Developing an Effective Security Awareness Program
Sean Lowther is the President and Founder of Stealth Awareness, Inc., www.stealthawareness.com.
Sean is an independent consultant who brings years of experience designing and implementing information security awareness programs at the highest level. He founded Stealth Awareness, Inc. in 2007.
Sean worked at Bank of America for over seven years, managing the enterprise information security awareness program. The program received the highest rating from its regulators and was consistently rated “world class” by industry peer groups.
Sean has worked with BITS, the Financial Services Roundtable Task Force on Privacy, prior to the enactment of the Gramm-Leach-Bliley Act. He produced the video “It’s Not If, But When” for the Financial Services Sector Coordinating Council in partnership with the U.S. Treasury Department with the goal to improve critical Infrastructure protection and Homeland Security. Sean was recognized by senior government officials and business executives for his “work to defend our nation’s critical infrastructure.”
Sean is a sought after speaker for a variety of events and meetings. Most recently he spoke at the Computer Security Institute’s annual 2007 conference in Washington, D.C., the Contingency Planning Association of the Carolinas, and the 2008 Charlotte ISSA annual conference.
Sean lives in the Charlotte, North Carolina area.
Introduction
In this chapter, I will talk about how to design and implement an effective information security awareness program. One chapter will not cover all you need to know, but it can serve as the foundation for starting a program and/or making an existing program better.
In today’s world, I don’t like the looks of data breaches, identity theft, and the apparent inability of people to safeguard sensitive information properly. If the issue is not at pandemic levels, it certainly has reached epidemic proportions. A couple of years ago, corporate America was concerned that the flu pandemic was more than a probability. Disaster recovery experts raced to put in place contingency plans. It was thought that as much as 30 percent of a company’s employees would be too sick to work. If the flu hit, many would stay home fearing they might become sick. Fortunately, the pandemic did not happen. I do not suggest the issue of properly safeguarding sensitive information in its electronic and non-electronic forms is an illness that can be cured easily. Like in any epidemic, people become more cautious, keep their hands away from their face, and practice good hygiene. We communicate, communicate, communicate to ensure that people know the risks and what they need to do to avoid becoming infected. So why are we not doing this in a consistent every-company-must-do-it manner when it comes to the proper safeguarding of sensitive information? This chapter is a call to action, because without one, most companies will not implement the resources within their company that ensure all new hires, existing employees, vendors, suppliers, and consultants to their company clearly understand and exhibit the correct information safeguard behaviors. So, let the chapter begin.
There is an old adage that says: Tell them what you are going to tell them. Tell them, and then tell them what you told them. In other words, repetition is the aide to memory. Before I tell you what I am going to tell you, I want to raise a major concern. It is not a new concern. It’s not a great revelation, and it is no big surprise, but it is probably the greatest risk we are facing in corporate America, as well as government today. It is our inability to safeguard sensitive information properly. Paraphrasing Harold Hill in The Music Man, “We’ve got trouble, right here in your town, and it starts with ‘T,’ which rhymes with ‘P,’ which stands for People.”
Since 2005, it is conservatively estimated that over 250 million people in America have had their personal sensitive information lost or stolen. The cost to manage this exodus of information is estimated at over $55 billion, give or take a billion. The Ponomen Institute puts the cost at $192.50 for each customer record. These costs, for the most part, are purely administrative and are not related to actual identity theft. That means it is wasted money, and brings nothing to the bottom line other than an unnecessary expense.
If we were working for the CDC (Center for Disease Control), this problem would be way past the epidemic stage. Yet no one is raising the issue to the degree it needs to be heard. Thirty-nine states have enacted legislation requiring companies report compromised customer data. Penalties can be assessed, which is a way for the states to bring in more money, but these laws do not address the real issue. The Federal Trade Commission has entered the arena, threatening the penalty of an “audit” on those companies that fall under their jurisdiction who fail to safeguard sensitive information properly. We have companies, who, on further inspection, were following the latest prescribed security practices when an incident occurred. So, can we find them at fault?
The reality is that no one will ever stay ahead of those who are hacking systems, or those who are using social engineering to get sensitive information from company employees. If we close one hole, the hacker will likely exploit another. Social engineers will survive because they are magicians at extracting information from employees who have been told that providing quality customer service means everything to the company. In a way, company employees are willing to give up sensitive information because they want to help and “do the right thing.” Where we are failing (miserably, in my opinion), is in addressing the human side of this epidemic.
What we need is an “antibiotic” to eradicate these ills. Or maybe a chip that, once embedded into each employee, will ensure that he/she will not make stupid mistakes, like leaving sensitive information on the copy machine, or leaving their laptop on the table at the coffee shop when they go to the bathroom—only to find it gone when they return. Unfortunately, that chip has not been developed yet. In a real epidemic, one with viruses, a high temperature, sneezing, and so on, we encourage people to wash their hands, cover their nose when sneezing, and stay home from work when they are sick so they don’t infect others. If this was a flu pandemic, that’s exactly what we’d be doing. The loss in productivity during a pandemic would probably be higher, in terms of cost, than what is currently experienced with “data breaches,” but not by much.
Welcome to the Information Risk Pandemic. It is time to properly educate employees and senior leadership on how to protect their customers, company, and stakeholders from this costly plague by concentrating on the people who design applications, implement programs, and use the technology given to them to perform their function in a safe and secure manner.
When people fail to do the right thing out of ignorance, speed to market, or greed, then the short-term reward is soon lost against the long-term consequences of their actions. A case in point is SCADAs. How one technology has been allowed to be embedded into the fabric of our society with such vulnerabilities to the whole is just unfathomable. Who knew? Today, we know that the unintentional loss of sensitive information is at pandemic proportions throughout corporate America and government. Nevertheless, we continue to not provide adequate information security awareness training to our employees on handling, transmitting, storing, destroying, and transporting sensitive information properly.
For companies that do have information security awareness programs in place, are they designed and implemented to change the overall security behavior of their employees, or are they simply one-time events that make it look like the company is taking the issue seriously?
The wake-up call is here and now. Companies need to check their information security awareness quotient. In other words, how well do employees know how to properly safeguard sensitive information at your company? Unfortunately, you are the wrong demographic to be preaching this message to. I would suggest you share this chapter with those in your company who are responsible for information security, physical security, privacy, auditing, and compliance. Not providing adequate awareness training to employees on how to safeguard customer, employee, company intellectual property, and other associated risks is simply business suicide in this day and age. I recognize you are not the one to lead the charge, but the more people who are willing to become the messenger brings us one step closer to effectively managing this information risk pandemic.
Why an Information Security Awareness Program Is Important
If the opening to this chapter isn’t enough reason to start an information security awareness program at your company, then I’m not sure what is.
How many security conferences have you been to where speaker after speaker brings up the issue of people as the major risk to safeguarding sensitive information? I’m sure you have sat in these conferences and listened and agreed, but because the discussion does not affect you personally, it remains in the conference room. “Yeah, it’s a big risk, but I’m more interested in securing the Unix platform, or learning what’s new in forensics,” you say. We seem to be absorbed with chasing the next technology and not so concerned about how we are going to safeguard it. We allow our employees to bring technology into the workplace, such as iPods and USBs, that have enough memory to easily store the company’s crown jewels. Information that can easily walk out the door unnoticed. We also give employees equipment to store and access the company’s most inner sanctum of sensitive information with little thought or control over their activities. As Deming, a noted quality guru, said in his day, “if you are going to put all your eggs in one basket, then you better watch the basket.”
For example, during the 2008 presidential campaign, three candidates had their passport information accessed without a valid need to know. Three separate incidents by contractors who had been given access, but apparently little guidance in their responsibilities. Was it right? No. Was there any intent to steal information? Probably not. It was a stupid mistake that resulted in another example of the government’s inability to properly safeguard sensitive information. Unfortunately, this scenario replicates itself in corporations millions of times a day across the world. Even worse, though a disgruntled employee with authorized access may be displaced, his/her access to such information often is not terminated immediately. So, he/she may leave behind a “time bomb,” designed to disrupt communications. Or, he/she may decide to steal confidential customer information or intellectual property. This scenario happens every day in government and private enterprise offices around the world. All because an employee’s access was not terminated in a timely manner.
We Fail to Recruit Our Employees into the Company’s Security Program
Somehow it is expected that everyone will “do the right thing.” If I asked a room of 100 people to raise their hands if they thought they would ever be the direct cause of a data breach at their company, guess how many hands would go up? Your’re right, none, or at least not yours. But the statistics tell us their answer isn’t true. It is pretty safe to say that every company and government agency will lose at least one laptop this year, and it is pretty safe to say that a very high percentage of those laptops will have sensitive information on them. It’s also safe to say that a very high percentage of the laptops do not have encryption installed, and that in many cases, the user’s ID and password are taped to the bottom of their laptop, thereby making the encryption useless. No one really knows what these statistics are. For sure, not everyone is reporting this type of incident, not to mention the loss of cell phones, iPods, USBs, and other storage devices. We have made information more mobile and far more vulnerable. Because of this, the cost to businesses is skyrocketing. As mentioned earlier, the Ponomen Institute suggests in their most recent study that the loss of one customer record to a company is $192.50. That covers customer notification, customer support, call center resources, and so on. What is the actual cost, and what will that reported cost be as more and more companies and industries come under scrutiny? Just type “data breaches” into your search engine and a wealth of opinions and facts will come pouring forth.
We Need to Take the Issue Seriously
On television is an advertisement where two people are inspecting a dam. They come upon a small leak and look at each other. One person is chewing gum and takes it out of his mouth and sticks it into the leak. They nod in agreement that the problem has been fixed. Of course, we all know what is ultimately going to happen. The dam will burst, questions will be asked, the news media will report the incident, and somewhere along the line the truth will be discovered. Chewing gum is not an effective tool when it comes to maintaining a dam. If the dam collapses due to poor maintenance or undue stress, the potential loss of life, not to mention the possible benefits lost from the power and other factors that could have been gained, could be catastrophic. Of the 79,000 dams in America, the American Society of Civil Engineers considers 10,000 to have a “high-hazard risk of failure.” Bridges are another example. According to federal highway statistics, “nearly 50 percent of all rural bridges in America, 20 feet or longer, are structurally or functionally deficient.” In some cases, the bridges have simply been closed. In other circumstances, weight restrictions have been posted.
Companies need to look at their infrastructures, and how they were built, and recognize that the information age has moved their most valuable asset, information, outside of the brick-and-mortar establishment and made it easy to access by authorized and unauthorized persons. An information security awareness program will not stop the intentional incidents. In an ideal world, we would have a super-system that would keep everyone honest. If access was attempted by an unauthorized person, or an authorized person was taking information for unauthorized purposes, the super system would identify the action immediately by frying the information. Of course, some of us might dream that such a scenario could be possible, but the legal and ethical ramifications of such a super-system would be beyond our comprehension, and frankly beyond our everyday reality.
How to Design an Effective Information Security Awareness Program
I do not necessarily believe in teams creating your information security awareness program. Consensus can often hinder the design of a program and, in fact, take people down the wrong path. The Aboliene Paradox easily demonstrates my point. The paradox says that a group of people can come together and agree on something that no one wants to do. I am sure that you have been in meetings where this has happened. You walk out of the room thinking the decisions made were nuts, but you agree to follow them anyway. Another problem is when a company takes a Vice President and asks them to wear the awareness cap, along with all their other hats. In small companies, you probably do not have much of an alternative. But, if your organization is rather sizable, a full-time employee should be assigned and dedicated to implementing your program.
Creating an information security awareness program is not rocket science. It is marketing. Because of this you should look for someone in your organization that has a flair for marketing. Having a CISSP is not an advantage or disadvantage. When I first introduced the concept of marketing information security awareness back in the ′90s, most people in the organization and other companies I talked to thought I was crazy. They used the sledgehammer/fear approach. My CISO happened to be one of the best marketing minds I’ve ever met, and when I presented my business plan to her, she fell in love with the concept.
Today, based on the many articles I’ve read, the marketing of information security awareness is universally accepted and applied. Here is what this looks like. If an employee does not value the content of the information you are delivering, then why would they follow it? It is this value proposition that makes a program work.
I don’t believe most employees think this way. “It’s everyone’s responsibility,” the slogan says, so if everyone else is doing the right thing, I’m covered and need not worry about it. No matter what expert you read or listen to, they all seem to agree on one thing: “80% of the risks to your company’s sensitive information rests on the inside with employees.” And yet most companies continue to look over the castle wall, protecting and defending their perimeter. This is why it is so important that management clearly understands the bigger picture, and the bigger risks if an effective information security awareness program is not implemented. It is another reason why a sound business plan is important. It gets everyone in the decision-making process thinking and agreeing along the same lines. This way, as you implement it, there will be no rude awakenings, or at least not with management.
The best presentation I ever heard was of a salesperson selling a satellite phone to an Arab sheik back in the 1980s, as I recall. Rather than try and present facts and figures, the salesperson went out and hired a graphic artist. The picture he had drawn was of the sheik in his tent in the desert sitting in his comfortable chair speaking on his phone to someone who was on another continent. The picture also showed the phone communicating with a satellite as well as the price tag for the picture to come to life. I think it all came to 3 million dollars then. The presentation lasted less than one minute, according to the salesman. The sheik looked at the picture. It was clearly what he wanted. He turned the picture over and signed his approval. Deal done! This is exactly how I approached presenting my business plan to my CISO. I painted the picture, showed how it all connected, and what it would cost. It was the plan that would solve her problem. Figuratively speaking, at the end of the presentation, she turned the presentation over and gave me her approval to go forward.
Seven Times, Seven Different Ways
My belief is that an effective plan is one that says the same thing seven times, seven different ways. So this challenges you to look at all the possible products and delivery channels available to you. This is something you need to constantly look for, to constantly seek. For example, I knew that video streaming would ultimately become available at the company. What a great channel for delivering information. We were the first to use the technology at the company simply because we were constantly looking for new channels. I knew it was becoming available, and we were ready to take advantage of the opportunity. In fact, we were the first. You could go to our Web site and view Video Quick Tips on several topics such as SPAM, Encryption, Password Creation, and so on. Not all employees are comfortable with reading guidelines. These Video Quick Tips became very popular and provided “just-in-time” training for the employee. Again, seven different times, seven different ways. Looking for new delivery channels, new ideas allow you to introduce old and new messages through other touch points.
Not everyone will think your ideas are good. I remember making a presentation to use iPods as a delivery channel for some of our messages. My manager at the time was not a proponent of the idea. Listening to your customers is where you will get many of your ideas. Surveying your customers will help determine which delivery channels are preferred, and help you defend the direction you are taking your program, keeping it alive, fresh, and most importantly, in your employees’ minds. Today, iPods are being used as a viable delivery channel of awareness messages.
I cannot impress upon the reader how important this is to the overall success of your program. If your program is to ever have a chance of success, the vision must be laid out and agreed upon by your CISO. If it is a stopgap solution to a particular incident or problem, your program will become exactly (and only) that: “A stopgap solution with no long-term effect.” Management is terrific at implementing knee-jerk reaction solutions. An effective awareness program needs to be ongoing and viewed by management and employees as an important company value. “Wow, that’s a tall order to achieve?” you might say, but you MUST protect the information assets of your company to reduce exposure to theft. You also MUST reduce the exposure of risk to the integrity of the processes in place or of them being developed to provide the coveted services of your company. The following are what I believe to be the key components of a business plan presentation:
1 What is your objective? An overview of your program.
2 What products and delivery channels are you recommending? (I am a believer, as I mentioned earlier, that if you want to affect change, you must package each message into seven different products, seven different ways. Over time, this reinforces key messages. With management’s due diligence, the company’s culture will reflect a greater understanding and appreciation about properly safeguarding sensitive information, as exhibited through each employee’s attitude, awareness, and behavior.
3 What is your schedule to roll out the program? (Here, you want to make sure you have Audit’s input on “what” and “how” you are going to accomplish your objective. Build that relationship with Audit. It will make your boss happy that they approved of your plan and efforts.)
4 Budget. What is it going to cost to implement your program? (Always ask for more knowing that you will not get it. I will show you where you can get the money to implement your program if it is not readily available to you.)
Show Me the Money!
Can you hear Cuba Gooding, Jr. and Tom Cruise screaming, “Show me the money!” in the movie Jerry Maguire? It is one of the key questions asked by those responsible for implementing an information security awareness program. “I can’t get the money budgeted!” they exclaim. Would it surprise you that I did not have a budget? Yes, I worked for one of the largest financial institutions in the world, and it would be easy to conclude that there were buckets and buckets of dollars at my disposal, but this wasn’t true. Like with anything else, when the mind is ready, the money is ready. This is why a good incident will get the attention of senior leadership or the Audit department. Personally, I never had a large incident that opened the money door for me, but then again I never had a problem getting my program funded either. The following are some suggestions to help you find the money.
1 As discussed earlier, I created a good business plan. A plan that laid out the entire program, including the budget. There were no surprises for management.
2 Ask for the money. If you need additional dollars above and beyond what you requested in your presentation, or that has been allocated to your program, simply ask for it. Present your ideas, why they are important to the overall program, and ask for the money to fund it. Do not worry about whether you receive the funds or not. The following are other resources you can tap:
3 If your company acquires another company, normally transition dollars are available. This is good because those dollars do not come out of your budget, but rather a special fund (bucket) set up by the company. Often, you can kill two birds with one stone by using these additional dollars for the transition as well as other items you want to add to your enterprisewide program.
4 Another source is the supply budget. Budgets are normally lost or lowered if they are not used. The supply budget, especially at the end of the year, is an easy one to pirate.
5 Other people’s money. Go back to your alliances, which I will talk about shortly, and see where you can partner with them to share the expense of your program. Online training is an example where information security and privacy can partner and share expense.
6 What budget dollars are available in other departments within your division?
7 Be creative. You are your own best resource. I never took a concept or idea to my manager for approval other than my business plan. I also took what appeared to be a finished product. It was more than “how can I paint the right picture in words.” Give it to them in such a way that they can see it, touch it, and even smell it if need be. Sometimes this requires working with alliances you have nurtured.
To get the CEO’s endorsement of your program, simply compose the message you would like to see the CEO make. Contact the CEO’s secretary and tell him/her why you are sending the message, why it is important, and that you need the CEO’s endorsement. I not only got the message back with a few minor edits, but with his electronic signature, too.
People were amazed that it was that simple, but it was. There isn’t a CEO alive who doesn’t understand the importance of safeguarding sensitive information properly. He/she trusts that those under him/her are doing the right thing to put in place the processes that will secure the information assets of the company.
The first product I released was a Quick Reference Guide for employees. On the inside flap of the guide was the message from our CEO explaining the importance of safeguarding sensitive information properly at the company, along with his support and request to all employees to follow the information security policy and program. I never had the question asked again from anyone in the company: “Why do we need to do this?”
Two Important Keys to Implementing an Effective Program
Implementing an information security awareness program can be done without a policy approved by the Board of Directors, but it is a lot easier if you have it. In some industries, a policy is mandated by regulation. Whether it is in your industry or not, it behooves a company in this day and age to have one, if for no other reason than to reduce legal exposure. The key words to look for in the policy are: All employees are required to follow the Information Security Program . . . failure to do so can lead to discipline up to and including termination. What Board of Directors would not approve an information security policy and program for their company? It is the right thing to do. You’ll notice that the word “Program” is included. This connects all information security guidance and your awareness program to the policy.
Awareness is part of the “Information Security Program.” If you do not have an Awareness Standard, compose one. An Awareness Standard says, “Who, what, and when will people comply with the information security awareness program implemented at your company.” First, who should receive training? Should it be all employees regardless of whether they have system access or not? I would say yes. This should be required of consultants and vendors, too.
Vendors sometimes challenge this issue. If they are on the premises, I would suggest they take your training, unless their company provides training that is equal to, or greater than, what your company requires. If an employee or vendor, consultant, and so on is a chauffeur, for example, the argument is that they do not have access to company systems, and therefore should not be required to take the training. Company chauffeurs probably have more access to sensitive information than you might think. They can overhear what’s being said in car conversations and on cell phone calls, and may even look through important papers left in the car while the senior manager is off at a meeting, if they so choose.
Don’t think it can happen? In 1973, I was working for a company in Osaka, Japan. The CEO of the company enjoyed driving to work in his Rolls-Royce. He would pick me up every morning on the way to the office to discuss our marketing plans and status—a good use of commuting time. As time went by, the CEO decided to hire an Assistant to the President (AP). Part of his job was to be the CEO’s chauffeur and traveling secretary. So, now, the CEO and I were being driven by the AP to the office. To make a long story short, we discovered that the AP was actually employed by one of our competitors, and was a mole in our company. Imagine how upset the boss was, and how it affected some of our marketing plans. Having an employee who does not have system access take your awareness training will not stop this kind of threat, but it does tell someone like the chauffer how important properly safeguarding sensitive information is to the company.
To that end, each employee is a sales representative for your company. If you are out at a party and someone asks, “What does your company do to safeguard sensitive information properly?” What would you say? The final two things you need to consider in your Awareness Standard is the “What” and the “When.” “What” are the awareness training requirements you have created (attending new hire orientations, completing an online training program, and so on). And then comes “When.” What are the expectations to complete specific awareness training? Should it be done prior to system access, or within 30 days of hire? As I mentioned earlier, write and get your Awareness Standard approved. Don’t wait for someone else to write it. You do it. Vet it with your manager and your CISO, and then take it through your company’s internal approval process.
You may ask, “Why not have your manager discuss the Awareness Standard (if you do not report directly) to the CISO?” Your CISO needs to know and respect your involvement and responsibility to the program. You are one of the few people in your division, other than those who report directly to the CISO, who is representing your division throughout the enterprise. Having his/her direct ear is an important relationship to develop.
I certainly know what we would like people to do, but it is not always easy for a company, especially a large one, to ensure that all their employees are complying with your Information Security Awareness Standard in a timely manner. Be sensible with the standard you create to ensure the processes can be followed in a timely manner by all. Otherwise, you could create your own nightmare.
For example: All employees must complete information security awareness training prior to system access. I know we would all like to see that, but it’s not going to happen, especially in a large organization. Take your proposed Awareness Standard to the Audit department, after it has been viewed with your manager and prior to the CISO’s review. This puts you in a better position with your CISO if he/she knows Audit is satisfied with the Standard. The final decision rests with the CISO. You do not want your program to burden the company. You simply want to enhance awareness and validate that all employees are receiving awareness training on a timely basis and that each employee understands and acknowledges their responsibility to safeguard sensitive information properly.
To Print or Not to Print
One of the first products I produced and released was a Quick Reference Guide. Though there is a lot of pressure to utilize the company’s intranet to distribute information, I remain a fan of print. There is still nothing like walking into the store and touching the merchandise. So, too, there is nothing like receiving a well-designed brochure or booklet, especially when it has the opportunity to stay around as a reminder. Having said that, there is a lot to be said for an intranet, because it allows you to upload updates on-the-fly and make your materials more current. A printed guide lasted at least one year, and after the initial print to all employees, we only printed enough to support new hire orientations. Of course, in the document was a reference to our Web site and to check for updates.
This Quick Reference Guide should do one very important thing. Tell employees where to find Information Security (through a URL, e-mail, and/or telephone number) when they have a question or concern about securing information properly. For awareness, I had my own extension on our 1-800 number. The following are the key topics you want to cover in this document:
1 What is sensitive information?
2 The importance of a clean desk policy.
3 How to create a good hard-to-crack password.
4 Use of a password-protected screensaver.
5 Remote computing safeguarding procedures.
6 Safeguarding the transmission of sensitive information.
7 The destruction of sensitive information.
8 The risk from social engineers.
In keeping with “what is sensitive information,” a classification of data matrix should be given to every employee so they clearly understand what security levels have been assigned to information in your company. What are the classifications you use to designate sensitivity of information. Examples show each level of sensitive information (see Figure 4.1), how it should be marked, transmitted electronically or non-electronically, stored, and destroyed.
Though all this guidance should be in a standard or other format, putting it in a concise, easy-to-read, and easily accessible resource is important to your overall awareness program. Many employees posted this matrix in their workspace. As you’ll notice, it also included a Web site URL and phone number as an easy reminder of how to contact Information Security. Marketing our contact information proved to be a significant benefit to the awareness program. When privacy, through the Gramm-Leach-Bliley Act became an important issue at the company I worked for, the group that was put together to manage that process proceeded to do conduct training. When questions were raised, guess who received the phone calls? Our employees did not know the difference between information security and privacy. This became the impetus of information security and privacy joining forces to implement an online awareness component to our individual programs. Later in the chapter, I’ll talk more about how aligning with other departments and divisions within your company can greatly benefit your program.
Online Training Programs
It’s better to have something rather than nothing. If all you have for your awareness training program is an annual online training program, then at least you have something. The risk is that you rely on this program as your only touch point and channel to reinforce principles and correct behavior. Some companies have an online orientation program. This should not replace the guide. It should merely supplement the program. Remember, seven different times, seven different ways. If you do have an online training program, it is a good place to get an employee’s acknowledgement that they understand their responsibility in properly safeguarding sensitive information at the company. This can soften public opinion if and when a data breach occurs. It is better to hear that “the company has an ongoing awareness program and as grievous as the incident may be, it was not because the company was not paying attention to their responsibility to safeguard customers’ sensitive information properly.”
Your In-House Web Site
If you have a company intranet, this is a great place to support information security services. If you are a small company, having your policies, standards, procedures, baselines, and other guidance housed on your Information Security Web site so those with a need to know have easy access and know whom to communicate with for the right answers is a good idea.
List the “Service Tasks” that information security provides, including your Awareness Program. This is where you can house an archive of articles you have written, as well as other products used in your awareness program, such as your Employee Quick Reference Guide, the Manager’s Guide, and even an orientation video. If you make your products easily available (communicate, communicate, communicate!), you’ll be amazed at how many within your organization will utilize the materials you’ve put in place. An example of those materials is shown in Figure 4.3. You should also consider placing “quick links” to other Web sites, such as those regarding privacy and compliance.
How to Implement an Information Security Awareness Program
Send to every employee in the company a card or sticker that includes the Corporate Information Security name, the intranet URL for your Web site, and a contact number for questions and/or for reporting an incident.
Implementing your information security awareness program is not always as easy as one may think. I know… just put it out there. It’s policy and it’s what employees need to know. However, it is how you implement it that is just as important as what you implement. Here’s what I mean. You are about to send a document to every employee in the company. How this document will be received is very important, because if employees do not read it, then why send it? Each department within your company has their own priorities, schedules to keep, and day-to-day processes that must be accomplished. If you simply send your document to every employee without advance notice to management that it is coming and why it is important for every employee to read, then you might as well kick back and watch the trash cans fill up. You want management to embrace your program, so communication is really important. You need managers, at all levels, to support your program.
What We Have Here Is a Failure to Communicate
In “Cool Hand Luke,” the Captain of Road Prison 36 first used the phrase, “What we have here is a failure to communicate.” It is a condition that exists across America’s corporate culture and why awareness is so important. Lack of awareness is a failure to communicate. Symptoms of this condition are the appearance of silos, employees not following policy, standards, or other defined process—doing their own thing, rather than the right thing.
Communicate, Communicate, Communicate!
Anyone in a company who works with technology, software applications, and systems can negatively impact the security of the company’s information assets. For example: An employee’s failure to communicate with information security specialists about an application they are developing can result in the exposure of sensitive information. Even if an application developer is proficient in secure coding, they should include an information security specialist as part of their development team. Undoing months of work, because Information Security was not consulted is no excuse for placing the company in a vulnerable position and incurring additional costs to have the code rewritten. Senior leaders, in my opinion, should mandate this requirement. Conversely, when Information Security releases new applications, processes, and due dates to follow without communicating these changes to the affected lines of business, animosity is generated, which can overtly affect what you are trying to accomplish.
Other Touch Points
If you create a Quick Reference Guide for employees, have it included in the company’s post-acceptance package. This is the package you received as a new employee that includes your benefits and other important information that you need to know on your first day at the company. Include the “Classification of Data Matrix” in the centerfold of the guide. This gives the employee an easy way to remove the matrix and post it in their work area. If you are ever going to get an employee to read what is important to the company, it will be during their welcoming process. If your company does not have a post-acceptance package, then the document should be given to the new hire during orientation. If you do not have a formal new hire orientation program, then the manager or their designee should sit down with the new employee and go through the guide. One of the values a new employee is hoping to see when they hire on to a company is that the company is trying to do the right thing. Safeguarding sensitive information properly is just such a worthy value to adopt.
Manager’s Quick Reference Guide
Managers, as I have discussed, are a key implementation partner. But how do you get them engaged in the process? Every manager in a company should clearly understand their responsibility ensuring that employees (and themselves) are effectively following the company’s information security policy and program. The Manager’s Quick Reference Guide should be part of every new hire manager’s post acceptance package. This information should be in an Information Security Standard, such as Roles and Responsibilities, or other guidance. The Manager’s Quick Reference Guide brings the importance of the manager’s responsibilities out of the maze of documented procedures and requirements and gives it the importance it deserves. In this guide, the following topics should be discussed:
1 Information Security is not responsible for safeguarding sensitive information properly. It is a team effort.
2 Application development and working with IT.
3 Know your employees’ safeguarding sensitive information properly behaviors.
4 The importance of encryption and the secure transmission of electronic and non-electronic information properly.
5 The downloading of unlicensed software.
7 Consultant/vendor guidelines.
8 Updating or deleting an employee’s system access immediately when they are transferred or terminated.
Managers should look to include discussion about information security topics in their staff meetings. When new materials or directions are released from information security, managers should ensure their employees have received the materials or guidance and understand the direction. It can be as simple as pointing out a new poster that is up and why the topic is important, or that a new standard has been released and what it means to both their department and job function. Information security awareness is an ongoing process with which everyone in the company should be engaged. Managers can determine whether employees need to see certain information. As mentioned earlier, imagine that a new standard is released and that employees in your company, who need to know this information, do not receive it!
Let’s Talk about Alliances
If you want your program to be successful, then don’t do it without input from others in your company. Embrace other divisions within your firm that can assist you in completing your mission. Some of them include the following.
Audit
Yes, Audit personnel are your friends! Any products or programs you create should be approved with Audit’s input. This accomplishes a few things. First, it embraces Audit as part of the process, part of the team. So, Audit should be easier to work with along the way. Secondly, your CISO will most likely ask you whether Audit was consulted when you make your presentation, and you don’t want to stand there with a stupid look on your face.
Legal
Submitting materials to your Legal department is the right thing to do. Rarely will you ever get a “you can’t do this” statement from your legal council. It is managing the perception and protecting your program that counts. Obviously, not everything needs to be sent to Legal, but, say for example, you were creating an online information security awareness program, you would want your legal department’s input for obvious reasons, and also to make sure you have not overlooked something, such as co-employment issues.
Privacy
I have mentioned the Privacy division as a good partner previously in this chapter. To me it is a natural fit. If your company is mandated by federal regulation, such as the Gramm-Leach-Bliley Act, to implement an awareness program, then I highly suggest you partner with Privacy. As I mentioned earlier, your employees do not know the difference between Information Security and Privacy. You want to eliminate confusion. It benefits everyone in the company and also provides an additional shared resource to fund your program.
Compliance
Companies are burdened with more and more regulations and requirements than ever before. If you can get your program aligned with the Compliance division, implementing it becomes a lot easier. For example, if you merge your efforts with another division, such as Privacy (suggested earlier), you will find it easier to gain Compliance’s support in implementing an annual information security awareness training requirement. Depending on processes at your company, you may find that Compliance is willing to take over and fund the delivery of your annual online training requirement. The greatest benefit to an online training program is its ability to track compliance. This is something you do not want on your plate, if at all possible. Otherwise, your life will become an administrative nightmare, as opposed to allowing you to be creative and move your program forward.
Training and Communications
If your company has a Training and/or Communications division, embrace their services. In some cases, you will have no alternative. For example, your company has a Learning Management System (LMS). To wander away from an established training platform does not make sense. In fact, it could possibly get you in trouble. Additionally, you want to make sure your materials are written in “corporate speak.” I don’t always agree with this, because it can sometimes stifle creativity, but it is still the right thing to do.
Coordinating your division’s internal messages to the enterprise is important, too. You are not the only one in your division communicating to the enterprise. You want to ensure that conflicting messages are not being sent out, that what is being communicated is in “people speak,” not “technical speak,” unless that is your audience.
Personnel
These folks are not critical to your program, but if you have materials that you want sent out to new hires in their post-acceptance package, these are the people to work with. In addition, get to know whom you can rely on to get distribution lists. This helps especially when you are sending out a survey (either print or electronic). They can slice and dice the distribution profile you want to survey. I mean by that the SVPS, VPS, and the corporate officers, by hierarchy, so you have a good representation across the enterprise.
Information Security Consultants
If your company is large enough to have internal consultants working with lines of business, then get to know these people. One of the dangers of implementing an information security awareness program is releasing a product or requirement that is in conflict with another division’s calendar. Your internal Information Security consultants can help you with this issue.
I think one of the worst things an Information Security Department can do is alienate the other departments in the company from your services and support. Developing the attitude of “enabler” goes a long way toward implementing a successful information security awareness program. There was never a time that I could not find a “Win, Win” solution to an internal customer’s need. And that needs to be your attitude to get their willingness to buy in to your program.
Some final thoughts around alliances. Do not forget other direct reports in your division. When building your information security awareness program, ask those who report directly to the CISO to designate someone on their team who you can interact with in the development and/or review of the program you are putting together. Everyone in Information Security should be an advocate of the awareness program. Many of your co-workers support other employees in the company. Make sure everyone knows that information security awareness materials are available, where to find standards and other guidance, and how to contact Information Security for clarification of questions, concerns, or to report an incident. This can be accomplished in staff meetings, brown bag lunches, and e-mail notifications, as well as covering the components and materials in your awareness program.
How Do You Keep Your Program a Successful Component of Your Company’s Mindset?
In the beginning of this chapter, I gave you the answer to this question. Repetition is the aid to memory. How many different touch points have you created in your program? I have discussed print, online training, and Web sites. Certainly using posters, Post-It notes, tchotchkes with proper information security behavior reminders, articles, and e-mails can help. And with today’s compression and streaming capabilities, video has become a viable delivery channel, too.
This is a great way to get students on your campus involved and to get these important messages out. If your company has a video production studio, use their resources. What are your creative talents? It might be designing posters. If you have an idea, but not the creative ability, who inside your company can help you create the product? The Awareness Intra-preneur within you is constantly looking for new products, and new channels through which to deliver awareness messages.
In small companies, this warning is neither true nor prudent, but in larger companies it can create a significant issue in the programs’ continuity and emphasis. The need for an Information Security Awareness Specialist is emerging. This is a person who has a good handle on marketing, communications, media, design, project management, and implementation. This individual doesn’t necessarily need to be a subject-matter expert, because a lot of what they must know is common sense or outlined in the company’s information security policy, standards, and other guidance.
An Information Security Awareness Specialist is also someone who can communicate effectively with all levels in the company. Often he/she will directly support the CISO and other senior leaders in presentation needs supporting the information security awareness messages. I suggest this because I have seen employees who do not have the presence, drive, and maturity to implement and sustain a program. This is not to slight all those who are trying to make a difference. This is to say that the issue is a major one that requires major attention and proven leadership ability. It requires a risk-taker, an intra-preneur, someone who is willing to use entrepreneurial skills on the inside of the company to advance the awareness program.
Now, let’s move on to the final portion of this chapter where I describe the most difficult thing you’ll need to do: measure an information security awareness program.
How to Measure Your Program
What gets measured gets done. Historically, it is difficult to measure the effectiveness of an information security awareness program. If you can connect your training to specific behaviors and have a way of monitoring those behaviors to see if compliance has improved, then that is what you are looking for. It validates the training. However, I caution that awareness is not training. It is not learning how a widget works. It is understanding and exhibiting the correct safeguarding sensitive information behaviors. So what can you measure to justify the effectiveness of your program?
First, how many employees have received training, whether through an annual class or a new hire orientation? How many employees have received the Quick Reference Guide or other key materials you have distributed? How many “Awareness” calls have you received and what categories are they in? If you do some marketing on creating easy-to-remember yet hard-to-crack passwords, and your password resets go down, this is a good indicator that your program is working. You want to capture this before and after information to show improvement. It is not always easy to find applications or programs that can give you timely and accurate information.
For example, how many sensitive customer documents that include Social Security numbers, account numbers, and so on are not truncated and are being e-mailed outside the company without encryption? If I had a section on encryption in my training, can I document improvement? If you can, great, but in most organizations this is a challenge.
In my experience, I relied heavily on subjective measurements that ultimately validated the effectiveness of our program. It showed steady improvement over time. It also provided critical objectives to the program so that we complied with the Six Sigma quality management process. Here’s how I did it.
I created a paper mailer initially, because at that time we did not have an online survey resource. In fact, we didn’t really have anyone who knew how to write survey questions. It is a skill. To maximize return of the survey, it was sent out with a way to respond anonymously. I actually had two surveys: one for new hires and one for all employees. The new-hire survey was done on a monthly basis, while the employee survey was done once a year. I needed, on the annual survey, 600 responses to have a statistically valid survey. The easiest way to figure this out was to go on the Internet and search “sample size calculator.” I can tell you that when I went from a paper to an online survey, the number of respondents went up. I can also tell you that offering a trinket or other incentive to respond did not make a difference in the number of responses. You want a cross section of your organization, so survey all levels of employees and all hierarchies or divisions. Your personnel department should be able to provide a report that slices and dices this information for you. Obviously, you want the employee’s full name, mail code and hierarchy, and position (CEO, SVP VP, Officer). If your survey is being delivered via an online channel, then you would want the employee’s e-mail address, too. My response ratio was always high.
I asked questions in six basic categories:
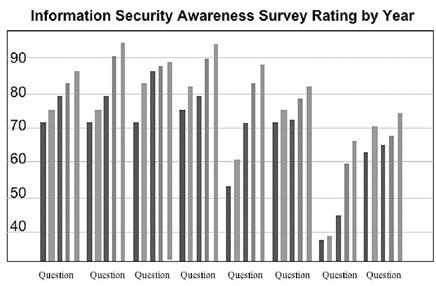
I also asked questions that pertained to the level of service our division was providing. I would track all the questions, but for reporting purposes for CTQ (Critical to Quality), we only used ten questions in what we called our “Awareness Quotient,” for lack of a better term. It showed over time how the program was working and where there was a need for improvement. Over a five-year period of time, we went from an “Awareness Quotient” of under 50 percent to over 90 percent. The chart in Figure 4.4 reflects one question, but gives you an idea of what improvement looks like over time. Could we define one product or component that made the improvements? I believe it is a cumulative effect of your program over time, as long as it remains consistent, that will show improvement and a cultural difference in your company. I must say that when the company came out of a survey application we could use, the administrative nightmare was over, and surveying became a lot easier.
The survey also gave us an indication, by levels in management, of who better understood the behaviors and what areas within the company were complying (for instance, were new hires receiving the Employee Quick Reference Guide?). When our online training program was put into effect, it gave us other collaborating data, such as how many employees within a hierarchy were not taking the annual training. This allowed us to target a hierarchy or division for follow-up and generated discussion on what we could do to ensure compliance was being met. One thing that can help in this arena is support from Compliance and your CEO. The CEO should mandate that all of his/her directly reporting officers ensure at least 93 percent or above compliance to all mandatory training. Historically, that would include regulatory- or industry-required training as well as sexual harassment training, code of ethics or conduct, and privacy and information security awareness training.
The graph in Figure 4.5 is a way of showing over time how your program is doing and, again, where improvement is needed. Post these graphs in your work area. As people visit you, it shows that you have a handle on your program. It also helps if you are working with training specialists and people who design training programs. They are continually trying to find the widget to measure the before-and-after effect of training. Having your own statistics allows you to keep this discussion in a broader perspective.
Summary
The subject of implementing an effective information security awareness program is something more than what can be included in a single chapter. The Internet affords us access to a lot of good information, and companies that can help you design and implement your program. Nothing, though, will do this better than your own spirit and desire to make such a program “world class.”
Specifically in reference to SCADAs, because that is what this book is primarily about, this chapter on awareness would not have been included if the lead author and publisher did not feel it was an appropriate and important topic to discuss. Awareness is communications. Awareness is understanding risks. Awareness is being proactive to those risks with sensible solutions. Each individual can significantly reduce the exposure of sensitive information by following simple behaviors and raising their hand with conviction when they see a potential or real risk. No one has all the answers, but collectively the risk can be addressed and reduced. Each company in America can significantly reduce the loss of sensitive information through an effective employee awareness program. There is no question about that. One lost laptop can be a devastating incident that very well may not have occurred if the employee clearly understood both the risk and their responsibility. The cost to implement an information security awareness program is incalculably far less than what it could cost you later without one.
Today’s information risk pandemic should be treated like any other event that requires a disaster recovery plan. Prevention is an important key, and through it we just might bring the level of this risk down from pandemic status to that of a cold.
Solutions Fast Track
How to Design an Effective Information Security Awareness Program
![]() Security should have an employee dedicated to creating an implementing a program.
Security should have an employee dedicated to creating an implementing a program.
![]() Your program should be treated as a maketing campaign and each employee should be “touched” repeatedly by marketing messages about being secure.
Your program should be treated as a maketing campaign and each employee should be “touched” repeatedly by marketing messages about being secure.
![]() Create a business plan for your program and make sure you have institutional buy-in to ensure its success.
Create a business plan for your program and make sure you have institutional buy-in to ensure its success.
![]() Print a “Quick Reference” gide and eliver the rest of your program online, to make updating information easier.
Print a “Quick Reference” gide and eliver the rest of your program online, to make updating information easier.