Connecting to the Internet wirelessly has become ubiquitous. (For details, see Chapter 9, “How Wireless Connections and WiFi Work.”) Many people have wireless networks in their home, and in addition, many corporations are setting up wireless networks as well. They do it because it’s much less expensive to set up a wireless network than a wired one, and more convenient for users as well—they can connect to the Internet and corporate network anywhere in the building, not just when they’re next to an Ethernet port.
People also connect to the Internet when they travel, by using hot spots at cafes, airports, and other locations.
This wireless technology is called WiFi. But with all of WiFi’s convenience, comes danger. The same technology that lets you browse the Web from your back porch can let invaders hop onto your network from outside your house or apartment.
By its very nature, WiFi is an open technology. A wireless router broadcasts its presence to any device with a WiFi adapter within its range, and if the router is unprotected, anyone who wants to can connect to it and use the network. That makes it easy for intruders to get in.
A common kind of intruder is called a “war driver.” These people drive through areas of cities and suburbs known for having WiFi networks, and they search for unprotected networks they can break into. They use software that makes it easy to find unprotected networks. Some use high-powered antennas so they can find as many networks as possible. But, in fact, they don’t even need this kind of equipment to get into networks. Software built directly into Windows XP, for example, makes it easy for anyone to find and connect to an unprotected network.
When war drivers target a business network, they may be looking for proprietary business information, or they may be looking to do malicious damage. When they target a home network, they may look for personal information, such as credit card numbers or they may also be looking to damage computers, as well.
But WiFi intruders can cause other problems—and these may even be more serious than stealing information or damaging computers. They can use the network for illegal activities, and if those activities are uncovered, it will look as if the owner of the network is guilty, because the war driver will be long gone.
Computers aren’t the only devices that connect to the Internet wirelessly; cell phones do as well. Most cell phones are at heart computers—computers that are surprisingly powerful, and pack more power and memory than large computers of a dozen years ago.
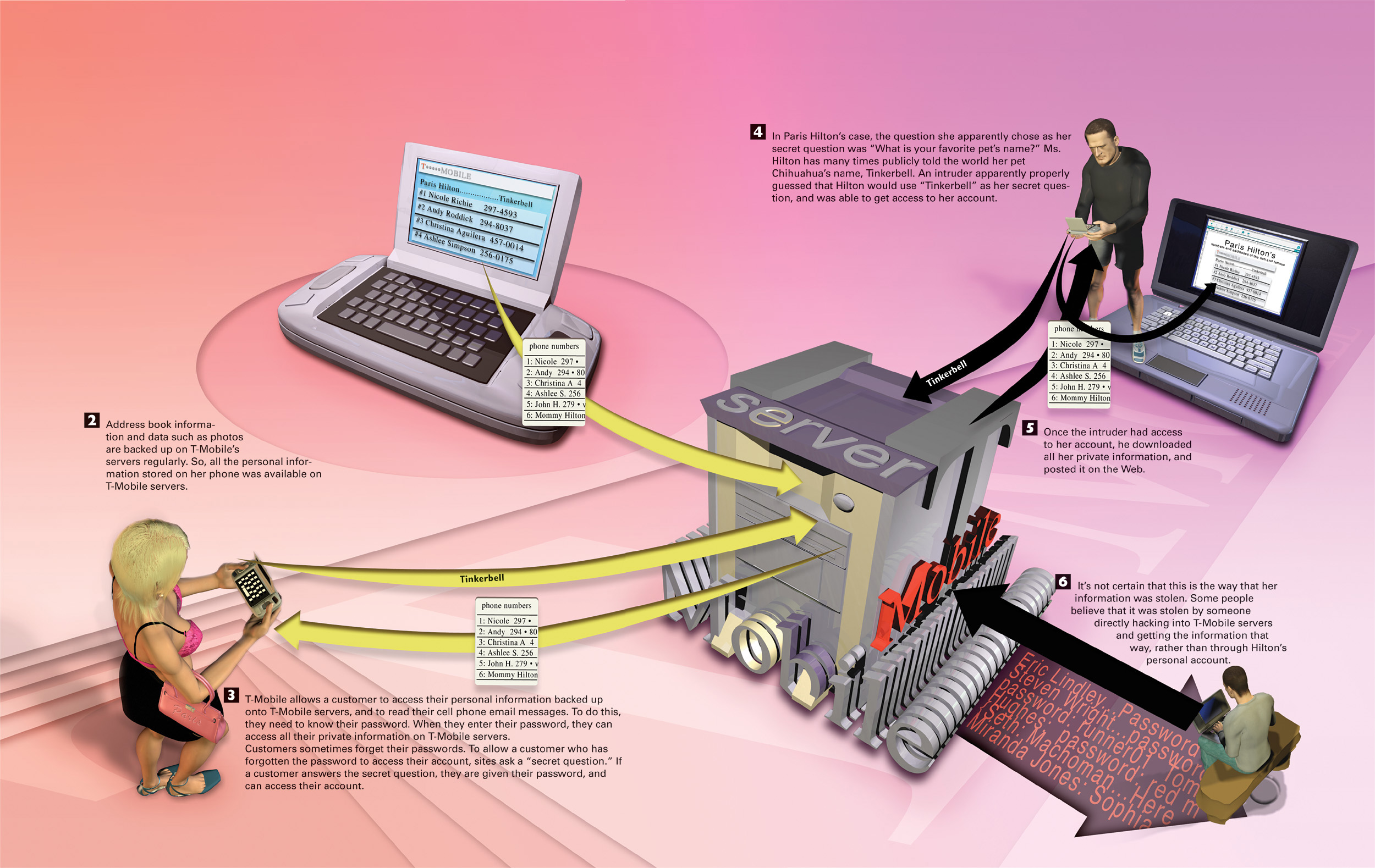
And where there are computers, there are hackers. As cell phones get increasingly complex and powerful, they become more vulnerable to viruses and hackers. And as they get more powerful, cell phones have more data that hackers want to use. For example, B-list celebrity Paris Hilton had her cell phone hacked, and her personal address book and intimate photos that were on the phone were made available to the world when they were posted on the Internet.