Practice Exam 2 Questions
- Ralph is reviewing user accounts and matching up the permissions assigned to those accounts in the ERP to access requests made by managers. What activity is Ralph undertaking?
A. Credential management
B. Usage auditing
C. Privilege auditing
D. Multifactor authentication
- Tom is concerned about the fact that executives routinely leave their mobile devices unattended on their desks in the office. What control can he enforce through his MDM tool to prevent misuse of those devices?
A. Remote wipe
B. Geofencing
C. Screen locking
D. Application control
- Taylor is conducting a business impact analysis for her organization as part of the organization's business continuity planning initiative. During that analysis, she identifies the amount of time that would be acceptable for a system to be down during a disaster. What metric should she use to capture this information?
A. RPO
B. RTO
C. MTTR
D. MTBF
- George is evaluating the performance of his organization's business continuity efforts and measures the amount of time that passes between each time that a web server experiences a hard drive failure. What metric should George use to capture this information?
A. RPO
B. MTTR
C. MTBF
D. RTO
- Ralph comes across a legacy infrastructure that uses telnet to create an administrative connection between a client and a server. Even though this connection takes place over a private network link, Ralph would like to replace telnet with a secure protocol to prevent eavesdropping. What protocol would be the easiest drop-in replacement for telnet?
A. TLS
B. FTPS
C. SSL
D. SSH
- Will is selecting a new encryption algorithm for use in his organization. Which one of the following algorithms is weak and should not be considered for use?
A. DES
B. 3DES
C. AES
D. RSA
- What type of proxy server is shown in the following illustration?

Figure 8.1
A. Forward proxy
B. Reverse proxy
C. Caching proxy
D. Content filtering proxy
- Fred created a set of IP restrictions on his Cisco router using Cisco's extended access control list (ACL) functionality. What type of access control model is Fred enforcing?
A. Role-based access control
B. Rule-based access control
C. Attribute-based access control
D. Discretionary access control
- Sandy is designing a new computing environment for his company. He is contracting with XYZ Cloud Services, who will be providing him with the ability to provision servers on a self-service basis. What type of cloud provider is XYZ?
A. SaaS
B. IaaS
C. PaaS
D. SecaaS
- Tom is investigating a report from his organization's intrusion detection system. After an exhaustive investigation, he determines that the activity detected by the system was actually not an attack. What type of report took place?
A. False negative
B. True positive
C. True negative
D. False positive
- What common clause in software is used specifically for error handling?
A. Try...catch
B. If...then
C. Do...while
D. For loop
- Which one of the following EAP protocols does not take advantage of transport layer security?
A. EAP-FAST
B. EAP-IKEv2
C. EAP-TLS
D. EAP-TTLS
- Linda is investigating a security incident that took place in her organization. The attacker issued himself checks from an organization account and then created false journal entries in the accounting system to cover them up. There are no signs of unauthorized activity in IPS or firewall logs. What type of attacker most likely conducted this attack?
A. Script kiddie
B. Organized crime
C. Insider
D. Competitor
- Carla is conducting a penetration test and she has successfully gained access to a jumpbox system through the use of social engineering. Her current access is as a standard user and she is attempting to gain administrative access to the server. What penetration testing activity is Carla engaged in?
A. Initial exploit
B. Pivot
C. Persistence
D. Escalation of privilege
- Kevin is deploying a new customer relationship management (CRM) server. The services offered by this device will be accessible only to employees of Kevin's company. What network zone offers the most appropriate placement for this server?
A. DMZ
B. Extranet
C. Intranet
D. Guest network
- Samantha is the administrator of her organization's mobile devices and wants to ensure that users have current versions of the operating system firmware. Which one of the following approaches will best meet this need?
A. Administrator installation
B. OTA upgrades
C. User installation
D. Sideloading
- Which one of the following data destruction techniques produces waste material that requires wearing a respirator during exposure?
A. Pulverization
B. Wiping
C. Purging
D. Degaussing
- Tim is investigating an ARP spoofing attack that took place on his organization's network. What is the maximum scope of a single ARP spoofing attack?
A. The attacker and the victim must be using the same router.
B. The attacker and the victim must be behind the same firewall.
C. The attacker and the victim must be connected to the same switch.
D. The attacker and the victim must be sharing a switch port.
- Which one of the following is not an appropriate use of the MD5 hash function?
A. Verifying file checksums against corruption
B. Partitioning database records
C. Creating digital signatures
D. Identifying duplicate records
- What type of lock is shown here?

Figure 8.2
A. Preset lock
B. Cipher lock
C. Biometric lock
D. Smartcard lock
- What cryptographic cipher is used in the Bcrypt key stretching function?
A. 3DES
B. AES
C. Blowfish
D. RSA
- Patrick is investigating a security incident and is able to monitor an intruder's activity on one of his servers. The intruder wrote a script that is attempting to log into a web application using an administrator account. It first attempted the password aaaaaaaa, followed by aaaaaaab, aaaaaaac, and so on. What type of attack is taking place?
A. Offline brute force
B. Online brute force
C. Dictionary
D. Rainbow table
- Which one of the following activities is not a passive test of security controls?
A. Configuration analysis
B. Penetration testing
C. Network monitoring
D. Intrusion detection
- Which one of the following is an example of a privilege escalation attack against a mobile device?
A. Jailbreaking
B. Sideloading
C. Man-in-the-middle
D. Tethering
- Which one of the following is an example of a platform-as-a-service (PaaS) computing environment?
A. Amazon EC2
B. Amazon Lambda
C. Microsoft Azure Virtual Machine
D. Microsoft Azure DNS
- Which one of the following techniques is an example of dynamic code testing?
A. Fuzzing
B. Data flow analysis
C. Taint analysis
D. Lexical analysis
- David is purchasing cloud infrastructure services from Microsoft Azure. Use of the servers he purchases will be strictly limited to employees of his company. What type of cloud environment is this?
A. Hybrid cloud
B. Private cloud
C. Public cloud
D. Community cloud
- Which one of the following tools is useful in testing the security of a wireless network's encryption key?
A. nmap
B. NetStumbler
C. Aircrack
D. QualysGuard
- Frances is investigating a security incident where a former employee accessed a critical system after termination, despite the fact that the employee's account was disabled. Frances learned that the employee, a software engineer, created a dummy username and password that was hardcoded into the application and used those credentials to log in. What type of attack took place?
A. Logic bomb
B. Backdoor
C. Remote access Trojan
D. Ransomware
- Orlando is configuring his network firewall to allow access to the organization's email server, as shown in the following image. He would like to allow internet users to send emails to the organization but would like to only allow internal users to access emails on the server. What protocol(s) should Orlando allow to access the email server from the internet?

Figure 8.3
A. IMAP only
B. SMTP only
C. POP3 only
D. IMAP and POP3
- Which one of the following RADIUS messages is normally found only in situations where an organization is implementing multifactor authentication?
A. Access-Accept
B. Access-Request
C. Access-Challenge
D. Access-Reject
- Visitors to the website arifrance.com found themselves directed to a website containing discount travel information when they expected to find the Air France corporate website. What type of attack took place?
A. Typosquatting
B. Website defacement
C. Clickjacking
D. Session hijacking
- Which one of the following terms best describes the level of firewall protection that is typically found in router access control lists?
A. Stateful
B. Stateless
C. Next-generation
D. Proxying
- Norm is designing a file transfer mechanism to facilitate the flow of information between the hospital where he works and an X-ray service provider with locations around the city. Which one of the following protocols does NOT provide a secure option for these file transfers?
A. SFTP
B. SCP
C. FTP
D. FTPS
- After running a vulnerability scan of a copy machine, Tom discovers the results shown in the following screenshot. What is the most likely cause of these results?

Figure 8.4
A. The copy machine has an embedded operating system.
B. The results are false positives.
C. Tom scanned the wrong IP address.
D. The results are true negatives.
- Colleen is running two load balancers in active/active mode. What is the most significant risk that she is likely facing?
A. Servers must be manually assigned to load balancers.
B. Network traffic may be misrouted.
C. The load balancers may not have the capacity to survive the failure of one device.
- Which one of the following cipher types works on plaintext one bit or byte at a time?
A. Block cipher
B. Stream cipher
C. AES
D. Blowfish
- What mode of cipher operation is shown here?

Figure 8.6
A. CBC
B. OFB
C. ECB
D. CFB
- Which one of the following tools may be used to scan a system over the network and detect potential vulnerabilities in that system?
A. Nessus
B. Nmap
C. Jack the Ripper
D. Kismet
- Which one of the following mobile device deployment models allows employees to bring personally owned devices into the corporate environment?
A. COPE
B. CYOD
C. BYOD
D. Corporate-owned
- Roger is conducting a penetration test and has gained administrative access to a system on his target network. He is now using those administrative privileges to set up a back door. What stage of the attack is Roger in?
A. Persistence
B. Initial exploitation
C. Privilege escalation
D. Pivot
- During a web application security review, Crystal discovered that one of her organization's applications is vulnerable to SQL injection attacks. Where would be the best place for Crystal to address the root cause issue?
A. Database server configuration
B. Web server configuration
C. Application code
D. Web application firewall
- Tim is choosing a card-based control system for physical access to his facility. His primary concern is the speed of authentication. Which type of card would be most appropriate for this situation?
A. Proximity card
B. Smart card
C. Magnetic stripe card
D. Photo ID card
- Which one of the following types of access is necessary to engage in a pass-the-hash attack?
A. Access to a domain workstation
B. Access to a domain controller
C. Access to a network segment
D. Access to a public website
- This diagram shows the results of testing the accuracy of a biometric authentication system. In this diagram, what characteristic is designated by the arrow?

Figure 8.7
A. CER
B. FAR
C. IRR
D. FRR
- Gail is a software developer who recently completed the coding of a new module that will be incorporated into one of her organization's products. Now that her work is complete, she is ready to request that the code be moved to the next environment. Where should the code go next?
A. Development environment
B. Test environment
C. Staging environment
D. Production environment
- What is the primary purpose of the Diffie-Hellman (DH) algorithm?
A. Digital signatures
B. Key exchange
C. Message confidentiality
D. Authentication
- Which one of the following characteristics does not accurately describe an Agile approach to software development?
A. Features are prioritized by the value added.
B. Customers should be available throughout the project.
C. Requirements are clearly defined before beginning development.
D. Changes are welcomed in the process.
- Carl is creating an authentication system where users seeking to access web applications will be redirected to a login page, such as the one shown here. What type of authentication is Carl seeking to implement?

Figure 8.8
A. SAML
B. SSO
C. Federation
D. RADIUS
- Which one of the following wireless networking protocols makes use of a backend authentication server?
A. WPA-PSK
B. WPA-Enterprise
C. WEP-PSK
D. WPS
- Nadine recently accepted a new position as the CISO of a financial institution. What regulatory body produces information security standards that specifically apply to financial institutions?
A. FDA
B. FERC
C. FFIEC
D. FRA
- Roger recently deployed an IDS on his organization's network and tuned it to reduce the false positive rate. Which one of the following categories best describes this control?
A. Corrective
B. Preventive
C. Detective
D. Compensating
- Xavier is concerned about the security of a wireless network in his organization's conference facility that uses WPS to connect new clients. What is the best action that Xavier can take to protect this network?
A. Remove WPS stickers from wireless access points.
B. Disable WPS.
C. Use a strong WPS PIN.
D. Change the PSK.
- Bruce is investigating a security incident that involves the embezzlement of funds from his organization. Which one of the following groups should be the first focus of his investigation?
A. Script kiddies
B. APTs
C. Insiders
D. Hacktivists
- Consider the hardware passcode generator shown here. What algorithm does this token use to generate passcodes?

Figure 8.9
A. LOTP
B. TOTP
C. HOTP
D. KOTP
- Which one of the following categories of account should normally exist on a secured server?
A. Guest account
B. Service account
C. Generic account
D. Shared account
- Which encryption mode of operation is shown in the following figure?

Figure 8.10
A. CTM
B. GCM
C. ECB
D. OFB
- Roger's digital forensics team places any mobile devices collected as evidence in bags such as the one shown here. What is the primary purpose of this bag?

Figure 8.11
A. Prevent communication with the device.
B. Maintain the chain of custody.
C. Categorize the evidence.
D. Prevent others from seeing the evidence.
- Mike would like to allow users on his network to securely access their personal Gmail accounts using the service's standard interface. What protocol must he allow through his network firewall to Google's servers to allow this access?
A. IMAP
B. SMTP
C. HTTPS
D. POP3
- Taylor is building a server where data will be infrequently written but frequently read. He would like to use a redundant storage solution that maximizes read performance. Which one of the following approaches would best meet his needs?
A. RAID 0
B. RAID 1
C. RAID 3
D. RAID 5
- In the following diagram, what type of attack is Mal waging against Alice?
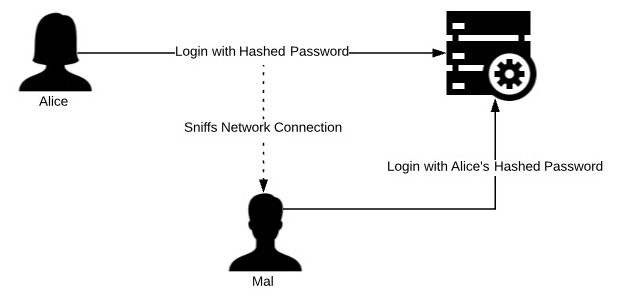
Figure 8.12
A. Man-in-the-middle
B. Social engineering
C. Replay attack
D. Dictionary
- Which one of the following statements is true about NTLM authentication?
A. NTLMv2 is protected against pass-the-hash attacks that exist in the original version of NTLM.
B. NTLM uses SHA-512 hashing to protect passwords.
C. NTLM and NTLMv2 are both insecure and should not be used.
D. NTLM is only available for Windows systems.
- When a certificate authority creates a digital certificate for a web server, what key does it use to apply the CA's digital signature to the certificate?
A. Server's private key
B. CA's public key
C. CA's private key
D. Server's public key
- Which one of the following authentication techniques generally provides the least degree of security for a mobile device?
A. Password authentication
B. Fingerprint authentication
C. PIN authentication
D. Facial recognition
- Mike stores some sensitive passwords in a text file called mypasswords.txt. The permissions for this file are shown here. Mike's user ID is mchapple. Which statement best describes the access permissions for this file?

Figure 8.13
A. Anyone on the system can read the file.
B. Only Mike can read the file.
C. Mike and any member of the staff group can read the file.
D. Only Mike and system administrators can read this file.
- In what type of attack does the attacker place malicious content on a website that is frequented by individuals in the target organization in the hopes that one of those individuals will visit the site with a vulnerable system and become compromised?
A. Man-in-the-middle attack
B. DDoS attack
C. Watering hole attack
D. Man-in-the-browser attack
- During a vulnerability scan of an internal web application, Christine discovers the issues shown in the following screenshot. What action should she recommend to correct the issue while minimizing cost and labor?
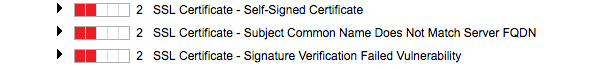
Figure 8.14
A. Replace the certificate with a certificate from a third-party CA.
B. Replace the certificate with a certificate from the same source.
C. No change is required. These are false positive reports.
D. Replace the certificate with a certificate supporting stronger encryption.
- Consider the statistics shown here for a biometric authentication system. What is the system's FAR based upon this data?

Figure 8.15
A. 1%
B. 2%
C. 8%
D. 16%
- Examine the digital certificate shown here. How many intermediate CAs were involved in the creation of this certificate?

Figure 8.16
A. 0
B. 1
C. 2
D. 3
- Frank is revising an application that currently stores Social Security numbers in a database. This is the only unique identifier available to him but he would like to store it in a way that nobody can determine the original Social Security numbers, but it remains useful as a unique identifier. What technology can Frank apply to best meet this requirement?
A. Steganography
B. Encryption
C. Decryption
D. Hashing
- Roger's company did not have a strong disaster recovery plan and suffered a catastrophic data center outage. With no plan in place, what option likely allows them the quickest recovery at their primary site?
A. Warm site
B. Hot site
C. Mobile site
D. Cold site
- Henrietta is concerned about the possibility that an attacker will obtain a copy of her password file and conduct a rainbow table attack against it. What technique can she use to best prevent this type of attack?
A. Salting
B. Hashing
C. Password complexity requirements
D. Encryption
- Flora is conducting a penetration test of a client and wishes to gain physical access to the building during daylight hours. Which one of the following techniques is least likely to arouse suspicion?
A. Pretexting
B. Lock picking
C. Tailgating
D. Climbing in an open window
- Andrea was investigating the IP address(es) associated with a domain name and obtained the results shown in the following screenshot. What tool did she use to obtain these results?
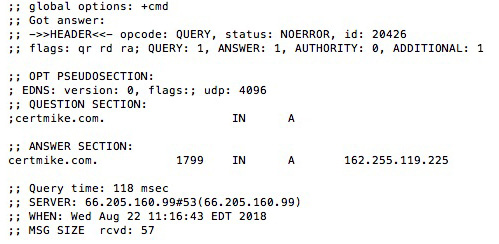
Figure 8.17
A. dig
B. nslookup
C. dnsquery
D. resolve
- Which one of the following objects, if successfully stolen, would be most useful in a session hijacking attack?
A. IP address
B. Public key
C. Digital certificate
D. Cookie
- Dan recently received a digitally signed message and when he attempted to verify the digital signature received an error that the hash values did not match. What can Dan conclude from this error?
A. The message was accidentally corrupted in transit.
B. The message was altered by a malicious individual after being sent.
C. Dan can't draw one of these specific conclusions.
D. There was an error creating the digital signature.
- Which one of the following technologies can be used to mitigate the effects of a denial-of-service attack on a local area network?
A. Flood guard
B. Loop prevention
C. Split horizon
D. Hold-down timers
- Melanie is the system administrator for a database containing sensitive information. She is responsible for implementing security controls to protect the contents of the database. Which term best describes her role?
A. Data owner
B. Data steward
C. Data user
D. Data custodian
- Greg visits a website and sees the error shown in the following screenshot. What is the most likely cause of this error message?

Figure 8.18
A. The certificate uses an insecure cipher, such as DES.
B. The website is using a self-signed certificate.
C. The certificate is expired.
D. The certificate does not support TLS communication.
- Brendan is helping a colleague troubleshoot a connectivity issue for two systems using the Secure File Transfer Protocol (SFTP). He would like to check whether the traffic is being blocked by his network firewall. What TCP port is used for these connections?
A. 22
B. 21
C. 20
D. 23
- Ben finds that the DNS servers in his organization are configured to allow unrestricted recursive queries. What type of attack are these servers vulnerable to as a result of this configuration?
A. ARP poisoning
B. CDNS poisoning
C. DNS amplification
D. Man-in-the-middle
- In a Kerberos authentication scheme, who provides the client with the TGS session key?
A. Authentication server
B. Ticket granting server
C. Service server
D. Key generation server
- Ron would like to implement a security control that requires that employees protect the confidentiality of corporate information, even after they leave the organization. Which one of the following agreements would best meet his needs?
A. SLA
B. NDA
C. BPA
D. ICA
- Norma has held several positions in her company and is still able to carry out system actions that were granted to her based upon her previous roles. She no longer has a job-based requirement to perform those activities. What term describes what has happened here?
A. Privileged account
B. Least privilege
C. Privilege creep
D. Privilege migration
Questions 85-90 refer to the following scenario:
Melanie is conducting a quantitative risk assessment for her organization. She is specifically focusing on the risk of an earthquake damaging her Southern California data center. After consulting geologists, she estimates that her area is likely to experience a significant earthquake once every 50 years.
Melanie asked an architect to help her develop a replacement cost estimate for the facility and determined that the cost is $5 million. She also consulted a structural engineer who estimated that a typical earthquake would cause approximately $1 million in damage to the facility. An earthquake insurance policy would require payment of a $75,000 annual premium.
- What is the asset value in this scenario?
A. $20,000
B. $75,000
C. $1,000,000
D. $5,000,000
- What is the single loss expectancy in this scenario?
A. $20,000
B. $75,000
C. $1,000,000
D. $5,000,00
- What is the annualized rate of occurrence in this scenario?
A. 0.02
B. 0.05
C. 0.20
D. 0.50
- What is the exposure factor in this scenario?
A. 0.02
B. 0.05
C. 0.20
D. 0.50
- What is the annualized loss expectancy in this scenario?
A. $20,000
B. $75,000
C. $1,000,000
D. $5,000,000
- Which one of the following statements best describes the risk situation Melanie is in?
A. Melanie should recommend that the business always purchases insurance for any risk with an ALE greater than 0.005.
B. The purchase of insurance in this scenario is not cost-effective from a purely financial viewpoint.
C. The purchase of insurance in this scenario makes good financial sense.
D. Melanie should recommend against the purchase of insurance because the SLE is less than the AV.
Practice Exam 2 Answers and Explanations
- C. Ralph is conducting a privilege audit by ensuring that each permission assigned to a user account is backed by an approved access request. Usage auditing is a similar activity but it analyzes actual privilege usage, rather than privilege existence.
- C. Tom can use screen locking to prevent someone walking by from using a device that he or she is not authorized to use. Remote wiping is not an effective control for this scenario, as it would destroy all data on the device and is only effective when actively triggered. Geofencing is not an effective control because the device is located in the office where it is expected to be. Application control would limit the applications that users can install on the device but would not prevent an unauthorized user from accessing the device.
- B. The recovery time objective (RTO) is the amount of time that it is acceptable for a system to be down prior to recovery during a disaster. The recovery point objective (RPO) is the amount of acceptable data loss during a recovery effort. The RTO and RPO are targets, rather than measures of actual performance. The mean time between failures (MTBF) is the average amount of time that elapses between failures of a system or component. The mean time to repair (MTTR) is the amount of time that it takes to recover a failed system. The MTBF and MTTR are measures of actual performance.
- C. The recovery time objective (RTO) is the amount of time that it is acceptable for a system to be down prior to recovery during a disaster. The recovery point objective (RPO) is the amount of acceptable data loss during a recovery effort. The RTO and RPO are targets, rather than measures of actual performance. The mean time between failures (MTBF) is the average amount of time that elapses between failures of a system or component. The mean time to repair (MTTR) is the amount of time that it takes to recover a failed system. The MTBF and MTTR are measures of actual performance.
- D. The secure shell (SSH) functions in a manner that is functionally equivalent to telnet but adds encryption and other security features. SSL and TLS may be used to encrypt communications but they do not provide the connection features of SSH on their own. The file transfer protocol – secure (FTPS) is used for transferring files and does not allow interactive administrative sessions similar to the ones provided by telnet.
- A. The Data Encryption Standard (DES) is a weak algorithm that is no longer considered secure. The Triple DES (3DES) algorithm is a stronger variant of DES that is acceptable. The Advanced Encryption Standard (AES) and Rivest Shamir Adelman (RSA) algorithm are both considered secure.
- B. This is a reverse proxy because the proxy server is located on the same network as the web server. Users connect directly to the reverse proxy and the proxy server then connects to the web server. This process is transparent to the end user. It is not possible to determine whether this proxy server is performing caching and/or content filtering based upon this illustration.
- B. Network access control lists are examples of rule-based access control because the router will make decisions based upon the rules that Fred provides. The router does not know the identity of the user, so it cannot perform role-based or attribute-based access control. Users have no authority to delegate access control decisions, so this is not an example of discretionary access control.
- B. XYZ Cloud Services is allowing Sandy to provision servers on his own, as he needs them. This is an example of providing customers with the basic building blocks of a computing environment as a cloud service and, therefore, is an example of infrastructure as a service (IaaS).
- D. In a true positive report, the system reports an attack when an attack actually exists. A false positive report occurs when the system reports an attack that did not take place. A true negative report occurs when the system reports no attack and no attack took place. A false negative report occurs when the system does not report an attack that did take place.
- A. While it is possible to perform error handling with a variety of constructs, the most appropriate tool is the use of the try...catch construct. In this approach, developers include the code that might generate an error in the try clause and then provide error handling code in the catch clause.
- B. The EAP-TLS, EAP-TTLS, and EAP-FAST protocols all use transport layer security (TLS) to provide security for the EAP session. EAP-IKEv2 relied upon the Internet Key Exchange (IKE) protocol.
- C. The most likely culprit is an insider with access to the accounting system. There are no signs of IPS or firewall anomalies, which reduces the likelihood that this was an external attack.
- D. Carla has already completed the initial exploitation phase of the test. She is now attempting to expand her permissions on the compromised system. This is an example of escalation of privilege.
- C. Servers that provide services only to internal users should be placed on the intranet. DMZ servers provide services to the general public. Extranet servers may be accessed by vendors and other business partners. Guest networks are designed for visitors to a facility to gain internet access.
- B. Over-the-air (OTA) upgrades occur automatically and without user or administrator intervention, making them the best way to ensure that devices remain current. If Samantha wants to control when these updates occur, she can manage OTA updates through her mobile device management (MDM) platform. Manual installation or sideloading by users or administrators is not likely to keep devices consistently updated.
- A. Pulverizing materials reduces them to a fine dust, which may pose an inhalation hazard. Anyone working around pulverized materials should wear a respirator.
- C. ARP spoofing attacks occur by poisoning the MAC address table either on an individual host or on the switch used by the victim. In order for this attack to be successful, the attacker and victim must be attached to the same switch, although they do not need to be sharing the same switch port.
- C. The MD5 algorithm is cryptographically broken and should never be used for secure applications, such as creating a digital signature. It is still appropriate for use in non-cryptographic applications, such as identifying duplicate records, partitioning database keys, and verifying file checksums to detect unintentional corruption.
- A. This is an example of a preset lock, where a locksmith sets the lock to work with a specific key or keys. Cipher locks use a keypad that requires individuals to enter a code. Biometric locks use fingerprint readers or some other form of biometric identification, while smartcard locks require the user to insert a smartcard or place one in the immediate proximity of the lock.
- C. The Bcrypt algorithm relies upon the Blowfish cipher to perform key stretching of passwords.
- B. This is a brute force attack because the intruder seems to be generating possible passwords sequentially without using a dictionary or rainbow table. It is an online attack because the intruder is conducting the hacking attempt against the live service.
- B. Penetration tests interact with systems and seek to exploit vulnerabilities. Therefore, they are an active test of security controls. Configuration analysis, network monitoring, and intrusion detection are passive activities.
- A. Jailbreaking a mobile device breaks the user out of the controls imposed by the operating system developer, granting the user root privileges on the device. This is an example of privilege escalation. Sideloading is the process of loading information on a device via USB or another non-wireless mechanism. It is a capability included in devices by design and is not an example of privilege escalation. Man-in-the-middle attacks are used to eavesdrop on network connections and do not require privilege escalation. Tethering is an intended capability of mobile devices that allow users to connect other devices to the network through the mobile device's network connection.
- B. Amazon's Lambda service is a serverless computing platform offered to customers on a platform-as-a-service (PaaS) basis. Microsoft Azure Virtual Machines and Amazon EC2 are both virtual server environments that offer infrastructure-as-a-service (IaaS). Microsoft Azure DNS is also an infrastructure service offering for name resolution.
- A. Fuzzing uses artificially generated input to a program to test it for security purposes. Fuzzing executes the code, so it is an example of dynamic code analysis. Data flow analysis, lexical analysis, and taint analysis are all examples of static code-testing techniques.
- C. In a public cloud environment, providers offer services on the same shared computing platform to all customers. Customers do not necessarily have any relationship to, or knowledge of, each other. In a private cloud environment, an organization builds its own computing environment. In a hybrid cloud environment, an organization combines elements of public and private cloud computing. In a community cloud environment, a group of related organizations builds a shared cloud environment that is not open for general public use. Despite the fact that David is limiting access to these servers to his own organization, Microsoft Azure is still a public cloud computing environment.
- C. Aircrack is specifically designed to test the security of WiFi encryption keys and would be the ideal tool in this situation. NetStumbler is an outdated tool used to survey wireless networks but is no longer supported. Nmap is a network mapping tool and QualysGuard is a network vulnerability scanner, neither of which has a wireless encryption testing capability.
- B. The developer created a backdoor in the system by hardwiring credentials into the application that allowed later access. A logic bomb is set to automatically trigger when certain conditions are met, which is not the case in this scenario. A remote access Trojan (RAT) is a type of malware that establishes a backdoor but there is no indication that one was used in this case, as the engineer added the backdoor directly into the code. Ransomware is a form of cryptomalware that encrypts files and then demands payment of a ransom before restoring access. There is no indication of a ransomware attack in this scenario.
- B. The Simple Mail Transfer Protocol (SMTP) is used to relay inbound emails and should be allowed from the internet. The Internet Message Access Protocol (IMAP) and the Post Office Protocol version 3 (POP3) are used to retrieve messages from an email server and should only be allowed from the internal network.
- C. The RADIUS Access-Request message is sent by a client to the server requesting RADIUS authentication. The server then normally responds with an Access-Accept or Access-Reject message, depending upon whether the authentication was successful or unsuccessful. When a system is using two-factor authentication, the RADIUS server may respond to the client's request with an Access-Challenge message asking for additional authentication.
- A. The individual who set up this website registered a domain name that was extremely similar to a legitimate domain: arifrance.com instead of airfrance.com. This is an example of typosquatting (or URL hijacking), anattack that hopes to garner web traffic by having a name that is quite similar to that of a legitimate site. This is a different website than the legitimate site, so no defacement took place. In a clickjacking attack, the attacker seeks to fool individuals into clicking links on a website. In a session hijacking attack, the attacker attempts to interfere with ongoing communication between a client and web server.
- B. Router access control lists are only capable of performing stateless filtering, which does not take connection status into account. Other firewall technologies, including stateful inspection firewalls, next-generation firewalls, and proxy firewalls, all track connection state and typically require dedicated firewall hardware.
- C. The basic File Transfer Protocol (FTP) does not provide encryption for data in transit and exposes both transferred files and authentication credentials to eavesdropping attacks. The Secure File Transfer Protocol (SFTP) and File Transfer Protocol – Secure (FTPS) offer the same functionality over a secure, encrypted connection. The Secure Copy (SCP) protocol copies files over a secure SSH connection and is also a viable alternative to FTP.
- A. While it is possible that Tom scanned the wrong IP address or that these are false positive results, the most likely explanation is that the copy machine contains an embedded Windows operating system that is vulnerable to these issues. True negative reports occur when a scanner does not report an issue that does not exist; therefore, they would not appear in a scan report.
- C. Active/active mode is a perfectly acceptable way to operate two load balancers and the load balancers will take care of synchronization issues between themselves and the servers. The major risk with active/active mode is that if both load balancers run at greater than 50% capacity, a single load balancer will not be able to handle the full workload in the event that one device fails.
- B. Stream ciphers work on a single bit or byte of plaintext at a time, while block ciphers work on plaintext in chunks. AES and Blowfish are examples of block ciphers.
- D. This illustration shows the cipher feedback (CFB) mode of encryption. You can determine this by noting that in each encryption operation, the ciphertext from the previous operation is encrypted and then XORed with the plaintext block to produce the next ciphertext block.
- A. Nessus is a vulnerability scanner designed to scan systems over the network and identify potential vulnerabilities. Nmap performs a similar function but only identifies open ports on remote devices without probing for vulnerabilities. Jack the Ripper is a password cracking tool. Kismet is a wireless network assessment tool.
- C. In a bring-your-own-device (BYOD) model, employees are able to bring personally owned devices into a corporate computing environment. The other models listed all involve the use of corporate-owned equipment.
- A. Roger is installing a back door so that he can regain access to the system at a later date. This is an example of persistence. He will be able to use this back door to regain access even if the initial vulnerability that he exploited is patched.
- C. While it may be possible to mitigate this issue by adjusting the settings on any of the devices mentioned here, the root cause of a SQL injection vulnerability is faulty input validation in the application's source code. This root cause may only be addressed by modifying the application code.
- A. The proximity card provides the fastest scanning time, as the user simply needs to hold it near the reader. Smart cards and magnetic stripe cards require more time-consuming interaction with the reader. Photo ID cards require scrutiny by a human guard.
- A. In a pass-the-hash attack, the attacker must gain access to a hashed Windows account passwords. This is possible by gaining access to a Windows workstation where the target user logs into his or her domain account. Access to a domain controller is not necessary. Access to a network segment or public website is not sufficient because hashed passwords are not generally found in those locations in unencrypted form.
- D. The accuracy of a biometric authentication system is described using three metrics. The false acceptance rate (FAR) is the frequency at which the system admits a person who should not be admitted. The false rejection rate (FRR) is the frequency at which the system denies access to an authorized user incorrectly. The FAR can be improved by increasing the sensitivity of the system, while the FRR can be improved by decreasing the sensitivity of the system. Because of this, the best measure of accuracy is the crossover error rate (CER), which is the sensitivity point at which the FAR and FRR are equal.
- B. Development environments are designed for active use by developers who are creating new code. These environments are the only location where code should be modified. Once code is ready for testing, it is released from the development environment into a test environment for software testing. After the completion of user acceptance testing, the code is moved from the test environment into a staging environment where it is prepared for final deployment into the production environment. Developers should never have permission to move code themselves but should only be able to move code between environments through the use of a managed change control system.
- B. The Diffie-Hellman (DH) algorithm is a key exchange algorithm designed to facilitate the creation of a mutually shared secret.
- C. An Agile approach to software development embraces change and prioritizes feature requests by the value added to the deliverable. Customers are encouraged to engage throughout the process. Agile projects often begin without clearly defined requirements and requirements evolve as the project unfolds.
- B. This approach, redirecting users to a central authentication service, is an example of single sign-on (SSO), where a user authenticates once and may use that authenticated session to access a variety of services. While this authentication may be part of a federated environment, there is no indication of this and there is no description of the specific technologies used to support this SSO environment.
- B. The WPA-Enterprise and WPA2-Enterprise standards both rely upon an enterprise authentication server. Pre-shared key (PSK) mode uses a shared secret key. WPS is not a wireless encryption standard.
- C. The Federal Financial Institutions Examination Council (FFIEC) is responsible for overseeing the audits of financial institutions and produces a series of information security standards that apply to those institutions. The Federal Energy Regulatory Commission (FERC) produces security standards for the energy industry. The Food and Drug Administration (FDA) regulates healthcare products and food items, while the Federal Railroad Administration (FRA) regulates rail transportation.
- C. An intrusion detection system (IDS) has the ability to identify suspicious network traffic but cannot take any preventive action to block the traffic. Therefore, it is best classified as a detective control.
- B. Recent attacks against WPS have rendered it insecure and made it unsuitable for use. Xavier should discontinue the use of WPS and switch to a more secure authentication and access control technology.
- C. Most embezzlement attacks are waged either entirely by insiders or with significant support from an insider with access to the organization's financial systems and accounts.
- C. The two main technologies used to generate one-time passwords are the HMAC-Based One Time Password (HOTP) algorithm and the Time-Based One Time Password (TOTP) algorithm. HOTP passcodes are generated sequentially and do not expire until use. TOTP passcodes are based upon the time of authentication and expire frequently. This hardware token requires that the user press a button to generate a passcode sequentially, rather than generating them continuously. Therefore, it is an HOTP token.
- B. Generic, shared, and guest accounts should not be used on secure servers due to their lack of accountability to an individual user. Service accounts normally exist on all servers and are required for routine operation of services.
- B. This image shows the Galois/Counter Mode (GCM) cipher mode of operation. The distinguishing feature of this approach is that block numbers are generated by a counter and those numbers are combined with an initialization vector using a block cipher.
- A. While this bag may be used to perform all of the functions listed in the question, the primary purpose of this bag is to serve as a portable Faraday cage that prevents electromagnetic signals from reaching the device. This allows the forensic analysts to leave the device powered on without worrying that someone will remote wipe the device. Powering the device off may lose critical evidence stored in memory.
- C. The standard access mechanism for Gmail accounts is to use a web browser over a secure connection. This traffic occurs using the HTTPS protocol. While it is possible to access Gmail through the SMTP, IMAP, and POP3 protocols, the basic version of those protocols are not secure and do not use the standard web interface. There are secure, encrypted alternatives to SMTP, IMAP, and POP3, but those still do not use the Gmail web interface.
- B. RAID 1, also known as disk mirroring, writes identical data to two disks. This approach allows read operations to recover all data by accessing a single disk and is quite efficient for that use. RAID 3 and RAID 5 stripe data across multiple disks and incur overhead in reassembling information that reduces read performance. RAID 0 does not provide redundancy, as it simply stripes data across multiple disks without parity information.
- C. In this attack, Mal is obtaining Alice's hashed password by sniffing the network connection. He then reuses the hashed password to log in to the service. This is an example of a replay attack.
- C. NTLM and NTLM v2 both contain critical security vulnerabilities that make them poor choices for authentication protocols. They use the MD4 and MD5 hash algorithms. While NTLM is most commonly found on Windows systems, there are NTLM implementations for Linux systems as well.
- C. The purpose of a CA signing a certificate is to prove that the CA was involved in the certificate's creation. The CA uses its own private key to create the digital signature and then other users may verify the signature using the CA's public key.
- C. Facial recognition and fingerprint-based authentication both use acceptably strong biometric authentication techniques. The remaining two options, passwords and PINs, both use knowledge-based authentication. Passwords allow users to select from a wider range of characters than PINs, which only allow the use of digits. Therefore, PINs provide the weakest level of security of all of these techniques.
- A. The three "r" values in this permission string indicate that the file's owner can read the file, members of the file's group can read the file, and all system users can read the file. Therefore, anyone on the system has permission to read this file.
- C. Watering hole attacks take advantage of the fact that many people are predictable in their web surfing patterns. They place malicious content at a site likely to attract the target audience (the watering hole) and then wait for a compromise to occur.
- B. This is an internal application, so the use of a self-signed certificate is likely appropriate. However, this certificate issued for an incorrect domain name and, therefore, should be replaced. Using a certificate from the same self-signing source will minimize costs compared to the use of a third-party CA. There is no sign in this report that the certificate does not support strong encryption.
- C. The false acceptance rate (FAR) of a system is calculated by dividing the number of false acceptances by the total number of authentication attempts. In this dataset, there are 200 total authentication attempts, of which 16 were false acceptances of an unauthorized user. Therefore, the false acceptance rate is 8%.
- B. This certificate was issued by an intermediate CA known as the InCommon RSA Server CA. This intermediate CA was certified by the USERTrust RSA Certification Authority root CA.
- D. Hashing would allow Frank to create a unique value from each SSN that would still uniquely identify each record but would not be reversible by anyone. Encryption would also protect the data but could be reversed by someone with the decryption key. Steganography is used to hide data within images.
- C. Cold sites have only basic infrastructure available and require the longest period of time to activate operations. They are also the cheapest option. Warm sites add hardware, and possibly software, to the mix but do not have a current copy of the data running. They require hours to activate. Hot sites are up and running at all times and can assume operations at a moment's notice. They are the most expensive option. Mobile sites are transportable on trailers and are a good choice for a last-minute recovery plan. They would work well in this scenario because Roger could bring a mobile site to their primary facility and use it to recover operations during the restoration effort at the primary site.
- A. While all of these techniques will help reduce the likelihood of a password cracking attack, the best defense against rainbow tables is to implement salting. Rainbow table attacks precompute hashes and then check the password file for those values. Salting adds a value (the salt) to each password prior to hashing to make rainbow table attacks no more effective than a brute force attack.
- C. During a tailgating attack, the attacker simply blends in with a crowd of people entering a facility and hopes they will hold the door open for him or her. This is the least likely way to arouse suspicion during daylight hours when the office is occupied. Lockpicking, pretexting, and climbing in a window are all likely to attract unwanted attention.
- A. Both the dig and nslookup tools are useful when seeking to determine the IP address(es) associated with a domain name. However, the results shown in the figure are formatted as output from the dig tool. Dnsquery and resolve are not domain lookup tools.
- D. If an eavesdropper gains access to the cookie used to authenticate a session, the attacker could use that cookie to take over the session. Public encryption keys, digital certificates, and IP addresses are all commonly shared publicly and would not be very useful in a session hijacking attack.
- C. Any one of these scenarios is a plausible reason that the digital signature would not verify. Dan cannot draw a specific conclusion other than that the message he received is not the message that was sent by the originator.
- A. Flood guard prevents a single device from flooding the network with traffic, which may cause a denial of service. Loop prevention, hold-down timers, and split horizon routing are all used to detect and correct routing loops.
- D. System administrators are examples of data custodians: individuals who are charged with the safekeeping of information under the guidance of the data owner.
- B. This error message indicates that the certificate was not issued by a trusted certificate authority. This error most often occurs when a certificate was self-issued.
- A. The SFTP protocol uses SSH connections to transfer files securely. Therefore, it works over the same port used by SSH, TCP port 22. Ports 20 and 21 are used for traditional FTP connections and would not apply here. Port 23 is used by the insecure Telnet protocol.
- C. In a DNS amplification attack, the attacker sends short queries to servers that allow unrestricted recursive queries. Those queries include forged source addresses, causing the third-party DNS servers to unwittingly flood the victim system with lengthy and unsolicited DNS responses.
- A. When a Kerberos client requests a session key, the client creates an authenticator consisting of the client's ID and a timestamp. The client then encrypts this authenticator with the TGS session key, which the client obtained earlier from the authentication server.
- B. A non-disclosure agreement (NDA) is a confidentiality agreement between two organizations or between an individual and an organization. NDAs are commonly used to enforce employee confidentiality and typically remain in effect after the end of an employment relationship.
- C. Privilege creep is the term used to describe the situation where a user moves through various job roles and accumulates permissions over time without having unnecessary permissions revoked. Privilege creep is a violation of the principle of least privilege.
- D. The asset value (AV) is the full value of the facility. In this scenario, Melanie consulted with an architect and determined that the facility value is $5 million using the replacement cost method.
- C. The single loss expectancy (SLE) is the amount of damage, in dollars, that the organization should expect as the result of a single incident. From the scenario, we know that a single earthquake would cause approximately $1 million in damage.
- A. The annualized rate of occurrence is the number of events expected in a given year. Geologists expect an earthquake once every 50 years. This is equivalent to a 0.02 annual risk of an earthquake.
- C. The exposure factor is calculated by dividing the single loss expectancy ($1,000,000) by the asset value ($5,000,000), resulting in a value of 0.20, or 20%.
- A. The annualized loss expectancy is the amount of damage expected to occur in any given year. It is computed by multiplying the single loss expectancy by the annualized rate of occurrence (or ALE=SLE*ARO). In this scenario, that is ALE=$1 million * 0.02 or $20,000.
- B. The purchase of an insurance policy is never purely a financial decision; however, in this case, it does not make good financial sense because the annualized loss expectancy ($20,000) is less than the policy premium cost ($75,000). Tonya should not use the ALE or SLE alone to make this decision and must do so in the context of the control costs and other business factors.
