Hackers are equal opportunity attackers—they attack individuals as well as websites by using a variety of software and malicious programs. Among hackers’ many targets are Internet service providers (ISPs)—companies that sell access to the Internet. A hacker might target an ISP for several reasons: He might be angry at the ISP or at someone using the ISP, or he might attack the ISP for the mere thrill of it. Hackers also often attack big websites as well.
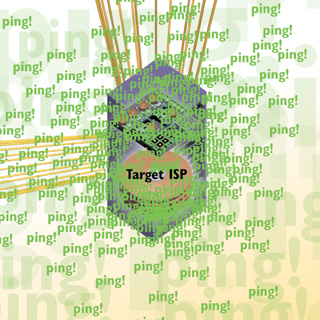
One of the most common attacks against an ISP or websites is a denial of service (DOS) or distributed denial of service (DDOS) in which a hacker incapacitates a network by flooding it with extraneous traffic. There are several ways that a hacker can launch a DOS or DDOS attack. One of the most popular ways is called a smurf attack, or smurfing. In a smurf attack, a hacker floods the ISP with so many garbage packets that all the ISP’s available bandwidth is used up. The ISP’s customers can’t send or receive data and can’t use email, browse the Web, or use any other Internet service.
In a smurf attack, hackers exploit a commonly used Internet service—ping (Pocket Internet Groper). People normally use ping to see whether a particular computer or server is currently attached to the Internet and working. When a computer or server is sent a ping packet, it sends a return packet to the person who sent the ping, which in essence says, “Yes, I’m alive and attached to the Internet.” In a smurf attack, hackers forge the return addresses on ping requests so that, instead of going back to them, the return packets go to the hackers’ target ISP. The hackers can use networks attached to the Internet as a way of relaying their ping requests and magnifying each ping request many times. In this way, a hacker can use networks attached to the Internet to flood the ISP with so many return ping packets that the ISP’s customers can’t use the ISP’s services. Hackers can use multiple networks attached to the Internet in a single smurf attack. Smurf attacks are hard to ward off because the ping answering packets come from legitimate networks and not from the hacker.
Hackers don’t just target ISPs, of course. They attack individuals as well. As you’ll see in the illustration later in this chapter, hackers can take over people’s computers to delete and steal files, steal personal information and passwords, and even use the person’s computer as a launch pad for attacks on ISPs and websites.
One of the most insidious dangers on the Internet is zombies, computers that have been taken over by hackers, and will do their bidding. The reason for the name is obvious—in non-computer terms, a zombie is someone who has been dead, and then resurrected to do the bidding of a zombie master. The zombie has to follow the commands of his master, and has no will of his own. Hackers take over ordinary PCs and turn them into zombies.
How do hackers get into your PC to turn it into a zombie or to attack it in other ways? Often, right from the Web via your web browser, or else via email—and you’ll see both means of attacks illustrated in the following pages.
Note
Those who run zombie networks look to infect computers that have broadband cable and DSL connections, because they can send out many more messages per minute than computers connected to the Internet via dial-up. Broadband-connected PCs are also online all the time, while dial-up PCs are only available sporadically, when they have dialed into their ISPs.





