Chapter 9: Information Security Monitoring Tools and Techniques
In this chapter, we will discuss the methods, tools, and techniques for monitoring information security. We will discuss the technical aspects of implementing firewalls, as well as how intrusion prevention systems (IPSes) and intrusion detection systems (IDSes) function. We will also discuss some important aspects of digital signatures, public key infrastructure (PKI), and asymmetric encryption, which are very important from the CISM exam's perspective.
The following topics will be covered in this chapter:
- Firewall types and their implementation
- IDSes and IPSes
- Digital signature
- Elements of PKI
- Asymmetric encryption
Let's understand each of these topics in detail.
Firewall types and their implementation
A firewall is a device that's used to monitor and control network traffic. It is generally placed in-between an enterprise's internal network and the internet to protect the system and infrastructure of the organization.
Security management should understand the following types of firewalls, as well as how they should be structured to protect information assets. CISM aspirants need to understand the following types and implementations of firewalls:

Figure 9.1 – Types of firewalls
Next, let's look at the different types of firewalls.
Types of firewalls
The following are the basic characteristics of the different types of firewalls.
Packet filtering router
A packet-filtering router is the most simple and initial version of a firewall. It tracks the IP address and port number of both the destination and source and takes action (either to allow or deny the connection) as per the defined rules. A packet-filtering router functions at the network layer of the OSI model.
Stateful inspection firewall
A stateful inspection firewall monitors and tracks the destination of each packet that is being sent from the internal network. Stateful inspection firewalls only allow incoming messages that are in response to the request that went out from the internal network. A stateful inspection firewall operates at the network layer of the OSI.
Circuit-level firewall
A circuit-level firewall operates on the concept of a bastion host and proxy server. It provides the same proxy for all services. It operates at the session layer of the OSI.
Application-level firewall
Here are a few characteristics of application-level firewalls:
- An application-level firewall is regarded as the most secure type of firewall.
- It operates at the application layer of the OSI.
- It controls applications such as FTP and HTTP.
- It also works on the concept of the bastion host/DMZ and proxy server, but it provides a separate proxy for each service.
Now, let's understand what bastion host/DMZ and proxy server are.
Bastion host/DMZ and proxy
CISM aspirants should understand the concept of the bastion host, proxies, and Demilitarized Zone (DMZ).
What is a proxy?
The following diagram shows the concept of a proxy:

Figure 9.2 – Proxy server
The following are the features of a proxy server:
- A proxy can be regarded as a middleman. A proxy stands in between the internal and external networks.
- No direct communication will be allowed between the internal and external networks. All communication will pass through the proxy server.
- The outside world will not have the addresses of the internal networks. It can only recognize proxy servers.
- Proxy technology operating at the session layer is known as a circuit-level proxy, while proxy technology operating at the application layer is referred to as an application-level proxy.
Now, let's understand what demilitarized zones and bastion hosts are.
Demilitarized Zone (DMZ)/bastion host
DMZ is an area that can be accessed by an external network. The objective of setting up a DMZ is to prevent external traffic from having direct access to the critical systems of the organization. All the systems that are placed in DMZ should be hardened and all the required functionalities should be disabled. Such systems are also referred to as bastion hosts.
The firewall ensures that traffic from the outside is routed into the DMZ. Nothing valuable is kept in a DMZ because it is subject to attack and can be compromised.
Now, let's understand proxies, bastion hosts, and DMZ by looking at a simple example.
Your office has a receptionist. The receptionist has a phone number that is available in the phone dictionary. You and your colleagues have been given specific extension numbers. Only your receptionist and the internal staff know about this extension:
- Proxy: You cannot directly call outside your extension. First, you need to call your receptionist and request an outside connection. Your receptionist will do all the due diligence and then get you connected. The outsider will only know the receptionist's phone number. They will not be able to track your extension. This is known as a proxy.
- Bastion host/demilitarized zone: Similarly, the outsider cannot directly contact you on your extension. They need to call the receptionist first. The receptionist will do the necessary due diligence and then pass the call on to you. Since your receptionist is beautiful and has direct contact with outsiders, she is more vulnerable. You need to ensure that she does not possess any sensitive or critical data. This is known as a bastion host or demilitarized zone.
Now, let's discuss how the different types of firewalls are implemented.
Types of firewall implementation
CISM aspirants need to understand the following types of firewall implementation.
Dual-homed firewall
A dual-homed firewall includes one packet filtering router and one bastion host with two Network Interface Cards (NICs).
The following diagram illustrates the concept of a dual-homed firewall:

Figure 9.3 – Dual homed firewall
Screened host firewall
A screened host firewall includes one packet filtering router and one bastion host.
The following diagram illustrates the concept of a screened host firewall:

Figure 9.4 – Screened host firewall
Screened subnet firewall (demilitarized zone)
The following are the characteristics of a screened subnet firewall:
- A screened subnet firewall consists of two packet filtering routers. It also has one bastion host.
- Of the preceding firewall implementations, a screened subnet firewall (demilitarized zone) is regarded as the most secure type of firewall implementation.
The following diagram illustrates the concept of a screened subnet firewall:

Figure 9.5 – Screened subnet firewall
Generally, servers that interact with the internet (extranet) are placed in a demilitarized area as this area is separate from internal servers and properly hardened. Also, generally, IDS is placed on a screened subnet, which is a decentralized zone.
Placing firewalls
A firewall should be placed in a hardened server with minimal services enabled. It is not recommended to place a firewall and IDS on the same physical server. A firewall should be implemented on a domain boundary to monitor and control incoming and outgoing traffic.
The most effective way to ensure that firewall rules are adequate is to conduct penetration tests periodically. Any gaps that are identified during the penetration test should be addressed immediately. This will help to improve the security posture of the organization.
Source routing
A firewall, by default, should be able to reject traffic with IP source routing. Source routing lets you get information about all the routers a packet transmits. This could potentially be used to bypass firewalls and hence is a security threat. If the firewall permits source routing, it is possible to conduct spoofing attacks by capturing the IP address of the organization.
Firewall and the corresponding OSI layer
CISM aspirants should have a basic understanding of the OSI layer for each type of firewall. The following table illustrates the different types of firewalls and their corresponding OSI layers:

Figure 9.6 – Firewalls and OSI layers
The functionality of the firewall improves with the increase in layers. An application-level firewall that operates at the seventh layer is regarded as the most robust firewall.
Key aspects from the CISM exam's perspective
The following are some of the key aspects from an exam perspective:


Table 9.1 – Key aspects from the CISM exam perspective
Questions
- What is the most robust firewall rule?
A. The rule to permit all traffic and deny specific traffic.
B. The rule to deny all traffic and permit only specific traffic.
C. The rule to decide dynamically based on the nature of traffic.
D. To provide discretion to the network administrator to permit or deny the traffic.
Answer: B. The rule to deny all traffic and permit only specific traffic.
Explanation: From all these options, the most robust firewall configuration is to deny all traffic and permit only specific traffic. This will be the most effective method to prevent unknown traffic from going to the organization's network.
- At which of the following OSI layers does a packet filtering firewall operate?
A. The packet filtering firewall operates at the network layer.
B. The packet filtering firewall operates at the application layer.
C. The packet filtering firewall operates at the transport layer.
D. The packet filtering firewall operates at the session layer.
Answer: A. The packet filtering firewall operates at the network layer.
Explanation: CISM aspirants should note that packet filtering and stateful inspection operate at the network layer (the third layer). The circuit-level firewall operates at the session layer (the fifth layer), and the application-level firewall operates at the application layer (the seventh layer).
- What is the most robust and secure firewall system implementation?
A. Screened host firewall
B. Screened subnet firewall
C. Dual-homed firewall
D. Stateful inspection firewall
Answer: B. Screened subnet firewall.
Explanation: A screened subnet firewall (demilitarized zone) is regarded as the safest type of firewall implementation. A screened subnet firewall includes two packet filtering routers. It also has one bastion host. The screened subnet firewall acts as a proxy and does not allow direct communication between external and internal networks. A demilitarized zone and a screened subnet firewall function in the same way. It must be noted that with a screened subnet firewall, there are two packet filtering routers, while with a screened host firewall, there is only one packet-filtering firewall.
- What firewall provides the most robust and secure environment?
A. Stateful inspection
B. Packet filter
C. Application gateway
D. Circuit gateway
Answer: C. Application gateway.
Explanation: An application-level firewall is considered the most secure kind of firewall. It functions at the highest level of the open system interconnection (OSI) model; that is, the application layer. It also works on the concept of bastion hosts and proxy servers, but it provides a separate proxy for each service. It controls applications such as FTP and HTTP. The application firewall functions at the application layer of OSI, whereas the circuit gateway functions at the session layer. The application gateway operates in a more granular aspect compared to other firewalls.
- Which of the following firewall structures will best protect a network from internet attacks?
A. Screened subnet firewall
B. Screened host firewall
C. Packet filtering router
D. Circuit-level gateway
Answer: A. Screened subnet firewall.
Explanation: A screened subnet firewall (demilitarized zone) is regarded as the safest kind of firewall implementation. A screened subnet firewall includes two packet filtering routers. It also has one bastion host. A screened subnet firewall acts as a proxy and does not allow direct communication between external and internal networks. A demilitarized zone and a screened subnet firewall function in the same way. It must be noted that with a screened subnet firewall, there are two packet filtering routers, while with a screened host firewall, there is only one packet-filtering firewall.
- Which of the following firewalls has been configured to permit external traffic only if it is in response to traffic from an internal host?
A. Application-level gateway firewall
B. Stateful inspection firewall
C. Packet filtering router
D. Circuit-level gateway
Answer: B. Stateful inspection firewall.
Explanation: A stateful inspection firewall monitors and tracks the destination of each packet that is being sent from the internal network. It makes sure that the incoming message is in response to the request that went out from the internal network. A stateful inspection firewall functions at the network layer of the OSI.
- Which of the following firewalls will not allow a file to be downloaded through file transfer protocol (FTP)?
A. Stateful inspection
B. Application gateway
C. Packet filter
D. Circuit gateway
Answer: B. Application gateway.
Explanation: An application-level firewall is regarded as the most secure type of firewall. It functions at the application layer of the OSI model. It also works on the concept of bastion hosts and proxy servers, but it provides a separate proxy for each service. It controls applications such as FTP and HTTP. The application firewall operates at the application layer of OSI, whereas the circuit gateway operates at the session layer. The application gateway operates in a more granular aspect compared to other firewalls.
- Which of the following firewalls will safeguard the most against hacking attempts?
A. Stateful inspection
B. A remote access server
C. Application-level gateway
D. Packet filtering
Answer: C. Application-level gateway.
Explanation: An application-level firewall is regarded as the most secure type of firewall. It functions at the application layer of the OSI model. It also works on the concept of bastion hosts and proxy servers but it provides a separate proxy for each service. It controls applications such as FTP and HTTP. The application firewall operates at the application layer of OSI, whereas the circuit gateway operates at the session layer. The application gateway operates in a more granular aspect compared to other firewalls.
- What area is of most concern for a risk practitioner while reviewing a firewall implementation?
A. The availability of a documented security policy.
B. The availability of an updated firewall infrastructure with the most secure algorithm.
C. The effectiveness of the firewall in enforcing compliance with information security policies.
D. The technical skills of end users.
Answer: C. The effectiveness of the firewall in enforcing compliance with information security policies.
Explanation: If the firewall is not able to enforce the requirements of the security policy, then that is a major loophole. The availability of a good security policy is important but it will be of little value if the same is not effectively implemented. Other options are not as significant as the effectiveness of the firewall.
- Which of the following is the most common type of error while setting a firewall configuration?
A. Incorrect configuration of the access lists.
B. Inadequate protection of the administrator password.
C. End users are not trained on firewall configuration.
D. Anti-virus software is not updated at frequent intervals.
Answer: A. Incorrect configuration of the access lists.
Explanation: Accurately updating the current access list is a major challenge that's faced by most organizations. Hence, incorrectly configuring an access list is the most common type of error while setting a firewall configuration. The other options are not relevant to firewall configuration.
- Which of the following is the first step of implementing a firewall in a big organization?
A. To develop a security policy
B. To conduct a gap analysis
C. To review the access control list
D. To set firewall configuration rules
Answer: A. To develop a Security Policy.
Explanation: The security policy specifies which firewall rules are to be configured. In the absence of a security policy, firewall rules will be ad hoc and may not support the objective of the organization. The other options are subsequent steps.
- What is the most significant job of a firewall?
A. Providing a routing service to connect different networks.
B. Supporting load balancing.
C. Connecting authorized users to a trusted network.
D. Improving the network's performance.
Answer: C. Connecting authorized users to a trusted network.
Explanation: The prime function of a firewall is to connect authorized users to a trusted network, thereby preventing unauthorized access to the server. The other options are secondary factors.
- What area is of the most concern for a security manager reviewing the firewall infrastructure?
A. The firewall administrator has not been trained on the security aspects.
B. The firewall rules are not reviewed at periodic intervals.
C. The firewall configuration is not approved by the security manager.
D. The implementation of a firewall above the commercial operating system with all the installation options enabled.
Answer: D. The implementation of a firewall above the commercial operating system with all the installation options enabled.
Explanation: When a firewall is placed on top of a commercial operating system without blocking the installation options, firewall security can be compromised. The other options are not as significant as option D.
- What is the most effective way to ensure that firewall is configured as per the security policy?
A. To conduct a review of the security policy
B. To conduct a review of the reported incident.
C. To conduct a review of the access control list
D. To conduct a review of the parameter settings
Answer: D. To conduct a review of the parameter settings.
Explanation: Reviewing the parameter settings helps us understand the configuration. This can then be compared with the requirements of the security policy. The other options are not as significant as reviewing the parameter settings.
- The primary function of a firewall is to address which of the following issues?
A. Unauthorized attempts to access the network outside the organization.
B. Unauthorized attempts to access the network within the organization.
C. Slow bandwidth.
D. Input processing error.
Answer: A. Unauthorized attempts to access the network outside the organization.
Explanation: The primary function of the firewall is to protect the network from external resources. The other options are not the objective of implementing a firewall.
- What is the primary objective when installing two parallel firewalls attached directly to the internet and the same demilitarized zone?
A. To establish a multi-layer defense
B. To distinguish the test and production environments
C. To allow for traffic load balancing
D. To control denial of service risks
Answer: C. To allow for traffic load balancing.
Explanation: Two parallel firewalls with two separate entries are useful to allow traffic load balancing. A multi-level defense will only be established if firewalls are installed in a series; that is, one behind another. If the firewalls are deployed in parallel, then they provide concurrent paths for compromise and do not provide a multi-layer defense. Both firewalls are connected to the same demilitarized zone, so they cannot separate the test and production environments. Firewalls generally cannot control denial of service risks.
- Where should an internet-facing server (extranet) be best placed?
A. Before the firewall
B. Outside the router
C. On a screened subnet
D. On the firewall server
Answer: C. On a screened subnet.
Explanation: Generally, servers that interact with the internet (extranet) are placed in a demilitarized area as this area is separate from internal servers and properly hardened. Placing the server before the firewall or outside the router would make it defenseless. The firewall should be placed in a hardened server with a minimum service enabled. It is not recommended to place anything else on the firewall server.
- Where should an intrusion detection system (IDS) be placed?
A. Before the firewall
B. Outside the router
D. On the firewall server
Answer: C. On a screened subnet.
Explanation: Generally, IDS is placed on a screened subnet, which is a decentralized zone. The demilitarized area is separate from internal servers and properly hardened. Placing the IDS before the firewall or outside the router is not recommended as the IDS will generate alerts on all malicious traffic, even though the majority of such traffic will eventually be blocked by the firewall and never reach the internal network. The firewall should be placed in a hardened server with minimal services enabled. It is not recommended to place anything else on the firewall server.
- Where is the best place to deploy a firewall?
A. On the database server
B. On the web server
C. On the IDS server
D. On the domain boundary
Answer: D. On the domain boundary.
Explanation: A firewall should be placed on a domain boundary to monitor and control incoming and outgoing traffic. The firewall should be placed in a hardened server with minimal services enabled. It is not recommended to place the firewall along with other services such as an IDS, database, or web server.
- What is the most effective method to ensure that firewall rules and settings are adequate?
A. To survey the IT team members.
B. To periodically analyze the system logs to determine any abnormal activities.
C. To conduct penetration tests frequently.
D. To conduct system audits frequently.
Answer: C. To conduct penetration tests frequently.
Explanation: The most effective way to ensure that firewall rules are adequate is to conduct penetration tests periodically. Gaps that have been identified during the penetration test should be addressed immediately. This will help improve the security posture of the organization. The other options are not as effective as penetration testing.
- What is one disadvantage of emailing a password-protected ZIP file?
A. They do not use strong encryption
B. The firewall administrator can read the file
C. They may be quarantined by the firewall or mail filters
D. They utilize high network bandwidth
Answer: C. They may be quarantined by the firewall or mail filters.
Explanation: Generally, firewall or mail filters would quarantine the password-protected ZIP files as the filter (or the firewall) will not be able to determine if the file contains malicious code. ZIP files can use strong encryptions. Generally, the firewall will not be able to read the password-protected file. A Password-protected file, by itself, does not increase network bandwidth.
- What area is of the main concern for a security manager reviewing the firewall configuration?
A. The firewall allows source routing
B. The firewall server is standalone
C. The firewall rules are reviewed on an ad hoc basis
D. The firewall allows unregistered ports
Answer: The firewall allows source routing,
Explanation: Firewalls, by default, should be able to reject traffic with IP source routing. Source routing lets you get information about all the routers a packet transmits. This could potentially be used to bypass firewalls and hence is a security threat. If source routing is allowed by the firewall, the intruder can attempt spoofing attacks by stealing the internal IP addresses of the organization. Deploying a firewall in a standalone server is a good practice. The firewall should be placed in a hardened server with minimal services enabled. Firewall rules should be reviewed in a structured way periodically. Allowing unregistered ports is not recommended but does not necessarily pose a significant security risk.
- What is the best way to prevent external individuals to access and modify the critical database of the organization?
A. A screened subnet
B. An acceptable usage policy
C. Role-based access controls
D. An intrusion detection system
Answer: A. A screened subnet.
Explanation: In a screened subnet, one bastion host is deployed along with two packet filtering routers. It is considered the most secured type of firewall implementation. It acts as a demilitarized zone. An acceptable usage policy and role-based access will not have an impact on external users. Intrusion detection systems will be able to identify invalid attempts, but they will not be able to prevent attempts.
- What device can be normally placed in a demilitarized zone?
A. Financial database
B. Web server
C. Operational database
D. Print server
Answer: B. Web server.
Explanation: A demilitarized zone is a separate area that is exposed to an external-facing untrusted area. Generally, servers that interact with the internet are placed in a demilitarized area as this area is separate from internal servers and hardened properly. Servers and resources placed in DMZ are isolated and are not directly connected to the internal network. The database should not be placed in a DMZ as it is exposed to an external connection.
- Generally, where is an intranet placed?
A. On the internal network
B. Outside the firewall
C. On a demilitarized zone
D. On the external router
Answer: A. On the internal network.
Explanation: An intranet server is not required to communicate with external networks as external people do not need to access the same one. So, for security purposes, it should be placed on an internal network. Placing the intranet server outside the firewall or on a demilitarized zone or an external router will expose it to external threats.
- What area is of major concern when there is an excessive number of firewall rules?
A. One rule may conflict with another rule and create a loophole
B. High expenditure for maintaining the rules
C. It may impact network performance
D. The firewall may not able to support excessive rules
Answer: A. One rule may conflict with another rule and create a loophole.
Explanation: Firewall rules should be simple and easy to implement. In the case of an excessive rule, it is difficult to manage the same and there is a chance that a particular rule may conflict with another rule, which may result in a loophole. Also, it becomes complex to test a high number of rules, so the operating effectiveness of the rule cannot be determined. High expenditure and network performance is a secondary concern. Next-generation firewalls can handle any number of rules.
IDSes and IPSes
Monitoring security events is a very important aspect of information security. Two important monitoring tools are IDS and IPS.
Intrusion detection system
IDS helps monitor a network (network-based IDS) or a single system (host-based IDS) to recognize and detect an intrusion activity.
Network-based and host-based IDS
The following table differentiates between network-based and host-based IDSes:


Table 9.2 – Difference between network-based and host-based IDSes
Components of IDS
The following table shows the various components of the IDS:

Table 9.3 – Components of IDS
Limitations of IDS
The following are some of the limitations of IDS:
- IDS operates based on the policy's definition. The weakness of the policy definition weakens how IDS functions.
- IDS cannot control application-level vulnerabilities.
- IDS cannot control the backdoor into an application.
- IDS cannot analyze the data that is tunneled into an encrypted connection.
Types of IDS
The following are the types of IDS:
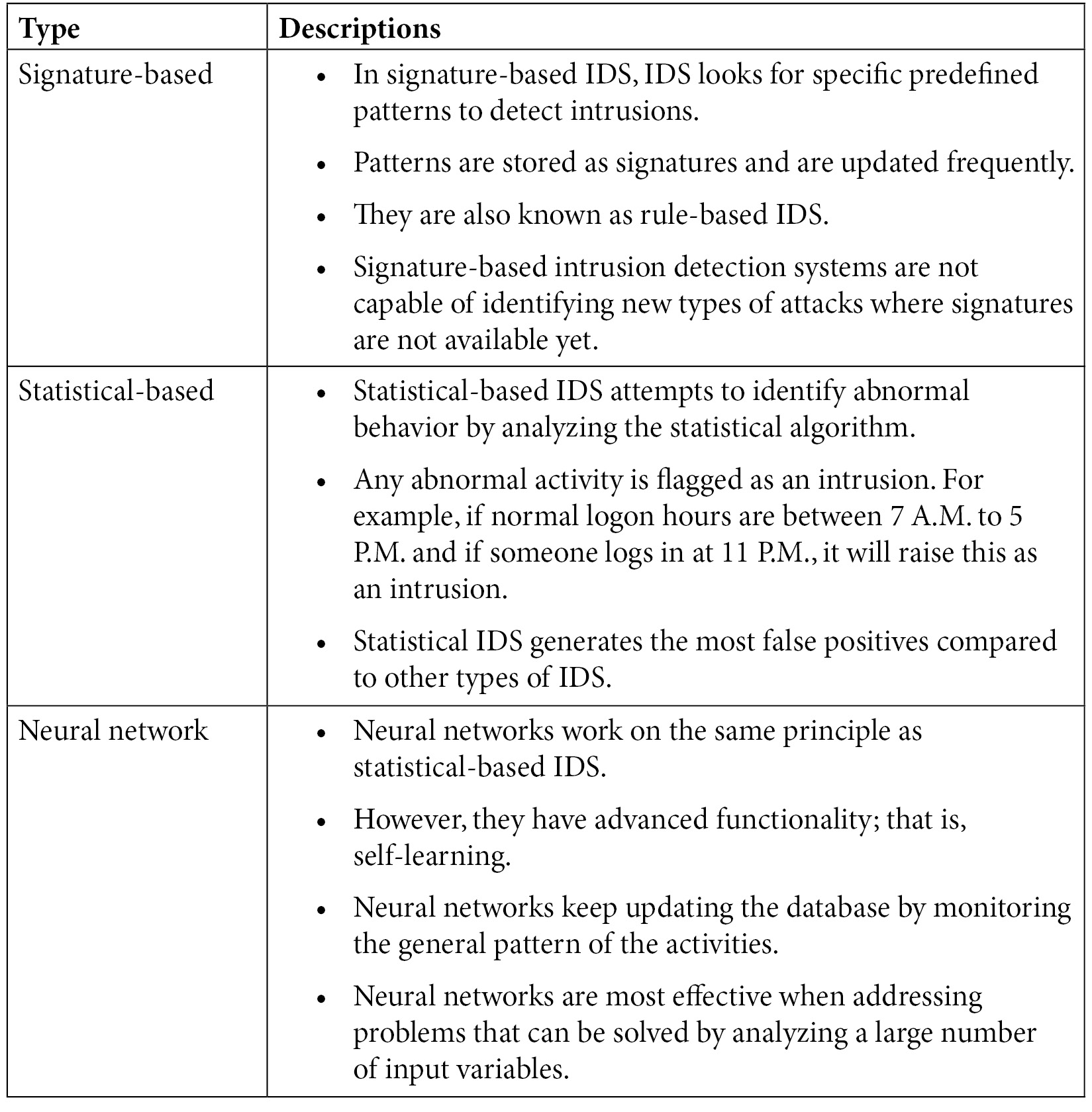
Table 9.4 – Types of IDS
Tuning is the most important element for successfully implementing IDS. Tuning is the process of adjusting the criteria to determine abnormal behavior. If the criteria are not tuned properly, IDS may generate false alarms or may not identify the actual abnormality. The most effective way to determine whether IDS has been tuned properly is to simulate various attack scenarios and review the performance of the IDS.
Placing IDS
Network-based intrusion detection systems can be installed either between the firewall and the external network (that is, the internet) or between the firewall and the internal network.
If an IDS is installed between the firewall and the external network, it will be able to identify all the intrusion attempts, irrespective of whether any intrusion packets bypassed the firewall or not:

Figure 9.7 – IDS placed before the firewall
If an IDS is installed between the firewall and the internal network, it will be able to detect only those attempts that bypassed the firewall rules:

Figure 9.8 – IDS placed after the firewall
Next, let's understand the IPS.
Intrusion prevention system
IPSes can not only detect intrusion attempts but also prevent the impact of intrusion attacks.
Difference between IDS and IPS
IDS only monitors, records, and provides alarms about intrusion activities, whereas the intrusion prevention system also prevents intrusion activities.
Honeypots and honeynets
A honeypot is a decoy system that's been set up to attract hackers and intruders. The purpose of setting up a honeypot is to capture the details of intruders to proactively strengthen the security controls. High interaction honeypots provide a real environment to attack, whereas low-interaction honeypots provide limited information.
A honeynet is a combination of linked honey pots. Honeynets are used for large network setups.
Key aspects from the CISM exam's perspective
The following are some of the key aspects from the exam's perspective:


Table 9.5 – Key aspects from the CISM exam perspective
Questions
- Which intrusion detection system observes the general pattern of activities and updates its database?
A. Neural network-based IDS
B. Statistical-based IDS
C. Signature-based IDS
D. Role-based IDS
Answer: A. Neural network-based IDS.
Explanation: Neural networks work on the same principle as statistical-based IDS. However, they have the advanced functionality of self-learning. Neural networks keep updating the database by monitoring the general pattern of the activities.
- Which part of an IDS collects data?
A. The console
B. The sensor
C. The analyzer
D. The interface
Answer: B. The sensor.
Explanation: The sensor's job is to collect data. Data may be in the form of IP packets, log files, and so on. The analyzer's job is to analyze the data and determine the intrusion activity. The administration console helps the administrator control and monitor IDS rules and functions. The user interface lets the user view the results and carry out the required task.
- Which intrusion detection system has the highest false alarms?
A. Neural network-based IDS
B. Statistical-based IDS
C. Signature-based IDS
D. Host-based IDS
Answer: B. Statistical-based IDS
Explanation: Statistical-based IDS attempts to identify abnormal behavior by analyzing the statistical algorithm. Any abnormal activity is flagged as an intrusion. For example, if the normal logon hours are between 7 A.M. to 5 P.M. and if someone logs in at 11 P.M., it will raise this as an intrusion. Statistical IDS generates the most false positives compared to the other types of IDSes.
- What is the major concern for an auditor verifying an intrusion detection system (IDS)?
A. The number of false alarms
B. Not being able to identify the intrusion activity
C. Using an automated tool for log capturing and monitoring
D. The IDS is placed between the internal network and the firewall
Answer B. Not being able to identify the intrusion activity.
Explanation: If the IDS is not able to identify and detect the intrusion activity, then this will be the area of most concern. It defeats the core purpose of installing the IDS. Attacks will remain unnoticed if they're not identified by the IDS, so no corrective and preventive action needs to be taken for such attacks. The number of false alarms is not as significant as IDS not being able to detect the intrusion attack. Options C and D are not areas of concern.
- Where is the best place to put an intrusion detection system that detects intrusions that bypass firewalls?
A. Between the firewall and the external network
B. Between the firewall and the internal network
C. Between the external network and the internal network
D. Alongside the firewall
Answer: B. Between the firewall and the internal network.
Explanation: If an IDS has been installed between the firewall and the internal network, it will be able to detect only those attempts that bypassed the firewall rules. If an IDS is installed between the firewall and the external network, it will be able to identify all the intrusion attempts, irrespective of whether the intrusion packets bypassed the firewall or not.
- Which of the following is a characteristic of an intrusion detection system (IDS)?
A. To collect evidence on intrusive activity
B. To route the traffic as per the defined rule
C. To block restricted websites
D. To act as an access control software
Answer: A. To collect evidence on intrusive activity.
Explanation: The intrusion detection system helps monitor a network (network-based IDS) or a single system (host-based IDS) to recognize and detect an intrusion activity. The function of IDS is to analyze the data and determine the intrusion activity. IDS does not provide features as per the other options.
- What is the most frequent problem regarding an intrusion detection system (IDS)?
A. False rejection rate
B. False acceptance rate
C. False positives
D. DDoS attacks
Answer: C. False positives.
Explanation: Identifying false positives is one of the routines and frequent issues when implementing IDS. IDS operates based on policy definitions. The weakness of policy definitions is that they weaken how IDSes function. The false acceptance rate and the false rejection rate are associated with biometric implementations. DDoS is a type of attack and is not an issue regarding how IDSses operate.
- Intrusion attacks and network penetration can be detected based on unusual system behavior from which of the following?
A. Hub
B. Packet filters
C. Switch
D. Intrusion detection system (IDS)
Answer: D. Intrusion detection system (IDS)
Explanation: IDS attempts to identify abnormal behavior by analyzing the statistical algorithm presented. Any abnormal activity is flagged as an intrusion. Hubs and switches are the networking devices for routing. A packet filter is a type of firewall that restricts blocked traffic.
- Which of the following is the most important control for detecting intrusions?
A. Access control procedures
B. Automatically logging off inactive computers
C. Monitoring unsuccessful login attempts
D. Account lockout after a specified number of unsuccessful logon attempts
Answer: C. Monitoring unsuccessful login attempts.
Explanation: The most important control for identifying and detecting intrusions is to actively monitor unsuccessful login attempts. The other options will not directly help detect the intrusion.
- Which of the following is the most important concern regarding intrusion detection systems?
A. Many false alarms are generated by statistical-based IDSes.
B. A firewall is installed between the intrusion detection system and the external network.
C. The intrusion detection system is used to detect encrypted traffic.
D. Zero-day threats are not identified by signature-based IDSes
Answer: A. Many false alarms are generated by statistical-based IDSes.
Explanation: Many instances of false alarms indicate that the IDS configuration needs to be tuned further. A poorly configured IDS would impact business processes or systems that need to be closed due to false alarms. It can harm business profitability. An IDS cannot read encrypted traffic; however, it can be compensated by a next-generation firewall. The other options are not as significant at blocking critical services and systems.
- What is the most important factor that impacts the effectiveness of a neural network?
A. The neural network detects all the known types of intrusion.
B. The neural network flags all activities that are not normal.
C. The neural network monitors the general pattern of activities, creates a database, and addresses the complex problems involving input variables from different sources.
D. The neural network solves problems where a large database is not required.
Answer: C. The neural network monitors the general pattern of activities, creates a database, and addresses the complex problems involving input variables from different sources.
Explanation: Neural networks work on the same principle as statistical-based IDSes. However, they have advanced functionality regarding self-learning. Neural networks keep updating the database by monitoring the general pattern of the activities. They are most effective at addressing problems that can be solved by analyzing a large number of input variables.
- An organization that wishes to protect the public-facing website on its server should install the network intrusion detection system where?
A. In a demilitarized zone
B. On the same web server where the website is hosted
C. Between the firewall and the external network
D. In the organization's internal network
Answer: A. In a demilitarized zone.
Explanation: Public-facing websites are placed in demilitarized zones to safeguard the internal network from external attacks. The IDS should be placed in the same demilitarized zone. The IDS will monitor the network traffic to detect any intrusions. A network-based intrusion would not be installed in a web server, just like a host-based IDS. Placing the IDS outside the firewall would not help protect the website.
Placing an IDS in an internal network is good to ensure that the website is not prone to internal attacks. However, an IDS would normally be placed in a demilitarized zone.
- To prevent a rootkit from being installed on a web server hosting an application, which of the following should be installed?
A. Packet filtering
B. A network-based intrusion detection system
C. The latest operating system patch
D. A host-based intrusion prevention system
Answer: D. A host-based intrusion prevention system.
Explanation: The most recommended option is to install a host-based intrusion prevention system. A host-based IPS will prevent the activities on the host computer or server such as files being deleted, programs being modified, and so on. A network-based IDS will be able to detect irregular traffic but if signatures are not updated or traffic is encrypted, it may bypass the IDS. Regular OS patch updates address such vulnerabilities, but host IPSes are more effective at preventing unauthorized installation. A network based intrusion detection system will not able to prevent rootkit installation. A packet-filtering firewall will not able to restrict the rootkit if the incoming IP is correct.
- Which of the following helps capture information to proactively strengthen the security controls?
A. Honeypot
B. Proxy server
C. IDS
D. IPS
Answer: A. Honeypot.
Explanation: A honeypot is a decoy system that's set up to attract hackers and intruders. The purpose of setting up a honeypot is to capture the details of intruders to proactively strengthen your security controls.
- Which of the following systems can block a hacking attempt?
A. Intrusion prevention system
B. Router
C. Switch
D. Intrusion detection system
Answer: A. Intrusion prevention system.
Explanation: Intrusion prevention systems can not only detect intrusion attempts but also prevent the impact of an intrusion attack. Intrusion detection systems only monitor, record, and provide alarms about intrusion activities, whereas intrusion prevention systems prevent intrusion activities. Router and switch are devices that are used for network routing.
- Which of the following is the first action you should perform when preparing for a system attack?
A. Capture information
B. Erase the evidence
C. Gain access
D. Launch a DoS attack
Answer: A. Capture information.
Explanation: The first step that an intruder takes is capturing and gathering relevant information about the target environment. Based on this information, they attempt various techniques to gain access. Once the objective has been accomplished, they try to erase the evidence.
- After the firewall, which of the following is considered the next line of defense for network security?
A. Anti-malware software
B. Router
C. Switch
D. Intrusion detection system
Answer: D. Intrusion detection system.
Explanation: Network-based intrusion detection systems are considered the next line of defense after firewalls. Intrusion detection systems monitor, record, and provide alarms about intrusion activity that bypasses the firewall. IDSes can identify abnormal traffic easier compared to anti-malware software. Router and switch are devices that are used for network routing.
- What is the major concern regarding a poorly configured intrusion prevention system?
A. The administrator has to verify high instances of alarms
B. Critical services or systems are blocked due to false alarms
C. The network is slowed down
D. The cost of the intrusion prevention system is high
Answer: B. Critical services or systems are blocked due to false alarms.
Explanation: A poorly configured firewall would largely impact business processes or systems that need to be closed due to false alarms. It can harm business profitability. The other options are not as significant as blocking critical services and systems.
- What is the most important aspect to consider while deploying an intrusion detection system?
A. Tuning
B. Patch updating
C. Logging
D. Change management
Answer: A. Tuning.
Explanation: Tuning is the most important element for successfully implementing IDSes. Tuning is the process of adjusting the criteria to determine abnormal behavior. If the criteria are not tuned properly, the IDS may generate false alarms or may not identify the actual abnormality. Patch updates are more related to the operating system. Logging and change management are not as relevant as tuning.
- Statistical-based IDSes are not as popular as signature-based IDSes due to which reason?
A. They are more expensive than signature-based IDSes
B. They require specialized staff to monitor
C. They generate false alarms from different user or system actions
D. They are not capable of detecting new types of attacks
Answer: C. They generate false alarms from different user or system actions.
Explanation: Statistical-based IDSes attempt to identify abnormal behavior by analyzing the statistical algorithm. Any abnormal activity is flagged as an intrusion. For example, if normal login hours are between 7 A.M. to 5 P.M. and if someone logs in at 11 P.M., it will raise this as an intrusion. Statistical IDSes generate the most false alarms compared to other types of IDS. Statistical-based IDSes can identify new attacks while signature-based IDSes cannot. Statistical-based IDSes may be more expensive and may require specialized staff, but the more important aspect is that they can detect false alarms.
- What is the main disadvantage of signature-based intrusion?
A. High instances of false alarms
B. Unable to detect new attack methods
C. High cost of maintenance
D. Use of high network bandwidth
Answer: B. Unable to detect new attack methods.
Explanation: In signature-based IDSes, the IDS looks for specific predefined patterns to detect intrusions. These patterns are stored as signatures and are updated frequently. They are also known as rule-based IDSes. Signature-based IDSes are not capable of identifying new types of attacks that signatures are not available for yet. The other options are not relevant.
- What is the most effective way to determine the deployment of an intrusion detection system?
A. Simulate various attack scenarios and review the performance of the IDS
B. Deploy a honeypot to determine any abnormal activity
C. Review the configuration of the IDS
D. Compare the IDS rules to the industry benchmark
Answer: A. Simulate various attack scenarios and review the performance of the IDS.
Explanation: The most effective way to determine whether the IDS has been tuned properly is to simulate various attack scenarios and review the performance of the IDS. The other options are secondary aspects.
- What is the main objective of deploying an intrusion detection system?
A. To comply with the information security policy
B. To comply with regulatory requirements
C. To determine the patterns of suspicious access
D. To identify the attacks on internal networks
Answer: D. To identify the attacks on internal networks.
Explanation: The main objective of an IDS is to identify the attacks on an internal network and provide alerts for immediate countermeasures, thereby minimizing the impact of the attack. The other options are secondary aspects.
- Which of the following is very important to ensure that the intrusion detection system can view all the traffic in DMZ?
A. Placing the IDS before the firewall.
B. Ensuring that all the end devices are connected to the IDS.
C. Ensuring encrypted traffic is decrypted before being processed by the IDS.
D. Ensuring the appropriate network bandwidth is being used.
Answer: C. Ensuring encrypted traffic is decrypted before being processed by the IDS.
Explanation: IDSes cannot read encrypted traffic. Encryption should be terminated before it is processed by the IDS. Encryption should be terminated at the secure socket layer or a VPN server to allow all traffic to be monitored. Placing an IDS before the firewall will generate a high number of alerts that will be eventually blocked by the firewall. The end devices don't need to be connected to IPS. Network bandwidth is not relevant.
- What is the most effective way to detect an intruder who has successfully penetrated a network?
A. Perform periodic audits
B. Perform periodic penetration testing
C. Establish vendor-provided default settings
D. Install a honeypot on the network
Answer: D. Install a honeypot on the network.
Explanation: A honeypot is a decoy system that's set up to attract hackers and intruders. The purpose of setting up a honeypot is to capture the details of intruders to proactively strengthen your security controls. As honeypots are closely monitored, any unauthorized attempts are more likely to be detected before significant damage is inflicted. The other options will not directly help detect the intruder.
- Denial or distributed denial of service (DDoS) attacks can be mitigated by which of the following?
A. Signature-based detection
B. An external router
C. Anti-virus software
D. Anomaly-based detection
Answer: D. Anomaly-based detection.
Explanation: Anomaly-based detection works based on the statistics of normal traffic patterns. It is also known as a statistic-based IDS. Anything different from the normal traffic range will be considered as deviation and an alert will be generated. In a DDoS attack, incoming traffic increases tremendously, so it is detected by anomaly-based detection. The other options will not be effective in detecting DDoS attacks.
- What is the most effective way to lure hackers and get their information without exposing the information assets?
A. Set a firewall
B. Set a proxy
C. Set a decoy file
D. Set a router
Answer: C. Set a decoy file.
Explanation: A decoy file is also known as a honeypot. A honeypot is a decoy system that's set up to attract hackers and intruders. The purpose of setting up a honeypot is to capture the details of intruders to proactively strengthen your security controls. The other options are used to keep the hacker out of the internal network.
- What will happen if an IDS is set with a low threshold value to determine an attack?
A. An increase in the number of false positives
B. An increase in the number of false negatives
C. Logs will not be captured
D. Active monitoring will be ignored
Answer: A. An increase in the number of false positives.
Explanation: Intrusion detection systems use different logs such as firewall logs, system logs, and application logs. These logs are analyzed to determine the trends and patterns of attacks. A threshold is an acceptable deviation from the normal pattern. A low threshold value means anything outside that value will be considered as an attack. Even genuine business traffic will be considered an attack if it is above the threshold. A low threshold value generally increases the number of false positives.
Digital signature
A digital signature is a process wherein a digital code is attached to an electronically transmitted document to validate the integrity of the document and the identity of the sender.
Creating a digital signature
A digital signature can be created by performing two steps:
- Create a hash (message digest) of the message.
- Encrypt the hash with the private key of the sender.
The following table shows how to create a digital signature:

Figure 9.9 – Digital signature
Now, let's discuss hash values and message digests.
What is a hash or message digest?
A hash function is a mathematical algorithm that provides a unique fixed string for any given message. Note that the hash value will be unique for each message. Let's understand this by looking at the following table:

Figure 9.10 – Hash values
The following software shows the hash value of the message Meeting at 8 AM:

Figure 9.11 – Hash software
The following software shows the hash value of the message Meeting at 8 PM:
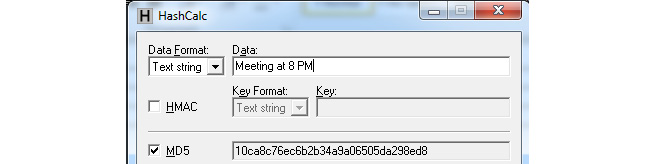
Figure 9.12 – Hash software
The hash value of the first message is for 8 A.M., while the second is for 8 P.M. As you can see, the hash value has changed, even though only one letter has changed in our message:

Figure 9.13 – Matching hash value
Let's look at how the message flows from sender A to recipient B:

Figure 9.14 – Verifying the digital signature
Receiver Mr. B will perform the following steps:
- First, he will independently calculate the hash value of Meeting at 8 AM. The hash value will be 4526dee03a36204cbb9887b3528fac4e.
- Then, he will decrypt the digital signature – that is, 4xxxxxxxxxxxxxxxxxxxxxxxxx4e – using the public key of sender Mr. A. (This proves authentication and non-repudiation.)
- Finally, he will compare the value derived from Step 1 with the value derived from Step 2. If both tally, this proves the integrity of the message.
Thus, a digital signature is used to verify the following properties:
- Integrity (that is, a message has not been tampered with)
- Authentication (that is, a message has been sent by the sender)
- Non-repudiation (that is, the sender cannot later deny sending the message)
However, a digital signature does not provide confidentiality
Key aspects from the CISM exam's perspective
The key aspects regarding digital signatures are as follows:
- In any given scenario, a digital signature ensures the integrity of the message (that is, the message hasn't been altered), the authentication of the message (that is, the message has been sent by the sender), and non-repudiation (that is, the sender cannot deny that they sent the message in a court of law).
- When creating a digital signature, only the hash of the message is encrypted (and not the entire message). Hence, the digital signature does not provide confidentiality or privacy.
- When encrypting the hash of the message, the private key of the sender should be used.
- Non-repudiation provides the best evidence about the occurrence of specific actions or transactions. The initiator of the transaction cannot deny that transaction.
Questions
- A hash function is used to ensure what?
A. The confidentiality of the message
B. The integrity of the message
C. The availability of the message
D. The compression of the message
Answer: B. The integrity of the message.
Explanation: A digital signature is used to validate the integrity, authentication, and non-repudiation of messages. However, it does not ensure message confidentiality. A digital signature includes an encrypted hash total of the message. This hash value would change if the message was subsequently altered, thus indicating that the alteration had occurred. Hence, it helps to ensure message integrity. Digital signatures will not able to address and support any of the other options.
- A digital signature addresses which of the following concerns about electronic messages?
A. The authentication and integrity of data
B. The authentication and confidentiality of data
C. The confidentiality and integrity of data
D. The authentication and availability of data
Answer: A. The authentication and integrity of data.
Explanation: A digital signature is used to validate the integrity, authentication, and non-repudiation of electronic messages. It does not ensure message confidentiality or the availability of data. A digital signature can be created by performing the following two steps:
Step 1: Create a hash value (message digest) of the message.
Step 2: Encrypt the hash with the private key of the sender.
- A digital signature addresses which of the following concerns about electronic messages?
A. Unauthorized archiving
B. Confidentiality
C. Unauthorized copying
D. Alteration
Answer: D. Alteration.
Explanation: The hash value of a message is used to create the digital signature. Each message has a unique hash. If the message changes, the hash also changes. Thus, the hash value will not be the same if the message is altered afterward. A digital signature will not address other concerns.
- Which of the following is used to address the risk of a hash being compromised?
A. Digital signatures
B. Message encryption
C. Email password
D. Disabling an SSID broadcast
Answer: A. Digital signatures
Explanation: A digital signature is created by encrypting the hash of the message. An encrypted hash cannot be altered without knowing the public key of the sender.
- A digital signature provides which of the following?
A. Non-repudiation, confidentiality, and integrity
B. Integrity, privacy, and non-repudiation
C. Integrity, authentication, and non-repudiation
D. Confidentiality, privacy and non-repudiation
Answer: C. Integrity, authentication, and non-repudiation.
Explanation: A digital signature is used to validate the integrity, authentication, and non-repudiation of electronic messages. It does not ensure message confidentiality or the availability of data.
- The MAIN reason to use digital signatures is to ensure data is what?
A. Private
B. integral
C. Available
D. Confidential
Answer: B. Integral
Explanation: Digital signatures provide integrity because the hash of the message changes if any unauthorized changes are made to the data (file, mail, document, and so on), thus ensuring data integrity.
- The strongest evidence of the occurrence of a specific action is provided by which of the following?
- Proof of delivery
- Non-repudiation
- Proof of submission
- Authorization
Answer: B. Non-repudiation.
Explanation: Non-repudiation assures that the sender of the message or initiator of the transactions can later deny the fact of sending the message or initiating the transaction. Non-repudiation is the most effective way to validate that a specific action occurred. Digital signatures are used to provide non-repudiation.
- A sender's authenticity can be best ensured by which of the following?
A. The use of the sender's private key to encrypt the hash of the message.
B. The use of the receiver's public key to encrypt the entire message.
C. The use of the sender's public key to encrypt the hash of the message.
D. The use of the receiver's private key to encrypt the entire message.
Answer: A. The use of the sender's private key to encrypt the hash of the message.
Explanation: The sender encrypts the hash of the message with their private key. If the recipient is successful in decrypting the message with the public key of the sender, then it proves authentication – that is, the message was sent from the sender. It ensures non-repudiation – that is, the sender cannot repudiate having sent the message. For authentication, the entire message doesn't need to be encrypted. Encrypting the entire message would involve more cost and time, so only encrypting the hash is necessary.
- In an e-commerce transaction, an organization is validating the customer through a digital signature when they receive communication from the customer. How can this be done?
A. A hash of the message can be transmitted and encrypted with the organization's private key.
B. A hash of the message can be transmitted and encrypted with the customer's private key.
C. A hash of the message can be transmitted and encrypted with the customer's public key.
D. A hash of the message can be transmitted and encrypted with the organization's public key
Answer: B. A hash of the message can be transmitted and encrypted with the customer's private key.
Explanation: A digital signature can be created as follows:
Step 1: Create the hash (message digest) of the message.
Step 2: Encrypt the hash with the private key of the sender.
In the question, the sender is the customer. So, the hash is to be encrypted with the customer's (sender's) private key.
- Digital signatures help with what?
A. Detecting spam.
B. Providing confidentiality.
C. Adding to the workload of gateway servers.
D. Decreasing the available bandwidth.
Answer: A. Detecting spam.
Explanation: By using a digital signature, a sender can be tracked. A digital signature helps authenticate the sender. The recipient will be able to set the configuration to their system to delete messages automatically from specific senders. The file size of the digital signature is only a few bytes and will not have any impact on bandwidth. There will be no major impact on the workload of gateway servers.
- What is the basic difference between hash and encryption regarding a hash value?
A. It cannot be reversed.
C. It is concerned with integrity and security.
D. It creates an output of a bigger length than the original message.
Answer: A. It cannot be reversed.
Explanation: Let's understand the outcome of hashing, as well as encryption:
For the Meeting at 8 AM message, the hash value is 4526dee03a36204cbb9887b3528fac4e.
For the Meeting at 8 AM message, the encryption value is Mxxxxxx xx x xM.
Now, from the 4526dee03a36204cbb9887b3528fac4e hash value, we cannot derive the message, but from Mxxxxxx xx x xM, we can derive the original message via decryption.
Hashing operates in a one-way fashion; it cannot be reversed. We can create a hash from the message, but it is not possible to create a message from that particular hash. Thus, the hash value is irreversible, whereas encryption is. This is the major difference between encryption and hash values.
- An organization is sharing critical information with vendors via email. Organizations can ensure that the recipients of emails (that is, vendors) can authenticate the identity of the sender (that is, employees) by doing what?
A. Having employees digitally sign their email messages.
B. Having employees encrypt their email messages.
C. Having employees compress their email messages.
D. Password protecting all email messages.
Answer: A. Have employees digitally sign their email messages.
Explanation: When an employee digitally signs their email messages, the receiver will be able to validate the integrity or authenticity by checking the digital signature.
- A digital signature ensures that the sender of the message cannot deny generating and sending the message. This is known as what?
A. Integrity
B. Authentication
C. Non-repudiation
D. Security
Answer: C. Non-repudiation.
Explanation: Non-repudiation provides the best evidence about the occurrence of a specific action or transaction. The sender of the email or initiator of the transaction cannot deny that transaction. Digital signatures are used to provide non-repudiation.
- In an e-commerce transaction, which of the following should be relied on to validate the occurrence of the transaction?
A. Proof of delivery
B. Authentication
C. Encryption
D. Non-repudiation
Answer: D. Non-repudiation.
Explanation: Non-repudiation provides the best evidence about the occurrence of a specific action or transaction. The initiator of the transaction cannot deny that transaction. Digital signatures are used to provide non-repudiation.
- Mr. A has sent a message containing the encrypted (by A's private key) hash of the message to Mr. B. This will ensure which of the following?
A. Authenticity and integrity
B. Authenticity and confidentiality
C. Integrity and privacy
D. Privacy and non-repudiation
Answer: A. Authenticity and integrity.
Explanation: In this case, the message is not encrypted (only the hash is encrypted), so it will not ensure privacy or confidentiality. Encrypting the hash will ensure authenticity and integrity.
- To implement a digital signature, which of the following is required?
A. The signer must have the public key of the sender, while the receiver must have the private key of the sender.
B. The signer must have the private key of the sender, while the receiver must have the public key of the sender.
C. Both the signer and receiver should possess a public key.
D. Both the signer and receiver should possess a private key.
Answer: B. The signer must have the private key of the sender, while the receiver must have the public key of the sender.
Explanation: A digital signature can be created as follows:
Step 1: Create a hash (message digest) of the message.
Step 2: Encrypt the hash with the private key of the sender.
On the recipient's end, the hash is decrypted using the public key of the sender.
- What is the objective of including a hash value (message digest) in a digital signature?
A. Ensuring the integrity of the message
B. Defining the encryption algorithm
C. Confirming the identity of the originator
D. Compressing the message.
Answer: A. Ensuring the integrity of the message.
Explanation: A digital signature is created by calculating the hash value for the given message. Recalculating the hash of the original message should provide the same hash value. Thus, it helps to ensure message integrity.
- What is the best way to ensure that the information that is transmitted over the internet is genuine and transmitted by the known sender?
A. Use a steganographic technique
B. Use an encryption technique
C. Use two-factor authentication
D. Use an embedded digital signature
Answer: D. Use an embedded digital signature.
Explanation: A digital signature is used to determine the identity and integrity of the data. The other options are not relevant for determining whether the message and sender are genuine.
- What is the most effective way to ensure non-repudiation?
A. Encryption
B. Hash
C. Symmetric encryption
D. Digital signatures
Answer: D. Digital signatures.
Explanation: A digital signature is used to validate the integrity, authentication, and non-repudiation of electronic messages. Non-repudiation is the process of ensuring that the sender of the message or initiator of the transaction is not in a position to deny the message. Encryption and symmetric encryption provide confidentiality but not non-repudiation. Hash provides integrity but not non-repudiation.
- What is the most effective way to ensure that a data file has not changed?
A. Validate the last modified date of the file
B. Encrypt the file
C. Provide role-based access control
D. Create a hash value of the file, then compare the file hashes
Answer: D. Create a hash value of the file, then compare the file hashes.
Explanation: The best way is to create the hash of the original file and then compare it with the suspected file to ensure that both files are the same. If the hash has changed, then it indicates that the file has been modified. The last modified date can also be fabricated. File encryption and role-based access control are good forms of access control but they do not prevent the file from being corrupted or modified by a valid user.
- What is the most effective way to validate the password that's entered by a user?
A. Packet filtering
B. Encryption
C. System hardening
D. Hashing
Answer: D. Hashing.
Explanation: Hashing is the process of converting a given password into another value. The result of a hash function is known as a hash value. When a user enters the password, it is converted into a hash and compared with the stored hash. If the hash matches, then access is granted. The actual password cannot be generated from the hash (because it is a one-way algorithm), so the actual password remains the same.
Elements of PKI
A public key infrastructure (PKI) is a set of rules and procedures for creating, managing, distributing, storing, and using a digital certificate and public key encryption.
PKI terminologies
CISM aspirants should have a basic understanding of the following terms regarding public key infrastructure:
- Digital certificate: A digital certificate is an electronic document that proves the ownership of a public key. The digital certificate includes details about the key, details about the owner, and detail about the digital signature of the issuer of the digital certificate. It is also known as a public key certificate.
- Certifying Authority (CA): A certification authority is an entity that is responsible for issuing digital certificates.
- Registration Authority (RA): A registration authority is an entity that verifies user requests for digital signatures and recommends the certificate authority to issue them.
- Certificate Revocation List (CRL): CRL is a list of digital certificates that have been revoked and terminated by the certificate authority before their expiry date. These certificates should no longer be trusted.
- Certification Practice Statement (CPS): A certification practice statement is a document that prescribes the practice and process of issuing and managing digital certificates by certifying authority. It includes details such as the controls that are in place, the method for validating applicants, and using certificates.
- Public Key Infrastructure: PKI is a set of roles, policies, and procedures for issuing, maintaining, and revoking public key certificates.
Now, let's discuss the process of issuing a PKI.
The process of issuing a PKI
Issuing a public key involves the following process:
- The applicant applies for a digital certificate to be issued to CA.
- The CA delegates the verification process to RA.
- RA verifies the correctness of the information provided by the applicant.
- If the information is correct, then RA recommends CA for issuing the certificate.
- CA issues the certificate and manages the same throughout its life cycle. CA also maintains details of certificates that have been terminated or revoked before their expiry dates. This list is known as CRL. CA also maintains a document called a CPS that contains the standard operating procedure (SOP) for issuing and managing certificates.
CA versus RA
The following table shows the differences between CA and RA:

Table 9.6 – Differences between CA and RA
Single point of failure
The private key of a certificate authority is used to issue the digital certificate to all the parties in the public key infrastructure. If the private key of CA is compromised, it will lead to a single point of failure for the entire PKI infrastructure because the integrity of all the digital certificates is based on this private key.
Functions of RA
A registration authority does the following:
- Verifies and validates the information provided by the applicant.
- Ensures that the applicant owns a private key and that it matches the public key that was requested for a certificate. This is known as proof of possession (POP).
- Distributes physical tokens containing private keys.
- Generates shared secret keys during the initialization and certificate pickup phase of registration.
Key aspects from the CISM exam's perspective
The following table covers some important aspects from the CISM's exam perspective:

Table 9.7 – Key aspects from the CISM exam perspective
Questions
- Which of the following functions manages the life cycle of a digital certificate?
A. Registration Authority (RA)
B. Certifying Authority (CA)
C. Public key authority
D. Private key authority
Answer: B. Certifying Authority (CA).
Explanation: A CA is an entity that is responsible for issuing digital certificates. The CA is responsible for issuing and managing digital certificates.
- Which of the following is the function of the Registration Authority (RA)?
A. To issue the digital certificate
B. To manage the certificate throughout its life cycle
C. To document and maintain certificate practice statements
D. To validate the information of the applicants for the certificate
Answer: D. To validate the information of the applicants for the certificate.
Explanation: A registration authority has the following functions:
- To verify and validate information provided by the applicant.
- To ensure that the applicant owns a private key and that it matches the public key requested for a certificate. This is known as proof of possession (POP).
- To distribute physical tokens containing private keys.
- To generate shared secret keys during the initialization and certificate pickup phase of registration.
- Which of the following authorities manages the life cycle of a digital certificate to ensure the existence of security in the digital signature?
A. Certificate Authority (CA)
B. Registration Authority (RA)
C. Certification practice statement
D. Public key Authority
Answer: A. Certificate Authority (CA).
Explanation: A CA is an entity that issues digital certificates. The CA is responsible for issuing and managing digital certificates.
- A certificate authority can delegate which process?
A. Certificate issuance
B. Certificate life cycle management
C. Establishing a link between the applicant and their public key
D. Maintaining the certificate revocation list
Answer: C. Establishing a link between the applicant and their public key.
Explanation: CA delegates some of the administrative functions such as verifying the information provided by applicants. RA is delegated with the function of verifying the correctness of information provided by applicants. RA verifies that the applicant owns a private key and that it matches with the public key requested for the certificate. This is known as proof of possession (POP).
- Which of the following is considered a weakness in a public key infrastructure process?
A. The certificate authority is in a centralized location
B. The transaction can be executed from any device.
C. The user organization is also the owner of the CA
D. The availability of multiple data centers to manage the certificate
Answer: C. The user organization is also the owner of the CA.
Explanation: This indicates that there is a conflict of interest as the user and owner of the certificate are the same. The independence of the certifying authority will be impaired in this scenario, and this is considered a major weakness.
- Which of the following is the function of the Registration Authority?
A. Issuing certificates.
B. Validating the information provided by the applicant.
C. Signing the certificate to achieve authentication and non-repudiation.
D. Maintaining the certificate revocation list.
Answer: B. Validating the information provided by the applicant.
Explanation: A Registration Authority has the following functions:
- To verify and validate information provided by the applicant.
- To ensure that the applicant owns a private key and that it matches the public key requested for a certificate. This is known as proof of possession (POP).
- To distribute physical tokens containing private keys.
- To generate shared secret keys during the initialization and certificate pickup phase of registration.
- The procedural aspect of dealing with a compromised private key is prescribed in what of the following?
A. Certificate practice statement
B. Certificate revocation list
C. Certificate disclosure statement
D Applicant disclosure form
Answer: A. Certificate practice statement.
Explanation: A certification practice statement is a document that prescribes the practice and process of issuing and managing digital certificates by certifying authority. It includes details regarding the controls in place, the method for validating applicants, and the usage of certificates.
- Which of the following is a function of a certifying authority?
A. To ensure the availability of a secured communication network based on certificates.
B. To validate the identity and authenticity of the certificate owner.
C. To ensure that both communicating parties are digitally certified.
D. To host the private keys of subscribers in the public domain.
Answer: B. To validate the identity and authenticity of the certificate owner.
Explanation: A registration authority has the following functions:
- To verify and validate information provided by the applicant.
- To ensure that the applicant owns a private key and that it matches the public key requested for a certificate. This is known as proof of possession (POP).
- To distribute physical tokens containing private keys.
- To generate shared secret keys during the initialization and certificate pickup phase of registration.
- When is a certificate authority not required in a public key infrastructure?
A. When users are not related to each other
B. When two-factor authentication is used
C. When users attest to each other's identities
D. When role-based access control is used
Answer: C. When users attest to each other's identities.
Explanation: The objective of the certificate authority is to support the identification of the key holder. If the users have already attested to each other's identity, the certificate authority may not be required. The certificate authority is relevant for the other options.
- In a public key infrastructure, the contractual relationship between parties is provided in which of the following?
A. Certificate revocation list
B. Digital certificate
C. Non-repudiation certificate
D. Certification practice statement
Answer: D. Certification practice statement.
Explanation: A certification practice statement (CPS) is a document that prescribes the processes for issuing and managing the digital certificates of the certifying authority. It also provides the contractual requirements between the relying parties and the certificate authority. It includes details such as the controls that should be in place, the method for validating applicants, and how certificates are used.
- What is the role of the certificate authority in public key infrastructure?
A. It supports the accuracy and integrity of the transferred data.
B. It prevents repudiation of transactions.
C. It attests to the validity of a user's public key.
D. It reduces the cost of data transfers.
Answer: C. It attests to the validity of a user's public key.
Explanation: The certifying authority is responsible for issuing and managing digital certificates. The certifying authority authenticates and validates the holder of the certificate after issuing the certificate. The other options are not the function of a certificate authority.
- What is the single point of failure in PKI?
A. The public key of the certificate authority (CA)
B. The private key of the holder of a digital certificate
C. The private key of the certificate authority
D. The public key of the holder of a digital certificate
Answer: C. The private key of the certificate authority.
Explanation: The private key of a certificate authority is used to issue the digital certificate to all the parties in public key infrastructure. If the private key of CA is compromised, it will lead to a single point of failure for the entire PKI infrastructure. This is because the integrity of all the digital certificates is based on this private key. If the private key of a holder is compromised, it will affect only that holder. The public key is published and poses no risk.
Asymmetric encryption
Cryptography is defined as the art or science of writing secrets using techniques such as encryption. Encryption is the process of converting data into unreadable code so that it cannot be accessed or read by unauthorized people. This unreadable data can be converted into a readable form via decryption. Different types of algorithms are available for encryption and decryption.
Symmetric encryption vis a vis asymmetric encryption
There are two types of encryption: symmetric encryption and asymmetric encryption. The following table shows the difference between the two terms:


Table 9.8 – Differences between symmetric and asymmetric encryption
Now, let's discuss the different types of encryption keys.
Encryption keys
In an asymmetric environment, a total of four keys are available with different functions. The following table indicates who possesses the different keys:

Table 9.9 – Different types of key and their functions
Using keys for different objectives
The aforementioned keys are used to achieve the following objectives:
- Confidentiality
- Authentication and non-repudiation
- Integrity
Let's discuss these further.
Confidentiality
In asymmetric encryption, two keys are used – one for encryption and another for decryption. Messages that are encrypted by one key can be decrypted by another key. These two keys are known as private keys and public keys. A private key is only available to the owner of the key; a public key is available in the public domain.
Messages can be encrypted with the following keys:
- Receiver's public key: If a message is encrypted using the public key of the receiver, then only the receiver can decrypt the same as they are the only one who has access to that private key. This will ensure message confidentiality as only the owner of the private key can read the message.
- Receiver's private key: The sender will not own the receiver's private key and hence this option is not feasible.
- Sender's public key: If a message is encrypted using the public key of the sender, then it can only be decrypted using the private key of the sender. The receiver will not own the sender's private key, so this option is not feasible.
- Sender's private key: If a message is encrypted using the private key of the sender, then anyone with a public key can encrypt the same. The public key is available in the public domain, so anyone can encrypt the message. This will not ensure the confidentiality of the message.
So, regarding message confidentiality, the receiver's public key is used to encrypt the message, while the receiver's private key is used to decrypt the message.
Authentication
Authentication is ensured by verifying and validating some unique features of the sender. Normally, we validate a document by verifying the signature of the sender. This signature is unique for everyone. Similarly, for digital transactions, a private key is unique for each owner. Only the owner owns their unique private key. Each private key has a corresponding public key. A third person can authenticate the identity of the owner by using a public key. When the objective is to authenticate the sender of the message, the sender's private key is used to encrypt the hash of the message. The receiver will try to decrypt the same by using the sender's public key. If it's successfully decrypted, this will indicate that the message is genuine and that the sender has been authenticated.
So, to authenticate a message, the sender's private key is used to encrypt the message, while the sender's public key is used to decrypt the message.
Non-repudiation
Non-repudiation refers to a situation wherein the sender cannot take on the responsibility of the digital message or transaction. Non-repudiation is established once the sender has been authenticated. Hence, for non-repudiation, the same concept of authentication will apply.
Hence, for non-repudiation of the message, the sender's private key is used to encrypt the message, while the sender's public key is used to decrypt the message.
Integrity
Integrity refers to the correctness, completeness, and accuracy of the message/data. To achieve integrity, the following steps must be performed:
- The sender will create a hash of the message.
- This hash is encrypted using the sender's private key.
- The message, along with an encrypted hash, is sent to the receiver.
- The receiver will do two things. First, they will decrypt the hash value using the sender's private key. Then, they will calculate the hash of the message that was received.
- The receiver will compare both hashes and if both hash values are the same, the message is considered correct, complete, and accurate.
The following table shows the process of using different keys to achieve each of these objectives:

Table 9.10 – Process of using different keys
Key aspects from the CISM exam's perspective
The following are some of the key aspects from the exam's perspective:


Table 9.11 – Key aspects from the CISM exam perspective
Questions
- What is the best way to secure customer communication in an e-commerce application?
A. Data encryption
B. Multiple authentication methods
C. Digital signature
D. Maximum password age
Answer: A. Data encryption.
Explanation: The best method is to encrypt the communication, which will ensure the confidentiality of the transactions. Multiple authentications, maximum password age, and digital signatures may help with strong authentication, but they will not help maintain the confidentiality of data in transit.
- What is the most commonly used protocol to safeguard the confidentiality of data that's transmitted in an e-commerce application?
A. Secure Socket Layer
B. Dynamic Host Configuration Protocol
C. Secure Shell
D. Telnet
Answer: A. Secure Socket Layer.
Explanation: Secure Socket Layer (SSL) is the protocol that operates at the transport layer. It is used for privacy and data security while communicating over the network. SSL makes use of cryptographic functions to protect the confidentiality, reliability, and integrity of private documents traveling through the internet. Dynamic Host Configuration Protocol (DHCP) is a protocol that's used to manage the network configuration. A DHCP assigns an IP address and other network configuration parameters to every device on a network so that they can communicate with other IP networks. Secure Shell (SSH) and Telnet are remote terminal control protocols. Through these protocols, a user can connect to a terminal from a remote location.
- What is the most effective way to protect the data on a mobile computing device?
A. To conduct a data integrity check
B. To encrypt the data stored on the mobile
C. To enable a screensaver for the device
D. To enable biometric access control
Answer: B. To encrypt the data stored on the mobile.
Explanation: Encryption is the most effective way to safeguard the data stored on mobile devices. Encryption converts the data into an unreadable format. It can only be read by the person possessing the encryption key. The other options are good controls but they are not as effective as encrypting the data.
- For a large number of key distributions, why is public key encryption preferred compared to symmetric key encryption?
A. Computation is more efficient in public key encryption
B. Scaling is comparatively more convenient in public key encryption
C. The maintenance cost is less in public key encryption
D. Public key encryption provides greater encryption
Answer: B. Scaling is comparatively more convenient in public key encryption.
Explanation: One of the limitations of the symmetrical key is that it requires a key for each pair of individuals who wish to have communicated privately, resulting in an exponential increase in the number of keys. This, in turn, results in complex distribution and storage problems. Public key encryption does not have this issue. Public key encryption requires more computation efforts and maintenance costs compared to symmetric keys. A public key by itself does not provide greater encryption strength.
- Which of the following is more likely to cause an internal attack on a network?
A. No minimum timeframe defined for password expiry
B. Security training is not given in a structured manner
C. User passwords are not encrypted
D. All PCs are placed in a single subnet
Answer: C. User passwords are not encrypted.
Explanation: If passwords are sent over an internal network in plain text, they can be easily sniffed. Passwords should be encrypted for adequate security. The other options do not present significant exposure.
- What is the most effective way to prevent a database administrator from reading sensitive data from a database?
A. Capture the log for database access
B. Implement application-level encryption
C. Implement a DLP solution
D. Provide security awareness training to the database administrator
Answer: B. Implement application-level encryption.
Explanation: Encryption makes the database unreadable for DBA and other staff. This helps the DBA perform this routine function without reading the data in cleartext. The other options cannot prevent the DBA from reading the data in a database.
- In a public key infrastructure, the public key of the other party is required to do what?
A. Authorize the user
B. Create the digital signature
C. Authenticate the sender
D. Compress the file
Answer: C. Authenticate the sender.
Explanation: The public of the other party is used to decrypt the message and if the message is successfully decrypted, it helps authenticate the user; that is, the owner of the corresponding private key. Authorization and compression are not functions of PKI. A private key is used to create a digital signature.
- What is the best way to secure a wireless network as a point of entry into an organization's network?
A. Intrusion detection system
B. Strong encryption
C. Two-factor authentication
D. Packet filtering router
Answer: B. Strong encryption.
Explanation: The most effective way to secure a wireless network is to provide strong encryption. IDSes and routers will not offer any protection from local attacks. Two-factor authentication is for access control and will not protect data from being sniffed.
- What is the best way to secure data on a USB device?
A. Authentication-based access
B. Only read data on the USB device
C. Encrypt the USB device
D. Restrict the use of the USB device
Answer: C. Encrypt the USB device
Explanation: Encryption is the most effective way to safeguard the data stored on mobile devices. Encryption converts the data in the USB in an unreadable format. It can only be read by the person who possesses the encryption key. The other options are good controls but they are not as effective as encrypting the USB device.
Summary
In this chapter, we discussed various information security monitoring tools and techniques such as firewalls and various types of IDSes and IPSes. Hopefully, this chapter has helped you understand the important methods, tools, and techniques for developing a security program effectively and efficiently. We also discussed digital signatures and encryption technology from an information security perspective.
In the next chapter, we will provide an overview of incident management procedures.
