Practice Exam 1 Questions
- After running a vulnerability scan on a server containing sensitive information, Mitch discovers the results shown here. What should be Mitch's highest priority?

A. Modifying encryption settings
B. Disabling the guest account
C. Disabling cached logins
D. Patching and updating software
- Gary is configuring a wireless access point that supports the WPS service. What risk exists in all implementations of WPS that he should consider?
A. Weak encryption
B. Physical access to the device
C. An offline brute force attack
D. Impossible to disable WPS
- Alan is a software developer working on a new security patch for one of his organization's products. What environment should he use when actively working on the code?
A. Production
B. Test
C. Development
D. Staging
- Bill suspects that an attacker is exploiting a zero-day vulnerability against his organization. Which one of the following attacker types is most likely to engage in this type of activity?
A. Hacktivist
B. Script kiddie
C. APT
D. White hat
- Ryan works for a firm that has a limited budget and he would like to purchase a single device that performs firewall, intrusion prevention, and content filtering functions. Which one of the following product categories is most likely to meet his needs?
A. SIEM
B. UTM
C. DLP
D. NAC
- Cole is testing a software application that must be able to handle the load of 10,000 simultaneous users each time a new product goes on sale. Which one of the following software testing techniques will best help Cole determine whether the environment will meet this requirement?
A. Fuzz testing
B. Regression testing
C. Static analysis
D. Stress testing
- Jacob's company recently implemented a new technique for securing remote access for users of BYOD mobile devices. In this approach, the user opens an application that then allows the user to connect to corporate systems. No corporate data is available outside the application. What term best describes this approach?
A. Sideloading
B. Storage segmentation
C. Full device encryption
D. Containerization
- Consider the Linux filesystem directory listing shown here. Robert has the user account "rsmith" and would like to access the secret_file.txt file. Robert is a member of the "leaders" group. What permission does Robert have for this file?

Figure 7.2
A. Robert can only read the file.
B. Robert can read and execute the file.
C. Robert can read and write the file.
D. Robert can read, write, and execute the file.
- This diagram shows the results of testing the accuracy of a biometric authentication system. In this diagram, what characteristic is designated by the arrow?

Figure 7.3
A. IRR
B. FRR
C. CER
D. FAR
- Henry would like to use a secure protocol to obtain a graphical user interface on a Windows system that he manages remotely. Which one of the following protocols would best meet his needs?
A. VPN
B. SSH
C. Telnet
D. RDP
- Rudy is configuring a router that sits at the connection between his organization's network and the internet. He is concerned about spoofed packets and would like to configure the router to perform anti-spoofing filtering. Which one of the following source IP addresses should be blocked at the router for inbound traffic?
A. 129.168.1.100
B. 12.168.1.100
C. 278.168.1.100
D. 192.168.1.100
- Julian is attempting to correlate information from the security logs of several different systems and notices that the clocks on those systems are not synchronized, making it difficult to compare log entries. Which one of the following services can best help Julian synchronize clocks?
A. LDAP
B. SMNP
C. NTP
D. RTP
- Jena is looking for a permanently situated disaster recovery option that best balances cost and recovery time. Which one of the following options should she consider?
A. Cold site
B. Warm site
C. Hot site
D. Mobile site
- Roger found the following image on a website that he administers. What type of attacker likely performed this defacement?

Figure 7.4
A. APT
B. A hacktivist
C. A nation-state
D. Organized criminals
- Frank is implementing a new VPN that will carry communications between his organization's offices around the world. His primary requirement is that the network must be able to withstand outages without disrupting communications. What term best describes Frank's requirement?
A. High latency
B. Low resiliency
C. Low latency
D. High resiliency
- Allen is building a cloud computing environment that will provide on-demand services to other administrators within his organization. What type of cloud environment is Allen creating?
A. A public cloud
B. A private cloud
C. A hybrid cloud
D. A community cloud
- Tom would like to conduct a security assessment that provides an accurate evaluation of the likelihood of an attacker gaining access to systems on his network. Which one of the following assessment tools would best meet Tom's goal?
A. A code review
B. A vulnerability scan
C. A penetration test
D. A risk assessment
- Roger is responsible for implementing a set of data quality guidelines and ensuring that they are being carried out on a day-to-day basis. Which one of the following best describes Roger's role in data governance?
A. Data custodian
B. Data owner
C. Data steward
D. Data user
- Consider the US government personal identity verification (PIV) card shown here. When the cardholder wishes to provide non-repudiation for a message, which certificate is used?

Figure 7.5
A. A PIV authentication certificate
B. An encryption certificate
C. A card authentication certificate
D. A digital signature certificate
- Which mode of cipher operation is shown here?

Figure 7.6
A. CFB
B. ECB
C. OFB
D. CBC
- Which one of the following is the most likely motivation for an attack waged by a criminal organization?
A. Financial
B. Political
C. Thrill
D. Grudge
- Ryan is configuring his organization's network firewall to allow access from the internet to the web server located in the DMZ. He would like to configure firewall rules to ensure that all access to the web server takes place over encrypted connections. What rules should he configure regarding traffic from the internet to the web server?

Figure 7.7
A. Allow both TCP ports 80 and 443
B. Allow TCP port 443 and block TCP port 80
C. Block both TCP ports 80 and 443
D. Allow TCP port 80 and block TCP port 443
- Which one of the following algorithms was approved by the US federal government for use in creating digital signatures under the Digital Signature Standard (DSS)?
A. RSA
B. DSA
C. AES
D. 3DES
- Susan is conducting a business impact analysis for her organization as part of the organization's business continuity planning initiative. During that analysis, she identifies the amount of data loss that it would be acceptable to incur while recovering a system during a disaster. What metric should she use to capture this information?
A. RPO
B. RTO
C. MTTR
D. CMTBF
- Paul is evaluating the performance of his organization's business continuity efforts and measures the amount of time that it takes to restore service when a critical router fails. What metric should Paul use to capture this information?
A. MTBF
B. MTTR
C. RTO
D. RPO
- Karl would like to take advantage of mobile devices to implement a second authentication factor for his organization's ERP system. Which one of the following approaches typically has the highest user satisfaction rate?
A. Email notifications
B. SMS notifications
C. Push notifications
D. An app-based passcode generator
- During a vulnerability scan, Bill discovers that a system running on his network has an outdated version of Linux. The system is a network appliance, and Bill can only access it through the appliance's GUI. What should Bill do next?
A. Upgrade the operating system by downloading the source files for a current version of Linux.
B. Obtain an update from the appliance manufacturer.
C. Use the yum or apt-get commands to upgrade the operating system.
D. No action is necessary.
- When performing encryption using the Triple DES algorithm, how many different keys are required to use the most secure mode of operation?
A. 1
B. 2
C. 3
D. 4
- Alison is troubleshooting a connectivity issue where the database server is unable to access a file stored on the file server. She verified that the filesystem permissions are correct. She suspects a firewall issue and examines the network diagram shown here. What is the best place for her to investigate next?

Figure 7.8
A. The web server host firewall
B. The database server host firewall
C. The hardware firewall
D. The file server host firewall
- Flo is the administrator for a server that is using RAID 5 with a six-disk array. In this approach, what is the maximum number of disks that can fail without permanent loss of data?
A. 1
B. 2
C. 3
D. 4
- April recently selected a high-quality safe that is rated as requiring at least 30 minutes for a skilled intruder to open it with appropriate tools. She selected this over a lesser-quality safe that did not provide a guaranteed rating. What type of control is this upgraded safe?
A. Corrective
B. Detective
C. Preventive
D. Compensating
- Eric would like to select a key stretching algorithm that is protected against attack by requiring a brute force attacker to use both extensive memory and CPU resources. Which one of the following algorithms would be most appropriate?
A. RIPEMD
B. PBKDF2
C. HMAC
D. Bcrypt
- When a filesystem consults an access control list (ACL), what phase of the AAA process is occurring?
A. Authentication
B. Identification
C. Authorization
D. Accounting
- Maureen is conducting a penetration attack against a website and she has gained access to a hashed password file from the site. The site does not have a strong password policy. Which one of the following techniques would be the most effective way for Maureen to exploit this file?
A. A rainbow table attack
B. A dictionary attack
C. An offline brute force attack
D. An online brute force attack
- What mode of encryption is shown here?

Figure 7.9
A. OFB
B. CFB
C. CBC
D. ECB
- Which one of the following key lengths is not supported by the AES encryption algorithm?
A. 128 bits
B. 192 bits
C. 256 bits
D. 512 bits
- Fran would like to prevent users in her organization from downloading apps from third-party app stores. Which one of the following mobile device categories provides the strongest controls against the use of third-party app stores?
A. Apple iPhone
B. Samsung Galaxy
C. Motorola Moto
D. Huawei P-series
- Consider the load-balanced servers shown in the following diagram. The load balancer is using affinity scheduling and receives a request from a client who already has an active session on Server B. Which server will receive the new request from that client?

Figure 7.10
A. Server A
B. Server B
C. Server C
D. Server D
- Lynn would like to adjust her organization's password policy to be in line with current standards published by NIST. How often should she set user passwords to expire?
A. Every 180 days
B. Every 30 days
C. Every 90 days
D. Never
- Peter is conducting a penetration test of his own organization. He has completed his reconnaissance work and is now attempting to gain access to a system with internet exposure. What phase of the test is Peter in?
A. Pivot
B. Initial exploitation
C. Escalation of privilege
D. Persistence
- Given the network diagram shown here, what is the most appropriate location to place the correlation engine for a SIEM?
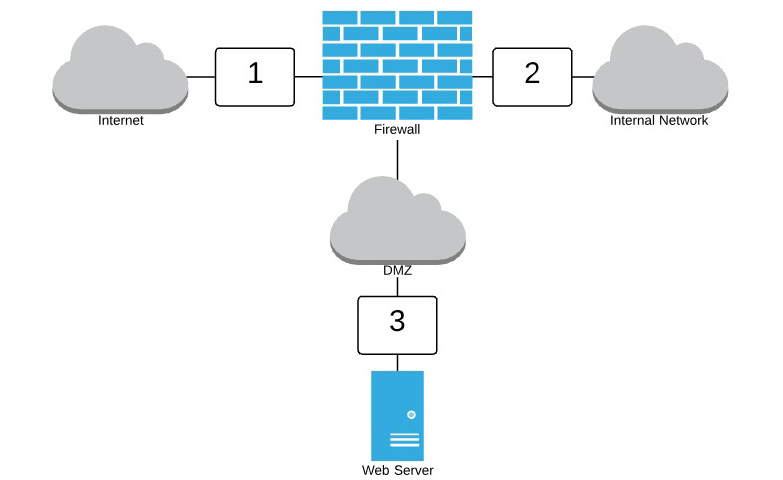
Figure 7.11
A. Location 1
B. Location 2
C. Location 3
D. None of the above
- Marty is designing a new access control system for his organization. He created groups for each type of user: engineers, managers, designers, marketers, and sales. Each of these groups has different access permissions. What type of access control scheme is Marty using?
A. Role-based access control
B. Rule-based access control
C. Discretionary access control
D. Mandatory access control
- Tina is concerned that an intruder who gains access to a facility may disconnect an existing network device from the wired network and use the jack to connect a malicious device. What switch security feature would prevent this type of attack?
A. Port security
B. Flood guard
C. Loop protection
D. Traffic encryption
- Solve the exclusive or (XOR) operation shown here:

Figure 7.12
A. 1101
B. 0110
C. 1001
D. 0010
- Which one of the following security tasks would benefit the least from introducing automation?
A. Password resets
B. Firewall log analysis
C. Risk assessments
D. Configuration management
- Which one of the following mobile device deployment models allows employees to select the device they would like to use from a list of approved corporate-owned models?
A. BYOD
B. COPE
C. CYOD
D. Corporate-owned
- Glenn is designing the network security controls around a crucial system that controls the functioning of a manufacturing process. He would like to apply the strongest degree of network segmentation possible. Which one of the following controls would best achieve his objective?
A. VLAN segmentation
B. Air gap
C. Firewall zone segmentation
D. Router segmentation
- Gary is conducting a penetration test and obtains a copy of the password file for a web service. He creates a list of common passwords and uses it to try to break passwords in the file. What type of attack is Gary waging?
A. Offline brute force
B. Online brute force
C. Rainbow table
D. Dictionary
- Tom is investigating an application that slowly consumes the memory on a server until it is using all of the available resources, at which time the system hangs. After a reboot, the application uses a minimal amount of memory, but that memory consumption again grows until the next crash. What is the most likely cause of this issue?
A. Pointer dereference
B. Buffer overflow
C. Integer overflow
D. Memory leak
- Which one of the following authentication mechanisms is generally not used in smartphone devices?
A. Fingerprint scanning
B. Facial recognition
C. Passcode
D. Retinal scanning
- Laura is implementing DNSSEC to add security to her organization's Domain Name Service (DNS) infrastructure. What cipher suite must she support to ensure compatibility with other DNSSEC servers?
A. RSA/SHA-512
B. RSA/MD5
C. RSA/SHA-256
D. RSA/SHA-1
- Which one of the following attack types does NOT usually depend upon a design flaw in a web application?
A. XSRF
B. Shimming
C. XSS
D. SQL injection
- What attribute of a digital certificate indicates the specific purpose for which the certificate may be used?
A. The private key
B. The serial number
C. The public key
D. OID
- Gina's organization uses a minification function to process their JavaScript code. This results in code that uses generic variable names, no comments, and minimal spacing, such as the code shown here. What term best describes what has happened to this code from a security perspective?

Figure 7.13
A. Encryption
B. Obfuscation
C. Hashing
D. Masking
- What type of security control is shown here?
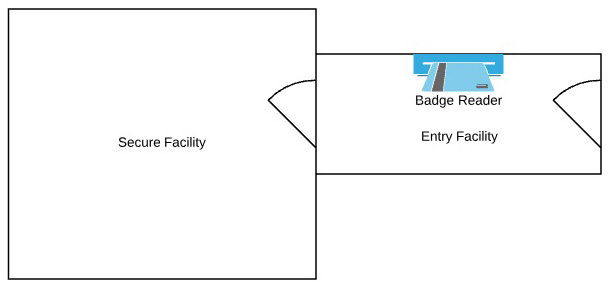
Figure 7.14
A. Mantrap
B. Faraday cage
C. Bollard
D. Fence
- What cryptographic technique does WPA use to overcome the weaknesses in the WEP algorithm?
A. TKIP
B. CCMP
C. Hashing
D. AES
- Yvonne is investigating an attack where a user visited a malicious website and the website sent an instruction that caused the browser to access the user's bank website and initiate a money transfer. The user was logged into the bank website in a different browser tab. What type of attack most likely took place?
A. Stored XSS
B. XSRF
C. Reflected XSS
D. DOM XSS
- Brianne is concerned that the logs generated by different devices on her network have inaccurate timestamps generated by the differing internal clocks of each device. What protocol can best assist her with remediating this situation?
A. NTP
B. TLS
C. SSH
D. OSCP
- Tina is investigating a security incident on a system in her organization. The user reports that he can't access any files on the device and he sees the warning message shown here. What type of attack has taken place?
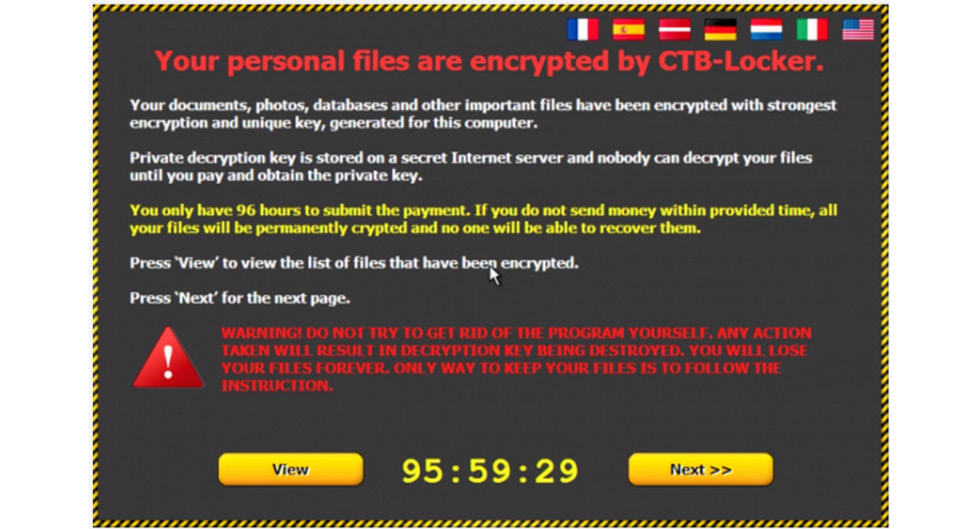
Figure 7.15
A. Keylogger
B. Spyware
C. RAT
D. Ransomware
- Which one of the following systems would be most likely to detect a distributed denial-of-service attack that attempts to perform SYN flooding from across the internet to a web server on an organization's DMZ network?
A. Heuristic NIDS
B. Heuristic HIDS
C. Signature NIDS
D. Behavioral NIDS
- Mandy works for an organization that is planning an expansion into Italy and France over the next 2 years. What privacy regulation will apply to her company's operation in those countries?
A. HIPAA
B. DPD
C. GDPR
D. GLBA
- During a vulnerability assessment, Sonia discovered the issue shown here in a web server used by her organization. What is likely to be the most effective method for resolving this issue?

Figure 7.16
A. Patching Apache Tomcat
B. Patching the operating system
C. Deploying a web application firewall
D. Deploying a content filter
- Paul is conducting a penetration test and has gained a foothold on a web server used by the target organization. He is now attempting to use that web server to gain access to a file server on the organization's internal network. What stage of the penetration testing process is Paul in?
A. Reconnaissance
B. Initial exploitation
C. Pivot
D. Scoping
- Lynn examines the userPassword attribute for a variety of users of the OpenLDAP system and sees the results shown here. How are these passwords stored?
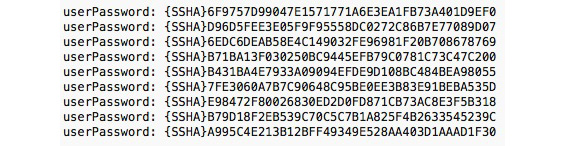
Figure 7.17
A. In unsalted form
B. In hashed form
C. In encrypted form
D. In cleartext form
- What biometric authentication technology could be used on the image shown here?

Figure 7.18
A. Facial recognition
B. Iris recognition
C. Retinal recognition
D. Fingerprint recognition
- Roland's company requires supervisors to approve payment requests entered by accounting clerks when the total amount of the payment is over $10,000. What type of control is this?
A. Least privilege
B. Separation of duties
C. Two-person control
D. Job rotation
- During a recent penetration test, the attacker dressed up in a security guard uniform identical to those used by a firm and began directing people to vacate the data center due to a security threat. What principle of social engineering BEST describes this technique?
A. Authority
B. Intimidation
C. Consensus
D. Scarcity
- Vic is the security administrator for a field engineering team that must make connections back to the home office. Engineers also must be able to simultaneously connect to systems on their customer's networks to perform troubleshooting. Vic would like to ensure that connections to the home office use a VPN. What type of VPN would best meet his needs?
A. Full tunnel
B. Split tunnel
C. TLS
D. IPsec
- What type of hypervisor is shown in the diagram?

Figure 7.19
A. Type 1 Hypervisor
B. Type 2 Hypervisor
C. Type 3 hypervisor
D. Type 4 hypervisor
Questions 70 through 73 refer to the following scenario:
Kyle is conducting a business impact assessment for his organization. As a result of his work, he identifies a single point of failure in his network, caused by an expensive network firewall that protects a big data storage environment. The organization chooses not to make the firewall redundant. Kyle estimates that the firewall will fail once every 4 years and that it will take 3 days to obtain and install a replacement if it does fail.
Kyle explains this disruption to business leaders and determines that the business cannot tolerate an outage of more than 4 hours. If there were an outage, the organization must be able to restore all of the data contained in the environment to the state it was in, at most, 1 hour prior to the failure.
- What is the MTTR in this scenario?
A. 1 hour
B. 4 hours
C. 3 days
D. 4 years
- What is the MTBF in this scenario?
A. 1 hour
B. 4 hours
C. 3 days
D. 4 years
- What is the RTO in this scenario?
A. 1 hour
B. 4 hours
C. 3 days
D. 4 years
- What is the RPO in this scenario?
A. 1 hour
B. 4 hours
C. 3 days
D. 4 years
- Consider the transitive domain relationships shown here. Joe has a user account in Domain D. Which one of the following statements is incorrect?

Figure 7.20
A. Joe can use his account in Domain A.
B. Joe can use his account in Domain B.
C. Joe can use his account in Domain C.
D. Joe can use his account in Domain D.
- Molly's organization has a shared account that they use to provide access to vendors. What is the primary security objective that is sacrificed using this model, assuming that the password is not shared with unauthorized individuals?
A. Least privilege
B. Accountability
C. Confidentiality
D. Integrity
- Donna is looking for a secure way to transfer files between systems. The systems in question are already configured for SSH connections. What file transfer method could she use that would leverage the SSH protocol?
A. SFTP
B. FTPS
C. Dropbox
D. HTTPS
- Kristen's organization recently entered into a business partnership with a new shipping vendor. She is placing a server on the network that will facilitate shipping transactions and must be accessed by both the vendor and internal users. Which network zone is the most appropriate placement for this server?
A. The guest network
B. The intranet
C. DMZ
D. The extranet
- Tonya is analyzing host firewall logs in an effort to diagnose a service that is not responding to user requests. She finds entries in the host firewall logs indicating that the traffic was allowed. What is the most likely cause of the service not responding?
A. Application failure
B. Host firewall misconfiguration
C. Network IPS misconfiguration
D. Network firewall misconfiguration
- Which one of the following security controls would be the least effective at detecting fraud committed by an employee?
A. Separation of duties
B. Job rotation
C. Mandatory vacation
D. Privileged access monitoring
- Brian is the physical security official for a data center hosting organization. While entering the building this morning, he noticed that one employee used his badge to enter the building and then held the door open for two other employees. Which one of the following situations occurred?
A. Piggybacking
B. Dumpster diving
C. Shoulder surfing
D. Impersonation
- Consider the statistics shown here for a biometric authentication system. What is the system's FRR based upon this data?

Figure 7.21
A. 2%
B. 4%
C. 5%
D. 10%
- Carl is selecting a data loss prevention (DLP) system for use in his organization. He would like to choose an approach that requires the least maintenance effort from his team. Which solution would best meet Carl's needs?
A. Host-based DLP
B. Network-based DLP
C. Cloud-based DLP
D. Signature-based DLP
- Ryan would like to restrict the use of a sensitive mobile application so that users may only use it when they are located in a building on his company's corporate campus. Which one of the following technologies can he use to best enforce this restriction?
A. Application control
B. Geofencing
C. Remote wiping
D. Containerization
- Val is conducting a black-box penetration test on a website and would like to try to gain access to a user account. If she has not yet gained access to any systems on the target network, which one of the following attacks would be most effective?
A. Rainbow table
B. Offline brute force
C. Offline dictionary
D. Online brute force
- Gayle is logging onto a website managed by a third-party vendor using credentials provided by her employer. The authentication system uses SAML-based authentication. In this scenario, who is the identity provider?
A. Gayle's web browser
B. The vendor
C. Gayle's employer
D. The certificate authority
- Corwin is beginning a penetration test and is reviewing the technical documentation provided by management that explains how the systems are designed and laid out. What type of test is Corwin most likely performing?
A. Red box
B. Grey box
C. White box
D. Black box
- Sandra would like to prevent users of her organization's mobile devices from using those devices to connect laptops and other systems to the network. What feature of mobile devices should she disable through her mobile device management platform?
A. Split tunneling
B. Tethering
C. Split horizon DNS
D. TLS
Questions 88 through 90 refer to the following scenario.
Gavin is considering different options for backing up the file server used by his organization. This server exhibits the normal usage patterns of an office file server. The four strategies he is considering are shown here:

Figure 7.22
- If Gavin's primary concern is conserving disk space, which option should he choose?
A. Option A
B. Option B
C. Option C
D. Option D
- If Gavin's primary concern is the speed of recovering the system after a failure, which option should he choose?
A. Option A
B. Option B
C. Option C
D. Option D
- If Gavin's primary concern is the amount of time required to perform the backups, which option should he choose?
A. Option A
B. Option B
C. Option C
D. Option D
Practice Exam 1 Answers and Explanations
- D. In this scenario, there are several critical vulnerabilities that all relate to the system running unsupported or unpatched components. While the other issues presented in this question do also appear in the scan results, updating this software and applying necessary security patches would result in the greatest risk reduction and should be Mitch's highest priority.
- B. Several vulnerabilities exist in different implementations of WPS. Some allow an offline brute force attack known as Pixie Dust. Others may make it impossible for device administrators to disable WPS. Others may use weak encryption. The risk that applies to all WPS devices is the risk of physical access. If an attacker gains physical access to the device, they can join the network.
- C. Development environments are designed for active use by developers who are creating new code. These environments are the only location where code should be modified. Once code is ready for testing, it is released from the development environment into a test environment for software testing. After the completion of user acceptance testing, the code is moved from the test environment into a staging environment, where it is prepared for final deployment into the production environment. Developers should never have permission to move code themselves but should only be able to move code between environments through the use of a managed change control system.
- C. While it is possible that any type of attacker might engage in a zero-day attack, it is most likely to find these vulnerabilities exploited by an advanced persistent threat (APT). APT attackers are more likely to have the technical resources to discover and use zero-day vulnerabilities.
- B. Unified threat management (UTM) solutions combine the features of many different security technologies into a single, cost-effective platform. They are most appropriate for use in small businesses, as they typically are not capable of high-performance activities.
- D. Stress testing, otherwise known as load testing, is a technique designed to determine the maximum capacity of an application. Cole can use stress testing to evaluate the performance of the application environment under the pressure of 10,000 simultaneous users. Static analysis, regression testing, and fuzz testing all test applications but are not able to determine an application's performance under load.
- D. Containerization approaches embed all access to corporate systems with a secure application container. No data from inside the container is accessible from other applications on the device. The entire container is controlled by the organization's mobile device management solution. Storage segmentation is a similar solution that provides separate storage for different data classifications but this approach goes beyond storage segmentation. Sideloading is a technique for loading applications and data onto a device outside of normal channels. Full device encryption provides encrypted storage for all data on a device but does not differentiate between corporate and personal data.
- A. Robert is not the file's owner, nor is he a member of the file's group. Therefore, the permissions that he has are those that apply to all users. In a Linux permission string, the first character indicates whether an object is a directory or not. The next three characters indicate the permissions assigned to the file's owner. The three characters after that assign permissions to members of the file's group. The next three characters indicate the all users permissions. The all users permissions for this file are 'r--'. Therefore, Robert can read the file but cannot write to it or execute it.
- D. The accuracy of a biometric authentication system is described using three metrics. The false acceptance rate (FAR) is the frequency at which the system admits a person who should not be admitted. The false rejection rate (FRR) is the frequency at which the system denies access to an authorized user incorrectly. The FAR can be improved by increasing the sensitivity of the system, while the FRR can be improved by decreasing the sensitivity of the system. Because of this, the best measure of accuracy is the crossover error rate (CER), which is the sensitivity point at which the FAR and FRR are equal.
- D. The Remote Desktop Protocol (RDP) provides a secure graphical user interface connection to a remote Windows system and would meet Henry's needs out of the box. It may be possible to configure remote access via a secure shell (SSH) connection, but this would require an additional tool and configuration. A virtual private network (VPN) could provide a secure connection to the remote network but does not inherently offer a graphical interface to manage a system. Telnet is not a secure protocol.
- D. 12.168.1.100 and 129.168.1.100 are valid public IP addresses and should be permitted as inbound source addresses. 278.168.1.100 is not a valid IP address because the first octet is greater than 255. It does not need to be blocked because it is not possible. This leaves 192.168.1.100. This address is a private address and should never be seen as a source address on packets crossing an external network connection.
- C. The Network Time Protocol (NTP) is designed to synchronize clocks on systems and devices with a centralized source. The Simple Network Management Protocol (SNMP) is designed for the management of network devices and does not synchronize time across a variety of devices. The Lightweight Directory Access Protocol (LDAP) is a directory services protocol and does not perform time synchronization. The Real-Time Protocol (RTP) is an application protocol designed for videoconferencing and, despite the name, does not perform time synchronization.
- B. Cold sites have only basic infrastructure available and require the longest period of time to activate operations. They are also the cheapest option. Warm sites add hardware, and possibly software, to the mix but do not have a current copy of the data running. They require hours to activate. Hot sites are up and running at all times and can assume operations at a moment's notice. They are the most expensive option. Mobile sites are transportable on trailers and do provide a cost/benefit balance but they are not permanently situated like cold, hot, and warm sites.
- B. This is a classic example of a hacktivist attack where the attacker was motivated by an ideological agenda. There does not seem to be any financial motivation here, which would be the primary sign of organized criminal activity. The attack is also prominent and obvious, lacking the stealthy characteristics of an attack waged by a nation-state or other APT.
- D. Resiliency is the ability of a system to withstand potentially disruptive actions. In this scenario, Frank is seeking to design a VPN solution that exhibits high levels of resiliency.
- B. In a public cloud environment, providers offer services on the same shared computing platform to all customers. Customers do not necessarily have any relationship to, or knowledge of, each other. In a private cloud environment, an organization builds its own computing environment. In a hybrid cloud environment, an organization combines elements of public and private cloud computing. In a community cloud environment, a group of related organizations builds a shared cloud environment that is not open for general public use.
- C. Penetration tests take an attacker's perspective on the network and actually seek to bypass security controls and gain access to systems. This would be the best way for Tom to determine the likelihood of a successful attack.
- C. Data owners and data stewards both bear responsibility for data quality standards. However, day-to-day data quality issues are the domain of a data steward, while a data owner bears executive-level responsibility. Data custodians and users generally do not have overarching data quality responsibilities.
- D. PIVs contain four digital certificates. The card authentication certificate is used to verify that the PIV credential was issued by an authorized entity, has not expired, and has not been revoked. The PIV authentication certificate is used to verify that the PIV credential was issued by an authorized entity, has not expired, has not been revoked, and that the holder of the credential (you) is the same individual it was issued to. The digital signature certificate allows the user to digitally sign a document or email, providing both integrity and non-repudiation. The encryption certificate allows the user to digitally encrypt documents or emails.
- D. This image shows the cipher block chaining (CBC) mode of cipher operation. You can determine this by noting that the plaintext block being encrypted is XORed with the ciphertext of the preceding block.
- A. Attacks sponsored by organized crime groups almost always have financial motivations.
- B. Web servers use TCP port 80 for unencrypted HTTP communications and they use TCP port 443 for encrypted HTTPS communications. If Ryan would like to require the use of encrypted connections to the web server, he should allow TCP port 443 and block TCP port 80.
- B. The US federal government's Digital Signature Standard (DSS) endorses the use of the Digital Signature Algorithm (DSA) for the creation of digital signatures.
- A. The recovery time objective (RTO) is the amount of time that it is acceptable for a system to be down prior to recovery during a disaster. The recovery point objective (RPO) is the amount of acceptable data loss during a recovery effort. The RTO and RPO are targets rather than measures of actual performance. The mean time between failures (MTBF) is the average amount of time that elapses between the failures of a system or component. The mean time to repair (MTTR) is the amount of time that it takes to recover a failed system. The MTBF and MTTR are measures of actual performance.
- B. The recovery time objective (RTO) is the amount of time that it is acceptable for a system to be down prior to recovery following a disaster. The recovery point objective (RPO) is the amount of acceptable data loss during a recovery effort. The RTO and RPO are targets rather than measures of actual performance. The mean time between failures (MTBF) is the average amount of time that elapses between the failures of a system or component. The mean time to repair (MTTR) is the amount of time that it takes to recover a failed system. The MTBF and MTTR are measures of actual performance.
- C. Push notifications are a secure way to implement a second authentication factor and also have high user satisfaction because they typically only require the user to click approve on a notification pushed to their device. SMS notifications and app-based passcode generators have lower user satisfaction because they require the user to enter a passcode to complete the authentication process. Email notifications are not an acceptable way to implement multifactor authentication with mobile devices because an email account is not tied to a specific device and, therefore, does not constitute a "something you have" authentication approach.
- B. Bill should definitely update the operating system to bring it into compliance with current security standards. However, he does not have console access to the device, so the only way he can do this is to obtain the update from the device vendor.
- C. The Triple DES algorithm performs three different rounds of DES encryption. The most secure way of doing this is with three different keys. A less secure mode of operation uses only two keys, while an insecure mode of operation uses a single key to replicate the functionality of DES. It is not possible to use Triple DES with four encryption keys.
- D. Communication between the database server and the firewall server would not travel through the hardware firewall because they are located on the same network segment. In this case, the database server is attempting to connect to the file server, so the file server's host firewall is the most likely culprit.
- A. In a RAID 5 array, all of the disks contain data except for the parity disk. Therefore, regardless of the number of disks in the array, only a single disk may fail before data is permanently lost.
- C. This upgraded safe is best described as a preventive control because it is designed to prevent an intruder from successfully cracking it in less than 30 minutes. This time period allows detective controls the time to work and identify the intrusion.
- D. Bcrypt is a key stretching algorithm that is both memory-hardened and CPU-hardened. PBKDF2 is CPU-hardened but not memory-hardened. HMAC and RIPEMD are not key stretching algorithms.
- C. Identification occurs when a user makes a claim of identity. This claim is then proven during the authentication phase, through the use of one or more authentication factors, such as a password, smart card, or biometric reading. The system then determines the specific activities that the authenticated user is authorized to engage in by consulting access control lists (ACLs) and other mechanisms and then tracks user access in an accounting system.
- A. Maureen can use a rainbow table attack against this website because she has access to the password file. This would be more productive than a dictionary attack because it precomputes the password hashes. Both dictionary and rainbow table attacks are more productive than brute force attacks when the site does not have a strong password policy.
- A. This is the output feedback (OFB) mode of encryption. You can determine this because it generates keystream blocks to combine with the plaintext and arrive at ciphertext.
- D. The Advanced Encryption Standard (AES) supports key sizes of 128, 192, and 256 bits. It does not support 512-bit keys.
- A. Apple's iOS platform limits users to installing applications downloaded from Apple's App Store. The other three device types listed – Samsung Galaxy, Motorola Moto, and Huawei P-series – are all Android devices, which allow users to download apps from a variety of third-party app stores.
- B. In a load-balanced network that uses server affinity, client requests are assigned to the server that is already handling requests from that same client to minimize the number of network connections.
- D. NIST changed their password security guidelines in 2017 and now recommends that organizations do not enforce the expiration of user passwords.
- B. In this scenario, Peter has already completed his reconnaissance but has not yet gained access to any systems on the target network. Therefore, he is still in the initial exploitation phase of the penetration test.
- B. The SIEM correlation engine is a sensitive device that should be accessed only by security personnel. Therefore, it should be placed on the internal network where it is not exposed to external traffic.
- A. The assignment of permissions based upon a user's job indicates that this is a role-based access control system. There is not enough information provided to come to the conclusion that this is a mandatory or discretionary access control system. There is also no indication that the attributes of the user's account are scrutinized during the authorization process.
- A. Port security restricts the number of unique MAC addresses that may originate from a single switch port. It is commonly used to prevent someone from unplugging an authorized device from the network and connecting an unauthorized device but may also be used to prevent existing devices from spoofing the MAC addresses of other devices.
- C. The exclusive or (XOR) operation is true when one and only one of the inputs is true. This means that one input must have a value of 1 while the other has a value of 0. Applying this operation to the problem shown here gives the answer of 1001.
- C. Firewall log analysis can be easily automated to identify common configuration issues and attack signatures. Password reset automation is a very commonly used technique to reduce the burden on help desks. Configuration management is generally only possible through automation. Risk assessments are an inherently time-intensive activity that would not likely benefit from automation.
- C. In a choose-your-own-device (CYOD) model, the employee is permitted to choose from a selection of approved devices. The company owns the device. In a bring-your-own-device (BYOD) model, the employee owns the device. In corporate-owned, personally-enabled (COPE) and corporate-owned models, the company owns the device but the employee does not necessarily have the ability to choose the device.
- B. While Glenn may use any of the technologies described here to segment the sensitive network, the question specifically asks for the strongest degree of separation possible. This is achieved by designing an air-gapped network that is not connected to any other network.
- D. Gary is engaging in a dictionary attack because he begins the attack with a dictionary of possible passwords. This is not a brute force attack because Gary begins with a list of possible passwords. A brute force attack would simply try every possible value. It is not a rainbow table attack because Gary did not create a rainbow table: a prehashed file of possible password values.
- D. This is a classic example of a memory leak. The application is not releasing memory that it no longer needs, and it continues to make requests for new memory allocations. This activity persists until the system runs out of memory and is rebooted.
- D. Retinal scanning is a slow, intrusive technique that requires specialized hardware and cannot be performed with a standard smartphone. Smartphones do commonly use passcodes, fingerprint scanning, and facial recognition for authentication.
- D. All DNSSEC implementations must support the RSA/SHA-1 cipher suite to maintain compatibility between systems. The RSA/MD5 cipher suite should never be used due to insecurities in the MD5 hash algorithm. The RSA/SHA-256 and RSA/SHA-512 cipher suites are recommended for use but are not required.
- B. Cross-site scripting (XSS), cross-site request forgery (XSRF), and SQL injection attacks all exploit vulnerabilities in web applications. Shimming is a technique used to manipulate device drivers.
- D. The object identifier (OID) indicates the specific purpose of the digital certificate. For example, OID 1.3.6.1.5.5.7.3.1 is for server authentication, while 1.3.6.1.5.5.7.3.4 is for email protection.
- B. Minifying code makes it very difficult for humans to interpret, but not impossible. This is an example of obfuscation. If the code were encrypted, it would require decryption prior to execution. If the code were hashed or masked, it would not function because those operations are irreversible.
- A. The image shows a mantrap, a physical security control designed to limit access to a facility to one person at a time. This control prevents tailgating by preventing one individual from holding the door open, intentionally or accidentally, for a second person.
- A. WPA uses the Temporal Key Integrity Protocol (TKIP) to rapidly cycle encryption keys and overcome the weaknesses of WEP. WPA2 uses the Counter Mode Cipher Block Chaining Message Authentication Code Protocol (CCMP) to provide enhanced security using AES. Hashing is not an integral component of the cryptographic improvements.
- B. In this attack, the attacker executed a request against a third-party website by taking advantage of the fact that the user already had an established session with that site. This is an example of a cross-site request forgery (XSRF) attack.
- A. The Network Time Protocol (NTP) is used to synchronize the clocks of devices to a standardized time source. NTP is quite useful in helping to ensure consistent timestamps on log entries.
- D. The image explains that the malware encrypted the contents of the computer and will only restore access after the user pays a ransom. This is an example of ransomware, a category of crypto-malware.
- C. Any of these systems would be capable of detecting the attack. However, a SYN flood attack is a well-documented attack and any signature-based IDS would have a built-in signature that defines the attack precisely. Therefore, a signature-based system is most likely to successfully detect this attack.
- C. The General Data Protection Regulation (GDPR) is a sweeping privacy regulation covering operations in the European Union. It replaced the older Data Protection Directive (DPD) in 2018. The Health Insurance Portability and Accountability Act (HIPAA) and Gramm-Leach-Bliley Act (GLBA) are US, not European, laws.
- A. The most effective way to address this issue is to deploy a patch that corrects the vulnerability. Since this vulnerability is in Apache Tomcat, the patch must be applied to that service. Patching the operating system will not correct an issue with the service. Web application firewalls and content filters, if deployed in the correct location, may block an attack from exploiting this vulnerability but they do not remediate the root issue.
- C. Paul has already gained initial access to a system: the web server. He is now attempting to take that access and pivot from the initial compromise to a more lucrative target: the file server.
- B. The passwords shown here are hashed using the salted SHA hash algorithm, as described by the {SSHA} attribute. They are neither encrypted (because the hash cannot be reversed) nor stored in cleartext form (because you can't examine the value and determine the password). If they were hashed using an unsalted version of SHA, the attribute before the hash would read {SHA} instead of {SSHA}.
- B. This image clearly shows the patterns in an individual's iris. Retinal scanning requires images of the blood vessels inside the eye, which are not visible in this image. Facial recognition requires an image of a significant portion of the individual's face.
- C. Two-person control requires the concurrence of two individuals for sensitive actions. That is the scenario described here. Separation of duties says that an individual should not have both permissions necessary to perform a sensitive action. This is a closely related but distinct principle. There is no evidence given that supervisors do not have the ability to create payments, so separation of duties is not in play here.
- A. This attack leveraged the implied authority of someone wearing a security guard's uniform. It may also have leveraged intimidation by threatening employees, or consensus when employees followed each other's lead, but this is not clear in the scenario. There is no indication of scarcity being used in this particular attack.
- B. A split tunnel VPN policy allows Vic to specify that only traffic destined for the home office should be routed through the VPN. If Vic used a full tunnel policy, engineers would not be able to access systems on the customer's local network. Vic may use either an IPsec or TLS VPN to meet this requirement. That technology decision is separate from determining what traffic is sent through the VPN.
- B. In a Type 1 hypervisor, the hypervisor runs directly on the physical hardware. In a Type 2 hypervisor, the hypervisor runs on a host operating system which, in turn, runs on the physical hardware. In both cases, guest operating systems run on top of the hypervisor.
- C. The mean time to repair (MTTR) is the amount of time that it will typically take to restore service after a failure. In this case, the MTTR is 3 days: the amount of time to obtain and install a replacement firewall.
- D. The mean time between failures (MTBF) is the amount of time that typically passes between failure events. In this scenario, Kyle has determined that events typically occur once every 4 years.
- B. From his conversations with business leaders, Kyle determined that the business can tolerate an outage of 4 hours, making this the recovery time objective (RTO).
- A. From his conversations with business leaders, Kyle determined that the business can tolerate the loss of 1 hour of data, making this the recovery point objective (RPO).
- C. The diagram shows federated trust relationships. Arrows with only one arrowhead are one-way trusts. Joe's account is in Domain D and the relationships show that Domains A and B have one-way trust in Domain D. Therefore, Joe can use his account to access resources in Domains A and B. Domain A trusts Domain C, but Domain C does not trust Domain A, so Joe can't use his account to access resources in Domain C.
- B. If the password remains known only to authorized individuals, this does not violate the principles of confidentiality or integrity. There is no indication from the scenario that the account has excess privileges, so least privilege is not violated. However, the use of a shared account prevents security staff from determining which individual performed an action, violating the principle of accountability.
- A. The Secure File Transfer Protocol (SFTP) provides a file transfer capability through a Secure Shell (SSH) connection. The File Transfer Protocol Secure (FTPS) also provides secure file transfers, but does so through a modified version of the FTP protocol and does not use SSH. Dropbox is a proprietary file sharing service that does not use SSH. The HyperText Transfer Protocol Secure (HTTPS) is a secure web protocol that may be used for file transfers but does not leverage SSH.
- D. Servers that provide services to business partners should be placed on the extranet. Intranet servers should have access restricted to internal users. DMZ servers may be accessed by the general public. Guest networks are designed for visitors to a facility to gain internet access.
- A. The fact that the packets are reaching the host rules out a network firewall or IPS issue. The fact that the logs indicate that the traffic was allowed rules out a host firewall issue. Therefore, the most likely remaining cause is an issue with the application.
- A. Mandatory vacation and job rotation policies seek to uncover fraud by requiring employees to be unable to perform their normal job functions for an extended period of time, subjecting those functions to scrutiny by other employees. Privileged access monitoring tracks the activity of users with special privileges and may also uncover fraud. Separation of duties seeks to prevent fraudulent activity before it occurs and would not detect the misuse of privileges in a fraudulent manner.
- A. This is a classic example of a piggybacking attack where one person enters a physical facility and then holds the door open for others to enter without requiring them to also use the access control system. In a dumpster diving attack, individuals rummage through the trash searching for sensitive information. In a shoulder surfing attack, the perpetrator looks over the shoulder of an individual while they use a computer. There is no sign that the individuals entering the building without authenticating were making false claims of identity, so there is no evidence of an impersonation attack.
- C. The false rejection rate (FRR) of a system is calculated by dividing the number of false rejections by the total number of authentication attempts. In this dataset, there are 100 total authentication attempts, of which 5 were false rejections of an authorized user. Therefore, the false acceptance rate is 5%.
- C. Cloud-based DLP solutions are updated and maintained by the cloud vendor and would involve the least maintenance effort from Carl's team. Host-based and network-based DLP would require the local team to install the solution and keep it updated. The use of signature-based DLP technology does not have a significant impact on the amount of maintenance time.
- B. Geofencing allows an organization to restrict certain actions so that they may only take place when the device is in a specified area. If a user exits the geofenced area, the action is no longer possible. This technology is ideal for limiting the use of an application to a specific geographic area, such as a corporate campus.
- D. While it is not an incredibly productive attack, an online brute force attack is Val's only option of the choices provided. Val does not have access to a password file, which would be a requirement for an offline attack, such as an offline dictionary attack, a rainbow table attack, or an offline brute force attack.
- C. In SAML authentication, the user agent is the web browser, application, or other technology used by the end user. The service provider is the service that the user would like to access. The identity provider is the organization providing the authentication mechanism. The certificate authority issues the digital certificates required to secure the connections.
- C. In a black-box attack, the attacker does not have access to any information about the target environment before beginning the attack. In a grey-box attack, the attacker has limited information. In a white-box attack, the attacker has full knowledge of the target environment before beginning the attack.
- B. Tethering allows mobile devices to share their network connection with other devices. Split tunneling allows a device to send traffic through a VPN tunnel only when connecting to corporate systems, while split-horizon DNS allows the use of different DNS servers for different networks. Transport layer security (TLS) is an important encryption protocol used to secure communications between devices.
- B. The use of incremental backups is the best way to conserve disk space. If Gavin chooses this option, he will back up the entire file server on Monday. Then, each of the other day's backups will include only the files added or modified on those days, which is the approach used by incremental backups.
- A. If Gavin performs a full backup each day, when he recovers the system, he will only need to restore the single full backup that occurred most recently before the failure. All of the other strategies require restoring multiple backups.
- B. Each strategy requires performing a full backup on the first day, which is the most time-consuming operation. Options A and D require performing additional full backups, so those options may be eliminated immediately. This leaves us with a choice between strategies that perform incremental backups and differential backups. Differential backups only back up files that have changed since the last full backup, making them a faster choice than full backups. However, incremental backups only back up files that have changed since the last full or incremental backup, making them even faster to perform.
