This chapter is dedicated to one of the oldest methods of gaining unauthorized access to target systems: dial-in penetration over telephone lines. While this is no longer the primary means of gaining access, dial-in vulnerabilities remain one of the most common weaknesses in networks today. Insecurely configured modems listening for a connection from anywhere represent a significant vulnerability. We identify listening modems by using mass-dialing software to dial blocks of phone numbers owned by an organization. This is more commonly called war dialing.
Through war dialing, we are looking for a modem connected to a telephone line that is listening for incoming connections. These modems can be a part of a modem bank or be connected to desktop machines or routers. Organizations may also have modems connected to facilities control programs, voicemail systems, air conditioning systems, and PBXs (the main controllers for a telephone system). Exploitation of these systems can cause significant problems and loss for organizations.
Organizations normally use dial-in modem banks for remote user access for employees who travel, telecommute, or choose to work from home after hours. Companies often designate telephone lines for their hardware or software vendor partners to dial in remotely to manage, upgrade, and perform maintenance. These vendors have dial-in access to these lines and generally have (default) user names and passwords for authorization. Routers are possibly the most common hardware devices that support dial-in access through modems. These modems should be disabled or the modem or telephone line simply unplugged, except for the specific times when vendors are set to perform maintenance. However, administrators often forget to do so, leaving a potential avenue of attack open to the public.
Among all the targets for war dialing, the largest security hole is the rogue modem: an unknown modem connected to a user's desktop. With a rogue modem, desktop users may believe they can hide their Internet surfing habits and personal e-mail from their employers. In addition, a user may use an unauthorized, rogue modem to log into their work machine from home.
The risk of this scenario is significantly increased when the desktop user installs remote management tools, such as the popular pcAnywhere. At times users can unknowingly allow anyone with a modem to simply dial in and connect to the box (pcAnywhere can be configured to not ask for a password). This leaves the desktop vulnerable to external penetration. Even without pcAnywhere, it is not uncommon to see file sharing enabled. This potentially leads to the compromise of all the data on the machine. While the rogue modem is the primary target of war dialing, any modem can provide a potential entry point to the target network.
War dialing involves randomly calling each number in your target range in search of a listening modem. Once all listening modems are identified, brute force or strategic guessing attempts are made on the user name/password challenge (sometimes only passwords are necessary) to gain unauthorized access.
In order to perform the dialing, we program the war dialing software (several are discussed in detail later in this chapter) to dial the numbers and record the responses it receives. The software produces two outputs: (1) a carrier log identifying all dial tones found, busy signals, and potential modems and (2) a carrier hack file that can even identify the listening systems through overly descriptive banners. The banners may indicate the system is a router, identify the OS, or identify the application.
This is the penetration part of dial-in penetration. After we find the listening modems, we can attempt to gain access. The war dialing software can be programmed to attempt access whenever it receives a user name/password challenge. There are two approaches to this. The first is to use a brute force process with the largest list of user names and passwords you can find. Alternatively, a comprehensive list of default user name/password pairs can be used. The second option has been found to produce better results because it takes less time to complete and can often be just as successful since system defaults on dial-in access are more likely to be left in place than for other networking devices.
In addition, if the number of modems identified is small and the carrier hack file offers an indication of the kind of system the modem is connected to, you may elect to attempt access manually. This can be done through a hyper terminal program where you simply dial the modem and use defaults or strategically guess the user name/password pair.
For example, if you come across a Cisco router, you can try the default pairs, such as cisco/cisco or enable/cisco. Often, Cisco routers request only a password, in which case commonly used passwords, such as c, cc, cisco, and Cisco router, can be attempted.
If either method works, you have gained access to the system through the telephone network without having to go through the Internet. However, be warned—this can be a slow process since most systems hang up after three attempts.
In addition, by using Web-hacking techniques you may be able to externally exploit systems in a DMZ but not have access to internal systems. Using the DMZ access, you could install sniffers and keyboard loggers on the exploited systems to capture IDs and passwords. Since many people use the same user ID and password on multiple systems, you can use the captured information on the dial-in systems. This essentially enables you to bypass the firewall controls.
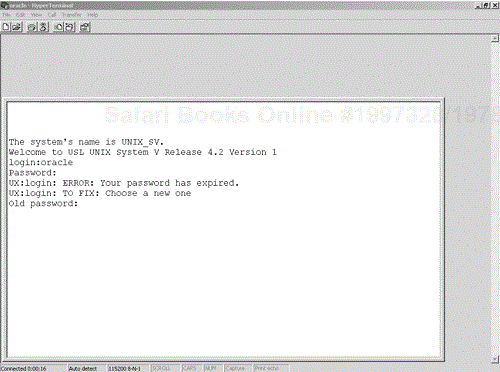
When you dial a number and receive a connection, there are several things you may see. The computer you have dialed may show you a banner describing what it is and asking for a user name and password, as shown in Figure 6-1, for a connection to a UNIX host. This illustrates a user account (oracle) that can gain access with a blank, default password. Note in this example that the user was asked to set the password. This may have been the user's first time dialing into the system.
As in the case of Cisco routers, you may be requested to present only one field, either the login name or password. At times, successful connections result in only a blank screen where you need to hit Enter for the system to prompt you with a user name/password challenge. There are other cases where no authentication is demanded and you are simply connected to the listening service. For example, pcAnywhere can be configured to allow access to any calling pcAnywhere client.
Representatives of a client organization may give you a set of numbers to dial. However, they may also want to know how easy it would be for a hacker to first get the numbers and then find the rogue modems. In this case, obtaining numbers is somewhat of an endeavor in social engineering.
The first step in gathering phone numbers is to identify the general ranges of numbers associated with the organization. For this piece, we are looking for area codes and prefixes. With these we deduce the range in which the target company's phone numbers lie. For example, if the target company's number is (123) 456-xxxx, then we know that the numbers we want to dial are somewhere within the 10,000 numbers between (123) 456-0000 and (123) 456-9999.
Further, whatever the target company's phone numbers are, they likely form one (or more) continuous blocks of phone numbers within this range. For example, if you determine two numbers at the company to be (123) 456-7830 and (123) 456-7925, the company probably has all the numbers between 7830 and 7925. You can go so far as to postulate that the company may have all (123) 456-78xx and -79xx numbers. Therefore, with even a small collection of sample phone numbers, you should be able to determine the numbers you want to dial. Keep in mind that telephone numbers, to some extent, are geographically assigned. If you know where your target company is located, you will be able to find its area code and, to a lesser extent, its prefix.
Sample phone numbers can be found from various places, including Web sites, company literature, the phone book, and even telephone directory assistance, which should be able to give you the phone number for any company in the country. Often multiple numbers are listed; ask for all of them. The public library likely has phone books for all regions of the country that also contain this information.
You can use these numbers to get additional numbers at the target company. For example, you can call a receptionist and ask for the fax number; this usually does not require any cover story at all. You can pretend to be interested in employment at the company and ask for the number of the human resources department or person. Similarly, you can ask to speak to someone in the benefits department and even a hiring manager, saying you want to get an idea of what the company is looking for in a new employee. If your target has several departments, you can ask for the number for another receptionist. Often, if you ask for the company president or a director, you will get his or her secretary's phone number. It is also fairly easy to get the number to the security office or the mail room (to see if your package was shipped or has arrived). This is social engineering, a topic we cover in more detail in Chapter 8.
With these sample numbers, you can develop your target ranges. You can then pick random numbers within this range to screen. For example, if you have (123) 456-7830 and (123) 456-7925 as two sample numbers, try (123) 456-7891 and see if it belongs to anyone at the company.
There are ways to get the entire phone number range. Again, you should make sure your engagement letter with the client covers these types of activities in case someone questions their legality. Contact the company's telephone billing office and ask someone to verify the telephone number ranges. You can do this by making up any story you like to cover your interest in their telephone numbers. For example: pretend to be calling from the local phone company performing a routine audit of the phone company's billing records. Ask to verify the target company's telephone numbers. If you sell yourself well, the employees may just tell you what they are. If they don't go for it, kindly commend them on their interest in security and ask if they would simply confirm or deny the telephone number ranges you tell them. Give them the ranges you have ascertained, a bit at a time, starting with those that you are most confident belong to them. Now they should be more at ease discussing their phone numbers with you and you may be able to get all the numbers you need.
War dialing is still considered a threatening activity, and the authorities do remain on the lookout for evidence of possible war dialing instances. Be certain to verify all number ranges with the target organization prior to beginning. The organization should be able to positively identify all numbers as belonging to them. Additionally, if you are going to war dial, please make sure to have your client's signed authorization letter with you at all times. There are several things you should remember when war dialing in order to make sure you avoid suspicion of criminal activity.
Call during off hours. Dial-in penetration is best performed after working hours so that people sitting at their desks don't answer the phone when your war dialing software calls.
Do not dial numbers sequentially. This is a crucial point. In an effort to thwart dial-in penetration attempts several years ago, phone companies modified their networks to monitor for and generate an alert when consecutive numbers are dialed from a single phone number. Therefore, it is imperative that you configure your war dialing software to randomize the phone numbers you dial. If the phone company notices sequential numbers being dialed, it may disable your phone line and notify a certain law enforcement agency. Don't be surprised if representatives of that law enforcement agency contact you in regards to your actions.
Go slowly. You may want to spread your war dialing over a large period of time. Just because you have the capability to dial 10,000 numbers a night doesn't mean you have to. You could spread 10,000 numbers out over two or three nights (or weeks, given your time constraints) to reduce the likelihood that you will be noticed.
There are several tools available for war dialing, both commercial software and freeware. Our experience has identified the following tools as the most useful:
ToneLoc
THC-Scan
TeleSweep
PhoneSweep
The first two are freeware. ToneLoc is, perhaps, the original war dialing software tool available for the masses. THC-Scan, which stands for The Hacker's Choice-Scan, is essentially an upgraded version of ToneLoc.
TeleSweep and PhoneSweep are commercial tools that can perform testing much faster and are quite expensive (especially when compared to freeware). These products have the ability to coordinate dialing across numerous telephone lines simultaneously. This is the significant contributor to their speed advantage. In addition, they are better than freeware at identifying the types of modems and systems that respond.
Client OS: DOS
Description. ToneLoc is perhaps the oldest of the commonly used war dialing software package available. It is fairly straightforward to install and not terribly complicated to use.
There are only a few configuration settings that must be made. The command tlcfg brings up the configuration screen, shown in Figure 6-2. This screen has six pull-down menus containing all the screens on which ToneLoc can be configured. Under the Files pull-down menu are several output files, including the Log file, which is a full record of ToneLoc's actions; the Carrier Log file, which logs all detected carriers; and the Found file, which logs the carriers and tones detected. The black list is a list of numbers that should never be dialed. As you move the cursor over a particular line, a brief description of the setting is displayed at the bottom of the screen. This descriptive line is available throughout ToneLoc.
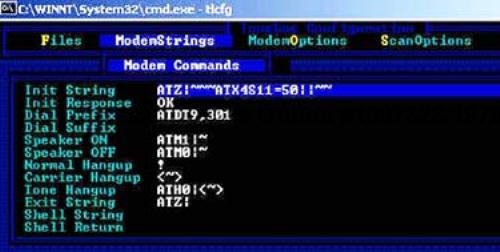
The dial prefix (the area code in this context) can be set under the ModemStrings pull-down menu, shown in Figure 6-3.
Under the ModemOptions menu, shown in Figure 6-4, you can configure various settings that enable ToneLoc to properly access the modem, such as the Serial Port, Port IRQ, and Baud Rate.
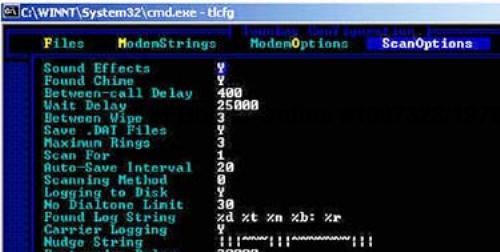
Additional settings, such as the Nudge String and Carrier Logging (do set to Y) can be set on the ScanOptions screen, shown in Figure 6-5. Be careful when setting the Between-call Delay option. You may have to resist the urge to make this as small as possible because a small delay may not give ToneLoc enough time to complete the telephone call and determine whether there is a carrier present.
When you have made your changes, save and quit the configuration screen (use the Quit pull-down menu). ToneLoc can then be launched by a command similar to the following:
TONELOC Run1.txt 123-XXXX /r:1000-6999 /S:20:00
In the command above, the first three digits of the phone number are specified and the final four digits are specified in the range /r: command. The /S: option is the time at which to start the war dialing. ToneLoc runs on a 24-hour clock.
Client OS: DOS
Description. THC-Scan can be considered a modification of ToneLoc. It offers all of the same functionality of ToneLoc and further allows the telephone numbers to be dialed to come from a noncontinuous range. It also runs on DOS, including all version of MS-DOS, DR-DOS, and PC-DOS. It also runs on Linux and BSD in the DOSEMU.
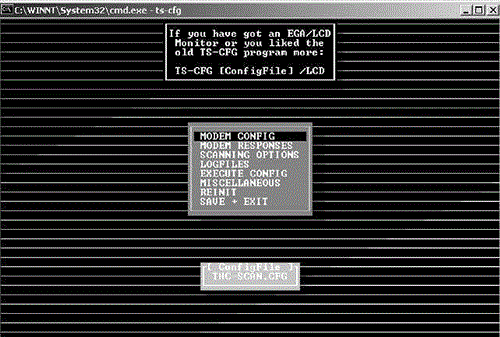
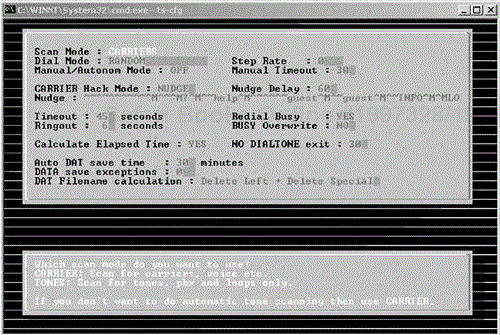
Like ToneLoc, THC-Scan is straightforward to install and configure, and it features fairly extensive documentation, including a helpful README file. The command ts-cfg brings up the configuration screen, shown in Figure 6-6.
If you are going to set the numbers to dial from the command line, set the area code of those numbers on the Modem Config screen, shown in Figure 6-7. A hang-up command (used to disengage the connection) and various other options can be set on this screen as well.
The arrow keys scroll between the settings and each displays an explanation of the setting in the lower window of the screen. The documentation provides further explanations of these settings.
Additional options must be set under the Scanning Options screen, shown in Figure 6-8. For example, you can set a timeout for calling, whether or not to redial busy numbers, and, importantly, whether or not to dial numbers randomly. As mentioned above, this is a critical setting, so remember to ensure that this is set to RANDOM. Also, make sure to enable the Nudge setting so that you can view any login screens that are accessed while dialing.
When it is all ready, THC-Scan can be kicked off by the following command:
thc-scan filename.dat /m:123-xxxx /r:1000-9999
The /m:, or mask, option specifies the prefix and range of the telephone numbers to be dialed. The prefix indicates the digits of the phone numbers that are common to all the numbers you want to dial; the range (the /r: option) specifies the numbers that go into the spots marked with x's in the command. In other words, the above command will dial all numbers between 123-1000 and 123-9999. The mask can specify three to six digits.
The data is stored in the file filename.dat. The start and the end times can also be specified on the command line.
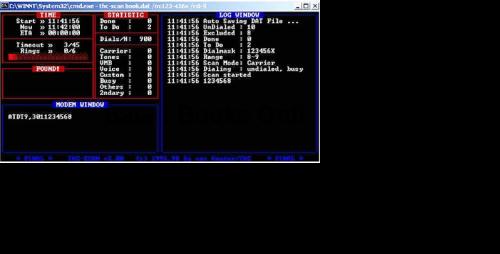
While THC-Scan is executing, its displays the screen shown in Figure 6-9, allowing you to track the number of carriers detected, busy signals, and overall progress.
THC-Scan can attempt to use a brute force attack on any login screens it discovers. (The THC Login Hacker tool, also free, is required for this.) This is best performed by taking the list of modems THC-Scan has identified and redialing them with THC-Scan and the THC Login Hacker tool to connect to and attempt a scripted brute force login process.
Client OS: Windows 98 or NT
Description. TeleSweep Secure by SecureLogix actually comes in two forms. There is a Solution System version which includes the war dialing software as well as the hardware necessary to implement TeleSweep's distributed war dialing capability. The company also sells a software-only version for which you must provide the hardware.
TeleSweep Secure has a manager/agent type of architecture with a central manager able to control agent dialers, possibly located remotely, which then perform the war dialing over a modem or modem bank to which the agent dialers are connected. If your target has locations across the country, a dialer can be placed in the local calling area of each location while still being controlled by the central manager. This will save on long distance charges, a frequently overlooked cost of this activity. Triple Data Encryption Standard (DES) encryption is available for manager/agent dialer communication.
As a distinction from the freeware tools, TeleSweep performs automatic system identification. In the version current at the time of this writing, the company claimed that TeleSweep could identify 48 systems by name. This removes the necessity to spend time reading the carrier log file and system banners to determine to what type of system you have connected.
TeleSweep can further attempt to use brute force at login prompts and even contains lists of standard logins (user names and passwords) for identified systems. The number of modems used in war dialing is not restricted by TeleSweep. The product works with Hayes-compatible modems, but Zoom modems are recommended.
Client OS: Windows 9x/NT
Description. PhoneSweep from SandStorm Enterprises can also use multiple modems (as many as 48 with the Enterprise version) to perform war dialing. While PhoneSweep is compatible with Hayes AT–compatible modems, there is a list of modems with which the product is especially recommended, including AOpen External Box Modem FM56-EX, Multi-Tech Systems MultiModem 56K Voice/Data/Fax, Zoltrix FM-VSP56e2 and FM-VSP56e3, and Psion Dacom's Gold Card Global PC Card. It is not recommended with US Robotics modems or Winmodems.
PhoneSweep can identify over 250 remote access systems by name (as of this writing). However, PhoneSweep places a restriction on the number of phone numbers that can be dialed in a single profile. This number depends on the version of the product you have licensed. Naturally, the more phone numbers in a profile, the more expensive the product. It also requires the use of a specific hardware dongle.
PhoneSweep can also perform automated brute forcing of any login prompts it comes across with user-specified user name and password files. However, it does not contain default account information for identified systems.
Remember that although the commercial war dialers come with multiple payment options (depending on how much of the product you chose to license), they are quite expensive, so it is important to balance their added functionality with their cost.
In one engagement, we were asked to war dial a client's entire phone bank. The client wanted to identify any insecure dial-in access among its dial-in modem banks, routers, and potential rogue modems on employee desktops. Since there is less chance users may disconnect modems during work hours or when they leave for the day, we performed the testing during both working and nonworking hours. The tests were scheduled for between 2:30 p.m. and 5:00 a.m. each day for several days.
Our approach was to run the war dialer and then analyze the carrier log for potential numbers to examine more closely. We wanted to run default password pairs against some and try a brute force method against others. To brute force the authentication challenge, we relied on the THC Login Hacker. The “surgical strike” approach was performed manually using hyper terminal.
Among the targets we identified were dial-up modems that issued a user name/password challenge, a few routers and servers that had open modem lines (which we learned were for vendors to dial in and service the machines), and even a rogue modem or two.
For the dial-in modem bank, we did not have even a list of employees and were unaware of any account lockout that may be in place. Therefore, we made limited access attempts and stuck to trying very generic accounts, such as “new user/<blank password>,” “admin/admin,” “admin/password,” and so on.
We were not successful gaining access this way. We had far greater success with the lines directly to routers and servers that were generally reserved for vendors. Vendors often have dial-up connections to their products to perform remote management and/or to upgrade software in accordance with the service agreement. Ideally, the lines should be active when they are specifically requested for a certain purpose (for example, to apply the latest Oracle patch) and removed as soon as they have finished their work. However, we do not live in an ideal world. These lines turned out to be fairly straightforward to compromise. For one thing, the banner identified the hardware and software running on the host. With this information, you can look up all default accounts for that hardware and software. Not surprisingly, the defaults work on such accounts all too often. Since multiple engineers from the vendor may be tasked to do the upgrade or maintenance, system defaults are often left in place for the sake of convenience. Further, there is an expectation that the modem line will not necessarily be available 24/7, so it doesn't seem so bad to leave the defaults in place.
Once we were into the company's Internet facing router, there was much that we could do. We attempted to crack the enable password (Cisco specific) and add our machine to the routing table so that traffic from our host would be “internal” to the subnet and therefore trusted. Once this is done, your machine is, for all intents and purposes, internal, and you can begin footprinting to gather information and proceed.
At this point, we attempted to gain access to the rogue modems attached to user desktops. (To be fair, we had no idea whether the modems were “rogue” or whether the employee had permission to have both a modem and a remote control tool on their computers. Perhaps they were telecommuting.)
The remote control tool, pcAnywhere, was found running on several of these hosts. PcAnywhere can be configured to simply grant access to incoming connections or to request user names and passwords. On several occasions, we did find pcAnywhere would simply allow access over dial-up connections. There were cases when user names and passwords were requested. Since we did not have user names and since we had already gained control of other hosts through rogue modems, we didn't proceed with a brute force attempt against both the user name and password. However, since pcAnywhere and telecommuting in general is designed to be convenient, the passwords are generally easy to crack.
At this point, we had user access to employee desktops. From there, we could read files, perform footprinting, and begin to target other hosts on the network.
Dial-in access to systems, be they routers, servers, or user desktops, represent a potential channel of unauthorized access. Telephone access must be closely monitored to ensure that dial-in lines for vendors are not left active and that employees do not have modems on their desktops. As a countermeasure, a company can use all-digital phone lines in employee workspaces. This reduces the dangers of the analog modem.
For those employees who must dial in to telecommute, deploy a two-factor authentication scheme, such as a SecurID card, to protect the access from unauthorized hackers.