Figure 16-1: Database table.
Chapter 16
Ten Emerging Trends
In This Chapter
![]() Examining information governance
Examining information governance
![]() Understanding cloud computing
Understanding cloud computing
![]() Assessing the impact of social media
Assessing the impact of social media
![]() Reducing duplication
Reducing duplication
Although Records and Information Management principles have tended to stay constant over the years, the volume of content that organizations have to manage has significantly increased. The increase in information is directly attributable to the advancements in Communication and Collaboration technologies, such as e-mail, instant messaging, Facebook, Twitter, and Microsoft SharePoint.
Product vendors, consultants, and their clients have seen the information train barreling down the track for more than a decade. Most companies have acknowledged the fact that they need to take action. However, most organizations have not implemented the appropriate steps and technologies needed to offset the effects of the information onslaught.
The objective of this chapter is to introduce and examine emerging Records and Information Management trends and to see how they can help you begin the process of addressing and resolving your challenges.
Governing Information
We know for a fact that companies are being bombarded with information from a variety of sources, such as customers, social media, employees, vendors, and regulatory agencies. The issue we’re facing today is that organizations don’t have the appropriate infrastructure in place to capitalize on the value of the information they possess.
Information governance is a concept born out of organizational necessity. Most companies understand that they aren’t properly managing their informational assets. Information governance is a process that allows organizations to mesh technologies, processes, and people together to build an information infrastructure that will allow them to understand what information they have and how to appropriately use it.
The overarching principles of information governance are control and accountability. Typically, information governance takes the form of a committee comprised of employees from key organizational areas such as Records Management, Legal, Compliance, IT, and Information Security. The employees who serve on the committee should be in a decision-making capacity.
The committee provides oversight on all information-related areas and is specifically tasked with formulating the organization’s information strategy. Such a strategy would address the following:
![]() How information is to be accessed and used
How information is to be accessed and used
![]() Security of information
Security of information
![]() Quality and integrity of information
Quality and integrity of information
![]() Management and disposal of information
Management and disposal of information
Computing in the Clouds
Cloud computing is a term that many are familiar with at this point, but aside from a catchy name, what is it? Ask five people what cloud computing is and you’ll likely get five different answers. In layman’s terms, cloud computing describes a situation where you’d use a vendor’s software (and store any associated data) on a vendor’s computers and servers located in its data center via the Internet. It’s software as a service (rather than as a product or application) that you load on your own computer.
It’s important to understand the premise that supports cloud computing. Cloud providers (such as Amazon, IBM, and CSC) have data centers full of state-of-the-art computer equipment. All the vendor’s clients share the computing power of the equipment. Think of it as the electrical grid in your city. When a customer needs more power, it’s there for the taking, and in most cases, you pay only for what you use.
Cloud computing can provide significant benefits. It reduces the amount of computer equipment, software, storage, and supplies that have to be purchased and maintained by any single organization. However, some organizations are still reluctant to use it on a large-scale basis due to the following concerns:
![]() Availability: A major cloud concern centers around potential downtime. The vendor’s cloud must be available to organizations whenever needed.
Availability: A major cloud concern centers around potential downtime. The vendor’s cloud must be available to organizations whenever needed.
![]() Performance: Organizations are concerned that an Internet-based computing approach will result in diminished processing time.
Performance: Organizations are concerned that an Internet-based computing approach will result in diminished processing time.
![]() Security: Security is a major concern to companies. Organizations continue to be reluctant to transmit and retrieve their sensitive data via the Internet, as well as to store this type of information in a vendor’s data center whose equipment is used by other clients.
Security: Security is a major concern to companies. Organizations continue to be reluctant to transmit and retrieve their sensitive data via the Internet, as well as to store this type of information in a vendor’s data center whose equipment is used by other clients.
![]() Disaster recovery: Companies need assurance that their information is being appropriately backed up. Storing information in a cloud data center eliminates the control that IT departments had in ensuring that proper backups were conducted.
Disaster recovery: Companies need assurance that their information is being appropriately backed up. Storing information in a cloud data center eliminates the control that IT departments had in ensuring that proper backups were conducted.
![]() Information ownership: Organizations must be sure to include contractual language that establishes their ownership of the data that they store in the cloud.
Information ownership: Organizations must be sure to include contractual language that establishes their ownership of the data that they store in the cloud.
If your organization is considering a move to the cloud, it’s important to conduct an extensive vendor evaluation that includes the issues mentioned here, as well as to ensure that your information can be retained for the appropriate retention periods and that you have the ability to remove your data from the vendor’s cloud in the event that you terminate the relationship. In addition, you should establish a Service Level Agreement (SLA) with the cloud provider that documents performance and availability expectations. The SLA should provide remedies for actual results that don’t meet your requirements. Remedies need to be specified. Usually they include a reduction in the monthly fees you are contractually required to pay.
Big Data
Big data, the big brother to data mining and analytics, is a new concept that’s starting to gain some traction in large private and governmental organizations that have huge amounts (petabytes and exabytes) of structured and unstructured data. The objective of big data is content analysis, or trying to identify repeatable business trends and patterns in an effort to make better-informed business decisions. Many organizations feel that hidden within their repositories of data are gems that could provide significant competitive advantages and operational knowledge.
The problem with big data is that the volumes are so vast that you just can’t dump the information into a Microsoft Access database and run some queries against it. It requires exceptional computing horsepower — what is being referred to as Big Data technologies. Large cloud providers and their extensive computing framework can be a good option for Big Data processing.
Social Media
Who would have thought something like social media would affect businesses, let alone that it would impact the management of organizational policies, records, and information?
Most folks are familiar with Facebook, Twitter, and the many other social media sites that continue to spring up. They’re now a regular part of how businesses and customers stay in touch. Many companies have departments dedicated to social media interaction. Companies use social media sites to post special deals, upcoming events, and coupons. In turn, customers are able to post reviews and comments about the organization.
Social media has an impact on Records and Information management. Many of the communications between organizations and the public qualify as official records. For example, if a company provides coupons or offers product discounts on its Facebook page, it constitutes a promise to honor the deal. The record of the offer should be retained in accordance with the company’s retention schedule in the event of a customer dispute. In addition, customer inquiries and employee responses can also be records of the company. It is recommended that all organizations using social media for external communication purposes analyze the record types that are created and assign appropriate retention periods to them.
Organizations using social media tools are discovering the need to develop social media usage policies. Similar to e-mail usage policies, social media policies address the proper usage of social media by employees both during work and during nonwork hours. The intent of the policy is not to stifle employee creativity and opinions, but to ensure the integrity and reputation of the organization.
Companies don’t want employees using social media sites to disparage the company or co-workers or divulge personal and confidential information about its customers. Therefore, many organizations have included some of the following topics in their policies:
![]() Access: In some organizations, only certain job roles may need access to social media sites. It’s important to ensure that corporate oversight exists when it comes to who is actually granted access.
Access: In some organizations, only certain job roles may need access to social media sites. It’s important to ensure that corporate oversight exists when it comes to who is actually granted access.
![]() Confidentiality: The policy should include language that instructs employees not to disclose any information of a personal, confidential, or competitive nature.
Confidentiality: The policy should include language that instructs employees not to disclose any information of a personal, confidential, or competitive nature.
![]() Accuracy: Employees should be instructed to ensure that all information they post on social media sites is accurate.
Accuracy: Employees should be instructed to ensure that all information they post on social media sites is accurate.
![]() Appropriate conduct: Employees shouldn’t post any content that is of an inappropriate or offensive nature.
Appropriate conduct: Employees shouldn’t post any content that is of an inappropriate or offensive nature.
![]() Transparency: When appropriate, employees should clearly identify themselves in their postings and specify their role within the organization.
Transparency: When appropriate, employees should clearly identify themselves in their postings and specify their role within the organization.
Putting Some Structure to It
Traditionally, Records and Information Management has addressed physical content such as paper accounting, Human Resources records, and unstructured content (images, word processing documents, spreadsheets, and PDF documents). However, the need to manage structured data has recently started to receive a lot of attention.
Structured data is information found in database table fields, such as the information you’d find in an Accounting or HR software application. Just like unstructured information, structured data can accumulate significantly over time if not properly managed. Most organizational Record and Information retention schedules don’t address the retention of structured application data. This is primarily due to the challenge of managing data fields as records.
For example, in an Accounting database, vendor invoice information may reside in multiple fields such as vendor name, vendor number, street address, city, state, and zip code. (See Figure 16-1 for an example.)
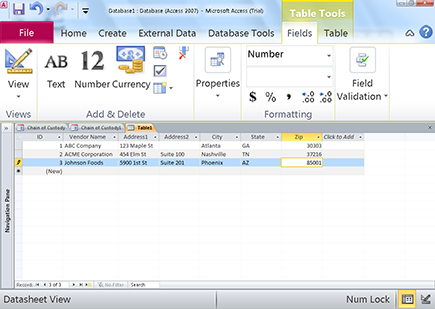
When the underlying software brings these fields together, you end up with a viewable invoice. However, viewing each field separately doesn’t have much meaning. So the question is, should individual fields be considered records? The answer is yes — but. The but in this case is due to data fields being used for other purposes. In the previous example, the vendor name is used for invoice purposes, which may need to be retained for seven years. However, the Vendor Name field may also be used for tax form purposes, which may have a different retention period. Therefore, it’s important to understand the connection between fields and tables in the application.
Let’s Collaborate
Organizations understand the importance of project collaboration. Collaboration is defined simply as working with others to achieve a goal. This may involve initiatives such as the development of a new product, the implementation of a software application, or the review of existing company policies.
Vendors have created software tools to assist employees (and, in some cases, entities outside the organization) to collaborate on projects. One such application is Microsoft SharePoint. SharePoint is now commonly used by quite a number of companies for collaboration purposes.
Organizations should provide oversight and guidance to employees who need to use SharePoint. This includes a review, approval, and periodic follow-up process for anyone wanting to establish a SharePoint site. This approach helps to ensure that only valid needs are approved and that sites are regularly audited to properly account for company records. Some Records and Enterprise Content Management systems offer SharePoint integration tools. This provides the ability to ensure that record content is unalterable and that the retention periods are managed.
Generally Accepted Recordkeeping Principles
ARMA, a not-for-profit professional association and the authority on managing records and information, has published its Generally Accepted Recordkeeping Principles (GARP). GARP was developed to bring awareness to records management principles and standards.
![]() Accountability: An organization shall assign a senior executive who will oversee a recordkeeping program and delegate program responsibility to appropriate individuals, adopt policies and procedures to guide personnel, and ensure program auditability.
Accountability: An organization shall assign a senior executive who will oversee a recordkeeping program and delegate program responsibility to appropriate individuals, adopt policies and procedures to guide personnel, and ensure program auditability.
![]() Integrity: A recordkeeping program shall be constructed so that the records and information generated or managed by or for the organization have a reasonable and suitable guarantee of authenticity and reliability.
Integrity: A recordkeeping program shall be constructed so that the records and information generated or managed by or for the organization have a reasonable and suitable guarantee of authenticity and reliability.
![]() Protection: A recordkeeping program shall be constructed to ensure a reasonable level of protection to records and information that are private, confidential, privileged, secret, or essential to business continuity.
Protection: A recordkeeping program shall be constructed to ensure a reasonable level of protection to records and information that are private, confidential, privileged, secret, or essential to business continuity.
![]() Compliance: The recordkeeping program shall be constructed to comply with applicable laws and other binding authorities as well as the organization’s policies.
Compliance: The recordkeeping program shall be constructed to comply with applicable laws and other binding authorities as well as the organization’s policies.
![]() Availability: An organization shall maintain records in a manner that ensures timely, efficient, and accurate retrieval of needed information.
Availability: An organization shall maintain records in a manner that ensures timely, efficient, and accurate retrieval of needed information.
![]() Retention: An organization shall maintain its records and information for an appropriate time, taking into account legal, regulatory, fiscal, operational, and historical requirements.
Retention: An organization shall maintain its records and information for an appropriate time, taking into account legal, regulatory, fiscal, operational, and historical requirements.
![]() Disposition: An organization shall provide secure and appropriate disposition for records that are no longer required to be maintained by applicable laws and the organization’s policies.
Disposition: An organization shall provide secure and appropriate disposition for records that are no longer required to be maintained by applicable laws and the organization’s policies.
![]() Transparency: The processes and activities of an organization’s recordkeeping program shall be documented in an understandable manner and be available to all personnel and appropriate interested parties.
Transparency: The processes and activities of an organization’s recordkeeping program shall be documented in an understandable manner and be available to all personnel and appropriate interested parties.
ARMA also provides the GARP Maturity Model. The model serves as a reference tool that allows an organization to determine the state of its Records and Information Management program. The GARP Maturity Model can be found in the online appendix for this book, available for download at www.dummies.com/go/recordsmanagefd.
Mapping Your Data
Most organizations are finding it difficult to manage the explosion of electronic information. Most large companies have hundreds of data repositories and software applications in use. It’s important to know where your information is located, its purpose, and who owns it. Determining these factors is known as data mapping. Data mapping is a time-consuming process. However, many companies have decided to undertake the initiative in an effort to be better positioned to meet the electronically stored information (ESI) requirements that were introduced in the updated Federal Rules of Civil Procedure (FRCP 2006).
To comply with the FRCP, parties to a lawsuit have to provide each other with a copy or description, by category and location, of all documents and electronically stored information that each side has that supports its case.
Enterprise Searching
When using the Search feature on your computer to locate a file, you usually end up entering all or part of the filename or a phrase of text in the body of the document, as well as the specific drive you need to search. For example, if you search your hard drive first, but don’t find what you are looking for, you then can specify another drive location if you are connected to a network. The point is that you have to search each repository individually. Enterprise search eliminates this issue.
Enterprise search software allows you to search for content in multiple network repositories at the same time by using a query as long as you have access to the repositories. Think of it as an internal Google, Bing, or Yahoo! search. Enterprise search allows you to search for structured and unstructured data located on shared drives, e-mail servers, databases, intranets, extranets, external-facing websites, and other network repositories.
Enterprise search engines work by first indexing all content in specified repositories through the use of a crawler. The crawler wanders through each repository, database, and website, collecting information to form a searchable index of the content. It’s important to remember that an enterprise search engine crawler has to be provided authentication rights to enter a repository or application. Without the proper permissions, the crawler will skip the repository.
Using enterprise search to find organizational content provides the look and feel of an Internet search, including the format of the search results. Many of the enterprise search engines will sort the results in order of relevance based on the search criteria.
Don’t Get Duped
It’s been estimated that over 50 percent of organizational information is duplicates. Duplicates exist in paper and electronic formats. So why is there so much duplication of information? Duplication of information can exist for valid reasons, such as needing to print a copy of an e-mail to review at a meeting, or if multiple departments need the same information to process different functions. Duplicate information should be properly disposed of as soon as it has served its business purpose.
However, the duplication and ongoing retention of electronic information are often the result of improper folder and file naming. Folders and files that are named in a cryptic manner make it difficult for other employees to know whether the file they’re saving already exists. In addition, e-mail attachments are a significant source of duplicate information.
Don’t despair; once again, technology has come to the rescue. Deduplication software tools can help organizations identify and delete duplicate and potentially duplicate content. Deduplication works by comparing chunks of data and looking for duplication. Deduplication uses two primary approaches:
![]() Postprocess: Postprocess deduplication allows new data to be entered in the application or repository throughout the workday without interruption. Then at a later time, the deduplication process will run to determine whether any duplicate information exists.
Postprocess: Postprocess deduplication allows new data to be entered in the application or repository throughout the workday without interruption. Then at a later time, the deduplication process will run to determine whether any duplicate information exists.
![]() In-line: The In-line deduplication process is working at all times in an effort to detect duplicate information. When duplicate or potentially duplicate information is entered in the application, the employee is notified of the issue.
In-line: The In-line deduplication process is working at all times in an effort to detect duplicate information. When duplicate or potentially duplicate information is entered in the application, the employee is notified of the issue.
Deduplication can provide several significant benefits. It shrinks the volume of information that needs to be backed up, reduces the volume of information during eDiscovery, and can improve system performance.

 SharePoint has provided significant benefits to organizations, but it has also created Records and Information Management challenges. The issues aren’t typically software related but are due to a lack of organizational control and governance. In many companies, employees can create a SharePoint site without having to obtain approval. This approach leads to numerous SharePoint sites that contain official company records that aren’t appropriately accounted for and managed. In addition, when the project collaboration ends, the content remains on the site, which is no longer actively used.
SharePoint has provided significant benefits to organizations, but it has also created Records and Information Management challenges. The issues aren’t typically software related but are due to a lack of organizational control and governance. In many companies, employees can create a SharePoint site without having to obtain approval. This approach leads to numerous SharePoint sites that contain official company records that aren’t appropriately accounted for and managed. In addition, when the project collaboration ends, the content remains on the site, which is no longer actively used.
 Many organizations that have tried to complete a data map themselves have found that the project is too big to do alone. Vendors provide software designed to assist in the mapping process. In addition, consultants are available that specialize in electronic records and information management that provide data-mapping services.
Many organizations that have tried to complete a data map themselves have found that the project is too big to do alone. Vendors provide software designed to assist in the mapping process. In addition, consultants are available that specialize in electronic records and information management that provide data-mapping services.