What Is Information Security Governance?
For almost any organization, data is a valuable asset. Yet, over 50 percent of large corporations report that they do not treat data as a business asset.1 An organization must find ways to use its data to meet its business goals, such as providing services to consumers and making a profit. It also must protect its data. This balance is key to an organization’s success. Failing to strike the right balance can harm the organization’s goals. Consider the following:
- An organization cannot market its products without access to customer lists.
- Customers may complain about incorrect electronic data.
- If confidential data is disclosed, an organization faces embarrassment.
An organization’s executive management team is responsible for governing the organization. This means it is also responsible for information security governance (ISG), the executive management team’s responsibility to protect an organization’s information assets. ISG makes protecting information assets a business decision. To do this, an organization must align its information security goals to its business needs. ISG moves information security beyond technical decisions and makes security a strategic decision.
![]() NOTE
NOTE
The security goals of confidentiality, integrity, and availability are called the C-I-A triad or the A-I-C triad.
Organizations use ISG to enhance their business. ISG makes sure that information security concepts are applied in a way that helps meet business goals. ISG also makes sure that there is proper accountability and oversight for meeting these goals. The C-I-A triad appears in FIGURE 13-1.
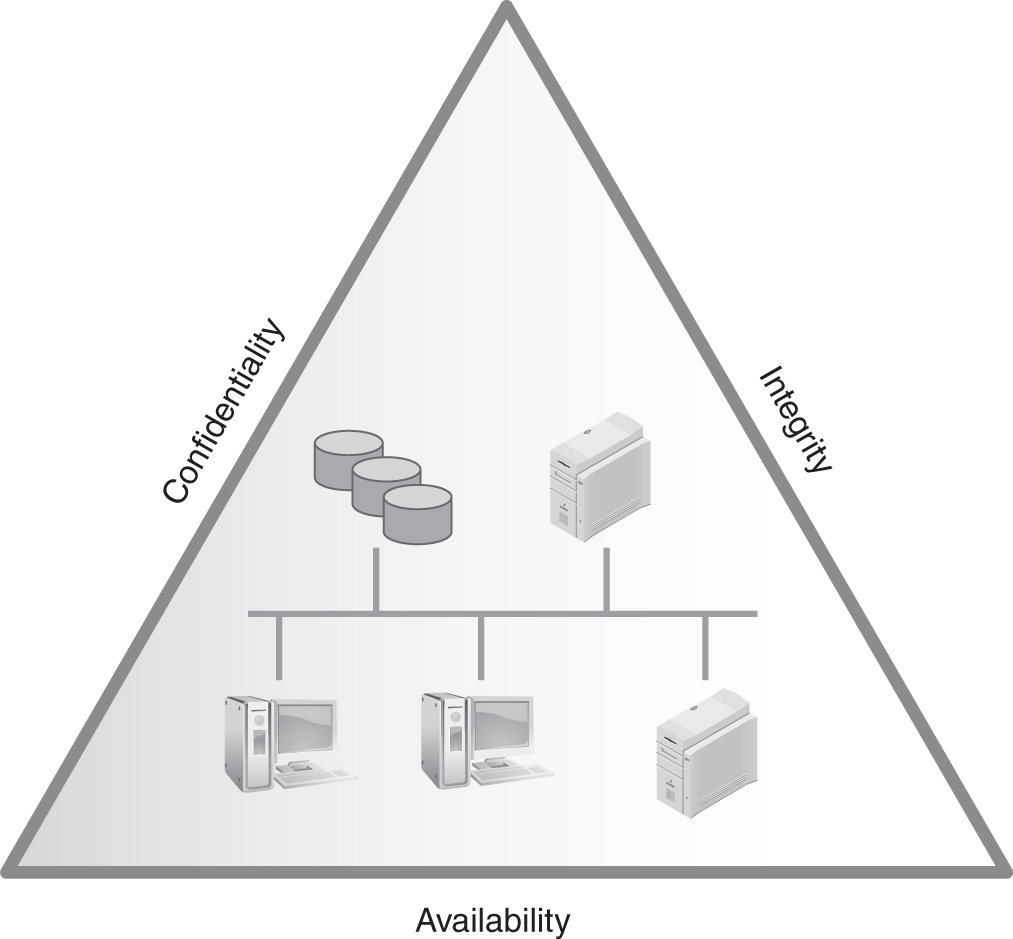
FIGURE 13-1
The C-I-A triad.
Information Security Governance Planning
ISG refers to executive management’s responsibility to provide strategic direction, oversight, and accountability for the security of its data and information technology (IT) resources. Their main duty is to make sure that the information security strategy supports its business goals.
A common business goal is to make a profit. The organization must consider many factors that affect this goal. Business drivers are the forces that influence the organization’s business goals. They can be internal or external and include people, processes, and trends. Common business drivers may include the availability of raw materials and employees, the location of factories, and the costs of transporting products to market.
An organization must balance business drivers to meet its goals. They do this during the business planning process. There are three types of business planning. They are:
- Strategic planning—This is long-term planning. Strategic planning focuses on preparing new approaches and planning for new products, technologies, or processes. It lays the groundwork for new business directions.
- Tactical planning—This is short- to medium-term planning. Tactical planning allows organizations to be responsive to market conditions. It allows them to take advantage of short-term or unexpected opportunities. Tactical plans are usually 6 months or less in length.
- Operational planning—This is day-to-day planning. Operational planning focuses on the normal operations of an organization. It is responsive to daily issues.
FIGURE 13-2 illustrates the different types of business planning.
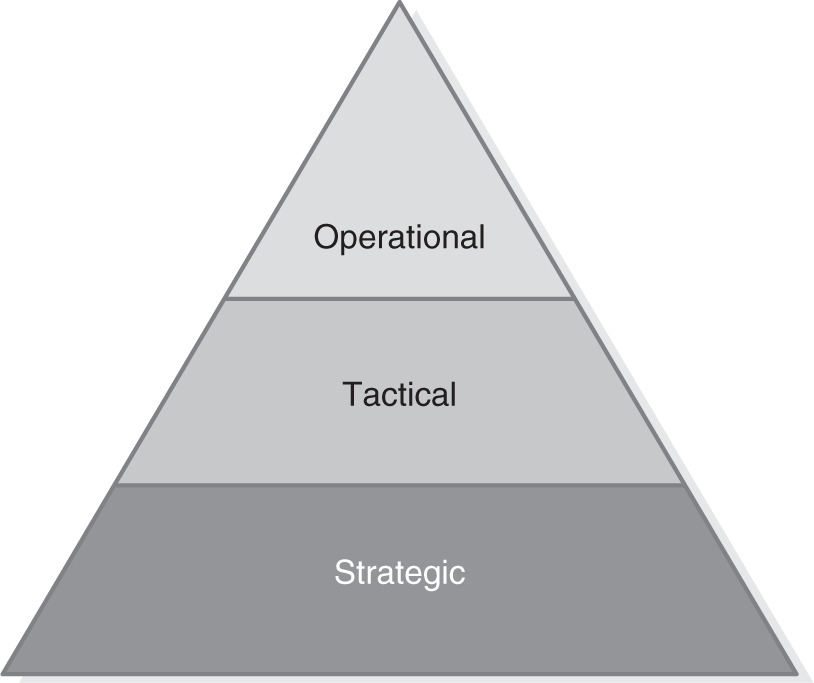
FIGURE 13-2
Business planning hierarchy.
The organization’s executive management team carries out strategic planning. This is when it determines the business’s goals. Once it determines its business goals, it must figure out how information security can help support these goals. It will use the same types of planning strategies to think about information security. This is ISG planning. When planning for information security, the organization must think about:
- Information needs—The organization must ask how it uses data to meet its business goals. It must then think about how information security can support this. For instance, if an organization conducts most of its business on the internet, it may need to focus its attention on techniques to ensure availability and integrity. Its IT systems must hold accurate data and be ready to conduct business.
- Regulatory requirements—The organization must know its regulatory landscape. It must know the data protection laws that it must follow. Often these laws focus on protecting the confidentiality of certain types of data.
- Risk management—The organization must adopt a risk management approach. It must know the information security risks that it faces. It also must prioritize that risk and decide how it will respond to it.
- Security failures—The organization must think about information security failures and how those failures might harm the business. For instance, it must consider the impact of a security breach, malware-infected IT resources, or unavailable data. There are many negative impacts of an information security failure. These include lawsuits and breach notification costs. An organization will certainly lose customers after an information security incident. This affects its bottom line.
![]() NOTE
NOTE
A 2019 survey found the average organizational cost of a data breach in the United States is almost $4 million.2
An organization answers these questions to determine ISG strategic direction. It makes sure that its information security goals support its business objectives. This is the role of ISG.
Common Information Security Governance Roles
It is important to know who makes information security decisions, whether they are strategic, tactical, or operational. Not every organization has the same structure. Organizations can have different legal forms, such as corporations, partnerships, or limited liability companies. These legal forms are governed by state law. This section reviews ISG roles. You will be more likely to find the roles described here in larger organizations, such as corporations. Smaller organizations may not fill all of these roles; rather, they may combine many duties within one role. Nonprofit and educational organizations may also have different roles for people. These organizations tend to have structures with many shared responsibilities.
Many different roles can make decisions about information security. The typical ISG roles are:
- Board of directors
- Chief information officer
- Chief information security officer
- Information security managers
The board of directors (BOD), an organization’s top governance group, runs the organization. A BOD is required by law to act with due care. It must make all of its decisions in the best interests of the organization. The BOD plans an organization’s strategic direction and determines its business goals. It makes sure that an organization uses its resources effectively to meet these goals. Finally, it makes sure that an organization acts legally. If an organization does not have a BOD, then its top-ranking executive group performs these duties.
The BOD determines how information security will reduce risk and support business goals through strategic planning. The BOD issues high-level information security policies and delegates tactical and operational activities to other senior managers. The main duty of a BOD is governance for the organization and for information security.
The chief information officer (CIO) is the organization’s senior IT official. The CIO focuses on strategic IT issues and defines the organization’s IT mission. It is the CIO’s job to keep the BOD advised about IT issues. CIOs are not usually involved in day-to-day IT operations. Their duties are strategic and tactical in nature. They often delegate responsibility for information security management (ISM) to a CISO.
A CIO is not the same as a chief technology officer (CTO). A CIO is responsible for a company’s internal IT systems and focuses on the systems used to run the organization’s business. A CIO tends to be internally focused. In contrast, a CTO develops a company’s technology products. These are the products that the company delivers to its customers. A CTO tends to be externally focused.
The chief information security officer (CISO) is the organization’s senior information security official. The role of the CISO is relatively new and continues to evolve. Depending on an organization’s structure, the CISO might report to the CIO. A CISO also could report to the organization’s chief financial officer (CFO). CISOs are responsible for an organization’s information security strategy. They also are very involved in tactical planning. However, they are not generally involved in daily IT operations.
The CISO makes sure that the CIO and BOD understand information security threats and how to respond to those threats. The CISO may make information security policy suggestions to the BOD. A CISO also helps determine information security safeguards, and usually delegates functional and operational tasks to other managers.
![]() NOTE
NOTE
In March 2009, U.S. President Barack Obama appointed the first federal CIO, who was responsible for government IT spending.
Information security managers are responsible for the functional management of an organization’s information security program. They manage the operational activities and implement the controls specified by the CISO. These managers might also:
- Create information security standards, guidelines, and procedures
- Participate in risk assessments
- Manage the security infrastructure
These roles work together. The higher-level roles make governance decisions, whereas the lower-level roles are responsible for carrying out ISM and operational activities.
Information Security Governance and Management
ISG and ISM are not the same thing. Although the terms are often used interchangeably, the distinction is subtle. You should keep in mind that sometimes the difference is not clear. Many organizations use one or both terms to refer to all ISG and ISM activities. Many activities have both ISG and ISM elements.
ISG, which is handled by the BOD, CIO, and CISO, makes sure that security is used to support business goals. It offers a process for oversight and accountability and makes sure that there is a structure in place to direct information security activities.
Creating an Information Security Governance Program
There are many resources available to help organizations create an ISG program. The International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC) have created a comprehensive standard to help guide this process.3 The standard uses the term ISM system to refer to both ISG and ISM activities.
The standard helps organizations create an ISM system by using a risk-based approach. It reviews how to operate, monitor, review, maintain, and improve the ISM system. It walks through each step and outlines the processes that an organization must consider at each step.
Any organization can use this standard, as it is designed to be flexible to meet an organization’s needs. It can be especially helpful to organizations that have never managed information security on a strategic level. It is also designed to work with the ISO/IEC security controls standard called “ISO/IEC 27002:2013, Information Technology—Security Techniques—Code of Practice for Information Security Controls.”
Organizations must review their ISM systems regularly. They need to know if their ISM controls are improving security. To do this, they must measure their effectiveness. The ISO/IEC has guidance on this as well. That document is titled “ISO/IEC 27004:2016 Information Technology—Security Techniques—Information Security Management—Monitoring, Measurement, Analysis, and Evaluation.”
This standard helps organizations review their ISM system. It helps organizations create control measurements and analyze the measurements. The process helps organizations decide if their policies or controls need to be changed.
ISM, the organization’s day-to-day security operations, is the visible part of ISG activities. It makes sure that ISG policies are put into practice. ISM maintains the organization’s overall security posture. ISG states what that posture must be. TABLE 13-1 compares ISG and ISM.
TABLE 13-1 Comparison of Information Security Governance and Information Security Management
| INFORMATION SECURITY GOVERNANCE | INFORMATION SECURITY MANAGEMENT |
|---|---|
Strategic and tactical |
Tactical and operational |
Creates policies and strategy |
Implements policies and strategy |
Ultimate compliance authority and oversight |
Day-to-day management and authority |
BOD, CIO, CISO |
CISO and information security managers |
Information Security Governance in the Federal Government
Congress created the Federal Information Security Management Act (FISMA) to protect federal data and IT resources.4 Federal agencies fall under the executive branch of the U.S. government and report to the president of the United States. U.S. federal agencies must comply with FISMA.
FISMA requires each federal agency to develop an information security program and name a CISO to lead the program. The program must assess the agency’s information security risk, include plans to reduce that risk, and provide security awareness and training activities to employees. Agencies must report on their FISMA compliance progress each year. They send these reports to the Government Accountability Office (GAO).
![]() NOTE
NOTE
You can view the GAO high-risk website at https://www.gao.gov/highrisk/overview.
Information security is a high priority for the federal government. Since 1997, the GAO has included protecting the nation’s information systems and cyber critical infrastructure on its “high risk list.” Issues are high-risk if they are vulnerable to fraud, waste, abuse, or mismanagement. The GAO publishes the list every 2 years.5
