Figure 15-1: Choosing the Hyperlink option.
Chapter 15
Ten Simple Management Guidelines
In This Chapter
![]() Putting good records and information principles to work
Putting good records and information principles to work
![]() Finding what you need, when you need it
Finding what you need, when you need it
![]() Reducing duplicate information
Reducing duplicate information
![]() Keeping it simple
Keeping it simple
A Records and Information Management program has many components, processes, and principles. However, the positive thing is that all the different pieces are not that complicated; remembering to do them all is the hard part. The solution is simple: Build good Records and Information Management principles into your daily work routine. Chances are, after a while, you will not identify them as “Records and Information Management principles,” but as processes that make your work life easier.
Employees should take the time to understand the tricks of the Records and Information Management trade. The investment in time will begin to immediately pay dividends as employees realize that they can find information more quickly, aren’t always having to manage their e-mail quota, and don’t need additional file cabinets.
This chapter provides ten guidelines guaranteed (okay, not guaranteed, but proven) to help simplify the management of records and information.
Limiting E-Mail Attachments
A great way to help manage your e-mail quota and reduce the amount of duplicate company information is to use links to access documents in an e-mail instead of sending the attachments themselves. However, remember that if you send a link to a file in your e-mail rather than an attachment, the recipient has to have access to the server and folder where the file resides.
Here’s how it’s done:
1. Open your e-mail application.
2. Place your cursor where you want the link to appear.
3. Right-click in the body of the e-mail.
4. Choose Hyperlink from the menu that appears. (See Figure 15-1).
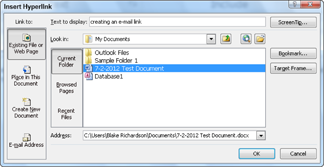
The Insert Hyperlink window appears, as shown in Figure 15-2.
5. Click in the Text to Display box.
6. Type the name of the link as you would like it to appear.
7. Using the Look In box, navigate to the document that you want to provide access to and select it.
8. Click OK.
A link to the document is added to your e-mail. You can now send the e-mail, knowing that your e-mail recipient only has to click the link to access the document.
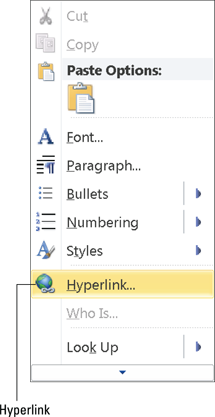
Figure 15-2: Naming the hyperlink and establishing the link.
Knowing How to Dispose of Information
Following these simple guidelines takes the guesswork out of information destruction:
![]() If information is business related, it should be placed in a secure document shred bin.
If information is business related, it should be placed in a secure document shred bin.
![]() Documents that contain no business information can be placed in a secure shred or recycle bin.
Documents that contain no business information can be placed in a secure shred or recycle bin.
All records whose retention periods have expired and are not part of an information hold order should be disposed of in a secure document shred bin. Nonrecord information that has or once had business value should also be placed in a secure document shred bin. This may include documents, spreadsheets, and presentations. Nonrecord information may still contain information of a personal, confidential, or competitive nature, requiring that it be placed in a secure document shred bin for disposal.
Information of a nonbusiness nature can be placed in a recycle bin. However, some organizations use a shred-all approach for disposing of information. This means that all information is placed in secure document shred bins.
Structuring Electronic Folders
Imagine opening your file cabinet drawer and inside is one large hanging folder containing various record types and date ranges. Now imagine attempting to quickly find what you need. This scenario is played out electronically every day in companies throughout the world. You open a shared network drive folder and it’s full of unrelated documents, spreadsheets, presentations, image files, and PDFs that have accumulated over the years.
Creating an effective electronic folder structure can significantly improve electronic filing and retrieval. The first steps in creating a folder structure are to understand your primary business functions and to develop a folder and subfolder structure that supports it. Figure 15-3 provides an example of an Accounts Payable folder structure.
Figure 15-3: Effective folder structure.

When naming folders, avoid using cryptic names, numbers (dates may be appropriate), and acronyms. Employees should be able to determine the contents of a folder or subfolder by its name.
Naming Files
So the boss needs you to send her the analysis you saved to your hard drive six months ago. Trying to find the document can be a challenge if you saved it with a name that made sense then, but doesn’t seem as obvious now. You may have to open several files before you find it. Knowing how to effectively name electronic folders and files can help you to quickly find information when you need it. Following are tips for filing electronic information:
![]() Hard drives: Avoid storing company records and information of business value on your local hard drive — go for the shared network drive instead. Information that may be useful to other employees is inaccessible if it’s stored on your local drive. This may include information that is useful for processing or lawsuits, audits, or governmental inquiries.
Hard drives: Avoid storing company records and information of business value on your local hard drive — go for the shared network drive instead. Information that may be useful to other employees is inaccessible if it’s stored on your local drive. This may include information that is useful for processing or lawsuits, audits, or governmental inquiries.
![]() Naming conventions: An effective filename allows others to determine the contents of the file without having to open it. The way files are named can be the difference between quickly being able to retrieve information or having to open several files before you find what you need. You should avoid using cryptic names, numbers (except dates as a prefix or suffix to the filename), and acronyms. Be consistent in the way that you name files. For example, if you use an employee name in the filename, always use the last name first.
Naming conventions: An effective filename allows others to determine the contents of the file without having to open it. The way files are named can be the difference between quickly being able to retrieve information or having to open several files before you find what you need. You should avoid using cryptic names, numbers (except dates as a prefix or suffix to the filename), and acronyms. Be consistent in the way that you name files. For example, if you use an employee name in the filename, always use the last name first.
![]() Maintenance: A key to efficiently finding electronic information is to maintain the repository in which it resides. If you store files to a shared network drive, you should regularly delete eligible information. This reduces the number of files that you have to scroll through or potentially review.
Maintenance: A key to efficiently finding electronic information is to maintain the repository in which it resides. If you store files to a shared network drive, you should regularly delete eligible information. This reduces the number of files that you have to scroll through or potentially review.
Managing Active and Inactive Periods
All records and information have life cycle phases that need to be managed. Two phases of the life cycle include an active and inactive period. In the active phase, records and information are used to process functions and are retrieved for inquiry purposes. During this time, physical (paper) records and information need to be readily accessible and typically are stored in departmental file cabinets. Active electronic information is stored on a server for quick retrieval.
During the inactive phase, records and information are infrequently needed. Although official company records may no longer be considered active, they may still need to be retained for legal, regulatory, and operational purposes. Inactive nonrecord information should be deleted as soon as it’s no longer needed as long as it’s not part of an information hold order. Inactive electronic records that must be retained are sometimes migrated to less-expensive storage media, such as optical discs or magnetic tape.
Scheduling Destruction and Deletion
Destroying records and information in the normal course of business helps to ensure that the organization stays in compliance with laws and regulations and eliminates clutter. Destroying and deleting eligible information prevents the accumulation of unneeded information that, over time, can make it difficult to find the information you need.
This includes routinely reviewing, destroying, and deleting eligible physical and electronic information in file cabinets, in record storage boxes, and on hard and shared network drives, as well as archived data. An effective electronic information file review can eliminate or significantly reduce the need to purchase additional storage.
Before destroying or deleting company information, it’s essential to ensure that the retention periods have expired and that the content is not part of any active or anticipated information hold orders.
Creating the Proper Filing System
Selecting the right filing method can enhance employee efficiency, customer service, and compliance to laws and regulations. Implementing the wrong filing system can lead to lost records, misfiles, increased labor costs, and frustration.
Understanding the types of records and information you have, as well as how they are used and requested, is the key to developing and implementing the appropriate filing system. For example, if employee files are normally requested by employee ID, you don’t want to file them by last name or department.
Information growth is an important factor to consider and analyze when developing a physical (paper) filing system. Past growth can serve as an effective indicator of future growth. However, you should take into consideration new corporate initiatives such as acquisitions, new product launches, and services that may impact future volumes.
Avoiding the “Keep Everything” Syndrome
Don’t be a corporate hoarder — only specific records, with long-term operational or historical value, are meant to be retained permanently. Only keep information that has active business value. When the information no longer provides benefit to your company, it should be discarded, unless the content’s retention period hasn’t expired or if you need the information for an active or potential lawsuit.
It is common for employees to feel the need to hang on to everything for that just-in-case moment — like the one that happened ten years ago when Bob in Accounting asked you for a copy of that travel invoice you had thrown out the week before. The CYA effect is another classic example and reason why employees feel the need to keep information that was eligible to be destroyed years ago. It may be appropriate in some cases to retain information for CYA purposes. However, if an issue hasn’t surfaced after a reasonable amount of time, it’s probably safe to destroy it.
Managing Copies
Copies of records and information are the biggest contributor to corporate clutter. This includes both electronic and physical content. Records and document management experts have estimated that over 50 percent of organizational information consists of copies that could be immediately destroyed.
Many times, it’s appropriate and necessary to create a copy. However, if not properly managed, copies can increase organizational costs and risks by increasing storage and discovery costs. To properly manage copies, it’s important to understand their characteristics and intended uses. Copies are meant to be
![]() Temporary in nature
Temporary in nature
![]() Not an official record
Not an official record
![]() Used for short-term or immediate reference purposes, such as meetings and reporting
Used for short-term or immediate reference purposes, such as meetings and reporting
A significant source of copies is system-generated reports. Many employees treat reports as official company records and retain them for long periods of time. Many organizational reports are generated on a daily, weekly, or monthly basis and lose their immediate value when the next the report is generated. For example, you may receive a weekly sales report that includes the previous week’s sales figures. It may be appropriate in this case to only retain the current report and shred the previous week’s information.
![]() Retention schedule: Some retention schedules list the department of record. This is the department or custodian responsible for a specific record type. Other departments that possess the information should consider the item a copy and only retain it for the period of time it serves its intended business purpose.
Retention schedule: Some retention schedules list the department of record. This is the department or custodian responsible for a specific record type. Other departments that possess the information should consider the item a copy and only retain it for the period of time it serves its intended business purpose.
![]() Electronic filing: Electronic filing practices can have a significant impact on the volume of organizational copies. The absence of an effective departmental folder structure and cryptic filenames lead to duplicate information with different names being stored throughout the organization. A good folder structure and use of proper file-naming conventions provide employees with a filing road map. After an employee locates the folder she needs to save a file to, she can determine whether the file already exists, reducing the potential for information duplication.
Electronic filing: Electronic filing practices can have a significant impact on the volume of organizational copies. The absence of an effective departmental folder structure and cryptic filenames lead to duplicate information with different names being stored throughout the organization. A good folder structure and use of proper file-naming conventions provide employees with a filing road map. After an employee locates the folder she needs to save a file to, she can determine whether the file already exists, reducing the potential for information duplication.
 Using shared network drives instead of local hard drives reduces information duplication. Shared drives enable files to be accessed by multiple employees, eliminating the need for additional file copies.
Using shared network drives instead of local hard drives reduces information duplication. Shared drives enable files to be accessed by multiple employees, eliminating the need for additional file copies.
![]() Software: The use of Records, Document, or Content Management software can significantly reduce the amount of duplicated information. The software allows you to provide multiple metadata fields to electronic content, which reduces the potential for duplicated content to exist. Many software applications alert the user when he attempts to assign metadata to a file and another file with that exact metadata already exists.
Software: The use of Records, Document, or Content Management software can significantly reduce the amount of duplicated information. The software allows you to provide multiple metadata fields to electronic content, which reduces the potential for duplicated content to exist. Many software applications alert the user when he attempts to assign metadata to a file and another file with that exact metadata already exists.
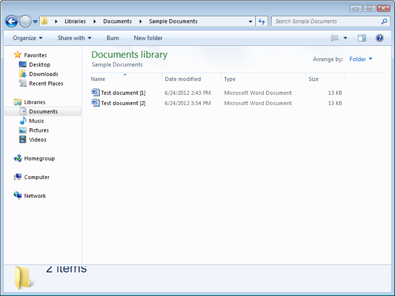
![]() Version control: Version control is a process that allows you to determine the most recent version of a document. If you use a Document or Content Management system, version control can happen automatically. However, versioning can also be performed manually, just by eyeballing the modification dates. (See Figure 15-4.) Knowing which file is the most recent allows you to delete prior versions or copies.
Version control: Version control is a process that allows you to determine the most recent version of a document. If you use a Document or Content Management system, version control can happen automatically. However, versioning can also be performed manually, just by eyeballing the modification dates. (See Figure 15-4.) Knowing which file is the most recent allows you to delete prior versions or copies.
![]() E-mail: It’s very common for employees to attach documents to an e-mail and distribute the message to multiple recipients. This creates duplicate information. Whenever possible, it’s recommended that you include a link to documents in your e-mail instead of including them as attachments.
E-mail: It’s very common for employees to attach documents to an e-mail and distribute the message to multiple recipients. This creates duplicate information. Whenever possible, it’s recommended that you include a link to documents in your e-mail instead of including them as attachments.
Figure 15-4: Version control (manual).
Keeping It Simple
Records and information concepts and principles are simple:
![]() Know what you have.
Know what you have.
![]() Know how long to keep what you have.
Know how long to keep what you have.
![]() File what you need to keep so that you can find it when you need it.
File what you need to keep so that you can find it when you need it.
![]() Properly dispose of what you don’t need.
Properly dispose of what you don’t need.
Granted, this may be an oversimplification of Records and Information management, but it’s not too far off. The concepts are simple; it’s the volume of records and information that makes it seem such a daunting task. The good thing is that Records and Information Management processes are consistent and repeatable. The variable is volume. Volume determines how much time it will take to inventory your content, how many individual record series you have listed on your retention schedule, and how long it will take to review records and information that are eligible for destruction. Although you may have a lot of volume, the principles are simple.
When communicating Records and Information Management issues to employees, it’s recommended that you keep it as simple as possible. This is not because employees aren’t intelligent enough to grasp the concept — the concepts themselves are not complicated — but because Records and Information management simply isn’t an employee’s core function. Regardless of what new initiative or program a company is rolling out, if employees perceive it to be easy and convenient, they are more likely to comply.

