Chapter 3
Understanding the OSI Model
The Open Systems Interconnection (OSI) Model is one of the most referenced models in networking. It includes seven layers with specific activities, protocols, and devices working on each. Many network exams test your knowledge of the different elements of the OSI Model, and even some hiring managers quiz potential network employees on their knowledge. The TCP/IP Model is similar but includes only four layers instead of seven. This chapter introduces both models.
- Understanding the OSI Model
- Understanding the TCP/IP Model
- Mapping devices on the OSI and TCP/IP models
- Mapping protocols on the OSI and TCP/IP models
The seven-layer Open Systems Interconnection (OSI) model is a general framework, or set of guidelines, for network communication. It defines how data is handled at several different layers. It also identifies the framework of TCP/IP protocols and hardware used on networks. There is no single standard or compliance test for the OSI Model itself. Instead, many standards have been created based on the different elements of the model.
The OSI Model is a framework for network communication. The ISO created it, and it includes seven layers.
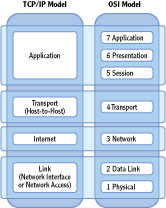
Figure 3-1 shows the seven layers of the OSI Model. One of the primary goals of the OSI Model is operating system independence. In other words, the OSI Model allows computers running any operating system to communicate with other computers.
Figure 3-1: The OSI Model

The OSI Model was created by the International Organization for Standardization (ISO). The following are many advantages to the OSI Model:
The ISO may look like a typo. However, it’s not an acronym for the International Organization for Standardization. Instead, ISO is derrived from isos, which is Greek for equal.
Layers Interact Only with Adjoining Layers For example, the Transport layer interacts with the Session and Network layers only. It doesn’t matter to the Session layer what applications are used on the Application layer. Similarly, it doesn’t matter to the Session layer what type of cable media is used to transmit the data on the Physical layer.
It Has Encouraged Creation of Industry Standards Functions at each layer are standardized. Development of network components by different vendors is simplified, and different operating systems are able to communicate with other.
Network Communication Processes Are Segmented Instead of a single protocol that does everything, multiple protocols are used. Troubleshooting is easier once the OSI Model is understood.
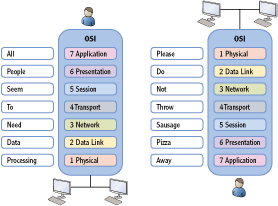
You should know the names and number of each layer. Figure 3-2 shows two commonly used memory techniques.
Notice that one method (All People Seem To Need Data Processing) starts at layer 7 and goes to layer 1. The other method (Please Do Not Throw Sausage Pizza Away) starts on layer 1 and goes to layer 7. There are many other sayings used by technicians to memorize these layers. The technique you use isn’t as important as using some method to memorize it.
Of course, just knowing the names and numbers of the layers isn’t all you need to know. You should also have a basic understanding of what happens at each layer.
Figure 3-2: Mnemonics and the OSI Model
Application Layer
Layer 7 is the Application layer. It interacts with the Presentation layer and the end user. Several protocols operate on the Application layer:
Domain Name System (DNS) DNS is the primary name resolution service used on the Internet and in Microsoft networks. DNS resolves host names to IP addresses. In other words, you can pass the name of a server (such as DC1) to DNS, and DNS will return the IP address. DNS is also used to locate servers running specific services within a Microsoft network.
DNS is a required service in Microsoft domains and is heavily used on the Internet. Chapter 10 presents name resolution and DNS in greater depth.
Hypertext Transfer Protocol (HTTP) HTTP is the primary protocol used to transmit data across the Internet for web pages. Similarly, HTTPS is a secure version of HTTP used to transmit data in an encrypted format.
File Transfer Protocol (FTP) FTP is the protocol used to transfer files to and from an FTP server. FTP servers are commonly hosted on the Internet. In contrast, file servers are used on internal networks to host files needed by users.
Trivial FTP (TFTP) TFTP is a lightweight FTP protocol used to transfer smaller files. TFTP is often used to transfer files to network devices such as routers.
DHCP saves a lot of labor and is found in most networks. Chapter 5 covers DHCP in more depth.
Dynamic Host Configuration Protocol (DHCP) DHCP is a method of dynamically assigning TCP/IP configuration information to clients. A DHCP server assigns IP addresses to systems. It also assigns the subnet mask, the address of the default gateway (a router), the address of a DNS server, the domain name, and much more.
Lightweight Directory Access Protocol (LDAP) LDAP is a protocol used to query a directory service, such as Microsoft’s Active Directory Domain Services (AD DS). AD DS is hosted on domain controllers.
Post Office Protocol (POP3) POP3 is an email protocol used to retrieve email from POP3 email servers. POP3 servers are commonly hosted by Internet service providers (ISPs).
Simple Mail Transfer Protocol (SMTP) SMTP is an email protocol used to send email. Clients can send email from an email server. When a POP3 email server is used, users receive email with POP3 and send email with SMTP.
Internet Message Access Protocol (IMAP) IMAP is a protocol used to receive email messages. An IMAP server allows clients to store and manage their email on the server. Users can download the email onto their computer or organize the email in different folders on the server.
Simple Network Management Protocol (SNMP) SNMP is a protocol used to manage network devices such as routers and managed switches. It can detect and report problems before they become significant.
Server Message Block (SMB) SMB is a file transfer protocol used on Microsoft networks. It’s primarily used for file and printer sharing.
The Application layer determines whether sufficient network resources are available for network access. For example, if you want to use Internet Explorer to access a web page on the Internet, the Application layer determines whether access to the Internet is available using HTTP.
It’s worth pointing out that the Application layer doesn’t refer to end user applications. For example, applications such as Internet Explorer are not part of this layer and aren’t actually part of the OSI Model at all. However, when the user launches an application that needs network access, protocols on the Application layer ensure that the resources are available to support it.
Presentation Layer
The Presentation layer interacts with the Session and Application layers. In essence, it acts as a translator and determines how to format and present the data.
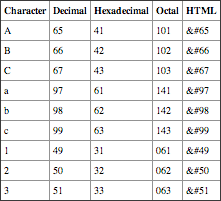
A common method of formatting data is with the American Standard Code for Information Interchange (ASCII) table. This table includes 128 codes to display characters such as numbers, letters, and symbols. Table 3-1 shows a partial listing of the ASCII table.
Table 3-1 Partial ASCII table
Many other codes beyond ASCII are defined at the Presentation layer. For example, the Extended Binary Coded Decimal Interchange Code (EBCDIC) extended the ASCII table from 128 characters to 256 characters. File types such as MP3, JPG, and GIF also have their own codes defined on this layer.
The Presentation layer is also responsible for data compression and decompression and data encryption and decryption. For example, multimedia transferred over the Internet is often compressed to conserve bandwidth. If it wasn’t, the World Wide Web might be known as the World Wide Wait.
Session Layer
The Session layer has the responsibility of establishing, maintaining, and terminating sessions. A session is simply a lasting connection between two networking devices. For example, if you use a chat program on your computer, it will establish a session with another computer to exchange the data.
Another way of saying this is that the Session layer manages the connections. It starts the session, manages the traffic during the session, and terminates the session when appropriate.
The Session layer also ensures that data from different applications are kept separate for each application at the Application layer. This becomes critical when multiple applications are running or when applications require more than one resource.
For example, you may be having a chat session in one window, downloading music in another, and reading email in a third. Three sessions are established and maintained for three different applications. The Session layer ensures that resources are available for each session and kept separate from each other.
The Session layer also tracks the mode of transmission used by the computers. Computers can transmit data using simplex, half-duplex, or full-duplex modes:
Simplex Data can be sent only one way. This isn’t commonly used today in networking applications.
Networking professionals sometimes use the terms simplex and half-duplex interchangeably. However, they are different.
Half-Duplex Data can be sent both ways but only one way at a time. This is similar to a walkie-talkie where one user can press a button to talk but cannot receive any transmissions while the button is pressed.
Full-Duplex Data can be sent and received at the same time. Separate methods are used to send and receive.
The Session layer coordinates the communication and determines which mode to use. Two network protocols that operate on this layer are the Network Basic Input/Output System (NetBIOS) and Remote Procedure Call (RPC).
Transport Layer
The Transport layer is responsible for transporting data. It handles flow control, reliability, and error checking. The Transport layer divides data into smaller chunks, or segments, and then reassembles the received data.
Data traveling on the Transport layer is referred to as segments.
For example, imagine you wanted to mail all volumes of Harry Potter to a friend in another state, but you could only use envelopes. You’d have to tear the pages from the books and mail them all separately. Your friend would then have to reassemble the books from all the envelopes.
This is similar to how data is managed on the Transport layer. Huge megabyte-sized files can’t travel over the network. Instead, the Transport layer segments, or divides, these large files into smaller-sized segments. These smaller segments are transmitted over the network and then reassembled when they’re received. The Transport layer also manages the ordering of the segments so that when the packets arrive, they can be returned to the same order.
Two primary protocols operate on the Transport layer:
Chapter 4 covers TCP and UDP in more depth.
Transmission Control Protocol (TCP) TCP provides guaranteed delivery of data. It starts by establishing a session and will not transmit data until a session is established. TCP is commonly referred to as connection-oriented. This means that it establishes a session before transmitting data.
User Datagram Protocol (UDP) UDP provides a best-effort method of delivering data. It does not provide guaranteed delivery of data like TCP. UDP is referred to as connection-less. Again, this doesn’t refer to the physical connections but instead indicates that data is sent without first verifying a connection with the other system. UDP is commonly used for media streaming and diagnostic messages. Instead of using the additional overhead to establish the connection or session, UDP accepts that there may be some data loss and simply transmits the data.
Port numbers identify details about data on the Transport layer. There are 65,536 possible TCP ports and another 65,536 possible UDP ports. Some protocols use both TCP and UDP ports, while others use only one or the other. In this context, a port is simply a number from 0 to 65,535 that is utilized by a protocol for connection purposes. It does not represent a physical port.
Although port 0 is a valid port, it is reserved for both TCP and UDP.
For example, the HTTP protocol uses the well-known port of 80 by default. When you visit a website, you could use the HTTP address by itself as http://www.bing.com/. However, you could also include the port number as http://www.bing.com:80. Bing.com is the website, and once your request reaches the server hosting it, the TCP port of 80 identifies the data as HTTP traffic. The web server passes the data to the service handling the HTTP protocol.
In short, the IP address is used to get traffic from one computer to another. Once the traffic arrives, the port number is used to identify what application, service, or protocol should process the data.
Logical and Physical Ports
The term ports means different things depending on the context. Ports can be either logical (numbers) or physical (connections on devices).
TCP and UDP ports are logical ports. They are simply numbers used to indicate how data is handled when it reaches its destination. Many ports represent specific protocols such as port 80 representing the well-known port of HTTP. Chapter 4 explores ports in greater depth.
Switches and routers have physical ports. Cables plug into these ports. A switch learns what computers are connected to each port, and a router learns what networks are connected to each port.
Network Layer
The Network layer is responsible for determining the best route to a destination. It uses routing protocols to build routing tables and uses Internet Protocol (IP) as the routed protocol. IP addresses are used at this layer to ensure the data can get to its destination.
Data traveling on the Network layer is referred to as packets.
Several protocols operate at this layer:
Internet Protocol v4 (IPv4) IPv4 is an addressing protocol using 32-bit addresses. The TCP/IP suite uses IP addressing to get traffic from one computer to another. IPv4 addresses are commonly expressed in dotted decimal format such as 192.168.1.1.
Internet Protocol v6 (IPv6) IPv6 is an addressing protocol using 128-bit addresses. IPv6 is intended to replace IPv4 and is currently being used concurrently with IPv4 on networks throughout the world. IPv6 addresses are commonly expressed in hexadecimal format such as 2001:0000:4137:9E76:3C2B:05AD:3F57:FE98.
Valid hexadecimal characters are 0 through 9 and A through F.
Address Resolution Protocol (ARP) This protocol resolves IP addresses to the physical address or the Media Access Control (MAC) address. The IP address is used to route packets to the next hop’s network interface card. Switches use MAC addresses to track computers connected to different physical ports. While ARP resolves the IP address to a MAC address, the Reverse Address Resolution Protocol (RARP) does the opposite. RARP can be used to resolve a MAC address to an IP address.
The MAC address is a 48-bit address assigned to network interface cards. The MAC address is explained more in the “Data Link Layer” section of this chapter.
Internet Group Multicast Protocol (IGMP) IGMP is used for multicasting traffic. Multicast traffic goes from one computer to multiple computers. As a reminder, unicast is one-to-one traffic, and broadcast is one-to-all traffic on the same subnet.
Internet Control Message Protocol (ICMP) ICMP is used for error messages and diagnostic reporting. Several diagnostic tools such as Ping, PathPing, TraceRt, and others use ICMP.
Chapter 14 covers troubleshooting techniques using Ping, PathPing, and TraceRt.
Internet Protocol Security (IPSec) IPSec is a security protocol used to secure IP traffic. IPSec can encrypt traffic to protect it when it’s transmitted. It also includes authentication mechanisms. IPSec authentication allows computers to ensure they communicate only with known entities.
Routing Information Protocol (RIP) This is a basic routing protocol used by routers in internal networks. Routers use RIP to communicate with each other and share information on the network. The current version is RIPv2, though OSPF has replaced it on most networks.
Open Shortest Path First (OSPF) OSPF is another routing protocol used by routers to communicate with each other on internal networks. OSPF is more advanced than RIP and is used in more networks.
The Network layer includes two key physical devices. The primary device working on this layer is a router. Routers are the devices that perform IP based routing functions. The router looks at the IP address and determines the best path to the destination network. Data packets are then sent to the destination using this path.
Layer 3 switches also operate on the Network layer (layer 3). Layer 3 switches combine the capabilities of layer 2 switches and routers. Chapter 8 covers switches in more depth.
RIP and OSPF are common routing protocols used in internal networks. These two protocols determine the best route to a destination based on a metric (cost). The route with the best metric will have a lower cost and will be the selected route for IP.
This is similar to using a map for highways. You look at a map to determine the best route when traveling from point A to point B. The map provides the routing information, and you can identify the best path to get to your destination. Of course, maps are static and show only paths. They don’t show construction, accidents, or other events that can slow traffic down. You may use other online tools to identify traffic congestion or areas of construction.
Routing protocols such as RIP and OSPF are dynamic protocols that can adjust to changing conditions on a network. Routers use these protocols to communicate with each other regularly. If network events occur that impact known routes or if new routes get added, the routing protocols are used to ensure that all the routers quickly learn about the impact.
Data Link Layer
The Data Link layer is concerned with data delivery on a local area network. This is where local area network (LAN) technologies such as Ethernet are defined. The Data Link layer is comprised of two sublayers.
Data traveling on the Data Link layer is referred to as frames.
Logical Link Control (LLC) IEEE 802.2 LLC interacts directly with the network layer. It is defined by the IEEE 802.2 standard. LLC provides flow control and error control and allows multiple protocols to work simultaneously.
Media Access Control (MAC) IEEE 802.3 MAC defines how packets are placed onto the physical media at the Physical layer. IEEE 802.3 defines Carrier Sense Multiple Access/Collision Detection (CSMA/CD), which is used to handle data collisions.
MAC addresses are also defined at the Data Link layer. The MAC address is also called a physical address, hardware address, burned-in address, or Ethernet address. It used to be a permanent address that was written into, or burned into, the read-only-memory (ROM) chip on the network interface card (NIC), but it is usually stored on the NIC’s firmware today.
Listing 3-1 shows the results of entering the command ipconfig /all at the command prompt of a server named DC1. This provides a lot of information including the physical address (or MAC address) of the NIC. Notice that it has an address of A4-BA-DB-FA-60-AD.
Listing 3-1: Output of ipconfig /all
C:>ipconfig /all
Windows IP Configuration
Host Name . . . . . . . . . . . . : DC1
Primary Dns Suffix . . . . . . . : Sybex.pub
Node Type . . . . . . . . . . . . : Hybrid
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
DNS Suffix Search List. . . . . . : Sybex.pub
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Realtek RTL8168C(P)/8111C(P) Family PCI-E
Gigabit Ethernet NIC (NDIS 6.20)
Physical Address. . . . . . . . . : A4-BA-DB-FA-60-AD
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
IPv4 Address. . . . . . . . . . . : 192.168.1.205(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.1.1
DNS Servers . . . . . . . . . . . : 127.0.0.1
NetBIOS over Tcpip. . . . . . . . : Disabled
Other Devices Have MAC Addresses
Although the code snippet shows the physical address of a NIC on a server, other devices also have MAC addresses. For example, each interface on a router has a separate MAC address. These MAC addresses at the Data Link layer are then mapped to an IP address assigned at the Network layer.
The MAC is represented with 12 hexadecimal characters (or 6 pairs of hexadecimal characters). Four bits represent each hexadecimal character. Four bits times 12 characters shows that the MAC address is 48 bits long.
Every device on a network has a different MAC address. If MAC addresses on the network aren’t unique, the computers with the same MAC address can’t communicate on the network.
Organizations that manufacture NICs are assigned an organizationally unique identifier (OUI) that they use in the MAC. They then use serial numbers added to this OUI to create the MAC. Table 3-2 shows how these numbers are combined to create the MAC address of A4-BA-DB-FA-60-AD.
Table 3-2 MAC address
| Organizationally unique identifier | Manufacturer serial number |
| AA-BA-DB | FA-60-AD |
| Six hexadecimal characters (24 bits) | Six hexadecimal characters (24 bits) |
These are some of the protocols that operate on the Data Link layer:
Point-to-Point Tunneling Protocol v4 (PPTP) PPTP is commonly used with virtual private networks (VPNs). VPNs provide remote users with access to a private network over a public connection such as the Internet.
Chapter 13 covers VPNs in more depth.
Layer 2 Tunneling Protocol (L2TP) L2TP is another protocol used with VPNs. It often uses IPSec (as L2TP/IPSec) to encrypt the traffic.
Token ring IEEE 802.5 defines a token ring technology. A logical token is passed between the computers, and a computer can communicate on the network only when it has the token. Using the token for communication prevents collisions.
Asynchronous Transfer Mode (ATM) ATM is a cell-based method of transferring data. Data is converted into small fixed-sized cells and transferred over the network. ATM is used in WANs.
Frame relay Frame relay is another WAN technology. Data is converted to variable-sized frames and transferred over permanent virtual circuits.
Physical devices operating on the Data Link layer include bridges, switches, and NICs.
NICs also operate on the Physical layer.
Physical Layer
The Physical layer defines the physical specifications of the network. This includes physical media such as cables and connectors. It also includes basic devices such as repeaters and hubs. The Physical layer converts the data stream into zeros and ones (bits) and places them onto the physical media in the form of either electrical pulses for copper cable such as twisted-pair cable or light pulses for fiber-optic cable.
Data traveling on the Physical layer is converted to bits, or ones and zeros (such as 110011010101).
The Physical layer has some simple yet unique functions. It defines the physical characteristics of cables and connectors. It is also responsible for encoding signaling types, such as converting digital signals to analog signals.
Ethernet operates on the Physical layer. IEEE 802.3 defines the different technologies used for wired local area networks. Twisted-pair or fiber-optic cables are used for connectivity. It uses CSMA/CD for collision detection.
Putting It Together
Figure 3-3 shows how the OSI Model works when two different computers are interacting. The overall process is referred to as encapsulation where data from higher layers is encapsulated in lower layers.
Imagine a user launching Internet Explorer to access a web search engine such as Bing. The Application layer accepts the data, and the Session, Presentation, and Application layers work together to send the request to the Transport layer.
Figure 3-3: Data traveling up and down the OSI Model

The Transport later then adds a TCP header. This header will include port information for the source and destination computers. Websites serve data using HTTP, and HTTP uses port 80, so the destination port is set as port 80. TCP assigns a port such as 49152 to Internet Explorer as the source port. The source port is to ensure that the return traffic is returned to Internet Explorer to display the page provided by the website.
At this point, you have two TCP ports assigned and added a part of the TCP header:
- Destination port: 80
- Source port: 49152
Next, the IP addresses are added at the Network layer. The IP address of the computer running the web server is added as the destination IP address, and the IP addresses of the user’s computer is added as the source IP address. This information is added as the IP header and combined with the TCP header and the data. At this point, you have the following:
Notice how the packet grows as it travels down the OSI Model. Lower layers add additional information to the previous layer.
- Destination IP address and destination port: 80
- Source IP address and source port: 49152
Routers on the network use the destination IP address to route the packet to the destination computer. When it arrives, the destination port is used to send the data to the service, application, or protocol associated with the port.
When the packet reaches the network where the destination computer is located, the Data Link layer discovers the MAC address of the destination computer. The MAC address is then added to the packet so that the destination computer processes the data.
The Physical layer converts the data into 1s and 0s and places it on the wire. When the data reaches the destination computer, the process is reversed. Information at the different layers is stripped off, and it’s passed to the next layer.
In the example, the data will be passed to the service handling HTTP at the Application layer. The user’s request is processed, and a web page is built and sent back. The entire encapsulation process is repeated on the server and then sent back to the computer that originally requested the data.
Packets and Frames
Although the terms packets and frames are often used interchangeably, this isn’t entirely accurate. The actual name depends on the layer of the OSI Model.
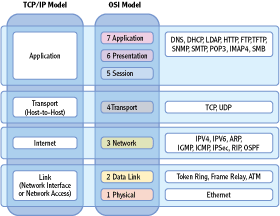
Figure 3-4 shows the names of the encapsulated data at the different layers of the OSI Model. Although there are multiple protocols throughout the OSI Model, this chapter has primarily focused on the TCP and UDP protocols on the Transport layer (using port numbers) and the IP protocol (using IP addresses) on the Network layer.
Figure 3-4: Encapsulated data names
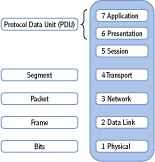
Protocol Data Unit (PDU) Data units at layers 5, 6, and 7 are called protocol data units.
Segment At layer 4, the Transport layer, a TCP unit of data is called a segment. Remember that data is divided into smaller segments at this layer. This layer uses source and destination ports to identify the protocol, service, or application that will process the segment.
Segment has two meanings. On a physical network, it’s a common connection between multiple computers. On the OSI Model, it’s the data at layer 4.
Packet At the Network layer, a unit of data is called a packet. This layer uses IP addresses to get the packets from the source to the destination.
Frame At the Data Link layer, a unit of data is called a frame. MAC addresses are defined here.
Bits At the Physical layer, the data is simply bits, or ones and zeros.
Some sources identify a datagram as a unit of data on the Transport layer (layer 4) using the User Datagram Protocol. Since Datagram is in the UDP name, this makes a lot of sense. It implies that the terms segment and datagram are interchangeable. However, official reference sources don’t support this usage. At this point, you should be able to name each of the seven layers of the OSI Model and their layer number. You should also be able to identify the location of various protocols (such as TCP, UDP, and IP) on the OSI Model and the names of encapsulated data at different layers.
What About Datagrams?
You may come across the term datagram in your studies. However, depending on what source you use, the term datagram can mean different things. Conventional sources indicate that a datagram is simply another name for a packet.
RFC 1594 (www.faqs.org/rfcs/rfc1594.html) identifies a datagram as “A self-contained, independent entity of data carrying sufficient information to be routed from the source to the destination computer without reliance on earlier exchanges between this source and destination computer and the transporting network.”
That’s a mouthful. What RFC 1594 is saying is that a datagram is on the layer doing routing, which is layer 3, the Network layer. This implies that the terms packet and datagram are interchangeable.
Ideally, you should be able draw a diagram similar to Figure 3-4 (without looking at the diagram). If you can do it now, great, but it does take a little practice. Use your favorite mnemonic (All People Seem To Need Data Processing, Please Do Not Throw Sausage Pizza Away, or another one you’ve learned) to help.
Understanding the TCP/IP Model
The TCP/IP Model is a four-layer model created in the 1970s by the U.S. Department of Defense (DoD). It’s also called the DoD Model. The TCP/IP Model works similarly to the OSI Model; it just has fewer layers.
NOTE that the TCP/IP Model was created in the United States for the DoD before the OSI Model, and the OSI Model was created by the ISO as an international standard.