Chapter 3: Overview of Information Risk Management
In this chapter, we will provide an overview of information risk management and understand risk management tools and techniques, along with other important concepts from the perspective of the CISM exam. This chapter will help CISM candidates understand the different aspects of implementing risk management strategies.
The following topics will be covered in this chapter:
- Risk management overview
- Risk management strategy
- Implementing risk management
- Risk assessment and analysis methodologies
- Risk assessment
Let's look at each of these topics in detail.
Risk management overview
The prime objective of a risk management process is to achieve an optimum balance between maximizing business opportunities and minimizing vulnerabilities and threats. To achieve this objective, the information security manager should have a thorough understanding of the nature and extent of the risks that an organization may encounter. A mature organization has a dedicated enterprise risk management (ERM) group to monitor and control such risks.
The first step in developing a risk management program is to establish the context and purpose of the program. Management support can be gained only if the program has an appropriate context and purpose.
Risk management must operate at multiple levels, including strategic as well as operational. The effectiveness of risk management depends on how well risk management is integrated into an organization's culture and the extent to which risk management becomes everyone's responsibility.
Phases of risk management
The overall risk management program includes the following four phases:
- Step 1: Risk identification: In risk identification, various risks impacting the business objectives are identified by way of risk scenarios. In risk identification, the threat landscape and vulnerabilities are identified.
- Step 2: Risk analysis: In risk analysis, the impact and the level of the risk are determined (that is, high, medium, or low). Risk analysis helps determine the exposure to the business and to plan for remediation.
- Step 3: Risk evaluation: In risk evaluation, it is determined whether the risk is within an acceptable range or whether it should be mitigated. Thus, based on risk evaluation, risk responses are decided.
- Step 4: Risk response: Risk response can be in the form of risk mitigation, risk acceptance, risk avoidance, or risk transfer.
A security manager should also understand the outcome of the risk management program, which is detailed in the next section.
The outcome of the risk management program
The most important outcome of an effective risk management program is to reduce the incident that's impacting the business objectives. This can be done by addressing the threat and reducing the vulnerabilities and their exposure. The risk management program supports the organization's ability to operate effectively and efficiently.
Key aspects from the CISM exam's perspective
The following are some of the key aspects from an exam perspective:
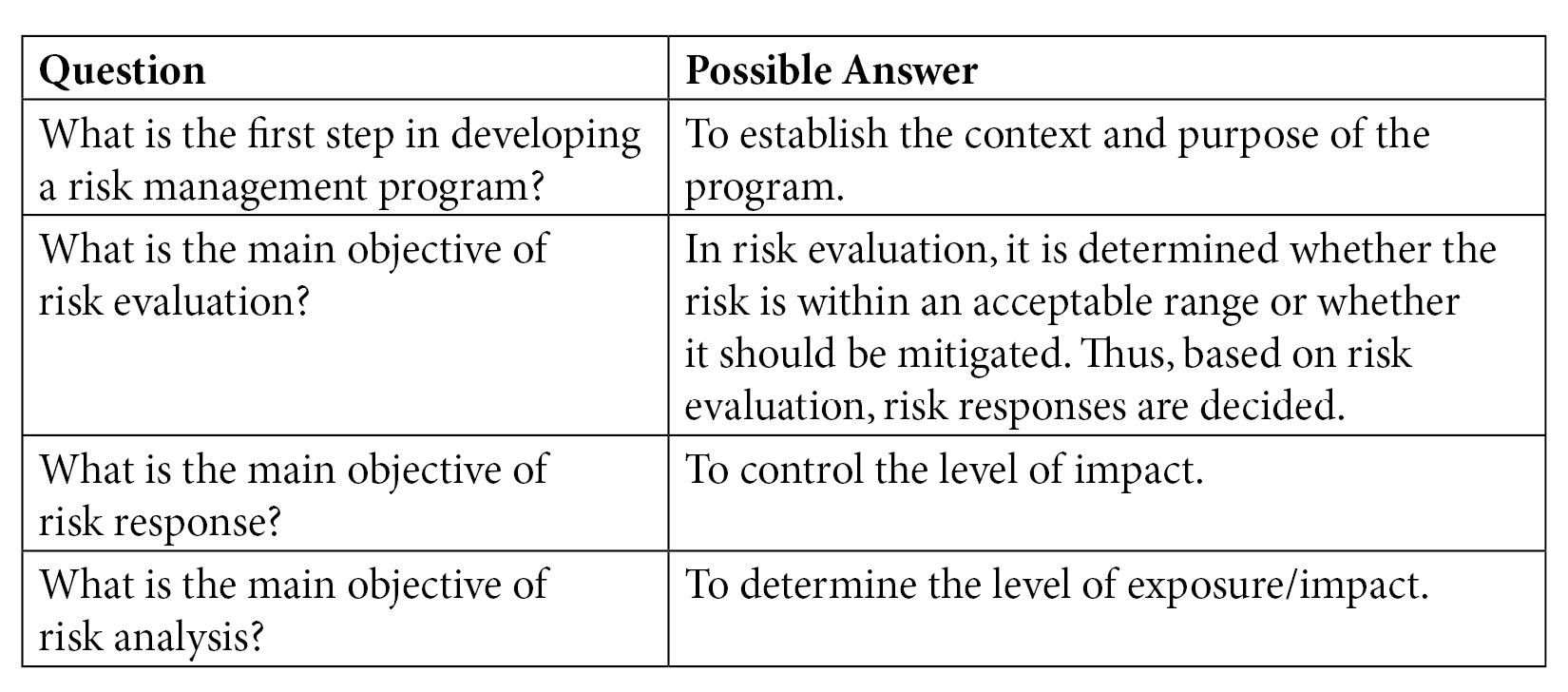
Table 3.1 – Key aspects from the CISM exam perspective
Questions
- The first step in developing a risk management program is to establish what?
A. Management support
B. A security policy and procedure
C. An oversight committee
D. The context and purpose of the program
Answer: D. The context and purpose of the program.
Explanation: The first step is to establish the context and purpose of the program. Management support can only be gained if the program has an appropriate context and purpose. The security policy and oversight committee are subsequent steps.
- What is the main objective of risk evaluation?
A. It provides a basis for selecting risk response.
B. It ensures that all the controls are effective.
C. It provides an assessment of the risk management program.
D. It ensures that risks are categorized appropriately.
Answer: A. It provides a basis for selecting risk response.
Explanation: In risk evaluation, it is determined whether a risk is within an acceptable range or whether it should be mitigated. Thus, based on risk evaluation, risk responses are decided.
- What is the main objective of risk response?
A. To decrease the cost of control
B. To decrease the level of vulnerability
C. To decrease the level of threat
D. To decrease the level of impact
Answer: D. To decrease the level of impact.
Explanation: The most important objective of risk response is to treat the risk in such a way that the impact of the risk is within an acceptable level. Lowering the vulnerability or addressing the threat is one of the approaches to controlling the impact of risk. The objective of risk response is not to decrease the cost of control.
- What is the main objective of risk analysis?
A. To justify the security budget
B. To prioritize the assets to be protected
C. To determine the residual risk
D. To assess the level of exposure and plan for remediation
Answer: D. To assess the level of exposure and plan for remediation.
Explanation: In risk analysis, the impact and level of the risk are determined (that is, high, medium, or low). Risk analysis helps determine the exposure and planning for remediation. Prioritizing assets is the indirect benefit of risk analysis but not the main objective.
Risk management strategy
First, let's understand what a strategy is. A strategy is a plan that helps us achieve the objective. In this sense, a risk management strategy is a plan for achieving the risk management objective. The ultimate objective of any risk management program is to support the business objective by mitigating the risk to an acceptable level. Thus, the main objective of the risk management strategy is to support the business objective.
The risk management strategy should be aligned with the overall governance strategy. It should be consistent and integrated with the overall governance strategy.
Risk capacity, appetite, and tolerance
The first step of learning about risk management is understanding the following three important terms:
- Risk capacity
- Risk tolerance
- Risk appetite
Let's understand the difference between risk capacity, risk appetite, and risk tolerance, as follows:
- Risk capacity: This is the maximum risk an organization can afford to take.
- Risk tolerance: This is made up of two things: that the risk tolerance levels are acceptable deviations from risk appetite, and that they are always lower than the risk capacity.
- Risk appetite: This is the amount of risk that an organization is willing to take.
Now that you have an idea of what these terms are, let's dive into an example.
Example
Mr. A's total savings are $1,000. He wants to invest in equities to earn some income. Since he is risk-averse, he decides to only invest up to $700. If the markets are good, he is willing to invest a further $50. Let's derive the risk capacity, risk appetite, and risk tolerance for this example, as follows:
- Risk capacity: Total amount available; that is, $1,000
- Risk appetite: His willingness to take risks; that is, $700
- Risk tolerance: The acceptance deviation from risk appetite; that is, $750
The following diagram demonstrates the relationship between risk capacity, risk tolerance, and risk appetite:

Figure 3.1 – Risk appetite/tolerance/capacity
We can infer the following from this diagram:
- Risk capacity is always greater compared to tolerance and appetite.
- Tolerance can either be equal to, or greater than, appetite. Risk tolerance levels are acceptable deviations from risk appetite.
- Risk acceptance should generally be within the risk appetite of the organization. In no case should it exceed the risk capacity.
Another important aspect for a security manager is to understand in terms of risk communication, which we will discuss in the next section.
Risk communication
The communication of risk management activities is key to effectively implementing a risk management strategy. Communication should involve all the relevant stakeholders. Communication channels should have the ability to provide interaction both ways; that is, management can communicate to end users and end users should also be able to pass on information related to risks to management.
Risk awareness
Having an awareness of risk management programs improves the risk culture of the organization. Awareness is a key element that impacts the behavior of end users. Through an awareness program, each member of the organization can help identify vulnerabilities, suspicious activities, and other abnormal behavior patterns. This helps with responding faster to an attack or incident and thus minimizing the impact.
Tailored awareness program
An effective awareness program should be tailored to the needs of the individual groups. Specific awareness content, as applicable to respective job functions, enhances the effectiveness of awareness training. For example, a developer can be made aware of the secure coding practices, whereas the end user may be made aware of the risk of phishing emails.
While developing an awareness program, the following aspects need to be considered:
- The awareness program should be capable of highlighting the relevant risk.
- The awareness program should be able to highlight the impact if risks are not controlled.
- The awareness program should not openly discuss open vulnerabilities or the details of an ongoing investigation.
- The awareness program should periodically change messages and communication channels so that it's more effective.
Training effectiveness
It is equally important to determine the effectiveness of awareness training at periodic intervals. Metrics can be in the form of security quizzes, phishing attack simulations, blind penetration tests, and so on.
Awareness training for senior management
Senior management should be frequently reminded that they are the ones who own the risk and are responsible for implementing the relevant controls. The highlights for senior management should be regulatory requirements, the impact on business objectives, and the liability of the organization. Senior management plays an important role in adopting a risk-aware culture in the organization.
Key aspects from the CISM exam's perspective
The following are some of the key aspects from an exam perspective:

Table 3.2 – Key aspects from the CISM exam perspective
Questions
- What is the most effective strategy for risk management?
A. To achieve a balance between risk and business goals
B. To reduce the risk to an acceptable level
C. To develop policy statements
D. To document all unmitigated risks
Answer: B. To reduce the risk to an acceptable level.
Explanation: The most effective strategy for risk management is to reduce the risk to an acceptable level. This will help the organization manage risk as per their risk appetite. It may not always be practical to achieve a balance between risk and business goals. Developing a policy statement and documentation of the risks is not as significant as reducing the risk to an acceptable level.
- Risk assessment is always subjective. The best way to improve the accuracy of the assessment is to do what?
A. Provide training to the assessor
B. Use a standardized assessment framework
C. Ensure the independence of the assessor
D. Use a different framework
Answer: A. Provide training to the assessor.
Explanation: The best way to reduce the subjectivity of the risk assessment is to provide frequent training to the risk assessor. This improves the accuracy of assessment. Without appropriate training, other options may not be effective.
- What is the main objective of the risk management program?
A. To reduce the inherent risk
B. To eliminate all the risk
C. To establish effective control
D. To achieve acceptable risk
Answer: D. To achieve acceptable risk.
Explanation: The main objective of a risk management program is to ensure that risk is within a level acceptable to management. If an inherent risk is already within the acceptable level, there is no need to further reduce the same. It is not practical and feasible to eliminate all risks. The ultimate objective of establishing effective control is to ensure that risks are within an acceptable level.
- What is the most effective way to ensure the overall effectiveness of the risk management program?
A. The program is convenient to implement.
B. The program is adopted from industry standards.
C. The program is monitored by senior management.
D. The program is supported by all members of the organization.
Answer: D. The program is supported by all members of the organization.
Explanation: For effective risk management, the most important criterion is that the program should be supported by all members of the organization. All staff members should be able to understand their roles and responsibilities concerning risk management. The other options are secondary criteria.
- The objective of the risk management program is to reduce the risk to what?
A. Nil
B. An acceptable level
C. An acceptable percentage of revenue
D. Eliminate all the hazards
Answer: B. An acceptable level.
Explanation: The objective of a risk management program is to reduce the risk to an acceptable level for management. Reducing the risk to zero is not possible.
- The information security team noted that management has not mitigated the risk, even though the risk exceeds the risk appetite. What is the most likely reason for this?
A. Controls have already been applied.
B. Controls are expensive.
C. The risk is within the risk tolerance level.
D. The probability of it occurring is very low.
Answer: C. The risk is within the risk tolerance level.
Explanation: Risk tolerance is an acceptable level of deviation from risk appetite. Generally, risk tolerance is slightly higher than risk appetite. Other options are not the main factor for ignoring risk.
- For effective risk management, it should be applied to what?
A. All organizational processes
B. Processes identified by a risk assessment
C. Processes whose risk appetite is low
D. Processes that can have a potential impact
Answer: A. All organizational processes.
Explanation: Risk management should be applied to all the processes of the organization. Whether a risk level is acceptable can only be determined when the risk is known.
- What is the best way to support the business objectives through risk management?
A. The risk assessment is to be performed by asset owners.
B. Timely updates of the risk register.
C. Monitoring by the steering committee.
D. Risk activities are embedded in business processes.
Answer: D. Risk activities are embedded in business processes.
Explanation: The main objective of a risk management process is that risk is identified and mitigated promptly. This can be best done by embedding risk activities into all business processes. The other options are not as significant for embedding risk management activities into business processes.
Implementing risk management
Implementing a risk management program is one of the important aspects for ensuring effective and efficient governance, risk management, and compliance (GRC). The security manager should identify the existing risk management activities and try to integrate these activities to utilize resources. Integrating risk management activities helps prevent efforts from being duplicated and minimizes the gaps in assurance functions.
Risk management process
Implementing a risk management program in a structured way helps you achieve maximum efficiency and effectiveness with minimum effort. It is recommended to implement the program as per the following sequence:
- Determine the scope and boundaries of the program.
- Determine the assets and processes that need to be protected.
- Conduct a risk assessment by identifying the risks, analyzing the level of risk based on the impact, and evaluating whether the risk meets the criteria for acceptance.
- Determine the risk treatment options for risks that are above the acceptable level. Risk treatment can be in any of the following forms:
- Mitigating the risk by implementing additional controls.
- Accepting the risk (generally, this option is selected when the impact is low and the cost of treatment exceeds the impact).
- Avoid the risk (generally, this option is selected when the feasibility study or business case does not indicate positive results).
- Transfer the risk to third parties such as insurance companies (generally, this option is selected for a low probability risk that has a high impact, such as natural disasters).
An appropriate risk treatment method helps achieve the control objective efficiently.
- Determine the acceptability of the residual risk (that is, any risks remaining after treatment) by management.
- Monitor the risk continuously and develop an appropriate procedure to report the results of risk monitoring to management.
During all these steps, it is equally important to share relevant information about risk management activities with concerned stakeholders. Having an effective communication process improves the whole risk management process.
Effective risk management requires participation, support, and acceptance by the relevant members of the organization, starting with senior management. Employees must understand their responsibilities and be able to perform their required roles.
Risk controls are measures and are considered to be sufficient when the residual risk is less than or equal to an acceptable risk.
Integrating risk management in business processes
For effective risk management, the risk management processes must be integrated with the business processes. The best way to implement this is to conduct workflow analysis, understand the process vulnerabilities, and build the relevant controls within the process.
Prioritization of risk response
It may not be feasible for the organization to address all the risks. In such cases, the risk should be prioritized based on its criticality. High-level risks should be addressed first. Prioritizing the treatment options will be most effective if they're based on the likelihood of compromise and their impact on the business.
Defining a risk management framework
A framework is a structure or outline that supports the implementation of any program. Frameworks are flexible structures that any organization can adopt as per their environment and requirements. Many standards and guidelines on best practices are available for effectively managing IT risk, such as the following:
- COBIT
- ISO 31000 on Enterprise Risk Management
- ISO 27001 on the Information Security Management System
Generally, all these frameworks/standards have the following requirements:
- The documented policy that defines the objective of the program must be available.
- The documented roles and responsibilities for implementing the program must be available.
- Commitment from senior management to review the program frequently.
- Procedure documents must be available.
- Adequate records to satisfy an independent audit must be available.
By defining the risk management framework, the basic parameters for managing the risk are established. Basic parameters include criteria for acceptable risk, the objective of the controls, and processes to monitor the effectiveness of these controls. A framework helps achieve the following objectives:
- Having a common understanding of organizational objectives.
- Developing a set of criteria for measuring risk.
- Developing a structured process for identifying risk and assessing the level of risk.
- Integrating different assurance functions.
Defining the external and internal environment
While designing the risk management program, the requirements of the stakeholders should be considered. Stakeholders can be either external or internal. External context includes laws and regulations, social and cultural conditions, risk from competitors, financial and political environment, and so on. It also includes considering threats and opportunities that have been generated by external sources.
The internal context includes the management requirements, the organization's structure, culture, goals, and objectives, and the organization's strengths and weaknesses.
Determining the risk management context
Context means the scope and applicability of risk management activities. Context defines the environment in which risk management will operate. A security manager needs to understand the risk management context. Context is generally determined by the culture of the organization in terms of risk averseness or risk aggressiveness.
Gap analysis
Gap analysis is the process of determining the gap between the existing level of the risk management process compared to the desired state. Based on the desired state, control objectives are defined. The objective of gap analysis is to identify whether control objectives can be achieved through the risk management process.
Periodically determining the gap between the actual controls and their objectives should be routine practice. Gap analysis is generally done by determining the effectiveness of controls through control testing. If a gap is identified, then the controls may need to be modified or redesigned to improve their effectiveness.
Cost-benefit analysis
The most important factor when selecting controls is the cost-benefit balance. Implemented controls should be effective (that is, able to address the risk) as well as efficient (providing the most benefit compared to cost incurred).
Cost-benefit analysis is performed to ensure that the cost of a control does not exceed its benefit and that the best control is implemented for the given cost. Cost-benefit analysis helps justify the implementation of a specific control measure.
Other kinds of organizational support
Organizations can rely on the services of external service providers to understand the current threat landscape and to identify industry-level best practices. These services help leverage the expertise of service providers and improve the security posture of the organization. Some of the most widely used services are as follows:
- Organizations such as ISACA, NIST, ISC, and SANs, which often publish best practices and other industry-wide data that can be used to determine and evaluate the security program.
- Many organizations sponsor security-related roundtables to discuss topics of common interest. This helps accumulate the knowledge base from experts in the industry.
- Various organizations sponsor research and studies related to security-related aspects.
- Many institutes are involved in training related to security aspects such as vulnerability assessment, penetration testing, secure coding, and end user awareness.
- Many organizations release a list of current vulnerabilities impacting specific technology. This can be either a free service or a subscription-based service. External vulnerability sources are the most cost-effective way of identifying new vendor vulnerabilities.
Information security is an ever-evolving subject and security managers should keep themselves updated by using these sources.
Key aspects from the CISM exam's perspective
The following are some of the key aspects from an exam perspective:


Table 3.3 – Key aspects from the CISM exam perspective
Questions
- What is the most effective way to address the risk of data leakage?
A. Availability of backup procedures
B. Availability of data integrity checks
C. Availability of acceptable usage policy
D. Availability of the incident management process
Answer: C. Availability of acceptable usage policy.
Explanation: An acceptable usage policy is a document stipulating constraints and practices that a user must agree on to use organizational resources. Many organizations require employees to sign an acceptable use policy before access is granted. Other options may not directly impact data leakages.
- What is the best way to identify new vendor vulnerability cost-effectively?
A. External vulnerability reporting sources
B. Network scanning software
C. Periodic vulnerability assessment
D. Implementing honeypots
Answer: A. External vulnerability reporting sources.
Explanation: Many agencies publish new vulnerabilities and provide recommendations to address the vulnerabilities. This is the most cost-effective way to understand new vulnerabilities. Other options may not be as cost-effective as external vulnerability sources.
- What is the SDLC phase in which risk assessment should first be conducted?
A. Implementation
B. Testing
C. Programming
D. Feasibility
Answer: D. Feasibility.
Explanation: Risk assessment should commence at the earliest phase of SDLC; that is, the feasibility phase. The feasibility study should include risk assessment so that the cost of controls can be determined at the beginning.
- What is the most important factor for implementing controls and countermeasures?
A. Reducing IT risk
B. Cost-benefit balance
C. Resource utilization
D. Count of assets protected
Answer: B. Cost-benefit balance.
Explanation: Selecting controls and countermeasures primarily depends on cost-benefit analysis. The others are secondary factors.
- Which area is the data owner responsible for risk mitigation?
A. Operating system security
B. User entitlements
C. Network security
D. Intrusion detection
Answer: B. User entitlements.
Explanation: The data owner is accountable for ensuring that access to their data is provided based on user entitlement and on a need-to-know basis. The other options are the responsibility of the security team.
- Taking out insurance is an example of what?
A. Risk avoidance
B. Risk acceptance
C. Risk transfer
D. Risk mitigation
Answer: C. Risk transfer.
Explanation: Taking out insurance is an example of risk transfer. In risk transfer, the risk is shared with partners or transferred via insurance coverage, a contractual agreement, or other means. Natural disasters have a very low probability but a high impact. A response to such risks should be risk transfer.
- The mitigating control should be decided by who?
A. Senior manager
B. Business manager
C. Audit manager
D. Security manager
Answer: B. Business manager.
Explanation: The business manager will be in the best position to decide on any particular control based on the risk assessment as they are aware of the risks that are relevant to their processes. The senior manager should provide appropriate funding for the control. The audit and security managers support the business manager by reviewing and monitoring the effectiveness of the control.
- What is the prime objective of a gap analysis?
A. To evaluate the business impact
B. To design a balanced score card
C. To determine the overall cost of control
D. To measure the current state versus the desired future state
Answer: D. To measure the current state versus the desired future state.
Explanation: The objective of a gap analysis is to identify the gap between the current level of control versus the desired level of control. This gap is also known as control deficiencies. Risk practitioners analyze the desired state of the risk management requirements of the organization and then determine the current condition of the risk management affairs. This helps them identify the gaps. They should recommend that the gaps are closed.
- Which risk of a new application should be assessed first?
A. Feasibility
B. Design
C. Development
D. Testing
Answer: A. Feasibility.
Explanation: It is always advisable to identify and address the risk at the early stage of new system development. The risk of the new system may challenge the feasibility of the system's development.
- What is the most effective way to select a control when there is a budget constraint?
A. A business impact analysis
B. A risk analysis
C. A cost-benefit analysis
D. A vulnerability analysis
Answer: C. A cost-benefit analysis.
Explanation: The objective of a cost-benefit analysis is to determine the benefits compared to the cost of the project. If the benefit that's realized from the control is less than the cost of implementing the control, then it does not justify implementing it. Selecting a control is primarily based on a cost-benefit analysis.
- An organization started operating in a country where identity theft is widespread. What is the best course of action for the organization?
A. Set up monitoring techniques to detect and react to fraud.
B. Make the customer liable for fraud.
C. Make the customer aware of the possibility of fraud.
D. Outsource the process to a well-established service provider.
Answer: A. Set up monitoring techniques to detect and react to fraud.
Explanation: The best course of action for the organization in this situation is to set up monitoring techniques to detect and react to potential frauds. It is not possible to make customers liable for the fraud. Making customers aware of fraud is a good option but not as effective as setting up monitoring techniques. For outsourcing the process, a business case needs to be reviewed so that decisions can be made. However, the most effective method would be setting up monitoring techniques to detect and react to fraud.
- What is the first step in establishing a data leakage program?
A. Create user awareness training
B. Develop an information classification program
C. Design network control
D. Develop physical control
Answer: B. Develop an information classification program.
Explanation: The first step is to develop a classification program. Based on that, critical data can be identified. The other options are subsequent steps.
- What is the most effective way to mitigate a phishing attack?
A. Create user awareness training.
B. Email encryption.
C. Develop two-factor authentication.
D. Develop physical control.
Answer: A. Create user awareness training.
Explanation: Phishing is an attack where employees are contacted via email by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords. The best way to combat this attack is by providing frequent user awareness.
- What is the next step after identifying residual risk?
A. Transferring risk to an insurance company
B. Transferring risk to a third-party service provider
C. Determining that residual risk is acceptable
D. Accepting the residual risk
Answer: C. Determining that residual risk is acceptable.
Explanation: Once the residual risk has been determined, the next step is to validate whether the residual risk is acceptable. If the risk is within the risk appetite, it can be accepted. Otherwise, further controls are to be implemented to reduce the same.
- What is the best response to a risk scenario with low probability and high impact, such as a natural disaster?
A. Risk avoidance
B. Risk acceptance
C. Risk transfer
D. Risk mitigation
Answer: C. Risk transfer.
Explanation: Taking out insurance is an example of risk transfer. In risk transfer, the risk is shared with partners or transferred via insurance coverage, a contractual agreement, or other means. Natural disasters have a very low probability but a high impact. A response to such a risk should be risk transfer.
- What is the most important factor in determining an acceptable level of IT risk?
A. Organizational requirements
B. Security requirements
C. International standards
D. Audit requirements
Answer: A. Organizational requirements.
Explanation: The acceptable level of risk is determined by the overall organizational requirements. Other options may not directly determine an acceptable level of IT risk.
- What is the best way to mitigate the liability risks that arise due to breaches in privacy laws?
A. To mitigate the impact by purchasing insurance
B. To implement an application-level firewall
C. To conduct a business impact analysis
D. To implement an intrusion prevention system
Answer: A. To mitigate the impact by purchasing insurance.
Explanation: The best way is to purchase insurance to compensate for the financial liability. Privacy laws aim to protect the privacy of the customer and generally mandate heavy penalties for data breach incidents. Breaches can still happen, even after implementing technical controls, so the best way is to purchase insurance.
- What is the outcome of a successful risk management program?
A. The organization can quantify the risk.
B. The organization can eliminate the inherent risk.
C. The organization can minimize the residual risk.
D. The organization can monitor control risk.
Answer: C. The organization can minimize the residual risk.
Explanation: The prime objective of any risk management program is that residual risk is minimized and is within the risk appetite of the organization. It is not practical and feasible to eliminate inherent risk. The quantification of risk and the monitoring thereof is a good indicator, but something more significant is minimizing the residual risk.
- What is the best way to protect confidential information from insider threats?
A. Role-based access control
B. Capturing transaction logs
C. Developing a privacy policy
D. Defense-in-depth
Answer: A. Role-based access control.
Explanation: The best way is to provide access to confidential information on a need-to-know basis, which can be done through role-based access control. Defense-in-depth is generally for external threats. Capturing transaction logs is a detective control.
- Risk acceptance is one of the components of which of the following?
A. Risk reporting
B. Risk treatment
C. Risk monitoring
D. Risk assessment
Answer: B. Risk treatment.
Explanation: Risk treatment consists of four options: risk acceptance, risk avoidance, risk mitigation, and risk transfer.
- A security manager has determined the likelihood of a risk event. What should be assessed next to determine the level of risk?
A. Magnitude of impact
B. Tolerance for the risk
C. Appetite for the risk
D. Asset book value
Answer: A. Magnitude of impact.
Explanation: To determine the risk level, two things are required: the probability (likelihood) of the event and the impact of the event. The risk is a combination of probability and impact. Once the likelihood has been determined, the next step is to assess the magnitude of the impact. Once the level of risk has been determined, it is compared against risk appetite and risk tolerance.
- What is the most important aspect of risk?
A. Threat and impact
B. Likelihood and consequences
C. Impact and insurance
D. Sensitivity and threat
Answer: B. Likelihood and consequences.
Explanation: To determine the risk level, two things are required: the probability of the event and the impact of the event. Risk is a combination of probability (likelihood) and impact (consequences).
- What is the prime objective of segmenting a critical database?
A. To reduce the threat
B. To reduce the sensitivity
C. To reduce the criticality
D. To reduce the exposure
Answer: D. To reduce the exposure.
Explanation: Segmenting the data helps reduce exposure as more controls are implemented for segmented critical databases. Segmentation by itself does not reduce threats, sensitivity, or criticality.
- What is the main objective of implementing security aspects during the first stage of the project life cycle?
A. To minimize the cost of security
B. To determine project feasibility
C. To obtain budget approval
D. To classify the project
Answer: B. To determine project feasibility.
Explanation: Information security requirements may directly impact the feasibility of the project. The cost of security must be considered while calculating business cases and feasibility studies. Sometimes, the cost of security may exceed the benefit that's expected from the project, so you may not be able to implement the project.
- What is the main objective of including an indemnity clause in a service-level agreement?
A. To decrease the probability of the incident
B. To limit the impact on the organization
C. To comply with regulatory requirements
D. To improve performance
Answer: B. To limit the impact on the organization.
Explanation: The objective of the indemnity clause is to compensate or recover from any losses due to a breach of the agreement. It helps reduce the financial impact on the organization. An indemnity clause may not always be a regulatory requirement. Merely by incorporating an indemnity clause, probability cannot be reduced, and performance improvement cannot be ensured.
- The information security manager has noted that due to slow biometric responses and a large number of employees, a substantial amount of time is wasted in gaining access to buildings. This has also increased instances of piggybacking. What should the security manager do?
A. Replace the biometric system with a better response time
B. Escalate the issue to management
C. Discontinue the use of the biometric access system
D. Ensure strict enforcement
Answer: B. Escalate the issue to management.
Explanation: Management will be the best position for addressing such kinds of issues where security requirements are adversely impacting the business.
- In a BCP, prioritizing an action is primarily dependent on what?
A. A business impact analysis
B. A risk analysis
C. A threat analysis
D. A vulnerability assessment
Answer: A. A business impact analysis.
Explanation: A business impact analysis helps determine the critical processes/assets of the organization. These critical processes/assets should be recovered on priority.
- What is the most effective way to determine the existing level of risk?
A. A vulnerability analysis
B. A threat analysis
C. An impact analysis
D. A security review
Answer: D. A security review.
Explanation: A security review is conducted to determine the current state of the security posture of the organization. Vulnerability and threat analyses will help determine the level of vulnerability and threat, but without knowing about the existing security arrangement, existing risks cannot be determined. An impact analysis is more effective for determining the potential impact of a loss event.
- What are the results of the risk management process used for?
A. Changing business objectives
B. Updating audit charters
C. Making security policy decisions
D. Updating SDLC processes
Answer: C. Making security policy decisions.
Explanation: The risk management process helps highlight the risks that can impact the business processes. It helps make security policy decisions address the highlighted risks. The risk management process is used to support the business objectives and not change them. The audit charter highlights the roles and responsibilities of the audit department and is not directly impacted by the risk management process.
- What is the best way to determine the most critical factor among confidentiality, integrity, and availability?
A. Based on the threats that can be applied to each factor
B. Confidentiality should always be given preference
C. Based on the risks that can be applied to each factor
D. All three factors should be treated equally
Answer: C. Based on the risks that can be applied to each factor.
Explanation: The most important factors are considered based on the risks that can be applied to them. For example, if an automatic door fails, the organization can opt for fail open (the door should remain open) or fail closed (the door should remain closed). In the case of fail open, confidentiality and integrity may be compromised, while in the case of fail closed, availability may be compromised. In such a situation, risks must be determined for each element and a call needs to be given. Considering only the threat elements will not serve this purpose as both the threat and its impact (that is, the overall risk) need to be considered.
- What area is of most concern for a security manager concerning a homogeneous network?
A. Risk of reliability
B. Single point of failure
C. Slow network performance
D. Aggregated risk
Answer: D. Aggregated risk.
Explanation: A homogenous network is a computer network comprised of similar configurations and protocols. This allows for common threats for all the devices, so a major concern is that all the devices are being impacted by a single threat. The other options are not directly impacted by homogeneous networks.
- The recommendation to implement information system controls such as antivirus software is an example of what?
A. Risk acceptance
B. Risk mitigation
C. Risk transfer
D. Risk avoidance
Answer: B. Risk mitigation.
Explanation: Risk mitigation is the act of implementing security controls to reduce the impact of risk and bringing the risk level down to an acceptable level.
- What is the best risk treatment method?
A. A method that eliminates risks completely
B. A method that is least costly
C. A method that addresses the control objective
D. A method that reduces the risk as much as possible
Answer: C. A method that addresses the control objective.
Explanation: The control objective is met when risk is mitigated effectively and efficiently. The best risk treatment should be both effective (that is, it should be able to address the risk) and efficient (that is, the cost of treatment should be optimal).
- What is the prime objective of a cost-benefit analysis before control is implemented?
A. It helps us adhere to a budget.
B. It is a mandatory requirement by senior management.
C. Conducting industry benchmarks.
D. Ensuring that costs are justified by the reduction in risk.
Answer: D. Ensuring that costs are justified by the reduction in risk.
Explanation: The main objective of a cost-benefit analysis is to ensure that the cost of the project does not exceed the benefit expected from the project. The cost should be justified by an appropriate reduction in the risk.
- What is the most effective way to mitigate the critical vulnerabilities identified during a recent security test?:
A. All the vulnerabilities should be addressed immediately.
B. Mitigation should be based on threat, impact, and cost considerations.
C. Mitigation should be based on the available security budget.
D. Compensating controls must be implemented for major vulnerabilities.
Answer: B. Mitigation should be based on threat, impact, and cost considerations.
Explanation: Mitigation must consider the level of risk and the cost of various treatment options. High-risk vulnerabilities should be addressed based on priorities. Low-risk vulnerabilities may not be addressed immediately. Resources should be utilized first to address any high-risk vulnerabilities.
- What is the most effective way to address the risk of the acquisition of new IT resources?
A. Acceptance of the risk by the IT manager.
B. To obtain approval of compliance before acquiring the new system.
C. To obtain approval from the senior manager before acquiring the new system.
D. Implement the appropriate procurement process.
Answer: D. Implement the appropriate procurement process.
Explanation: The most important aspect is to implement a structured process that will help identify the risks that may be introduced by the new system. Options A, B, and C can be made part of a structured process.
- When should a risk assessment be performed in an SDLC life cycle?
A. Only before starting development
B. During the system deployment stage
C. During the feasibility stage
D. At each stage of the SDLC life cycle
Answer: D. At each stage of the SDLC life cycle.
Explanation: Risk management should be performed at each stage of the SDLC life cycle. This will help in identifying risks early as they can occur during any stage.
- The enterprise's current risk appetite can be best quantitatively indicated by which of the following?
A. A count of the incidents and subsequent mitigation efforts
B. Layers of implemented controls
C. Level of security requirements in policy and standards
D. Ratio of cost to insurance coverage for business interruption protection
Answer: D. Ratio of cost to insurance coverage for business interruption protection.
Explanation: The best quantification is to derive the cost of business interruption and the level of insurance that's been taken to protect against such losses. For example, let's say that the cost of business disruption is $100,000 and that the insurance covers up to $80,000. Here, the risk appetite of the organization can be considered $20,000. Other options will only provide a rough estimate of the risk appetite.
- What is the most effective way to manage a security program with low funding?
A. Remove security services that address low risk.
B. Accept all the remaining risks.
C. Use third-party service providers to manage low-risk activities.
D. Eliminate monitoring and reporting activities.
Answer: C. Use third-party service providers to manage low-risk activities.
Explanation: The best option is to use the services of a third party that has expertise in information security. This will result in cost reductions and ensure that the security requirements are adhered to. Other options are not feasible and practicable and increase security risks.
- When is the control level said to be appropriate?
A. The risk acceptable level is less than the total risk level.
B. The residual risk level is less than the risk acceptable level.
C. The residual risk level is more than the risk acceptable level.
D. The annual risk expectancy is more than the risk acceptable level.
Answer: B. The residual risk level is less than the risk acceptable level.
Explanation: Controls are said to be effective when the residual risk is less than the risk acceptance level. The residual risk is the risk that remains once the controls have been implemented. An acceptable level of risk is the willingness of the management to take risks.
- What is the most important factor for risk-based information security programs?
A. Prioritization
B. Threat
C. Standardization
D. Budget
Answer: A. Prioritization.
Explanation: Prioritization helps determine the importance of assets/processes that need to be addressed first. Prioritization is done based on risk level. The highest risks are addressed first on a priority basis. Threats are not sufficient as we need to consider the vulnerability as well as impact.
- An organization has two servers having similar content, but only if the server is hardened. What is the most plausible reason for this?
A. The second server is only a backup server.
B. The second server supports non-critical functions.
C. The second server has been placed where there is no exposure.
D. The second server is monitored continuously.
Answer: C. The second server has been placed where there is no exposure.
Explanation: If the second server is placed where there is no exposure, then there is no chance of compromise and hence hardening may not be required. For other options, such as having a second server in a backup server, it supports non-critical functions, or it is monitored continuously, while the risk remains the same as it contains the identical content, so it should be given the same level of protection as the first server.
- What is the most effective risk treatment where the probability of the event occurring is very low but the impact can be very high?
A. Accept the high cost of controlling such an event.
B. Install the detective control.
C. Avoid the risk.
D. Transfer the risk to a third party.
Answer: D. Transfer the risk to a third party.
Explanation: The best risk response in such a scenario (low probability and high impact) is to transfer the risk to a third party. Insurance for natural calamities is one such example. This will help the organization compensate itself for financial losses.
- What is the first course of action when integrating risk management practices into business processes?
A. A workflow analysis
B. A threat analysis
C. A hierarchy analysis
D. A business impact analysis
Answer: A. A workflow analysis.
Explanation: A workflow analysis is the process of understanding the workflow and helps determine the risk and build relevant controls. The other steps follow this step.
- An indemnification clause in a service agreement does what?
A. Addresses the legal as well as the financial liability of the organization
B. Makes it preferable to purchasing insurance
C. Addresses the reputational risk of the organization
D. Addresses the financial liability but leaves legal and reputational risk generally unchanged
Answer: D. Addresses the financial liability but leaves legal and reputational risk generally unchanged.
Explanation: The objective of an indemnity clause is to compensate the organization for any financial loss due to what the service provider has done. However, it does not reduce the legal or reputation risk for the organization.
- Reducing exposure will result in what?
A. A reduction in impacts, if compromised
B. A reduction in vulnerabilities
C. A reduction in the likelihood of being exploited
D. A reduction in the time needed to recover
Answer: C. A reduction in the likelihood of being exploited.
Explanation: Reducing exposure means keeping the information assets away from public reach. For example, a sensitive database is not connected through the public internet. This reduction in exposure will reduce the likelihood of being exploited. However, this will not automatically reduce other vulnerabilities. Also, it will not reduce the impact in case the database is compromised.
- Residual risk is best determined by what?
A. Management discretion
B. Legal requirements
C. Level of security budget
D. Audit findings
Answer: A. Management discretion.
Explanation: Residual risk means the risk that management is willing to accept. It is an acceptable level of risk for management. Residual risk is ultimately subject to management discretion.
- Prioritization of risk is based on what?
A. Asset value
B. Frequency and impact
C. Legal requirements
D. Frequency and scope
Answer: B. Frequency and impact.
Explanation: Risk is a product of probability and impact. Frequency (that is, probability) and impact can help determine the actual level of risk. Both terms are equally important when determining the level of risk. Each risk is determined based on its frequency (that is, probability), and impact and high-level risks are prioritized and addressed first. The other options are not as important as frequency and impact.
- What is the best indicator of a quantifiable acceptable level of risk?
A. Interviewing senior management
B. Ratio of security budget to total budget
C. Ratio of insurance coverage to the total cost of business interruption
D. Determining the count of an incident impacting the organization
Answer: C. Ratio of insurance coverage to the total cost of business interruption.
Explanation: The objective here is to determine the acceptable level of risk by management. The best quantification is to derive the cost of business interruption and the level of insurance taken to protect against such losses. For example, the cost of business disruption is $100,000 and the insurance covers up to $80,000. Here, the risk appetite of the organization can be considered $20,000. The other options will only provide a rough estimation of the risk appetite.
- What is the most important outcome of a risk management program?
A. Continuous monitoring of vulnerabilities
B. Continuous monitoring of threats
C. Determining the implementation of control objectives
D. Decreasing the number of incidents impacting the organization
Answer: D. Decreasing the number of incidents impacting the organization.
Explanation: The most important objective of a risk management program is to reduce the number of incidents that harm the objective of the organization. The other options are specific and actionable to achieve the outcome of addressing the adverse incidents.
- Effectively protecting information assets strongly supports which of the following?
A. Data workflow
B. Data classification policy
C. Security culture
D. Business-oriented risk policy
Answer: D. Business-oriented risk policy.
Explanation: A risk policy that is aligned with business objectives helps in achieving an organization's objectives. A business-oriented risk policy is strongly supported by effectively managing information assets. The other options do not directly impact the effectiveness or efficiency of information assets.
- What is the most effective option for addressing the defined threat?
A. Implementing a deterrent control
B. Reducing the exposure
C. Implementing a compensating control
D. Implementing an administrative control
Answer: B. Reducing the exposure.
Explanation: If a threat is already known, then the best way is to reduce its exposure. This reduces the probability of the risk being exploited. The other options are not as effective as reducing the exposure itself.
- What is the best way to address the excessive exposure of sensitive databases?
A. Implement an incident response procedure.
B. Reduce the attack surface.
C. Compartmentalize the sensitive database.
D. Implement a deterrent control.
Answer: B. Reduce the attack surface.
Explanation: The attack surface is where you have various entry points where an attack can happen. The attack surface determines the level of exposure. By decreasing the attack surface, the level of exposure decreases. The attack surface can be reduced by limiting entry points, ports, and protocols and disabling unused services. The other options are not as effective at reducing the attack surface.
- What is the best way to measure the effectiveness of risk management?
A. The number of incidents not detected by the security team
B. The number of security audits
C. The number of vulnerabilities not mitigated by the security team
D. The number of security incidents causing significant financial loss or business disruptions
Answer: D. The number of security incidents causing significant financial loss or business disruptions.
Explanation: The main objective of risk management is to reduce the number of security incidents that can cause a significant financial loss or business disruption. If such incidents are high, then the effectiveness of risk management is questionable. The other options are not as significant as security incidents.
- What is the most likely reason for management choosing to mitigate risk, even though it is within the risk tolerance level?
A. A mandate from the board of directors to address all the risks.
B. Management does not want to accept the risk.
C. Addressing the risk is very cost-effective.
D. Management may have concerns that the impact is underestimated.
Answer: D. Management may have concerns that the impact is underestimated.
Explanation: The most likely reason is that management may have doubts about the estimation of the level of risk. In such cases, management may choose to mitigate the risk, even though it is within the risk tolerance level. It is less likely that the board will require all the risks to be mitigated. This is not practical or feasible. Also, management generally accepts the risk if the risk is within the risk appetite. It makes no sense to address a risk that is within the risk appetite, even though treatment is cost-effective.
- What is the most likely reason for the security manager to not be concerned about an identified major threat?
A. The vulnerability is compartmentalized.
B. The availability of the incident response procedure.
C. The availability of the compensating control.
D. The threat hasn't been exploited so far.
Answer: A. The vulnerability is compartmentalized.
Explanation: Compartmentalization means separating sensitive information assets in such a way that there is reduced or no exposure. If compartmentalization of the vulnerability results in no exposure, then there is no risk. The availability of an incident response procedure and compensating controls are not as effective as compartmentalization is a preventive control. Even if no exploits occurred in the past, threats can materialize at any time, so the appropriate safeguards should be in place.
- Prioritizing risk treatment is primarily based on what?
A. Identified threats and vulnerabilities
B. Likelihood of compromise and the subsequent impact
C. Cost of risk treatment
D. Level of exposure of the asset
Answer: B. Likelihood of compromise and the subsequent impact.
Explanation: Risk is a product of probability and impact. Probability (that is, likelihood) and impact can help determine the actual level of risk. Both terms are equally important for determining the level of risk. Each risk is determined based on its probability (that is, likelihood) and impact and then high-level risks are prioritized and addressed first. The other options are not as important as likelihood and impact.
- What area is a major concern when arranging for disaster recovery in a reciprocal agreement?
A. Variation in the processes in both the organizations
B. Variation in the BCP testing procedure in both organizations
C. Variation in the infrastructure and capacity in both organizations
D. Variation in the security policy and procedure in both organizations
Answer: C. Variation in the infrastructure and capacity in both organizations
Explanation: In a reciprocal agreement, two organizations that have similar capabilities and processing capacities agree to provide support to one another in case of an emergency. If both organizations have different infrastructure and capacities, then they may not be able to support the other organization in the case of a disaster. Recovery becomes difficult in such cases. This is the area of major concern for a reciprocal agreement. The other options will not have a major impact on the recovery aspect.
Risk assessment and analysis methodologies
Different methodologies are available for assessing the risk. An organization should use a methodology that best fits its requirements. The method should have the ability to achieve the goals and objectives of the organization to identify the relevant risk. One such risk assessment methodology is COBIT 5.
Risk assessment is an important process for identifying significant risks and cost-effective controls to address the identified risks.
Phases of risk assessment
Generally, a risk assessment process follows three phases:
- Risk identification: In this phase, significant business risks are identified. Risk identification is generally conducted by risk scenarios. A risk scenario is a visualization of a possible event that can have some adverse impact on the business objective. Organizations use risk scenarios to imagine what could go wrong and create hurdles for achieving the business objectives.
- Risk analysis: Risk analysis is where you rank a risk based on its impact on business processes. The impact can be either quantifiable in dollar terms or can be qualitative, such as high risk, medium risk, or low risk. Both the probability of the event and the impact on the business are considered to determine the level of risk.
A risk with a high level is ranked higher and given priority to address the same. More resources are allocated to high-risk areas.
Risk analysis results help prioritize risk responses and allocate resources.
- Risk evaluation: Risk evaluation is the process of comparing the result of risk analysis against the acceptable level of risk. If the level of risk is more than the acceptable risk, then risk treatment is required to bring down the level of risk.
Let's understand each of these by looking at a practical example of each:
- Risk identification: The risk of a machine malfunctioning due to heavy rain.
- Risk analysis: In this phase, the level of risk is determined. Let's say that a machine costs $100,000 and that the probability of heavy rain is 50%. In that case, the risk level is $50,000 (that is, $100,000 * 50%).
- Risk evaluation: In this phase, we will compare the risk level with the level acceptable to management. Let's say, that the acceptable level is only $20,000, so the current risk of $50,000 exceeds the acceptable level of risk. In such cases, risk treatment is required to bring the risk level down. The organization may choose to take out insurance worth $30,000 so that the net risk remains as $20,000.
Risk assessment
As we discussed in the previous section, risk assessment includes the following three components:
- Risk identification
- Risk analysis (to determine the level of risk; that is, whether the risk is high, medium, or low)
- Risk evaluation (to determine whether the risk is acceptable or whether risk treatment is required)
Asset identification
The first and most important step in a risk assessment process is to identify and list all the information assets and determine their value based on criticality or sensitivity. In the absence of a detailed asset inventory, you may miss out on protecting some significant assets. Assets can be in the form of people, processes, system and network components, databases, or any other factor that can have an impact on business processes. Assets aren't only tangible assets but intangible assets such as the reputation of the organization.
Asset valuation
Once all the assets have been identified, the next step is to determine their valuation. This is very important to avoid underprotecting or overprotecting the asset. The efforts required to protect an asset should be justified by its criticality. It does not make sense to spend $100 to protect a $10 asset.
The security manager should be careful while valuing the assets. In some situations, valuation should not be based only on the actual cost or replacement cost but based on the impact it will have on the business if such an asset is not available.
Let's understand this with an example. A server that costs $1,000 is hosting data that supports the project, which is worth $20,000. If this server is not available, then the full project will be adversely impacted. In this case, the value of the server is considered to be $20,000, even though the cost of the server is $1,000.
This is also known as opportunity cost. Opportunity cost reflects the cost of the organization/business loss that results from the unavailability of an asset.
Aggregated and cascading risk
The security manager should consider the impact of the aggregated risk and the cascading risk while designing the overall control environment.
Aggregated risk
Aggregated risk means having a significant impact caused by a large number of minor vulnerabilities. Such minor vulnerabilities individually do not have a major impact but when all these vulnerabilities are exploited at the same time, they can cause a huge impact.
The goal of risk aggregation is to identify the significant overall risk from a single threat vector. Let's understand this with an example. To protect a critical database, the organization has implemented multiple controls. Even if one control fails, the other controls can compensate for the same. However, when a threat exploits all the controls together, it can have a significant adverse impact.
Cascading risk
Cascading risk is where one failure leads to a chain reaction of failures. This is more relevant when IT and operations have close dependencies. The security manager should consider the impact of one activity failing on other dependent systems.
Identifying risk
Risk management begins with risk identification. Risk identification is the process of identifying and listing the risks in the risk register.
The primary objective of the risk identification process is to recognize the threats, vulnerabilities, assets, and controls of the organization. Risk practitioners can use the following sources to identify the risk:
- Review past audit reports.
- Review incident reports.
- Review public media articles and press releases.
- Through systematic approaches such as vulnerability assessment, penetration testing, reviewing BCP and DRP documents, conducting interviews with senior management and process owners, scenario analysis, and more.
All the identified risks should be captured in the risk register, along with details such as description, category, probability, impact, and risk owner. Maintaining the risk register process starts with the risk identification process.
Risk identification process
The following steps are part of the risk identification process:
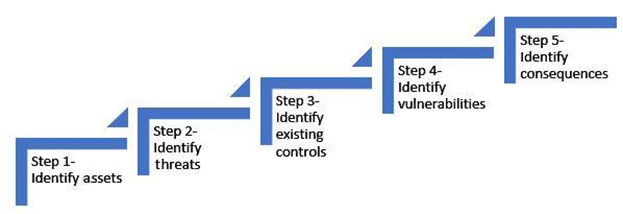
Figure 3.2 – Risk identification process
A security manager should understand the risk identification process. Generally, this process begins with identifying the critical assets. A security manager should be aware of all the assets that need to be protected. Once the threats have been identified, assets should be determined, followed by the existing control and vulnerabilities being identified, and the consequences being determined.
Conducting interviews
The following are some of the good practices for using interview techniques to identify risk:
- Risk practitioners should ensure that the staff who are being interviewed have sufficient authority and knowledge about the process.
- Risk practitioners should study the business process in advance of the interview. This will help in smoothly conducting interviews. It also means that risk practitioners can concentrate on areas of concern.
- Interview questions should be prepared in advance and shared with the interviewee so that they come prepared and bring any supporting documentation, reports, or data that may be necessary.
- Risk practitioners should obtain and review relevant documentation such as SOPs, reports, and other notes that support the statement of the interviewee.
- Risk practitioners should encourage interviewees to be open about various risk scenarios.
Information can be gathered through the Delphi technique, which will be covered in the next section.
Delphi technique
Many organizations resort to using the Delphi technique, in which polling or information gathering is done either anonymously or privately between the interviewer and interviewee.
Threats and vulnerabilities
CISM aspirants should be able to establish the difference between threat and vulnerability. Vulnerability means weakness in the system. A threat is a factor that attempts to exploit the vulnerability. For example, when antivirus software is not updated, it is a vulnerability. The hacker who attempts to exploit the vulnerability (un-updated antivirus) is a threat. The objective of an internal control is to reduce the vulnerability; that is, its weakness. The internal control cannot directly control the threat.
Advanced persistent threat
An advanced persistent threat (APT) is a type of cyberattack that's performed on a computer network where the attacker gains and maintains unauthorized access to the targeted network and remains undetected for a significant period. During the time between infection and remediation, the hacker will often monitor, intercept, and relay information and sensitive data.
The term's definition was traditionally associated with nation-state sponsorship, but over the last few years, we have seen multiple examples of non-nation state groups conducting large-scale targeted attacks for specific goals.
Risk, likelihood, and impact
Let's understand some of the widely accepted definitions of risk, as shown in the following table:

Table 3.4 – Definitions of risk
From a CISM exam perspective, you don't need to worry about any of the definitions in this table. As you can see, almost every definition speaks directly or indirectly about two terms: probability and impact. In its simplest form, the risk is the product of probability and impact. In other words, we can say the following:
- Risk = Probability * Impact
- Risk = P * I
The following diagram illustrates this:
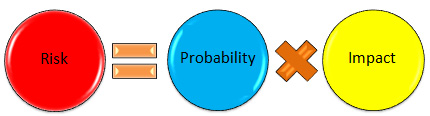
Figure 3.3 – Risk
Note
Probability is also known as likelihood, possibility, and chances.
Both terms are equally important while determining risk. Let's understand this with an example. The probability of a product being damaged is very high – let's say 1. However, that product hardly costs anything and the impact is nil, which is zero, even if the product is damaged. So, the risk of rain will be Risk = P * I. In other words, Risk = 1 * 0 = 0.
Risk register
All the identified risks should be captured in the risk register, along with details such as its description, category, probability, impact, risk owner, and other details. Maintaining the risk register process starts with the risk identification process.
The risk register is the inventory of all the existing risks of the organization. The best way to understand any kind of risk is to review the risk register. This includes details of all the risks, along with the relevant control activities. The most effective use of a risk register is to facilitate a thorough review of all the risks periodically.
Risk analysis
Risk analysis is where you rank a risk based on its impact on business processes. The risk with the highest impact is ranked higher and given priority to address the same. More resources are allocated to high-risk areas.
The risk analysis results help prioritize the risk responses and how resources are allocated.
Risk analysis is the process of ranking various risks so that areas of high risk can be prioritized and be treated. Risk can be measured and ranked by using any of the following methods:
- Quantitative risk assessment
- Qualitative risk assessment
- Semi-quantitative risk assessment
One factor that influences what technique is selected is the availability of accurate data for the risk assessment. When a data source is accurate and reliable, an organization will prefer quantitative risk assessment as it will give risk value in numeric terms, such as monetary values. Monetary value is easy to evaluate to determine the risk response.
In the next section, we will look at each method in detail.
Quantitative risk assessment
In quantitative risk assessment, the risk is measured based on numerical values. This helps with a cost-benefit analysis as the risk, in monetary terms, can easily be compared to the cost of various risk responses. In quantitative risk assessment, various statistical methods are used to derive the risk.
Risk is quantified as per the following formula: Risk = Probability * Impact.
CISM aspirants should always remember that risk is quantified by a combination of probability and impact. Let's understand this with the help of an example.
The probability of equipment being damaged that costs $1,000 is 0. Here, the probability is zero and the impact is $1,000. The risk is probability * impact; that is, P * I. In this case, the risk is 1000*0; that is, 0. If some other asset's probability is 0.5 and the asset costs $100, then the risk will be $50 (0.5 * 100). The risk of the equipment costing $100 is more than the risk of the equipment costing $1,000. This is because probability plays an important role in quantifying risk.
Challenges in implementing quantitative risk assessment
A major challenge when conducting a quantitative risk assessment is the availability of reliable data. To quantify a risk, accurate details of the probability and impact are required.
Determining the probability or frequency of the occurrence of a threat is a challenging aspect. Mostly, the probability can be found based on historical data. However, it is very difficult to ascertain the probability of natural events such as hurricanes, earthquakes, and tsunamis.
Quantitative risk assessment is not feasible for events where the probability or impact cannot be quantified or expressed in numerical terms.
Thus, a quantitative risk assessment does the following:
- Makes use of statistical methods to derive risk
- Makes use of likelihood and impact
- Helps derive a financial impact
Qualitative risk assessment
In a qualitative risk assessment, risks are measured based on qualitative parameters such as high, medium, and low or on a scale of 1 to 5.
Qualitative assessment is considered more subjective compared to quantitative assessment.
Few risks cannot be calculated in numeric terms. Qualitative assessment is useful in such scenarios.
Qualitative risk assessment is more relevant for examining new and emerging threats and advanced persistent threats (APTs). The qualitative risk analysis method involves conducting interviews with various stakeholders. There are some techniques such as the Delphi method wherein information can be gathered by way of anonymous questionnaires.
Semi-quantitative risk assessment
Here are some facts about this type of risk assessment:
- A semi-quantitative risk assessment is the combination of qualitative and quantitative risk assessment. It is a hybrid approach that considers the input of the qualitative approach combined with a numerical scale to determine the impact of a quantitative risk assessment.
- In a semi-quantitative analysis, the descriptive rankings are associated with a numeric scale.
- For example, the qualitative measure of "high" may be given a quantitative weight of 5, "medium" may be given 3, and "low" may be given 1.
- Such methods are frequently used when it is not possible to use a quantitative method or reduce subjectivity in qualitative methods.
- Risk practitioners should ensure that a standardized process and scale are used throughout the organization for semi-quantitative risk assessment. Also, risk owners should not mistake the origins of these values as coming from purely objective sources.
The best method for risk analysis
A risk practitioner should always prefer a quantitative approach. The quantitative approach helps with a cost-benefit analysis as the risk, in monetary terms, can easily be compared to the cost of various risk responses. However, a major challenge in conducting a quantitative risk analysis is the availability of accurate data. In the absence of proper data or when data accuracy is questionable, a qualitative analysis is preferable.
Annual loss expectancy
Annual loss expectancy is a calculation that helps you determine the expected monetary loss for an asset due to a particular risk over a single year.
The annualized loss expectancy is the product of the annual rate of occurrence and the single loss expectancy. It is mathematically expressed as SLE * ARO. For example, a particular risk event can have an impact of $1,000 every time it occurs. $1,000 is the single loss expectancy (SLE). Now it is expected that this particular risk event will materialize 5 times a year. 5 is the annual rate of occurrence (ARO). So, in this case, the annual loss expectancy is $5,000.
Value at Risk (VaR)
Value at Risk (VaR) is a statistical computation based on historical data to arrive at probability. VaR is mostly used in the financial sector to determine the risk of an investment. However, although primarily being used by a financial organization, it can be applied to the information security domain also. The following are some of the characteristics of VaR:
- VaR is a quantitative approach to evaluating risk.
- VaR is used to determine the maximum probable loss over a certain period.
- VaR calculations are typically complex and time-consuming.
OCTAVE
Operationally critical threat asset and vulnerability evaluation (OCTAVE) is a risk assessment approach with the following characteristics:
- In this approach, critical assets are identified first.
- The next step is to focus risk analysis activities on identified critical assets.
- It considers the relationship between critical assets and threats and the vulnerabilities that can be applied to critical assets.
- It evaluates the risk in terms of operational aspects; that is, the impact on business operations due to the risk of these critical assets.
- It creates a protection strategy for risk mitigation to safeguard the critical assets of the organization.
Other risk analysis methods
A consistent risk analysis technique should be used whenever the goal is to produce results that can be compared over time. Each approach has certain advantages and possible weaknesses, and the risk practitioner should choose a technique that's appropriate for the circumstances of the assessment.
The following are some of the most common approaches:
- Bayesian analysis
- Bow tie analysis
- A bow tie analysis is a simple process for identifying areas of concern.
- It makes the analysis more effective by linking possible causes, controls, and consequences.
- The cause of the event is depicted in the middle of the diagram (the "knot" of the bow tie). In this diagram, threats are placed on the left, whereas consequences are placed on the right.
The following diagram shows the flow of a bow tie analysis:
Figure 3.4 – Bow tie analysis
- Delphi method:
- In the Delphi method, opinions from experts are obtained using two or more rounds of questionnaires.
- After each round of questioning, the results are summarized and communicated to the experts by a facilitator.
- This collaborative technique is often used to build a consensus among experts.
- In the Delphi technique, polling or information gathering is done either anonymously or privately between the interviewer and interviewee.
- Event tree analysis:
- Fault tree analysis:
- Markov analysis:
- A Markov analysis is a method that's used to forecast the value of a variable whose predicted value is influenced only by its current state.
- The Markov model assumes that future events are independent of past events.
- A Markov analysis is often used to predict behaviors and decisions within large groups of people.
- A Markov analysis is used to analyze systems that can exist in multiple states.
- Monte Carlo analysis:
- Monte Carlo analysis is a risk management technique that is used for conducting a quantitative analysis of risks.
- This technique is used to analyze the impact of risks on your project.
- Monte Carlo methods, or Monte Carlo experiments, are a broad class of computational algorithms that rely on repeated random sampling to obtain numerical results.
Evaluating risk
In the risk evaluation phase, the level of each risk is compared against the acceptable risk criteria. If the risk is within an acceptable level, then the risk is accepted as-is. If the risk exceeds the acceptable level, then treatment will be some form of mitigation.
Risk ranking
A risk with high impact is ranked higher and given priority to address the same. More resources are allocated to high-risk areas. Ranking each risk based on impact and likelihood is critical in determining the risk mitigation strategy. Ranking the risk helps the organization determine its priority.
Risk ownership and accountability
The following are some of the important aspects concerning risk ownership and accountability:
- For successful risk management, each risk should have assigned ownership and accountability.
- Risk should be owned by a senior official who has the necessary authority and experience to select the appropriate risk response based on analyses and guidance provided by the risk practitioner.
- Risk owners should also own associated controls and ensure the effectiveness and adequacy of the controls.
- Risk should be assigned to an individual employee rather than as a group or a department. Allocating accountability to the department as a whole will circumvent ownership.
- The accountability for risk management lies with senior management and the board.
- Risk ownership is best established by mapping risk to specific business process owners.
- The details of the risk owner should be documented in the risk register.
- The results of the risk monitoring process should be discussed and communicated with the risk owner. This is because they own the risk and are accountable for maintaining the risk within acceptable levels.
Risk treatment options
The following are the four options for responding to risk:
- Risk avoidance:
- Risk mitigation:
- Risk sharing/transferring:
- Risk acceptance:
- In this approach, the risk is accepted as per the risk appetite of the organization.
- Risk is accepted where the cost of controlling the risk is more than the cost of the risk event.
- For example, for a few non-critical systems, the cost of anti-malware installation is more than the anticipated cost of damage due to malware attacks. In such cases, the organization generally accepts the risk as-is.
- In risk acceptance, no steps are taken to reduce the risk.
- However, organizations need to be careful while accepting the risk. If the risk is accepted while the correct level of risk isn't known, it may result in a higher level of liabilities.
Understanding inherent risk and residual risk
Let's understand this with the help of an example. Let's say you have purchased a machine for $100,000 that is placed in an earthquake-sensitive zone. Any damage to the machine will cost you $100,000. To safeguard against this loss, you take out insurance worth $80,000 for the machine. Now, if anything happens to your machine, the insurance company will reimburse you up to $80,000. Your final loss will only be $20,000.
In this case, your risk before taking out insurance is $100,000. This risk is known as the inherent risk; that is, the gross risk or risk before implementing any control.
The risk after taking out insurance is only $20,000. This risk is known as the residual risk; that is, the net risk or risk after implementing any control.
Inherent risk
This is the risk that an activity would pose if no controls or other mitigating factors were in place (the gross risk or risk before controls). It is the susceptibility of a business or process to make an error that is material in nature, assuming there were no internal controls.
The inherent risk depends on the number of users and business areas. The higher the number of users and business processes, the higher the level of inherent risk.
Residual risk
This is the risk that remains after controls are considered (the net risk or risk after controls). Residual Risk = Inherent Risk - Controls.
For a successful risk management program, residual risk should be within the risk appetite. When the residual risk is within the risk appetite, it is an acceptable risk level.
The primary objective of a risk management program is to ensure that residual risk is within levels acceptable to management. If the residual risk is within the risk appetite of the organization, it determines its compliance with the risk appetite. Achieving acceptable risk indicates that the residual risk is minimized and within control.
Security baseline
The security baseline is the minimum security requirement across the organization. The baseline may be different based on asset classification. For highly classified assets, the baseline will be more stringent. For example, for low classified assets, the baseline can be single-factor authentication, though the baseline will increase to two-factor authentication for highly classified assets.
Baseline security should form part of the control objective. The baseline should be reviewed at regular intervals to ensure that it is aligned with the organization's overall objectives.
Key aspects from the CISM exam's perspective
The following are some of the key aspects from an exam perspective:

Table 3.5 – Key aspects from the CISM exam perspective
Questions
- A risk analysis for a business process can be best conducted by which of the following?
A. Audit team
B. Legal team
C. Business process owner
D. External consultant
Answer: C. Business process owner.
Explanation: The business process owner is in the best position to conduct the risk analysis for their respective processes. They have detailed knowledge of the risks and controls that can be applied to their processes.
- When should a risk assessment for a project be performed?
A. At the initial stage of the project
B. Continuously
C. Before implementing the project
D. When there is a change in the process
Answer: B. Continuously.
Explanation: The effectiveness of risk assessment increases if the assessment is done continuously. This will help the organization address the emerging risks and other significant changes in the business environment. It must be noted that risk assessment is not a one-time activity.
- What is the main objective of a risk management program?
A. To eliminate all the risks
B. To support management's due diligence process
C. To comply with regulatory requirements
D. To improve the investment portfolio
Answer: B. To support management's due diligence process.
Explanation: It is the responsibility of management to conduct due diligence for organization processes. The risk management program supports this objective. The main objective when conducting risk management is that it is an important part of management's due diligence.
- The frequency for a risk assessment should be done when?
A. Annually for each process
B. As per the risk management budget
C. Every 6 months for critical business processes
D. Annually or whenever there is a significant change
Answer: D. Annually or whenever there is a significant change.
Explanation: The risk environment is changing constantly. The most effective risk assessment frequency is annual or whenever there is a significant change. This will help to assess risk at a reasonable timeframe and provides flexibility for assessing the risk when there is a significant change.
- A risk analysis includes assessing what?
A. Probability and visibility
B. Likelihood and impact
C. Impact and appetite
D. Appetite and tolerance
Answer: B. Likelihood and impact.
Explanation: Risk is a combination of two components: probability (likelihood) and impact. Both components are essential for analyzing risk. Hence, likelihood and impact are the primary elements that are determined in a risk analysis.
- What is the main objective of a network vulnerability assessment?
A. To identify deviation from a secure coding policy
B. To identify malware and spyware
C. To identify weaknesses in the security design
D. To identify misconfigurations and missing updates
Answer: D. To identify misconfigurations and missing updates.
Explanation: The objective of a network vulnerability assessment is to identify common misconfigurations.
- What is the prime objective of conducting a risk assessment continuously?
A. For optimum utilization of the security budget
B. To comply with the security policy
C. To address a constantly changing risk environment
D. For optimum utilization of security resources
Answer: C. To address a constantly changing risk environment.
Explanation: Changes in the risk environment introduce new threats and vulnerabilities to the organization. To address this risk, assessments should be conducted continuously. Other options are not prime objectives for conducting a risk assessment.
- Which of the following is used to identify deficiencies in the system?
A. Performance metrics
B. A business impact analysis
C. A security gap analysis
D. Incident management procedure
Answer: B. A business impact analysis.
Explanation: The objective of a security gap analysis is to identify any deficiencies in the control environment against the desired state of control.
- What are the main criteria for approving a policy exception?
A. Project deadlines.
B. The risk is justified by the benefits.
C. High cost of policy compliance.
D. Inconvenience to the users.
Answer: B. The risk is justified by the benefits.
Explanation: Generally, policy exceptions are approved where the impact of non-compliance is less than the benefits of taking the risk.
- The security manager has observed that the organization is using FTP access, which can be exploited. Which of the following is used to determine the necessity for remedial action?
A. To conduct a penetration test
B. To conduct a security baseline review
C. To conduct a risk assessment
D. To conduct a business impact analysis
Answer: C. To conduct a risk assessment.
Explanation: A risk assessment helps determine the impact of the vulnerability. Based on that impact, the necessary remedial measures can be decided. The other options will not help determine the impact of the vulnerability.
- What is the main objective when using risk assessment techniques?
A. To justify the selection of risk mitigation strategies
B. To maximize the return on investment
C. To comply with regulations
D. To provide better documentation
Answer: A. To justify the selection of risk mitigation strategies.
Explanation: Risk assessment will help you determine the impact of the vulnerability, on which basis the necessary remedial measures can be decided. It helps justify the selection of risk mitigation strategies.
- What is the prime objective of a risk management program?
A. To remove all inherent risk
B. To maintain residual risk at an acceptable level
C. To comply with regulatory requirements
D. To remove all control risk
Answer: B. To maintain residual risk at an acceptable level.
Explanation: The objective of a risk management program is to ensure that the risks that apply to the organization are brought down to an acceptable level by implementing various mitigation strategies. It is not possible to eliminate all inherent risks or control risks.
- What is the most important element of risk assessment?
A. Protecting all the assets
B. Benchmarking the process with other organizations
C. Evaluating both monetary value and the likelihood of loss
D. Evaluating past threats
Answer: C. Evaluating both monetary value and the likelihood of loss.
Explanation: Risk is a combination of two components: probability (likelihood) and impact. Both components are essential for analyzing risk. Hence, likelihood and impact are the primary elements that are determined in a risk analysis.
- The security manager has noted that a new regulatory requirement applies to the organization. What should be the next course of action?
A. To take approval from the information security committee to implement the new requirement
B. To perform a gap analysis
C. To implement control
D. To evaluate budget availability
Answer: B. To perform a gap analysis.
Explanation: The first step is to perform a gap analysis to determine whether the organization already complies or whether some action is required for the compliance. Based on the gap analysis, further action can be decided.
- What is the main reason for repeating risk assessment at regular intervals?
A. To address constantly changing business threats
B. To rectify errors of earlier assessments
C. To apply different methodologies
D. To improve security awareness
Answer: A. To address constantly changing business threats.
Explanation: The business environment changes constantly and hence new threats emerge. Risk assessments should be repeated at regular intervals because business threats are constantly changing.
- The security manager has noted that a new privacy requirement has been enacted. What should be the next course of action to determine the potential impact of the privacy law on the organization?
A. To develop a roadmap for the implementation to achieve compliance with the privacy law
B. To determine systems and processes that contain privacy components
C. To stop business processes until compliance is achieved
D. To determine the action that will be taken by other organizations
Answer: B. To determine systems and processes that contain privacy components.
Explanation: The best course of action is to determine systems and processes that may have an impact due to new privacy laws. The other options may be implemented as subsequent steps.
- Quantitative risk assessment is best used to assess which of the following?
A. Reputational risk arising due to data leakage
B. Risk of an electrical power outage for a business process
C. Risk of a defaced website
D. Risk of high staff turnover
Answer: B. Risk of an electrical power outage for a business process.
Explanation: Impact due to loss of power can be more easily measurable and quantifiable compared to the other options.
- The most important element of a quantitative risk analysis is that the result does what?
A. Includes customer perceptions
B. Contains percentage estimates
C. Lacks specific details
D. Is subjective
Answer: B. Contains percentage estimates.
Explanation: Results derived from a quantitative risk analysis are measurable. Percentage estimates are a characteristic of a quantitative risk analysis. The other options are general characteristics of a qualitative risk analysis.
- What is the most important aspect of an effective risk management program?
A. High-security budget
B. Defined security baseline
C. Being able to detect new risks
D. Documented risk reporting process
Answer: C. Being able to detect new risks.
Explanation: Though all these options are very important for effective risk management, if the program can't identify new risks, other procedures will only be useful for a limited period.
- The valuation of assets in a business impact analysis is based on which of the following?
A. Cost of acquisition
B. Cost of replacement
C. Opportunity cost
D. Cost to recreate
Answer: C. Opportunity cost.
Explanation: For business impact analysis purposes, valuation should be based on the opportunity lost due to the unavailability of the assets. This is known as opportunity cost.
- What is the best way to estimate the potential loss?
A. Determine the productivity ratio
B. Determine the impact of data leakage
C. Determine the value of the information or asset
D. Determine the probability of it occurring
Answer: C. Determine the value of the information or asset.
Explanation: The best way to estimate the potential loss is to determine the value of the information assets. Value can be in the form of productivity loss, the impact of data leakage, or opportunity costs due to the unavailability of the assets.
- What is the risk register best used for?
A. Identifying emerging risks
B. Identifying risk owners
C. Reviewing all IT-related risks periodically
D. Recording annualized loss due to incidents
Answer: C. Reviewing all IT-related risks periodically.
Explanation: The risk register contains details about all the identified risks. The main objective of the risk register is to facilitate a thorough review of all the risks periodically. The other options are secondary factors.
- Which of the following components of a risk assessment will require the highest amount of speculation?
A. Consequences
B. Exposure
C. Vulnerability
D. Likelihood
Answer: D. Likelihood.
Explanation: Likelihood is the most difficult to estimate. It will require the highest amount of speculation. The other options can be determined within a range.
- The security manager has received a request from a business unit to implement a new technology that is against the information security standards. What should be the next course of action for the information security manager?
A. Reject the request.
B. Modify the standard to allow the new technology.
C. Conduct a risk assessment to quantify the risk.
D. Engage experts to identify the better technology.
Answer: C. Conduct a risk assessment to quantify the risk.
Explanation: The first course of action for a risk manager is to conduct a risk assessment and determine the level of risk. Policy exceptions are generally allowed where benefits from the project outweigh the perceived risks. The other options can be meaningful, but only if the security manager is aware of the level of risk.
- The security manager has received a request from the IT function to not update the business impact analysis for a new application as there is no change in the business process. What should be the next course of action for the security manager?
A. Verify the decision of the business unit after a risk analysis.
B. Reject the request.
C. Instruct IT to modify the business impact analysis after a post-implementation review of the new application.
D. Recommend an audit review.
Answer: A. Verify the decision of the business unit after a risk analysis.
Explanation: The best course of action in this scenario is to conduct a risk analysis and determine the impact that the new application will have on the business impact analysis. If there is no impact, then there is no need to update the business impact analysis.
- What is the best way to address the conflict of security requirements with a business objective?
A. To change the security requirements
B. To change the business objective
C. To conduct a risk analysis
D. To accept the risk
Answer: C. To conduct a risk analysis.
Explanation: The first course of action for a risk manager is to conduct a risk assessment and determine the level of risk. Policy exceptions are generally allowed where benefits from the project outweigh the perceived risks. The other options can be meaningful, but only if the security manager is aware of the level of risk. A business objective could be changed to accommodate a security requirement.
- An aggregate risk of linked vulnerabilities can be assessed by which of the following?
A. System audits
B. Penetration tests
C. Auditing the codes
D. A vulnerability analysis
Answer: B. Penetration tests.
Explanation: Aggregated risk means a significant impact caused by a large number of minor vulnerabilities. Such minor vulnerabilities individually do not have a major impact, but when all these vulnerabilities are exploited at the same time, they can have a huge impact. The goal of risk aggregation is to identify the significant overall risk from a single threat vector. Penetration testing is the best way to assess the aggregate risk by exploiting them sequentially. This gives you a good measurement and prioritization of the risk. Penetration testing can give the risk a new perspective and can prioritize it based on the result of a sequence of security problems.
- What is the most important factor when reviewing the migration of IT operations to an offshore location?
A. Reviewing new regulations
B. Modifying operating processes
C. Reviewing budget adherence
D. Performing a risk assessment
Answer: D. Performing a risk assessment.
Explanation: Risk assessment will help the organization determine new risks introduced by migrating IT operations to an offshore location. The new risk may inform you of non-adherence to regulations, overspending, or some operational aspects.
- The security manager has noted a security breach at another organization that has employed similar technology. What should be the next course of action for the security manager?
A. Evaluate the likelihood of incidents from the reported cause.
B. Stop using the already breached technology.
C. Assure senior management about the security posture.
D. Remind staff that the organization is not affected by security breaches.
Answer: A. Evaluate the likelihood of incidents from the reported cause.
Explanation: The first course of action for a security manager is to evaluate the likelihood of the incident from the reported cause. Once the likelihood has been determined, other suitable actions can be taken.
- What is the main objective of including threat and vulnerability assessment in a change management process?
A. To reduce the requirement for periodic full risk assessments
B. To ensure that the risk assessment is cost-effective
C. To ensure that changes are approved by the information security team
D. To ensure legal compliance
Answer: A. To reduce the requirement for periodic full risk assessments.
Explanation: Threat and vulnerability assessment during change management helps identify vulnerabilities in the initial stages. The same can be addressed without us having to wait until a full risk assessment has been performed. This keeps the risk assessment current without the need to complete a full reassessment.
- What is the objective of calculating Value at Risk?
A. To evaluate the risk by applying a qualitative approach
B. To determine the maximum possible loss over a certain period
C. To evaluate risk but only for the financial organization
D. To expedite the assessment process
Answer: B. To determine the maximum possible loss over a certain period.
Explanation: Value at Risk is a statistical computation based on historical data to arrive at a probability. Value at Risk is mostly used in the financial sector to determine the risk of an investment. However, since it is primarily used by the financial organization, it can be applied to the information security domain as well.
- Which process can help address the risk at various life cycle phases?
A. The change management process
B. The patch management process
C. The configuration management process
D. The problem management process
Answer: A. The change management process.
Explanation: The change management process can be best used to address risk in the various life cycles of the system. All these changes should go through the risk management process. This helps identify and address the new risks at the earliest possible time. Change management addresses a broader range of risks. The other options are not directly relevant to the life cycle stages.
- What is the main objective of a vulnerability assessment?
A. To eliminate all the risks to the business
B. To adhere to the security policy
C. To assure management
D. To monitor the efficiency of the security team
Answer: C. To assure management.
Explanation: Vulnerability assessment helps identify all the existing vulnerabilities and plans to address the same. This gives comfort to management that the risks to business objectives are actively being monitored and controlled. It is not possible to eliminate all the risks. Vulnerability assessment is not primarily conducted to adhere to the security policy or to monitor the efficiency of the security team.
- A project for implementing new regulatory requirements should be primarily driven by which of the following?
A. The audit department
B. The system analyst
C. The business process owners
D. The legal department
Answer: C. The business process owners.
Explanation: The business process owners will be in the best position to drive the project for implementing regulatory requirements. They have a thorough understanding of their processes and the impact of regulatory requirements on their processes. The other options do support the business process owner when implementing the project but primarily, the project should be driven by the business process owner.
- A security manager is conducting a qualitative risk analysis. What is the best way to get the most reliable result?
A. Estimate the productivity losses
B. Determine the possible scenarios, along with their threats and impacts
C. Determine the value of assets
D. Conduct a vulnerability analysis
Answer: B. Determine the possible scenarios, along with their threats and impacts.
Explanation: For a qualitative risk analysis, the best way is to list all possible threats and impact scenarios. This will facilitate an informed risk management decision. The other options are generally used for quantifying risk.
- Which is the most important aspect of the effective risk management of IT activities?
A. Risk management activities should be treated as different processes.
B. Risk management activities should be controlled by the IT department.
C. Risk management activities should be integrated within business processes.
D. Risk management activities are communicated to all staff.
Answer: C. Risk management activities should be integrated within business processes.
Explanation: Integrating risk management activities within business processes is a more effective way to enhance risk management. Risk management should not be treated as a separate activity.
- What is the most important element of a business impact analysis?
A. Downtime tolerance
B. Security budget
C. The BCP testing process
D. The crisis management procedure
Answer: A. Downtime tolerance.
Explanation: A business impact analysis is a process that determines the critical processes of the organization and decides on the recovery strategy during a disaster. The key criterion for determining the severity of service disruption is the period for which the system will remain down. The higher the system downtime, the higher the severity of the disruption. The other options are not directly related to the business impact analysis.
- The security manager has determined the objective of the review. Their next step is to determine what?
A. Limitations
B. Approach
C. Scope
D. Report structure
Answer: C. Scope.
Explanation: Once the objective has been finalized, the next step is to determine the scope. The limitations and the approach must be defined after the scope. The report's structure is the last step.
- The security manager has noted that there is a considerable delay between identifying a vulnerability and applying a patch. What should be the first course of action to address the risk during this period?
A. Apply compensating controls for vulnerable systems.
B. Discontinue the service of vulnerable systems.
C. Communicate the weakness to end users.
D. Update the signature of the antivirus system.
Answer: A. Apply compensating controls for vulnerable systems.
Explanation: The best course of action is to apply compensating control until the time patch is installed. This will help address the risk. Updating signatures for antivirus does not address the zero-day vulnerability.
- The security manager has noted that not all employees comply with the access control policy for the data center. To address this issue, the security manager should do what?
A. Determine the risk of non-compliance
B. Arrange security awareness training
C. Report the same to senior management
D. Impose a heavy penalty for non-compliance
Answer: A. Determine the risk of non-compliance.
Explanation: The most important aspect for a security manager is knowing the level of risk for this non-compliance. The risk may be very high or may be negligible. Based on the level of risk, a further course of action needs to be determined.
- What is the main objective when conducting a penetration test?
A. Determining weaknesses in the network and server security
B. Determining improvements in the incident management procedure
C. Determining the capabilities of threat vectors
D. Determining the strength of the security team
Answer: A. Determining weaknesses in the network and server security.
Explanation: The objective of a penetration test is to identify weaknesses in the network and server security. Based on the results of the penetration test, these weaknesses that have been identified are addressed to improve the security posture of the organization.
- Risk assessment produces output in the form of what?
A. A list of implemented controls
B. A list of applicable threats
C. A list of possible impacts
D. A list of risks that may impact the organization
Answer: D. A list of risks that may impact the organization.
Explanation: Risk assessment helps derive a list of all the applicable risks that may impact the organization.
- Which of the following is used to determine the level of effort required to improve risk management processes?
A. A workflow analysis
B. Program evaluation and review technique
C. A gap analysis
D. Return on investment
Answer: C. A gap analysis.
Explanation: The objective of a gap analysis is to identify the gap between the current level of control versus the desired level of control. A gap analysis is used to improve the maturity level of risk management processes. A workflow analysis is used to understand the current level of the risk management process, but it does not provide support for improvement opportunities. Program evaluation and review technique (PERT) is used to determine project timelines.
- The security manager is implementing a bring your own device (BYOD) program. What should their first step be?
A. To allow or reject access to devices, as per their approval status
B. To perform a comprehensive assessment process before approving the devices
C. To report compliance with the BYOD policy to senior management
D. To install a mobile device management system in each of the approved devices
Answer: B. To perform a comprehensive assessment process before approving the devices.
Explanation: The first step is to develop a comprehensive assessment process, based on which approval should be granted to devices. The other options are subsequent steps.
- The security manager noted that different criteria are used by different departments for measuring risk. To improve this situation, the security manager should recommend which of the following?
A. Applying standard risk measurement criteria throughout the organization
B. Introducing a common risk appetite across the organization
C. Mandating the quantification of each risk
D. Getting the results of the risk assessment reviewed by the head of the department
Answer: A. Applying standard risk measurement criteria throughout the organization.
Explanation: The best way to address this situation is to apply a standard risk measurement criterion for all the departments throughout the organization. This will help in arriving at a standard risk level where each risk can be compared to others to prioritize the risk response. The other options will not help address this issue directly.
- What is the most important aspect to be included in a BYOD policy?
A. Requirement to return the device to the organization
B. Requirements to protect the sensitive information on the device
C. Restrictions on installing third-party applications
D. Requirement to seize the application during a forensic investigation
Answer: B. Requirements to protect the sensitive information on the device.
Explanation: The most important aspect is to ensure that users understand various requirements for protecting sensitive data on the device. Generally, personal devices are not returned to the organization. The other options are not as important for protecting data.
- How should regulatory compliance requirements be dealt with?
A. As a zero deviation area
B. As a risk management area of focus
C. As operational issues
D. Just another risk
Answer: D. Just another risk.
Explanation: It should be dealt with just like any other risk. Like every other risk, regulatory risk should be addressed while considering its impact on business processes. Priority should be given based on feasibility, possible impacts, and the cost of compliance.
- What is the most effective way to address regulatory risk?
A. Regulatory risk should be treated like any other risk.
B. Regulatory risk should be treated as a zero deviation area.
C. Regulatory risk should be complied with mandatorily.
D. Regulatory risk should be transferred by taking out insurance.
Answer: A. Regulatory risk should be treated like any other risk.
Explanation: Regulatory risk should be treated just like any other risk. Like every other risk, regulatory risk should be addressed while considering its impact on business processes. Priority should be given based on feasibility, possible impacts, and the cost of compliance.
- The security manager should be most concerned about what while evaluating a vulnerability scanning tool?
A. The ability of a tool to perform multiple functions
B. Regular signature updates of the scanning tool
C. Its user-friendly graphical user interface
D. Ability to delete viruses
Answer: B. Regular signature updates of the scanning tool.
Explanation: The most important aspect of a scanning tool is to update it with new signatures to address the new and emerging risks. A vulnerability scanner doesn't need to delete viruses. Multiple functions and GUIs are good to have features but regular updates are extremely important.
- Risk management should be considered as an ongoing activity because of which reason?
A. Processes are prone to errors.
B. Technology gets updated.
C. The environment changes.
D. The policy gets updated.
Answer: C. The environment changes.
Explanation: Existing controls may not be relevant for addressing new and emerging risks due to changes in the environment. As a result, effective risk management should be applied on an ongoing basis.
- The security manager has noted that a web-based service is gaining popularity in the market. What should the security manager do first?
A. Conduct an annual vulnerability assessment.
B. Obtain third-party liability insurance.
C. Perform a business impact analysis.
D. Arrange a real-time failover capability.
Answer: C. Perform a business impact analysis.
Explanation: The first thing a security manager should do is determine the level of risk of the non-availability of the service. This can be done by performing a business impact analysis. The other options can be considered based on the results of the business impact analysis.
- What is the best way to treat vulnerabilities?
A. All identified vulnerabilities should be treated, even though there is no threat.
B. Identified vulnerabilities should be prioritized based on the number of threats.
C. Identified vulnerabilities should be prioritized based on the effectiveness of control.
D. Identified vulnerabilities should be evaluated for threat, impact, and the cost of mitigation.
Answer: D. The vulnerability identified should be evaluated for threat, impact, and the cost of mitigation.
Explanation: To prioritize and decide on how to treat a vulnerability, it should be evaluated based on the threat, impact, and the cost of mitigation. All three factors should be considered.
- What is the most cost-effective way to test the security of a legacy application?
A. To determine the security weaknesses of similar applications
B. To use debugging software to identify code errors
C. To determine system functionality by using reverse engineering
D. To conduct a vulnerability assessment to detect the application's weaknesses
Answer: D. To conduct a vulnerability assessment to detect the application's weaknesses.
Explanation: The most cost-effective way to test the security of a legacy application is to conduct a vulnerability assessment.
- What is the objective of risk aggregation?
A. To merge all homogenous types of processes to reduce the overall risk
B. To increase the risk appetite of the organization
C. To simplify the risk reporting process
D. To identify the significant overall risk of a single threat
Answer: D. To identify the significant overall risk of a single threat.
Explanation: The goal of risk aggregation is to identify the significant overall risk from a single threat vector. An aggregated risk has a significant impact that's caused by a large number of minor vulnerabilities. Such minor vulnerabilities individually do not have a major impact, but when all these vulnerabilities are exploited at the same time, they can have a huge impact.
- What is the best way to achieve cost-effective risk mitigation activities throughout the organization?
A. Decentralized risk management
B. Continuous risk assessments
C. Assurance process integration
D. Having a standard risk appetite across the organization
Answer: C. Assurance process integration.
Explanation: Integrating the activities of various assurance functions helps ensure that there are no overlapping activities or gaps in risk management activities. It is the most cost-effective method as duplicate efforts are streamlined. decentralization of risk management functions increases the cost of risk management. The other options do not directly impact the cost-effectiveness of risk management functions.
- What is the most essential element for conducting a risk assessment?
A. Consequences
B. Likelihood
C. Vulnerability
D. Budget
Answer: A. Consequences.
Explanation: If there is no impact or consequences of the exploitation, then there is no risk. Risk analysis, risk evaluation, and risk treatment are primarily based on the impact of the risk.
- The security manager has received a request to overwrite the data stored on a magnetic tape due to limited storage availability. The security manager should refer to which policy?
A. Data classification policy
B. Data retention policy
C. Data access policy
D. Data protection policy
Answer: B. Data retention policy.
Explanation: The data retention policy defines the minimum period of data retention. Overwriting any data may impact the data retention policy.
- What is the most essential element when considering the extent of protection requirements?
A. Exposure
B. Threat
C. Vulnerability
D. Probability
Answer: A. Exposure.
Explanation: The level of exposure of the data affects the threat, vulnerability, probability, and impact of the data. It is the most important aspect when considering the extent of the level of protection.
- Legal and regulatory requirements should be prioritized based on what?
A. The level of penalty action
B. Probability and consequences
C. The level of the director's liability
D. The discretion of the compliance manager
Answer: B. Probability and consequences.
Explanation: Risk can be determined based on probability and consequences. They will help derive the level of risk for non-compliance. Hence, both probability and consequences should be used to prioritize requirements.
- As per good practices, when should a full risk reassessment be performed?
A. In case of material control failure
B. In case of a residual risk above the acceptable risk level
C. In case a new patch is installed
D. In case of emergency changes being implemented
Answer: A. In case of material control failure.
Explanation: Failure of material control indicates that control was not designed and monitored properly. It indicates the requirement for a full reassessment of risk. All the other options do not require a full reassessment.
- In which of the following circumstances is high-risk tolerance useful?
A. When the risk appetite is high
B. When the uncertainty of a risk is high
C. When the impact of a risk is high
D. When the inherent risk is high
Answer: B. When the uncertainty of a risk is high.
Explanation: Risk tolerance is the acceptable deviation from risk appetite. For example, the risk appetite of an organization is $100 and their risk tolerance is $125. In this case, the organization is comfortable even if the risk level reaches $125. High-risk tolerance means a wider gap between risk appetite and risk tolerance. This will be more helpful when there is high uncertainty regarding the level of risk.
- What is the main objective of conducting a risk assessment consistently?
A. To lower the cost of risk assessments
B. To adhere to the security budget
C. To comply with the security policy
D. To determine trends in the evolving risk profile
Answer: D. To determine trends in the evolving risk profile.
Explanation: Consistency in the risk assessment process helps determine trends over a certain period. If the risk assessment process is not consistent, then the results of the risk assessment cannot be compared to earlier results.
Summary
In this chapter, we discussed the important aspects of risk management. We learned about different risk identification and risk assessment methods. We also understood various risk treatment options. This will help security managers identify the risks in their organization, access the level of risk, and determine the appropriate treatment options.
In the next chapter, we are going to cover the practical aspects of risk management.
