Chapter 13
Stereoscopic Watermarking
13.1. Introduction
The success of movie releases such as Avatar or Alice in Wonderland marks, for audiences, the coming of age of three-dimensional (3D) stereoscopic cinematography. The launch of 3D television systems allowing direct retransmission of major events has reinforced the trend. This new content presents high added value and increases the risk of illegal copying; therefore, we need to find the means of preserving its intellectual property rights, without imposing additional operational constraints on the underlying chain of production, distribution and consumption.
Watermarking technology presents a response to this need: digital works can be authenticated and traced by inserting additional information that is invisible (transparent) to the user but persistent (robust) against attacks. In practice, the main watermarking challenge is to find a point of operational balance between transparency, robustness and the amount of inserted information. Computational cost is also a key factor in the case of real-time applications.
The state of the art in stereoscopic watermarking is broadly made up of a variety of approaches inherited from 2D/2D+t watermarking. These approaches are based either on spread spectrum (SS) communications theory [COX 02] or on side information (SI) theory [COS 83, SHA 58].
SS techniques offer excellent levels of transparency while guaranteeing robustness for a mark of small size. SI techniques allow the insertion of a larger quantity of information, often to the detriment of transparency and robustness levels. Hybrid methods, which make use of both SS and SI techniques, aim to ensure robustness and transparency while inserting a large quantity of information [MIT 07].
While the capture, production and projection of stereoscopic content are based solely on two views, left and right, the reduction of bandwidth during transmission and/or storage requires the use of intermediary representations, such as disparity maps. This raises questions for the watermarking of stereoscopic video content concerning the optimal domain for insertion.
This issue is the subject of this chapter that is structured into four sections. In section 13.2, we present the constraints of stereoscopic video watermarking. Section 13.3 contains an analysis of different watermarking techniques. Section 13.4 presents experimental results obtained using these techniques, and section 13.5 concludes the chapter, offering perspectives for future research.
13.2. Constraints of stereoscopic video watermarking
13.2.1. Theoretical framework
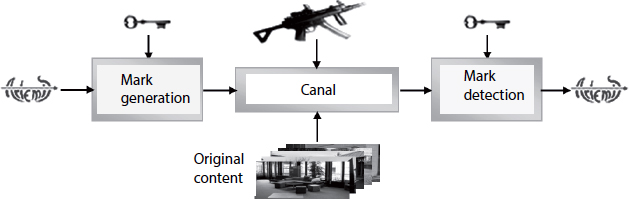
Watermarking techniques [COX 02] consist of inserting additional information (a mark) into multimedia content. This mark must be imperceptible (transparent) and persistent (robust). The information must be found in all replicas of the watermarked content, even following more or less severe transformations, whether malicious or mundane. From a theoretical standpoint, all watermarking processes are modeled by a noisy transmission channel (see Figure 13.1). The mark represents a sample of the information source, which must be transmitted through a channel of this type. The host content and malicious attacks represent noise sources. In this context, the properties of transparency and robustness are contradictory. Our aim is to optimize transmission via the subjacent information channel, i.e. to maximize the quantity of information while respecting transparency and robustness constraints. While the right and left views of stereoscopic content constitute a natural domain for the insertion of a mark, other modes of representation may be considered: the representations defined for optimal transmission in terms of bandwidth for efficient storage of stereoscopic content, for example, also constitute possible domains of insertion. The disparity map, which is clearly interesting as a representation derived from stereoscopic content, may also be considered as original content in Figure 13.1.
Figure 13.1. Theoretical model of watermarking
13.2.2. Properties
13.2.2.1. Transparency
The property of transparency is linked to the (non-)perception of artifacts introduced during the watermarking procedure. It relates to the notions of watermark fidelity and quality. A watermarking procedure is said to demonstrate fidelity if there is no perceivable difference between the original and marked media. However, it is said to be of good quality if the artifacts do not disturb the human user [COX 02].
The assessment of transparency is essentially subjective, and depends on the observer (who will possess personal characteristics such as age, professional experience and visual acuity) and other factors such as the environment, test conditions and evaluation methodology. The International Telecommunications Union (ITU) defines recommendations for evaluating image quality in documents ITU-R BT 500-12 [ITU 02] and BT 1438 [ITU 00]. These recommendations include general test methods, conditions linked to the evaluators, evaluation scales and observation conditions. Evaluators must possess a prescribed level of visual acuity and normal color vision. The number of evaluators depends on the sensitivity and reliability of the selected test procedure, with a lower limit of 15 individuals. Laboratory observation conditions are also specified, including observation distances, screen dimensions and lighting conditions.
In spite of these recommendations, a wide variety of test methods are used. In practice, each evaluation problem requires a particular method. Nevertheless, a five-level perception quality scale has been widely adopted: bad, poor, fair, good and excellent.
As this type of procedure is long and costly, approaches using objective evaluation measurements have been developed. While these measurements cannot guarantee the absolute quality of visual data, they are widely used due to the practical advantages they present: the measurements are automatic, precise, rapid and highlight trends. In this study, the visual quality of content has been assessed objectively using two types of measurements [CHI 11, ESK 95, WAN 04]:
– Pixel difference: peak signal-to-noise ratio (PSNR) and image fidelity (IF).
– Correlation: normalized cross correlation (NCC) and structural similarity (SSIM).
These measurements are calculated individually for each frame of the video sequence, and then averaged across the whole sequence. In an ideal case, for two identical images, the PSNR tends toward infinity and the IF, NCC and SSIM values are equal to 1.
13.2.2.2. Robustness
Robustness is the ability of a watermarking process to resist mundane or malicious attacks, i.e. to recover inserted information after an attack. It can be measured by the bit error rate in the detected mark after an attack. Attacks on video content may be classified according to their effects on the original content. The first attack type (noise, quantification and collusion) aims to make the mark unreadable at detection level. Geometric attacks (rotations, random geometric transformations, etc.) destroy the synchronization of the mark. After an attack of this type, the mark remains present in the video, but is difficult to locate. Protocol attacks aim to make the mark unusable by creating ambiguities. Finally, cryptographic attacks aim to detect the mark without possessing the security key. As the last two attack classes are broadly generic, this study will focus on the first two classes, which are specific to watermarking.
13.2.2.3. Data payload
The data payload is defined by the size of the inserted mark (expressed in bits). It depends on the target application and may vary from 64 bits to approximately 100 kbits per video sequence. The data payload is directly linked to the robustness and imperceptibility of the watermark. The larger the mark, the more perceptible it will be, and its robustness will decrease. The capacity of a watermark is defined as the theoretical upper limit of the quantity of information inserted into original content, which satisfies the imposed constraints of robustness and transparency.
13.2.2.4. Computation cost
The computation cost of a watermarking technique takes into account the execution time and the complexity of the algorithm. The execution time corresponds to the time needed for the mark insertion and detection phases. It is expressed in milliseconds (ms) and must be compatible with real-time services, such as video on demand (VOD) or live television. Knowledge of the complexity of an algorithm allows us to allocate the necessary resources in terms of memory. Analyzing the complexity of candidate algorithms for a given problem allows us to identify the most efficient candidate.
13.2.3. Corpus
13.2.3.1. Constitution criteria
For all types of application and all types of content (text, image, video, etc.), a number of criteria are involved in organizing a corpus [PIN 99]. The main criteria are as follows:
– Significance conditions: as a corpus is generally constructed for a specific study relating to a specific object, a reality as perceived from a certain viewpoint, the study corpus must be relevant and coherent. In our experiments, we will consider both high-definition television sequences and content intended for use by computers or cell phones.
– Acceptability conditions: the corpus must be representative and comprehensive. It must present a level of detail suited to the degree of precision and the desired richness of the results of analysis. For the sequences analyzed in this study, particular attention will be paid to the generation source, the variety of sizes, shape factors and visual/semantic content.
– Exploitation conditions: the corpus must be homogeneous and of a large size. The data that form the corpus must be commensurable and provide enough elements to allow identification of significant behaviors, in the statistical sense of the term. These aspects will be expressed via statistical analysis of 95% confidence intervals
13.2.3.2. Considered corpus
Experimental tests were carried out on two corpora: 3DLive and moving picture experts group (MPEG). Each includes indoor and outdoor scenes, both static and dynamic, in a variety of lighting conditions (see Figures 13.2 and 13.3).
Figure 13.2. Examples of left and right views sampled from the 3DLive corpus: rugby, volleyball, dance, theater play and rock concert sequences

Figure 13.3. Examples of left and right views sampled from the MPEG corpus: roller, office, city tour and cartoon sequences. The frames are represented at the same size, although their original sizes differ

The 3DLive corpus was generated as part of the 3DLive project [3DL 12], and is made up of 2 h 11 min of stereoscopic video sequences, or 197, 000 stereoscopic pairs encoded at a rate of 25 frames per second. It includes sequences from rugby matches (Rugby), volleyball (Volley), a dance performance (Dancing), theater (Theater) and a rock concert (Rock). The sequences are coded in full high definition (HD) (1, 920 × 1, 080 pixels).
The MPEG corpus [MOB 12] is made up of 41 sequences, corresponding to 17 min 29 s, or 29, 908 stereoscopic pairs, with several different frame scanning frequencies. A variety of resolutions are present, from 320 × 192 to 640 × 480 pixels. The content includes street-based sports (roller skating or bicycle races), indoor scenes (office), city tours and cartoons.
13.2.4. Conclusion
The principle of watermarking consists of associating additional information (copyright information) with original multimedia content in a transparent and robust manner. In specifying an operational watermarking technique, the aim is to establish a method satisfying the operational balance between the data payload, transparency, robustness and computation time.
13.3. State of the art for stereoscopic content watermarking
A number of recent studies concerning stereoscopic content watermarking demonstrate the state of the art in the domain [BHA 09, HWA 03a, HWA 03b, KUM 09, YU 11, ZHA 07]. The insertion method is inherited from ![]() watermarking. These studies may be grouped into two categories by domain of insertion. This domain may be one view (left or right) from the stereoscopic pair, or a representation derived from this pair (the disparity map). Watermarking approaches involving inserting a mark in one of the views of the stereoscopic pair are more widespread than other techniques, and are mostly used for still stereoscopic images [BHA 09, HWA 03a, HWA 03b, KUM 09, YU 11].
watermarking. These studies may be grouped into two categories by domain of insertion. This domain may be one view (left or right) from the stereoscopic pair, or a representation derived from this pair (the disparity map). Watermarking approaches involving inserting a mark in one of the views of the stereoscopic pair are more widespread than other techniques, and are mostly used for still stereoscopic images [BHA 09, HWA 03a, HWA 03b, KUM 09, YU 11].
In their successive studies [HWA 03a, HWA 03b], Dong-Choon et al. consider problems associated with SS watermarking of stereoscopic images. In [HWA 03a], a 1,024 bit mark (representing a visual logo) was inserted in the discrete cosine transform (DCT) of each right view of a sequence of 25 stereoscopic pairs, with a resolution of 256 × 256 pixels. Transparency performances were evaluated in terms of the PSNR between the marked and original images, with a mean PSNR of 34.89 dB. Robustness was also evaluated in terms of PSNR calculated between the detected and inserted logos; this produced a mean value of 19.04 dB. However, the study includes no information on the applied attacks. In [HWA 03b], mark insertion was carried out in the discrete wavelet transform (DWT). The study used a sequence of three image pairs of 512 × 512 pixels with a logo of 64 × 64 pixels for the mark. The mean transparency value in this case was increased by 3.92 dB, reaching a limit of 38.81 dB. The robustness decreased by 2.36 dB (to 16.68 dB).
Kumar et al. [KUM 09] also considered an SS watermarking technique. The disparity map was first estimated in the DWT domain. Insertion was carried out in the singular value decomposition (SVD) of the DWT of the left view and optimized using a genetic algorithm. Validation tests were carried out using five grayscale stereo images with a resolution of 512 × 512 pixels. The transparency was expressed by a PSNR of 42.88 dB. The robustness against average filtering, rotations, redimensioning and the addition of Gaussian noise was evaluated by calculating the NCC between original messages and those detected after the attacks, producing results of 0.91, 0.91, 0.90 and 0.89, respectively.
In the study carried out by Bhatnager et al. [BHA 09], the inserted mark is represented by the disparity map, calculated directly in the pixel domain. Additionally, this disparity map was inserted using an SS technique applied in the SVD of the discrete fractional Fourier transform (DFrFT) of the left view. The experimental validation process considered a corpus of three stereo images (two image pairs of 256 × 256 pixels and one pair of 512 × 512 pixels). The transparency evaluation gave a mean PSNR of 45.92 dB. This value is excellent, but was obtained at the expense of robustness. The robustness, expressed by the NCC between the original and detected marks, was calculated to be 0.64, 0.71, 0.69, 0.98, 0.57, 0.63 and 0.46 for average filtering, median filtering, redimensioning, Joint Photographic Experts Group (JPEG) compression, noise addition, cropping and rotation, respectively.
Campisi [CAM 08] developed a semi-fragile stereoscopic watermarking approach based on the quantization index modulation (QIM) insertion method applied in the DWT domain. The quantity of information inserted was 2, 000 bits per image. Experimental tests showed the proposed method to be robust to JPEG and JPEG 2000 compression, but fragile in relation to simple signal manipulations. The fragility property was evaluated by calculating BER (bit error rate) values. The following numerical results were obtained: 0.07 after Gaussian filtering, 0.11 after median filtering, 0.38 after removal of a line/column, 0.30 after a rotation of 0.25 degree and 0.39 after a rotation of 0.50 degree. No information is supplied concerning transparency and the experimental database.
Yu et al. [YU 11] inserted the mark into the left and right views of the stereoscopic pair, taking account of statistical relationships within and between blocks, established by combining the DWT and the DCT. A parity quantization was also designed to handle the cases not verifying a relationship of this type. During the experiments, a binary pixel logo was inserted into a stereo image of 640 × 480 pixels. Transparency was evaluated in terms of PSNR between the original and watermarked images, giving values of 52.14 and 51.99 dB, respectively, for the left and right views. Robustness was evaluated in terms of watermarking recovering ratio (WRR) (also called HC in [YU 11]) given by ![]() , where
, where ![]() is exclusive-OR,
is exclusive-OR, ![]() is the original binary mark of size
is the original binary mark of size ![]() and
and ![]() is the detected mark. WRR values of 0.94, 0.90, 0.94 and 0.81 were obtained after application of JPEG compression, salt-and-pepper noise, median filtering and cropping, respectively. Note that
is the detected mark. WRR values of 0.94, 0.90, 0.94 and 0.81 were obtained after application of JPEG compression, salt-and-pepper noise, median filtering and cropping, respectively. Note that ![]() .
.
Watermarking techniques where the mark is inserted into a disparity map are represented by the study described in [ZHA 07]. The insertion technique combines the SS principle with the low-density parity control (LDPC) error correction code. Experimental tests were carried out using four video sequences: three of these sequences were made up of 22 stereoscopic images, while the fourth included 192 frames of 720 × 576 pixels. The transparency was calculated using the mean image degradation index, defined as ![]() , where
, where ![]() and
and ![]() designate the PSNRs of the unmarked and marked video images, respectively (no details are given on the way in which the mean PSNR of the non-marked images was calculated). In the study, the authors showed that
designate the PSNRs of the unmarked and marked video images, respectively (no details are given on the way in which the mean PSNR of the non-marked images was calculated). In the study, the authors showed that ![]() . The robustness was evaluated using the watermarking detection ratio (WDR), evaluated for each product and defined by WDR =
. The robustness was evaluated using the watermarking detection ratio (WDR), evaluated for each product and defined by WDR = ![]() , where
, where ![]() and
and ![]() are, respectively, the numbers of “0” and “1” in the original mark, while e0 and e1 denote, respectively, the numbers of “0” and “1 “ in the detected mark. The reported WDR values were more than 0.78 after recoding and 0.74 after recoding with the addition of noise.
are, respectively, the numbers of “0” and “1” in the original mark, while e0 and e1 denote, respectively, the numbers of “0” and “1 “ in the detected mark. The reported WDR values were more than 0.78 after recoding and 0.74 after recoding with the addition of noise.
Table 13.1 provides an overview of different approaches to watermarking stereoscopic data. From an application perspective (e.g. protection of 3D HD TV content in real time), there are a number of limitations:
– The domain of insertion is still chosen by the experimenter, and has not been the subject of objective studies to determine optimality.
– Transparency is only evaluated in terms of PSNR and not using subjective approaches, limiting the legitimacy and the relevance of results.
– Robustness to geometric attacks has yet to be attained.
– Computation cost has not been studied.
– The structure and size of the corpus considered are too small to guarantee the generality and relevance of results.
Table 13.1. Synthesis of performances of stereoscopic image/video watermarking methods

In the remainder of this chapter, we will consider the issues mentioned above, by analyzing the following:
– The extension of 2D/2D+t watermarking methods: SS [COX 97], binary QIM, 5-QIM [BEL 10, HAS 11] and IProtect [CHA 10].
– The potential offered by the 3DV-NTSS disparity map [CHA 12] for watermarking in terms of optimality as a domain of insertion.
– Transparency, evaluated using (1) a subjective protocol considering the recommendations contained in UIT-R BT 500-12 [ITU 02] and BT 1438 [ITU 00], and (2) an objective protocol using four measurements: PSNR, IF, NCC and SSIM.
– Robustness, objectively expressed in terms of BER in mark detection after attacks such as linear and nonlinear filtering, compression and geometric transformations (StirMark random bending).
– Computation cost, estimated for each stage in the watermarking process.
13.4. Comparative study
A general view of our watermarking evaluation procedure is shown in Figure 13.4. The insertion domains under consideration include the left view of video sequences and the disparity map, calculated using three algorithms: NTSS [LI 94], FS-MPEG [STA 08] and 3DV-NTSS [CHA 12]. These algorithms use NCC as their block matching criterion. Mark insertion is carried out using the DWT representation of each of these four domains of insertion. To simplify the notation, these domains will be referred to as left view, NTSS, FS-MPEG and 3DV-NTSS, respectively. Four insertion methods will be considered, taken from the SS, binary QIM, 5-QIM and IProtect method families. The performances of the watermarking method will be evaluated in terms of transparency (subjective and objective), robustness and computation cost. The quantity of information inserted will remain constant at 1 bit per frame (i.e. 25 bits per second).
Figure 13.4. Watermarking procedure evaluation protocol

13.4.1. Transparency
13.4.1.1. Subjective protocol
The evaluation was carried out (1) in professional test conditions, in the 3D cinema room at Cesson Sévigné and (2) in laboratory conditions in the ARTEMIS department, using a 47′ LG LCD monitor with full HD 3D (1,920 × 1,080 pixels) and maximal luminosity 400 cd/m2. Twenty-five non-expert observers participated in the tests. This is above the lower limit, set at 15 by the ITU-R. The participants were aged between 20 and 33 years, with a mean age of 25. They all presented visual acuity and color vision tested using a Snellen chart and the Ishihara test, respectively [ITU 00]. The tests involved two subjects per session. The subjects sat in a line in front of the center of the screen at a distance equal to three times the height of the screen. Each observer randomly evaluated 34 video excerpts, each with a duration of 40s. These excerpts represented the two corpora and all of the possibilities under study: original videos and watermarked videos, obtained using the four insertion methods applied in the four domains of insertion. The double stimulus continuous quality scale (DSCQS) method was used. Visual comfort, image quality and depth perception were noted independently on a quality scale from 1 to 5 (1 = bad and 5 = excellent).
The results were analyzed using the mean opinion score (MOS), taking the mean of the individual scores for each test condition. These results are summarized in Figure 13.5, where MOS values are indicated with a confidence interval of 95% [WAL 72].
In a synthetic manner, these observations provide us with the following preliminary conclusions:
– The visual experience was better for marked 3DLive content than for that sampled from the MPEG database. The average difference in MOS was 0.16. This result can be linked to differences in quality in the original material itself, which may influence observers in their evaluation of the quality of marked content.
– IProtect offers the best visual quality, with a mean MOS value of 0.18 for the 3DLive corpus and 0.11 for the MPEG corpus above the values for the SS method, which took second place. This result is unexpected, as when using 2D video content, SS methods give the best visual quality [COX 97, COX 02].
Figure 13.5. Subjective evaluation: a) image quality, b) depth perception and c) visual comfort. The squares represent MOS values for each insertion technique/domain (from left to right: left view, NTSS, FS-MPEG and 3DV-NTSS), and the vertical lines centered on the squares show the 95% confidence intervals for watermarked content. The bold horizontal lines show the 95% confidence intervals for subjective evaluation of the original content

– In terms of domains of insertion, 3DV-NTSS offers the best visual quality, with an average MOS value of 0.06 for the 3DLive corpus and 0.12 for MPEG above NTSS, the second best domain. This result highlights the advantages produced by managing the interdependence of stereoscopic views in calculating the disparity map, and thus shows the relevance of 3DV-NTSS for watermarking applications.
– The IProtect method, applied to the 3DV-NTSS domain, was the only solution allowing imperceptible mark insertion. For the two corpora and the three evaluation criteria (image quality, depth perception and visual comfort), IProtect/3DV-NTSS was the only solution providing confidence limits within the confidence intervals of the original context.
The conclusions presented above are of a general nature and may be enriched by noting that several method/insertion domain combinations may be taken into account for specific applications. For example, with depth perception constraints, low-resolution sequences from the MPEG corpus may be protected by three types of solutions: SS/NTSS, IProtect/FS-MPEG or IProtect/3DV-NTSS (see Figure 13.5).
13.4.1.2. Objective protocol
The visual quality of watermarked content was evaluated using four quality measurements: PSNR, IF, NCC and SSIM. These measurements were calculated individually for each watermarked frame of the video sequence, and then averaged out for the whole sequence (see Figure 13.6). Confidence limits at 95% were also calculated for each experimental test (each corpus, watermarking method and domain of insertion). As the corresponding error was always lower than 0.45 dB for PSNR and 0.001 in the other cases, the associated confidence limits cannot be represented. The only exception is for the 3DLive corpus using IProtect with insertion of the mark in a view from the stereoscopic pair, which allows this visualization.
From the obtained experimental data, we find the following:
– For a given similarity measurement and domain of insertion, the 3DLive and MPEG corpora behaved in a very similar manner. This is a reflection of the balanced conditions of the comparative analysis.
– The mean PSNR values were above 30 dB (except for the 5-QIM method applied to the left view of the 3DLive corpus). All of the method/domain of insertion combinations were able to ensure fundamental transparency properties. Note the transparency of more than 35 dB obtained using SS methods for all domains of insertion and for the two corpora. The same results can be achieved by using the IProtect method combined with 3DV-NTSS for 3DLive, and for any of the four domains of insertion in the case of MPEG. According to the PSNR values, the SS methods represent the best watermarking methods, followed by IProtect.
Figure 13.6. Objective evaluation of visual quality of watermarked content using different objective quality metrics
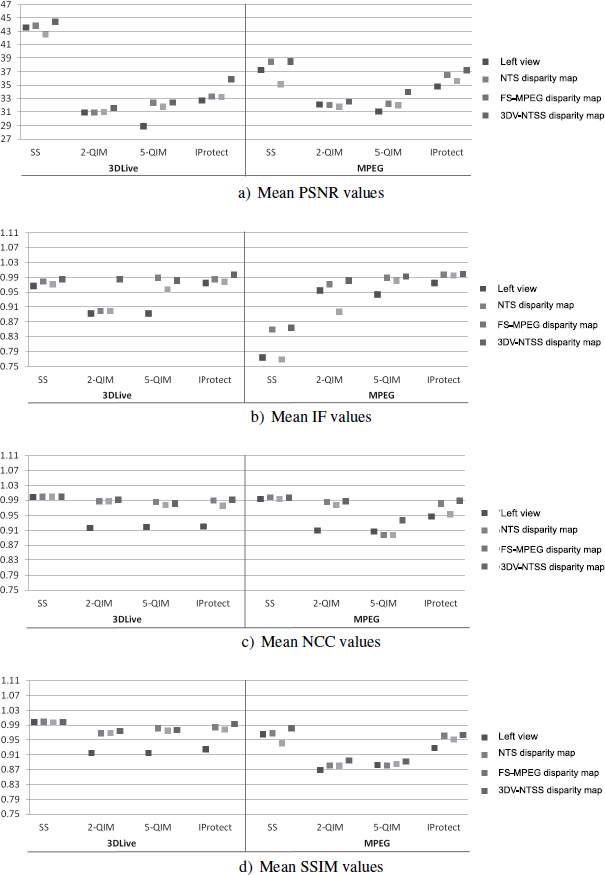
– The IF, NCC and SSIM measurement values show that transparency values between 0.95 and 1.05 can be virtually guaranteed using all of the watermarking methods under consideration (with certain constraints in the choice of a domain of insertion). Only the SS method was refuted by the IF values, estimated for the MPEG corpus. In general, the SS and IProtect methods appear to offer the best solutions.
– For each watermarking method and for each corpus, the four objective quality indicators selected the 3DV-NTSS disparity map as the optimal domain of insertion, except for NCC values calculated for the 5-QIM insertion method applied to the 3DLive corpus.
13.4.2. Robustness
Robustness was evaluated in terms of BER during detection of the mark following the application of three types of attacks: filtering, compression and geometric attacks. The Gaussian and enhancement filtering techniques considered a 3 × 3 convolution kernel. JPEG compression was applied with an average quality factor of Q = 60. Rotations were generated at random with angles less than ±0.5 degree. The StirMark random geometric attack was applied using default parameters [PET 98, PET 00]. Each attack was applied to a view of a stereo image. The corresponding BER values were averaged for the corpus and the corresponding 95% confidence intervals were calculated (see Figure 13.7).
Analysis of the results shows that IProtect/3DV-NTSS is the only combination presenting robustness, expressed by a reduction in BER of 0.05 after filtering and JPEG compression and a reduction of less than 0.1 after geometric attacks for either corpus. The 2-QIM method, applied to the 3DV-NTSS domain, gives the same BER values after Gaussian filtering, JPEG compression and geometric attacks, but does not respond to robustness requirements after contour enhancement (for both the 3DLive corpus and the MPEG corpus) or after StirMark random bending attacks in the case of the MPEG corpus. The SS method did not fulfill robustness requirements for any domain of insertion for either corpus.
13.4.3. Computation cost
The results presented above show that the IProtect watermarking method, applied to the 3DV-NTSS disparity map, is the most effective method for protecting stereoscopic videos, considering constraints of transparency and robustness, and for a fixed quantity of information.
Figure 13.7. Robustness of watermarking methods to different attacks: mean BER values and associated 95% confidence intervals


Computation cost, which is crucial in the context of real-time applications (for example the protection of live broadcasting HD 3DTV content), should also be considered.
Thus, for each of the five main steps in the watermarking process (calculation of the 3DV-NTSS disparity map, DWT, insertion of the mark using IProtect, calculation of the inverse DWT and reconstruction of the image), the computation time is estimated at 137, 547, 38, 579 and 47 ms, respectively. The values are calculated at frame level and averaged for the corpus. They were obtained using a Core 2 CPU@ 2.13 GHz PC with 2 GB RAM.
The computation times for the 3DV-NTSS disparity map, IProtect insertion and image reconstruction are, respectively, 4, 15 and 12 times lower than those for the DWT. For solutions where DWT/IDWTs are calculated in real time [GAL 11], IProtect/3DV-NTSS watermarking can therefore be carried out in real time.
13.4.4. Conclusion
To summarize, methods inherited from 2D/2D+t watermarking offer very good performances in protecting stereoscopic videos. Our experimental results show that from a selection of these approaches, the hybrid IProtect method, which combines the aspects of SS and SI approaches, applied to a 3DV-NTSS disparity map offers a generic solution responding to a wide variety of applications:
– This is the only one of the studied insertion methods that ensures imperceptibility of the watermark according to subjective tests (ITU-R BT 1438 and BT 500-12 recommendations) and criteria of image quality, depth perception and visual comfort.
– This subjective evaluation of transparency is reinforced by PSNR values larger than 35 dB and IF, NCC and SSIM approaching the ideal value of 1 with an error lower than 0.05.
– It is the only one of the studied methods that ensures robustness expressed in BER with a value less than 0.05 after JPEG compression and linear/nonlinear filtering, and less than 0.1 after geometric transformations and StirMark random bending attacks.
– The computation cost is compatible with real-time applications (in the sense discussed in section 13.4.3).
The size and composition of the two corpora (almost 2 h 30 min of heterogeneous stereoscopic video content) and statistical error monitoring (confidence limits of 95% with relative error less than 0.1) guarantee the validity of our results and conclusions from a statistical perspective.
13.5. Conclusions
The multiplication of stereoscopic content, and their high added values increase the risks of digital piracy. Therefore, we need to find the means of preserving intellectual property rights, without imposing additional operational constraints in the chain of production, distribution and consumption of this content. Digital watermarking offers a solution to this issue, and consists of inserting additional information in a way that is imperceptible to the user and resistant to attacks.
In practice, the main challenge in watermarking is to find a point of operational balance between transparency, robustness and the amount of inserted information. Computation cost is also a key factor in the case of real-time applications. The optimality of the domain of insertion (one of the two views, or another derived representation, such as a disparity map) is another essential consideration in terms of the performance of stereoscopic watermarking approaches.
The research work presented in this chapter can be divided into three broad parts:
– An introduction concerning issues in the application of digital watermarking for stereoscopic content.
– An overview of the state of the art of stereoscopic video watermarking.
– A comparative analysis of the main classes of watermarking methods, considering their properties of transparency, robustness and the computation costs.
The experimental results obtained from almost 2 h 30 min of stereoscopic videos provide objective proof concerning the concept of stereoscopic watermarking: the IProtect method, applied to 3DV-NTSS, ensures operational equilibrium between constraints concerning the quantity of inserted information, transparency, robustness and computation cost. Future research will aim to establish a theoretical viewpoint of the limitations of stereoscopic video watermarking. As a result, watermarking may be integrated in a relevant manner into applications from content protection to adaptive enrichment for collaborative virtual environments.
13.6. Bibliography
[3DL 12] 3DLIVE, “Projet français 3D Live”, available at http://3dlive-project.com, 2012.
[BEL 10] BELHAJ M., MITREA M., PRÊTEUX F., et al., “MPEG-4 AVC robust video watermarking based on QIM and perceptual masking”, 8th International Conference on Communications (COMM), Bucharest, Romania, pp. 477–480, 10–12 June 2010.
[BHA 09] BHATNAGAR G., KUMAR S., RAMAN B., et al., “Stereo image coding via digital watermarking”, Journal of Electronic Imaging, vol. 18, no. 3, pp. 033012–033012, 2009.
[CAM 08] CAMPISI P., “Object-oriented stereo-image digital watermarking”, Journal of Electronic Imaging, vol. 17, no. 4, pp. 043024–043024, 2008.
[CHA 10] CHAMMEM A., MITREA M., PRÊTEUX F., “Speeding-up the hybrid video watermarking techniques in the DWT domain”, Society of Photo-Optical Instrumentation Engineers (SPIE) Conference Series, vol. 7535, p. 75350E, 2010.
[CHA 12] CHAMMEM A., MITREA M., PRÊTEUX F., “High-definition three-dimentional television diapsrity map computation”, Journal of Electronic Imaging, vol. 21, no. 4, pp. 043024–043024, 2012.
[CHI 11] CHIKKERUR S., SUNDARAM V., REISSLEIN M., et al., “Objective video quality assessment method: a classification, review, and performance comparison”, IEEE transaction on broadcasting, vol. 57, no.2, pp 165–182, 2011.
[COS 83] COSTA M., “Writing on dirty paper (corresp.)”, IEEE Transactions on Information Theory, vol. 29, no. 3, pp. 439–441, 1983.
[COX 97] COX I., KILIAN J., LEIGHTON F., et al., “Secure spread spectrum watermarking for multimedia”, IEEE Transactions on Image Processing, vol. 6, no. 12, pp. 1673–1687, 1997.
[COX 02] COX I., MILLER M., BLOOM J., Digital Watermarking, Morgan Kaufmann, San Francisco, New york, 2002.
[ESK 95] ESKICIOGLU M.A., FISHER P.S., “Image quality measures and their performance”, IEEE Transaction on Communications, vol. 43, no. 12, pp 2959–2965, 1995
[GAL 11] GALIANO V., LÓPEZ O., MALUMBRES M., et al., “Improving the discrete wavelet transform computation from multicore to gpu-based algorithms”, Proceedings of International Conference on Computational and Mathematical Methods in Science and Engineering, Benidorm, Alicante, Spain, 26–30 June 2011.
[HAS 11] HASNAOUI M., BELHAJ M., MITREA M., et al., “mQIM principles for MPEG-4 AVC watermarking”, Society of Photo-Optical Instrumentation Engineers (SPIE) Conference Series, vol. 7881, p. 78810L, 2011.
[HWA 03a] HWANG D., BAE K., KIM E., “Stereo image watermarking scheme based on discrete wavelet transform and adaptive disparity estimation”, Proceedings of SPIE, vol. 5208, pp. 196–205, 2003.
[HWA 03b] HWANG D., BAE K., LEE M., et al., “Real-time stereo image watermarking using discrete cosine transform and adaptive disparity maps”, Proceedings of SPIE, vol. 5241, pp. 233–242, 2003.
[ITU 00] ITU-R BT.1438, “Subjective assessment of stereoscopic television pictures ITU-R BT.1438”, Recommendation, 2000.
[ITU 02] ITU-R BT.500-12, “Methodology for the subjective assessment of the quality of television pictures”, Recommendation, 2002.
[KUM 09] KUMAR S., RAMAN B., THAKUR M., “Real coded genetic algorithm based stereo image watermarking”, IJSDIA International Journal of Secure Digital Information Age, vol. 1, no. 1, pp. 23–33, 2009.
[LI 94] LI R., ZENG B., LIOU M., “A new three-step search algorithm for block motion estimation”, IEEE Transactions on Circuits and Systems for Video Technology, vol. 4, no. 4, pp. 438–442, 1994.
[MIT 07] MITREA M., PRÊTEUX F., “Tatouage robuste des contenus multimédias”, in CHAOUCHI H., LAURENT-MAKNAVICIUS M., La sécurité dans les réseaux sans fil et mobiles 1: Concepts fondamentaux, Hermes-Lavoisier, Paris pp. 169–224, 2007
[MOB 12] MOBILE3DTV, “MPEG data base”, available at http://sp.cs.tut.fi/mobile3dtv/stereo-video/, 2012.
[PET 98] PETITCOLAS F., ANDERSON R., KUHN M., “Attacks on copyright marking systems”, Information Hiding, Springer, Berlin, Heidelberg, pp. 218–238, 1998.
[PET 00] PETITCOLAS F., “Watermarking schemes evaluation”, IEEE Signal Processing Magazine, vol. 17, no. 5, pp. 58–64, 2000.
[PIN 99] PINCEMIN B., “Construire et utiliser un corpus: le point de vue d’une sémantique textuelle interprétative”, in CONDAMINES A., PÉRY-WOODLEY M.-P. & FABRE C. (eds), Atelier Corpus et TAL: pour une réflexion méthodologique, pp. 26–36, 1999.
[SHA 58] SHANNON C., “Channels with side information at the transmitter”, IBM journal of Research and Development, vol. 2, no. 4, pp. 289–293, 1958.
[STA 08] STANKIEWICZ O., WEGNER K., “Depth map estimation software version 2”, ISO/IEC MPEG meeting M, vol. 15338, p. 2008, 2008.
[WAL 72] WALPOLE R., MYERS R., MYERS S., et al., Probability and Statistics for Engineers and Scientists, vol. 5, Macmillan, New York, 1972.
[WAN 04] WANG Z., BOVIK A.C., SHEIKH H.R., et al., “Image quality assessment: from error visibility to structural similarity”, Image Processing, IEEE Transactions on, 2004.
[YU 11] YU M., WANG A., LUO T., et al., “New block-relationships based stereo image watermarking algorithm”, ICSNC 2011, The Sixth International Conference on Systems and Networks Communications, pp. 171–174, 2011.
[ZHA 07] ZHANG Z., ZHU Z., XI L., “Novel scheme for watermarking stereo video”, International Journal of Nonlinear Science, vol. 3, no. 1, pp. 74–80, 2007.
