Chapter 6: Overview of Information Security Program Development Management
In this chapter, we will discuss information security program development management and look at the methods, tools, and techniques for developing an information security program. The main objective of information security program development is to achieve the objectives of information security in an effective and efficient manner. Program development includes the process of planning, implementing, testing, monitoring, and controlling the activities related to information security. A structured security program will help an organization manage its security initiatives in an effective manner.
The following topics will be covered in this chapter:
- Information security program management overview
- Information security program objectives
- Information security framework components
- Defining an information security program road map
- Information security policies standards, and procedures
- Security budget
- Security program management and administrative activities
- Privacy laws
Let's look at each one of the preceding topics in detail.
Information security program management overview
An information security program covers all the activities and processes that collectively provide security services to an organization. Some of the common activities of security programs include the design, development, and implementation of security-related controls throughout the organization. Controls can be in the form of simple policies and processes or an advanced technological structure. Depending upon the size and nature of the organization, the security program can be managed by either a single individual or an exclusive team headed by a chief information security officer (CISO).
A security manager is expected to have a thorough knowledge of information technology as it helps to understand how changes in the technical environment affect the security posture. An information security manager is required to evaluate the risk of technology and determine relevant controls to safeguard the IT resources.
Apart from technical skills, a security manager is expected to have a thorough understanding of business processes and objectives. A security manager should ensure that the objectives of the security program are aligned with business objectives. Security objectives should have the consensus of business management. Security objectives are an important element of a security program and without security objectives, it will not be possible to define metrics and monitor the progress of the program. The main goal of a security program is to implement the strategy and achieve the defined program.
Outcomes of an information security program
Security programs should have the following outcomes to support the business objectives.
Strategic alignment
A security program should be designed in such a way that it provides strategic alignment with business requirements. Alignment should take into account business processes, culture, governance, existing technology, and the structure of the organization. Strategic alignment can best be achieved through a security strategy committee that is composed of senior representatives of all the relevant business units.
A security manager is required to have a thorough understanding of business processes and regular interaction with business owners to gain an understanding of their requirements. Strategic alignment also requires the submission of key aspects of the security program to senior management at regular intervals.
Risk management
Security programs should be able to manage the risk applicable to the business objectives. For effective risk management, a security manager should be aware of threats, vulnerabilities, and the risk profile of the organization. Risk must be managed to a level acceptable to senior management.
Value delivery
A security program should provide value to the organization. For value delivery, security should be managed effectively and efficiently. Security investment should be managed to provide maximum value to the organization.
Resource management
A security manager should be able to utilize resources – that is, staff, finance, technology, and the knowledge bank – efficiently and effectively. If there is resource constraint, protection efforts should be prioritized to support areas of greatest needs and benefits. These efforts will provide the basis for good resource management.
Performance management
A security manager should develop processes to monitor the performance of the security program. Metrics should be developed to determine the performance. Performance metrics should be submitted to senior management at regular intervals.
Assurance process integration
A security manager should be aware of various assurance functions to align security activities with the activities of other assurance functions. Assurance functions generally include physical security, risk management, quality control, audit, legal, HR, IT, business continuity, and so on.
The starting point of a security program
Most of the framework starts with conducting a risk assessment and establishing the objectives of control. An information security program is established to close the gap between the existing state of controls (as identified by a risk assessment) and the desired state (that is, control objectives).
Information security charter
A charter is the formal grant of authority or rights. An information security charter states that the organization formally recognizes the information security department. In the absence of a charter, it will be difficult for the information security department to operate within the environment. A charter defines the scope, responsibility, and authority of the information security function.
A charter can act as the foundation to provide guidance to the governance of information security.
Support from senior management
Support from senior management is considered the biggest challenge for every security manager. Investment in security does not provide any tangible benefits and calculating return on investment (ROI) is not as simple as ROI for any other business investment. On a lighter note, most security managers face the challenge depicted in the following diagram:

Figure 6.1 – Senior management support
A security manager should consider the following aspects when seeking support and budget from senior management:
- The security strategy should be aligned with the business objectives and goals.
- The security manager should obtain consensus from other business units when designing a security strategy.
- To the extent possible, the benefits of the proposed project should be quantified in the business case.
Thus, the best way to obtain support from senior management is to let them know how information security is supporting the business objectives.
Defense in depth
Defense in depth (DiD) is an arrangement wherein multiple layers of controls are implemented to protect the information resources. Its intent is to provide redundancy in case one control fails. The first layer of defense in depth is to prevent the event from occurring, that is, implementing preventive controls such as authentication. The second layer is containment, that is, to isolate and minimize the impact. The third layer is reaction, that is, incident response procedures, and the next layer is the recovery and restoration procedure, that is, backup arrangements.
Key aspects from a CISM exam perspective
The following are some of the key aspects from an exam perspective:

Table 6.1 – Key aspects from the CISM exam perspective
Questions
- An organization has recently been impacted by a major security incident. Learning from this incident can be best utilized by the security manager doing which of the following?
A. Improving the integration of business and information security processes
B. Increasing the information security budget
C. Improving the industry benchmarking process
D. Obtaining better technical controls
Answer: A. Improving the integration of business and information security processes
Explanation: The most important challenge for a security manager is to obtain support from senior management and other business units to change the business processes to include the security aspect. As an incident has already occurred, business units will be open to supporting security processes. In the absence of close integration of business and security processes, other options will not be effective.
- Why should an information security manager have a thorough understanding of information technology?
A. To ensure that the latest and most feasible technology is being used
B. To understand the risk of technology and its contribution to the security objectives
C. To provide consultation on the deployment of information technology
D. To improve the relationship between information security and business units
Answer: B. To understand the risk of technology and its contribution to the security objectives
Explanation: An information security manager is required to evaluate the risk of technology and determine relevant controls to safeguard the IT resources. The other options are secondary aspects.
- The requirements for information security resources are identified in which of the following?
A. Risk assessment
B. Architecture
C. Strategy
D. Guidelines
Answer: C. Strategy
Explanation: An information security strategy is a set of actions to achieve the security objectives. The strategy includes what should be done, how it should be done, and when it should be done to achieve the security objectives. The strategy also includes details of the resources necessary to implement the program.
- What is generally the starting point for an information security framework?
A. Development of an information security policy
B. Remediation of internal audit findings
C. A risk assessment and control objectives
D. Allocating a security budget
Answer: C. A risk assessment and control objectives
Explanation: Most of the framework starts with conducting a risk assessment and establishing the objectives of control. Once the objectives are established, the information security policy is developed and a security budget is allotted. An internal audit is not relevant.
- What is the most important aspect to be considered at the time of establishing an information security program?
A. To understand the existing culture within the organization
B. To understand the existing control system of the organization
C. To understand the overall risk exposure of the organization
D. To determine the availability of security resources in the organization
Answer: C. To understand the overall risk exposure of the organization
Explanation: It is of utmost importance that the security manager is aware of the overall risk exposure of the organization. The other options – that is, culture, control system, and resource constraints – will be evaluated as a part of risk exposure.
- The involvement of senior management in the information security program will first determine what?
A. The charter
B. The security strategy
C. The budget
D. The security procedure
Answer: A. The charter
Explanation: A charter is a formal grant of authority or rights. An information security charter states that the organization formally recognizes the information security department. In the absence of a charter, it will be difficult for the information security department to operate within the environment. All of the other choices follow the charter.
- What is the first layer of a defense in depth strategy?
A. Containment
B. Prevention
C. Reaction
D. Recovery
Answer: B. Prevention
Explanation: DiD is an arrangement wherein multiple layers of controls are implemented to protect the information resources. Its intent is to provide redundancy in case one control fails. The first layer of defense in depth is to prevent the event from occurring, that is, implementing preventive controls such as authentication. The second layer is containment, that is, to isolate and minimize the impact. The third layer is reaction, that is, incident response procedures, and the next layer is the recovery and restoration procedure, that is, backup arrangements.
- Which of the following is the first layer for defense in depth?
A. Isolation
B. Authentication
C. Incident procedures
D. Recovery procedures
Answer: B. Authentication
Explanation: Defense in depth is an arrangement wherein multiple layers of controls are implemented to protect the information resources. Its intent is to provide redundancy in case one control fails. The first layer of defense in depth is to prevent the event from occurring, that is, implementing preventive controls such as authentication and so on. The second layer is containment, that is, to isolate and minimize the impact. The third layer is reaction, that is, incident response procedures, and the next layer is the recovery and restoration procedure, that is, backup arrangements.
- What does the effectiveness of an information security program primarily depend on?
A. The availability of a documented security policy and procedures
B. Senior management commitment
C. Periodic awareness training
D. Developing an information security management system
Answer: B. Senior management commitment
Explanation: The most important element for an effective information security program is support and commitment from senior management. If senior management is committed to robust information security for the organization, there will no constraints for the security budget and resources. The other options are secondary aspects.
Information security program objectives
A security manager should understand the following objectives of a security program while implementing the program:
- To provide maximum support to business functions
- To minimize operational disruption
- To implement the strategy in the most cost-effective manner
After establishing the objectives, key goal indicators (KGIs) to reflect these objectives need to be developed. The next step is to determine the current state of security. The current state should be compared with established objectives and identified gaps should be addressed to improve the security processes.
Key aspects from a CISM exam perspective
The following are some of the key aspects from an exam perspective:

Table 6.2 – Key aspects from the CISM exam perspective
Questions
- The security manager notes that senior management is dissatisfied with the current state of information security. To address this, what is the most important consideration?
A. Industry benchmarks
B. Business strategy
C. Technology advancement
D. User awareness
Answer: B. Business strategy
Explanation: The security framework and security policy should closely align with the organizational needs. Policies must support the needs of the organization. For alignment of the security program, the security manager should have an understanding of the business strategy, plans, and objectives. Effective strategic alignment of the information security program requires regular interaction with business owners.
- What should the security policy be most closely aligned with?
A. Industry-recognized practices
B. Organizational needs
C. International standard organization
D. Legal requirements
Answer: B. Organizational needs
Explanation: The security framework and security policy should closely align with the organizational needs. Policies must support the needs of the organization. The other options are secondary aspects.
- Before implementing a security strategy, it is most important to do what?
A. Communicate with the IT department.
B. Train all the end users.
C. Determine the technology to be used.
D. Obtain sign-off from the stakeholders.
Answer: D. Obtain sign-off from the stakeholders
Explanation: Before implementing a framework and security policy, sign-off should be obtained from all relevant stakeholders to ensure that the policy is supporting the objectives and expectations of the business. The other options are secondary aspects.
Information security framework components
Frameworks are structures or outlines that support the implementation of an information security strategy. They provide the best practices for a structured security program. Frameworks are flexible structures that any organization can adopt as per their environment and requirements. Governance frameworks such as COBIT 5 and ISO 27000 are widely accepted and implemented frameworks for security governance.
Generally, a security framework has the following components:
- Technical components: This means the part of the framework that covers the technical and IT aspects of security. Examples of technical aspects include the configuration, monitoring, and maintenance of technical components such as a firewall, IDS, SIEM, and so on. It is very important to have assigned ownership for each technical asset to ensure proper risk treatment and compliance with security policies.
- Operational components: This means the part of the framework that covers ongoing management and administrative activities to ensure the required level of security assurance. Examples of operational components include preparing SOPs, patch management, log analysis, change management and other routine types of activities to support security, and so on. Each of these activities should be assigned to an individual who has the requisite authority and knowledge.
- Management components: This means the part of the framework that covers oversight functions. Examples of management components include the availability of a security policy, adequate resources for security, regulator monitoring of key aspects of information security, and so on.
- Administrative components: This means the part of the framework that covers support functions such as human resources, finance, and other functions. Examples of administrative components include personnel job descriptions, performance management, budget preparation, calculating return on investment, and so on.
- Educational and informational components: This means the part of the framework that covers education, awareness, and training requirements for enhancing the security posture of the organization.
Framework – success factor
A security framework should be designed and developed considering the business objectives and goals. It is important to have the consensus of business units for a security framework. On a lighter note, most security managers will find themselves in the situation depicted in the following diagram:

Figure 6.2 – Information security framework
A security manager should consider the following factors for successful implementation of the framework:
- To get the framework approved, the security manager should demonstrate a positive return on security investment. The best method to evaluate the return on security investment is to determine the level of support information security provides for the achievement of the business objectives.
- The most important thing when developing a framework for an information security program is to determine the desired outcome. If the desired outcome is not considered at the time of developing the framework, it will be difficult to determine a strategy, control objectives, and logical architecture.
- The security manager should consider the advantages and disadvantages of centralized as well as decentralized security functions. It is more convenient to monitor and control a centralized function. A decentralized function makes it easier to promote security awareness and ensures a faster turnaround for security requests as it is closer to business units. A decentralized unit is more responsive to business unit needs.
- The security framework and security policy should closely align with organizational needs. Policies must support the needs of the organization. For alignment of the security program, the security manager should have an understanding of business plans and objectives. Effective strategic alignment of the information security program requires regular interaction with business owners.
- Before implementing the framework and security policy, sign-off should be obtained from all relevant stakeholders to ensure that the policy is supporting the objectives and expectations of the business.
- Support from senior management is critical for an effective information security program.
- The framework should also define the process for handling exceptions to the policy and procedures. Inherent authority to grant an exception to the information security policy should reside with the authority that has approved the policy.
- While implementing a framework, policy, and controls, the most important consideration is the safety of human life.
Information security management needs to ensure that the framework supports the business objectives.
Key aspects from a CISM exam perspective
The following are some of the key aspects from an exam perspective:

Table 6.3 – Key aspects from the CISM exam perspective
Questions
- A security manager can determine the return on security investment by evaluating what?
A. Extent of support for business objectives
B. Number of security metrics developed
C. Industry standards
D. Process maturity model
Answer: A. Extent of support for business objectives
Explanation: To get the framework approved, the security manager should demonstrate a positive return on security investment. The best method to evaluate the return on security investment is to determine how information security supports the achievement of business objectives. The other options do not directly help to determine the return on investment.
- The security manager notes that privileged access was granted to the entire HR team. What should the security manager do first?
A. Revoke privileged access for all.
B. Report to senior management.
C. Talk to the data owners to understand the business needs.
D. Implement a procedure to grant emergency access.
Answer: C. Talk to the data owners to understand the business needs.
Explanation: The first step is to determine the business needs for granting privileged access to all the team members. Access to all team members may be a business process requirement. Without understanding the business requirements, the security manager should not revoke or report to senior management.
- What is the first step in the development of a well-defined information security program?
A. Determine the security budget.
B. Determine the strategic requirements.
C. Determine the desired outcomes.
D. Determine the security architecture.
Answer: C. Determine the desired outcomes.
Explanation: The most important thing when developing a framework for an information security program is to determine the desired outcome. If the desired outcome is not considered at the time of developing the framework, it will be difficult to determine a strategy, control objectives, and security architecture.
- What is the benefit of a centralized information security organization structure?
A. Comparatively easy to promote security requirements
B. Comparatively easy to manage and control
C. More responsive to business unit needs
D. Enables a quick turnaround time for security requests
Answer: B. Comparatively easy to manage and control
Explanation: Due to centralized control, it is easy to manage the security functions as compared with decentralized functions. A decentralized function is more convenient and it is easier to promote security awareness and ensure a faster turnaround for security requests as it is closer to business units. A decentralized unit is more responsive to business unit needs.
- What is the main advantage of a decentralized security function?
A. Easy to manage and control
B. Increased compliance with policies and procedures
C. Better alignment of security to business needs
D. Reduction in security budget
Answer: C. Better alignment of security to business needs
Explanation: A decentralized unit is more responsive to business unit needs as it is closer to business units. The other options are the advantages of centralized functions, that is, centralized management is easy to manage and control, ensures increased compliance, and reduces the cost of security.
- The security manager notes that compliance to a particular set of standards is weak. What should be their first step?
A. Remove that standard from the policy.
B. Update the policy to address the risk.
C. Enforce a penalty for non-compliance.
D. Perform a risk assessment.
Answer: D. Perform a risk assessment.
Explanation: The first step is to conduct a risk assessment and determine the impact of non-compliance. On the basis of the potential impact, subsequent action should be determined.
- How can the strategic alignment of a security program best be achieved?
A. Active benchmarking with industry
B. Increasing the security budget
C. Regular interaction with business owners
D. Addressing culture differences
Answer: C. Regular interaction with business owners
Explanation: The security framework and security policy should closely align with the organizational needs. Policies must support the needs of the organization. For alignment of the security program, the security manager should have an understanding of the business plans and objectives. Effective strategic alignment of the information security program requires regular interaction with business owners.
- The security manager has received a request for an exception from the standard configuration of an operating system. What should be the security manager's first step?
A. Reject the request for an exception.
B. Determine the risk and identify the compensating controls.
C. Seek guidance from senior management.
D. Determine the industry practice.
Answer: B. Determine the risk and identify the compensating controls.
Explanation: The first step for the security manager is to determine the risk involved in granting the exception and evaluate whether any compensatory controls are in place to address the risk. On the basis of the perceived risk, the other options can be considered.
Defining an information security program road map
For effective implementation of a security program, it is recommended to develop a road map covering different stages with a clear objective to be achieved during each stage. The initial stage of program development is to talk to concerned stakeholders such as business units, legal, HR, finance, and other units. This will help the security manager to determine the security requirements of different units.
In the second stage, security requirements should be formalized to draft a basic security policy and approval should be obtained from senior management. A security steering committee consists of officials from different business functions. It plays an important part in the finalization of security requirements. In the third stage, members of the security steering committee emphasize the promotion of security awareness of the policy and conduct a security review to see whether they are in compliance. In the fourth stage, gaps identified during the security review should be addressed and a continuous monitoring process should be developed. Gradually, the security manager can start developing a consensus around roles and responsibilities, processes, and procedures in support of the policy.
A road map for the development of a security program should evolve around the security strategy of the organization. A road map should consider objectives, resources, and constraints. A road map should include various milestones in terms of KGI.
In the absence of a well-defined strategy, there can be a risk that a security program may not be integrated or prioritized as per the requirements of the organization. Most of the information security development efforts will evolve around the design, development, and implementation of the controls.
Gap analysis
A security manager should conduct gap analysis at periodic intervals to determine the gap between the control objectives and the performance of existing controls. Identified gaps should be addressed for improvement. It is also important to develop a procedure for monitoring the control effectiveness. This will help the security program to evolve and mature. On a lighter note, the following diagram depicts root cause analysis for security gaps:

Figure 6.3 – Gap analysis
Thus, the final objective of gap analysis is not only to identify the gap but also to address it for the improvement of security processes.
Value of a security program
A security program should provide value to the organization. A security manager should determine the cost of implementation of controls and the corresponding value of the assets to be protected. This will form the basis for determining that the information security program is delivering value. If the cost of control is higher than the value of the assets, then it does not provide any value.
Security program integration with another department
A security program should be integrated with the processes of other departments, such as IT, audit, risk management, quality assurance, HR, and so on. This helps to improve the effectiveness of the overall security program. The most important aspect is integration with information technology processes. Automated controls are considered to be more effective than manual controls. Automated controls are generally driven by the IT department. Also, IT is responsible for the implementation and operation of information processing systems. For any new IT project, the security department should be involved right from the feasibility stage to the implementation stage. In fact, the security department should be involved throughout the system development life cycle (SDLC) process. The security manager should be well versed in information technology in order to make informed decisions about technology risk.
A security program should also be integrated with HR processes. For example, in the event of the termination of an employee, details should immediately be made available to the security team so they can revoke all the access rights of that employee.
Also, when an employee is transferred to another department, it is very important to review and update their access rights to ensure that any access no longer needed is removed and appropriate access for the new position is granted.
Key aspects from a CISM exam perspective
The following are some of the key aspects from an exam perspective:


Table 6.4 – Key aspects from the CISM exam perspective
Questions
- How can value delivery by an information security program best be determined?
A. Count of controls implemented
B. Cost of achieving the control objectives
C. Count of controls monitored
D. Results of control testing
Answer: B. Cost of achieving the control objectives
Explanation: A security program should provide value to the organization. The security manager should determine the cost of implementation of control and the corresponding value of the assets to be protected. This will form the basis for determining whether the information security program is delivering value. If the cost of control is higher than the value of the assets, then it does not provide any value. The other options are secondary aspects.
- Who should provide final approval for security patch updating hours?
A. System administrator
B. Business asset owner
C. Security manager
D. Business continuity manager
Answer: B. Business asset owner
Explanation: It is very important to take approval from the business asset owner for patch updating timings as patch updating may lead to unexpected problems and can interrupt business processes. Generally, the business asset owner will prefer non-working hours for patch updating.
- While selecting the controls to meet the business objectives, what should the security manager primarily do?
A. Focus on role-based access controls
B. Focus on key controls
C. Focus only on financial applications
D. Focus on preventive controls
Answer: B. Focus on key controls
Explanation: The security manager should primarily focus on key controls to reduce the risk and protect the information assets. Role-based control may be one of the key control areas. Focusing only on financial applications is not justifiable as protection of other data (for example, customer data) may be equally critical. Key controls need not necessarily be only preventive controls.
- What should an information security program primarily be integrated with?
A. Audit department
B. Risk management department
C. Information technology
D. Quality assurance
Answer: C. Information technology
Explanation: A security program should be integrated with the processes of other departments, such as IT, audit, risk management, quality assurance, HR, and so on. This helps to improve the effectiveness of the overall security program. The most important aspect is integration with information technology processes. Automated controls are considered to be more effective than manual controls. Automated controls are generally driven by the IT department. Also, IT is responsible for the implementation and operation of information processing systems. The other options are secondary aspects.
- To protect and control the mobile devices issued by the organization, which of the following activities carried out by HR should be monitored?
A. Issuing a termination notice
B. Conducting background checks
C. Releasing a paycheck
D. Conducting a security awareness program
Answer: A. Issuing a termination notice
Explanation: In the event of termination of an employee, details should be immediately made available to the security team so they can revoke all the access rights of that employee, including de-provisioning of mobile devices. The other options are not as significant as the termination process.
- For a new IT project, at which stage should the information security department be involved?
A. Feasibility stage
B. Implementation stage
C. Design stage
D. Post-implementation stage
Answer: A. Feasibility stage
Explanation: For any new IT project, the security department should be involved right from the feasibility stage till the project completion stage. In fact, the security department should be involved throughout the SDLC process. Security considerations will affect feasibility. Involving the security team only at later stages may not be an effective and efficient option.
- What is the best way for the data owner to determine what access and authorization should be provided to users?
A. The system administrator should have the authority to provide access.
B. Access should be provided on the basis of user requests.
C. Access should be provided on the basis of hierarchical preferences.
D. Access should be provided by mapping to business needs.
Answer: D. Access should be provided by mapping to business needs.
Explanation: Access should be provided on a need-to-know basis, that is, by mapping to business needs. The other options are not justifiable if users do not require data to perform their duties.
- If an employee is transferred to another department, what is the most important aspect?
A. Reviewing and updating their access rights
B. Updating the job profile document
C. Conducting training for the new assignment
D. Reviewing their performance in their last profile
Answer: A. Reviewing and updating their access rights
Explanation: When an employee is transferred to another department, it is very important to review and update the access rights to ensure that any access no longer needed is removed and appropriate access for the new position is granted. The other options are secondary aspects.
- An information security manager should have a thorough understanding of information technology primarily for what reason?
A. To ensure that IT staff cannot mislead the security manager
B. To implement new IT technology
C. To understand the IT budget
D. To understand the IT issues for achieving adequate information security
Answer: D. To understand the IT issues for achieving adequate information security
Explanation: The security manager should be well versed in information technology in order to make informed decisions about technology risk. Technology knowledge will help the security manager to understand the IT issues for achieving adequate information security. The security manager is not expected to implement IT technology or adhere to the IT budget.
Policy, standards, and procedures
A security program is implemented through a specific set of policies, standards, and procedures. Let's understand how each one of these operates:
- Policies: A policy is a set of ideas or strategies that are used as a basis for decision making. They are the high-level statements of direction by management.
There can be multiple policies at the corporate level as well as the department level. It should be ensured that department-level policies are consistent and aligned with corporate-level policies.
- Standards: A standard is a mandatory requirement to be followed in order to comply with a given policy or framework or certification or regulation. A standard provides detailed directions to comply with the policy.
A standard helps to ensure an efficient and effective process, resulting in reliable products or services. Standards are updated as and when required to incorporate new processes, technology, and regulatory requirements.
A standard is a dynamic document and is changed if control objectives are not achieved or on the basis of the result of risk assessments.
- Procedures: Procedures are detailed steps and actions that help to support the policy and standards. Generally, procedures are changed more frequently as compared to policies and standards.
- Guidelines: In some cases, guidelines are required to implement procedures. Guidelines include information such as examples, suggestions, requirements, and other details for executing procedures.
Policies, standards, procedures, and guidelines should be available in the documented format.
Reviewing and updating documents
All the previously mentioned documents – that is, policies, standards, procedures, and guidelines – should be reviewed at periodic intervals to address new and emerging risks. The appropriate version history should be maintained. The security manager should check for currency.
The last review date confirms the currency of the documents and helps to determine that management has reviewed the standards to meet and address the current business environment.
The security manager should also consider the applicability of policies, standards, procedures, and guidelines to third-party vendors and service providers and their adherence to said documents.
Key aspects from a CISM exam perspective
The following are some of the key aspects from an exam perspective:

Table 6.5 – Key aspects from the CISM exam perspective
Questions
- "All computers are required to have the Windows 10 operating system and all servers are required to have Windows 2008." What is this statement an example of?
A. A policy
B. A guideline
C. A standard
D. A procedure
Answer: C. A standard
Explanation: A standard is a mandatory requirement to be followed to comply with a given policy or framework or certification or regulation. A standard helps to ensure an efficient and effective process, which results in reliable products or services. A policy is a high-level statement of management intent and it does not cover this type of requirement. Guidelines and procedures provide detailed dos and don'ts to support the organization's policies.
- Which of the following is a function that should be exclusively performed by the information security department?
A. Monitoring the performance of an operating system
B. Implementing user access of operating systems
C. Approving operating system access standards
D. Setting firewall rules to protect an operating system
Answer: C. Approving operating system access standards
Explanation: Approving the standards should be performed by the information security team. The security team should ensure that standards meet the requirements of the security policy. Implementation of the approved standard is to be performed by the IT department. The other options are generally performed by the IT department.
- Procedures are correctly linked to security policies through which of the following?
A. Standards
B. Audit
C. Maturity model
D. Guidelines
Answer: A. Standards
Explanation: Standards are the set of minimum requirements to be followed to comply with the requirements of the security policy. Standards (minimum requirement) are included in procedures to ensure that they comply with the intent of policies. Guidelines are generally detailed descriptions of the procedures. A maturity model is adopted to ensure continuous improvement in the security process.
- What is the most appropriate document to ensure compliance with a specific regulatory requirement?
A. Policies
B. Standards
C. Procedures
D. Guidelines
Answer: B. Standards
Explanation: A standard is a mandatory requirement to be followed to comply with a given framework or certification or regulation. Standards help to ensure an efficient and effective process, which results in reliable products or services. A policy is a high-level statement of management intent and it does not cover specific regulatory requirements. Guidelines and procedures provide detailed dos and don'ts to support the organization's policies and standards.
- The information security standard should primarily include what?
A. Date of creation
B. Author of the document
C. Approval of the document
D. Last review date
Answer: D. Last review date
Explanation: The most important element is the last review date, which helps to ensure the currency of the standard and provides assurance that the document is reviewed and updated to address the current issues.
- Which of the following documents will be updated most frequently?
A. Database hardening procedures
B. Password complexity standard
C. Information security policy
D. Document retention standard
Answer: A. Database hardening procedures
Explanation: Generally, procedures are changed more frequently as compared with policies and standards. As an operating system changes, procedures for hardening also need to be changed. Policies and standards should be more static and less subject to frequent change.
- What is the best way to relate a standard to a policy?
A. A policy provides detailed directions to comply with the standard.
B. Both policies and standards have the same content.
C. A standard provides detailed directions to comply with the policy.
D. A standard is a standalone document without a relationship to any particular policy.
Answer: C. A standard provides detailed directions to comply with the policy.
Explanation: A policy is a high-level statement of management intent and it does not cover specific requirements or actions. A standard is a mandatory requirement to be followed to comply with a given framework or policy. A standard provides detailed directions to comply with a policy.
- An information security standard is most likely to be changed because of which of the following?
A. Change in the effectiveness of controls
B. Change in information security procedures
C. Change in security budgets
D. Change in the result of a periodic risk assessment
Answer: D. Change in the result of a periodic risk assessment
Explanation: A standard is a mandatory requirement to be followed in order to comply with a given framework or certification or policy. If the results of a risk assessment are not encouraging, then the standard should be updated to ensure that it appropriately addresses the organization's security objectives. The other options will not directly impact the standard.
- An information security standard is most likely to be changed because of which of the following?
A. Reduction in security budget
B. Change in security procedure
C. Change in security guidelines
D. Control objectives not being met
Answer: D. Control objectives not being met
Explanation: A standard is a mandatory requirement to be followed in order to comply with a given framework or certification or policy. If the current standard does not help to achieve the intended control objectives, the standard should be modified to ensure that it appropriately addresses the organization's security objectives. The other options will not directly impact the standard.
- Who is ultimately responsible for ensuring that information policies are consistent with laws and regulations?
A. Quality assurance team
B. Head of audit
C. Board of directors
D. Head of technology
Answer: C. Board of directors
Explanation: The final responsibility resides with the board of directors for compliance with laws and regulations. The other options will support the board to execute the security policy.
- An exception to the information security policy can be granted by which of the following?
A. Process owner
B. Security manager
C. Policy approver
D. Audit manager
Answer: C. Policy approver
Explanation: A framework should define the process for handling exceptions to the policy and procedure. The inherent authority to grant an exception to the information security policy should reside with the authority that has approved the policy.
Security budget
Budgeting plays a significant role in the effective implementation of an information security program. The availability of adequate security personnel and other security resources is dependent on the security budget. The information security manager should be familiar with the budgeting process and methods used by the organization.
Primarily, the security budget is derived from and supported by the information security strategy. Before seeking approval for the budget, the security manager should ensure that senior management has approved the strategy and other business units have a consensus on the security strategy. This is a key element in a successful budget proposal.
Apart from routine expenditure, the budget should also consider unanticipated costs. Generally, in the area of incident response, it is difficult to predict the expenditure. The security manager may require obtaining external services to support the incident response processes where an organization does not have the necessary skills or bandwidth. The best approach to the budget for this kind of situation is to use historical data of incidents and related expenditure. If this information is not available, the security manager may rely on statistics from peer organizations to arrive at a reasonable budget.
Getting a security budget approved is a dream for every security manager, as depicted in the following diagram:

Figure 6.4 – Information security budget
Adequate funding for information security is the biggest challenge for a security manager. When funds are inadequate, the best option is to allocate available resources to areas of highest risk and at the same time educate management about the potential impact of underfunding.
Key aspects from a CISM exam perspective
The following is a key aspect from an exam perspective:

Table 6.6 – Key aspect from the CISM exam perspective
Questions
- Security spending and budgeting are prioritized primarily on the basis of what?
A. Identified levels of risk
B. Incident trends
C. Discretion of the security manager
D. Industry benchmarking
Answer: A. Identified levels of risk
Explanation: On the basis of the risk assessment, areas of high risk should be identified. Priority should be given to these areas of high risk. Security investment should be prioritized on the basis of the level of risk. Prioritization should not be based on trends or the discretion of the security manager and industry benchmarking.
- Awareness for security funding should be raised by which of the following?
A. Chief financial officer
B. Chief information officer
C. Information security manager
D. Business process management
Answer: C. Information security manager
Explanation: Responsibility for raising awareness for sufficient and adequate funds for security initiatives resides with the information security manager. Even though the chief information officer, business process owner, and chief audit officer do play important roles in the final approval of funds, the information security manager has the ultimate responsibility to raise awareness for adequate security funds.
- What is the best approach for a security manager who does not have adequate funding for a security program?
A. Discontinue low-priority security controls.
B. Ask management to accept the unaddressed risk.
C. Prioritize risk mitigation and educate management.
D. Reduce reliance on technology and perform more manual processes.
Answer: C. Prioritize risk mitigation and educate management.
Explanation: When funds are inadequate, the best option is to allocate available resources to areas of highest risk and at the same time educate management about the potential impact of underfunding. The other options are secondary factors.
Security program management and administrative activities
Information security program management includes activities to direct, monitor, and control the procedures related to information security. It includes both short-term and long-term planning for the achievement of security objectives. The security manager should ensure that the security program supports the requirements of management. In most organizations, the security manager is responsible for executing the security program. The information security steering committee, which consists of senior leadership from relevant functions of the organization, is responsible for ensuring that security objectives are aligned with business objectives. Senior management represented in the security steering committee is in the best position to support and advocate for the information security program. The role of the steering committee, as well as the security manager, is of utmost importance to ensure that security resources are utilized in an optimized manner. It is the responsibility of the CEO and senior management to support the security initiatives and provide adequate resources and authority to ensure that objectives are achieved.
A security program should be aligned with the program of other assurance functions to ensure that roles and responsibilities are not overlapping and at the same time there are adequate controls to protect the information assets of the organization.
An information security manager is required to be well versed in major security frameworks and international standards such as ISO 27001 and COBIT and be able to implement them as per the requirements of the organization. A framework is generally dependent on the structure, culture, business objectives, and so on of the organization.
The most effective way for an information security manager to perform their responsibilities is to act as a facilitator or consultant to help address the issues that impact the business objectives. They should be able to understand the impact of security on the performance level. There is no use in implementing heavy security if it degrades the performance drastically. The security manager is required to resolve competing objectives between security and performance. As a facilitator and consultant, the security manager is likely to achieve support from senior management and this will improve the effectiveness of the security program.
Information security team
For effective implementation of a security program, the most important element is the availability of skilled personnel resources. An information security team generally includes security engineers, quality assurance and testing specialists, access controllers, project managers, security architects, ethical hackers, security trainers, security auditors, and so on. Each team member should have the appropriate technical and administrative skills in accordance with their job functions. Skills can be in the form of education, expertise, and experience held by the individual. These skills should be mapped with the required job functions. On a lighter note, the following diagram depicts why relevant skills are important:

Figure 6.5 – Information security skills
A security manager should ensure that each security team member possesses and maintains relevant skills.
Roles and responsibilities
A role is a designation assigned to an individual in accordance with their job function. Responsibilities mean the set of actions an individual is required to perform. For example, system administrator is a role, and their responsibilities include assigning access to the system, monitoring system performance, ensuring backup schedules, and so on.
A clear and documented detail of roles, responsibilities, and accountability is necessary to ensure the effective implementation of an information security program.
Role-based access control is very important from a security perspective. An individual is assigned different access on the basis of their role. This will help to ensure that various accesses are provided on a need-to-know basis only.
External resources
Many organizations obtain the services of external resources to manage their information security program. It is of utmost importance to conduct a cost-benefit analysis before appointing external resources. External resources are generally preferred where a skill is required for a short time or for specific projects.
Acceptable usage policy
An acceptable usage policy (AUP) is a summary of the information security policy and procedures and includes details in a user-friendly manner about the acceptable usage of information resources. It helps to effectively communicate the dos and don'ts for improving the security posture of the organization.
Security managers need to ensure that the AUP is made available to all end users and it is read and understood. An AUP generally includes information about access control, information classification, document handling, incident reporting procedures, and other requirements related to end users. An AUP provides a general security baseline for the entire organization.
Documentation
Documentation of security policies and procedures helps to ensure that security procedures are repeatable and sustainable. A security manager is required to provide oversight over the creation and maintenance of security-related documentation. For better handling of documents, it is recommended to assign an owner for each document. The document owner is responsible for updating the documents as per defined procedures of approval and review. The document owner is also responsible for safeguarding the document in accordance with the classification level of the document.
A defined process should be in place for the creation, approval, change, maintenance, distribution, and retirement of a document. Each document should have appropriate classification and labeling to ensure that the document is handled and distributed in a secured manner.
Also, document version control is an important element to ensure the integrity of the document and to ensure that all recipients are using current documentation.
Project management
A security manager should ensure that security-related projects are appropriately managed in accordance with generally accepted project management techniques. Each major project should have defined goals, completion timelines, a process of measuring the progress and adherence to budget, assigned responsibilities, and other elements of project management. This will increase the effectiveness of security-related projects.
In the case of a large organization with multiple projects, the security manager should have a documented portfolio of the projects to determine the progress of each project. A project's portfolio will help to determine the priorities for each project and ensure that projects do not overlap, resources are appropriately allocated, and progress is continuously monitored.
Program budgeting
Budgeting plays a significant role in the effective implementation of an information security program. The availability of adequate security personnel and other security resources is dependent on the security budget. The information security manager should be familiar with the budgeting process and methods used by the organization.
Primarily, the security budget is derived from and supported by the information security strategy. Before seeking approval for the budget, the security manager should ensure that senior management has approved the strategy and other business units have a consensus on the security strategy. This is a key element in a successful budget proposal.
Apart from routine expenditure, the budget should also consider unanticipated costs. Generally, in the area of incident response, it is difficult to predict the expenditure. The security manager may need to obtain external services to support the incident response processes where an organization does not have the necessary skills or bandwidth. The best approach to budget for this kind of situation is to use historical data of incidents and related expenditure. If this information is not available, the security manager may rely on statistics from peer organizations to arrive at a reasonable budget.
Adequate funding for information security is the biggest challenge for a security manager. When funds are inadequate, the best option is to allocate available resources to areas of highest risk and at the same time educate management about the potential impact of underfunding.
Plan – do – check – act
To ensure the effective and efficient management of an information security program, a security manager should implement the following four elements of total quality management (TQM):
- Plan: Structured planning is the most important element for the success of any program. Planning includes developing a strategy to achieve the program objective and scheduling different activities of the program.
- Do: Execute the strategy as per the plan.
- Check: Monitor the progress of the program and determine the areas of improvement. This requires the development of various metrics that indicate the progress or otherwise of the program.
- Act: Take action and address the risks and other irregularities identified by the monitoring processes.
The preceding TQM approach will help in the effective and efficient management of security processes with continuous improvement.
Security operations
A security manager should consider the following aspects of security operations to improve the effectiveness and efficiency of an information security program:
- A security manager should ensure that security monitoring processes such as scanning, testing, audit, and so on do not interrupt any running production process.
- Patches need to be applied as and when important updates are released after being tested. The patch management process should include an appropriate process of testing and approvals.
- It is highly recommended to update the anti-virus signature files on a daily basis. New attack patterns are introduced almost on a daily basis. If signature files are not updated on a daily basis, an organization is exposed to new types of attacks. The effectiveness of anti-virus software primarily depends on virus signatures stored in definition files.
The most effective way to verify that all critical systems are utilizing up-to-date virus signature files is to check sample systems and ensure that signature files installed are the latest ones.
For anti-virus software to be effective, it must be easy to maintain and updated frequently to address new viruses.
- A security manager should take adequate steps to protect the wireless network. Strong encryption is the most effective method to secure a wireless network as a point of entry into a corporate network.
- Implementation of monitoring products such as firewall, IDS, anti-virus, and so on may slow down the performance of the systems and networks. It can create a major impact as a system overhead for servers and networks.
- Overhead means excess or indirect utilization of computation time, memory, bandwidth, and other resources. A security manager should consider this aspect when evaluating products to monitor security across the organization. Monitoring products should support the business processes and should not become a cause of unnecessary interruptions.
- The most important element for the success of an information security program is support and commitment from senior management. If senior management is committed to the robust information security of the organization, there will no constraint for security budget and resources.
Thus, security operations should support the business operations in the most effective and efficient manner.
Key aspects from a CISM exam perspective
The following are some of the key aspects from an exam perspective:

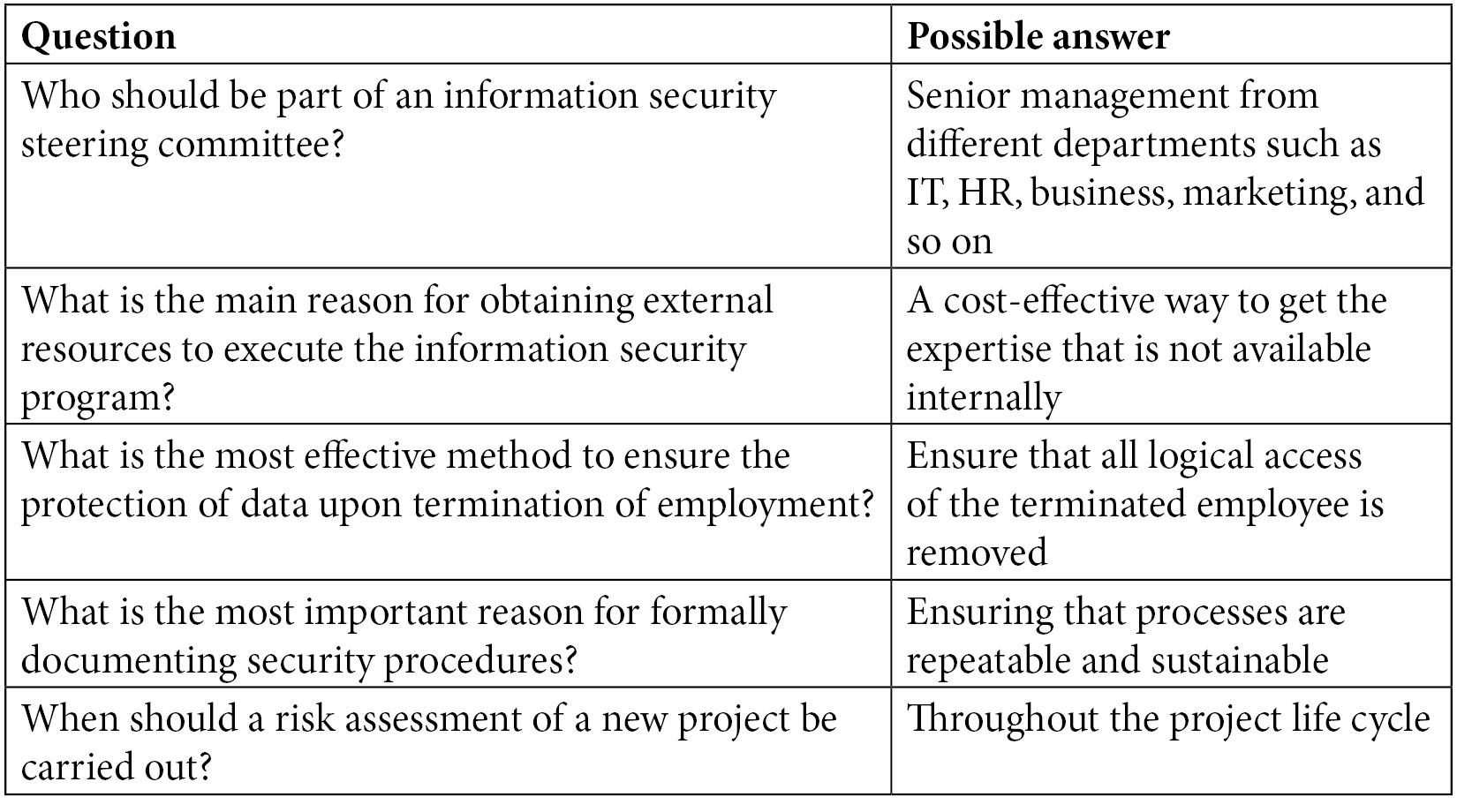
Table 6.7 – Key aspects from the CISM exam perspective
Questions
- What is the most important aspect of the use of a vulnerability scanner?
A. Not to use open source tools.
B. Scan only critical servers.
C. Adhere to the security budget.
D. Not to interrupt the production process.
Answer: D. Not to interrupt the production process.
Explanation: The most important aspect is to ensure that the scan process does not interrupt the production process. There is no harm in using industry-recognized open source tools. The scan should concentrate on all the servers within a network because if any of the servers is compromised then the entire network is in danger. Adherence to the budget is not a major concern.
- The effectiveness of an information security program can be best ensured by which of the following?
A. Chief information officer
B. Head of audit
C. Steering committee
D. Chief operating officer
Answer: C. Steering committee
Explanation: A security steering committee consists of senior officials from different business functions. It plays an important part in the finalization of security requirements. A security steering committee is in the best position to support the establishment of an information security program.
- When should anti-virus signature files be updated?
A. On a daily basis
B. On a weekly basis
C. During the hardware maintenance schedule
D. After the occurrence of a major incident
Answer: A. On a daily basis
Explanation: New attack patterns are introduced almost on a daily basis. If signature files are not updated on a daily basis, an organization is exposed to new types of attacks. The other options are not effective.
- The effectiveness of anti-virus software primarily depends on which of the following?
A. Operating systems
B. Updated patches
C. Application upgrades
D. Definition files
Answer: D. Definition files
Explanation: The effectiveness of anti-virus software depends on virus definition files. If definitions are not updated on a frequent basis, anti-virus software will not be able to control the new types of attacks. The other options are secondary aspects.
- What is the most important criterion for the selection of anti-virus software?
A. Availability of security budget
B. Ability to integrate with a firewall and IDS
C. Automatic alert notification feature
D. Ease of maintenance and frequency of updates
Answer: D. Ease of maintenance and frequency of updates
Explanation: For anti-virus software to be effective, it must be easy to maintain and updated frequently to address new viruses. The other options are secondary factors.
- What is the best way to reduce the risk of accidental system shutdown through the power button?
A. Use redundant power supplies.
B. Use protective switch covers.
C. Set system down alarms.
D. Install biometric readers.
Answer: B. Use protective switch covers.
Explanation: Installing protective switch covers will help to reduce the instances of an individual accidentally pressing the power button and shutting down the system. A redundant power supply will not prevent accidental system shutdown. Shutdown alarms will be after the fact. Biometric readers are generally used for granting access to the system and not for powering on or off the system.
- An information security steering committee should consist of which of the following?
A. External penetration testers
B. Representations from regulatory bodies
C. Board members
D. Leadership from IT, business management, and human resources
Answer: D. Leadership from IT, business management, and human resources
Explanation: The role of a steering committee is to ensure that the security initiatives are in harmony with the organization's mission and objectives. The steering committee monitors and facilitates the deployment of security resources for specific projects in support of business plans. The steering committee should consist of key executives and representatives from user management, which includes leadership from IT, business management, HR, and other departments.
- What is the most important consideration for implementing system monitoring devices?
A. Product documentation
B. Ease of configuration
C. Ease of available support
D. System overhead
Answer: D. System overhead
Explanation: Overhead means excess or indirect utilization of computation time, memory, bandwidth, and other resources. Monitoring products can have a significant impact on system overhead for servers, applications, and networks. A security manager should ensure that monitoring devices do not degrade the performance of servers, applications, and networks. The other options are secondary aspects.
- An organization is using a digital certificate along with a secure socket layer to authenticate a web server. What is the organization still vulnerable to?
A. IP spoofing
B. A man-in-the-middle attack
C. Repudiation
D. A Trojan program
Answer: D. A Trojan program
Explanation: If a computer is infected with a Trojan program, an attacker can take full control of the system and hijack, copy, or modify the information after authentication is done by the user. IP is not used for authentication and hence IP spoofing will not work. SSL along with a digital certificate will prevent a man-in-the-middle attack. A digital certificate will prevent the risk of repudiation.
- What is the most effective way to ensure compliance with an information security policy?
A. To circulate copies of a policy to all employees
B. To perform periodic reviews for compliance
C. To charge a heavy penalty for non-compliance
D. To establish a dedicated helpdesk to support employees
Answer: B. To perform periodic reviews for compliance
Explanation: The best method is to conduct periodic reviews and determine the status of compliance. Gaps, if any, should be addressed appropriately. The other options are secondary factors.
- What is the main advantage of using external resources for managing an information security program?
A. It is a cost-effective way to gain expertise not available internally.
B. It is the most effective way to delegate responsibility for maintaining the security program.
C. It helps to reduce dependency on internal resources.
D. It helps to adhere to the security budget.
Answer: A. It is a cost-effective way to gain expertise not available internally.
Explanation: The primary driver for obtaining the services of external resources is that it helps to contribute cost-effective expertise that is generally not available internally. The other options are secondary factors.
- A server containing an accounting database is maintained by a database administrator. Who should determine the appropriate level of classification?
A. Database administrator
B. Finance department
C. Security department
D. IT department
Answer: B. Finance department
Explanation: The responsibility for determining the appropriate level of classification resides with the data owner. In this case, the finance department is the owner of the accounting data and hence the finance department should determine the level of classification for the server.
- A particular module is accessible to all the members of the development team. The module is used to test the business data. From a security perspective, which of the following is the best option?
A. Restrict the access as read-only.
B. Capture and review logs for all the access.
C. Implement two-factor authentication.
D. Suspend the module and activate only as and when required.
Answer: A. Restrict the access as read-only.
Explanation: The best way is to allow read-only access for the module. The developer should not have the right to modify or download base data. The other options will not be as effective as read-only access.
- The involvement of which of the following groups is very important in the design of security processes to make them accurate and functional?
A. Audit management
B. Compliance management
C. Operational units
D. Legal management
Answer: C. Operational units
Explanation: The most effective way to optimize the security program is to embed security processes with operational processes. The involvement of operational units is of utmost importance to ensure the security process is accurate and functional.
- Which of the following roles should not be given the right to update a database access control list to ensure proper segregation of duties?
A. Team member of the department owning the data
B. Data custodian
C. System programmer
D. Security administrator
Answer: C. System programmer
Explanation: A system programmer should not have the privilege to update an access control list as it enables them to have unlimited control over the system. The data owner, data custodian, or security administrator may need to carry out the updating of access control lists as per their defined job responsibilities.
- As a business requirement, an application programmer requires access to production data. What is the best way to ensure that production data is used only for authorized purposes?
A. Make the application programmer a privileged user.
B. Log all of the application programmer's activity for review by their manager.
C. Take a non-disclosure agreement letter from the application programmer.
D. Conduct a regular audit of the application.
Answer: B. Log all of the application programmer's activity for review by their manager.
Explanation: The best way to mitigate the situation is to capture the log for the activities of the programmer, and it needs to be reviewed by their manager. This will help to detect any inappropriate action on the part of the application programmer. The other options will not be as effective as log capturing and review.
- What is the most important step upon the termination of employment?
A. Take back the identity card.
B. Take back the company-provided laptop.
C. Delete all of the employee's folders.
D. Remove all logical access provided to the employee.
Answer: D. Remove all logical access provided to the employee.
Explanation: The most important step is to remove all the logical access provided to the employee. Upon termination, an employee should not be able to access the organization's data. Taking back the identity card and laptop does not prevent the employee from logging in from external machines. Deleting an employee's folder needs to be considered after analyzing the nature of the data.
- What is the main objective of documenting the security procedure?
A. To ensure the process is repeatable and sustainable
B. To comply with the requirements of the policy
C. To ensure alignment with business objectives
D. To ensure evidence is available for audit
Answer: A. To ensure the process is repeatable and sustainable
Explanation: The primary objective of documenting the security processes is to ensure that processes are repeatable and sustainable. This helps to ensure that security processes are performed correctly and consistently.
- What should a process document for the use of a cryptography document primarily include?
A. Various circumstances where cryptography should be used
B. Type of cryptographic algorithms and key lengths
C. Handling procedures of cryptographic keys
D. Technical aspects of cryptographic solutions
Answer: A. Various circumstances where cryptography should be used
Explanation: The objective of a process document is to support the users to ensure the process is followed in a consistent and correct manner. The most important aspect that should be included in a process document is about circumstances where cryptography should be used. The other options are generally automated and system-driven and hence users may not be required to be involved much.
- When should the risk assessment for a new process be conducted?
A. Before the start of the process
B. Throughout the entire life cycle of the process
C. During the post-implementation review
D. During the development of the business case
Answer: B. Throughout the entire life cycle of the process
Explanation: Risk assessment is not a one-time activity. It should be conducted at every stage of the newly implemented process for the most effective result.
- The security manager notes that employees of the marketing department are sending some critical customer data through email. What should the security manager do first?
A. Discuss the finding with the marketing manager to evaluate the risk and impact.
B. Report the finding to the audit committee.
C. Report the finding to the incident management team for further investigation.
D. Conduct awareness training for the marketing department.
Answer: A. Discuss the finding with the marketing manager to evaluate the risk and impact.
Explanation: The first step for the security manager is to discuss the finding with the marketing manager and determine the risk and impact of such an act. Input from business unit management is very important in deciding the next step. The finding should not be directly highlighted to the audit committee without understanding the risk and impact. The other options are subsequent actions.
- The security manager has obtained commitment and approval from senior management for the establishment of an information security program. What should be their next step?
A. Develop metrics for measuring effectiveness.
B. Conduct a risk assessment.
C. Conduct a gap analysis.
D. Obtain security resources.
Answer: B. Conduct a risk assessment.
Explanation: The first step is to conduct a risk assessment to identify the current needs and requirements of the organization and accordingly develop a security strategy. The other options are subsequent steps.
- The security manager is creating security procedures for the entire organization. Which department should be given priority to write the procedure?
A. Security department
B. Legal department
C. HR department
D. Operations department
Answer: D. Operations department
Explanation: Most of the critical processes and data of the organization are generally handled by the operations department. The operations department has first-hand knowledge about the organization's processes and responsibilities and will help to ensure that written procedures are sound, repeatable, and sustainable.
- What is the best method to address the risk of sending confidential information in an email attachment?
A. To implement content filtering
B. To conduct an email audit
C. To perform security training
D. To encrypt the attachment
Answer: A. To implement content filtering
Explanation: Content filtering is the best tool to address the issue as it has the ability to examine the content of an attachment and prevent information containing specific words or phrases from being sent out of the organization. Encryption will not be effective because it does not prevent confidential information from going out; in fact, content filtering will not be able to read encrypted information. Email audit and security training will not be as effective as content filtering.
Privacy laws
Privacy is the right of the individual to demand the utmost care is taken of their personal information that has been shared with any organization or individual. Individuals can demand that the use of their information should be appropriate, legal, and for a specific purpose for which information is obtained. On a lighter note, nowadays, users are well aware of their privacy rights as depicted in the following diagram:

Figure 6.6 – Privacy laws
The Information Systems Audit and Control Association (ISACA) describes several privacy principles that can be considered as a framework for privacy audits. The following are some of the privacy principles:
- Organizations should obtain appropriate consent before the transfer of personal information to another jurisdiction.
- Organizations should specify the purposes for which personal information is collected.
- Organizations are required to retain personal information only as long as necessary.
- Organizations should have appropriate security safeguards for protecting personal information.
- Organizations should have an appropriate process for reporting compliance with the privacy policy, standards, and laws.
- Organizations should have an appropriate governance mechanism over the third-party service provider processing privacy data on behalf of the organization.
- Organizations should comply with applicable data protection regulations for the transfer of personal information across country borders.
Questions
- A privacy statement primarily includes which of the following?
A. Privacy budget of the organization
B. Notification about the accuracy of the information
C. Notification about what the company will do with the information it collects
D. Notification about the information classification process
Answer: C. Notification about what the company will do with the information it collects
Explanation: Generally, all privacy laws mandate the disclosure of how the information collected will be used. The privacy budget is generally not included in a privacy statement. Notification about the accuracy of information is included in a website disclaimer. Information classification is not part of a privacy statement.
Summary
In this chapter, we discussed information security program development management. This chapter will help CISM candidates understand important methods, tools, and techniques to develop a security program in an effective and efficient manner. This chapter will help CISM candidates to determine the budget requirements to run a security program. They will also have a basic idea about privacy laws and their impact on an information security program.
In the next chapter, we will discuss information security infrastructure and architecture.
