

Using CICS IA data for threadsafe analysis
In this chapter, we look at how CICS Interdependency Analyzer (IA) can be used to assist with ensuring that your applications can execute in a threadsafe manner and take advantage of the performance and throughput benefits of running on open task control blocks (TCBs).
Before using CICS IA to understand the implications of making a program threadsafe, you should use a performance tool such as the CICS Performance Analyzer to identify transactions that have the following specifications:
•Have many TCB swaps
•Are waiting on access to the QR TCB
In this example, we use the transactions used by the GENAPP application:
•SSC1
•SSP1
•SSP2
•SSP3
•SSP4
These transactions are not necessarily good candidates but are used to demonstrate the value of the CICS IA plug-in.
For more information about making your application threadsafe, refer to the popular IBM Redbooks publication: Threadsafe Considerations for CICS, SG24-6351. See section “Help from IBM” on page 240.
We look at the following steps:
5.1 What data to collect to enable threadsafe analysis?
In order to fully analyze and get the best data from running a CICS IA threadsafe report, it is important to collect the correct data. The best data is usually collected from a production region but collecting in a production region introduces performance considerations. Take some time to review how best to collect data in a production region, which is covered in 2.1, “Collecting CICS IA data in a production region” on page 24.
We now review the options that are required for a threadsafe report. We need to collect data for the following information:
•All CICS APIs and SPIs
•Detailed information for programs, files, and connections
•Dynamic COBOL calls
•Remote calls including:
– DB2
– IBM MQ
– IMS/DLI
– CPSM
•Load module reentrancy information
The CICS IA transaction CINT allows you to control and administer your collections. Figure 5-1 on page 119 shows the main administration menu for the CINT transaction. For more information about the CINT transaction, refer to the CICS IA Users Guide, which is in the IBM Knowledge Center:
http://www.ibm.com/support/knowledgecenter/SSPPUS/welcome.html
|
CIU000 CICS Interdependency Analyzer for z/OS - V5R3M0 2015/09/07
Main Administration Menu 10:39:38AM
Select one of the following. Then press Enter.
1 Operations Menu.
2 Configure Region Options.
3 Configure Global Options.
4 User Administration.
CICS Sysid: Z528 CICS Applid: IYDZZ528 TermID: TC82
CIU7000I 5655-Y22 (C) Copyright IBM Corp. 2001,2015
F1=Help F2= F3=Exit F4= F5= F6=
F7= F8= F9= F10= F11= F12=Exit
|
Figure 5-1 CINT: Main Administration menu
We use option 2 to “Configure Region options” for a threadsafe collection. Figure 5-2 shows the Region Configuration menu.
|
CIU200 CICS Interdependency Analyzer for z/OS - V5R3M0 2015/09/07
Region Configuration Menu 10:46:16AM
Type action code then press ENTER. More :
1=Add Region 2=Copy Region 3=Delete Region 4=Options
CICS CICS New New
Act Applid Sysid Applid Sysid Status Collecting
DEFAULTS DFTS
ALL ALL
IYDZZ518 Z518 STOPPED
IYDZZ528 Z528 STOPPED
IYDZZ538 Z538 UNCONNECTED
CICS Sysid: Z528 CICS Applid: IYDZZ528 TermID: TC82
F1=Help F2= F3=Exit F4= F5= Refresh F6=
F7=Page Up F8=Page Down F9= F10= F11= F12=
|
Figure 5-2 CINT: Region Configuration menu
From this menu, we can configure the following options:
•The DEFAULT options for all regions. The defaults are set when the CIUCNTL file is created.
•The REGION-specific options. You can use this to set region-specific options to override the DEFAULT options.
•The ALL options. This is a dummy record that enables you to reset the options for all CICS regions.
We configure the DEFAULTS record to collect dependency data. This is done by selecting line option 4 for “Options” against the DEFAULTS entry.
|
CIU290 CICS Interdependency Analyzer for z/OS - V5R3M0 2015/09/07
Resource Options for 10:52:43AM
CICS Sysid: DFTS CICS Applid: DEFAULTS
Type action code then press ENTER:
1 = General Options
2 = Time/Date Options
Interdependency Options Affinity Options
3 = CICS Options for APIs 7 = Affinity Options
4 = CICS Options for SPIs
5 = DB2/IMS/MQ/CPSM Options CICS TS Applications
6 = Natural Options 8 = Application Data
CICS Sysid: Z528 CICS Applid: IYDZZ528 TermID: TC82
F1=Help F2= F3=Exit F4= F5= F6=
F7= F8= F9= F10= F11= F12=Exit
|
Figure 5-3 CINT: Region Options for the DEFAULTS record
Figure 5-3 shows the Region Options menu for the DEFAUTS entry. We first look at “General Options” by entering option 1.
Figure 5-4 on page 121 shows the general options for the DEFAULTS record. For a threadsafe dependency collection, we need to collect information about dynamic COBOL calls so set:
Dynamic call . . . . . . . . : Y (Y=Yes, N=No)
We also need to ensure that we are collecting for dependency data only so set:
Data to Collect . . . . . . : I
|
CIU260 CICS Interdependency Analyzer for z/OS - V5R3M0 2015/09/07
General Options for 10:57:22AM
CICS Sysid : DFTS CICS Applid : DEFAULTS
Modify the options and press Enter to update, or PF12 to Cancel.
Control options
Data to Collect . . . . . . : I (A=Affinity, I=Interdependency, B=Both)
Perform periodic saves . . . : N (Y=Yes, N=No)
Trigger for CINB start . . . : 1 (2 to 9999 thousand record updates)
Restore data on start . . . : N (Y=Yes, N=No)
Maintain usage counts . . . : Y (Y=Yes, N=No)
Size of dataspace . . . . . : 16 (10 to 2000 Mbytes)
Transid prefix (optional). . : (1 to 4 characters)
Program exclude list . . . . : CIUXPROG (1 to 8 characters)
Transaction exclude list . . : CIUXTRAN (1 to 8 characters)
Command exclude list . . . . : CIUXCOMM (1 to 8 characters)
Resource compression list. . : CIUXRCOM (1 to 8 characters)
Dump HLQ . . . . . . . . . . : DUMP (1 to 8 characters)
Dynamic call . . . . . . . . : Y (Y=Yes, N=No)
Trigger for Task collection. : 1 (1 to 9999)
Collect Long Running Tasks . : N (Y=Yes, N=No)
CICS Sysid: Z528 CICS Applid: IYDZZ528 TermID: TC82
F1=Help F2= F3=Exit F4= F5= F6=
F7= F8= F9= F10= F11= F12=Cancel
|
Figure 5-4 CINT: General Options for the DEFAULTS entry
Next, we need to set the CICS APIs and the SPIs we collect. From the Regions Options menu in Figure 5-3 on page 120, select option 3 for CICS API options.
Figure 5-5 on page 122 shows the CICS “APIs” options panel. For a threadsafe collection, we need to collect DETAILED data for Programs and Files. So we need to set:
*Programs . . . D *Files. . . . . D
Now from the “Regions Options” menu in Figure 5-3 on page 120, select option 4 for CICS SPI options.
Figure 5-6 on page 122 shows the CICS “SPIs” options panel. For a threadsafe collection, we need to collect DETAILED data for connections. So we need to set:
*Connections . D
This captures data about your inter-region connections and reports them as IPIC or MRO. We need this information to determine whether your remote CICS calls are threadsafe.
|
CIU240 CICS Interdependency Analyzer for z/OS - V5R3M0 2015/09/07
CICS Resources Options for 11:10:09AM
CICS Sysid : DFTS CICS Applid : DEFAULTS
Modify the options and press Enter to update, or PF12 to Cancel.
Detect command types: Y=Yes, N=No
D=Yes+Detail ( Only for API types marked with * )
APIs
*Programs . . . D *Files. . . . . D *Transactions . D Task Control . Y
Presentation . Y *TS Queues . . D *TD Queues . . D Journals . . . Y
DTP . . . . . Y Counters . . . Y FEPI . . . . . Y *WEB Services . D
*Exits . . . . D Others . . . . Y *EVENTS . . . . D ATOMServices . Y
XMLtransform . Y WSAddressing . Y
CICS Sysid: Z528 CICS Applid: IYDZZ528 TermID: TC82
F1= F2= F3=Exit F4= F5= F6=
F7= F8= F9= F10= F11= F12=Cancel
|
Figure 5-5 CINT: CICS API options
|
CIU245 CICS Interdependency Analyzer for z/OS - V5R3M0 2015/09/07
CICS Resources Options for 11:13:50AM
CICS Sysid : DFTS CICS Applid : DEFAULTS
Modify the options and press Enter to update, or PF12 to Cancel.
Detect command types: Y=Yes, N=No
D=Yes+Detail ( Only for SPI types marked with * )
SPIs (Create/Inquire/Set/Discard/Perform)
Programs . . . Y Files . . . . Y Transactions . Y Temp Storage . Y
Transient Data Y DB2 . . . . . Y DJAR . . . . . Y BRFacility . . Y
Corbaserver . Y TCPIPService . Y FEPI . . . . . Y Journals . . . Y
Library . . . Y *Connections . D BTS proc . . . Y Bundles . . . Y
ATOMServices . Y CSD. . . . . . Y XMLTransform . Y MQCONN . . . . Y
JVMServices . Y Terminals. . . Y CICS System . Y Tasks . . . . Y
DUMPs . . . . Y VTAM Conn . . Y Statistics . . Y Tracing . . . Y
SHUTDOWN . . . Y
CICS Sysid: Z528 CICS Applid: IYDZZ528 TermID: TC82
F1= F2= F3=Exit F4= F5= F6=
F7= F8= F9= F10= F11= F12=Cancel
|
Figure 5-6 CINT: CICS SPI options
Last, we need to check the remote call options. From the Regions Options menu in Figure 5-3 on page 120, select option 5 for the DB2/IMS/MQ/CPSM Options.
Figure 5-7 shows the remote call options. If your environment uses any of these options, set the option to Y.
|
CIU250 CICS Interdependency Analyzer for z/OS - V5R3M0 2015/09/07
DB2/MQ/IMS/CPSM Resource Options for 11:21:25AM
CICS Sysid : DFTS CICS Applid : DEFAULTS
Modify the options and press Enter to update, or PF12 to Cancel.
Detect command types: Y=Yes, N=No
DB2 Options
Collect DB2 Resources . . . . . : Y
Collect resource name . . . . . : Y (Y/N) (Access the SYSIBM.SYSPACKSTMT
and the SYSIBM.SYSSTMT tables)
MQ Options
Collect MQ Resources . . . . . : Y
IMS Options
Collect IMS Resources . . . . . : Y
CPSM Options
Collect CPSM Resources . . . . : Y
CICS Sysid: Z528 CICS Applid: IYDZZ528 TermID: TC82
F1= F2= F3=Exit F4= F5= F6=
F7= F8= F9= F10= F11= F12=Cancel
|
Figure 5-7 CINT: Remote call options
We should have now set all the options required for a threadsafe collection.
Now you can start the collector, capture the data, and load the dependency data into the database. To load the data, you can run sample job CIUUPDB. Before submitting the job, change the collection ID to something meaningful that will help you identify your threadsafe collection. In our example, we use a collection ID of CICS510. In the ISPF editor for CIUUPDB, issue the following command and then run the job:
C _collid_ CICS510 all
Next, we look at how we run a threadsafe report in the CICS IA plug-in from the data we captured.
5.2 Running the load module scanner
Before you can make a program threadsafe, it must be linked with the attribute “reentrant”. CICS IA provides a load module scanner, which captures this information. In this section, we look at how to run a scanner and load the data into DB2 tables:
•CIU_SCAN_SUMMARY
•CIU_SCAN_DETAIL
The data store in these tables is used when we run a threadsafe report to obtain the reentrancy link attribute.
First, we must run a summary report against the load module data set. The sample JCL to run a summary report, which loads the data into DB2 can be found in SCIUSAMP(CIUJCLTS). You need to update the input load module data set name and the output data set name that holds the list of load modules that is used as input when running the DETAILED report. See Figure 5-8; we scan the load module data set “CICSIAD.GENAPP.V51.LOAD”.
|
//* _scan_ *
//* CICS LOAD DATASET TO BE SCANNED *
//* *
//* _ciudet_ *
//* Output dataset created by SCANNER SUMMARY JOB *
//* *
......
//INPUT DD DSN=CICSIAD.GENAPP.V51.LOAD,
// DISP=SHR
......
//INTMOD DD DSN=CICSIAD.GENAPP.DETAIL,
// DISP=(NEW,CATLG,DELETE),
// DCB=(RECFM=FB,LRECL=80,BLKSIZE=8000),SPACE=(CYL,(1,1))
|
Figure 5-8 Input for SUMMARY report
This job loads summary data into the DB2 table CIU_SCAN_SUMMARY and also produces a report as shown in Figure 5-9 on page 125.
|
CICS INTERDEPENDENCY ANALYZER Version 5.3.0
LOAD MODULE SCANNER - SUMMARY LISTING OF CICSIAD.GENAPP.V51.LOAD
Module Module Module Re- Language Possible
Name Length Language entrant Version Affinities Dependencies MVS
-------- -------- ---------- ------- -------- ---------- ------------
LGACDB01 00002540 COBOL II Y LE 0 9 0
LGACDB02 00001D60 COBOL II Y LE 0 6 0
LGACUS01 00001BC8 COBOL II Y LE 0 7 0
LGACVS01 00001BC8 COBOL II Y LE 0 9 0
LGAPDB01 00003868 COBOL II Y LE 0 12 0
LGAPOL01 00001B98 COBOL II Y LE 0 8 0
LGAPVS01 00001AA8 COBOL II Y LE 0 6 0
LGASTAT1 00001AA0 COBOL II Y LE 2 7 0
LGDPDB01 00001D30 COBOL II Y LE 0 7 0
LGDPOL01 00001B88 COBOL II Y LE 0 7 0
LGDPVS01 000019F8 COBOL II Y LE 0 6 0
LGICDB01 00001F70 COBOL II Y LE 0 7 0
LGICUS01 00001D58 COBOL II Y LE 2 10 0
LGICVS01 00001E50 COBOL II Y LE 7 10 0
LGIPDB01 00005E48 COBOL II Y LE 0 9 0
LGIPOL01 00001A88 COBOL II Y LE 0 7 0
LGIPVS01 00001870 COBOL II Y LE 0 3 0
LGSETUP 00003CA8 COBOL II Y LE 7 83 0
LGSTSQ 00001888 COBOL II Y LE 1 4 0
LGTESTC1 00002B10 COBOL II Y LE 8 26 0
LGTESTP1 00002898 COBOL II Y LE 0 22 0
LGTESTP2 000026E0 COBOL II Y LE 0 21 0
LGTESTP3 000026C8 COBOL II Y LE 0 21 0
LGTESTP4 00002868 COBOL II Y LE 0 16 0
LGUCDB01 00001E50 COBOL II Y LE 0 7 0
LGUCUS01 00001AA8 COBOL II Y LE 0 7 0
LGUCVS01 00001B88 COBOL II Y LE 0 9 0
LGUPDB01 000031B8 COBOL II Y LE 0 8 0
LGUPOL01 00001C60 COBOL II Y LE 0 7 0
LGUPVS01 00001C80 COBOL II Y LE 0 9 0
LGWEBST5 00004D68 COBOL II Y LE 10 49 0
SSMAP 000028B0 0 0 0
CICS INTERDEPENDENCY ANALYZER Version 5.3.0
LOAD MODULE SCANNER - SUMMARY LISTING OF CICSIAD.GENAPP.V51.LOAD
LOAD LIBRARY STATISTICS
=================================================================
Total modules in library = 32
Total modules scanned = 32
Total CICS modules/tables (not scanned) = 0
Total modules in error (not scanned) = 0
Total modules containing possible MVS POSTs = 0
Total modules containing possible Dependency commands = 31
Total modules containing possible Affinity commands = 7
Total ASSEMBLER modules = 0
Total C/370 modules = 0
Total COBOL modules = 0
Total COBOL II modules = 31
Total PL/I modules = 0
Total number of possible Dependency commands = 419
Total number of possible Affinity commands = 37
|
Figure 5-9 Sample summary report
We now need to run the DETAIL report to obtain the linkage attributes for the load modules in load library CICSIAD.GENAPP.V51.LOAD. The sample JCL to run a DETAILED report, which loads the data into DB2, can be found in SCIUSAMP(CIUJCLTD). Again, you need to update the input load module data set name and the detail input data set name that holds the list of load modules that was created by running the SUMMARY report. See 5.3, “Running the threadsafe report in the plug-in” on page 127; we scan the load module data set “CICSIAD.GENAPP.V51.LOAD”.
|
//* _scan_ *
//* CICS LOAD DATASET TO BE SCANNED *
//* *
//* _ciudet_ *
//* Input dataset created from a SCANNER SUMMARY JOB *
//* *
......
//INPUT DD DSN=CICSIAD.GENAPP.V51.LOAD,
// DISP=SHR
.....
//DETAIL DD DSN=CICSIAD.GENAPP.DETAIL,
// DISP=(OLD,DELETE)
|
Figure 5-10 Input for DETAIL report
This job loads the DETAIL data into the DB2 table CIU_SCAN_DETAIL and also produces a report as shown in Figure 5-11 on page 127.
|
LOAD MODULE SCANNER - DETAILED LISTING OF CICSIAD.GENAPP.V51.LOAD
Module Name - LGACDB01 / Load Module Length - 00002540 / Module Entry Point - 00000020
Offset Storage Content (HEX) EDF DEBUG Possible Command Type Depcy Affinity
-------- -------------------------------------------------- --------- ------------------------ ---------------- ------ --------
00000266 4A048002078002080000000000 00057 FORMATTIME TIME Yes
0000027B 4A028000078000000000000000 00057 ASKTIME ABSTIME TIME Yes
00000290 2006D000270000010200000101 00047 GET COUNTER Yes
000002CC 0E02E0000700000100 00059 LINK PROGRAM Yes
000002DD 0E02E0000700000100 00059 LINK PROGRAM Yes
000002EE 0E02E0000700000100 00058 LINK PROGRAM Yes
00000343 0E02E0000700000100 00045 LINK PROGRAM Yes
00000354 0E02E0000700000100 00044 LINK PROGRAM Yes
00000376 0E0C80000700006080 00042 ABEND PROGRAM Yes
Total possible Affinity commands = 0
Total possible Dependency commands = 9
Total possible MVS POSTs = 0
|
Figure 5-11 Sample DETAILED report
5.3 Running the threadsafe report in the plug-in
After we collected and loaded threadsafe data into the DB2 database, we can then run a threadsafe report in batch by using sample job CIUJTSQ2 or in the CICS IA plug-in. In this book, we run the report in the plug-in.
First, we reduce the amount of data we query in the plug-in by setting a scope to the collection ID that we used in the CIUUPDB load job, in our case CICS510. In the Collection IDs view, right-click your collection ID, CICS510, and select “Set as current scope” as shown Figure 5-12.

Figure 5-12 Set current scope
You can run a threadsafe report against a CICS region, a transaction, or a program. In this book, we run a region Thursdays report. From the Regions folder in the IA Navigation view and against your CICS region, select Report → Threadsafe Report, as shown in Figure 5-13.

Figure 5-13 Running a threadsafe report
This action opens the Threadsafe Report view as shown in Figure 5-14 on page 129. This report is broken into two parts. The top part shows the list of programs and a corresponding summary for each program. To see the summary, select the program and the following data is shown.
Total CICS calls
This value is the total number of CICS calls.
Threadsafe calls
This value is the total number of threadsafe commands, that is, commands that can run an open TCB and do not cause a swap back to the QR TCB.
Non-threadsafe calls
This value is the total number of CICS commands that are not threadsafe in that they need to run on the QR TCB and therefore can cause a TCB swap from an open TCB back to the QR TCB.
Total number of indeterminate calls
This value is the number of CICS calls where we do not have sufficient information to decide whether the call is threadsafe or not.
Total number of DB2 calls
This value is the total number of DB2 calls. DB2 calls moved to run on the open TCB in CICS TS V2.2.
Total number of IBM MQ calls
This value is the total number of IBM MQ calls. IBM MQ calls moved to run on the open TCB in CICS TS V3.2.
Total number of IMS calls
This value is the total number of IMS calls. IMS/DLI calls moved to run on the open TCB in CICS TS V4.2 when connected to the required level of IMS that supports this feature.

Figure 5-14 Threadsafe Report view
Dynamic calls
This value is the total number of dynamic COBOL calls that have been identified. You need to know if a program is dynamically called because a dynamically called program takes its resource definition attributes from the calling program. For example:
•Program PROGA is defined with CONCURRENCY QUASIRENT
•Program PROGB is defined with CONCURRENCY THREADSAFE
•Program PROGA dynamically calls program PROGB
You might think that program PROGB is now running as threadsafe but in fact it is still running as quasi-reentrant. This fact can be even more critical if PROGB calls PROGA. You might have decided that PROGB can be threadsafe but PROGA must remain as quasi-reentrant because it has commands that are threadsafe inhibitors and could lead to data integrity issues if it runs on an open TCB.
Threadsafe inhibitor calls
This value is the total number of CICS calls that could lead to data integrity issues. Following are the commands:
•ADDRESS CWA
•GETMAIN SHARED
•ENABLE EXIT PROGRAM
•LOAD HOLD
All of these commands are used to address areas of storage associated with the program. Before making a program that contains any of the commands threadsafe further investigation is needed to understand if the area of storage addresses is read only or can be updated. Programs using shared data must be serialized. This serialization can be done by leaving the program as quasi-reentrant so it goes back to the QR TCB. Or if you want to run in an open environment, you must use one of the following serialization techniques:
•CICS API enqueue/dequeue
•CICS SPI enqueue/dequeue
•Compare and swap
Total number of CPSM calls
•Threadsafe
•Non-Threadsafe
In CICS IA V5.2, we added the collection of CPSM commands. Currently, all CPSM commands are not threadsafe and run on the QR TCB.
For each program we also show:
•Library data set name
•API attribute
•Concurrency attribute
•Program storage execution key
•Region storage protection key
•Linkage reentrancy indicator
•CICS release level
These facts are all good to know when analyzing whether to make your program threadsafe.
The lower part of the Threadsafe Report view as shown in Figure 5-14 on page 129 shows us the actual commands issued by the program selected in the top part. We show the following commands:
Command type CICS, DB2, MQ, IMS, or CPSM
Function The actual command, for example, LINK
Type The resource type, for example, PROGRAM
Offset Offset of the command within the program
Use Count The number of times the command has been invoked
Threadsafe For a CICS command, is it threadsafe
Inhibitor For a CICS command, is it a possible inhibitor
Selecting the threadsafe report input parameters
The threadsafe report view allows you to change the input parameters and rerun your threadsafe report from the toolbar found in the top of the view as shown in Figure 5-15.

Figure 5-15 Threadsafe input parameters
You can change the following input options and then select the green arrow icon to rerun the report:
•Collection ID
•Region
•Program
•CICS TS Level
The CICS TS Level input parameter can be set to the CICS release level in which the data was collected or can be set to a specific release level as shown in Figure 5-16. This feature can be very valuable if you collected data on your existing CICS release say V4.1, but want to see what the report would look like if you went to CICS V5.2.

Figure 5-16 Choose your CICS level
5.3.1 Saving and printing threadsafe reports
In this section, we save our threadsafe report and then retrieve it for printing.
First, ensure that the threadsafe report view is active then select the option File → Safe from the upper-left corner or enter CTRL+S. The Save report window opens. Choose the threadsafe folder and enter an appropriate name as shown in Figure 5-17.

Figure 5-17 Saving a threadsafe report
Select OK and your report is saved.
|
Note: To save detailed information, you must first retrieve the detailed information by selecting the program and tick the “Save detailed program data” box in the Save report view.
|
All reports are stored in the Reports folder in the IA Navigation view. To retrieve your report, right-click the report and select Open Report as shown in Figure 5-18.

Figure 5-18 Opening a threadsafe report
The report is then displayed in a simple HTML format as shown in Figure 5-19.

Figure 5-19 HTML threadsafe report
To print the report, right-click anywhere within the report and select “Print” Preview” or “Print,” as shown in Figure 5-20.

Figure 5-20 Select “Print Preview”
5.4 Using the command flow data to analyze TCB swaps
As well as using the CICS IA threadsafe report to assist with threadsafe analysis, you can also use the Command Flow feature. The Command Flow feature was originally added for exactly this function and can assist you in identifying where the actual TCB switches occur.
Information about how to configure, load, and use the Command Flow data can be found in Chapter 8, “Command Flow feature” on page 197.
In this section, we focus on the Command Flow features that assist with threadsafe analysis. We use the Command Flow data captured for transaction SSC1 as described in 8.1.3, “Using the IA plug-in to collect Command Flow data” on page 204.
5.4.1 Identifying TCB switches
Right-click the required task and select Show Execution as shown in Figure 5-21.

Figure 5-21 Show Command Flow execution
This action opens the Command Flow view as shown in Figure 5-22.
This view is broken down into three parts:
•TCB Modes Used: The command execution count by TCB mode
•TCB Mode Switches: The command count causing a TCB mode switch
•The execution tree: The command execution tree
In this section, we look at the first two parts. The execution tree is described in detail in 8.3.1, “The Command Flow Execution view” on page 213.

Figure 5-22 Command Flow execution
TCB modes used
This section lists all the commands used under each TCB mode, as shown in Figure 5-23.

Figure 5-23 Commands by TCB mode
TCB mode switches
This section lists the commands that cause a TCB switch, as shown in Figure 5-24.

Figure 5-24 TCB mode switches
You can see that one DB2 SELECT command causes a switch from the QR TCB to the L8 TCB.
If you select the command, it takes you to that command in the execution part of the view, as shown in Figure 5-25.
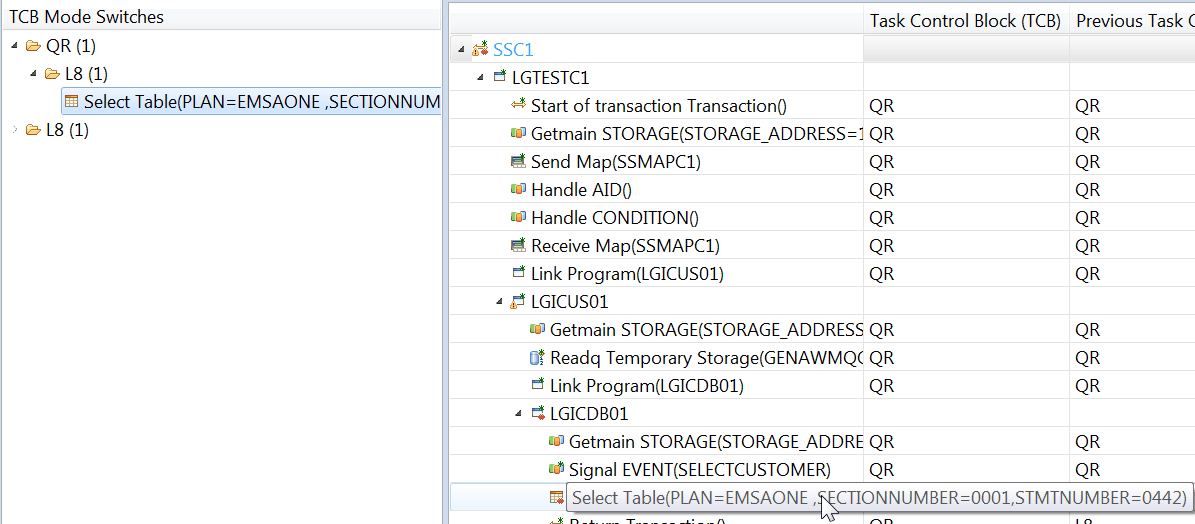
Figure 5-25 Select the DB2 command
If you look carefully, you also see a red diamond icon on the command as shown in Figure 5-26. This indicates that this command causes a TCB swap.
Figure 5-26 The red diamond ICON
For threadsafe analysis, you might want to modify the view to add the columns shown in Figure 5-27.

Figure 5-27 Add more columns
For more information about customizing columns, go to “Customizing columns” on page 215.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
