There are password crackers for almost every password-protected system available. A quick search on the Internet identifies password crackers for Windows NT, UNIX, Novell, PGP, Word, VNC, pcAnywhere, Lotus Notes, Cisco routers, WinZip, and many others. Password crackers can be effective tools to use during penetration testing to help ensure users are selecting strong passwords. If a strong password is used, password crackers can take weeks, months, or even years to crack it. If a weak password is used, the cracker could succeed in hours, minutes, or even seconds. In this chapter we concentrate on OS-specific password crackers and describe their use during testing.
URL: www.L0pht.com
Client OS: Windows 9x/NT
Target OS: Windows NT
Price: Under $100
Description: L0phtCrack is the premier NT password cracker. The first version provided administrators the ability to extract user names and encrypted password hashes from the SAM database and perform a dictionary and brute force password crack. The tool has matured to include a sniffer utility called SMB Capture that can grab user names and passwords directly from the network. Running in the background, it will watch all network traffic and extract user name and challenge/response hash combinations for later cracking.
L0phtCrack is an excellent tool for auditing Windows NT systems' password strength. By running the tool against a server's password database, you can identify users with insecure passwords and force them to change these passwords. It's better for someone with legitimate intentions to find the insecure passwords before someone without authorization does. You must carefully protect the extracted SAM file and cracked password file. If anyone gains access to these files, they will have the user passwords at their fingertips.
Use: This is a good time for a high-level review of how Windows NT (and UNIX) encrypts passwords. NT performs a one-way encrypted hash on passwords—the password is run through a cryptographic algorithm to produce the hash, but the hash cannot be run through an algorithm to return the password. L0phtCrack basically works on a trial-and-error basis. It runs a word or combination of characters in the form of a password guess through the NT encryption algorithm and compares the hash of this guess to the real stored encrypted password hash. If the hashes match, the tool successfully found the password. In addition, NT encrypts the passwords in seven character blocks. So if your password is password, NT would encrypt passwor and then the d with six nulls. L0phtCrack would attempt to crack the hash for passwor and the hash for d. Therefore, the most secure length for NT passwords is either seven or fourteen characters.
In order to use the tool, you need a file that contains the encrypted passwords. There are basically three ways you can capture the passwords. First, you can dump the password hashes from the registry, but this requires administrator-level access. Second, you can load the SAM file, the repair SAM file called Sam._ (once it has been expanded), or a file containing password hashes. Finally, you can use the SMB packet capture feature to sniff the password hashes from the network.
You can dump the password hashes from the registry either remotely or by physically being on the target server. If you load L0phtCrack on the server being tested and log in as an administrator, you can select Tools and then the option Dump Passwords from Registry. L0phtCrack then retrieves the passwords from the registry and loads them into the tool. To dump the passwords remotely, you must perform an NT NET USE command with administrator-level access:
C:>Net use * \targetipaddressipc$ adminpassword /user:administrator
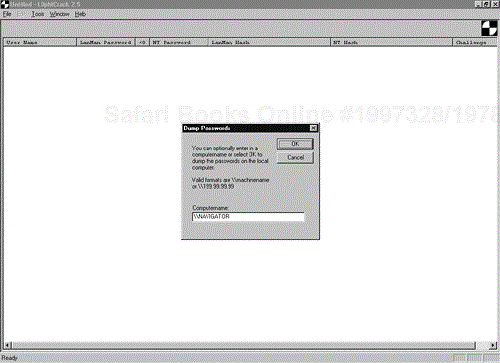
If the command is successful you should receive the message, “The command completed successfully.” Once this NET USE command has properly executed, you can select the Dump Passwords from Registry option from the Tools menu. In the Dump Passwords box, enter the host name or IP address of the remote system. Use the same format you used for the NET USE command—do not alternate between IP address and host name. In the example shown in Figure 15-1, “NAVIGATOR” is the host name of the target server.
If you have copied the SAM file from a different system or have created a file that contains the password hashes, you can load this file by selecting Open Password File from the File menu. NT locks the SAM file while the system is running. Therefore, you can either try to obtain a backup copy of the SAM file or boot into DOS to manually retrieve the file.
The repair SAM file often contains the actual passwords but often is not protected as closely as the actual SAM file. Try grabbing this file and running it through L0phtCrack to see if the passwords are still valid. If the passwords are still valid, properly secure the backup SAM file. The backup SAM file is located in the WINNT/System32/repair directory, on an emergency repair disk (ERD), or on backup tapes. Also, any other file containing password hashes can be read into L0phtCrack using the Open Password File option. For instance, if you had to use pwdump2 to retrieve a password file protected with System Key (SYSKEY) encryption (which essentially double-encrypts the password file), you will need to read this file into L0phtCrack using this method. If you are using L0phtCrack on a Windows 9x system, you will need to expand the Sam._ file on an NT system using the following command:
C:>expand sam._ sam.txt
The final method for gathering password hashes is through the use of the SMB Capture tool. SMB Capture sniffs the password hash directly from the network. This requires access to an active network segment where NT authentication traffic can be found. If the target network is a switched environment, you will probably be able to see only your own NT passwords. If the network is shared (uses hubs instead of switches), you will be able to see and capture all passwords on your segment. One of our favorite ways to use this tool is to find an active or critical segment on the network and plug our laptop into a live network jack on that segment. We run L0phtCrack and select SMB Packet Capture (also known as ReadSMB) from the Tools menu. Next, we hide the laptop in a filing cabinet or drawer, under the desk, or in another inconspicuous location and leave. We can then either come back in 24 hours to retrieve the laptop or use a remote control program to periodically pull the password files from the laptop. To save the captured passwords, we select Save Capture. Then we close Packet Capture, load the saved file into L0phtCrack, select a large word list or dictionary, and start cracking! While cracking the passwords, you can begin another SMB Packet Capture session. If the network uses both LANMAN hashes and NTLM hashes, the process of cracking the sniffed passwords proceeds very quickly since LANMAN hashes are not as secure. LANMAN passwords are not case sensitive and are therefore easier to crack. LANMAN hashes are necessary on networks that use Windows 9x clients. However, on networks that strictly use NT, it is a good idea to use only the NTLM passwords.
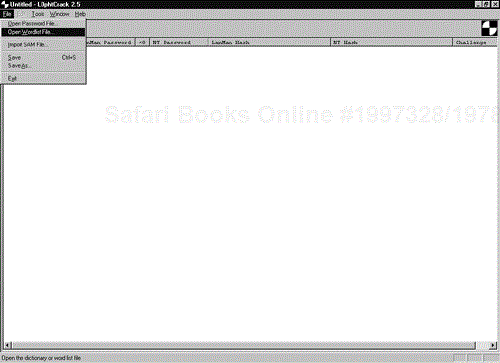
L0phtCrack uses three different cracking methods: dictionary, hybrid, and brute force (by default the tool tries to crack the passwords in this order). L0phtCrack comes with an English dictionary that contains over 25,000 words. You can obtain and load different dictionary files by selecting Open Wordlist File from the File menu, as shown in Figure 15-2. This can be useful if you are trying to crack and test passwords in a foreign location or if you wish to use a custom dictionary that may be specific to a particular organization.
The tool starts cracking passwords using the dictionary attack. If the dictionary method is unsuccessful, L0phtCrack begins the hybrid attack. The hybrid attack attempts to modify dictionary words in ways people commonly use when trying to create secure passwords. The hybrid attack adds numbers and symbols to the dictionary words. You can specify the number of numbers and symbols to use in the Tools menu under Options; the default is two.
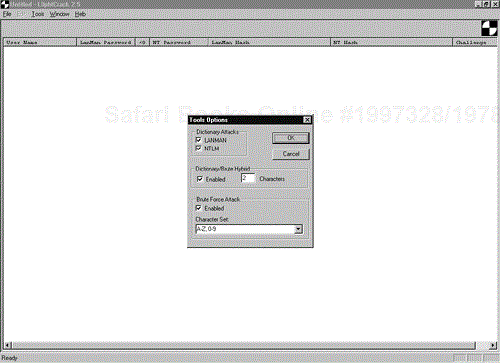
Finally, if the hybrid attack is unsuccessful, the tool begins a brute force attack by running through every number, letter, and symbol combination until successful. This is a slow process, so use a fast machine and allow a lot of time for cracking. Figure 15-3 displays the Tools Options screen, where you can customize the dictionary, hybrid, and brute force attack parameters.
Brute force cracking can take a long time. Additional processing resources can speed up the process, but it still takes significant time and resources to crack passwords. Brute force cracking of strong passwords can take weeks or months. Password change intervals must be based on the amount of time it would take to crack secure passwords through brute force. Therefore, password change intervals are key to security. The defense against password cracking should be two-fold: enforce strong password selection and enforce regular password change intervals. In addition, SYSKEY encryption can be used to further protect the NT password hashes.
If you find L0phtCrack has run for a significant amount of time and has not cracked a single password, or column three (<8) shows none of the passwords are less than eight characters, your password file may be SYSKEY protected. SYSKEY encrypts the password hashes and renders L0phtCrack and other password crackers useless. If SYSKEY encryption has been used, you will need to use pwdump2 to un-SYSKEY the file. (Pwdump2 is described in the next section of this chapter.)
Now that you know your passwords are not safe on the network, how do you defend against this tool? The best defense against password cracking is to choose a secure password that consists of at least seven characters (the most secure password length is either seven or fourteen characters); uses a mix of letters, numbers, and meta-characters; and does not contain any dictionary words. As you will see below, even if an attacker captures a secure password, it will hopefully take the attacker longer to crack the strong password than it will take the user to change that password. The Passflt.dll can be used to help enforce the use of strong passwords. The Passfilt.dll is available in Service Pack 3 and subsequent Service Packs. See the Service Pack 3 documentation for instructions on installing the password strength filter.
As we described above, SYSKEY encryption can be used to help guard against NT password crackers. SYSKEY encryption essentially encrypts the NT password hashes (SAM file), making it even more difficult to crack. L0phtCrack cannot crack SAM files that have been encrypted with SYSKEY encryption unless another tool, pwdump2, is used to decrypt the SAM file. Even though there is a tool to defeat SYSKEY encryption, it makes the task of cracking the SAM file more difficult for the attacker and may cause him or her to move on to another target. SYSKEY became available with Service Pack 3. Use of SYSKEY encryption must be carefully planned before being implemented. Once a server has been protected with SYSKEY encryption, it cannot be rolled back. SYSKEY uses a SYSKEY password that can be stored on the local server, stored on a floppy disk (the disk is required for reboot), or typed in during the boot process. The SYSKEY password must be properly protected because it can be used to un-SYSKEY the file. Instructions for implementing SYSKEY encryption can be found in the Service Pack documentation.
There are some steps that can be taken to guard against NT password sniffing. Implementing switched networks helps guard against password sniffers. It is much more difficult for an attacker to position the sniffer on a switched network to a location where he or she will be able to capture passwords. Forcing the use of NTLM passwords versus LANMAN hashes also helps guard against password sniffers. Using NTLM passwords is only possible in networks that do not have Windows 9x clients. In addition, steps should be taken to ensure the backup SAM file is protected through secure file permissions.
Benefits: L0phtCrack is an excellent tool for testing NT passwords. The tool can be used against an NT password file to identify users with weak passwords. SMB Capture is effective for capturing NT passwords during internal testing scenarios. In addition, L0phtCrack is an excellent tool for penetration testing of NT networks.
Cons: L0phtCrack works only for NT passwords and is available only for Windows NT platforms. It cannot crack SAM files that have been protected with SYSKEY encryption unless pwdump2 is used to decrypt the file. As with any password cracker, you must carefully guard both the password file and the cracked password file to ensure they do not fall into the wrong hands.
URL: www.packetstormsecurity.org
Client OS: Windows NT
Target OS: Windows NT
Price: Free
Description: Pwdump2 is a tool that can be used to overcome an NT password file protected with SYSKEY encryption. SYSKEY encryption, which was discussed in Section 15.1, encrypts the NT password hashes, rendering L0phtCrack and other password crackers useless. Pwdump2 uses dll injection to insert and execute code from pwdump2 in the memory space and user context of lsass.exe. The tool then returns a file containing password hashes that can be fed into a password-cracking program such as L0phtCrack or John the Ripper. Pwdump2 needs to be executed locally on the target server with administrator access.
Use: As stated above, pwdump2 must be run locally on the server with administrator privileges. First, you must determine the process ID of lsass.exe. To perform this step you need to use a tool called pulist.exe. Pulist is another NT Resource Kit utility. Execute pulist from the command line on the server and note the process ID number for lsass. The example below provides the syntax for pulist.
C:>pulist \server_name
Next, execute pwdump2 followed by the process ID for lsass. Use the following syntax to perform this step and direct the output to a file:
C:>pwdump2 process_id_lsass > passlist.txt
Now you can use L0phtCrack or John the Ripper (described in the next section) to crack the password file.
Benefit: Pwdump2 enables you to crack a password file protected with SYSKEY encryption.
Con: Pwdump2 must be executed locally on the target server and with administrator privileges. This can be a difficult set of prerequisites to achieve.
Client OS: Windows 9x/NT, UNIX
Target OS: UNIX, Windows NT LANMAN hashes
Price: Free
Description: John the Ripper started out as a password cracker for UNIX and was only available for UNIX platforms. A Windows client became available soon after, followed by a version capable of cracking NT LANMAN hashes. John the Ripper is a very fast password cracker. Currently there is not a GUI version available, so you have to use the command line even for the Windows version.
John the Ripper can be downloaded as source code or in binary format. If you are compiling the source code, it is better to compile and use the tool on the same platform. The binaries for each platform normally work fine, but we always recommend being wary of binaries unless you are confident of the source and its contents.
Use: To use John the Ripper, you first need a password file. For UNIX systems, the password file is usually located in the /etc/passwd file and the shadowed password file, usually located in /etc/shadow. For Windows NT systems, you need the SAM file or a different file containing the NT password hashes. For a UNIX system you need to unshadow the password file if the system uses shadowing. Of course, you need local root access to unshadow the password files. The following command unshadows the file:
#unshadow /etc/passwd /etc/shadow > crack.1
This command combines the contents from the /etc/passwd and /etc/shadow files and creates a file that John the Ripper can use for cracking.
If you are trying to crack NT passwords, you need to use the unafs utility that extracts the hashes from the binary SAM file and creates a file that John the Ripper can use. This tool also requires administrator access and must be run locally on the target system. The following command extracts the hashes from the SAM file:
C:>unafs SAM > Ntpassword.1
Now that you have files that John the Ripper can use, you are ready to start cracking. Similar to L0phtCrack, John the Ripper supports several different modes. The default order for these modes is single crack, a word list with rules, and finally incremental mode. Single crack mode uses login information and passwords guessed on other accounts against each password. Word list mode enables you to use the default word list or to specify a more comprehensive or targeted word list. Rules can be added to the word list through the -rules option such as capitalize, uppercase, lowercase, reverse, and so on. John the Ripper's documentation provides many options for specifying rules with word lists. Word lists can be found almost anywhere on the Internet, or you can create your own simply by entering one password per line in a text file. Incremental mode is similar to L0phtCrack's brute force mode. By default, incremental mode uses the full 95-character set and all possible password lengths up to eight characters. John the Ripper does enable you to input different options with incremental mode, such as alpha (use the alphabet), numeric, password lengths, and many other options. John the Ripper even offers the ability to create new character sets if you have detected passwords with unusual characters. The program documentation outlines the procedures for using these options.
For the purposes of this book, we demonstrate how to apply John the Ripper using the defaults. First, we need to start the program cracking on the password file we created earlier. The following command launches John the Ripper in default mode, where crack.1 is the name of the UNIX password file we created:
#john crack.1
Once this command has been issued, John the Ripper starts cracking. Many users receive an error message the first time they launch the program, “Loaded 0 password.” This message usually means your password file is shadowed and you did not unshadow it, or the password file is in a format that John the Ripper does not support. If you receive this message, make sure you correctly unshadowed the UNIX shadow password file or used unafs on an NT SAM file.
As the program cracks passwords, they are stored in a database, ~/john.pot. If John the Ripper has already cracked the entries in the file you specify, they will still be in the database and the program will not crack them again. This database can be cleared so that you are not retaining a long list of cracked passwords. To view the passwords use the show command:
#john –show crack.1
Benefits: John the Ripper is a very fast password cracker that can be customized to suit your specific needs. The tool can crack both UNIX and NT LANMAN hashes. John the Ripper is relatively easy to use and can be run on both UNIX and NT platforms.
Cons: John the Ripper currently comes in a command line version only. Also, the program supports only NT LANMAN hashes, not NTLM passwords. To crack NTLM passwords you need to use L0phtCrack or another NT-specific password cracker.
URL: www.confine.com/programs/Cain151.zip
Client OS: Windows 95/98
Target OS: Windows 95/98
Price: Free
Description: On Windows 9x systems using local authentication, passwords are stored in a .pwl file in the Windows directory. Cain uses dictionary, hybrid, and brute force attacks to crack these passwords. To use Cain, you must have physical access to the target system.
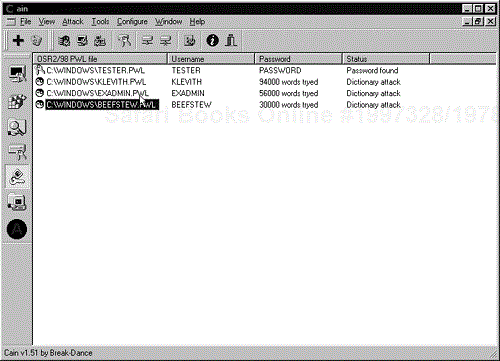
Use: First, you need to gain physical access to the target Windows 9x system. Then log into the system by pressing Esc. Next, copy the .pwl files to disk. Load the .pwl file into Cain with a large dictionary and start it cracking. It is a very fast tool, attempting approximately 5,000 tries per second. Figure 15-4 contains sample output from Cain.
Benefits: Cain is an easy and very fast password cracker for Windows 9x systems. Many of the passwords stored in an organization's Windows 9x system probably work on other systems in the organization.
Con: You need to obtain physical access to the system and copy the .pwl file off onto disk.
URL: www.packetstormsecurity.org
Client OS: Windows 95/98
Target OS: Windows 95/98
Price: Free
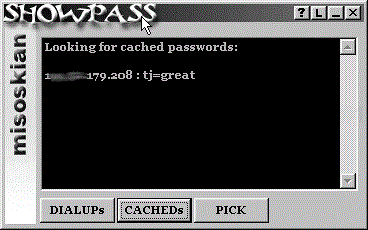
Description: ShowPass is a tool for extracting cached passwords from Windows 95/98 systems. The tool can be useful during penetration testing to illustrate the dangers of caching passwords. ShowPass demonstrates just how open and insecure an operating system Windows 95/98 really is. The tool can capture cached passwords for network connections, Lotus Notes, remote access, Internet access, and others. An attacker could use these passwords to access sensitive data or to log in as a user and exploit systems. This tool is very popular in universities and shared-system environments.
Use: The user must be logged into the Windows 95/98 system to be effective, and you, as the attacker, must have physical access to the system. ShowPass can be launched from a floppy disk. You then select whether to capture cached passwords or dial-in passwords. Slip the floppy into the system, launch the program, capture the passwords, and walk away. Figure 15-5 shows the ShowPass GUI and sample output.
You can attempt to guard against ShowPass by logging out when leaving a Windows 95/98 system unattended and enforcing password-protected screen savers. Also, always avoid caching passwords.
Benefits: ShowPass is useful for showing users the dangers of leaving a Windows 95/98 system logged in and unattended. The tool is free and easy to use. Also, ShowPass illustrates some of the weaknesses of the Windows 95/98 operating system and may convince you or company managers to move to a more secure operating system.
Con: The tool requires physical access and works only on Windows 9x systems.