Cyber forensics is a comparatively new field. Widespread use of computers dates back to the 1970s, and widespread computer crime to the 1990s. The field of cyber forensics has evolved only in the past 25 years. However, it is a branch of the science of forensics. As such, it takes forensics principles and applies them to cybercrimes. This brings up the question of what forensics is. The American Heritage Dictionary defines forensics as “the use of science and technology to investigate and establish facts in criminal or civil courts of law.”1
That still might not be a satisfying definition. So let’s put it another way. Essentially, forensics is the process whereby scientific principles are applied to the task of gathering and processing evidence. Whether the evidence is DNA, matching bullets to guns, or fingerprint analysis, the concept is the same. The investigator applies well-tested scientific principles to analyze the data and formulate conclusions.
What Is Cyber Forensics?
CERT (Computer Emergency Response Team) defines cyber forensics in this manner: “If you manage or administer information systems and networks, you should understand cyber forensics. Forensics is the process of using scientific knowledge for collecting, analyzing, and presenting evidence to the courts. (The word forensics means “to bring to the court.”) Forensics deals primarily with the recovery and analysis of latent evidence. Latent evidence can take many forms, from fingerprints left on a window to DNA evidence recovered from blood stains to the files on a hard drive.”2
There are really two primary objectives in cyber forensics. The first is to find out what happened. What data was affected, what files, what was done? Was there a denial-of-service attack, a virus, or perhaps sensitive files stolen? The first goal is to gather facts, to know what occurred and, if possible, to know how and when it occurred. The second objective is to collect data in a manner that is acceptable to a court. As you continue in this book, we will discuss how to ensure that the data is collected in the appropriate manner.

EXAM TIP Various organizations have established their own guidelines for digital forensics. The Certified Cyber Forensics Professional test focuses heavily on the standards published by the Scientific Working Group on Digital Evidence (www.swgde.org), and you will see their standards referenced frequently within this book.
Cyber forensics is a more appropriate term than computer forensics. Computers are not the only objects of forensic investigations. Any device that can store data is potentially the object of cyber forensics. That includes computers, but also includes smart phones, routers, tablets, printers, tablets, and GPS devices, even vehicle GPSs.
While the subject of cyber forensics, as well as the tools and techniques used, is significantly different from traditional forensics (like DNA analysis and bullet examination), the goal is the same: to obtain evidence that can be used in some legal proceeding. However, a few principles will be introduced now and dealt with in more detail later.
The first is securing the scene. You have to ensure that the crime scene is secure before proceeding to collect evidence. In the case of cybercrime, the “crime scene” could be a PC, cell phone, or server. It is imperative to make sure the device is not being monitored, and most importantly, that evidence is not being destroyed.
The other concept that is critical to forensics investigations is the chain of custody. Chain of custody is a documentation trail from the time that you secure the crime scene to the time the evidence is presented at court. You must be able to show clear documentation of every place the evidence was at, how it was stored, how it was secured, who accessed the evidence, and how they accessed it. Any break in the chain of custody is likely to render the evidence inadmissible in court.
Understanding the Science of Forensics
Forensics, of any type, is first and foremost a science. This means there are well-established scientific principles one must adhere to when conducting a forensic investigation. This is not an art, and there is no place for “gut feelings.” Chapters 2 and 3 will delve more deeply into these topics.
What do we mean when we say “well-established scientific principles”? First, scientific investigation is a very special way of thinking. In a scientific investigation, one forms a hypothesis, tests that hypothesis, and then records the results. A hypothesis must be a testable question. Questions that cannot be subjected to testing have no place in science. For example, in a cyber forensic investigation, you may hypothesize that there are deleted files on a suspect PC that can be recovered. You test that hypothesis by using an undelete tool to recover those files. If you find there are no files to recover, then you must reject your hypothesis. The nature of any scientific inquiry is to follow the evidence, even if it leads to conclusions we did not expect, or did not even want.
This brings us to the topic of “testing the hypothesis.” How do you test it? In any forensic investigation, you can only use well-established scientific tests. This means tools and techniques that have been widely accepted in the relevant scientific discipline—in this case, in the fields of computer science and engineering.
Elements of the Crime
What are the essential elements of the crime? This may seem a bit removed from forensic analysis. And it is true that not all forensics involves criminal cases. However, if a criminal case is involved, you should at least be aware of the elements of a crime. There are two main factors needed for a crime to be committed, which the following sections discuss.
Law
There must be some law that was broken. That may sound obvious, but you might find some conduct objectionable but not criminal. For example, it is legal for someone to provide biased stock advice on the Internet, as long as somewhere on their website they disclose the nature of the bias. That might be unethical, but it is not criminal.
Intent
Someone cannot accidentally commit a crime. They can accidentally commit a civil tort and be sued, but criminal law requires intent. For example, in a case of alleged child pornography, it may not be enough that a single image exists on the suspect’s computer. Forensics can help establish intent by showing when the suspect last accessed the image, if the suspect deliberately downloaded it, etc.
Burden of Proof
Depending on the case, the burden of proof might be a bit different. For example, in criminal cases, the burden of proof is “beyond a reasonable doubt.” It is not enough to show that the accused could have committed the crime, and might have committed the crime; you have to show “beyond a reasonable doubt” that they did commit the crime. Usually, defense attorneys attempt to introduce alternative theories of the crime in order to introduce reasonable doubt.
With civil cases, the standard is “by a preponderance of the evidence.” This is less than the “beyond a reasonable doubt” standard. Essentially, in a civil case, you just have to show that it is highly likely that the accused committed the offense in question.
Exculpatory Evidence
This is a rather simple concept, but an important one. Exculpatory evidence is evidence that proves the accused innocent. Let us assume you are investigating a computer wherein the suspect is accused of creating a virus and releasing it. Yet in your investigation, you find evidence that the suspect may have actually been a victim of the virus himself and accidentally downloaded it. That would constitute exculpatory evidence. In criminal cases, prosecutors have a legal duty to turn over exculpatory evidence to the defense.
Knowledge Base Needed for Cyber Forensics
Cyber forensics is not an area for novices. If you are new to computer science in general, you should get a solid background in hardware, basic networking, and operating systems before pursuing forensics. In this book (and on the CCFP exam), it is assumed that you have that background. If you don’t, the following section gives a brief overview of the bare minimum knowledge you should have. This is also useful if it has been a while since you studied one or more of these topics and need a refresher.
Hardware
It should be obvious that it is impossible to perform forensic analysis of computers without some knowledge of computers. In general, this means a working knowledge of motherboards, hard drives, RAM, expansion slots, etc. This would be equivalent to the knowledge gained from a basic PC course at a university or the level of knowledge tested on the CompTIA A+ certification. This merely covers computers, however. If you intend to perform forensic analysis of cell phones, vehicle GPS devices, routers, tablets, or other devices, you will need to be familiar with the hardware in those devices. For routers, a basic Cisco course and certification, like the CCNA, is a good place to start. At a minimum, you should familiarize yourself with the hardware in any device you intend to examine.
In this section, we will give you a general overview of hardware for PCs, servers, and laptops. The information presented herein should be considered the absolute minimum level of knowledge for a forensic investigator, and you are strongly advised to gain as deep an understanding of computer hardware as you can.
Hard Drives
Since evidence is often found on hard drives, let’s begin by looking at hard drives. The first step is simply to categorize the various types of hard drives you are likely to find.
• SCSI Small Computer System Interface. It is pronounced “scuzzy.” This has been around for many years, and is particularly popular in high-end servers. This standard is actually pretty old—it was established in 1986. SCSI devices must have a terminator at the end of the chain of devices to work and are limited to 16 chained devices. There is also an enhancement to the SCSI standard called Serial SCSI.
• IDE Integrated Drive Electronics. This is an older standard but one that was commonly used on PCs for many years. It is obvious you are dealing with an IDE or EIDE drive if you see a 40-pin drive connector. This was supplanted years ago by Extended IDE (EIDE). Chances are if you find any IDE drives, they will be EIDE. However, neither standard has been used in a long time.
• SATA Serial Advanced Technology Attachment. SATA and solid state are the two most common drives in use today. These devices are commonly found in workstations and many servers. The internals of the hard drive are very similar to IDE and EIDE—it is the connectivity to the computer’s motherboard that is different. Also, unlike IDE or EIDE drives, this type of drive has no jumpers to set the drive.
• Solid State These are becoming more common—in fact, many tablets use solid-state drives (SSDs) because they have a longer battery lifespan (they use less electricity). Unlike the other drive types discussed, SSDs don’t have moving parts like platters, spindles, etc. Since 2010, most SSDs use NAND (Negated AND gate)−based flash memory, which retains memory even without power. Unfortunately, this type of memory has a shorter lifespan than traditional hard drives.
Hard drives record data by magnetizing ferromagnetic material directionally to represent either a 0 or a 1 binary digit. The magnetic data is stored on platters; the platters are organized on a spindle with a read/write head that reads and writes data to and from the platters. The data is organized as follows:
• A sector is the basic unit of data storage on a hard disk, usually 512 bytes.
• A cluster is a logical grouping of sectors. Clusters can be one sector in size to 128 sectors. That means 512 bytes up to 64KB. The minimum size a file can use is one cluster. If the file is less than the size of a cluster, the remaining space is simply unused.
• Sectors are in turn organized by tracks.
The first practical thing you can use from this information is the issue of the cluster. For any computer operating system, files are stored in clusters. And once a cluster is allocated for a given file, the entire cluster is considered “used” even if it is not being used by that file. For example, assume you have 64KB clusters, and you save a file that is 70KB in size. Two clusters totaling 128KB will be allocated for that file. However, 58KB is not being used. As far as the file system is concerned, that space is allocated for the file. We call this “slack space,” and there are techniques for hiding data in slack space, which we will examine later.
A few other terms you should be familiar with include the following:
• Drive Geometry This term refers to the functional dimensions of a drive in terms of the number of heads, cylinders, and sectors per track.
• Low-Level Format This creates a structure of sectors, tracks, and clusters.
• High-Level Format This is the process of setting up an empty file system on the disk and installing a boot sector. This alone takes little time, and is sometimes referred to as a “quick format.”

EXAM TIP Asking about drive geometry is actually common to not just the CCFP exam, but other forensics tests as well.
The real issue with forensic examination of hard drives is preventing damage to evidence. Knowing that the data is stored magnetically explains why you must keep hard drives away from magnetic sources that could destroy evidence.
It is also important to understand the relationship when there are multiple hard drives. When you have more than one drive, the primary drive (the one that the system boots from) is called the master and the other drive(s) are slaves.
TIP If you have a drive that can no longer boot for whatever reason, take it out and plug it into one of your forensic lab machines as a slave. Then you can boot your lab machine and try to access that drive’s data as a slave.
RAM
RAM, or random access memory, is actually quite important in forensic investigations. It is frequently necessary to do a live memory capture. That means to take what is currently in memory, with the computer still running, and create an image of this. In the early days of cyber forensics, some guidelines suggested you should always shut down a running computer immediately. Eventually, it was realized that there might be things happening in memory that are very important to the investigation and are lost upon shutdown. So live memory captures have become quite important. Therefore, it is important that you have a good understanding of RAM.
There are a variety of ways to categorize RAM. One way is to look at the method whereby data is written to and read from the RAM (these are presented in sequential order from older to newer technologies):
• Extended Data Out (EDO) DRAM Single-cycle EDO has the ability to carry out a complete memory transaction in one clock cycle. Otherwise, each sequential RAM access within the same page takes two clock cycles instead of three once the page has been selected.
• Burst EDO (BEDO) An evolution of EDO, burst EDO DRAM, could process four memory addresses in one burst.
• DRAM (Dynamic Random Access Memory) This is the most common type of memory today, and it has been around for many years, with various improvements, some of which are described here.
• ADRAM Asynchronous DRAM is not synchronized to the CPU clock. This memory is no longer found, and is mentioned only for historical purposes.
• SDRAM Synchronous dynamic random access memory was a replacement for EDO.
• Double Data Rate (DDR) DDR was a later development of SDRAM. We now have DDR2 and DDR3
• Synchronous Graphics RAM (SGRAM) This type of memory is used primarily in certain graphics cards.
• Pseudo-static RAM (PSRAM) This is dynamic RAM with built-in refresh and address-control circuitry to make it behave similarly to static RAM. It is used in various devices, including the iPhone.
• Reduced Latency DRAM (RLDRAM) This type of memory has a high-performance double data rate.
These are the major types of RAM. All of these are volatile memory, and you must keep that in mind when working with live memory capture. We will discuss live memory capture in later chapters in great detail.
Operating Systems
Operating systems are a critical factor in forensics. In this section, we will discuss a basic overview of the major operating systems available today. However, you should absolutely not attempt to perform forensics on a system if you don’t truly understand the operating system. And, as you will see in later chapters, there is no such thing as learning “too much.” Every detail about an operating system might enhance your forensic investigation.
Windows
The Windows operating system has gone through many changes over the years. The first version of Windows that many people are familiar with is Windows 3.1. This was not really an operating system, but more of a graphical user interface that rested on the DOS operating system. With Windows 95 and beyond, there is no separation between operating system and graphical user interface. Rather, the operating system and the graphical user interface are intertwined. However, one can still open up a command prompt and utilize DOS commands. As we explore forensic methods, you will be introduced to specific DOS commands that can be quite useful.
We will get into more details on Windows in later chapters, where we discuss extracting information from Windows, but we can cover a few essentials now. The most critical part of Windows from a forensics perspective is the Windows registry. From this registry, you can get all kinds of information, including the password for wireless networks and the serial numbers for all USB devices that have been connected to that computer.

TIP Most forensics examiners have some knowledge of Windows. However, often their knowledge is not deep enough. The Windows registry is a treasure trove of information. You should delve into it as deeply as you possibly can.
In addition to the registry, Windows has a number of places you should look for evidence. There are certain folders and files (like the index.dat file that we will investigate later in this book) that are great places to find evidence. Even browser cookies and history can be useful. Given that Windows is such a common operating system, it is advisable to be very familiar with it.
Linux
While Linux may not be as common an operating system as Windows, it is very important forensically. There are open-source forensic tools that run on Linux, and even Linux commands that can be used for forensic purposes. You will find a lot of free forensics tools come on Linux, and we will be examining several in this book. In fact, there is a Linux distribution called BackTrack that has an extensive collection of forensics, security, and hacking tools.
Linux is a Unix clone developed originally by Linus Torvalds. There are now well over 100 different distributions (variations) of Linux. However, all have some commonalities. In the Linux world, command-line (called shell in Linux) work is far more important than it is in Windows.
Macintosh
For many years, Apple Macintosh was a complete operating system. However, beginning with OS X, the Macintosh system is based on Free BSD (a Unix clone very similar to Linux). The graphical user interface you interact with is just that, an interface. The underlying operating system is a Unix-like system.
This means that many forensics techniques you can use on Linux can also be used on Macintosh from the shell prompt. There are many such commands and techniques, which we will discuss later in this book.
iOS
iOS was developed by Apple and was released in 2007. It is the operating system used on iPhones, iPads, and the iPod Touch. The interface focuses on direct interaction, such as touching, swiping, tapping, pinching, etc., to make the operating system respond. It is derived from OS X but is significantly different. We will discuss iOS in more detail later in this book when we explore mobile forensics.
Android
Android is a mobile operating system based on the Linux kernel. It was developed by Android, Inc., but is now owned by Google. It is open source, so one can actually download the Android code from the Web; however, many vendors make their own proprietary alterations to it. We will explore Android in more depth later in this book when we discuss mobile forensics.
Files and File Systems
Files and file systems are just as critical as the operating system. It is important to realize that the computer organizes data on a disk according to the file system. The operating system must interact with that file system to interact with files. A few basic facts about files:
• File headers start at the first byte of a file. This is important in forensics, as a suspect may rename a file extension, but examining the first byte will still show what type of file it is.
• The Executable and Linkable Format (ELF, formerly called Extensible Linking Format) is a common standard file format for executables (i.e., programs, applications, etc.), object code, and shared libraries for Unix-based systems.
• Portable Executable (PE) is used in Windows for executables and DLLs (Dynamic Linked Libraries).
• The term area density refers to the data per area of disk.
• Windows Office files have a GUID (Globally Unique Identifier) to identify them.
There are actually quite a few different file systems, but they can be divided into two categories: journaling and nonjournaling. Journaling is basically the process whereby the file system keeps a record of what file transactions take place so that in the event of a hard drive crash the files can be recovered. Journaling file systems are fault tolerant because the file system will log all changes to files, directories, or file structures. The log in which changes are recorded is referred to as the file system’s journal. Thus, the term journaling file systems.
There are two types of journaling: physical and logical. With physical journaling, the system logs a copy of every block that is about to be written to the storage device before it is written. The log also includes a checksum of those blocks to make sure there is no error in writing the block. With logical journaling, only changes to file metadata are stored in the journal.
Specific File Systems This section will give you a brief look at some specific file systems:
• FAT (File Allocation Table) is an older system that was popular with Microsoft operating systems for many years. It was first implemented in Microsoft Stand-alone Disk BASIC.FAT stores file locations by sector in a file called, eponymously, the File Allocation Table. This table contains information about which clusters are being used by what particular files and which clusters are free to be used. The various extensions of FAT (FAT16, FAT32) differ in the number of bits available for filenames. For example, FAT16 only supports 16-bit filenames, whereas FAT32 supports 32-bit filenames. Note that floppy disks use FAT12.

EXAM TIP Floppy disks use FAT12. This is an important forensics fact, and you are likely to be tested on it.
• Microsoft eventually introduced a new file system to replace FAT. This file system is called New Technology File System (NTFS). This is the file system used by Windows NT 4, 2000, XP, Vista, 7, Server 2003, and Server 2008. One major improvement of NTFS over FAT was the increased volume sizes NTFS could support. The maximum NTFS volume size is 264−1 clusters. As of this writing, no version of Windows currently supports volumes that large.
• Extended File System (EXT) was the first file system created specifically for Linux. There have been many versions of EXT—the current version is 4. The EXT 4 file system can support volumes with sizes up to 1 exabyte (1018 bytes, or 1 billion gigabytes) and files with sizes up to 16 terabytes. This is frankly a huge file and volume size, and no current hard drives come even close to that. For an administrator, one of the most exciting features of EXT 4 is that it is backward compatible with EXT 2 and EXT 3, making it possible to mount drives that use those earlier versions of EXT.
• The Reiser File System is a popular journaling file system, used primarily with Linux. Reiser was the first file system to be included with the standard Linux kernel and first appeared in kernel version 2.4.1. Unlike some file systems, Reiser supported journaling from its inception, whereas EXT did not support journaling until version 3. Reiser File System is open source and was invented by Hans Reiser.
• The Berkeley Fast File System is also known as the Unix File System. As its names suggest, it was developed at Berkeley specifically for Unix. Like many file systems, Berkeley uses a bitmap to track free clusters, indicating which clusters are available and which are not. Like EXT, Berkeley includes the File System Check (FSCK) utility. This is only one of many similarities between Berkeley and EXT. In fact, some sources consider EXT to just be a variant of the Berkeley Fast File System.
Networks
Modern cyber forensics is very much intertwined with network operations. Many computer crimes take place across the network. Thus, it is imperative that any forensic examiner have a strong understanding of basic networking—something equivalent to the depth and breadth of knowledge to be gained from a good general networking course at a university, or perhaps the level of knowledge tested on the CompTIA Network+ certification. In this section, we will cover the absolute bare minimums of networking knowledge you must have to function as a forensic analyst. It is strongly recommended that you continue your study of networking beyond what is given in this section.
The Physical Connection
One of the first things to understand is the actual physical connection. Of course, many networks are now wireless, but physical connections are still important. The first thing to examine is your network interface card, commonly called a NIC. This is the card on your computer that you plug a cable into.
The cable connection used with traditional NICs (meaning not wireless) is an RJ 45 connection. (RJ is short for “registered jack.”) In contrast to the computer’s RJ 45 jacks, standard telephone lines use RJ 11 jacks. The biggest difference between jacks involves the number of wires in the terminator. Phone lines have four wires or in some cases six, whereas RJ 45 connectors have eight.
This type of cable is also often referred to as unshielded twisted-pair (UTP) cable. In UTP, the wires in the cable are in pairs, twisted together without any additional shielding. Each subsequent category of cable is somewhat faster and more robust than the last. It should be noted that although Cat-4 can be used for networks, it almost never is used for that purpose. You will usually see Cat-5 cable, and increasingly Cat-6; however, Cat-7 is also available.
Cat-5 cable works at speeds of up to 100 megabits per second (mbps), whereas Cat-6 works at 1000 mbps. It is widely available now, and has been for several years. However, for it to truly function properly, you need hubs/switches and NICs that also transmit at gigabit speeds. Category 7 is the latest advance in twisted-pair cabling, with frequencies up to 1000 MHz and speeds of up to 40 Gigabit Ethernet at 50 meters (164 ft) and 100 Gigabit Ethernet at 15 meters. Cat-5 is still found in many networks, with Cat-6 also being very common.
Coax cable has also been used for networking. It looks much like the coax cable used for your television. Two primary types are used for networking. The first is RG (an abbreviation for Radio Guide) 58 for Thinnet and RG 8 for Thicknet. Both are very resistant to crosstalk and interference.
Fiber-optic cable is becoming more common. There are two primary modes for fiber optic: The single-mode fiber optic is more expensive than the multimode fiber-optic cables and requires a light source with a narrow spectral width for propagation. The single-mode fiber (SMF) is a single strand of glass fiber with a core diameter less than 10 microns and has one mode of transmission.

TIP Fiber-optic cables are also called optic cables (OC), and their bandwidth is denoted by an OC number such as OC 3. A few common OCs are
OC3 155 megabits per second.
OC12 622 megabits per second. The equivalent of 336 T1 lines or 8,064 phone lines.
OC48 2.5 gigabits per second. The equivalent of four OC12 lines.
WiFi
Wireless is obviously becoming more widespread. There are various types of WiFi connections, all of which are based on the 802.11 standard. A brief summary of the variations is as follows:
• 802.11a WiFi 5 GHz wireless. This was the first 802.11 WiFi standard and is no longer used.
• 802.11b WiFi 2.4 GHz wireless. This is the networking commonly used in homes and SOHO (small office/home office) environments. It is being replaced by the faster 802.11g standard. It uses a wireless access point (WAP) to connect to other wireless computers. It has an indoor range of 125 ft and a bandwidth of 11 mbps.
• 802.11g WiFi 2.4 GHz wireless. This networking is also commonly used in homes and SOHO environments. It uses a WAP to connect to other wireless computers. It is backward compatible with 802.11b. It has an indoor range of 125 ft and a bandwidth of 54 mbps.
• 802.11n WiFi 2.4 or 5.0 GHz wireless. This standard has a bandwidth of 100 to 140 mbps and an indoor range of 230 ft.
• IEEE 802.11n-2009 This standard has a bandwidth of up to 600 Mbit/s with the use of four spatial streams at a channel width of 40 MHz. It uses multiple-input multiple-output (MIMO), which uses multiple antennas to coherently resolve more information than is possible using a single antenna.
Today, you are most likely to find 802.11n, usually just called “n” WiFi. There are three different WiFi security modes: WEP, WPA, and WPA2.
Wired Equivalent Privacy (WEP) uses the stream cipher RC4 to secure the data and a CRC-32 checksum for error checking. Standard WEP uses a 40-bit key (known as WEP-40) with a 24-bit initialization vector to effectively form 64-bit encryption. 128-bit WEP uses a 104-bit key with a 24-bit initialization vector. RC4 is a very good algorithm; however, it was implemented poorly in WEP. The initialization vector should be used once, but that is not the case with WEP. Therefore, WEP is relatively easy to crack.
WiFi Protected Access (WPA) uses the Temporal Key Integrity Protocol (TKIP). TKIP is a 128-bit-per-packet key, meaning that it dynamically generates a new key for each packet.
WPA2 is the only one of the three that fully implements the security features of the 802.11i standard. WPA2 uses the Advanced Encryption Standard (AES) with the Counter Mode-Cipher Block Chaining (CBC)-Message Authentication Code (MAC) Protocol (CCMP) that provides data confidentiality, data origin authentication, and data integrity for wireless frames.
Connection Devices
There are three connection devices that should also be discussed: the hub, the switch, and the router.
The Hub The simplest connection device is the hub . A hub is a device into which you can plug in network cables. It will have four or more ports, most likely RJ 45 jacks. You can also connect one hub to another; this strategy is referred to as “stacking” hubs. If you send a packet (we’ll discuss packets in a following section) from one computer to another, a copy of that packet is actually sent out from every port on the hub. There is no routing of any type. This was an old network traffic method that is no longer used today.

NOTE If you go to an electronics store and request a hub, they will give you a switch.
The Switch A switch is basically an intelligent hub. A switch works and looks exactly like a hub, but with one significant difference. When it receives a packet, it will send that packet out only on the port it needs to go out on. A switch accomplishes this routing by using the MAC address (described a little later in this chapter) to determine where the packet should be routed to.
The Router Finally, if you wish to connect two or more networks together, you use a router . A router is much like a switch, except that it routes traffic based on the IP address. Routers can also incorporate all types of network functionality such as a firewall.
What Is a Packet?
Packets are used to transmit data. The basic purpose of cable is to transmit packets from one machine to another. It does not matter whether that packet is part of a document, a video, an image, or just some internal signal from one computer to another. A packet is a certain number of bytes divided into a header and a body. The header tells you where the packet is coming from, where it is going, what type of packet it is, and more. Modern packets often have multiple headers. For example, standard network traffic will have an Ethernet header, TCP header, and IP header. The body contains the actual data, in binary format, that you wish to send. The aforementioned routers and switches work by reading the header portion of any packets that come to them. Packets usually have a footer that does some sort of error checking.
Protocols
There are different types of communications for different purposes. The different types of network communications are called protocols . A protocol is, essentially, an agreed-upon method of communication. Each protocol has a specific purpose and normally operates on a specific networking port. There are a total of 65,535 possible ports—1,024 are called “well-known ports.” Some of the most important protocols are listed in Table 1-1.
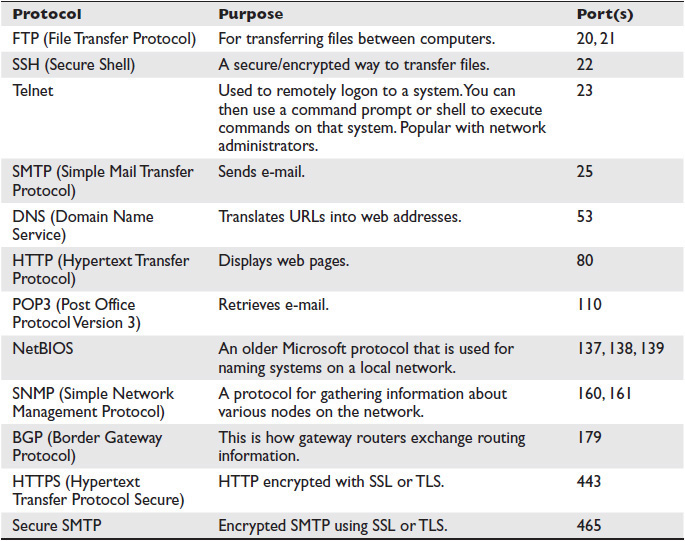
Table 1-1 Protocols and Ports
As was already mentioned, there are 1,024 “well-known ports,” so the list in Table 1-1 is not comprehensive. All of these protocols are part of a suite of protocols referred to as TCP/IP (Transmission Control Protocol/Internet Protocol). A port is, essentially, a channel through which communication can occur. The communication is still occurring via the NIC over either cable or wireless. As we will see in later chapters, the knowledge of ports can be very important in forensic investigation of network attacks.
IP Addresses
An IP (Internet Protocol) address is an address assigned to a machine (PC, laptop, server, tablet, smart phone, router, etc.). There are currently two types of IP addresses: IP v4, which is widely used, and IP v6, which is a new standard gaining wide acceptance. An IP v4 address is a series of four 3-digit numbers, separated by periods. (An example would be 107.22.98.198.) Each of the three-digit numbers must be between 0 and 255. The reason for this number range is that the IP address is actually four binary numbers; you just see them in decimal format. Recall that a byte is 8 bits (1’s and 0’s), and an eight-bit binary number converted to decimal format will be between 0 and 255.
IP v4 The IP v4 addresses come in two groups: public and private. The public IP addresses are for computers connected to the Internet. No two public IP addresses can be the same. However, a private IP address, such as one on a private company network, only has to be unique in that network. It does not matter if other computers in the world have the same IP address because this computer is never connected to those other worldwide computers. Often, network administrators use private IP addresses that begin with a 10, such as 10.102.230.17. The other private IP addresses are 172.16.0.0−172.31.255.255 and 192.168.0.0−192.168.255.255.
When you, as a forensic investigator, are tracing an IP address, be aware of a few facts. The first is that ISPs (Internet Service Providers) buy pools of IP addresses and assign them as needed. So if you trace suspect communication back to an IP address belonging to some ISP, you will then need to obtain more information from that ISP, often through a subpoena. The second issue is that IP addresses are easy to spoof. Someone can fake an IP address so that their traffic appears to be coming from somewhere else. This is commonly done in denial-of-service attacks.
IP v6 IP v6 utilizes a 128-bit address instead of a 32-bit one and utilizes a hex numbering method in order to avoid long addresses such as 132.64.34.26.64.156.143.57.1.3.7.44.122.111.201.5. The hex address format will appear in the form of 3FFE:B00:800:2::C, for example. This gives you 2128 possible address (many trillions of addresses), so there is no chance of running out of IP addresses in the foreseeable future.
MAC Addresses
A Media Access Control (MAC) address is a unique address for a NIC. Every NIC in the world has a unique address that is represented by a six-byte hexadecimal number. The Address Resolution Protocol (ARP) is used to convert IP addresses to MAC addresses. So when you type in a web address, the DNS protocol translates that into an IP address. Then, the ARP protocol will translate that IP address into a specific MAC address of an individual NIC.

TIP It is also possible for someone to spoof a MAC address, but this takes a bit more skill and is less common than spoofing an IP address. So when tracing down criminal activity, gathering MAC addresses is very important.
Basic Network Utilities
As already mentioned, there are network utilities that you can execute from a command prompt (Windows) or from a shell (Unix/Linux). Many readers are already familiar with Windows, so this discussion will execute the commands and discuss them from the Windows command-prompt perspective. However, it must be stressed that these utilities are available in all operating systems. In this section, you will learn about IPConfig, ping, and tracert utilities.
IPConfig The first thing you will want to do when determining the network status of the system you are examining is to get some information about that system’s network connection. This may include the MAC address, IP address, etc. To accomplish this fact-finding mission, you will need to get a command prompt. In Windows 7, you do this by going to the Start menu, selecting All Programs, and then choosing Accessories. You will then see an option called Command Prompt. For Windows 8 users, accessing the program requires clicking the Start menu on the bottom-left side and scrolling right until you see the program you are looking for. You may then need to right-click and select All Apps to find the command prompt.
However you find the command prompt, now you can type ipconfig. (You could input the same command in Unix or Linux by typing ifconfig from the shell.) After typing ipconfig (ifconfig in Linux), you should see something much like what is shown in Figure 1-1.

Figure 1-1 ipconfig
This command gives you some information about your connection to a network (or to the Internet). Most importantly, you find out your own IP address. The command also has the IP address for your default gateway, which is your connection to the outside world. Running the IPConfig command is a first step in determining your system’s network configuration.

TIP There are also variations or command flags you can add. For example, ipconfig /all will give you more details. Ipconfig/release releases a dynamically assigned IP address.
Ping Another commonly used command is ping. Ping is used to send an echo packet to a machine to find out if the machine is reachable and how long the packet takes to reach the machine. The command is shown in Figure 1-2.
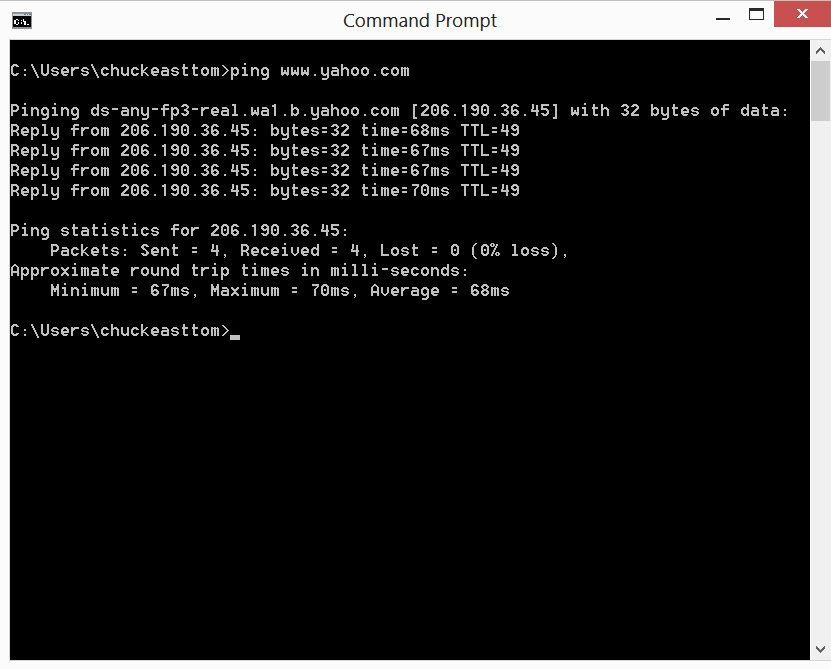
Figure 1-2 ping
This figure demonstrates that a 32-byte echo packet was sent to the destination and returned. The ttl item means “time to live.” That time unit is how many intermediary steps, or hops, the packet should take to the destination before giving up. Remember that the Internet is a vast conglomerate of interconnected networks. Your packet probably won’t go straight to its destination. It will have to take several hops to get there. As with all command-line utilities, you can type ping -? to find out various ways you can refine your ping.
Tracert The final command we will examine is tracert. This command is sort of a ping “deluxe.” Tracert not only tells you if the packet got there and how long it took, but also tells you all the intermediate hops it took to get there. (This same command can be executed in Linux or Unix, but there it is called “traceroute” rather than “tracert.”) You can see this utility in Figure 1-3.

Figure 1-3 tracert
Netstat Netstat is short for network status. It shows the current connections that machine is engaged in. This is very important from a forensic perspective. If you come upon a suspect machine that is running, before shutting that machine down, you should run netstat to determine connections. You can see netstat in Figure 1-4.

Figure 1-4 Netstat

TIP All of these commands have flags that you can learn about by typing the command name followed by a question mark—for example, ipconfig -?. These commands are all useful in forensics, and you should become very familiar with them.
This section is just a brief overview of the hardware, software, and networking knowledge you should have in order to study forensics. If you find you are lacking in one or more areas, it is probably a good idea to review that material before proceeding beyond this chapter.
The Fundamental Principles of Cyber Forensics
We briefly mentioned earlier in this chapter the need to secure the crime scene and to maintain chain of custody. These are two fundamental principles of forensics. We will be examining various such principles in detail throughout this book. However, let’s examine the two fundamental principles right now.
Securing the Crime Scene
The first, and perhaps most critical, step once you begin to actually analyze the evidence is to secure the crime scene. That usually means stopping access to the suspect system. In the past, various organizations have recommended immediately powering down the computer; however, it was discovered that this often led to a loss of evidence. So the recommendation now is to note all current connections, running software, processes, etc., and then shut down the system.
It is also important to then make sure the system is not accessible to any outside party. For laptops, this can mean turning off the wireless network card. For cell phones and other devices, it might mean transporting the device in some container that inhibits transmissions, such as a Faraday bag.
Limiting Interaction with the Evidence
Once the crime scene is secured, the next step is to make certain that you touch the actual evidence as little as possible. It is important that the investigator avoid any possibility of contaminating the evidence. For that reason, one of the first steps in a forensic investigation of a computer is to create a bit stream image of the hard drive; then the investigator investigates that image, not the original drive. This prevents any accidental tampering with the evidence. It is also important to use a write blocker. This is a device that prevents accidental writing of data to a storage device.
You can make a forensic copy with most major forensics tools, such as AccessData’s Forensic Toolkit, or Guidance Software’s EnCase. However, it can also be done with free tools using Linux. It is probably a good idea to understand how to do this manually even if you plan to use an automated forensic tool.

Tip One issue to keep in mind is testifying at deposition or trial. The opposing counsel might have a forensic expert advising them, and one common tactic is to ask you technical questions about your process. If you used an automated process, that is fine, as long as you can explain how it works. If not, you may find your testimony and your results excluded.
To make an image of a drive using Linux, you will need a bootable copy of Linux. Almost any Linux distribution will work. I personally use BackTrack. You will actually need two copies of a bootable Linux CD—one on the suspect machine and one on the target machine. Whichever version of Linux you use, the steps will be the same.
First, we have to completely wipe the target drive. This is done with the following command executed on the target drive:
![]()
Now we need to set up that target drive to receive the copy of the suspected drive we wish to examine. The Netcat command helps with that. The specific syntax is as follows:
![]()
We are telling the machine to listen on port 8888 and put whatever it receives into the file evidence.dd.
Now on the suspect machine we have to start sending the drive’s information to the forensics server:
![]()
Of course, this example assumes that the suspect drive is hda1. If this were not the case, then you would replace that part of the command with the partition you are using. This example also assumes the server has an IP address of 192.168.0.2. If this were not the case, you would replace it with whatever your forensics server IP address is.
Now that we have made a copy, we need to ensure it was done properly. The method for this is to create a cryptographic hash of the original drive and the copy we just made. Most forensics toolkits will do this, but we can also do it from the Linux command line:
![]()
Maintaining Chain of Custody
We have already mentioned the need to maintain the chain of custody—this is done via a thorough document trail. A forensic investigator must document everything. The more documentation, the better. Document the scene where evidence is seized, the condition of equipment, and photograph as much as is practical. Then document how the evidence is seized and transported. Document the specifics of how the evidence is stored. And, of course, document the details of all tests performed on the suspect machine, beginning with the imaging of the machine.
The Law and Cyber Forensics
While state laws may vary, U.S. federal laws are not only consistent throughout the United States, but often supersede state laws in matters of computer crime. Computer crimes often involve interstate commerce, financial institutions, or other factors that render them federal crimes.
Many laws affect forensic investigation. For example, some jurisdictions have passed laws requiring that in order to extract the evidence, the investigator must be either a law enforcement officer or a licensed private investigator. Of course, that does not prevent a forensic investigator from either working with data someone else extracted or extracting evidence if the data owner gave their permission. It is important to be aware of the legal requirements in the jurisdiction you work in.
That is just one of many laws that will be important to you as a forensic investigator. It is impossible for any book to cover all the laws you should know. However, there is one principle that is key to forensics and is all too often overlooked in forensics books. That is the Daubert standard. The Cornell University Law School describes the Daubert standard in the following manner:3
Standard used by a trial judge to make a preliminary assessment of whether an expert’s scientific testimony is based on reasoning or methodology that is scientifically valid and can properly be applied to the facts at issue. Under this standard, the factors that may be considered in determining whether the methodology is valid are: (1) whether the theory or technique in question can be and has been tested; (2) whether it has been subjected to peer review and publication; (3) its known or potential error rate; (4) the existence and maintenance of standards controlling its operation; and (5) whether it has attracted widespread acceptance within a relevant scientific community.
What this means, in laymen’s terms, is that you should only use tests, software, and equipment that has gained wide acceptance in the industry. If you conduct any part of your investigation with tools or techniques that have not been properly vetted by the scientific community, opposing counsel may issue a “Daubert challenge” claiming your evidence should be excluded. If they are successful, then any evidence you have collected will be excluded from the trial. Throughout this book, we will only use widely accepted tools and techniques.
General Legal Issues
There are two main branches of law: civil and criminal. Criminal law deals with intentional violations of law. Civil law deals with acts that may or may not be intentional, but the penalties don’t involve incarceration. A civil wrong is called a tort.
“Torts are civil wrongs recognized by law as grounds for a lawsuit. These wrongs result in an injury or harm constituting the basis for a claim by the injured party.”4Essentially, a tort results in a lawsuit where monetary damages may be awarded. In a civil case, the primary objective is to assess liability. Liability simply means who is responsible for the tort (if anyone) and then to assess the proper monetary value for that liability.
In any legal proceeding, the two parties are referred to as litigants. In a civil case, they are the plaintiff (the party that filed the lawsuit) and the defendant (the party being sued). It is not uncommon for there to be a countersuit where the defendant is also suing the plaintiff. It is also possible in civil law for one of the parties to be an organization or corporation rather than an individual.
In criminal law, the litigants are the prosecutor and the defendant. The prosecutor works for a government agency. When dealing with local crimes, that agency will be the district attorney’s office. In federal crimes, it will be the U.S. Attorney’s office. The defendant is represented by an attorney who is an advocate for their client. As a forensic analyst, you may work for either litigant. Keep in mind that, regardless of the attorney’s role, you are not an advocate for either party. Your job is to dispassionately find the truth.
Discovery
In either a civil or criminal case, discovery is the process of each litigant finding out what evidence the other party has. In a criminal case, the prosecutor has a legal obligation to turn over all evidence to the defense attorney. The defense attorney does not have a reciprocal obligation. It is legal for the defense to hold on to exculpatory evidence until trial. Now there are some caveats to this, and they will vary from one jurisdiction to the next.
In a civil case, both parties are required to provide evidence if the opposing party asks for it. The first step in that is a simple request for documents. The next step includes what are called interrogatories. These are essentially a list of questions the opposing side is required to answer under oath. Finally, there are depositions. This is a chance for each side to question the opposing side under oath before trial.

NOTE The concept of “under oath” is very important. Lying under oath is a crime, and one that judges take very seriously.
The scope of discovery is not unlimited. A common objection attorneys make to an interrogatory or a request for documents is that it is beyond the scope of the case. Litigants are only entitled to relevant discovery, not an unfettered fishing expedition.
A related, and popular, trend is e-discovery. This is merely the electronic version of discovery. The litigants exchange documents in electronic format. This is becoming increasingly common as more and more law firms rely on computer technology.
Warrants
When seizing any property, including computers, cell phones, or other electronic devices, it is important to be sure you have the legal authority to do so. If you illegally seize evidence, then that evidence will most likely be excluded from any legal proceedings. The most common way to legally seize evidence is with a warrant issued by a court.
According to the Supreme Court, a “‘seizure’ of property occurs when there is some meaningful interference with an individual’s possessory interests in that property” United States v. Jacobsen, 466 U.S. 109, 113 (1984), and the Court has also characterized the interception of intangible communications as a seizure in the case of Berger v. New York, 388 U.S. 41, 59−60 (1967). Now that means that law enforcement need not take property in order for it to be considered seizure. Merely interfering with an individual’s access to his or her own property constitutes seizure. And Berger v. New York extends that to communications. Now if law enforcement’s conduct does not violate a person’s “reasonable expectation of privacy,” then formally it does not constitute a Fourth Amendment “search” and no warrant is required.
There have been many cases where the issue of reasonable expectation of privacy has been argued. But to use an example that is quite clear, if I save a message in an electronic diary, I clearly have a reasonable expectation of privacy. However, if I post such a message on a public bulletin board, I can have no expectation of privacy. In less clear cases, a general rule is that courts have held that law enforcement officers are prohibited from accessing and viewing information stored in a computer if they would be prohibited from opening a closed container and examining its contents in the same situation.
In computer crime cases, two consent issues arise particularly often. First, when does a search exceed the scope of consent? For example, when a person agrees to the search of a location—for example, their apartment—does that consent authorize the retrieval of information stored in computers at the location? Second, who is the proper party to consent to a search? Can roommates, friends, and parents legally grant consent to a search of another person’s computer files? These are all very critical questions that must be considered when searching a computer. In general, courts have held that the actual owner of a property can grant consent. For example, a parent of a minor child can grant consent to search the living quarters and computers. However, a roommate who shares rent can only grant consent to search living quarters and computers that are co-owned by both parties. A roommate cannot grant consent to search the private property of the other person.
Federal Guidelines Forensics Investigators Need to Know
If you are setting up a forensics lab, or if you are new to forensics, a good place to start would be the federal guidelines. Two agencies in particular—the FBI and the Secret Service—are important sources of guidelines.
FBI
While the Secret Service is now the premier federal agency responsible for cybercrime, the FBI is also involved in many computer crime cases. Prior to the Patriot Act, the FBI took the lead role in computer crime investigations. The FBI lists its own guidelines, though they are largely consistent with those of the Secret Service. Those guidelines are explained in this section.
If an incident occurs, the FBI recommends that the first responder preserve the state of the computer at the time of the incident by making a backup copy of any logs, damaged or altered files, and, of course, any files left by the intruder. This last part is critical. Hackers frequently use various tools and may leave traces of their presence. Furthermore, the FBI warns that if the incident is in progress, activate any auditing or recording software you might have available. Collect as much data about the incident as you can. In other words, this might be a case where you do not take the machine offline, but rather analyze the attack in progress.
The FBI computer forensic guidelines stress the importance of securing any evidence. They further stress that computer evidence can come in many forms. A few common forms are
• Hard drives
• System logs
• Portable storage (USB drives, external drives, etc.)
• Router logs
• E-mails
• Chat room logs
• Cell phones
• SIM cards for cell phones
• Logs from security devices such as firewalls and intrusion detection systems
• Databases and database logs
Obviously, what you secure will depend upon the nature of the cybercrime. For example, in the case of child predators, online stalkers, or online fraud, e-mail may be very important but router logs may be irrelevant. The FBI also stresses that you work with a copy of the hard drive, not the original.

TIP The FBI has a cybercrimes5 web page, which is a very useful resource for learning more about trends in cybercrime and in cyber forensics.
Secret Service
The U.S. Secret Service is the premier federal agency tasked with combating cybercrime and with cyber forensics. They have a website devoted to cyber forensics6 that includes forensics courses. These courses are usually for law enforcement personnel.
The Secret Service also has released a guide for first responders to computer crime.7They have listed their “golden rules” to begin the investigation. Those are
• Officer safety. Secure the scene and make it safe.
• If you reasonably believe that the computer is involved in the crime you are investigating, take immediate steps to preserve the evidence.
• Do you have a legal basis to seize this computer (plain view, search warrant, consent, etc.)?
• Do not access any computer files. If the computer is off, leave it off.
• If it is on, do not start searching through the computer. If the computer is on, go to the appropriate sections in this guide on how to properly shut down the computer and prepare it for transportation as evidence.
• If you reasonably believe that the computer is destroying evidence, immediately shut down the computer by pulling the power cord from the back of the computer.
• If a camera is available and the computer is on, take pictures of the computer screen. If the computer is off, take pictures of the computer, the location of the computer, and any electronic media attached.
• Do special legal considerations apply (doctor, attorney, clergy, psychiatrist, newspapers, publishers, etc.)?
These are all important first steps to both preserving the chain of custody and ensuring the integrity of the investigation from the outset.
The Need for Cyber Forensics Certification
Why certifications? This question has been bandied about the information technology field for years. Various pundits come down upon one extreme or the other, with some claiming certifications are invaluable and others claiming they are worthless. Also, some subindustries within IT have different attitudes about certifications. In the Cisco world, certifications are kingpin, while in the Linux community, certifications have negligible value. So what is the worth of certifications in forensics?
First, one must examine the purpose of certifications—what does it mean to be “certified”? Frequently, people who have a dim view of certifications have that view because they have encountered someone with some certification who was not very competent. This denotes a misunderstanding of what any certification is. Certification is supposed to indicate that the holder of that certification has met a minimum standard. It does not mean that the person in question is the master of that topic, but rather, that they are competent. A good analogy would be a medical degree. That does not guarantee the person is a great doctor, merely that they have obtained a minimum competency in medicine.
However, it is possible to pass a certification test and not be very good at the topic. But the same is true of any field and any educational endeavor. There are certainly some medical doctors (thankfully few) who are incompetent. But if you suddenly have chest pains, I bet you would prefer someone call you a medical doctor rather than a plumber. Why? Because the odds of a medical doctor having the requisite skill is much higher than that of a plumber. The same is true for IT certifications. While it is certainly possible that someone could be certified and not be competent, the odds that a certified person is competent are much higher. That is why employers frequently require or prefer certifications. It makes the job of filtering through applicants much easier.
So any IT certification can be one valuable indicator of a job applicant’s skill. It is not the only indicator, and certainly should not be the only thing considered, but it is one factor. This brings us to forensic certifications. Is there a need for another one? First look at what cyber forensics certifications are currently available.
AccessData, the creators of the Forensic Toolkit, have multiple certifications for their product, as does Guidance Software, the creators of EnCase. Both of those vendor certifications are quite good. However, they are also both vendor certifications. The emphasis is on the particular proprietary suite of tools rather than on a general coverage of cyber forensics. If you are going to work with either tool, it is a very good idea to get the appropriate vendor certification, but that is not the same thing as a broad-based cyber forensics course/test.
The EC-Council has their Computer Hacking Forensic Investigator test, and it has been somewhat popular. However, as the name suggests, it has an emphasis on hacking and counter-hacking. The EC-Council’s primary focus has always been hacking.
This brings us to the topic of (ISC)2’s Certified Cyber Forensics Professional. Is this certification test worth taking? The first thing to realize is that (ISC)2 has a long history of well-respected certification courses/tests, starting with the CISSP, which is the oldest and most well-known computer security certification. This means the CCFP is backed by a strong support organization. The content of the course/test is also very good. The domains covered include forensic science, application forensics, investigatory procedures, law, and ethics. It is just the sort of broad coverage of cyber forensics that is needed.
Chapter Review
Forensics of any type is a science, and that is absolutely true with cyber forensics. Any sort of digital media can be the object of a cyber forensic investigation. This includes cell phones, routers, computers, tablets, even the new Google Glass. If an item can digitally store data, then it can be forensically examined by a cyber forensics investigator.
Cyber forensics requires a strong working knowledge of PCs, operating systems, and networking. That knowledge is the foundation of cyber forensics. The equivalent of a CompTIA A+ and Network+ certifications should be considered the base level of knowledge.
A variety of laws and principles are critical to cyber forensics, principles such as touch the evidence as little as possible; always work with an image of the drive, not the original; and document everything. There are also legal standards such as the Daubert standard that are critical to cyber forensic investigations.
Questions
1. What term describes the route that evidence takes from the time you find it until the case is closed or goes to court?
A. Chain of custody
B. Law of probability
C. Daubert path
D. Separation of duties
2. If a police officer without a warrant locks a door so that a suspect cannot access his (the suspect’s) own computer, what would be the most likely outcome?
A. The evidence will be excluded because the officer seized it without a warrant.
B. The evidence will be excluded because it does not meet the Daubert standard.
C. The evidence will be admitted; this is not a warrantless seizure.
D. The evidence will be admitted; the officer acted in good faith.
3. What U.S. federal agency is most responsible for cybercrime investigation?
A. The FBI
B. Homeland Security
C. NSA
D. Secret Service
4. Which of the following refers to functional dimensions of a drive in terms of the number of heads, cylinders, and sectors per track?
A. Drive layout
B. Hard drive geometry
C. Drive geometry
D. Hard drive layout
5. Space in a cluster not used by a file is called ________.
A. Slack space
B. Unused space
C. Ghost space
D. Empty space
Answers
1. A. Chain of custody, which is a critical concept you must understand for the CCFP exam.
2. A. Yes, any interference with a person’s property is a seizure
3. D. The U.S. Secret Service is the lead organization for cybercrime. This was implemented as part of the Patriot Act.
4. C. Drive geometry is the appropriate term.
5. A. Slack space is the term for unused space at the end of a cluster.
References
1. American Heritage Dictionary. http://education.yahoo.com/reference/dictionary/entry/forensics.
2. CERT Forensics Definition. http://www.us-cert.gov/reading_room/forensics.pdf.
3. Cornell Law School Daubert Standard. http://www.law.cornell.edu/wex/daubert_standard
4. http://www.law.cornell.edu/wex/tort.
5. FBI Cybercrime website. http://www.fbi.gov/about-us/investigate/cyber/cyber.
6. Secret Service, Cyber forensics. http://www.ncfi.usss.gov/.
7. First Responders Guide. http://www.forwardedge2.com/pdf/bestPractices.pdf.
