Chapter 6
Cloud Security
Almost every modern organization uses the cloud as part of their technology infrastructure to some extent. Some have abandoned their datacenters and shifted technology operations entirely to the cloud. Others are “cloud native” organizations that began in the cloud as start-ups and never operated their own physical IT infrastructure. Those who haven't made this type of large-scale shift likely use at least one software-as-a-service (SaaS) offering for email, calendaring, customer relationship management, videoconferencing, or other critical tasks. The widespread adoption of cloud computing dramatically impacts the work of cybersecurity analysts who must now understand how to gather, correlate, and interpret information coming from many different cloud sources.
Understanding Cloud Environments
Cloud computing is an umbrella term that covers almost any computing service delivered to customers over a network. It encompasses everything from building complete technology infrastructures in Amazon Web Services (AWS) or Microsoft Azure to deploying office productivity tools through Google's G Suite. Although many might define cloud computing as simply delivering computing services over a network, the National Institute of Standards and Technology (NIST) offers a more robust definition:
Cloud computing is a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction.
Take the time to read through that definition carefully. You'll find that it goes far beyond simply defining cloud computing and encompasses many of the characteristics and benefits of the cloud in very concise language. Let's pick apart some of the more critical pieces of this definition:
- Cloud computing is ubiquitous and convenient. It's designed so that customers can quickly and easily request services and have their needs met immediately. Those services are then accessible from anywhere with a network connection.
- The on-demand nature of cloud computing means that customer requests are fulfilled immediately. They don't need to call up the service provider and ask for capacity or request services with a long lead time. From the customer's perspective, there is an essentially infinite pool of resources waiting for their requests made through a self-service portal.
- Cloud computing environments draw on a shared pool of resources. They use an approach called multitenancy where many different customers share access to the same physical resources. The cloud provider is responsible for implementing isolation controls that prevent the actions of one customer from interfering with or accessing data from another customer.
- Cloud environments are highly configurable. The customer can tailor their use of cloud resources to meet their own specific business objectives.
- Cloud resources are not only rapidly provisioned, they can also be rapidly released. When a customer no longer requires a specific cloud resource, they can release that resource and, typically, stop paying for the use of that resource immediately.
- Cloud environments require minimal management effort from the customer. One of the core benefits of the cloud is that customers may transfer many responsibilities from their own IT teams to the cloud provider.
These characteristics broadly describe cloud services. As you will see, the exact implementation of them differs depending on the specific cloud service models and deployment models used by an organization.
The Case for Cloud Computing
Organizations adopting the cloud do so for a wide variety of reasons. They often initiate cloud efforts in response to a specific need but eventually find that they realize many other benefits as well. Some of the core benefits of the cloud include the following:
- Disruptive Innovation Cloud providers can generally develop and/or adopt new technologies at a much faster rate than organizations attempting to build their own infrastructures. After all, providing technology services is their core mission, whereas most organizations leverage technology in pursuit of another mission.
- Agility and Elasticity Cloud operations facilitate agility within the customer's organization. When new IT resources are required, they can be provisioned at a moment's notice. When they are no longer needed, they can be released, stopping the billing clock. This allows developers to experiment with new solutions in a cost-effective and agile fashion.
- Scalability Solutions built on cloud architectures have almost limitless scalability. Computing, storage, and networking resources may be added and removed as needed to meet changing demand. This scalability can be automated to shift dynamically with changing requirements.
- Cost Effectiveness Although it might seem counterintuitive that adding another provider to the mix reduces costs, this is generally the case for most organizations. Cloud providers operate massive datacenters that have an economy of scale that is untouchable by all but the very largest organizations.
- Security Cloud providers dedicate tremendous resources to cybersecurity. Later in this chapter, you'll learn about the shared responsibility model of cloud computing. Under this model, some responsibilities rest with the cloud service provider whereas others remain the responsibility of the customer. Most cloud service providers are able to do far more to meet their responsibilities than is possible for smaller organizations.
Each organization needs to analyze their own business requirements and develop their own justification for the adoption of cloud computing services, but these core benefits exist in almost every environment.
Cloud Service Models
The services offered by cloud providers fit into three cloud service models. Each of these models describes a different level of service delivered through the cloud and creates varying levels of responsibility for both the service provider and the customer.
Software as a Service (SaaS)
Software as a service (SaaS) offerings provide a customer with a complete application that is built and maintained by the service provider and runs in an infrastructure that is either operated or procured by the service provider. The customer of an SaaS offering typically accesses the service through a web browser and performs only limited application configuration. Almost all the responsibility for operating the service rests in the hands of the cloud service provider and, possibly, other cloud service providers who offer the SaaS provider access to underlying infrastructure resources.
Almost every modern organization makes use of at least one SaaS offering, and most organizations rely on a diverse bundle of services that meet a variety of business needs. SaaS offerings provide common productivity applications, such as Google's Gmail (shown in Figure 6.1) and Microsoft's Office 365. Other SaaS providers build industry-specific and function-specific offerings designed to appeal to a specific set of customers. For example, the Slate customer relationship management (CRM) tool, shown in Figure 6.2, is designed specifically for the administration of higher education admissions offices.
Infrastructure as a Service (IaaS)
Infrastructure as a service (IaaS) offerings operate under a very different service model. SaaS offerings endeavor to hide implementation details from the customer, but IaaS offerings expose basic infrastructure building blocks that customers may use to design and implement their own service offerings. These offerings include compute processing, storage, networking, and other basic components of a technology infrastructure.
FIGURE 6.1 Google's Gmail is an example of SaaS computing.
In an IaaS environment, the customer is able to choose and assemble basic cloud offerings to create the services they need to meet their business objectives. In an IaaS environment, the customer retains far more control of the infrastructure than they do in an SaaS environment and, therefore, has greater responsibility for monitoring, management, and security. These customer responsibilities include maintaining and upgrading the operating system as well as software running in the environment. Figure 6.3 shows an example of the AWS dashboard used to manage Elastic Compute Cloud (EC2) server instances.
IaaS cloud providers retain responsibility for maintaining the physical environment, enforcing isolation, and operating the underlying cloud infrastructure.
There are many IaaS providers offering services in today's marketplace, but three major providers dominate the market. The largest is AWS, followed by Microsoft Azure and Google Compute Platform.

FIGURE 6.2 Slate is a CRM tool designed specifically for higher education admissions teams.
Platform as a Service (PaaS)
Platform as a service (PaaS) approaches occupy a middle ground between SaaS and IaaS services. In this approach, the service provider operates an infrastructure that is fully managed and configurable to run customer applications. Customers then deploy applications that they either developed themselves or purchased from vendors onto the service provider's platform, where they run with minimal customer management.
PaaS platforms support a variety of application types and programming languages. For example, the Heroku PaaS offering shown in Figure 6.4 supports the deployment of customer applications written in Python, Java, Ruby, Node.js, PHP, and other common programming languages.
PaaS offerings allow customers to execute code without managing the underlying servers, but customers typically still need to be involved in provisioning appropriate levels of infrastructure, usually by specifying the number of servers they wish to use. PaaS offerings are then billed based on this provisioned capacity.
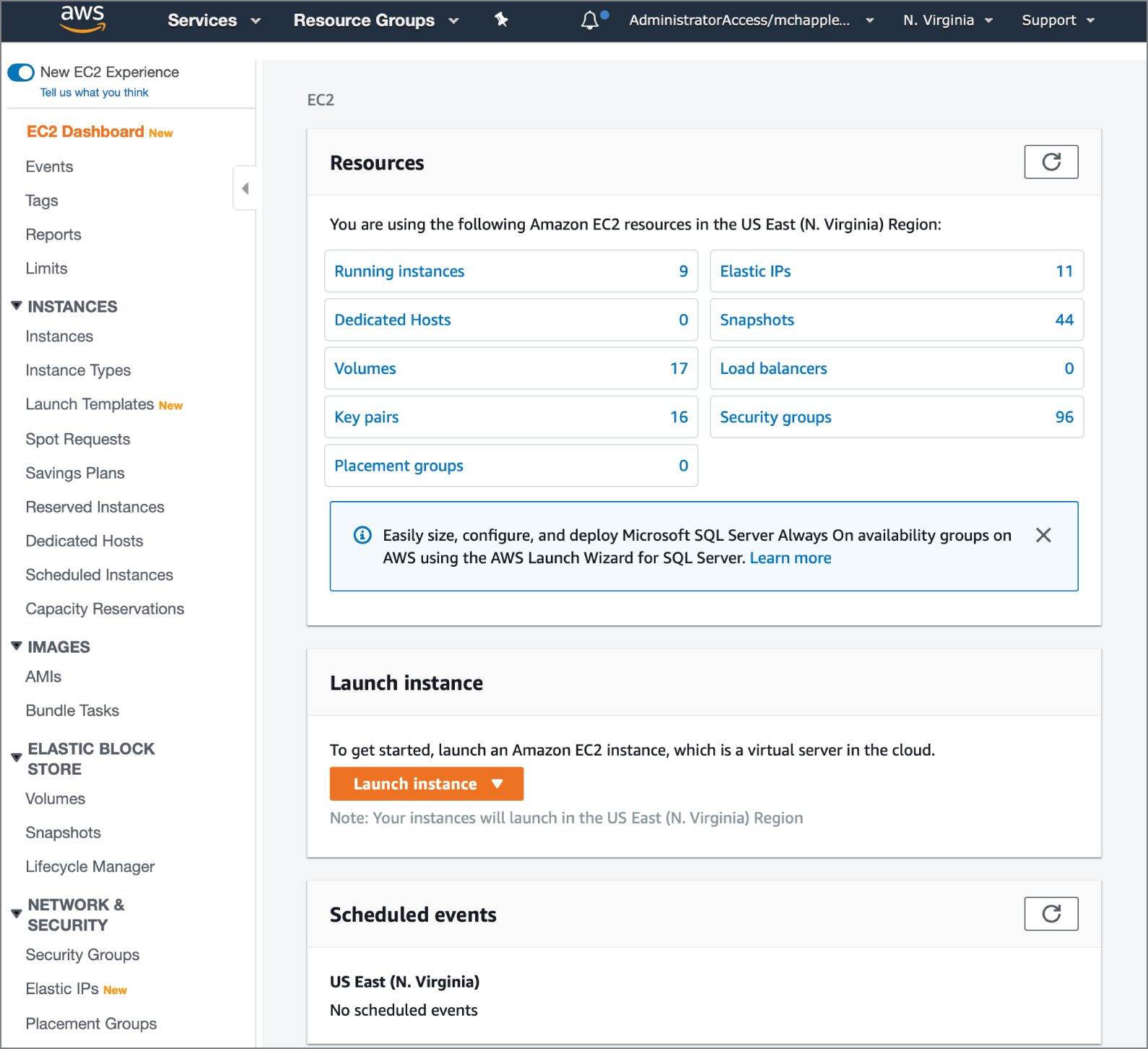
FIGURE 6.3 AWS provides customers with access to IaaS computing resources.

FIGURE 6.4 Heroku is a popular PaaS offering that supports many popular programming languages.
Cloud Deployment Models
Cloud deployment models describe how cloud infrastructure is (or is not) shared among different users. Some cloud deployment models embrace multitenancy, whereas others dedicate resources to specific customers in pursuit of physical isolation for performance and/or security reasons.
Public Cloud
When we think of cloud computing, we most often think of the public cloud. Public cloud service providers deploy infrastructure and then make it accessible to any customers who wish to take advantage of it in a multitenant model. A single customer may be running workloads on servers spread throughout one or more datacenters, and those servers may be running workloads for many different customers simultaneously.
The public cloud supports all cloud service models. Public cloud providers may offer IaaS, PaaS, SaaS, and FaaS services to their customers. The key distinction is that those services do not run on infrastructure dedicated to a single customer but rather on infrastructure that is available to the general public. AWS, Microsoft Azure, and Google Compute Platform all use the public cloud model.
Private Cloud
The term private cloud is used to describe any cloud infrastructure that is provisioned for use by a single customer. This infrastructure may be built and managed by the organization that will be using the infrastructure, or it may be built and managed by a third party. The key distinction here is that only one customer uses the environment. For this reason, private cloud services tend to have excess unused capacity to support peak demand and, as a result, are not as cost efficient as public cloud services.
Community Cloud
A community cloud service shares characteristics of both the public and private models. Community cloud services run in a multitenant environment, but the tenants are limited to members of a specifically designed community. Community membership is normally defined based on shared mission, similar security and compliance requirements, or other commonalities.
The HathiTrust digital library, shown in Figure 6.5, is an example of community cloud in action. Academic research libraries joined together to form a consortium that provides access to their collections of books. Students and faculty at HathiTrust member institutions may log into the community cloud service to access resources.

FIGURE 6.5 HathiTrust is an example of community cloud computing.
Hybrid Cloud
Hybrid cloud is a catch-all term used to describe cloud deployments that blend public, private, and/or community cloud services together. It is not simply purchasing both public and private cloud services and using them together. Hybrid cloud requires the use of technology that unifies the different cloud offerings into a single coherent platform.
For example, a firm might operate their own private cloud for the majority of their workloads and then leverage public cloud capacity when demand exceeds the capacity of their private cloud infrastructure. This approach is known as public cloud bursting.
AWS Outposts, shown in Figure 6.6, are examples of hybrid cloud computing. Customers of this service receive a rack of computing equipment that they install in their own datacenters. The equipment in the rack is maintained by AWS but provisioned by the customer in the same manner as their AWS public cloud resources. This approach qualifies as hybrid cloud because customers can manage both their on-premises AWS Outposts private cloud deployment and their public cloud AWS services through the same management platform.

FIGURE 6.6 AWS Outposts offer hybrid cloud capability.
Image property of Amazon Web Services; used with permission
Operating in the Cloud
In some ways, cybersecurity work in a cloud-centric environment is quite similar to on-premises cybersecurity. No matter where our systems are hosted, we still need to think about the confidentiality, integrity, and availability of our data and implement strong access controls and other mechanisms that protect those primary objectives.
However, cloud security operations also differ significantly from on-premises environments because cloud customers must divide responsibilities between one or more service providers and the customers' own cybersecurity teams. This type of operating environment is known as the shared responsibility model. Figure 6.7 shows the common division of responsibilities in IaaS, PaaS, and SaaS environments.

FIGURE 6.7 Shared responsibility model for cloud computing
In some cases, this division of responsibility is straightforward. Cloud providers, by their nature, are always responsible for the security of both hardware and the physical data center environment. If the customer was handling either of these items, the solution would not fit the definition of cloud computing.
The differences in responsibility come higher up in the stack and vary depending on the nature of the cloud service being used. In an IaaS environment, the customer takes over security responsibility for everything that isn't infrastructure—the operating system, applications, and data that they run in the IaaS environment.
In a PaaS solution, the vendor also takes on responsibility for the operating system, whereas the customer retains responsibility for the data being placed into the environment and configuring its security. Responsibility for the application layer is shared between the service provider and the customer, and the exact division of responsibilities shifts based on the nature of the service. For example, if the PaaS platform provides runtime interpreters for customer code, the cloud provider is responsible for the security of those interpreters.
In an SaaS environment, the provider takes on almost all security responsibility. The customer retains some shared control over the data that they place in the SaaS environment and the configuration of access controls around that data, but the SaaS provider is being paid to take on the burden of most operational tasks, including cybersecurity.
DevOps Strategies
Traditional approaches to organizing and running technology teams focused on building silos of expertise centered on technology roles. In particular, software development and technology operations were often viewed as quite disconnected. Developers worked on creating the software applications that the business desired and had their own processes for specifying requirements, designing interfaces, writing code, testing applications, and maintaining the code base. When they completed testing of a new version of an application, they then handed it off to the technology operations team, who managed the servers and other infrastructure supporting the application.
Separating the development and operations worlds provides technologists with a comfortable working environment where they have their tasks clearly defined and are surrounded by a community of their peers. It also, however, brings significant disadvantages, including the following:
- Isolating operations teams from the development process inhibits their understanding of business requirements.
- Isolating developers from operational considerations leads to designs that are wasteful in terms of processor, memory, and network consumption.
- Requiring clear hand-offs from development to operations reduces agility and flexibility by requiring a lengthy transition phase.
- Increasing the overhead associated with transitions encourages combining many small fixes and enhancements into one major release, increasing the time to requirement satisfaction.
Recognizing the inherent disadvantages of separating development and operational teams, many organizations now embrace a DevOps approach to technology management. This approach brings together development and operations teams in a unified process where they work together in an agile approach to software development. The software testing and release process becomes highly automated and collaborative, enabling organizations to move from lengthy release management processes to a world where they might release dozens of updates on a daily basis.
Infrastructure as Code (IaC)
Infrastructure as code (IaC) is one of the key enabling technologies behind the DevOps movement and is also a crucial advantage of cloud computing solutions. IaC is the process of automating the provisioning, management, and deprovisioning of infrastructure services through scripted code rather than human intervention. IaC is one of the key features of all major IaaS environments, including AWS, Microsoft Azure, and Google Cloud Platform.
IaC takes many forms and may be either a feature offered by a cloud service provider or a functionality enabled by a third-party cloud management platform. In most cases, the same actions available to operations teams through the cloud provider's web interface are also available for implementation in code. For example, Figure 6.8 shows the process of creating an EC2 server instance through the AWS graphical interface.

FIGURE 6.8 Creating an EC2 instance through the AWS web interface
AWS offers a service called CloudFormation that allows developers to specify their infrastructure requirements in several formats, including JavaScript Object Notation (JSON) and Yet Another Markup Language (YAML). Figure 6.9 shows an example of the JSON specification for an EC2 instance.

FIGURE 6.9 Creating an EC2 instance with CloudFormation JSON
The major advantages to using an IaC approach are
- Increasing the reusability of code
- Reducing the time spent by operations team creating infrastructure components
- Increasing the speed of infrastructure creation
- Reducing the likelihood of configuration errors by leveraging common templates
Application Programming Interfaces
IaC approaches require that developers interact directly with a cloud service through their code rather than requiring an individual to work within a web interface. As you saw in the previous section, this is sometimes done through a provider interface, such as the AWS CloudFormation service. Developers may wish, however, to write code that executes in their own environment and still interacts with the cloud service. That's where application programming interfaces (APIs) come into play.
APIs are standard interfaces used to interact with web-based services in a programmatic fashion. Cloud service providers create APIs and then expose them to their customers to allow customer code to provision, manage, and deprovision services.
Security is paramount when cloud providers expose APIs, as they must ensure that users requesting action through an API are authorized to do so. APIs manage this through the use of API keys, which are similar to passwords. When a user sends a request through an API, they also send their API key to authenticate the request. The cloud provider validates the API key and checks that the user, system, or application associated with that key is authorized to perform the requested action.
Insecure APIs are one of the key risks associated with operating in the cloud. Cloud providers generally manage their APIs well to enforce security requirements, but the security of a user's account depends on the security of their API key. Cloud service customers must ensure that they safeguard their keys using the following best practices:
- Limit exposure of the API key to the smallest set of individuals possible.
- Use different API keys for different users, applications, and services.
- Restrict the rights associated with each API key to the specific rights needed by the user, application, or service associated with the key.
- Never transmit API keys over unencrypted channels.
- Never store API keys in unencrypted form.
- Ensure that API keys are removed from any code that is placed in public code repositories or is otherwise at risk of unauthorized access.
Organizations should treat their API keys with the same level of security used to protect encryption keys. Improper key management practices can lead to devastating security consequences.
Cloud Monitoring
In Chapter 10, “Security Operations and Monitoring,” you'll discover the importance of monitoring in the world of cybersecurity operations. Security teams require access to historic information in order to detect policy violations, investigate incidents, troubleshoot tools, and perform a variety of other important tasks. The inability to access logs prevents security operations teams from achieving their objectives.
These concerns become paramount in a cloud-centric environment because most log records are generated within the providers' ecosystem. Security operations teams should ensure that they understand the logging and monitoring mechanisms available to them and integrate them with the other tools used within their security operations centers (SOCs). Insufficient logging and monitoring may lead to insufficient information in the wake of a security incident.
Cloud Infrastructure Security
Security analysts working in a cloud-centric environment use many of the same security tools and techniques used in traditional on-premises environments. After all, securing an operating system in the public cloud is not much different than securing one running on a server under your desk.
In addition to these controls, cybersecurity analysts also use cloud-specific tools that are designed to assess and improve the security of the cloud environment itself. These include cloud infrastructure security tools and cloud access security brokers (CASBs).
Using these tools can help protect organizations against cloud-specific risks. For example, unprotected storage environments pose a much greater security risk in the public cloud than they do in a private data center environment. In a private datacenter, firewall controls generally restrict direct access to storage, limiting the exposure of an unprotected file to users who already have access to datacenter systems. In the public cloud, on the other hand, an improperly managed storage bucket may be exposed to the entire Internet with only a few clicks. Cloud infrastructure security tools can help detect and mitigate these risks.
Cloud Infrastructure Security Tools
Cloud infrastructure assessment tools reach into a cloud environment, retrieve security information, and deliver a report showing the relative security of the environment. They might detect issues that would not appear on other vulnerability scans. For example, a cloud-focused tool might be able to reach into the cloud provider's API and identify the fact that a security key has not been rotated for years. Similarly, a tool might be able to retrieve a list of all security groups applied to an instance and determine the instance's network exposure without conducting an exhaustive port scan.
Cloud providers offer many tools to their customers, often at no charge or for very low cost, as it is in the provider's interest to ensure that resources in their environment are operated securely. For example, Figure 6.10 shows a scan run against an AWS environment using the AWS Inspector tool.
ScoutSuite
ScoutSuite is a multicloud auditing tool that reaches into the user's accounts with cloud service providers and retrieves configuration information using those services' APIs. It is capable of auditing accounts with AWS, Microsoft Azure, Google Compute Platform, Alibaba Cloud, and Oracle Cloud Infrastructure.
ScoutSuite deeply probes the service configuration and searches for potential security issues. Figure 6.11 shows an example of the high-level dashboard generated by a ScoutSuite scan. It displays the number of issues detected in each cloud service used by the customer.
Detailed reports for each service then drill into the specific issues that exist in the environment. For example, Figure 6.12 shows the AWS EC2 service issues in one account. Expanding each item in the report shows details about the potential problem. In Figure 6.12, you see that this account has 18 Elastic Block Store (EBS) disk volumes that do not use encryption to protect data in transit or at rest.

FIGURE 6.10 Results of an AWS Inspector scan.
Pacu
Pacu is not a scanning tool but rather a cloud-focused exploitation framework, similar to Metasploit. It works specifically with AWS accounts and is designed to help attackers determine what they can do with the access they have to an existing AWS account. For this reason, it is a favorite tool of AWS penetration testers.
Working with Pacu is quite similar to working with Metasploit in that Pacu offers a modular framework of plug-ins that test and probe various information sources. Figure 6.13 provides a partial listing of the AWS exploitation plug-ins available for Pacu.

FIGURE 6.11 ScoutSuite dashboard from an AWS account scan
Prowler
Prowler is a security configuration testing tool, quite similar to ScoutSuite in purpose. Prowler performs deeper testing of some parameters, but it is limited to scanning AWS environments. Figure 6.14 shows the partial result of a Prowler scan against an AWS account.

FIGURE 6.12 EC2 security issues reported during a ScoutSuite scan

FIGURE 6.13 Partial listing of the exploits available in Pacu
Cloud Access Security Brokers (CASB)
Most organizations use a variety of cloud service providers for different purposes. It's not unusual to find that a large organization purchases cloud services from dozens, or even hundreds, of different providers. This is especially true when organizations use highly specialized SaaS products. Managing security policies consistently across these services poses a major challenge for cybersecurity analysts.
Cloud access security brokers (CASBs) are software tools that serve as intermediaries between cloud service users and cloud service providers. This positioning allows them to monitor user activity and enforce policy requirements. CASBs operate using two different approaches:
- Inline CASB solutions physically or logically reside in the connection path between the user and the service. They may do this through a hardware appliance or an endpoint agent that routes requests through the CASB. This approach requires configuration of the network and/or endpoint devices. It provides the advantage of seeing requests before they are sent to the cloud service, allowing the CASB to block requests that violate policy.
- API-based CASB solutions do not interact directly with the user but rather interact directly with the cloud provider through the provider's API. This approach provides direct access to the cloud service and does not require any user device configuration. However, it also does not allow the CASB to block requests that violate policy. API-based CASBs are limited to monitoring user activity and reporting on or correcting policy violations after the fact.

FIGURE 6.14 Partial results of a Prowler scan against an AWS account
Summary
Cloud computing plays a crucial role in the technology strategies of modern organizations. Cybersecurity analysts must be familiar with the various cloud service and deployment models and understand how the use of cloud services impacts their organizations. They must be able to validate cloud configurations and ensure that they implement strong security controls, including key management, access controls, and logging and monitoring. They must also understand how to use cloud security assessment tools to verify the integrity of the cloud environment and remediate any security gaps that might exist.
Exam Essentials
Explain how the cloud service models differ in the type of service offered. Infrastructure as a service (IaaS) offerings provide customers with access to storage, computing, and networking capabilities—the basic building blocks of technology solutions. Software as a service (SaaS) offerings provide customers with a complete application, built and managed by the provider. Platform as a service (PaaS) offerings allow customers to run their own applications on an infrastructure managed by the provider. Function as a service (FaaS) offerings allow customers to execute discrete units of code on the provider's infrastructure.
Explain how cloud deployment models differ in how cloud infrastructure is shared. Public cloud services use the multitenancy model and are open to all customers. Private cloud services are restricted to use by a single customer. Community cloud services offer services to members of a defined, closed community. Hybrid environments combine aspects of public, private, and/or community cloud in a unified platform.
Know how cloud environments embrace automation to improve agility. The DevOps approach to technology unifies software development and technology operations practices. Cloud services enable DevOps by offering infrastructure as code (IaC) capabilities through their application programming interfaces (APIs). Cybersecurity analysts must understand how to secure these APIs and manage both API and encryption keys.
Be aware that operating in the cloud introduces new technology risks. Cybersecurity analysts must understand the controls implemented by cloud service providers and how security duties are divided according to the shared responsibility model. They must understand the risks associated with managing those controls and work to prevent undesirable situations, such as unprotected storage.
Know how to integrate cloud services into the organization's SOC. Cybersecurity analysts must ensure that cloud providers offer sufficient logging and monitoring capabilities and that the SOC has the ability to access logs through their existing security tools.
Be familiar with how cloud assessment tools supplement standard security controls. ScoutSuite offers cybersecurity analysts the ability to probe the security configurations of many different cloud providers, whereas Prowler performs the same function only in AWS environments. Pacu is an exploitation framework for use in cloud service penetration tests.
Define the purpose of CASB solutions. Cloud access security brokers (CASBs) serve as an intermediary between users and providers, allowing cybersecurity teams to monitor user activity and consistently enforce security policies. CASB solutions may either exist directly inline with user connections or interact with the provider through the provider's API.
Lab Exercises
Activity 6.1: Run a ScoutSuite Assessment
ScoutSuite is a Python script available for free download. In this activity, you will download and run the tool. Note that running ScoutSuite requires read-only access to a cloud account. You should only run this scan against an account that you have permission to scan.
- Download ScoutSuite from the GitHub repository at
github.com/nccgroup/ScoutSuite. - Run it on a system that has Python installed using the command
python3 scout.py. Review the instructions presented to you to configure and run ScoutSuite against the cloud provider of your choice. - Analyze the findings from your ScoutSuite report. What are the most pressing vulnerabilities that you found? How would you address them?
Activity 6.2: Explore the Exploits Available with Pacu
Pacu is also a Python script available for free download. In this activity, you will download and run the tool. Running Pacu requires access to an AWS account. You should only run Pacu against an account that you have permission to scan.
- Download Pacu from the GitHub repository at
github.com/RhinoSecurityLabs/pacu. - Install and configure Pacu on your system using the command
bash install.sh. - Run it on a system that has Python installed using the command
python3 pacu.py. Review the instructions presented to you to configure and run ScoutSuite against the cloud provider of your choice. - Run the
listcommand to determine the modules currently available in Pacu. Which of these seem most valuable to you? How might you use them in a penetration test?
Activity 6.3: Scan an AWS Account with Prowler
Prowler is a command-line tool available for free download. In this activity, you will download and run the tool. Note that running Prowler requires read-only access to an AWS account. You should only run this scan against an account that you have permission to scan.
- Download Prowler from the GitHub repository at
github.com/toniblyx/prowler. - Install it on your system, configure it, and run a scan. This is a fairly complex process, but you will find a document walking you through the current steps to do so in the
README.mdfile in the Prowler GitHub repository. - Analyze the findings from your Prowler report. What are the most pressing vulnerabilities that you found? How would you address them?
Review Questions
- Which one of the following statements about cloud computing is incorrect?
- Cloud computing offers ubiquitous, convenient access.
- Cloud computing customers store data on hardware that is shared with other customers.
- Cloud computing customers provision resources through the service provider's sales team.
- Cloud computing resources are accessed over a network.
- Under the shared responsibility model, in which tier of cloud computing is the customer responsible for securing the operating system?
- IaaS
- PaaS
- SaaS
- All of the above
- Helen designed a new payroll system that she offers to her customers. She hosts the payroll system in AWS and her customers access it through the web. What tier of cloud computing best describes Helen's service?
- PaaS
- SaaS
- FaaS
- IaaS
- Tony purchases virtual machines from Microsoft Azure and uses them exclusively for use by his organization. What model of cloud computing is this?
- Public cloud
- Private cloud
- Hybrid cloud
- Community cloud
- Amanda would like to run a security configuration scan of her Microsoft Azure cloud environment. Which one of the following tools would be most appropriate for her needs?
- Inspector
- ScoutSuite
- Prowler
- Pacu
- Kevin is using a service where a cloud provider offers a platform that executes his code in response to discrete events. He is billed based on the actual resources consumed during each code execution event. What term best describes this service?
- PaaS
- SaaS
- FaaS
- IaaS
- Under the shared responsibility model, which component always remains the responsibility of the customer, regardless of the cloud service model used?
- Application
- Hardware
- Datacenter
- Data
- Which one of the following services is not an example of FaaS computing?
- Lambda
- DeepLens
- Google Cloud Functions
- Azure Functions
- Which cloud computing deployment model requires the use of a unifying technology platform to tie together components from different providers?
- Public cloud
- Private cloud
- Community cloud
- Hybrid cloud
- Which one of the following would not commonly be available as an IaaS service offering?
- CRM
- Storage
- Networking
- Computing
- Which one of the following is a characteristic of DevOps approaches to technology?
- Isolating operations teams from development teams
- Requiring clear hand-offs between development and production
- Increasing the frequency of application releases
- Eliminating the need for developers to understand business requirements
- Which one of the following is not an example of infrastructure as code?
- Defining infrastructure in JSON
- Writing code to interact with a cloud provider's API
- Using a cloud provider's web interface to provision resources
- Defining infrastructure in YAML
- Which one of the following conditions is not likely to trigger an alert during an automated cloud security assessment?
- Presence of an API key in a public repository
- Unrestricted API keys
- Transmission of an API key over unsecured channels
- Sharing of API keys among different developers
- Brian is selecting a CASB for his organization and he would like to use an approach that interacts with the cloud provider directly. Which CASB approach is most appropriate for his needs?
- Inline CASB
- Outsider CASB
- Comprehensive CASB
- API-based CASB
- A coalition of universities banded together and created a cloud computing environment that is open to all member institutions. The services provided are basic IaaS components. What term best describes this cloud model?
- Public cloud
- Private cloud
- Community cloud
- Hybrid cloud
- In which cloud computing service model does the customer share responsibility with the cloud provider for datacenter security?
- IaaS
- SaaS
- PaaS
- None of the above
- Which one of the following statements about inline CASB is incorrect?
- Inline CASB solutions often use software agents on endpoints.
- Inline CASB solutions intercept requests from users to cloud providers.
- Inline CASB solutions can monitor activity but cannot actively enforce policy.
- Inline CASB solutions may require network reconfiguration.
- What type of credential is commonly used to restrict access to an API?
- Encryption key
- API key
- Password
- Biometrics
- Gina gained access to a client's AWS account during a penetration test. She would like to determine what level of access she has to the account. Which one of the following tools would best meet her need?
- ScoutSuite
- Inspector
- Prowler
- Pacu
- In which of the following cloud categories are customers typically charged based on the number of virtual server instances dedicated to their use?
- IaaS only
- SaaS only
- IaaS and PaaS
- IaaS, SaaS, and PaaS
