Locked but Not Secure
An Overview of Conventional and High Security Locks
Marc Weber Tobias is an investigative attorney and security specialist living in Sioux Falls, South Dakota. As part of his practice, he represents and consults with lock manufacturers, government agencies and corporations in the U.S. and overseas regarding the design and bypass of locks and security systems. He has authored six police textbooks, including Locks, Safes, and Security, (ISBN 978-0398070793), which is recognized as the primary reference for law enforcement and security professionals worldwide. The second edition, a 1400 page two-volume work, is utilized by criminal investigators, crime labs, locksmiths and those responsible for physical security. A fourteen-volume multimedia edition of his book is also available online. His website issecurity.org.
As a former prosecutor and Chief of the Organized Crime Unit for the Office of Attorney General, state of South Dakota, Marc supervised many major investigations and prosecutions. He continues to work investigations for government and private clients, mainly involving technical fraud issues.
Marc is a member of a number of professional security organizations, including the American Society of Industrial Security (ASIS), Association of Firearms and Tool Marks Examiners (AFTE), American Polygraph Association (APA) and American Association of Police Polygraphists (AAPP).
Marc has lectured extensively in the United States and Europe on physical security and certain aspects of criminal investigations and interrogation techniques. He holds several patents involving the bypass of locks and security systems. Marc contributes a column to engadget.com and has been featured in many publications as well as radio and television stories around the world.

Figure 6.1 A cutaway pin tumbler lock with all six pins aligned at shear line. In this photograph the plug, containing the bottom pins, is free to rotate.
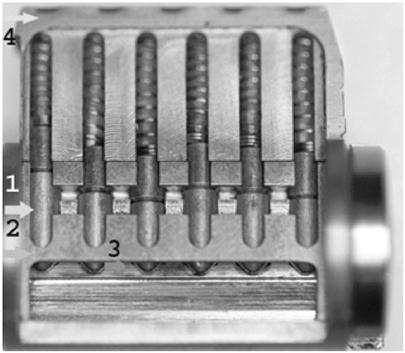
Figure 6.2 A cutaway of a pin tumbler lock in which some of the bottom pins are above and some below the shear line. The plug is not free to turn and the cylinder remains locked. The arrows indicate (1) bottom pins, (2) plug, (3) bitting of the key that raises the individual bottom pins to shear line, and (4) the shell of the lock.
Introduction
In most facilities, mechanical locks are relied upon as the first level of security. They protect doors, safes, and barriers from being opened, and they control the movement of obstacles to entry. The most popular mechanism, at least in the U.S., is the pin tumbler design although in some parts of the world the lever lock is still the first choice. In short, locks are used everywhere, and they are relied upon as the first line of defense.
Security officers, risk managers, information protection specialists, and others who are responsible for the physical security of a facility often base their selection of locks on the representations of the manufacturer in conjunction with security ratings that are established by standards organizations. High security-rated cylinders are most often specified to protect high value targets or critical infrastructure because it is assumed that they have met stringent requirements with regard to anticipated methods of entry during an attack.
Organizations are generally not capable of performing in-house tests to determine the suitability of locks for their specific requirements. They rely on the standards organizations and testing laboratories to promulgate minimum performance benchmarks and then to insure that the locks that are certified to such standards actually meet them. Reliance upon either Underwriters Laboratories or the Builders Hardware Manufacturers Association (BHMA) to insure a certain level of performance or security may not meet either expectation because of significant limitations in how these standards are promulgated and the certification testing that results from this.
The undue reliance upon standards as the primary protection criteria can potentially lead to significant breaches of security by knowledgeable attackers. In some cases, high security rated locks that were thought to be virtually impregnable can be compromised in seconds even by amateurs who are armed with certain information about their design deficiencies.
Understanding the limitations of locks and the standards by which they are rated should create a healthy skepticism about the claims and representations of their manufacturers with regard to resistance against forced entry, covert and surreptitious entry, and the compromise of key control. If you rely upon locks to provide any significant level of protection in terms of complexity to bypass them or time delay for an intruder to reach his or her intended target, then you need to explore further. What you have heretofore been taught with regard to just what protection the locks in your facility are actually providing may surprise you. After reading this chapter you might re-examine the way in which you employ locking hardware and the “real world” vulnerabilities that might be jeopardized by such reliance.
We shall first provide a survey of conventional pin tumbler locks and their attributes so that they can be distinguished from high security cylinders. Within the security community everyone knows that the typical pin tumbler mechanism is not particularly secure; pointing to their high security counterparts as the solution where greater protection against forced and covert entry attacks are required. We shall then review the standards that distinguish conventional from high security locks. Finally, we examine how conventional locks are compromised as a means to compare their attributes to their high security counterpart.
Conventional Pin Tumbler Locks
The generic pin tumbler mechanism comprises perhaps 95 percent of the locks in this country. They are produced in all forms and configurations and can provide any level of security from low to very high. There are billions of them and virtually all of the conventional pin tumbler locks are based upon the original Yale modification of the Egyptian concept. Most high security locks are also based upon a modification of the basic pin tumbler design.
We define conventional pin tumbler locks as those that do not have any special security enhancements. These locks provide the most basic in protection and do not have multiple layers of embedded security as encountered in high security cylinders.
These mechanisms do not carry “high security” ratings and thus are not produced to the same standards as their more expensive and rated counterparts. Conventional cylinders are what you find in hardware stores, Home Depot, Lowes, and the local lock shop.
As we will note there are no real security controls or any legal protection of their mechanical designs or keys. Conventional pin tumbler locks are relatively easy to open and generally offer little resistance against many forms of bypass, including some methods of forced entry, bumping, picking, impressioning, key duplication, and the replication of blanks by impressioning and casting techniques. The tolerances of the internal components may be significantly less than for high security locks, but so is their cost.

Figure 6.3 A conventional pin tumbler lock showing the three basic parts: the plug, the shell, and the keyway slot in the plug.
The Origins of the Modern Pin Tumbler Lock

Figure 6.4 The Egyptian pin tumbler lock was developed 4,000 years ago and relied upon a set of pegs to secure a moving bolt.
The original design of the pin tumbler lock was conceived more than four thousand years ago by the Egyptians. It was soon forgotten and lost in history until the mid-nineteenth century when Linus Yale decided it was time to produce a small, efficient, and secure lock. Yale’s invention of the double-detainer locking theory in combination with a shear line offered an alternative to the lever tumbler, which was really the only mechanism that was both practical and secure at the time.
The original Egyptian lock had several pegs (equivalent to pins) that dropped into the plug and were required to be lifted so that the movable portion (equivalent to the bolt) could be withdrawn. Yale decided that the more prudent approach was to incorporate two pegs (split pins) within each bore or chamber so that the key could be made very small and also accommodate many differs or different bitting combinations. This was the beginning of the revolutionary development of the modern pin tumbler lock.
In the Yale lock the two pins and a spring were forced downward to accomplish locking. Several sets of pins (called pin stacks) could be incorporated within one mechanism. Each of the bottom pins had to be lifted to a point called a shear line. Only when all of the bottom pins were elevated to the correct position could the plug be turned by the action of the key. The splitting of pins was the real genius of this invention because it allowed a very slight difference in their position to allow or prevent the key from working. Each bottom pin could have several different depth positions or increments and maintain a relatively high tolerance between the plug and shell.
From its inception, lock manufacturers began improving upon the original Yale design in order to provide for more differs (key combinations) and greater security. There are many variables that can be controlled within the pin tumbler lock to provide for different options and security enhancements.
In a perfect world a lock cannot be opened without the correct key or code. In the real world there are levels of difficulty or resistance levels to forced and covert entry techniques which are dictated by these alterations or modifications to basic designs. These include the type of mechanism, the development of secondary locking systems, and certain embedded security enhancements.
A Review: The Essentials of Pin Tumbler Lock Design
In its simplest form the modern conventional pin tumbler lock consists of six primary components, as we noted. Many subsystems and attributes determine the security, durability, and option flexibility of the mechanism and include:
![]() Physical characteristics (strength) of the material that is employed for the shell, plug and pins;
Physical characteristics (strength) of the material that is employed for the shell, plug and pins;
![]() Manner in which the rotation of the plug is transmitted to the actual locking mechanism (bolt, latch, or other fastener);
Manner in which the rotation of the plug is transmitted to the actual locking mechanism (bolt, latch, or other fastener);
![]() Number of pins, their shape and length, and available depth increments;
Number of pins, their shape and length, and available depth increments;
![]() Mechanical and geometric design of the key, including the number of bitting positions and bitting height;
Mechanical and geometric design of the key, including the number of bitting positions and bitting height;
![]() Design of the keyway with respect to its size and shape and the number, placement, and geometric design of the wards (within the keyway);
Design of the keyway with respect to its size and shape and the number, placement, and geometric design of the wards (within the keyway);
The double-detainer concept of security within the Yale pin tumbler lock is quite elementary and extremely clever. It can be seen that once a pin occupies space in both the shell and plug at the same time the plug is not free to rotate until the bottom pin is lifted to a point where blockage does not occur. That point is called shear line. It is defined as the place where the lower pin is precisely level with the diameter of the plug.
When the lower pin is lifted to shear line there is no longer an obstruction to rotation. This is because the top pin is fully contained within the shell and the lower pin is completely within the plug; no part of either pin is protruding into the other. The upper and lower pins are split at the exact point where a gap occurs between plug and shell. Because of the close tolerances achieved in manufacturing, the tumblers must be precisely leveled at their shear line. If they protrude or are recessed >±.003”, the plug will not turn. The exact tolerance depends upon the quality of the lock.
The keyway was added to the modern pin tumbler lock to limit what can enter the plug, unlike in the original Egyptian design. Once the key clears the wards within the keyway, the bitting can physically raise each of the lower pins to shear line. The bitting replaced the pegs in the Egyptian key.
All of the modern modifications to the Yale lock are but refinements of the simple principle of blocking rotation of the plug with movable detainers (pins, sliders, rotors, or other components). Thus, the rotating tumbler (Medeco®); dimple (Keso®, DOM, and Ikon); magnetic rotating tumbler (EVVA, Chubb); axial pin (Chicago Lock), and other iterations are all based upon the use of the split tumbler to stop rotation of the plug until all pins are lifted to one or more shear lines.
Security Enhancements for Conventional Locks
A conventional cylinder may employ any number of basic security options and convenience features but most do not. Kwikset is an excellent example. They are perhaps the most popular of the cheap locks that are sold in North America; more than twenty million cylinders are produced each year according to the manufacturer. They are everywhere and for the most part offer little to no security against forced or covert entry. Many of the cylinders contain what the author believes to be defective designs from the standpoint of security. Even high quality cylinder manufacturers offer little more in the way of security than does Kwikset. For consumer-level protection the conventional locking mechanisms may be sufficient, especially for residential applications. The security of the locks is minimal at best and they are not recommended for any critical facility.
Anti-Bumping Pins
As a result of the media attention to bumping in 2006, some manufacturers have implemented additional security measures in their cylinders. These steps have been taken to prevent common forms of bypass including bumping. Master Lock now integrates a special pin set in all of its locks to prevent bypass by this technique. Other manufacturers have designed preventative measures, but conventional pin tumbler locks are still inherently insecure. The approach that EVVA (Austria) and Master Lock have taken would appear to virtually eliminate the use of bumping as a bypass technique. Other manufacturers are expected to follow their lead especially because BHMA and UL are likely to add bumping to their testing standards.
Security Pins
Conventional locks employ security pins to make picking more difficult. The design of these specially shaped tumblers can take many forms, including serrated, mushroom, spool, or a modification of these basic shapes. They do not materially affect the ability to bump open most of these locks, nor will they frustrate certain other forms of bypass. These pins cannot significantly reduce the basic insecurity of conventional locks; they are only a minimally effective enhancement.
Keyways and Related Designs
Other enhancements can include restricted keyways, paracentric keyways, check-pins (such as Schlage Everest®), specially modified check-pins (such as Kaba Peaks®), interactive pins (Mul-T-Lock), changeable key systems (Instakey®, U-Change® and others), and interchangeable cores. The design of paracentric keyways can in some cases frustrate picking to some degree but not all forms of attack. Again, the fundamental problem is that the generic pin tumbler mechanism does not offer significant protection against many forms of bypass. There are only so many enhancements that can be implemented to the basic Yale design; it is still a relatively simple concept.
Bitting Design
The design of the bitting (cuts on the key) can also be modified to enhance the overall security of conventional as well as high security locks. Multiple layers of bitting may be utilized. These are generally referred to as Laser track locks and often employ sliding wafers. Some locks utilize multiple tracks such as the EVVA 3KS, and some are indented or stacked. Certain designs, such as the Mul-T-Lock MT5, employ multiple bitting systems, which use both dimple pin tumbler and a single track for a secondary locking system. Others may use dual bittings (such a BiLock)® or bitting overlays.
Irregular angles such as found with the DOM Diamant® are also popular and can be very difficult to duplicate but not to copy with silicone or other techniques. Interactive components and floating pins (Mul-T-Lock and others) have gained in popularity. Dimples, holes, protrusions, and embedded magnets have also been employed. In fact, perhaps the highest security cylinder in Europe (EVVA MCS) embeds four rare-earth magnets to make the replication of keys virtually impossible.
Design of the Key
Many security enhancements have been employed in an attempt to make keys and their corresponding internal locking mechanisms more secure. These solutions include side millings to control sliders and other pin sets, protrusions on keys in conjunction with internal sliders (Medeco m3 and Bilevel®), interactive elements (Mul-T-Lock and others), embedded magnets (Miwa, EVVA), notches in keys, rotation of bottom pins (Medeco), special keyways, irregular bitting shapes, single and telescoping dimple pins (Mul-T-Lock), holes in the key, embedded floating bearings, and transponders. The list of modifications to the basic pin tumbler design is endless but at the end of the day nothing can change the fact that it is the same insecure design that can be picked, impressioned, decoded, extrapolated for the top level master key, and bumped.
Standards for Conventional and High Security Locks
There are three primary standards that address the security of locks in the United States: UL 437, BHMA/ANSI 156.50, and 156.30. It is appropriate that the reader should understand the differences in specifications within these standards in order to clearly differentiate between conventional and high security cylinders.
The UL requirements apply to door locks, locking cylinders, security container key locks, and two-key locks. It does not directly refer to high security locking mechanisms although UL 437 is referenced in BHMA/ANSI 156.30, described later in this chapter. Neither UL 437 nor the BHMA standard addresses what we refers to as “real world testing” issues. Certain UL 437 and BHMA/ANSI rated locks can be bypassed in times much less than these standards provide for forced and covert entry. This issue has come to the forefront since 2006, and the media attention that resulted from reports about lock bumping in Europe and the United States.
Consumers, commercial facilities, and government agencies rely upon these standards because in most cases they do not have the in-house capability to test cylinders for bypass capability. It is incumbent upon UL and BHMA to develop performance ratings and tests to ensure that not only do the criteria contained within the standards reflect real-world techniques that are employed by criminals but also that the locks actually meet such testing criteria.
The process to adopt new standards by both UL and BHMA is based upon a consensus between manufacturers, security experts, insurers, consumers, trade organizations, and other interested groups. The procedure is cumbersome and overly restrictive, and it often results in the lowest common denominator in security because in many instances the lock manufacturers themselves are driving the process. Rather than defining the security of a lock in terms of time and perceived threat, the standards attempt to overly define each technique of attack. If the method that is employed to open a lock by a criminal does not precisely fit this standard, then these organizations deny any responsibility, saying that the standard does not address the issue and would have to be modified to encompass the particular bypass method. This is precisely the problem with bypass techniques for certain high security cylinders; both UL and BHMA have been placed on notice of certain techniques and have chosen not to investigative further.
As a result of research conducted by the author and others in both the United States and Europe, we can demonstrate that in some cases UL and BHMA are certifying locks that may not be secure for the intended purpose. We have advocated that UL and BHMA re-examine their testing protocols to ensure that what the consumers believe they are installing with regard to security is actually the case.
Transforming a Conventional Cylinder to High Security
High security locks are supposed to provide significantly greater resistance against many forms of attack that would be expected and commensurate with high value targets. These locks are more expensive, are produced to more exacting specifications, and have met certain performance criteria that manufacturers tout as their assurance that the locks can be relied upon to effectively stop an attacker for a defined period of time. The problem is that in some cases what the standards protect against may be a myth and can leave a facility vulnerable to forms of attack that may not have been contemplated in the standards when they were drafted.
Both UL and BHMA have made it very clear to the author that if the specific test protocol is not written into the standard then it does not count. Even worse, the manufacturer may not be cognizant of security vulnerabilities in their locks. This was documented through eighteen months of research by the author with regard to the dominant leader in the high security lock market in the United States and is the subject of a new book on the subject that has just been released.1
UL 437, BHMA/ANSI 156.50, and 156.30 are the three standards that you need to understand in order to distinguish between conventional and high security locks. The standards clearly distinguish the two categories of mechanisms. An understanding of the basic requirements will provide an insight into the levels of protection these locks are supposed to afford, how some of them can be compromised, and why the ability to do so can be catastrophic.
Notwithstanding the representations of some in the security industry, UL 437 is not a high security standard but rather a higher security standard. The UL standard primarily relates to pin tumbler locks; the BHMA standard is also directed at pin tumbler designs but does not exclude other locking mechanisms (such as wafer and lever tumblers). Many organizations rely upon UL 437 as the benchmark for security in their locks. However, what they think they are buying may indeed not be the case.
Tests to determine physical security against methods of forced attack specify the use of certain tools, timing, and breaking techniques. The standard defines the use of tools to include common hand tools, hand or portable electric drills, saw blades, puller mechanisms, pry bars, and picking tools.
UL 437 establishes minimum resistance times for different kinds of attacks. Net times in minutes are specified for each type of test and the lock upon which the procedure is to be performed. The sequence is not relevant, nor is the number of methods to be applied. One sample may be tested for several techniques or a new specimen may be utilized for each procedure. Door locks must resist picking and impressioning for ten minutes and forced entry attacks for five minutes. Unfortunately the standard does not contemplate that methods of attack that utilize both forced and covert methods can be applied to bypass the security of certain high security cylinders in far less time than is specified.
Deficiencies in the UL 437 Standard
It is submitted that significant deficiencies in the UL 437 standard exist that allow high security locks to be rated under the current protocols but will not actually protect against certain methods of forced and covert entry. UL is quite cognizant of these issues and is concerned about bringing certain standards into line with real world attacks. The organization took the first significant step in September 2007, when it decided that lock bumping might present a significant security issue and formed a bumping task force to examine the issue in detail. We will identify perceived deficiencies in UL 437 and how we believe these issues relate to the security of the locks that you may be using to protect your facility.
Failure to Specify Real World Testing
The standard fails to allow for the methods that are employed by criminals who may utilize advanced techniques or a combination of methods that may not have been contemplated by those who drafted the test protocols and resistance levels. By defining specific tests and tools that must be employed, the standard essentially excludes all others. Criminals do not follow the rules that are established in the UL protocols; they just open locks, containers, vaults, and strong rooms.
This point was graphically demonstrated in a recent bank burglary in New York where more than $700,000 was stolen by thieves who compromised a strong room that was rated to require a minimum of thirty minutes to make a small hole in the wall. During their endeavor the thieves started a fire to which the New York Fire Department responded. It took NYFD exactly four minutes to cut a large hole in the strong room wall that UL had certified to resist attack for a substantially longer period of time. That is what we define as a real world attack.
Pick and Impressioning Resistance
Only picking and impressioning techniques are considered in the UL standard. The use of special decoders, picks, electro-mechanical pick guns, borescopes, and many other techniques appear to be ignored although Section 11.2.5 of UL 437 seems to allow for picking tools designed for a specific lock.
The UL standard does not define the term “picking” but states that “any technique can be used to align the detainers.” It limits such tools to those commercially available and provides that an ALOA-certified locksmith of five years must conduct the tests. ALOA is the largest professional locksmith association in the United States.
In our view this definition is flawed because it does not contemplate special picking tools that may not be commercially available to locksmiths but may in fact be purchased by government agents and through unauthorized supply channels. Many of the tools that are described in the government version of LSS+ for bypassing high security locks are neither commercially available nor known to the locksmith community, yet the locks are installed to protect those very same government facilities.
This standard appears to apply only to attacks where the intruder may have limited sophistication or access to specialized picking tools. Those performing pick resistance tests may not even be aware of the existence of specialized tools that are available, even those that are sold in the commercial sector. An example is a tool that can be purchased to bypass three different generations of Mul-T-Lock UL rated cylinders. Many locksmiths are not aware of the availability of this pick that allows bypass of UL certified cylinders within a minute or two. If UL knows about this tool then they have chosen to exclude it from testing protocols. If those that are conducting covert entry resistance tests are not aware of its existence, then they are certifying locks that can be bypassed in well under the minimum times specified in the standard. In either event there is a serious problem because the UL 437 certification tacitly represents to insurers, consumer, and the security community that these locks will be essentially impervious or highly resistant to picking for ten minutes. In some cases this is simply not true.
Complex Forms of Picking
It is unclear whether the UL standard addresses advanced and complex forms of picking even though the language states “any method to manipulate the detainers.” To pick a Medeco lock, which is one of the most secure in the United States, the attacker must complete certain preliminary steps with regard to the rotation angles of the bottom pins. Whether this mode of picking would be included in UL 437 is unclear because it can be said to involve advanced forms of picking with code setting keys that are specially created for Medeco cylinders. This technique was never contemplated by the language of UL 437 because the Medeco attack requires the use of four special keys. Whether this constitutes a form of picking is an important issue because virtually all Medeco Biaxial and m3 cylinders can be reliably and rapidly picked if the correct procedures are followed, even though they carry a UL 437 rating.
The standard does not address the compromise of Interchangeable Core cylinders, which are utilized in many commercial facilities. They can be bumped and picked to the control shear line and the core removed. If the key code for the control key can be decoded the entire system can be easily compromised or be subject to sabotage.
Forced Entry Resistance
The UL standard specifies the type of tools that can be employed to test for forced entry resistance. We have developed several forms of forced attack that allow access to certain high security cylinders within seconds. These techniques are apparently not covered in UL 437 and can result in the complete bypass of all levels of security of these locks.
Issues Not Addressed by UL 437
The following issues are not addressed by UL 437 and may leave everyone who relies upon their expertise at risk.
Bump Keys
The industry now recognizes that bump keys are a serious threat both to conventional and high security locks. Any standard must adequately address different expertise levels of attack. A conventional bump key will never open any high security cylinder that contains a sidebar or other secondary locking system. If a bumping standard is defined only in terms of traditional bump keys, then it will not address the real issue. Any new standard must speak to advanced methods of bumping to encompass the types of attacks that can open many Medeco, Assa, Mul-T-Lock, and other cylinders within seconds.
Decoding Attacks
UL 437 is silent with regard to attacks based upon the decoding of internal components and the development of intelligence from the information that is deri-ved as the result of such techniques. Certain characteristics of a lock can be observed without the necessity of disassembly and the information that results can often be used to circumvent its security. The BHMA/ANSI 156.30 standard does address this issue on a very basic level, but does not go far enough. The UL standard is silent with regard to protecting the lock from such attacks.
Key Control

Figure 6.7 Key control is of prime importance in high security locks. In this photograph, a simulated key is shown in a Medeco Biaxial cutaway cylinder. This blank, fashioned from a safe deposit key, can be cut to open all of the latest Medeco cylinders and bypass virtually every keyway, even those that are the most proprietary and restricted.
UL 437 is silent with regard to any issues that relate to key control and for this reason alone it does not constitute a high security standard. The ability to compromise high security locks by copying, replicating, or simulating patent-protected keys is not addressed in UL 437 although it is in BHMA 156.30 to a limited extent. Key control is one of three primary criteria that define a high security lock because the ability to compromise keys can be critical in certain forms of attack, including bumping, picking, and the extrapolation of the top-level master key. An excellent example is the key control provided by the Medeco m3 and some Biaxial high security locks. It has been totally compromised by the author and allows for the simulation of specially coded keys that facilitate bumping and picking even in the most restricted of keyways utilized in government facilities.
Mechanical Bypass of Locking Mechanisms
Neither UL nor BHMA address the problem of mechanical bypass if the attack does not directly involve picking or manipulation of pin tumblers. This is a real problem because there are certain relatively simple techniques that can be employed to circumvent one or more levels of security on Grade 1 (BHMA 156.50) and high security cylinders. The use of wires, shims, magnetic fields, and other techniques should be addressed within the standards.
BHMA/ANSI Standards: 156.50 and 156.30
The Builders Hardware Manufacturers Association (BHMA) in conjunction with the American National Standards Institute (ANSI) has developed two primary standards that relate to locks: 156.50 (for auxiliary locks and cylinders) and 156.30 (for high security locks). Unlike UL, independent laboratories conduct compliance testing for the BHMA/ANSI standards.
BHMA/ANSI 156.50
This standard establishes criteria for auxiliary bored and mortise locks, rim locks, cylinders, and push button mechanisms. The testing protocols provide for operational, finish, dimensional, cylinder requirements, and security testing. BHMA 156.50 estab-lishes three grade levels: 1, 2 and 3; grade 1 is the most secure. Many of the locks that are rated as meeting grade 1 requirements can be rapidly bypassed by both forced and covert methods. 156.50 is not meant as a high security standard, but merely to provide some benchmark of quality of consumer-level cylinders. The reader should never rely on the 156.50 standard for security.
High Security Locks and the BHMA/ANSI Standard
High security locks are designed to provide a greater level of protection against the primary methods of attack that are employed by criminals, saboteurs, and spies – both outside of a protected area and from within by employees, service personnel, or those who may have or gain access to one or more locks. It is expected that a facility that is more likely to be a target will probably specify high security rated hardware. That is precisely the reason that manufacturers produce locks, deadbolts, access control systems, and other products to defend against more sophisticated forms of compromise.
High security locks are significantly more expensive than conventional cylinders. They are employed where security officers believe there is a higher risk of entry and compromise of infrastructure, assets, systems, and personnel. In many cases, insurers or government regulations demand the installation of this type of hardware because of its perceived resistance to methods of entry that are likely to be employed in an attack.
The Concept of Security
The term “security” must always be taken in context when considering mechanical locks and depends for its definition on a number of factors. In order to assess the “level of security” that a lock may provide, several questions must be asked. Specifically, “Secure against whom?” “Secure against what forms of attack?” “Secure for how long a period of time?” “What is the likely expertise of the attacker in terms of skill, training, and tools?” “What is the value of the assets that are to be protected?” “What other security measures are in place (defense in depth)?” and “What is the physical design of the facility?”
This concept of security is embodied in the 3T2R Rule. It is a shortcut that summarizes the requirements of any high security lock standard and relates those standards to five critical issues: Time, Tools, Training, Reliability and Repeatability. This rating expresses the ability to bypass a lock or locking system and is based upon the amount of time that is required, the training of the attacker, and the tools that he or she will employ. In order for the method of attack to be credible, it must be reliable and repeatable.
For example, previous methods of picking Medeco locks were not reliable because they were not completely repeatable. A new procedure has been developed that allows virtually all of the current generation m3 and Biaxial mechanisms to be reliably and rapidly picked open, and in many cases bumped open. Prior to 2007, such a method did not exist and so the criterion that requires that the technique must be both repeatable and reliable would not have been met. Thus the UL and BHMA rating for the Medeco m3 would have been valid and actually representative of the security of the lock prior to 2007.
As defined in BHMA/ANSI 156.30 there are three tenets of high security: protection against forced entry, protection against surreptitious or covert entry, and key control. All three of these criteria must be met in order for a lock to be rated for high security implementation. In contrast, a close examination of UL 437 reveals that only two of these criteria are present; key control is neither addressed nor required. The BHMA/ANSI standard establishes three security levels within its high security classifications (Level C, Level B, and the highest, Level A).
BHMA/ANSI 156.30 High Security Standard
This is the civilian high security lock standard in the United States. Although it references UL 437 for certain surreptitious entry tests, the BHMA definitions establish the criteria for high security lock certification. There are three critical sections that are enumerated within 156.30:
According to the BHMA, a standard lock must resist the defined forced entry attempts for five minutes and surreptitious attacks for a minimum of ten or fifteen minutes (depending upon security level). Consumers, commercial facilities, and government agencies rely upon these specifications to guarantee a minimum level of security. Unfortunately in certain cases the BHMA requirements, just like UL, do not address what we refer to as real world methods of entry.
They specify the types of tests that will be performed, but fail to address methods and techniques, as with UL, that will allow many high security rated cylinders and systems to be bypassed rapidly. Manufacturers may be unaware of such bypass techniques, may ignore them, may know about them and misrepresent the security ramifications to their customers, or they may be unable to make changes in their mechanical design that will prevent their bypass. If the standard does not address such methods of circumvention, then the public is misled and at risk.
Key Control
Key control relates only to the protection of keys and key blanks from access, duplication, and replication. The protection must encompass mechanical, legal, and tactical considerations. It is a fact of life that almost any mechanical key can be compromised, even those for high security locks. Patent protection will not prevent the illegal duplication or replication of keys, but may restrict the ability of an unauthorized supplier to make such blanks available commercially or otherwise. There are three levels of key control specified in the BHMA standard and they speak to the availability of blanks, legal protection, and factory control of blanks and cut keys. The requirements of 156.30 are intended to prevent or limit the availability of keys or credentials to unauthorized individuals.
The requirements under the BHMA/ANSI high security standard are supposed to protect keys from unauthorized duplication and generation by code. Unfortunately the standard is really directed at casual or non-professional attempts to obtain copies of keys and does not address the real world of determined attacks. We believe this is a serious flaw in the language of 156.30. There are many ways to create or obtain blanks or cut keys in order to circumvent the security of a system.
The requirements of the BHMA standard address only the most obvious aspects of key control and rely upon legal and manufacturer-imposed restrictions to limit access. In many instances this is quite sufficient, but in our view is inadequate when one contemplates attacks on high value or critical targets.
Destructive Testing
Destructive testing for forced entry methods encompass four categories under this standard and define three security levels (A, B, C). A is the highest level. Under these tests, plugs within cylinders are evaluated for their resistance to pulling, impact, torque, and drill resistance. Locks must not yield to these forms of force for a minimum of five minutes. The relevant issue is that some high security locks will not meet these requirements and may be subject to compromise by relatively simple techniques.
Surreptitious Entry Resistance
There are a total of five test criteria and three security levels for surreptitious entry resistance testing in order to receive a high security rating. The individual criteria relate to key changes (tolerance between depth increments), mechanical bitting, allowable differences between two adjacent depths (MACS), and pick and manipulation resistance. The requirements in this portion of the standard also speak to the ability to identify the dimensions of pins by a visual inspection or through the use of probes, shims, or other manual measuring tools.
There are two classifications within this section of the protocol: decoding and pick resistance. Locks must resist picking and decoding attacks for a minimum of ten minutes (as specified in UL 437) for the lower two security levels and fifteen minutes in the highest security level (A).
Pick resistance addresses three critical issues: security pins, paracentric keyways and balanced or graduated drivers (to prevent the use of comb picks). The standard also identifies certain forms of attacks for electronic locks and includes the use of electrostatic discharge, over-voltage, magnetic fields, and conductive liquids.
BHMA 156.30 requires that at least two security pins be placed in the lock to increase resistance to picking. Paracentric keyways must also be employed to make the vertical movement of picks more difficult. Finally, the standard requires that each pin stack length (bottom pin, top pin, and spring) be at least one depth increment longer than the overall length of the chamber. This will prevent comb picking which is a process of lifting all of the bottom pins above shear line to create a new shear line.
Deficiencies in the 156.30 Standard
There are deficiencies in the BHMA/ANSI 156.30 standard relating to key control, forced attacks, and picking that can and have resulted in the certification of cylinders that can be bypassed in far less time than is specified.
![]() The limitation to “manual manipulation” or picking tools that are commercially available to locksmiths is not sufficient to test high security cylinders against significant threats. The standard certainly would not include the government tools that are produced by John Falle nor would it address any of the bypass techniques that we document with regard to Medeco and other high security mechanisms.
The limitation to “manual manipulation” or picking tools that are commercially available to locksmiths is not sufficient to test high security cylinders against significant threats. The standard certainly would not include the government tools that are produced by John Falle nor would it address any of the bypass techniques that we document with regard to Medeco and other high security mechanisms.
![]() The standard fails to address the simulation of keys. It only speaks about the physical protection and control of key blanks, but does not address real world attacks. The ability to replicate or simulate restricted keys can be critical to advanced bumping and picking attacks and the copying of keys that are supposed to be secure.
The standard fails to address the simulation of keys. It only speaks about the physical protection and control of key blanks, but does not address real world attacks. The ability to replicate or simulate restricted keys can be critical to advanced bumping and picking attacks and the copying of keys that are supposed to be secure.
![]() The standard fails to test for certain methods to mechanically bypass the locking mechanism through the use of force. Most design engineers employed by lock manufacturers fail to understand or remember the first rule in designing a cylinder and related components that we noted earlier: The key never unlocks the lock; it merely actuates the mechanism that controls the bolt, latch, or other device. Many locks and their sophisticated security features can be easily bypassed through mechanical means with or without force.
The standard fails to test for certain methods to mechanically bypass the locking mechanism through the use of force. Most design engineers employed by lock manufacturers fail to understand or remember the first rule in designing a cylinder and related components that we noted earlier: The key never unlocks the lock; it merely actuates the mechanism that controls the bolt, latch, or other device. Many locks and their sophisticated security features can be easily bypassed through mechanical means with or without force.
![]() The BHMA standard should not be restricted to commercially available picking tools because it fails to consider advanced methods of attack that may be limited to a specific high security cylinder.
The BHMA standard should not be restricted to commercially available picking tools because it fails to consider advanced methods of attack that may be limited to a specific high security cylinder.
The BHMA requirement that ALOA-certified locksmiths must be utilized for those conducting a test does not ensure their familiarity with advanced techniques or competence to bypass certain types of mechanisms. Medeco, Mul-T-Lock, and Assa may perhaps provide the best evidence of this premise. Each of these Assa Abloy companies have vociferously objected and publicly denied that any of their high security rated cylinders could be bumped open, yet all of them can be bypassed in this manner.
Security Vulnerabilities of Conventional Locks: Why High Security Locks Are Supposed to Offer More Protection Against Methods of Entry
We now turn our attention to the limited security that is offered in non-high security locks and their vulnerability to attacks. These attacks have traditionally involved the compromise of the three fundamental criteria that distinguish high security locks from their less secure counterpart. We say “traditional” because there are other means to open locks that do not involve the standard methods of entry and which may be more practical and most often require less time and skill to accomplish. Such bypass techniques are often ignored or not even contemplated by UL or BHMA/ANSI.
There are other forms of bypass that may require advanced techniques: the use of special bump keys, sophisticated decoders, probes, manipulation devices, pin-and-cam systems (that combine picking and decoding), impressioning systems, and other procedures. They are all within the arsenal of the covert entry specialist and some professional burglars.
Most security managers rely upon UL and BHMA to establish the minimum requirements to protect their facilities. Mistakenly they believe that these standards organizations have developed comprehensive requirements that will effectively stop, deter, or resist the three primary methods of entry for a minimum period of time. However, there is a problem: the standards do not address certain forms of bypass and we believe specifically exclude certain tools, methodology, and expertise.
In short, if you rely upon UL or BHMA standards to protect your locks against knowledgeable or determined attackers, our advice would be that you do so at your peril. Their standards could be the model for Catch-22; any divergence from the defined protocols and the lock is not certified to protect against that risk, even though the intent of the specification is violated. To make matters worse, neither UL nor BHMA will even consider a report of the compromise of their rated locks unless such attack is already defined in the standard.
These special locks are employed in the most secure installations: the White House, the Pentagon, nuclear sites, and other critical targets. They are part of the security that protects advanced weapons systems, narcotics, huge amounts of cash, toxins, biological weapons, critical infrastructure, and most importantly, information relating to everything from financial data to top-secret national security issues. Yet some of these locks can be compromised in about thirty seconds when they were specifically designed to be impenetrable for a minimum of fifteen minutes! That precisely is the problem and what this chapter is about.
Conventional Pin Tumbler Locks: Security Vulnerabilities and Their Compromise
Virtually all pin tumbler locking mechanisms can be compromised covertly and by the application of force. At least fifty forms of bypass are indentified in LSS+ and the list is by no means exhaustive because as locks are examined by different experts, sports picking enthusiasts, and others that have a need to assess security, new methods of compromise are discovered.
Lock Control Procedures
The concept of lock control is often overlooked, but must be considered in the context of conventional cylinders and their ability to be compromised by removal from the system. Usually the purpose of such activity is to decode the top level master key (TMK). Organizations must define lock control policies to ensure the integrity of all of the cylinders within the system and to immediately account for missing or replaced locks as well as the inventorying or destruction of worn locks or those that are taken out of service. Locks are like hard drives from discarded computers; they can provide a wealth of information about a system and its security if they fall into the wrong hands.
Depending upon the hardware configuration most conventional cylinders can be easily and quickly removed even during normal business hours. This is especially true with regard to mortise cylinders, programmable locks, and some IC systems. If unauthorized access is gained to a cylinder, it can be quickly decoded by shimming or disassembled in order to derive all the possible pin combinations. Even easier is the ability to extrapolate the TMK without the necessity of taking the lock apart. Potentially a greater threat is the derivation of the control key (or, in some cases, the master control key in large systems) for interchangeable cores.
Key Control and Key Security
We have previously noted that UL 437 is silent with regard to key control. In our view a lock cannot be considered for high security installations unless its manufacturer implements certain safeguards with regard to the availability, duplication, and code cutting of keys. In contrast, the BHMA standard does address key control, but does not go far enough.
The BHMA/ANSI 156.30 High Security lock standard specifies three different levels of key control within its standard. The standard defines key control in terms of access to blanks and cut keys, but it fails to directly address perhaps the more relevant issue: the ability to replicate keys. Depending upon the security level in 156.30, key control under the BHMA standard attempts to ensure the following protection for the end-user:
![]() The availability of blanks for specific keyways;
The availability of blanks for specific keyways;
These three defined levels of key control are meant to prevent someone from having a key duplicated at Home Depot, Lowes, a hardware store, or the local locksmith unless that locksmith is part of a factory program and has the specific keyways assigned to him or her. In the lowest level of key control, designated locksmiths may be provided with certain keyways. Some are commercial and non-restricted, meaning that anyone can come in and have their keys duplicated.
Patent protection of blanks provides the manufacturer with legal remedies for anyone that produces, sells, or duplicates any blank for which a utility patent has been granted. Severe civil penalties are set forth in Title 35 of the United States Code for infringement. Many high security lock manufacturers have aggressively enforced their rights with respect to such infringement. In certain cases such protection may extend to the cutting of keys if the blanks have unique and patented characteristics.
Key Security
We define key security to mean the protection of any key, whether blank or bitted, from replication or simulation which would allow it to be used in an unauthorized manner. The key (and lock) must significantly resist the use of improperly replicated keys as well as altered, simulated, or copied keys. The intent is to prevent someone from obtaining access to one or more locks by using such keys to bypass the security of the internal mechanism. Methods would include picking, bumping, impressioning, simulation of the correct bitting, and other techniques.
The Concept of Key Control As It Applies to Security
The term “key control” may be misleading and identifies only part of the issue that is relevant to high security locks and their keys. Those responsible for ensuring that a facility and its locks are protected may believe their keys cannot be improperly obtained, but such may not be the case. Depending upon the required level of security, we believe that keys should be secure from compromise from casual, semi-skilled, or professional attackers.
The concept of key control usually relates only to the issue of availability of blanks from commercial sources and the implementation of controls for the duplication and generation of keys by code. It does not contemplate the illegal or unauthorized acquisition or production of keys to be used in conjunction with bypass techniques that rely on the use of such keys as a required precursor to a successful opening. In other words, we believe that 156.30 addresses one basic security threat: the acquisition of an original or duplicate key that will open the lock in the intended and normal manner. That is, the standard speaks only to inserting the correctly bitted key into the keyway, properly aligning the pins, and turning the plug. In our view, this is only one aspect of the insecurity of a lock that can be exploited by violating key control and key security.
The Importance of Key Control and Key Security
Why are “key control” and “key security” so important? The answer is quite elementary: the easiest way to compromise a lock is to open it with a key! That may seem obvious and overly simplistic, but it is an accurate statement and precisely why 156.30 addresses the issue of key control as one of its primary tenets. The circumvention of key control (and what should be its inherent key security) can also be used to facilitate several different forms of bypass. The compromise of certain high security locks relies upon the violation of key security to accomplish bumping, picking, master key extrapolation, and some forms of forced entry; it also includes completely compromising and circumventing the protection of restricted blanks (traditional key control of a facility). Medeco provides the classic example of how the simulation of a key can allow multiple levels of attack.
The violation of key security has wider implications and encompasses the compromise of keying systems, the simulation of blanks for restricted keyways, the circumvention of legal protection of keys, and rights amplification of blanks and cut keys. Any discussion of key control and key security should also include the consideration of policies relating to keys that are taken out of service because the bitting codes of associated locks have been changed. The failure to track old keys can provide an attacker with exactly the needed tools to create bump keys, system intelligence, special code setting keys, and the employment of advanced techniques.
Rights Amplification
A key that is subject to rights amplification can result in the compromise of a conventional or even high security cylinder. This term refers to the modification or alteration of a blank or cut key to use it in a manner not intended or to obtain rights to gain access to unauthorized areas. The concept has its roots in computer and software hacking and denotes the manipulation of software to obtain increased access privileges.
Perhaps the greatest threat from rights amplification is the use of a key to extrapolate the top level master key by probing the target lock for the presence of master pins. The tactical use of this technique is discussed in depth by the author in LSS+. An equal security threat is the modification of a change key into a bump key.
Replication, Duplication, and Simulation of Keys and Key Blanks
The concept of key control and key security necessarily includes protection against the replication, duplication, and simulation of key blanks and cut keys. Conventional pin tumbler locks are especially prone to these forms of attack. There are many techniques for both the replication and duplication of key blanks.
Replication refers to the ability to generate a blank key that precisely copies the warding patterns or approximates them so that the key is able to enter the keyway of a target lock. The concept is distinguishable from duplication of keys, which refers to the capability of copying the bitting pattern on a target key.
The concept of simulation refers to the ability to completely synthesize the requisite critical dimensions of a key blank so that it can be cut or shaped to align the pin tumblers to the shear line. A simulated key will generally be quite thin to allow it to pass through the center line of the wards within the keyway. Simulated keys are very difficult to use in true paracentric keyways because they cannot be properly inserted into the plug in vertical alignment to the base of the tumblers.
Gathering Intelligence About a System from Its Keys
Significant intelligence can be obtained with regard to a lock or system by gaining access to one or more keys. The process can be elementary for keys that fit conventional locks because usually only depth and spacing data is involved once the manufacturer and keyway have been identified. The process can be much more complicated for high security cylinders.
Information can be obtained with regard to the following parameters relating to conventional locks and keys and thus can present a significant threat to security:
![]() Whether the lock is high security rated;
Whether the lock is high security rated;
![]() Information regarding sub-master keys and bitting values assigned to progressed positions;
Information regarding sub-master keys and bitting values assigned to progressed positions;
![]() Whether odd or even progression has been employed in assigning individual codes;
Whether odd or even progression has been employed in assigning individual codes;
![]() Whether the system is master keyed and possibly the type of progression scheme;
Whether the system is master keyed and possibly the type of progression scheme;
![]() Predictability of keying progression;
Predictability of keying progression;
![]() The use of secondary locking systems;
The use of secondary locking systems;
![]() Use of check pins (such as Schlage Everest)
Use of check pins (such as Schlage Everest)
![]() Limitations on bitting values based upon MACS and the number of available depth increments;
Limitations on bitting values based upon MACS and the number of available depth increments;
![]() Other known manufacturer-imposed rules with regard to bitting;
Other known manufacturer-imposed rules with regard to bitting;
![]() Whether sectional keyways are employed and their hierarchy;
Whether sectional keyways are employed and their hierarchy;
![]() Master key system design and hierarchy based upon markings on keys or cylinders;
Master key system design and hierarchy based upon markings on keys or cylinders;
![]() Direct-reading codes that are stamped on keys;
Direct-reading codes that are stamped on keys;
![]() Ability to easily and rapidly decode keys either visually or with handheld instruments or key micrometers;
Ability to easily and rapidly decode keys either visually or with handheld instruments or key micrometers;
![]() Use of commonly available commercial keyways that may be obtained at hardware or DIY stores;
Use of commonly available commercial keyways that may be obtained at hardware or DIY stores;
![]() Ease of photographing or scanning keys and later reproduction.
Ease of photographing or scanning keys and later reproduction.
Covert Entry Techniques: Manipulation of Internal Locking Components
Manipulation of the internal locking components within conventional locks can be quite elementary in comparison to high security cylinders. There are many techniques that are available and they all accomplish the same function: simulating the action of the correct key by moving all the bottom pins (or a combination of master and bottom pins) to shear line. Recognized covert methods of entry include bumping, picking, impressioning, decoding, extrapolation of the top level master key, and mechanical bypass.
Bumping
Virtually all conventional pin tumbler locks can be opened by using traditional bump keys. The technique is easily learned, requires little skill, requires no specialized tools, and can be quite reliable. It is a serious security threat to all non-high security locks. Advanced bumping techniques have been developed to successfully open some cylinders produced by Medeco, Mul-T-Lock, Assa, and others. These procedures require the preparation of modified bump keys and the use of special techniques to circumvent locks with sidebar technology, but are highly effective against certain locks.
Picking
A distinguishing feature of conventional pin tumbler locks is their susceptibility to the manipulation of internal locking components through picking, raking, and key jiggling. The use of mechanical and electro-pick tools, pick-decoders, variable key generation systems, and other simple tools limits the security of these locks and demonstrate the need for higher security cylinders.
Impressioning
Virtually all pin tumbler locks can be impressioned with the result that a key is produced that will open the lock. Although some high security locks can also be impressioned or decoded and opened with this technique, it becomes much more complicated because there are often two or three separate and independent locking systems that must be bypassed. Even if a key is produced, it cannot open Medeco, Assa, or Primus locks without the simultaneous manipulation of the sidebar and its associated pin tumblers or finger pins.
Extrapolation of the TMK
The top level master key for almost all conventional pin tumbler locks can be easily extrapolated by probing the pin stack of each chamber with a change key for any cylinder within a keying system that is associated with the TMK.
Mechanical Bypass
Many conventional cylinders can be bypassed and opened without the use of the correct key because they are not designed to the same security specifications as those with high security ratings. Some UL 437 and BHMA 156.30 locks are not immune to simple methods of mechanical bypass. In OPEN IN THIRTY SECONDS: Cracking One of the Most Secure Locks in America, by the author, several techniques to open Medeco deadbolt, rim, and mortise cylinders by mechanically bypassing internal locking components are described. These techniques involve the bypass of multiple security layers that are supposed to prevent such practices.1
High Security to High Insecurity: Real World Attacks
In this chapter we have provided a brief analysis of conventional and high security locks and a review of UL 437 and BHMA/ANSI 156.30, the standards that are supposed to assure that certified mechanical locks will provide protection against an attacker. So how does all of this translate to real world threats and potential security vulnerabilities? If your facility employs conventional cylinders, then you have little protection against many forms of bypass, regardless of what any manufacturer represents. Conventional pin tumbler locks are inherently limited in the amount of security that they can provide. Manufacturers will tell you that if greater security against forced and covert methods of entry is required, then high security-rated cylinders must be installed.
That statement is in part true because these locks are manufactured to closer tolerances and generally employ added safeguards against many threats. But is that sufficient? The answer goes back to our discussion of just what constitutes “security” in the context of locks. If the concern is to prevent a knowledgeable attacker from circumventing the security of a lock, then the answer may be no. It is the last five to ten per cent of protection that we are concerned with, where you have to be certain that security cannot be easily compromised in critical areas.
If your facility has installed high security locks, it should be clear that they may still be at risk from threats that were not contemplated or covered in UL 437 or 156.30. The following abbreviated summary offers a view into the world of covert and forced entry and will hopefully cause those responsible for the security of their domains to reassess their locks and associated hardware. Further, if you think you have solved security problems inherent in mechanical locks by implementing an electronic access control system, you might want to consider that most of these systems have a mechanical lock as a backup against the failure of the electronics. The reality is that any such system can be compromised by neutralizing the lock and completely avoiding any smart card, RFID, magnetic stripe, or similar technology.
Virtually all conventional locks and some high security cylinders and their associated systems can be compromised by employing one or more of the following techniques. Caveat emptor!
![]() Extrapolation of the top-level master key by probing one cylinder;
Extrapolation of the top-level master key by probing one cylinder;
![]() Complete violation of key control and key security by the duplication, replication, and simulation of restricted keys and blanks;
Complete violation of key control and key security by the duplication, replication, and simulation of restricted keys and blanks;
![]() Rights amplification of cut keys to gain unauthorized access to secure areas by modifying the bitting to other values;
Rights amplification of cut keys to gain unauthorized access to secure areas by modifying the bitting to other values;
![]() Creation of bump keys from discarded keys within a system;
Creation of bump keys from discarded keys within a system;
![]() Use of a hybrid attack that involves two or more disciplines (such as forced and covert entry) to bypass deadbolt, mortise, and rim cylinders;
Use of a hybrid attack that involves two or more disciplines (such as forced and covert entry) to bypass deadbolt, mortise, and rim cylinders;
![]() Employment of simple methods of mechanical bypass to circumvent sophisticated and multiple layers of embedded security within mechanical locks by the use of wires, magnets, vibration, shock, sound, air pressure, and related techniques;
Employment of simple methods of mechanical bypass to circumvent sophisticated and multiple layers of embedded security within mechanical locks by the use of wires, magnets, vibration, shock, sound, air pressure, and related techniques;
![]() Determination of the sidebar code of the top-level master key from one key for one lock within a facility;
Determination of the sidebar code of the top-level master key from one key for one lock within a facility;
![]() Ability to externally view the internal components of a lock and derive significant intelligence that will allow the generation of keys that will open them;
Ability to externally view the internal components of a lock and derive significant intelligence that will allow the generation of keys that will open them;
![]() Ability to decode the control key within an interchangeable core system to allow access to any lock or to create a lockout condition.
Ability to decode the control key within an interchangeable core system to allow access to any lock or to create a lockout condition.
Summary
In this chapter we have presented a brief overview of conventional and high security locks. As more and more physical security responsibilities are assigned to information technology managers, it is incumbent upon them to understand “lock basics.” This is important in order to accurately assess potential threats against their facilities and infrastructure that may involve the bypass of locks and locking hardware. There is a great deal of marketing hyperbole in the security industry with regard to the resistance of locks against methods of covert and forced entry. Some manufacturers are unaware of certain methods of attack or will seek to minimize or downplay the potential results of such attacks. They often rely upon the UL and BHMA standards as their assurance that their locks have met those requirements and are thus deemed to be secure. If you take away one critical concept from this chapter it is that the standards may not adequately protect against certain threats that you may consider potentially serious.
Solutions Fast Track
High Security to High Insecurity
![]() Conduct independent research before selecting high security cylinders to be certain that what they promise is what they actually deliver.
Conduct independent research before selecting high security cylinders to be certain that what they promise is what they actually deliver.
![]() Do not rely solely upon standards when you select a high security solution. Consider specific risks that may be encountered in your facility and consult with covert entry experts that have conducted independent evaluations of the locks you intend to install.
Do not rely solely upon standards when you select a high security solution. Consider specific risks that may be encountered in your facility and consult with covert entry experts that have conducted independent evaluations of the locks you intend to install.
Frequently Asked Questions
Q Are there any high security locks that you consider secure against real world attacks?
A There are many cylinders that we would consider suitable for use in high security installations. It all depends on how you define security and what the threat level is perceived to be. Certain locks such as Schlage Primus, Assa Protec, and Medeco m3 will all provide a certain level of protection. If absolute security and key control is required, then we would recommend two locks that are produced by EVVA in Austria: the 3KS and the MCS.
Q Why are key control and key security so important?
A The compromise of a key is the quickest and easiest way to circumvent the security of an individual lock or entire system. For this reason, keys for the most secure locks will contain an element that cannot be easily duplicated, replicated, or simulated. The EVVA Magnetic Code System is the best example. It is virtually impossible to replace one of the four rare-earth magnets in these keys, so the system cannot be compromised.
Q Are there any high security locks that are bump-proof?
A All high security cylinders can be said to be bump-proof against conventional forms of bumping. However, many of them can be opened with advanced bumping techniques. The answer depends upon your security requirements. Some certified cylinders are essentially impervious to bumping and others can be relatively easy to bump open if certain preconditions are met.
Q Is there any one common exploit that presents the most threat and that a risk manager should be most concerned about when selecting a particular lock?
A We would look at mechanical bypass, certain forms of forced entry, and the ease with which keys can be compromised. This was graphically illustrated in the new book about the compromise of Medeco locks (by the author). Two tiny screws provided the entire security of the Medeco deadbolt cylinder for the past twenty years. A very simple exploit was developed to break these screws and open the lock. This is what we would consider a mechanical bypass as well as a forced entry attack.
Q Can master key systems be made secure?
A Very few master key systems are truly secure. Most are a compromise between convenience and security and for that reason are not recommended unless they are necessitated by security and safety requirements. Most master key systems can be very easily decoded and the top level master key code extrapolated. Once this occurs, every lock within a facility is at risk. There are certain systems that are more secure than others.
Q Can certain locks on a master key system be made more secure against attack?
A There are many techniques for securing individual cylinders within a master key system. These techniques often involve keying certain locks with individual keys but not on the top level master key. Perimeter doors should never be controlled to the TMK, and locks on restrooms and public access doors should likewise not be set up on any master key to ensure that they cannot be reverse engineered in order to decode the TMK by an intruder.


