Integration with other data and systems
Introduction
As the new generation of Information Technology is progressing at a rapid pace, with big data establishing a trend in organisations, integration between systems becomes substantial. In this chapter, we particularly look at information security as a system that has become an essential part of Business Intelligence (BI). BI systems represent one type of decision support system (DSS) with a focus on data analysing and presenting actionable information to decision-makers in an accessible and visual manner (Watson and Wixom, 2007). The way business information is presented and delivered through BI (Watson, 2009) can provide support to employees’ decision-making processes (Kowalczyk and Buxmann, 2014; Popovič et al., 2012) and affect organisational knowledge (Shollo and Galliers, 2015). In recent years, BI has been integrated aggressively in many different industries (Arnott and Pervan, 2008), including retail, telecommunication, healthcare, transportation and financial services (Chaudhuri et al., 2011). The rapid growth of mobile computing (Arnott and Pervan, 2014; Hosack et al., 2012) is challenging and changing the BI field (Watson, 2009). Mobile technologies extend BI usage scenario beyond users’ office desks and hours, giving rise to an extension of BI, coined as mobile business intelligence (m-BI). m-BI is defined as “data-driven decision support applications on mobile devices like smartphones and tablet computers” (Power, 2013, p. 6).
Even though the 2000’s denoted the first implementations of m-BI in organisations, m-BI only became popular after 2010, the year the iPad was released (Tona and Carlsson, 2013). m-BI grew in parallel with other innovative developments in this decade, which Wired refers to as mega-heist (Poulsen, 2009). This period is characterised as the decade run by underground marketplaces specialised on stealing data worth billions and causing significant impact in terms of damaging individuals, organisations, countries and the global economy. Thus, despite transforming the way organisations operate, technical revolutions can also jeopardise the security of resources, thus becoming one of the biggest threats among organisations (Njenga and Brown, 2012).
Because of the high loss and theft rate of mobile devices compared to others, namely laptops (Miller et al., 2012), m-BI use entails a higher risk of exposing organisational information. Additionally, organisations have very limited control on the information residing on mobile devices that are owned and used on a daily basis by employees (Miller et al., 2012). Under these circumstances, organisations need to acquire a robust embedded secure system within a m-BI system and create an intelligent secure environment (Chen et al., 2012) that accounts for the past, present and future threats and attacks that can occur in both, hard technical forms and soft policy violation forms. Security in a m-BI system – which represents a relationship of hardware and software, e.g. mobile devices and software that runs on the mobile device – is conceived not only as a technical dilemma alone, but also as a system that reacts proactively to prevent it from the vulnerability of unwanted data exposure.
In general, 30% of security breaches are attributed to technical cracks (Crossler et al., 2013), whereas 70% derive from the employees’ intentional and unintentional violation with security policies (Vance and Siponen, 2012). To respond to security threats, organisations actively implement information security measures that typically focus on protecting confidential information, ensuring security systems in the device is up-to-date, are wary of suspicious messages, emails and similar, and store confidential information on servers. Yet, security breaches as a result of human factor continue to spread (Crossler et al., 2013). This calls for a broader perspective of information security by defining it not only in technical terms but also in human resources terms (Furnell and Clarke, 2012), such as from a strategic organisational perspective on awareness of information security among employees (Bulgurcu et al., 2010; Hu et al., 2011).
Despite evidence indicating that employees can be controlled if security countermeasures are put into place and integrated in line with security standards (Humaidi and Balakrishnan, 2013), little is known how these security measures affect the potential benefits or outcomes of IT systems and more specifically of a m-BI system. This chapter examines the information security measures of m-BI from two main perspectives: organisations as m-BI providers and organisations as m-BI users. Furthermore, the influence of these information security measures on the desired outcome is explored. This chapter, therefore, represents an investigation into information security measures of a m-BI system. Even though published reports in trade press such as TechTarget (n.d.) and Microsoft (n.d.) discuss m-BI security at a general level, they fail to provide an understanding of what information security measures mean to be integrated within a m-BI system to the actual users versus providers. We now present some literature on m-BI and information security and this is followed by a brief description of our research method and our findings. We conclude with a discussion and conclusion.
Mobile business intelligence
Mobile business intelligence emerged as an extension of BI mainly due to the advancements of mobile technologies (Watson, 2009). In terms of technology enhancement compared to BI, m-BI runs on relatively small and lightweight devices (Gao, 2013), making them highly portable (Liang et al., 2007; Cousins and Robey, 2015). Because of the extreme popularity of mobile technologies (Sheng et al., 2005) and the new employee-driven IT revolution taking place (Harris et al., 2012), organisations are taking initiatives such as bring your own device (BYOD) to enable employees to use their mobile devices for both personal and work purposes (Cousins and Robey, 2015; Andriole, 2012). Accessing information just in time and from anywhere (Perry et al., 2001) increases employees’ sense of freedom and flexibility (Sarker and Wells, 2003) which in turn leads to higher m-BI usage rates (Sarker and Wells, 2003).
Mobile business intelligence extends further users’ availability and accessibility as it relies on mobile technologies (Palen, 2002; Yuan et al., 2010). Thus, by supporting employees’ flexibility, it offers a competitive advantage to organisations that operate in an increasingly fast-paced environment by making decisions “on the move” (Tona and Carlsson, 2013; Wen et al., 2008). With this advancement in place, m-BI contributes to increased decision-making speed (Wen et al., 2008) and enhanced work flexibility (Sheng et al., 2005). From a business perspective, better and quicker decision-making, instant data delivery, improved customer service, realtime monitoring and higher employee productivity are some of the promised benefits expected from m-BI use (Tona and Carlsson, 2013). Yet, how these benefits can be comprised when organisations implement different security measures to address information security is not completely understood.
Information security
Among the many troubling problems that keep organisations alert, lack of information security in sensitive environments tops the list (Schneier, 2012). Even when peaking with innovation and success, organisations struggled to retain and integrate information security into their existing systems due to the risks of unexpected insider or outsider attacks, intentionally or unintentionally (Siponen and Vance, 2014). To this end, organisations develop technological means and security strategies to protect their most valuable resources as a response to threats that often come without notice.
Security represents a duality aspect:
… on the one side, security has to face the incident issue. That is, those events that are produced by unpredictable users’ behaviour due to both the nature of technology under examination, and the possibility of unforeseen practices. On the other side, security is constituted by a protection system against predictable threats, breakdowns and other problems that can be recurrent or identifiable.
Spagnoletti and Resca, 2008
Departing from this security duality aspect and borrowing from Bulgurcu et al., (2010) we conceptualise at an organisational level two main concepts to denote the duality view of security and its integration on a m-BI system from an organisational perspective:
• Safety of resources – is a security state in which an organisation perceives its technology, such as m-BI, is safeguarded from security threats.
• Vulnerability of resources – is a security state in which an organisation perceives its technology, such as m-BI, increases the risk of security threats.
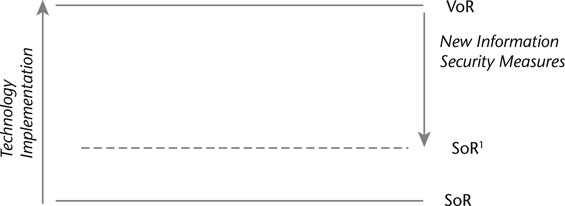
We build our framework based on the concepts of safety of resources (SoR) and vulnerability of resources (VoR) in order to understand the security state in which a m-BI system positions an organisation. Theorising about this, we argue that before implementing a new technology such as m-BI, an organisation perceives to be at the safety of resources state. If the implemented technology threatens to expose sensitive information, the organisation realises that it has shifted to another state, namely vulnerability of resources. Consequently, the current security state can prompt an organisation to take further measures in the form of information security measures. Through implementing information security measures, organisations reduce the risk of attacks and threats (Merete Hagan et al., 2008) and consequently aim to reach the safety of resources state. We portray this in Figure 19.1 overleaf.
On the one hand, organisations as providers, who are responsible for developing a m-BI system, are prone to perceive that their system guarantees an integration of safety of resources, whereas on the other hand, organisations that utilise a m-BI system are prone to perceive that the offered system shifts to a state of vulnerability of resources, keeping them more insecure about the resources that it holds. While such a perspective on information security is broad, we utilise this standpoint to tackle a contextual problem that focuses on the information security measures, which may affect organisations’ use of a system and how the security systems are integrated with that particular system.
Figure 19.1 Shifting between the states SoR (safety of resources) and VoR (vulnerability of resources)
Methodology
To explore how the potential outcomes of a m-BI system are affected by information security measures, 11 interviews have been conducted (as shown in Table 19.1) with two main groups: organisations that have implemented and use m-BI (Organisation 1–Organisation 5) and providers that design, build and support m-BI implementation (Provider 1–Provider 6). The majority of interviews have been contacted through a professional social network – LinkedIn – and due to interviewees’ different locations, the interviews, with the exception of one (Provider 2), were conducted using Skype. Semi-structured interviews were used as they made it possible to adjust questions and alter an interview sequence as the interview unfolded. The interviews lasted for approximately 30–60 minutes and were recorded with the interviewees’ consent.
Following interview transcription, the text-based content was uploaded into NVivo for further analysis. Considering that our empirical data focused on two types of organisations, we categorised them as users and providers. First, the interviews were coded at a descriptive level such as m-BI benefits, security, m-BI use and m-BI interpretation. Since the focus of this research is on security, we developed a second round of coding by identifying etic codes and nesting them within the general codes, which were more specific to the cases (Miles and Huberman, 1994) such as data aggregation, encryption and authentication. We identified that some patterns – in terms of information security measures – that were common across users and providers corresponded with International Organization for Standardization (ISO) best practices, such as protecting confidential/sensitive information, making sure that the security system in the device is up-to-date and storing confidential information on servers only. Thus, at a certain point there is an alignment between users and providers in terms of information security measures. Yet, additional information security measures were identified in users that were absent from a provider perspective.
Table 19.1 List of interviewees
Type of Organisation |
Cases |
Industry |
Location |
Organisations that have implemented and use m-BI |
User 1 |
Consulting |
Nashville, TN, US |
User 2 |
Retail |
Netherlands |
|
User 3 |
Non-Profit Organisation |
Florida, US |
|
User 4 |
Healthcare |
UK |
|
User 5 |
Retail |
Sweden |
|
Organisations that have designed, built and supported m-BI |
Provider 1 |
Vendor |
San Francisco, US |
Provider 2 |
Vendor |
Lund, Sweden |
|
Provider 3 |
Vendor |
Naperville, IL, US |
|
Provider 4 |
Vendor |
Seattle, WA, US |
|
Provider 5 |
Vendor |
Pleasanton, CA, US |
|
Provider 6 |
Vendor |
Melbourne, Australia |
Findings
Motivated by a lack of knowledge on how information security measures can have an impact on m-BI benefits, we set out to identify the information security measures from both a user and provider’s perspective. From our empirical material, we derive that providers perceive m-BI within the boundaries of safety of resources once technical concerns have been addressed appropriately, whereas users feel more vulnerable in utilising m-BI within their organisations setting. For this reason, the latter embrace a more data-centric focus and tend to increase the security measures already in place by the vendors. This section highlights the main information security measures that users and providers consider in regard to m-BI.
Users
In addition to the security provided by vendors, organisations take extra information security measures to feel they have a safety of resources state. In one instance, especially on sensitive information, organisations aggregated the data at a higher level before delivering it to users on their mobile devices:
So, we are not allowed to personally identify any child. If there is a child in a small area, and you say “aha I know that child is there” we cannot show that we have to have a bigger area. We say we’re [going to] go from this tiny area to a larger area so that there’s more kids, so we can’t identify those children … Security is just a huge deal for us. So, instead of dealing with it technologically, we deal with that through business processes to make sure that things shouldn’t go out. The data is presented in a way that allows our staff to put it in a special format.
User 3
Another strategy used to protect sensitive information is to avoid publishing particular types of data on mobile devices:
Because the devices themselves are not that secured, particularly with the iPads. They are very consumer devices; they are not really up to the enterprise level yet for security. The only thing we can do to prevent unauthorized data to go out is not to publish it.
User 3
It depends on the respective technology, it depends on the tool, it depends on the sensitivity of data. Some of the data sets that we have, for example, for looking at talent information on our people, we don’t allow that to stand on a mobile device.
User 1
Additionally, not having an organisation’s data stored locally reduces the risk of information security threats in case the mobile device is stolen or lost:
As you see here (demonstrating in the screen) you see a “data locally” that we deactivate. So, if a regional manager lost his phone or iPad there is no information locally at that unit. The thief doesn’t get any chance to get information out of it. As soon as you close the app the information is gone.
User 5
It has to be a live connection in order to get access to it.
User 1
Because it was a big shift if the tool was able to run online or offline and actually we said that we will go for an online tool … The thing we run into, is when we tried this, we found out that a lot of our stores are either in a peak department store setting or in a concrete building. No WiFi and 3G. So, actually what happened is well, we have to make screenshots of our reports when we are outside on the street.
User 2
Centralising an information technology system to manage devices remotely makes it possible to wipe everything out once a mobile device is declared lost by its user:
We have the ability to remote our own tables really.
User 4
[S]o, you need a kind of mobile device management tool where you can lock the iPad or the iPhone or you can swipe it or whatever. So, that was one concern from IT.
User 2
Providers
From a provider point of view, when it comes to information security, this is perceived purely from a technical perspective. For example, one technical solution is to secure information security by authentication algorithms:
And so far, we haven’t had any problems for two reasons: (1) We support all the authentication methods which are widely deployed like HTML. On top of that, when we communicate with the server we communicate over securely which is secure industry level authentication mechanisms, so it is not open.
Provider 2
[I]n most cases, all the authentication that is expected, either at the data level or application level, are still applied.
Provider 4
We are a server-based application. Even on a native application you have to authenticate every time you want to view or run a report or dashboard.
Provider 1
From an application point of view is when you’ve got a username and password, which is utilized for the mobile device and you can put your credentials at this level of app. You have the ability with the application to either ask you every time to log on, or have your credentials stored on the device.
Provider 6
Encryption also makes it possible that the information is securely transmitted and cannot be read by other parties:
In a web environment, in a mobile environment there are standard encryptions in different process across the communication path. One of the things we do in ensuring security in the web environment is to have https. We also did our native encryption algorithm. So, standard public encryption mechanism plus proprietary one side to another side, end to end encryption that’s the way we provide so far.
Provider 3
We just rely on the traditional encryption technology, so if you’re connecting from your device to a server, and to make sure that the path of the data from the server to the device going back and forth encrypted using standard https.
Provider 1
Another provider quoted below uses the security infrastructure that the company has already in place:
That means, because we are a web-server based application, at least behind the firewall, it’s sort like an intranet site to our customers and so whatever they already do to allow people never to access from their mobile device and that can be done in a hundred different ways and it can be really strict at some companies and that can be really relaxed at some companies, it doesn’t matter to us.
Provider 5
Discussion
Through a dual view of security, i.e. security of resources and vulnerability of resources, our findings suggest a clear contrast in terms of how two types of organisations (organisations as users versus organisations as providers) view the way security is integrated within a m-BI context.
Organisations as users view m-BI as a system that increases the risk of security threats, i.e. vulnerability of resources. Consequently, vulnerability of resources increases their awareness of tackling security issues in a stricter manner. To this end, users apply a data-centric lens to their information security measures in order to reduce the risk of exposing sensitive information, e.g. by aggregating sensitive information at a higher level or deciding not to publish any sensitive data. On the contrary, organisations as providers of a m-BI perceive m-BI safeguarded when free from security threats, i.e. safety of resources is in place. They perceive a user to be at the safety of resources state with m-BI once technical concerns have been handled appropriately, such as secure encryption methods and authentication algorithms. One possible reason for this discrepancy is the fact that it is typical for a provider to have a more technical-driven approach on how to integrate security into a new technological system against potential threats and attacks. There is a lack of data-driven focus in terms of information security measures as providers have a knowledge gap on the nature of data (such as degree of sensitivity) within an organisation. In contrary, it is typical for an organisation as a user to perceive the vulnerability of resources when implementing m-BI. This tightly connects to the high possibilities of theft and loss of mobile devices (Miller et al., 2012) and the sensitivity of the data that they store.
Figure 19.2 Users versus providers
Not surprisingly, in addition to the technical measures secured by providers, organisations as users integrate additional information security measures when it comes to their data sensitivity, to make sure they reach the state of security of resources. The higher the data sensitivity is, the more actions an organisation will take to feel secured against the threats. However, the findings show that information security measures may jeopardise m-BI benefits depending on the level of data sensitivity. Notably, the more sensitive the data are, the less benefits m-BI will generate in an organisational context. Seen from a dual organisational perspective (organisations as users and providers) Figure 19.2 depicts our ideas on how the level of data sensitivity and the information security measures taken from a user perspective affect the m-BI benefits.
As the main benefits of m-BI rely on delivering up-to-date information anytime and anywhere to users (Tona and Carlsson, 2013), we argue that the information security measures integrated in organisations’ technological systems may have an effect on the potential m-BI benefits. The providers offer their m-BI solution once it is protected through encryption and authentication algorithms regardless of data sensitivity. Afterwards, when the solution is acquired by the user both parties may agree not to store data locally, that is why “no data stored locally” is seen as a common point of view between users and providers. Later, users reflect upon the vulnerability of resources from a data-centric standpoint.
To illustrate our ideas further, an organisation decides to protect its sensitive information by aggregating data at a higher level and in doing so, reduces the risk of exposing data specifics such as individual details. However, providing aggregated information to users who are on the go, limits their promised capability of identifying a specific problem just in time. This is due to the fact that they are not able to drill down to lower levels of information to make better sense of what is happening (Tona and Carlsson, 2013), and therefore will not be able to take actions just in time. Deciding not to publish at all the sensitive information can be regarded as a drastic measure in relation to m-BI benefits. This threatens one of the core fundamentals of m-BI benefits in accessing the right information just in time regardless of a user’s location (Tona and Carlsson, 2013; Watson, 2015). Again, in this case, an additional information security measure reduces the m-BI benefits. From a providers’ perspective, m-BI will be able to provide potential benefits as long as encryption and authorisation are in place, with the result that providers can guarantee to some extent safety of resources – something users strive for along with the promised m-BI benefits.
Our findings are not free of limitations. While it is possible to generalise to other technologies, our findings should be cautiously interpreted, unless additional data collection of this nature takes place. Gaining first-hand experience, e.g. during the implementation phase and the actual use phase, might bring complementary views on safety of resources versus vulnerability of resources.
Conclusion
In this chapter, we have suggested that information security measures are implemented and integrated into the m-BI system both from the providers’ (integrated in the product) and organisations’ perspectives (integrated by policies and rules). Organisations that have implemented m-BI take a more data-centric strategy to protect their information (such as higher data aggregation, no publishing of sensitive data and no local data). Whereas providers embrace a more technical perspective to make sure that their customers’ resources are protected from external security threats (such as authentication algorithms and encryption), aspects that users often disregard.
We rationalised our findings by portraying that safety of resources versus vulnerability of resources depends on the level of data sensitivity. A higher level of data sensitivity will prompt organisations to cautiously consider new information security measures. Therefore, if an organisation perceives itself to be positioned at a level of vulnerability of resources as a result of a new technology, it will implement new information security measures as a means to move towards a new level of safety of resources. However, organisations should be careful when considering new information security measures because of the high risk that m-BI benefits, which they expect to obtain, can be reduced.
References
Andriole, S. J. (2012). Seven indisputable technology trends that will define 2015. Communications of the Association for Information Systems, 30(4), 61–72.
Arnott, D. and Pervan, G. (2008). Eight key issues for the decision support systems discipline. Decision Support Systems, 44(3), 657–672.
Arnott, D. and Pervan, G. (2014). A critical analysis of decision support systems research revisited: the rise of design science. Journal of Information Technology, 29(4), 269–293.
Bulgurcu, B., Cavusoglu, H. and Benbasat, I. (2010). Information security policy compliance: an empirical study of rationality-based beliefs and information security awareness. MIS Quarterly, 34(3), 523–548.
Chaudhuri, S., Dayal, U. and Narasayya, V. (2011). An overview of business intelligence technology. Communications of the ACM, 54(8), 88–98.
Chen, H., Chiang, R. H. and Storey, V. C. (2012). Business intelligence and analytics: from big data to big impact. MIS Quarterly, 36(4).
Cousins, K. and Robey, D. (2015). Managing work–life boundaries with mobile technologies. Information Technology and People, 28(1), 34–71.
Crossler, R. E., Johnston, A. C., Lowry, P. B., Hu, Q., Warkentin, M. and Baskerville, R. (2013). Future directions for behavioral information security research. Computers and Security, 32, 90–101.
Furnell, S. and Clarke, N. (2012). Power to the people? the evolving recognition of human aspects of security. Computers and Security, 31(8), 983–988.
Gao, S. (2013). Mobile decision support systems research: a literature analysis. Journal of Decision Systems, 22(1), 10–27.
Harris, J., Ives, B. and Junglas, I. (2012). IT consumerization: when gadgets turn into enterprise IT tools. MIS Quarterly Executive, 11(3), 99–112.
Hosack, B., Hall, D., Paradice, D. and Courtney, J. (2012). A look toward the future: decision support systems research is alive and well. Journal of the Association for Information Systems, 13(5), 315–340.
Hu, Q., Xu, Z., Dinev, T. and Ling, H. (2011). Does deterrence work in reducing information security policy abuse by employees? Communications of the ACM, 54(6), 54–60.
Humaidi, N. and Balakrishnan, V. (2013). Exploratory factor analysis of user’s compliance behaviour towards health information system’s security. Journal of Health and Medical Informatics, 4(2), 2–9.
Kowalczyk, M. and Buxmann, P. (2014). Big data and information processing in organizational decision processes. Business & Information Systems Engineering, 6(5), 267–278.
Liang, T.-P., Huang, C.-W., Yeh, Y.-H. and Lin, B. (2007). Adoption of mobile technology in business: a fit-viability model. Industrial Management and Data Systems, 107(8), 1154–1169.
Merete Hagen, J., Albrechtsen, E. and Hovden, J. (2008). Implementation and effectiveness of organisational information security measures. Information Management and Computer Security, 16(4), 377–397.
Microsoft. (n.d.). Business Intelligence and security. Retrieved September 19, 2017 from www.microsoft.com/betaexperience/nlarchive/bexp2/issue_6/Business%20Intelligence%20and%20Security.aspx.
Miles, M. B. and Huberman, A. M. (1994). Qualitative Data Analysis: An Expanded Sourcebook. Thousand Oaks, CA: SAGE.
Miller, K. W., Voas, J. and Hurlburt, G. F. (2012). BYOD: security and privacy considerations. It Professional, 14(5), 53–55.
Njenga, K. and Brown, I. (2012). Conceptualising improvisation in information systems security. European Journal of Information Systems, 21(6), 592–607.
Palen, L. (2002). Mobile telephony in a connected life. Communications of the ACM, 45(3), 78–82.
Perry, M., O’Hara, K., Sellen, A., Brown, B. and Harper, R. (2001). Dealing with mobility: understanding access anytime, anywhere. ACM Transactions on Computer-Human Interaction (TOCHI), 8(4), 323–347.
Popovič, A., Hackney, R., Coelho, P. S. and Jaklič, J. (2012). Towards business intelligence systems success: effects of maturity and culture on analytical decision making. Decision Support Systems, 54(1), 729–739.
Poulsen, K. (2009). The decade’s 10 most dastardly cybercrimes. Wired. Retrieved September 19, 2017 from www.wired.com/2009/12/ye_cybercrimes/.
Power, D. J. (2013). Mobile decision support and business intelligence: an overview. Journal of Decision Systems, 22(1), 4–9.
Sarker, S. and Wells, J. D. (2003). Understanding mobile handheld device use and adoption. Communications of the ACM, 46(12), 35–40.
Schneier, B. (2012). Liars and Outliers: Enabling the Trust That Society Needs to Thrive. Hoboken, NJ: John Wiley and Sons.
Sheng, H., Nah, F. F.-H. and Siau, K. (2005). Strategic implications of mobile technology: a case study using value-focused thinking. The Journal of Strategic Information Systems, 14(3), 269–290.
Shollo, A. and Galliers, R. D. (2015). Towards an understanding of the role of Business Intelligence systems in organisational knowing. Information Systems Journal, 26(4), 339–367.
Siponen, M. and Vance, A. (2014). Guidelines for improving the contextual relevance of field surveys: the case of information security policy violations. European Journal of Information Systems, 23(3), 289–305.
Spagnoletti, P. and Resca, A. (2008). The duality of information security management: fighting against predictable and unpredictable threats. Journal of Information System Security, 4(3), 46–62.
TechTarget. (n.d.). Mobile BI tools, trends and best practices guide. Retrieved September 19, 2017 from http://searchbusinessanalytics.techtarget.com/essentialguide/Mobile-BI-tools-trends-and-best-practices-guide.
Tona, O. and Carlsson, S. (2013). The organising vision of mobile business intelligence. Proceedings of the 21st European Conference on Information Systems.
Vance, A. and Siponen, M. T. (2012). IS security policy violations: a rational choice perspective. Journal of Organizational and End User Computing, 24(1), 21–41.
Watson, H. J. (2009). Tutorial: Business Intelligence – past, present, and future. Communications of the Association for Information Systems, 25(1), 487–510.
Watson, H. J. (2015). Tutorial: mobile BI. Communications of the Association for Information Systems, 37(1), 605–629.
Watson, H. J. and Wixom, B. H. (2007). The current state of Business Intelligence. Computer, 40(9), 96–99.
Wen, W., Chen, Y. and Pao, H. (2008). A mobile knowledge management decision support system for automatically conducting an electronic business. Knowledge-Based Systems, 21(7), 540–550.
Yuan, Y., Archer, N., Connelly, C. E. and Zheng, W. (2010). Identifying the ideal fit between mobile work and mobile work support. Information and Management, 47(3), 125–137.