SCADA Security Assessment Methodology
Greg Miles, (Ph.D., CISSP#24431, CISM#0300338, IAM, IEM) co-author of Security Assessment: Case Studies for implementing the NSA IAM (Syngress Publishing, ISBN 1-932266-96-8), Network Security Evaluation: Using the NSA IEM (Syngress Publishing, ISBN: 1-597490-35-0), and Security Interviews Exposed: Secrets to Landing your Next Information Security Job (Wiley Publishing, ISBN-10: 0471779873) is the President, and Chief Financial Officer of Security Horizon, Inc. Security Horizon is a Global, Veteran-Owned Small Business headquartered in Colorado Springs, Colorado. Security Horizon provides global information security professional services, training, and publishes The Security Journal, a quarterly online publication. Greg is a U.S. Air Force Veteran and has been supporting the technology and security community for the last 22+ years. Greg’s background includes work with NSA, NASA, and DISA. Greg has supported efforts covering security assessments, evaluations, policy, penetration testing, incident response, and computer forensics.
Greg holds a Ph.D. in Engineering Management from Kennedy Western University, a master’s degree in Management Administration from Central Michigan University, and a bachelor’s degree in Electrical Engineering (with a concentration in Control Systems and Power Systems) from the University of Cincinnati. Greg is a member of the Information System Security Association (ISSA) and the Information System Audit and Control Association (ISACA). He is also Adjunct Faculty for the University of Advancing Technology (www.uat.edu).
Introduction
Supervisory Control and Data Acquisition (SCADA) Systems have evolved over the years. With the growth of technology, the desire to simplify, the desire to remote manage, and the need to reduce labor costs, SCADA has moved to be more in line with traditional TCP/IP networks. With this evolution, the need for effective, comprehensive assessments of SCADA systems has never been greater. Old paradigms must change, organizations need to understand the threats they face, and appropriate protection measures must be incorporated. This chapter will discuss the need for SCADA security assessments and provide a comprehensive approach to conducting SCADA security assessments.
Why Do Assessments on SCADA Systems?
Historically, SCADA systems have been separate non-Internet-connected systems that provide the “command and control” for critical infrastructure. With the advent of technology and the desire to implement this technology to make communications and support easier and faster, SCADA systems have evolved into being very much like your typical office network. One of the challenges though is that the mentality concerning SCADA system security hasn’t always been embraced. Some organizations still don’t understand that the threat to SCADA systems has dramatically increased over the last several years due to these network-like connections. “Security by obscurity” is no longer an option for SCADA security.
Assessments Are the Right Thing to Do
Protecting the confidentiality, integrity, and availability of critical process, operational, corporate, and customer information should be enough of a motivator for organizations to assure that their SCADA systems are protected. This is the concept of due diligence and is generally referenced by considering whether the security protections compare sufficiently to what would be considered normal and reasonable in the industry. Organizations must want to protect our critical infrastructure from malicious hackers, botnets, Denial-of-Service attacks, viruses, corporate espionage, and human error.
Events such as the 2003 Northeast power outage that affected parts of the United States and Canada, the 2008 Florida power outage that affected large parts of Florida, and the 2007 sponsored hack at the Idaho National Laboratories where a hacker was able to blow up a generator should be a pretty serious wake-up call for the industry. No longer is SCADA separate and not exposed. It is very much out there as a target, with enough serious threats to warrant significant attention to the protection of SCADA and the information that is processed, transmitted, and/or stored.
Assessments Are Required
Homeland Security Presidential Directive (HSPD)-7 talks about the protection of critical infrastructure. SCADA systems are generally serving a command-and-control function within this critical infrastructure and therefore have a direct mandate for protection. Other requirements come from the North American Electric Reliability Council (NERC). Believe it or not, guidance is available on how to implement and protect SCADA.
Information Protection Requirements
United States Federal Government and Department of Defense (DoD) have done a great deal of work on information protection and information assurance. The National Institute of Standards and Technology (NIST) has developed an entire series of special publications with information on things to do to protect systems. The National Security Agency (NSA) has developed and provided two methodologies that you can be certified in for assessing organizations and information systems for vulnerabilities. The NSA INFOSEC Assessment Methodology (IAM) focuses on an organizational view of vulnerabilities, while the NSA INFOSEC Evaluation Methodology (IEM) focuses on finding technical vulnerabilities within the information systems that process, transmit, and/or store critical information.
This author is a firm believer that if you study the various standards out there for any industry, greater than 80 percent of the requirements are the same. These commonsense requirements reflect a best practice approach to protecting critical information. As we discuss the standards and methodologies in this chapter, you will see some of this reflected in the comparisons.
National Institute of Standards and Technology (NIST) Guidance
NIST has defined a layered security model that has 17 control families (Table 3.1), which covers a tremendous amount of security protection mechanisms. This information can be found in NIST Special Publication (SP) 800-53, Recommended Security Controls for Federal Information Systems. SCADA systems are not necessarily Federal Information Systems; however, NIST’s work lays an excellent foundation for security within organizations.
Table 3.1
| Class | Control Family |
| Management | Risk Assessment |
| Management | Planning |
| Management | System and Services Acquisition |
| Management | Certification, Accreditation, and Security Assessments |
| Operational | Personnel Security |
| Operational | Physical and Environmental Protection |
| Operational | Contingency Planning |
| Operational | Configuration Management |
| Operational | Maintenance |
| Operational | System and Information Integrity |
| Operational | Media Protection |
| Operational | Incident Response |
| Operational | Awareness and Training |
| Technical | Identification and Authentication |
| Technical | Access Control |
| Technical | Audit and Accountability |
| Technical | System and Communications Protection |
North American Electric Reliability Council (NERC) Critical Infrastructure Protection (CIP) Standards
NERC (www.nerc.com) works with the U.S. Department of Energy and the U.S. Department of Homeland Security to coordinate security needs and requirements. This collaboration allowed NERC the opportunity to create a series of Critical Infrastructure Protection Standards. These standards are:
![]() CIP-002 – Critical Cyber Asset Identification
CIP-002 – Critical Cyber Asset Identification
![]() CIP-003 – Security Management Controls
CIP-003 – Security Management Controls
![]() CIP-004 – Personnel and Training
CIP-004 – Personnel and Training
![]() CIP-005 – Electronic Security Perimeter(s)
CIP-005 – Electronic Security Perimeter(s)
![]() CIP-006 – Physical Security of Critical Cyber Assets
CIP-006 – Physical Security of Critical Cyber Assets
![]() CIP-007 – Systems Security Management
CIP-007 – Systems Security Management
Water Infrastructure Security Enhancement (WISE)
The American Water Works Association, the American Society of Civil Engineers, and the Water Environment Federation have taken a grant from the United States Environmental Protection Agency to develop WISE (Water Infrastructure Security Enhancement). WISE provides security guidance for water and wastewater/storm water utilities. These voluntary (so far) standards are heavily dependent upon physical security in the water utilities, but WISE does address an entire process of risk assessment and risk management that can easily be transitioned into supporting information security needs. It is a good start and may lead to greater guidance on the technical security as well. More information on WISE can be found at www.awwa.org/science/wise/.
The Critical Infrastructure Information Act of 2002
The Critical Infrastructure Information Act of 2002 and subsequent procedure clarifications established how Critical Infrastructure Information (CII) is received, validated, handled, stored, marked, and used. SCADA Systems have both direct and indirect involvement with CII. The United States Department of Homeland Security defines CII as information not normally in the public domain (including system, facility, and operation security information) that is associated with the security of critical infrastructure or protected systems.
An Approach to SCADA Information Security Assessments
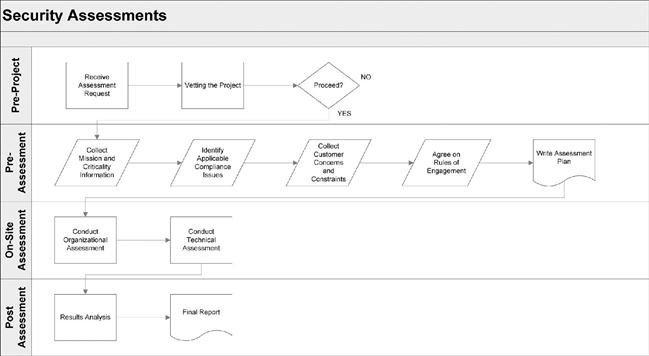
A methodology for conducting a security assessment is a process that utilizes a well-defined framework to identify the potential security vulnerabilities and determine what corrective measures must be implemented to protect the confidentiality, integrity, and availability of SCADA data.Figure 3.1represents a logical flow diagram of the security assessment process. The National Security Agency (NSA) INFOSEC Assessment Methodology (IAM) and the INFOSEC Evaluation Methodology (IEM) are the cornerstone of the assessment process discussed in this chapter.
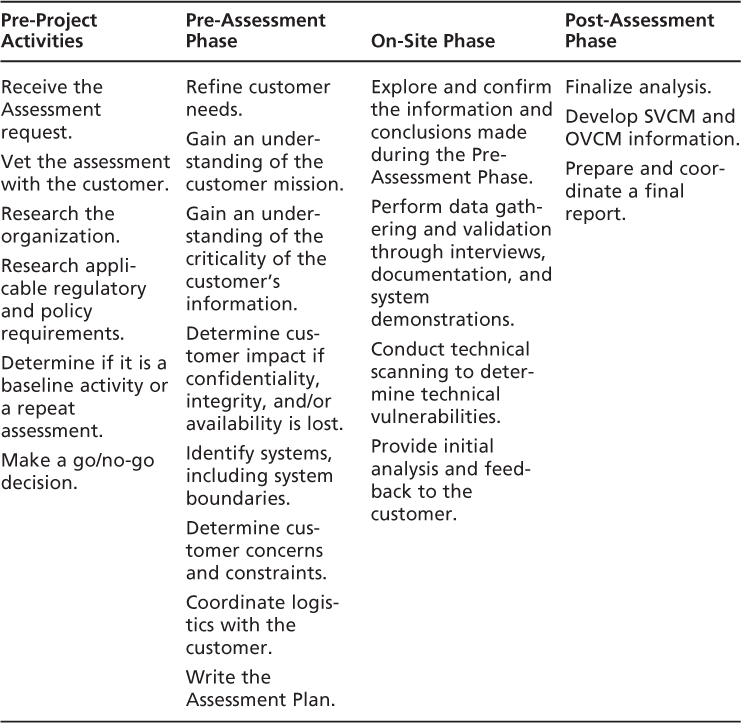
Prior to any project starting, several considerations must be taken into account to assure a complete understanding of the requirements. The pre-project activities will then lead into the three primary phases of the assessment, which are Pre-Assessment, On-Site Assessment, and Post-Assessment. Each phase will be outlined in the following sections.Table 3.2provides a high-level breakdown of the activities that occur during the full assessment process.
Pre-Project Activities
Pre-project activities include several steps that assist the assessment providers in assuring a basic understanding of the security needs of the customer. Several primary actions in the pre-project area are important to prepare the assessors for conducting the assessment process. These include:
![]() Vetting the assessment request
Vetting the assessment request
![]() Gaining management and technical buy-in for the assessment
Gaining management and technical buy-in for the assessment
![]() Researching the current regulatory and policy requirements
Researching the current regulatory and policy requirements
![]() Determining whether the action is a baseline activity or a repeated assessment
Determining whether the action is a baseline activity or a repeated assessment
Vetting the Assessment Request
Vetting, in this case, is simply assuring that the customer is getting both what they expect and what they need from the assessment process. Many times, organizations will catch hold of a buzzword like “penetration testing,” “assessment,” or “evaluation” without having an understanding of what the terms mean. A good approach to vetting is to spend quality time with the customer discussing the positive and negative aspects of each of the processes and explaining what the customer can expect at the end of the process, including deliverables.
The vetting process is accomplished by a combination of direct interaction with the customer and a small scoping questionnaire. It is then reinforced by educating the customer on the standard best practices for an assessment and any supporting regulations or policies that are applicable. Without the vetting process, you cannot understand or meet customer expectations, which can lead to project failure.
Gaining Buy-In from Management and Technical Personnel
Getting buy-in for the assessment from both the management staff and technical staff is essential to a successful project. Buy-in helps reinforce the importance of the assessment process and brings the organization’s attention to the importance and benefits of conducting an assessment within the organization. Without buy-in, official and unofficial roadblocks or constraints may be put on the assessment team, which could lead to project failure. Work hard on the front-end of the project to assure this buy-in, which will assist in a good experience and a smooth-running assessment.
Management Buy-In
Management support for the assessment is absolutely required since management does several things that will drive the success or failure of the project. For instance, it sets the tone of the organization and the necessity to show how important security is to the organization. Management will also enforce the necessity of staff cooperating with, and supporting, the assessment team.
To gain management buy-in, include them in the process. Help them feel ownership of the information, the determinations, and the responsibility to assure security. The use of “Fear-Uncertainty-Doubt” (otherwise known as the FUD factor) as a tool for getting management support should only be used as a last resort. A better way is to help management understand considerations such as:
Technical Staff Buy-In
Can you treat the technical staff the same way you treat management? The answer is, of course, NO! Technical staff will think of things from a different approach than management. Technical staff buy-in is also essential to the success of the project, however, so spend some quality time with the technical staff early in the assessment process. To gain technical staff buy-in, you must:
Researching the Organization
Another important step in understanding your customer is to research publicly available information about the organization. This will help display your interest in the customer, plus give you some points of discussion and clarification about the organization. Sources of information for this include:
![]() The customer’s Web site Shows how the organization wants to be seen by the public.
The customer’s Web site Shows how the organization wants to be seen by the public.
![]() The competitors of the customer Web sites Shows the potential areas competitors see as important and may identify some deficiencies, as well as additional questions to ask the organization.
The competitors of the customer Web sites Shows the potential areas competitors see as important and may identify some deficiencies, as well as additional questions to ask the organization.
![]() Whois With a “whois” query, you can input a URL and learn what IP address is associated with that URL. In this case, it helps you understand who a customer’s Internet service provider (ISP) might be and other possible interconnections within the customer environment.
Whois With a “whois” query, you can input a URL and learn what IP address is associated with that URL. In this case, it helps you understand who a customer’s Internet service provider (ISP) might be and other possible interconnections within the customer environment.
![]() Arin.net (American Registry for Internet Numbers) Utilizes a special “whois” query of its database through entering an IP range; it will show ownership information of that range of IPs.
Arin.net (American Registry for Internet Numbers) Utilizes a special “whois” query of its database through entering an IP range; it will show ownership information of that range of IPs.
![]() 10Q/10K Reports These are required quarterly (Q) and annual (K) reports that must be done by public companies to report the status of their business. It includes information like locations, employees, and so on, and may be useful in determining if there are areas of the business that may have been missed for assessment purposes.
10Q/10K Reports These are required quarterly (Q) and annual (K) reports that must be done by public companies to report the status of their business. It includes information like locations, employees, and so on, and may be useful in determining if there are areas of the business that may have been missed for assessment purposes.
![]() Business discussion boards These are Internet locations or blogs which discuss businesses in both a positive and/or negative way. These discussion boards can provide some useful information about the culture of the organization. However, you must be cautious since some of the information is more opinion- or emotion-driven than fact-driven.
Business discussion boards These are Internet locations or blogs which discuss businesses in both a positive and/or negative way. These discussion boards can provide some useful information about the culture of the organization. However, you must be cautious since some of the information is more opinion- or emotion-driven than fact-driven.
![]() Internet Search Engines Any of the Internet search engines can help you find useful information beyond the organization’s Web site. You might find articles written about the organization; press releases on products, services, or partnerships; and information about the corporation or leadership of the organization. This will help in better understanding the mission of the organization and its political and leadership structure.
Internet Search Engines Any of the Internet search engines can help you find useful information beyond the organization’s Web site. You might find articles written about the organization; press releases on products, services, or partnerships; and information about the corporation or leadership of the organization. This will help in better understanding the mission of the organization and its political and leadership structure.
Researching Regulatory and Policy Requirements
Most organizations are faced with the reality of falling under some kind of regulatory, legislative, or industry requirements. Especially when dealing with SCADA systems and other systems that affect critical infrastructure. Homeland Security Presidential Directive (HSPD) 7 drives the requirement for protecting critical infrastructure.
The pre-project efforts involve identifying the applicable regulations, legislation, and industry policies. This will vary between different organizations, and this research is essential to assure that you gather the appropriate requirements. You are conducting this research prior to the start of the project so you can talk coherently about the drivers and impacts within the organization. This does not mean you don’t have to ask the organization about what they must follow since there may be some unique aspects of their business that must be considered. The following is just a starter list of the different regulatory or legislative requirements the organization may be affected by:
Determining if this Is a Baseline Assessment or a Repeat Assessment
You are always hopeful this is not the first assessment that is being conducted on the SCADA system. However, due to the fact that SCADA security has been largely ignored over the years, this may very well be the first security assessment conducted. In that case, it is the baseline assessment. The value of it being a repeat assessment would be the existing information you can pull from to start the process. But if it is a baseline assessment, you need to expect to spend more time on the front-end of the project to document and better understand what is currently in place within the assessed organization.
Making a Go/No-Go Decision
Every project has a go/no-go decision point. In most cases, it will be a “Go”; however, if you cannot get management and technical support, or if there are severe limitations placed on the assessment team, you may have to make the difficult decision of “No-Go.”
Pre-Assessment Activities
The Pre-Assessment process is an essential activity that will provide a great deal of information and important mechanisms to assure that the organization gains a level of buy-in from both management and technical staff.
The Pre-Assessment process provides the following important identification activities:
![]() Information criticality matrices
Information criticality matrices
![]() Defining of security objectives
Defining of security objectives
![]() Logical and physical boundaries
Logical and physical boundaries
Determining the Organizational Mission
Understanding the organization mission assists in the remaining activities of the assessment. The mission will provide the final determination of what the security objectives and security requirements are for the organization. It will also drive the critical information considerations, impacts, and will lead to some of the concerns and constraints. To obtain this information, you must talk with the customer and take the information from the research completed in the pre-project activities. An example of a simplified organization mission might be: “Provide reliable electric power to the state of California while operating safely, securely, and within the federal, state, and regulatory guidelines.” This will be documented in the Assessment Plan.
Identifying Critical Information
Critical information is simply the information that the organization requires to function. There is a tendency for firms to immediately jump to systems without thinking about what information is important to the organization. One aspect of critical information identification is that it must be done with the customer. In the end, it must be accepted by the organization as their information.
In order to get this critical information, a brainstorm session is typically done with various senior members of the organization in a brainstorming session. You will ask them, “What is the information you must have to make your organization function or to meet your mission?” You will then take that information and roll it up into a manageable set of critical information types. Please understand, this is not an easy process. You will need to spend a day or two with senior members of the organization to sort out this information. Some examples of possible information types might include:
The lists will vary by organization and according to the industries in which the organizations function. You cannot do a “cookie cutter” listing of information types even if the organizations are in the same industry. Each organization will have different areas of concern, different customers, and different business processes, all of which will drive different critical information types.
Example: Information Criticality
The Organization for Optimal Power Supply (OOPS) example will be utilized throughout the rest of the chapter—for example, purposes under permission from National Security Agency (NSA) INFOSEC Assurance Training and Rating Program (IATRP). More information on IATRP can be found at www.iatrp.com.
Business Description
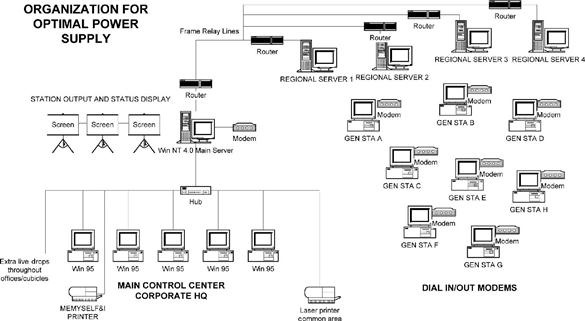
The Organization for Optimal Power Supply (OOPS) provides electricity to 1/20thof the United States’ citizens. They constantly monitor power consumption and redirect power according to demands. This includes initiating or terminating operations of generator stations.
Historically, OOPS has had a difficult time starting up idle generator stations when they are needed. Therefore, they have decided to place servers in each station to control the generator’s output and status. To activate a generator station, the regional office calls into the server and logs onto the machine. After a generator station has been activated, it updates its status and output to the regional server using hourly dial-up connections.
The control of all the OOPS generators is run through a main control center at the corporate headquarters. The control center decides when to activate any generators and which areas are in need of power. All of the regional offices are connected to the main server via frame relay lines, which allow for rapid updates of the current situation. All updates are done automatically by the servers, but can be initiated by authorized users if necessary.
Mission Statement
The Organization for Optimal Power Supply (OOPS) provides electricity to 1/20thof the United States’ citizens. OOPS constantly monitors power consumption and redirects power according to demands. This includes initiating or terminating operations of generator stations.
Critical Information for OOPS
Through a brainstorming session and detailed conversations with the OOPS customer, the following critical information types were agreed to between the assessment team and OOPS:
Please remember, this is not system information, but information that is needed for the OOPS to continue operations. The loss of confidentiality, integrity, and/or availability (CIA) of this critical information may lead to temporary or permanent damage to overall business operations or the business mission.
Identifying Impacts
The next step in the process is to identify the impact to the organization if there is a loss of CIA of the identified critical information. It is important at this point to identify the definitions of CIA.
![]() Confidentiality The information is only viewable by those with a need and an authorization to view it. Others may not view it. Sometimes called “need-to-know.”
Confidentiality The information is only viewable by those with a need and an authorization to view it. Others may not view it. Sometimes called “need-to-know.”
![]() Integrity The information is unchanged from its original state.
Integrity The information is unchanged from its original state.
![]() Availability The information is there when needed by those with the authorization to access or view it.
Availability The information is there when needed by those with the authorization to access or view it.
The organization may choose to add additional impact categories based on the business needs. Some of these additional categories may include (but are not limited to):
Identifying the impacts to an organization is absolutely the hardest part of the assessment methodology. An important aspect of identification of impact definition is that it must be done with the customer since it has to have the customer’s stamp of approval when completed. Why is this so difficult? Getting the customer to agree with themselves on what it means to lose CIA of their critical information is very difficult. It requires them to seriously consider their overall business operations, conduct a type of business impact analysis, and actually document and agree to the impacts as a whole based on their mission. The impact definitions are generally defined as High, Medium, and Low Impact.
Example Continued: OOPS Impact
In real-world situations, definitions will typically be between half a page and one page long. For presentation purposes in this chapter, we will keep it simple. However, please understand that this is just an example and more detail is needed to get a full picture of impact. For our purposes, the identified impacts to OOPS for the loss of CIA are the following:
![]() High Impact Competitive market loss greater than 10 percent; rolling blackouts; loss of generator station control greater than one hour.
High Impact Competitive market loss greater than 10 percent; rolling blackouts; loss of generator station control greater than one hour.
![]() Medium Impact Competitive market loss greater than 3 percent but less than 10 percent, or a regional blackout; or loss of generator station control greater than 15 minutes but less than one hour.
Medium Impact Competitive market loss greater than 3 percent but less than 10 percent, or a regional blackout; or loss of generator station control greater than 15 minutes but less than one hour.
![]() Low Impact Competitive market loss less than 3 percent or a regional brownout; or loss of generator station control less than 15 minutes.
Low Impact Competitive market loss less than 3 percent or a regional brownout; or loss of generator station control less than 15 minutes.
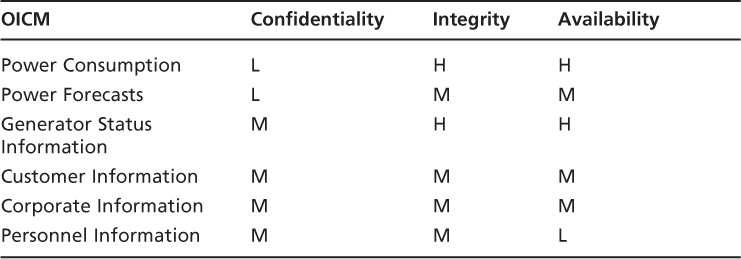
The Information Criticality Matrix
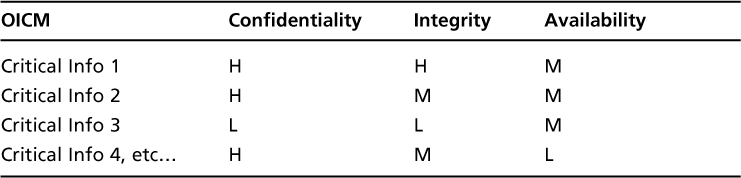
Taking into consideration the critical information types and the impact attributes, we can now build an information criticality matrix. The top line is simply the impact attributes (CIAs), while the rows are the critical information types identified by the organization.Table 3.3represents the framework for the Organizational Information Criticality Matrix (OICM).
Using the Impact Definitions
The impact definitions previously created are used to fill out the matrix. Be sure to create the impact definitions before trying to complete the matrix. The definitions of High, Medium, and Low will be utilized to determine what the impact is for the loss of any aspect of CIA.Table 3.4represents what the chart may look like when the values are input into the OICM.
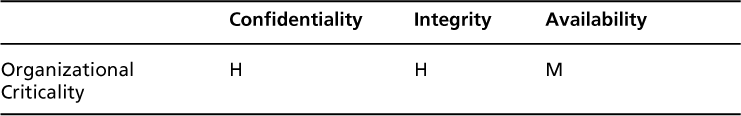
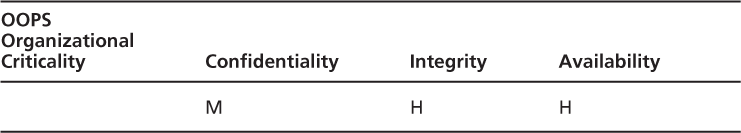
Organizational Criticality
The last step with the OICM is to take the highest level in each column to summarize the table and indicate the most critical impact areas for the organization. For our sample based onTable 3.5, the Organizational Criticality (sometimes called the “high water mark”) would be the following.
Example Continued: OOPS OICM
Based on the information we obtained from OOPS and through various discussions, we can now create the OICM for OOPS. Remember, we are using the definitions created earlier to fill out the matrix.
To complete this matrix, start with the first information type and ask yourself, “What can happen if I lose the confidentiality of my power consumption information?” Loss of the confidentiality of the power consumption information would result in a 3 percent or less competitive market loss, which is a Low. You then go to the next impact attribute, which is integrity. Again, ask yourself, “What can happen if I lose the integrity of my power consumption information?” In this case, inaccurate power consumption information could result in the generation of too much, or too little power, which could lead to brownouts or blackouts and loss of revenue or competitive advantage and would have a High Impact. The loss of availability of your power consumption information would have the same impact as loss of integrity.
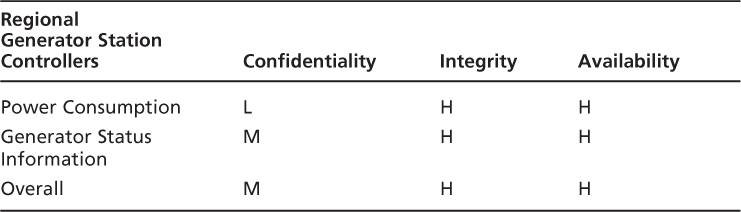
Let us work through the Generator Status Information type. If you lose the confidentiality of the generator status information, you may end up having too much information available to the public, allowing someone with ill intent to attempt to exploit the information to their advantage. For example, if it is known that a particular generator is down for maintenance and the backup generator is in use, someone could target the backup generator as a weak point in the system with no current backup capabilities. Therefore, the loss of confidentiality of the Generator Status Information would be at least a Medium. You do the same analysis with integrity and availability and find they could lead to High Impacts because they could cause brownouts or blackouts and a loss of revenue or competitive advantage. They could also lead to serious damage to the equipment.
Use the same concepts to complete the rest of the matrix, as shown inTable 3.6. Remember, however, that the matrix must be completed with the customer, and ultimately approved by the customer.
Now we determine the organizational criticality based on the highest level in each column and end up with the result displayed inTable 3.7. This shows that integrity and availability have a higher importance than confidentiality in relation to OOPS. This may be a common organizational criticality you might see within the SCADA environment.
Identifying Critical Systems/Networks
Critical systems can be defined as those systems that process, transmit, and/or store the critical information that was identified in the information criticality step. For our purposes, a system is not a single box but a group of components that work together to perform a function. You will identify the systems by communicating with the customer, looking at network and system diagrams, and asking many questions.
OOPS Example Continued
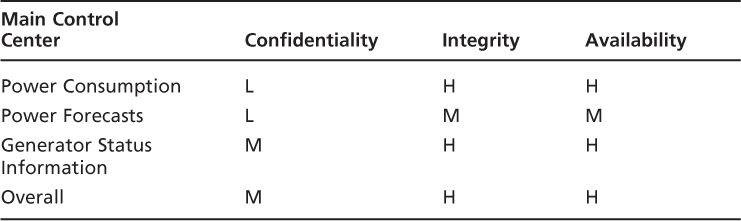
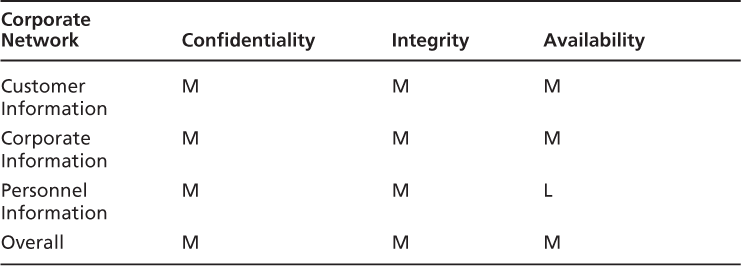
Note fromFigure 3.2that there are three (3) primary functional networks: The Main Control Center, the Corporate HQ Network, and the Regional Generator Station Controller. After the identification of the primary systems/networks, we are going to build a system criticality matrix for each. To do this, we utilize the information from the information criticality matrix and simply identify which critical information types are processed, transmitted, and/or stored on the identified systems/networks.
You will want to confirm with the OOPS personnel, but we can make a fairly logical guess that the following information types are processed, transmitted, and/or stored on the following:
Each system criticality matrix is created by simply cutting and pasting the applicable row from the OICM as demonstrated in the following three (3) tables. For each of the System Criticality Matrices, we can also do an overall “high water mark,” which is demonstrated as well.
Defining Security Objectives
Security Objectives are the targets the customer establishes for their security program. Without security objectives, they do not know what they are trying to accomplish for security and therefore will not reach any goals. Security Objectives are one of those areas requiring the customer’s involvement, and so the assessment team cannot make up the information.
Security Objectives come from a combination of inputs, including:
Security Objectives need to be well-defined and made known throughout the organization. Ultimately, the security objectives should be tied to the business objectives of the organization.
Determining Logical and Physical Boundaries
Understanding the logical and physical boundaries for the assessment plays an important role in managing the scope of the effort and preventing exceeding the bounds of the approved assessment and the scope. Be specific when defining the boundaries to assure a clear understanding.
Physical Boundaries
Physical boundaries are boundaries you can generally reach out and touch. These would include:
Determining the Rules of Engagement, Customer Concerns, and Customer Constraints
The rules of engagement, customer concerns, and customer constraints play an important role in baselining, scoping, and in better understanding the customer and any existing limitations.
The Rules of Engagement
The rules of engagement establish an understanding between the assessment team and the customer for those actions that will be part of the assessment. By establishing these rules, it allows both the assessment team and the customer to address any special needs. Included in the rules of engagement are:
Levels of Invasiveness
The typical technical assessment is not intended to be a penetration test or a red team. However, a customer may want additional activities above and beyond the standard evaluation to address some of their concerns. Some common additions to the standard activities for more invasive testing include:
Testing Machine Addressing
Arrange with the customer to obtain a static IP address for the scanning machines while conducting on-site activities. If this is not possible, ask the customer to implement an extended DHCP lease for these scanning machines to assure the IP addresses remain unchanged. You desire for the customer to know which scanning is coming from the assessment team. This is a cooperative effort and you don’t want someone implementing the Incident Response Plan inadvertently.
For external scanning, assure that the customer is aware of the external IP addresses the scans will be originating from during the testing. Again, you desire the customer to know it is an approved assessment team conducting the scanning and to know when it is an unauthorized entity running scans.
Time Frames for Scanning and Interviews
Every organization varies regarding when they are comfortable having scans run on their systems and networks. Since it is a cooperative effort, the assessment team will need to understand when peak processing times are on the systems and networks, as well as the potential impact to some important clients. In some organizations it is okay to scan at anytime. Others have limitations related to batch processing, or peak access times. These will be taken into account when planning and writing the Assessment Plan.
Conducting assessment interviews will also have an impact on the organization’s operations. The interview process should be documented in the Assessment Plan to assure there is an understanding of how the interviews are to be conducted and make certain that facilities are available to hold the interviews themselves.
Notification Procedures
Notification procedures are a necessity to address emergency situations where a system or server may have stopped operating during the testing. It is an objective of the NSA Methodologies to impact customers as little as possible. There also needs to be an understanding that bad things can happen and you must be prepared for any necessary recovery activities. Ask the customer to provide contacts that will be available to cover the time frames the team will be working with on the assessment effort.
Scanning Tools and Exclusions
NSA does not dictate the tools to be used for the technical scanning as part of the IEM process. However, the customer may not want certain tools used in their environment due to either a bad experience or things they may have heard from other organizations. It is important to honor these exclusions but try to understand why they have them.
Customer Concerns
Customer concerns are anything the customer has expressed as something they are particularly interested in or concerned about. This would include concerns about how the assessment might impact the customer’s network. They may also express a particular interest in one of the 18 Baseline INFOSEC Classes and Categories, which is introduced later in this chapter. Be sure to document any customer concerns in the Assessment Plan that were mentioned and be prepared to discuss them in the closing meeting and final report.
Customer Constraints
Customer constraints are simply anything that may limit the execution of the assessment or limit the recommendations that are made as a result of the assessment. Be sure to document any customer constraints in the Assessment Plan that were mentioned and be prepared to discuss these in the closing meeting and final report.
Legal Authorization
Since the assessment work includes a technical component that involves connecting to the customer’s networks and systems, there is a definite need to address the legal concerns. NSA recommends the assessment team have a “Letter of Authorization (LOA)” that is signed by the customer, which shows clear approval for the work being done. A copy of the LOA should be in the possession of each assessment team member while performing this work. I am not a lawyer and my lawyer says I cannot give legal advice; therefore, any work on the LOA will need to involve legal counsel from both the assessment team and the customer.
Writing the Assessment Plan
The Assessment Plan will encompass all of the considerations to conduct both an organizational and technical assessment for the organization. This is the scoping document and agreement between the assessment team and the customer to assure the full scope is well defined. Everything we have covered in the Pre-Assessment Process is to be documented in the Assessment Plan. The Assessment Plan will then be signed off on by both sides to assure mutual acceptance.
Components of the Assessment Plan
The following outline for the Assessment Plan takes into consideration the needs for understanding both the organizational and technical information necessary to accomplish the full assessment effort. These would be minimum essential considerations and may require additional business processes built around it to meet your organizational needs. This information is a combination of the Assessment Plan and the Technical Evaluation Plan that is part of the NSA IAM and IEM frameworks.
![]() Important Evaluation Points-of-Contact POC name, phone number, and e-mail
Important Evaluation Points-of-Contact POC name, phone number, and e-mail
![]() Methodology Overview Describe the methodology to be used to conduct the evaluation and identify the specific evaluation tools to be used during the evaluation process.
Methodology Overview Describe the methodology to be used to conduct the evaluation and identify the specific evaluation tools to be used during the evaluation process.
![]() Criticality Information A representation of the information criticality for each organizational system determined by discussion with the customer. Should include Organizational Criticality Matrix, System Criticality Matrices, Impact Value Definitions, and System Descriptions.
Criticality Information A representation of the information criticality for each organizational system determined by discussion with the customer. Should include Organizational Criticality Matrix, System Criticality Matrices, Impact Value Definitions, and System Descriptions.
![]() Detailed Network Information Include physical boundaries, identified subnets and IP ranges, detailed network diagrams, and contact information for system owners and administrators.
Detailed Network Information Include physical boundaries, identified subnets and IP ranges, detailed network diagrams, and contact information for system owners and administrators.
![]() Customer Concerns Include organizational and technical customer concerns.
Customer Concerns Include organizational and technical customer concerns.
![]() Customer Constraints Include organizational and technical customer constraints.
Customer Constraints Include organizational and technical customer constraints.
![]() Network connections and IP addresses, facilities, and so on. Scan windows, relevant IP addresses or subnets to access, and immediate administrator contact information for the customer.
Network connections and IP addresses, facilities, and so on. Scan windows, relevant IP addresses or subnets to access, and immediate administrator contact information for the customer.
![]() Internal and External Evaluation Team Requirements.
Internal and External Evaluation Team Requirements.
![]() Internal and External Customer Requirements.
Internal and External Customer Requirements.
![]() Evaluation team’s scanning of IP addresses, immediate contact information for assessment team, notification of personnel on assessment activities, CIRT coordination for test purposes.
Evaluation team’s scanning of IP addresses, immediate contact information for assessment team, notification of personnel on assessment activities, CIRT coordination for test purposes.
![]() Level of Detail for Recommendations How detailed does the customer want the recommendations to be? Will the standard low level for the executive summary and the mid-level for technical be ok, or is more detail going to be required?
Level of Detail for Recommendations How detailed does the customer want the recommendations to be? Will the standard low level for the executive summary and the mid-level for technical be ok, or is more detail going to be required?
![]() Anything not addressable in the other sections.
Anything not addressable in the other sections.
![]() Letter of Authorization Include the approved Letter of Authorization.
Letter of Authorization Include the approved Letter of Authorization.
![]() Time-Line of Events A sequence of important events and their associated dates. Some events include the following: the date of the receipt of the request letter, the date of the proposal or contract, customer coordination dates, planned internal and external dates, the report delivery.
Time-Line of Events A sequence of important events and their associated dates. Some events include the following: the date of the receipt of the request letter, the date of the proposal or contract, customer coordination dates, planned internal and external dates, the report delivery.
On-Site Assessment Activities
The On-Site Assessment is where the majority of the actual vulnerabilities will be identified for the organization and systems. This identification will include both organizational and technical findings. The way vulnerabilities are identified for the organization and the technical areas are different and are discussed next.
Conducting the Organizational Assessment
The organizational vulnerabilities are identified using the following methods:
The organizational portion of the assessment is focused around understanding the organizational security support concerning a set of control families or classes and categories. NIST identified 17 control families that must be considered as part of the controls put into place for federal government systems. These control families were identified earlier inTable 3.1.
NSA identifies 18 baseline categories to consider as part of any security implementation and are arranged by management, technical, and operational controls. This list of 18 areas is located inTable 3.11.
Table 3.11
NSA 18 Baseline INFOSEC Classes and Categories
| Management | Technical | Operational |
| INFOSEC Documentation INFOSEC Roles and Responsibilities Contingency Planning Configuration Management |
Identification and Authentication Account Management Session Controls Auditing Malicious Code Protection Maintenance System Assurance Networking/Connectivity Communications Security |
Media Controls Labeling Physical Environment Personnel Security Education Training and Awareness |
As you can see from the table, these control families and security categories are very comprehensive lists, covering a large volume of security considerations that must be part of a security review.
Documentation Review
Documentation plays a significant role in establishing the foundation for an organization’s security program. The organization should use documentation to set the organization’s vision and expectations. Documentation serves several purposes, including education, enforcement, and continuity. Lack of documentation within an organization would be a potential security vulnerability; however, it is unlikely it would be your only security finding. Documentation should establish the formal way an organization should be implementing their security program.
Interviews
Interviews are a key way to discover how the organization is actually doing things. Interview techniques are out of scope for this chapter, but understand that there is a psychology to interviews or “discussions.” In order to get the information you need from the individuals you are interviewing, you must first gain their trust. Remember you are not an auditor or an inspector—you are there to help the organization (and individuals) improve their security.
System Demonstrations
System demonstrations are an alternative way to get technical information from the organization without being required to run scanning tools or access their systems. It is simply a “Show-Me” activity. If you need clarification or information about something, you can simply say “Show me how you do that.”
Observation
The powers of observation are an inherent capability required of the typical security professional. From the very beginning of the assessment, you are watching what the organization does, how they treat employees, how they handle visitors, and the kinds of information that are freely available within the organization. This will lead you to additional questions, system demonstrations, or interviews.
Conducting the Technical Assessment
The technical portion of the assessment focuses on identifying and understanding the technical vulnerabilities that may exist within the SCADA environment. The technical assessment is referred to as an evaluation by NSA. The primary basis for these activities is defined in the NSA IEM. The IEM utilizes ten baseline activities that are necessary for consideration while conducting the technical portion of the assessment. These ten activities are broken out by enumeration and vulnerability identification areas, as identified inTable 3.12.
Table 3.12
| Enumeration | Vulnerability Identification |
| Port Scanning SNMP Scanning Enumeration and Banner Grabbing Wireless Enumeration |
Vulnerability Scanning Host Evaluation Network Device Analysis Password Compliance Testing Application-Specific Scanning Network Sniffing |
Enumeration Activities
Enumeration activities are used to determine what kinds of systems, applications, processes, and devices are on the customer systems. Enumeration activities are basically discovery activities that include:
![]() Port Scanning The act of connecting to potential services or ports on network accessible systems to determine what services and applications may be running on the network.
Port Scanning The act of connecting to potential services or ports on network accessible systems to determine what services and applications may be running on the network.
![]() SNMP Scanning With a known “community string,” active SNMP scanning can show information on user accounts, operating systems, services, and shared printers.
SNMP Scanning With a known “community string,” active SNMP scanning can show information on user accounts, operating systems, services, and shared printers.
![]() Enumeration and Banner Grabbing Enumeration tries to determine information such as users, servers, shared file systems, and other shared resources. Banner grabbing is a process of reaching out to an application and seeing if there is information about the application that can be pulled or “grabbed.”
Enumeration and Banner Grabbing Enumeration tries to determine information such as users, servers, shared file systems, and other shared resources. Banner grabbing is a process of reaching out to an application and seeing if there is information about the application that can be pulled or “grabbed.”
![]() Wireless Enumeration Looks for wireless networks that are part of the organization and how they are configured and secured. Also looks for external wireless networks that may impact the organization and searches for potential rogue wireless networks.
Wireless Enumeration Looks for wireless networks that are part of the organization and how they are configured and secured. Also looks for external wireless networks that may impact the organization and searches for potential rogue wireless networks.
Vulnerability Identification Activities
Vulnerability identification activities are the activities where a majority of the technical vulnerabilities will be discovered. The activities for vulnerability identification include:
![]() Vulnerability Scanning This activity is where the majority of vulnerabilities will be found. Vulnerability scanning runs from the network presence and looks for known vulnerabilities in the tools database.
Vulnerability Scanning This activity is where the majority of vulnerabilities will be found. Vulnerability scanning runs from the network presence and looks for known vulnerabilities in the tools database.
![]() Host Evaluation Look directly at individual systems to determine if they are configured with secure configurations and settings.
Host Evaluation Look directly at individual systems to determine if they are configured with secure configurations and settings.
![]() Network Device Analysis Analyze critical network devices to determine secure configuration and to evaluate if the device itself is functioning to provide security.
Network Device Analysis Analyze critical network devices to determine secure configuration and to evaluate if the device itself is functioning to provide security.
![]() Password Compliance Testing Test passwords to determine if the password policies are implemented and effective.
Password Compliance Testing Test passwords to determine if the password policies are implemented and effective.
![]() Application Specific Scanning Review the security of application functionality and secure programming techniques.
Application Specific Scanning Review the security of application functionality and secure programming techniques.
![]() Network Sniffing Analyze network traffic to determine what protocols are being used and if there is clear-text-sensitive information traversing the network.
Network Sniffing Analyze network traffic to determine what protocols are being used and if there is clear-text-sensitive information traversing the network.
Tools
The tools used to conduct the ten IEM baseline activities are determined by the team conducting the assessment work. NSA does not specifically imply or endorse any specific technical security tool or brand of tool. You can use freeware, shareware, or licensed tools. The IEM specifically requires you to run at least one tool to cover each of the ten activities. It is highly recommended you use more than one tool to cover each activity due to the limitations of the tools themselves. The tools are only as good as their underlying databases and the configuration the security consultants give to the tool.
Communication
Communication with the customer is required to assist in managing customer expectations. This involves assuring the proper opening meetings, closing meetings, and update meetings are conducted during the on-site effort. Good communications will reduce the number of potential issues between the customer and the assessment team.
Post Assessment Activities
The Post Assessment process involves taking all the information collected about potential vulnerabilities and determining the real risk to the organization. It is essential that the information gained in the Pre-Assessment process be taken into consideration during the analysis and reporting portion of the assessment.
Conducting Analysis
Detailed analysis not only involves looking at the scan results, it also involves using the skills and talents of the assessment team to determine the impact to the customer if a vulnerability is exploited. The assessment team cannot just “cut and paste” from the scanning tools, they must apply real analysis skills to the process. Effective analysis may involve bringing in additional expertise or conducting additional research to better determine how a particular vulnerability affects a customer.
Final Report Creation
The final report is the record of the activities conducted and the findings discovered during the assessment process. The final report needs to be a clear and concise document that provides a clear picture of the results. The minimum essential components of the final report should include:
![]() Executive Summary A short and concise description of the assessment and the major findings, written so executives can understand the results.
Executive Summary A short and concise description of the assessment and the major findings, written so executives can understand the results.
![]() Introduction This section will include a great deal of information from the Assessment Plan since it describes what was done during the assessment, which should be what you agreed to in the Assessment Plan.
Introduction This section will include a great deal of information from the Assessment Plan since it describes what was done during the assessment, which should be what you agreed to in the Assessment Plan.
![]() Analysis This section identifies what was found during the organization and technical assessment processes. This will include a detailed description of the finding, the analysis of how the finding affects the customer, and recommendations providing options.
Analysis This section identifies what was found during the organization and technical assessment processes. This will include a detailed description of the finding, the analysis of how the finding affects the customer, and recommendations providing options.
![]() Conclusion Answer the question for the organization: “What is my INFOSEC posture?” Recognize good security practices. Provide a recommended priority and roadmap for improving the organization’s security posture.
Conclusion Answer the question for the organization: “What is my INFOSEC posture?” Recognize good security practices. Provide a recommended priority and roadmap for improving the organization’s security posture.
![]() Appendices Include the analysis documents, the Assessment Plan, and a CD or other storage device with the raw scan reports on them.
Appendices Include the analysis documents, the Assessment Plan, and a CD or other storage device with the raw scan reports on them.
Resources
It is always helpful to have recommended resources for your client to get additional information on SCADA security or security assessments. I mention only a few here, but remember that your Web browser is a tremendous research tool. Some Assessment- and SCADA-related sites include:
![]() NSA INFOSEC Assurance Training and Rating Program www.iatrp.com
NSA INFOSEC Assurance Training and Rating Program www.iatrp.com
![]() NIST Special Publication 800-82: Guide to Industrial Control System Security www.nist.gov
NIST Special Publication 800-82: Guide to Industrial Control System Security www.nist.gov
![]() Digital Bond www.digitalbond.com
Digital Bond www.digitalbond.com
Summary
The evolution of SCADA systems toward standard TCP/IP networking and common applications is driving the need to implement and monitor effective security. Historically, SCADA systems have been considered separate systems that were not interconnected with the corporate network. Now the movement has been toward connecting to the internal intranets and even the Internet. This opens the possibility for the exploitation of holes in the security of these connected components. Implementing effective security and evaluating this security is critical to the continued successful operation of the SCADA environment.
An effective security assessment involves utilizing a solid defined framework that is repeatable. The NSA IAM and IEM provide a framework to work within for purposes of conducting the security assessment process. Four primary activities are discussed as part of the IAM and IEM, which support the security assessment process. These are:
The Pre-Project activities focus on gaining an understanding of what the customer is looking for in their security assessment engagement. Helping the customer get the service that will best benefit them will assist in establishing and managing the customer’s expectations. You will also want to address business processes, such as contracting and initiating legal aspects.
The Pre-Assessment process is an essential process for better understanding the customer’s needs. A great deal of the Pre-Assessment process involves understanding the customer mission and understanding the business information needed to make the organization run. This is a business focus, not just a security focus. Business risk and security risk are closely associated. An understanding of the impact to the organization if confidentiality, integrity, and/or availability are lost helps the assessment team better recommend improvements to the organization’s environment. Following the assessment team’s understanding of the mission, critical information, and impact, we go through the process of understanding which systems process, transmit, and/or store this critical information. The remaining portion of the Pre-Assessment process involves finalizing the scope of the assessment, establishing rules of engagement, defining customer concerns and constraints, and establishing timelines to meet and manage customer expectations.
The On-Site Assessment is broken down into two (2) areas: organizational and technical. The organizational assessment focuses on understanding what policies and procedures are in place in the organization and how the organization actually implements the security program. The information for the organizational assessment is collected based on interviews, documentation review, system demonstrations, and observation. The organizational assessment is also conducted based on the NSA IAM 18 Baseline INFOSEC Classes and Categories, or the NIST 17 Control Families. The organizational assessment is flexible enough to pull in the security requirements of any organizational need, including SCADA.
The second part of the On-Site Assessment is the technical assessment (or evaluation). The basis for the technical assessment is the NSA IEM 10 Baseline Activities, which encompass the majority of the technical scanning and analysis needs for a security assessment. The key consideration of using the NSA IEM is that it is not a “cut and paste” from the scanning tools, but a true analysis of the data collected to determine the technical vulnerabilities.
The Post Assessment process involves conducting the final analysis and putting together the final report. This process is important because it outlines the findings from the assessment process and gives the recommendations for improvement of the organization’s security posture. A critical aspect of the Post Assessment is to give a well-defined logical roadmap for security posture improvement.
SCADA systems control the majority of our critical infrastructure to include power, water, and sewage. Without the right security implementations and the continuous monitoring and assessment of SCADA system security, there could be a significant loss of confidentiality, integrity, and availability of the critical infrastructure.
Solutions Fast Track
The Evolution of SCADA
![]() SCADA systems have historically been treated as isolated entities that are relatively safe from security issues.
SCADA systems have historically been treated as isolated entities that are relatively safe from security issues.
![]() SCADA has evolved to utilize the same protocols as traditional networks; therefore, additional exposure now exists.
SCADA has evolved to utilize the same protocols as traditional networks; therefore, additional exposure now exists.
![]() SCADA is now being connected to the business network, exposing it to potential security issues.
SCADA is now being connected to the business network, exposing it to potential security issues.
![]() SCADA configurations and security must be tightly controlled.
SCADA configurations and security must be tightly controlled.
Pre-Assessment Activities
![]() Collect mission and business critical information, and impact if confidentiality, integrity, and/or availability are lost.
Collect mission and business critical information, and impact if confidentiality, integrity, and/or availability are lost.
![]() Determine the systems that process, transmit, and/or store the critical information.
Determine the systems that process, transmit, and/or store the critical information.
![]() Fully scope out the effort with the customer to include concerns, constraints, and rules of engagement.
Fully scope out the effort with the customer to include concerns, constraints, and rules of engagement.
![]() Write the Assessment Plan based on the Pre-Assessment activities and get a signature from the customer.
Write the Assessment Plan based on the Pre-Assessment activities and get a signature from the customer.
On-Site Assessment: Organizational Security
![]() Conduct interviews utilizing the NSA IAM 18 Baseline INFOSEC Classes and Categories as a guide or something similar, such as the NIST 17 Control Families.
Conduct interviews utilizing the NSA IAM 18 Baseline INFOSEC Classes and Categories as a guide or something similar, such as the NIST 17 Control Families.
![]() Review organizational security and business documentation.
Review organizational security and business documentation.
![]() Utilize system demonstrations to verify information or reduce conflict concerning the same.
Utilize system demonstrations to verify information or reduce conflict concerning the same.
![]() Use observation to continuously determine how the organization actually implements security.
Use observation to continuously determine how the organization actually implements security.
Frequently Asked Questions
Q I have never needed to worry about SCADA security in the past. Why should I now?
A SCADA systems have migrated toward common protocols such as TCP/IP instead of previously proprietary protocols. SCADA systems are now being interconnected on the same network as the business network, allowing for greater avenues of attack.
Q Why are the NSA IAM and IEM recommended as the methodology to use for SCADA assessments?
A These are extremely flexible methodologies that provide a clear and comprehensive framework for doing any kind of security assessment. The NSA IAM and IEM are not the only methodologies out there and the assessment team can choose which methodology to use. Be sure that, no matter which methodology you use, it covers a similar or better cross-section of information security topics.
Q Why not just give the potential customer exactly what they ask for?
A Because what they ask for may not be what they are really looking for. Be sure to conduct the Vetting process to give the customer what they need.
Q Is understanding critical information and impact important? Don’t we just need to know the systems?
A Understanding critical information and impact is essential to defining appropriate recommendations to improve the security posture. This process answers the question of “Why” security needs to be implemented and how much security is required.
Q Why is the On-Site Assessment work broken out between organizational and technical?
A The quick answer is because of the skill set. The skill set required for an individual to conduct the technical assessment is significantly different than those individuals who are conducting the assessment.
Q Can’t I just “cut and paste” the results out of the scanning tools?
A No. You must conduct an analysis to make it specifically relevant to that particular organization.
Q Can I get more help when I am conducting an analysis?
A Absolutely. Don’t be afraid to seek assistance either by doing additional research or bringing in additional expertise.
Q Are the NSA IAM and IEM rigid methodologies?
A No. The NSA IAM and IEM are very flexible methodologies that are usable across a broad section of organizational types.