Privacy Concerns with the Smart Grid
Information in this chapter:
“These patterns can be useful for analysing our energy use for energy conservation but, together with data from other sources, the potential for extensive data mining is very significant.”1
Giovanni Buttarelli, assistant director of the European Data Protection Supervisor.
Personal data
The above quotation refers to comments raised by the European Data Protection Supervisor raising his concerns about the massive amount of personal data that can be accessed without appropriate safeguards. Indeed, there have been numerous concerns related to the potential threat of personal data by Smart Grids. Consumer acceptance of the grid “depends upon the development of legal and regulatory regimes that respect consumer privacy, promote consumer access to and choice regarding third-party use of their energy data” according to a recent US Department of Energy report.2
As we analyze the proposed risks to consumer privacy, and effectively the implications to personal data, we should firstly consider what we mean by the term “personal data.” There are of course many different descriptions of the term personal data; invariably, they do refer to the text as outlined by the UK Data Protection Act:
UK Data Protection Act—Basic Interpretive Provisions
Effectively, what the above text refers to is, can a living individual be identified from the data, or, from the data and other information in the possession of, or likely to come into the possession of, the data controller?3
Using this premise as the basis to assess the privacy implications of the Smart Grid, it is likely that there will be data that can identify a living individual originating from the metering infrastructure. Moreover as has been identified in the quote from the European Data Protection Supervisor, without the implementation of appropriate safeguards, there will be massive amounts of personal data easily accessible by authorized and potentially unauthorized parties.
Privacy risks associated with the Smart Grid
Smart Grids provide many benefits to its stakeholders; in particular, consumers are given control and transparency over their energy usage. In practical, terms what this allows includes (but not limited to) as follows:
- Ability to login into their energy account and view how much energy they are using based upon information reported from their smart meter.
- Allow smart devices to adjust energy consumption based upon their preferences, and the price of energy (e.g. utilize off-peak pricing).
- Receive alerts based upon grid outages via the preferred communication channel as outlined in their profile preferences.
- Allow the grid operator to accurately identify the source of disruption, thus allowing for rerouting, and subsequently minimizing the time and impact of disruption.
The above consumer benefits are only a small subset of available examples. One thing, that is perfectly clear, is that to realize these benefits there will be a need to utilize personal data, in other words data that identifies the consumer. Consider that in Italy, for example, in 2009, it was reported that 85% of homes already had a smart meter in each home4 that of course puts the earlier quote into context whereby there will be a massive collection of personal data (note: the author(s) make no statement on the specific implementation of the Italian Smart Grid deployment, merely to illustrate the amount of personal data collected).
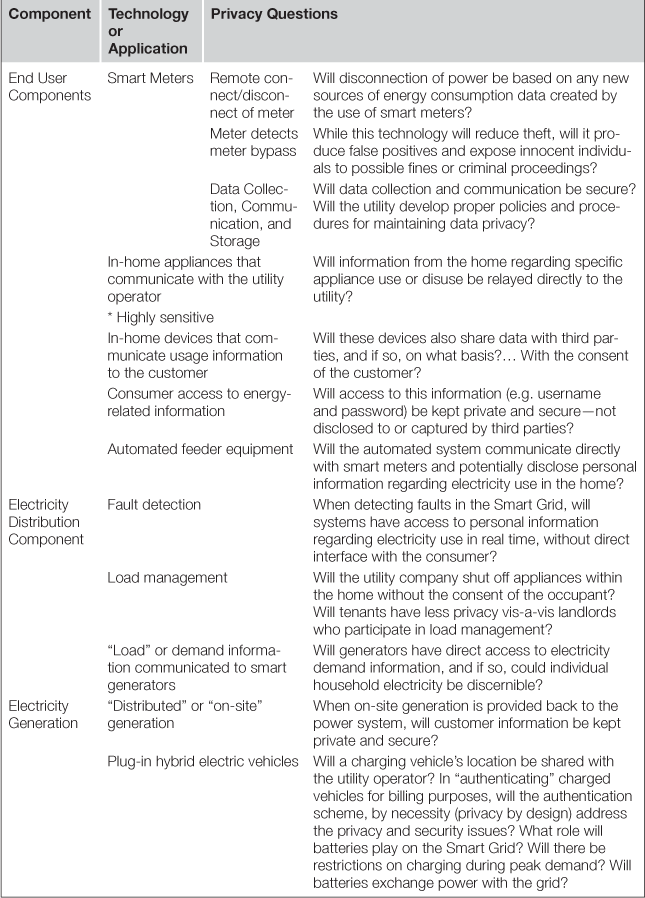
Earlier chapters discussed the technical components of the Smart Grid, but it is important to consider that these systems will collect personal data. Although specific implementations may have additional components capable of collecting and processing personal data, the following represents the core devices at the center of privacy concerns related to the grid.
Smart Meters: One of the key objectives of the meter is to record the energy consumption of the consumer, and report this back to the operator/energy company. As we mentioned earlier, one of the main consumer benefits is to report energy usage in a very granular fashion, where, for example, they could well report consumption in near real-time.
One could ask the question, well so what? Does it really matter if anybody knows how much energy you are consuming? Well, the impact on privacy is that it allows a third party to establish a profile of the activities being undertaken at a property. For example, if there is no usage of energy at specific times in the day, it may be an indication that property is vacant. Now ask the question, does it really matter? Do you really want third parties to know at what time your home is potentially vacant? Moreover, the level of granularity goes beyond simply on or off. For example, a third party may even be able to estimate the number of individuals at a given property.
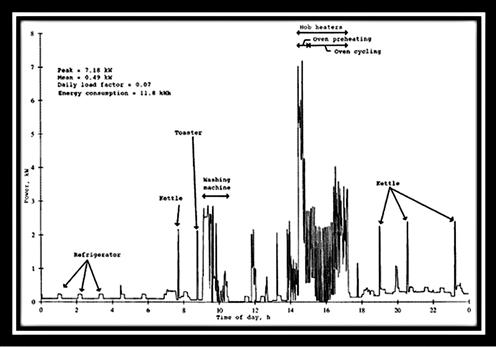
Consumer Appliances: Not only are the meters capable of capturing usage by consumers, the appliances that are now “smart” also have the opportunity to capture and reveal a wealth of information. According to the National Institute of Standards and Technology (NIST); NISTIR 7628, “Guidelines for Smart Grid Cyber Security: vol. 2, Privacy and the Smart Grid5,” it is possible to utilize Nonintrusive Appliance Load Monitoring (NALM) techniques to not only reveal usage patterns about individual appliances, but also identify individual appliances using libraries of known patterns. Indeed, an Italian research study from 2002 using data from 15 min intervals was able to pinpoint the use of washing machines, dishwashers and water heaters with an accuracy rate over 90%. Furthermore, this degree of accuracy is only likely to increase as more signatures become available.
This degree of accuracy is presented in graphical format in Figure 4.1.
Perhaps, letting third parties know about the appliances you use in your home is not an issue. It is not as though your medical records are being shared publicly? However, there have been a number of “worst cases” and in some cases farfetched scenarios presented that have raised some significant concerns by consumers. Some of these examples include the use by law enforcement to review the energy consumption of properties to determine whether, for example, marijuana is being grown! While this may seem one of those scenarios, we class under the farfetched category, consider that in Ohio, there are at least 60 subpoenas filed by law enforcement seeking customer’s energy records from power companies.6 This technique is confirmed as effective by enforcement, and according to a spokesperson from American Electric Power, they commented “We’re obligated when we get these requests. There’s not an option to say no.” Ultimately, the net result is that law enforcement are provided with information about the subscriber, including the billing details. It would be fair to say that when the grid becomes ubiquitous, more detailed information is available that the number of subpoenas is likely to increase. While this example may seem perfectly reasonable, and for those of you that are not marijuana growers, the risk that the Smart Grid can allow law enforcement the opportunity to undertake non-intrusive, real-time surveillance is of little concern. However, this particular use case does represent a very interesting precedent, the case in question is Kyllo v. United States; in this particular case, the government used the monthly energy records for its case against a suspected marijuana grower to demonstrate that the power usage of the suspect was deemed as excessive and in line with that of a marijuana growing operation. The case, however, demonstrated a very interesting precedent pertaining to the privacy interest under the Fourth Amendment. This contains a “search and seizure” provision that requires warrants before the government can invade one’s internal space. In this particular case, the Supreme Court stated.
“We think that obtaining by sense-enhancing technology any information regarding the interior of the home that could not otherwise have been obtained without physical intrusion into a constitutionally protected area, constitutes a search [and is] presumptively unreasonable without a warrant.”7
The case in question had some additional facets that related to the government’s use of thermal imaging to determine the areas of the house that were hotter than other parts. The court ultimately found that the Kyto had a reasonable expectation of privacy as the government used a technology not in general use.
One thing is clear that the use of a thermal imager was able to reveal a considerable amount of information related to the activities of the suspect, but if we consider smart meters—they can reveal considerably more. In this particular case (and as we saw with the statistics demonstrated in Ohio), law enforcement will invariably request the energy usage records from the grid operator/energy company. In this particular case the third-party doctrine of the Fourth Amendment will clearly apply. According to the Harvard Journal of Law & Technology vol. 25, Number 1 Fall 2011,8 it states that
“The third-party doctrine states that a person cannot legitimately expect information that is shared with a third party to remain private from law enforcement.”
Although this may not be a concern for the reader, why of course should you be concerned about law enforcement having access to full details about your energy consumption, law enforcement is only one class of third party that would benefit from data derived from meters. There exist considerably more data classes, and third parties that would benefit from gaining access to such information, examples of privacy concerns as detailed below and based on a report by the Information and Privacy Commissioner of Ontario, Canada.9
The Table 4.1 illustrates the type of data that could well be garnered from the Smart Grid, and this data could well become valuable to third parties beyond law enforcement. We will discuss the supply chain within the Smart Grid elsewhere in the book, but with regards to privacy, the concerns are very high for consumers where sensitive data could be made [legally] available to organizations outside of the energy supplier, grid operator, and of course law enforcement. One simple example may be insurance companies, where an insight into the behavior of consumers could well impact insurance premiums. Although the possibility of the insurance provider utilizing energy consumption to set premiums may seem somewhat far fetched, it is worthwhile considering that the grid operator may look to develop information it collects as a revenue stream. Consider also the attractiveness of such a rich repository of valuable information to those individuals that may seek to access data they are unauthorized to access.
Of course the release of individual, personal data will be covered by privacy legislation, and this was highlighted by the Article 29 Working Party opinion10 on Smart Grids which stated; “Where personal data are contained in the information generated and disseminated by a smart meter, the Working Party determines that Directive 95/46/EC applies to such processing.” Therefore it is expected that without some form of explicit consent, the grid operator/energy supplier cannot release this information to authorized third parties. Note, the caveat there? Authorized third parties. If you have a database with millions of records that are of economic benefit to many, then it does make the system considerably more attractive to malicious individuals looking to get the data for re sale. This becomes an unintended consequence of the Smart Grid, where the simple collation of such valuable data, makes it more attractive for malicious individuals to try and retrieve the data to sell on. This is out of scope for this book, mainly because the controls for protecting this data are covered by multiple books elsewhere (this will likely be within the IT domain).
As mentioned earlier, it is expected that the data will not be about the individual and therefore not covered under the scrutiny of data protection legislation. What is likely to be sold to authorized third parties should be anonymized. When we say authorized, however, we are likely to be referring to that authorization being provided by the operator, and not the consumer. This of course should not cause any privacy concerns, right? Well not quite.
The challenge we face with the release of very large volumes of data is the issue of inference. Of course, we make a very big assumption that the data cleansing routine is of sufficient quality so as not to inadvertently reveal personal information. However, if we assume that obfuscation of personal data fields is of sufficient quality, then we are faced with the inference challenge. In a nutshell, this refers to the ability to derive data that may be sanitized from the collation of multiple data sources. A simple example is those records which fall outside of normal, or average consumption, and is a technique we saw used by law enforcement to infer marijuana growth. The field of analytics for the Smart Grid is anticipated to grow enormously, and Pike Research estimates that the market for software and services that can mine intelligence could reach a cumulative $11.3 billion between 2011 and 2015.11 Of course, this figure in itself is not indicative of burgeoning privacy considerations and indeed, there could be tremendous value to the consumer in the operator in identifying intelligence that could be passed to the consumer. For example, recommendations on energy consumption that could save money; we noticed that your washing machine is used always during peak hours, but by doing your washing an hour later then you could save twelve dollars per month. However, what may be less desirable are a plethora of electronics manufacturers inundating consumers with details of their latest products with detailed prior knowledge about the devices and their consumption within the home, without prior consent. This concept of Big Data, and the ability to infer certain things about consumers are already uncovering things about consumers that somewhat blur the line of ethics. A recent example related to shopping habits reveals this in striking detail, whereby in a recent NY Times12 article, it was revealed that the US retail shopping organization “Target” were able to identify their customers that were likely expecting a baby. Simple indicators such as women buying larger quantities of unscented lotions at the start of their second trimester, as well as purchases of other indicating products, all suggested the customers that were likely pregnant. Indeed, the company built a “pregnancy prediction” score that predicted the likelihood of the data subject being pregnant based on the various products purchased together. This allowed the company to send coupons based on the stages of pregnancy (note: they were able to predict the due date). The implications of this degree of accuracy were demonstrated approximately a year after the pregnancy prediction was developed as cited below:
“A man walked into a Target outside Minneapolis and demanded to see the manager. He was clutching coupons that had been sent to his daughter, and he was angry, according to an employee who participated in the conversation.
‘My daughter got this in the mail!’ he said. ‘She’s still in high school, and you’re sending her coupons for baby clothes and cribs? Are you trying to encourage her to get pregnant?’
The manager didn’t have any idea what the man was talking about. He looked at the mailer. Sure enough, it was addressed to the man’s daughter and contained advertisements for maternity clothing, nursery furniture and pictures of smiling infants. The manager apologized and then called a few days later to apologize again.
On the phone, though, the father was somewhat abashed. ‘I had a talk with my daughter,’ he said. ‘It turns out there’s been some activities in my house I haven’t been completely aware of. She’s due in August. I owe you an apology.’”
Now of course there is no suggestion that Smart Grid analytics can indicate whether consumers are expecting a baby. However, what this example demonstrates is that here you have a commercial organization being aware that a girl was pregnant before her own father, and that the field of analytics is able to infer that level of accuracy simply based on a series of purchases. Although this example is entirely unrelated to the type of data that can be garnered with Smart Grids, it demonstrates the power of analytics and how “creepy” the conclusions it can draw. Furthermore, when it comes to Smart Grids there are three factors we know for sure:
1. The field of Smart Grid analytics is predicted to grow to monumental proportions.
2. Third-party organizations will most certainly be interested in gaining access to such data.
3. There will be financial benefits for operators who are able to “sell” such data to third parties.
When you combine these three factors, it is evident that the implications regarding the privacy of consumers may well be significant, and of concern. Of course if handled appropriately, there should not be this degree of concern. After all, what consumer wouldn’t want to know ways to save money? Or should I have said… what operator wouldn’t want to know ways to make money! However, a simple privacy notice is not sufficient, electronic distribution today only provides the opportunity to accept or reject. Reject in many cases is simply being prevented from utilizing the service; therefore, allowing some constructive feedback option is essential.
Moreover, what the above example does demonstrate is that there may be privacy concerns when at first glance there may not appear to be any issues. There is a great deal of research being conducted to determine the amount of information that can be garnered from Smart Grid deployments. One such example13 was presented at the hacker conference, the Chaos Computing Congress by researchers Dario Carluccio and Stephan Brinkhaus under the title “Smart Hacking for Privacy.” The title of the presentation does of course give the game away with regards to the content; however, the level of detail they were able to derive from their research was certainly surprising. By signing up with a company known as Discovergy to have a meter installed in their chosen location to conduct the research, they were able to identify a number of privacy concerns. Their research uncovered numerous security flaws that included the ability for their data and passwords to be intercepted, as they were transmitted in clear text, they also found that the smart meters were monitoring power usage, not in the fifteen-minute intervals suggested as standard earlier in this chapter, but rather in two-second intervals. We had previously discussed the privacy implications associated with fifteen-minute intervals, but the researchers then asked the question, what level of detail could be garnered from considerably smaller intervals? The outcome of their work found that not only are there likely signatures for the devices within a consumer’s home but also the research found that there are also likely to be signatures for movie or a television show based on the brightness levels for particular scenes. We had previously considered the need for security controls to protect the usage data from unauthorized third parties and suggested that they are out of scope for the book as this topic is extensively covered in other publications. However, just because it is covered elsewhere, its importance should not be underestimated. Carluccio and Brinkhaus found the historical records of meter usage were easily obtainable from the company’s systems despite the design only allowing access for the previous three months. The CEO of Discovergy, who was at the presentation, took to the stage and defended the polling interval as necessary in order to notify consumers if they had left their home with an iron left on, but had promised to make the polling interval configurable for their customers who are concerned with privacy issues.
Therefore operators should most certainly undertake an assessment to consider the privacy implications with any implementation. Who knows, as investment continues in the field of analytics, and as the data sets do get richer, it may well be likely to predict pregnancies.
Privacy impact assessment
As has been already discussed, there are potentially some considerable privacy concerns with regards to Smart Grid deployments. It therefore becomes important to ensure that a more detailed assessment is undertaken, invariably this assessment is comprised of a privacy impact assessment (PIA), a process designed to analyze the privacy implications within a given system. A privacy impact assessment or data protection impact assessment (DPIA) is a recommended action through a number of authoritative sources. For example, Expert Group 2 of the EC Task Force on Smart Grids is in the process of developing a DPIA template that can be then used by operators; in addition, vol. 2 of NISTIR 7628 recommends the following: “Conduct an initial privacy impact assessment before making the decision to deploy and/or participate in the Smart Grid.”
Undertaking a privacy impact assessment (or DPIA) is necessary for not only satisfying legal requirements, but according to the UK Information Commissioner’s Office (ICO),14 there are many other reasons:
• Identifying and managing risks: Conducting an exercise to identify potential privacy risks early in any project demonstrates good governance and business practice. Equally, from a security perspective, it is likely for risk assessments to be conducted in the early phases of projects, and a PIA may be considered part of this broader risk exercise.
• Avoiding unnecessary costs: The concept of “privacy by design” is an effective foundation toward ensuring that systems have the appropriate safeguards to reduce privacy risks. By undertaking an assessment early to identify potential privacy risks, it reduces the likelihood of after-market solutions being bolted on after the system has been deployed. Not only is this more likely to be cost effective, it will certainly allow the project team to consider any safeguards as part of the project budget. In comparison, unexpected costs after deployment will more than likely be after the setting of any project budgets.
• Inadequate solutions: Identifying risks early allows the opportunity and time to source appropriate safeguards. According to the Information Commissioner’s Office, the bolt-on solutions “devised only after a project is up and running can often be a sticking plaster on an open wound, providing neither the same level of protection for the individual nor organization that privacy risks have been identified and adequately addressed.” The same incidentally applies to security, whereby like privacy, integrating the controls into the design of solutions is key to the deliver of any implementation.
• Avoiding loss of trust and reputation: There are no assurances that conducting a PIA will entirely prevent privacy issues within any system deployment. However, the ICO, as well as numerous global authoritative sources, do feel that it reduces the likelihood. What is clear is that if an organization experiences a privacy breach and has not conducted any form of privacy impact assessment (PIA), then this will likely be seen negatively by the Data Protection Authority (DPA) that would consider this with regards to any punitive action.
• Informing the organization’s communications strategy: This is related to the loss of trust and reputation and allows any potential risks to identified and correlated with the communications plan.
• Meeting and exceeding legal requirements: Conducting a PIA provides the opportunity to ensure that any privacy risks are identified early, and therefore, implementing the appropriate controls that will allow for ensuring the implementation adheres to legal requirements. This applies even when engaging with a third party, whereby the operator still is responsible for ensuring that appropriate controls are in place to protect personal data.
One of the first steps in any Smart Grid deployment is to ask the question whether the system being deployed processes any personal data. This forms part of the necessity test when determining whether an impact assessment is indeed required. Although there are likely to be numerous definitions of the term “process,” broadly speaking this should include any actions related to the collection, storage, retrieval, communication, or modification of personal data. According to the Article 29 opinion on smart metering, “it is established that the Directive 95/46/EC places obligations on the data controller with regard to their processing of personal data.” In a smart metering/grid context, there is recognition that there are likely many organizations that can take on the role as the “data controller,” but once it has been determined the role of the controller has been assigned, they are bound by the legal requirements of the appropriate Data Protection Authority.
Upon completion of the necessity test, it is then necessary to undertake an exercise to consider the privacy risks to the data subject. We had earlier cited some examples of potential risks, for example, the profiling of data subjects based on the analysis of their energy consumption. To support the risk management process, other factors may want to be considered, such as the potential impact from the risk being realized, as well as the probability of the impact occurring in the first place. These are important fields as part of the overall process because it does allow for the prioritization of any remedial actions.
Upon the identification of any risks, a management exercise is undertaken to consider the steps taken to manage them based on the priorities. There exist a series of options:
- Risk Acceptance: The overall risk owner of the system accepts the risk as it is.
- Risk Transfer: The identified risks are transferred to a third party.
- Risk Mitigation/Reduction: An exercise is undertaken to identify potential controls that can reduce the identified risks to an acceptable level.
- Risk Avoidance: The risk owner decides not to implement the system and therefore avoids the potential for the risk to be realized entirely.
As detailed earlier, one of the objectives of the PIA is to demonstrate that due diligence has been undertaken regarding the processing of personal data. Therefore,itwill be necessary to present more information than simply presenting risks, and the management actions as follows:
- Overall Risk owner: The individual accountable for the presentation of the assessment.
- Justification: Outline the reasons for the decision to undertake the risk management process.
- Date: When the assessment was approved.
- External Review: Any details of this document being reviewed (with comments) from third-party review. This may include the Data Protection Authority (DPA).
Upon completion of the previous process, there may well be some amount of outstanding risk or residual risk. These residual risks are “the risk remaining after the risk treatment.” It is important to monitor and address these residual risks on a regular basis to ensure they do not exceed the risk appetite of the data controller. Upon completion of the impact assessment process, the Smart Grid system should be ready for deployment. The assessment should be signed and presented to the Data Protection Officer (DPO) and regularly reviewed.
While we have regularly referred to the grid operator being responsible for carrying out the impact assessment, there are many other stakeholders within the Smart Grid that are likely to have the obligation for conducting such assessments. One such example may well be the operators of charging stations for electric vehicles. This is because in this example, there will be personal information that will be captured for the purposes of charging. The vehicle itself will initially identify itself with the charging station, which in turn will calculate the parameters for the requested charge and submit that to the distribution or sub-distribution system operator. This will lead to the development of the charge plan, although it is worth noting that the charge station operator may calculate the charge plan and send this to the distribution operator. This process does require specific personal details, for example, the charge operator requires electric vehicle information such as the requested amount of energy, when the vehicle intends to depart, and the state of the battery. In addition, there will be customer-specific information that is also likely to be processed, this will include customer name, address, and possible financial information to determine how the charge plan will be paid for. Such information is relevant to determine the charge plan that may/may not be accepted by the distribution operator. Using this very high-level and simplistic example, the privacy risks to the electric vehicle driver are that it will be possible to uniquely identify the vehicle owner where they are physically located and their intended departure time at a minimum.
There is no suggestion that the PIA, or even a DPIA for that matter will eliminate risks. Also, as we experience the proliferation of smart meters in our homes, it is also more than likely that considerable research will be conducted to determine what additional information can be garnered. Just as we saw with the earlier example with the ability to detect what movie you may be watching, there are likely to be equally surprising results in the future. It is therefore imperative that not only security and privacy controls built from design, but that privacy assessments are conducted regularly to keep up with the evolving threat landscape, and research activities. There is real concern from consumers about smart meters, with some individuals taking very severe actions to stop meters being installed on their homes. For example,15 Thelma Taormina recently posted signs on her home that read, “No smart meters are to be installed on this property.” When a center point energy worker ignored this advice attempting to replace her old electricity meter, Taormina drew here gun on the individual demanding they leave the property. She later commented,
“Our constitution allows us not to have that kind of intrusion on our personal privacy. They’ll be able to tell if you are running your computer, air conditioner, whatever it is.”
Consumers are clearly, and based on recent research quite rightly very concerned about the privacy implications associated with smart meters. Be under no illusion, failure to protect our personal data, and behavioral data has the ability to not only slow down meter deployments but also possibly stop the rollout altogether.
References
1. Williams Diarmaid, Power Engineering International. European data watchdog puts spotlight on smart meters [document on the Internet]; July 2012. <http://www.powerengineeringint.com/articles/2012/07/european-data-watchdog-puts-spotlight-on-smart-meters.html> [cited July 2012].
2. Vijayan Jaikumar, Computer world. Energy department warns over Smart Grid privacy [document on the Internet]; October 2010. <http://www.computerworld.com/s/article/9191220/Energy_Department_warns_over_smart_grid_privacy> [cited July 2012].
3. Information Commissioner’s Office, Key Definitions—guide to data protection [document on the Internet]; <http://www.ico.gov.uk/for_organisations/data_protection/the_guide/key_definitions.aspx> [cited July 2012].
4. Scott Mark, Bloomberg BusinessWeek. How Italy beat the world to a smarter grid [document on the Internet]; November 2009. <http://www.businessweek.com/globalbiz/content/nov2009/gb20091116_319929.htm> [cited July 2012].
5. “NISTIR 7628 Guidelines for smart grid cyber security: Vol. 2, Privacy and the smart grid [document on the Internet]; <http://csrc.nist.gov/publications/nistir/ir7628/nistir-7628_vol2.pdf> [cited July 2012].
6. Narciso Dean. The Columbus dispatch. Police seek utility data for homes of marijuana-growing suspects [document on the Internet]; February 2011. <http://www.dispatch.com/content/stories/local/2011/02/28/police-suspecting-home-pot-growing-get-power-use-data.html> [cited July 2012].
7. IT Law Wiki. Smart Grid privacy considerations. <http://itlaw.wikia.com/wiki/Smart_Grid_-_Privacy_Considerations#cite_note-5> [cited July 2012].
8. Sonia McNeill. Harvard J Law Technol. 2011;25 Privacy and the modern grid [document on the Internet]; Fall 2011. <http://jolt.law.harvard.edu/articles/pdf/v25/25HarvJLTech199.pdf> [cited July 2012].
9. Information and Privacy Commissioner, Ontario, Canada. Smart privacy for the Smart Grid: embedding privacy into the design of electricity conservation [document on the Internet]; November 2009. <http://www.ipc.on.ca/images/resources/pbd-smartpriv-smartgrid.pdf> [cited July 2012].
10. Article 29 Data protection working party opinion on smart metering [document on the Internet]; December 2011. <http://idpc.gov.mt/dbfile.aspx/WP_183.pdf> [cited August 2012].
11. Fehrenbacher Katie. Gigaom. Big data meets the Smart Grid [document on the Internet]; August 2011. <http://gigaom.com/cleantech/big-data-meets-the-smart-grid/> [cited August 2012].
12. Duhigg Charles. NY Times. How companies learn your secrets [document on the Internet]; February 2012. <http://www.nytimes.com/2012/02/19/magazine/shopping-habits.html?pagewanted=1&_r=1&hp> [cited August 2012].
13. Wisniewski Chester. Naked security. Smart hacking for privacy [document on the Internet]; January 2012. <http://nakedsecurity.sophos.com/2012/01/08/28c3-smart-meter-hacking-can-disclose-which-tv-shows-and-movies-you-watch/> [cited August 2012].
14. Information Commissioner’s Office. Privacy impact assessment handbook [document on the Internet]. <http://www.ico.gov.uk/upload/documents/pia_handbook_html_v2/html/1-Chap1-2.html> [cited July 2012].
15. Sodahead.com. Woman pulls gun to prevent smart meter installation [document on the Internet]; July 2012. <http://www.sodahead.com/united-states/woman-pulls-gun-to-prevent-smart-meter-installation/question-2816327/?page=5&postId=89495167#post_89495167> [cited August 2012].