced in 1993 by the NSA. Now, its function is to take the input and produce a 160-bit hash value that is then turned into hexadecimal, which is about 40 characters long once it's converted. It's typically utilized with other protocols or security protocols, such as Pretty Good Privacy (PGP), Transport Layer Security (TLS), Secure Shell (SSH), and Secure Sockets Layer (SSL).
Now, I know what you may be thinking: "Dale, why'd we start with 1? Where's the SHA-0?" Well, SHA-0 was 160-bit, but it was so bad it was pulled for a significant flaw. Well, they then obviously came out with SHA-2. Now, SHA-2 is extremely similar to SHA-1, but it does use 256-bit, but it is stronger and larger than SHA-1. And, what I mean by that is there are two different block sizes that it can use, either SHA256, which gives you a 32-bit word, and SHA256, which, double it, 64-bit, right? Guess what?
They then came out with SHA-3. It's unlike SHA-2, which was similar to SHA-1 (and SHA-1 was similar to SHA-0); SHA-3's only likeness is in its name. The reason behind it being a completely different beast is that it uses what's referred to as sponge construction. The data is absorbed, or the input is absorbed, and the output or the result is squeezed out. Now, during the absorption process, the message blocks themselves are XORed into initial bits of state or a subset. That subset is then transformed using a permutation function. So, yeah, it's a little bit tougher.
So, now that we've got our hands on these different types of ciphers, there are some ciphers that are designed for messages.
Ciphers designed for messages
We first start with hash-based message authentication code (HMAC). This algorithm includes the embedding of the hash functions, such as SHA-1 or the message-digest algorithm (MD5). Where its strength comes from is dependent upon the embedded hash function, key size, and the size of the hash output.
How HMAC operates is there are two different stages. Now, in those stages, there's a secret key that's created. There's one for an innie and one for an outie. I know, I just made a belly button joke. It's inner and outer, but the concept remains the same.
The first pass of the algorithm produces an internal hash derived from the message and the inner key. The second pass includes the final HMAC code derived from the inner hash result and the outer key. Now, HMAC itself doesn't encrypt the message, but instead, it takes the message whether it's encrypted or not, and it must be sent alongside the HMAC hash. This way, both parties can verify using the secret key that the message is coming from who it says it's coming from, or that its authenticity is correct.
Let's discuss another authentication mechanism next.
CHAP
The Change Handshake Authentication Protocol (CHAP) is an authentication mechanism we use via Point to Point Protocol (PPP) and a three-way handshake. CHAP provides a way to protect yourself against what we refer to as replay attacks. Now, the downside is that CHAP uses that shared key thing where both the client and the server must know the plaintext of the secret key. Now, the funny thing here is Microsoft came out with their own version of CHAP (called MS-CHAP) that doesn't require either the sender or the receiver to know the plaintext, and it doesn't transmit it, but it's also been hacked.
EAP
The Extensible Authentication Protocol (EAP) was originally designed for point-to-point communications. It is used as an alternative to CHAP, as well as the Password Authentication Protocol (PAP). I didn't talk about PAP because it's so outdated. EAP itself is more secure and supports different authentication mechanisms, such as using either one-time passwords, standard passwords, or smart tokens.
Let's talk about what public key infrastructure (PKI) is next.
PKI made simple
The PKI is asymmetric, which means we have a two-key technology to help make sure that information is encrypted and only decrypted by the appropriate parties. Remember, in symmetric, we only use one key that is shared between both parties. In this one here, we're going to have two keys, and you've heard me talk about public keys and private keys. Next, let's see what PKI consists of.
Your certificate
"Hey, Dale, you keep talking about this certificate. What is this so-called certificate?" So, a certificate is a way of identifying an organization, or even a user. Typically, certificates are based on what's referred to as an X.509 standard, and they typically contain fields such as when the certificate is valid, when it's expired, what algorithm is used for the encryption of the public key, and who issues the certificate.
In fact, let me show you something here real fast. So, here I am at the Packt website, and because we have an HTTPS connection, that means it's a secured connection.
Figure 16.4 – An HTTPS site will show a lock indicating a secure connection
I'm going to just hover over the lock here, and it tells me that I can view the site information or the certificate. So, I can come down and select to look at the certificate. It tells me it's currently valid without me having to drill into it, but let's go ahead and drill into it here. You can see here that it's created for the following purpose, to verify the identity of the remote computer and to provide your identity to the remote computer.

Figure 16.5 – The certificate shows the purpose and valid dates
This way, Packt can make sure they know who they're talking to. It shows who it was issued to. It tells us it was issued by Cloudflare on their ECC CA-3 server. And, of course, the validity period here is anywhere from 6/6/2021 through 6/6/2022. I can go into the Details tab for the certificate, and I can see all kinds of things here.
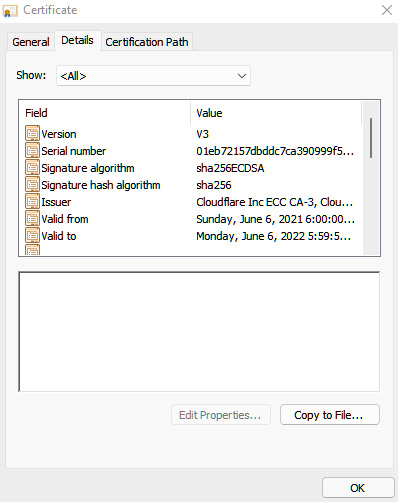
Figure 16.6 – The Details tab reveals more information
Again, I can see the issuer, which is sha256. I can see, again, the validity date, and the subject, which is basically, again, to who it applies. You can see that when they issued the certificate, you must fill out an application so they can issue it, and then they verify; in this case here, Cloudflare went through and verified that it was, in fact, Packt Publishing. This way, I can't create my own certificate for Packt and put it on the web and make people think that, hey, I'm Packt Publishing.
The public key, again, is ECC (256 bits), and that's the key there. I can again scroll down and see information here about the subject alternative names, which, they've got their wildcard in here.
Figure 16.7 – More details of the certificate including the public key
So, everywhere that we go, we are interacting with certificates. Sometimes, you don't even realize it. Now, when it comes to certificates, there are two different types:
- There's a signed certificate where a CA signs it, a public CA, and issues the certificate. And, again, these certificates normally contain the public key and the identity of the owner of that key. The private key is kept secret by the CA.
- There are also self-signed certificates. This is where the identity of the certificate is signed by the same organization or the entity that identifies that it's certified. So, for example, if I wanted to create my own certificate within my organization, I'm going to have my own CA server, and I'm going to do a self-signed certificate from that server. We don't normally use self-signed certificates. In fact, you should never use a self-signed certificate in the wild, only within your own infrastructure.
See? I told you I'd make PKI easy to understand.
Let's talk about digital signatures now.
Digital signatures
It's designed to verify that a particular email or document came from a particular source. For example, if Bruce Wayne was sending an email to Selina Kyle, they both would have a public key and a private key.
Selina would take her private key and sign her email so that Bruce Wayne can make sure that it was from her. She uses that private key to sign the document, which isn't a physical signature, it's just a code that's attached to the email saying that it was from Selina. Again, anybody could try to fake this if they wanted. But, here's what happens. When the email gets sent over to Bruce, he grabs a copy of her public key. Remember that key? It's public and can go to anybody, and he uses that public key to run against the signature to verify that the email came from Selina. Again, what you must remember here is digital signatures do not in any way whatsoever encrypt. It's just to verify a document, an email, or even a file.
Up next, we'll talk about additional ways to secure our communications over a network.
SSL and TLS
SSL and TLS are both cryptographic protocols that can be used to secure communications over an insecure network such as the internet. SSL is the predecessor to TLS and is more commonly used today.
SSL and TLS use a combination of a symmetric key cipher and an asymmetric key cipher to encrypt communications. The symmetric key cipher is used to encrypt the data, and the asymmetric key cipher is used to exchange the keys. SSL and TLS also use digital certificates to authenticate entities and prevent MITM attacks.
When we look at TLS, it goes through a handshake process:
- We're going to have our server that is encrypted or has the encrypted information, and then we have our client system. We know that we have public keys and private keys associated with that server or the data source itself.
- What happens is the client sends another client a Hello message, along with a random value, and it tells the server the supported ciphers it can use.
- The server responds by sending, "Hey, how you doing? I'm a server." It's called a server Hello message, along with the server's random value. The server also sends, "Hey, I'm done saying hello to you." Now, if the server has requested a certificate from the client, the client would then send one back.
- The client then creates a random pre-master secret and encrypts it with the public key from the server's certificate, then sends that pre-master secret to the server, and here's what's interesting; once it's received, the server and the client will each generate a brand-new master secret and session key, which is based on the pre-master secret.
- Once they've both done that, the client then sends a message that says, "Hey, I'm going to change the cipher spec." And that cipher spec is going to be based on the new session keys that we just generated, and we're going to use those for hashing, as well as encrypting. The client also sends a "Yo, I'm done" message or a client finished message. The server receives the updated cipher spec and switches over to a security state that will use a symmetric encryption using the session keys. The server also sends a "Yo, I'm finished" or a server finished message.
- Now, both the client and the server have the new master secret, as well as the session keys; they'll both start using those session keys to exchange data back and forth over a secure channel.
All the messages sent from the client to the server and from the server to the client are then encrypted. That's a lot, huh?
When it comes to using SSL and TLS, there are several different toolkits out there. The one I want to warn you about, it's probably one of the more popular but this is just more historical information, is one that's referred to as OpenSSL. Now, OpenSSL is like the Swiss army knife of cryptography, and because it's an open source resource, this makes it very attractive, right?
Now, there's one thing I need to warn you about and that is OpenSSL had a very big issue. It was something called Heartbleed, which was an extremely bad vulnerability. The Heartbleed vulnerability allowed anyone on the internet to read the memory of systems protected by the vulnerable versions of OpenSSL. Now, don't worry, it's been patched. Hint… you will want to know that in preparing to take the exam.
PGP
PGP is the understatement of the year. PGP gets its start all the way back in 1991. Now, the reason PGP is pretty good is we can use it for encrypting messages and files, as well as the digital signatures or signing documents, and, of course, deleting documents and even compression. In fact, PGP encryption uses a serial combination of hashing, then data compression, symmetric-key cryptography, and, finally, public-key cryptography. Each step uses several supported algorithms, and each of the public keys is bound to a username or an email address.
Let's look at how PGP happens and operates.
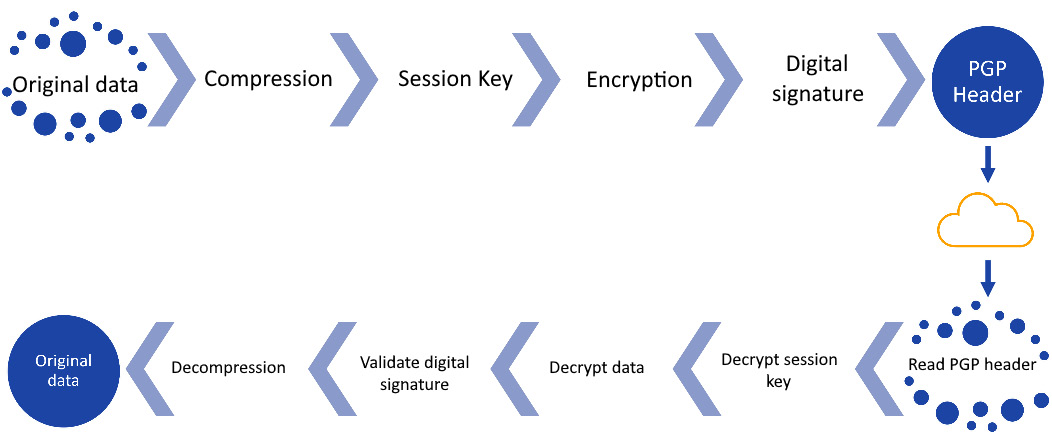
Figure 16.8 – PGP flow
- When a user encrypts data with PGP, PGP compresses that data down. This compression helps to avoid some exploits that could be used to try to crack the cipher because the patterns in the plaintext have been compressed.
- PGP then creates a random key that is a one-time-use-only, secret key, and it uses that key to encrypt the plaintext, which results in our ciphertext.
- Once it's done encrypting, the random key is encrypted using the recipient's public key. That encrypted data is sent to the recipient. Obviously, the encryption operates in a reverse manner.
You may be thinking, "But Dale, PGP is still good today. Isn't it?" Yeah, it really is. In fact, the only way I'm aware they have been able to crack or attack PGP is by installing a piece of malware that would capture keystrokes so they could capture the passwords as they type them in. Now, at the time of writing this book, Symantec owns PGP, and they've renamed it. They call it the Symantec Encryption Desktop, and the server component is just referred to as the Symantec Encryption Management Server. But basically, it's still PGP.
So, now that we've got that down, let's finish up talking about countermeasures.
Countermeasures for cryptography
You know me, I don't want to leave you all panicking that all is lost! There are some countermeasures that we can take to mitigate the attacks that might come our way. Let's talk about some of these countermeasures.
EC-Council lists 12 countermeasures to use:
- The first one is when it comes to accessing the cryptography keys, that access should only be given to users directly, as well as applications.
- You should also make sure you have an intrusion detection system (IDS) that's been deployed, and you are monitoring the exchange and access of those keys, so you've got a log somewhere of what happened and when. This is just in case you must go back and take a look at those logs because something got compromised.
- The other thing you're going to want to do is that if you plan on storing the encryption key on a system or on a drive, you need to use passphrases and passwords.
- This next one's for you more advanced developers out there: under no circumstances should the keys be inside of the source code or inside of any binaries.
- Now, when it comes to certificates for signing the transfer of private keys, it's a major no-no. We never, ever transfer private keys. We just say no, got it? I'll be a little happier now that you're agreeing with me.
- When it comes to symmetric algorithms, you should make sure you use the maximum number of bits that you possibly can. You should be using at least 168 bits or 256 bits.
- If you're going to implement encryption for symmetric key protocols, you've got to make sure that message authentication is performed.
- As far as asymmetric algorithms are concerned, you need to use the largest sizes available, either 1536 or 2048. Just say 2048, please.
- When it comes to your hash algorithms gain, use the highest bits possible, 168 or 256 bits, please!
- When creating or implementing a cryptographic environment, please don't do anything homemade. I know some of you developers might be like, "Well, I can do this a little bit better." Trust me, don't! Use what would be considered an industry standard. Some people will try to create self-engineered crypto algorithms as well as functions, and inevitably they're going to leave some holes open for you.
- I would also put a limit on the number of operations per second per key. This way, you don't have somebody trying to quickly brute force to try to discover what the key is.
- And finally, the output of a hash or any hash function should have the largest bit length possible, so it makes it hard to decrypt.
Okay, see? That's how easy those 12 things are. And, this brings us to the end. So, as you can see, standards and protocols are essential for us when dealing with and protecting our data and communications. Understanding the tools and processes is necessary for you to be an effective IT security professional.
Summary
One of the major ways to protect your resources from attackers is to use encryption for data in motion or in waiting. Your job as a security professional isn't to stop attackers, that's impossible. Anything is hackable. Your job is to slow them down or discourage them, and cryptography definitely does this.
This brings us to the end of this book and the beginning of your journey in cybersecurity. As you study for the CEH exam, remember that it's not an easy task to accomplish. The test is designed to make sure you know your craft.
Keep in mind that if you haven't fully grasped all the concepts we've talked about in this book, review it again. Do your own research. Reach out to me via my social media channels. My passion and mission are to help everyone and every company stay safer while using technology. Please be sure to tweet me or post on LinkedIn when you pass your exam or that you've learned something from me. The comments I get from my students, viewers, and readers really do bring a smile to my face. And, do me a favor…Be safe!
Questions
As we conclude, here is a list of questions for you to test your knowledge regarding this chapter's material. You will find the answers in the Assessments section of the Appendix:
- Which of the following terms does asymmetric encryption also go by?
- A shared key
- Hashing
- A public key
- Block
- Which of the following is a mechanism for SSL?
- Authenticating data
- Securing stored data
- Verifying data
- Securing transmitted data
- A common hashing protocol is which of the following?
- RSA
- MD5
- DES
- AES
- _________ is another name for symmetric cryptography.
- Shared key cryptography
- Steganography
- Public key cryptography
- Hashing
