Figure 6-1: Microsoft Outlook PST folder.
Chapter 6
A Message about E-Mail
In This Chapter
![]() Defining e-mail
Defining e-mail
![]() Analyzing e-mail risks
Analyzing e-mail risks
![]() Managing e-mail quotas
Managing e-mail quotas
![]() Reviewing Personal Storage Table (PST) folders
Reviewing Personal Storage Table (PST) folders
![]() Understanding e-mail filing methods
Understanding e-mail filing methods
![]() Coming up with better names for your e-mails
Coming up with better names for your e-mails
![]() Reviewing e-mail software
Reviewing e-mail software
Twenty years ago, most companies couldn’t have imagined the impact that e-mail would have on their business. In fact, e-mail now serves as the main contributor to the explosive growth of electronic information. With the growth of e-mail has come the challenge of how to manage it. Due to the volume of e-mail and its management challenges, it can pose significant risks to organizations. It’s important to understand these risks and to know how to reduce them.
Trying to manage e-mail may seem like an overwhelming task, but solutions to the dilemma exist — from employee awareness and education to e-mail management software applications. This chapter walks you through the various solutions so that you can determine which one fits your particular situation.
The Anatomy of an E-Mail
The first step in managing your e-mail is to understand its anatomy. The primary reason e-mail is a management challenge is that many employees don’t know how to properly evaluate or process e-mails. Understanding what e-mails are — and aren’t — can make it easier for employees to manage them.
The following sections provide you with an understanding of e-mail components and show you how to evaluate their contents and the risks of e-mail mismanagement.
Determining the value of the message
At some point each day, you make the trek to your mailbox to see what the postal service delivered. As you review the mail, you are making decisions to keep some items and discard others. In many cases, you can immediately determine the nature of the contents by the envelope and sender, whether it is junk mail or your monthly electric bill. In other cases, you have to open the envelope and analyze the contents to make a decision.
Although e-mail metadata is important (more on this topic later in the chapter), it’s the message or content delivered by the e-mail that employees need to evaluate. Some e-mails contain information of business importance and should be retained, while others are of no value and should be deleted immediately.
Microsoft estimates that the average inbox will receive 14,600 e-mail messages in 2012; that equates to over 40 e-mails per day that need to be evaluated by each employee. This doesn’t include the e-mails that you draft and send. If the sole responsibility of an employee was to evaluate e-mail, this would not be a big deal. However, employees have other duties and tasks they are required to accomplish each day. Therefore, it’s important that the evaluation process be structured, quick, and accurate.
![]() Delete: Determine whether the message is spam or of any nature that allows you to immediately delete it. Many times, you can determine whether to immediately delete an e-mail by the sender’s name or subject line. It is recommended that you explore the built-in spam-blocking features of your e-mail client software. If they seem skimpy, you may want to invest in third-party software applications from vendors such as Norton or Barracuda to help reduce the inbox burden.
Delete: Determine whether the message is spam or of any nature that allows you to immediately delete it. Many times, you can determine whether to immediately delete an e-mail by the sender’s name or subject line. It is recommended that you explore the built-in spam-blocking features of your e-mail client software. If they seem skimpy, you may want to invest in third-party software applications from vendors such as Norton or Barracuda to help reduce the inbox burden.
![]() Do: If the message requires action, take the necessary steps to process it if time currently permits. The rule of thumb is if the action can be completed in two minutes or less, go ahead and do it. This may include processing a function or filing the e-mail for future needs.
Do: If the message requires action, take the necessary steps to process it if time currently permits. The rule of thumb is if the action can be completed in two minutes or less, go ahead and do it. This may include processing a function or filing the e-mail for future needs.
![]() Delegate: Determine whether another employee should act upon the message. If so, forward the e-mail to the employee and delete your copy, if applicable.
Delegate: Determine whether another employee should act upon the message. If so, forward the e-mail to the employee and delete your copy, if applicable.
![]() Defer: If you believe the task will take longer than the time you currently have available, defer it. The message should stay in your inbox and be flagged for prompt processing.
Defer: If you believe the task will take longer than the time you currently have available, defer it. The message should stay in your inbox and be flagged for prompt processing.
It’s time for everyone — managers, supervisors, team leaders, and employees — to face facts: The digital age has forced us all to handle and process more information than we ever thought possible, much of which is spam, duplications, and files that have outlived their usefulness. We are being required to do things differently than we did a decade ago. This includes routinely deleting content that provides no value to our organizations.
Scheduling time for e-mail
If you aren’t careful, you can find yourself behind your computer for hours at a time working e-mail. Typically, most people take two approaches to processing e-mail — continuous and (the more disciplined) scheduled.
It is easy to get caught in the trap of monitoring your inbox continuously throughout the day: You hear the familiar “ding” and know you have a new e-mail and immediately click to view it. This approach can quickly become the “great momentum breaker.” For example, if you’re working on a project and regularly stop to view your new e-mail, you’ll constantly be losing your train of thought and getting nowhere fast.
The rising risks of e-mail
It’s hard to remember when e-mail didn’t exist. It’s now a staple of business communication. As much as we lament its impact on our inbox, most of us find it an essential part of our workday. Many experts consider e-mail the number one information management challenge that organizations face. The issue here is that most companies don’t know how to manage e-mail — and often are not even aware of the negative impact that not managing it can have on their business.
The extent of most organizations’ attempts to manage e-mail consists of an e-mail usage policy, which typically instructs employees not to send offensive or harassing messages. Although this is important, it doesn’t adequately address the numerous risks created by not managing e-mail. Such risks include the following:
![]() Operational: Allowing e-mail to go unmanaged can create significant losses in employee productivity. Most employees rely heavily on e-mail and must sift through large numbers of messages and attachments to find what they need. This can delay processing and decision-making. If an organization doesn’t use software to filter junk (spam) e-mail, the burden is increased.
Operational: Allowing e-mail to go unmanaged can create significant losses in employee productivity. Most employees rely heavily on e-mail and must sift through large numbers of messages and attachments to find what they need. This can delay processing and decision-making. If an organization doesn’t use software to filter junk (spam) e-mail, the burden is increased.
![]() Legal: Two primary types of legal risks are associated with e-mail — employee conduct and eDiscovery (producing information for a lawsuit; see Chapter 8 for additional information on eDiscovery). Employers are typically held responsible for the acts of their employees — and this includes e-mail. In addition, unmanaged e-mails make it extremely difficult and costly when attempting to produce e-mail messages and attachments in the event of litigation. (Additional information on this matter is covered in Chapter 8.)
Legal: Two primary types of legal risks are associated with e-mail — employee conduct and eDiscovery (producing information for a lawsuit; see Chapter 8 for additional information on eDiscovery). Employers are typically held responsible for the acts of their employees — and this includes e-mail. In addition, unmanaged e-mails make it extremely difficult and costly when attempting to produce e-mail messages and attachments in the event of litigation. (Additional information on this matter is covered in Chapter 8.)
![]() Compliance: Federal regulations and compliance rules now exist that govern how organizations should maintain electronic information (including e-mails) to prove evidence of transactions and prevent breaches of confidential information. The mismanagement of e-mail can lead to penalties, fines, and public relations nightmares.
Compliance: Federal regulations and compliance rules now exist that govern how organizations should maintain electronic information (including e-mails) to prove evidence of transactions and prevent breaches of confidential information. The mismanagement of e-mail can lead to penalties, fines, and public relations nightmares.
The following sections of this chapter provide you with the information you need to manage e-mail, which can assist you in reducing organizational risks.
Managing quotas
Most e-mail users have experienced the dreaded message — “Your inbox is over its size limit.” After the message is received, a mad scramble ensues to delete messages and attachments, or for employees with a Delete Key phobia, a phone call is made to IT to justify their need for more e-mail storage space. Welcome to the world of e-mail quotas!
An e-mail quota is the amount of spaced reserved on a server for your e-mail messages. The quotas established by organizations vary greatly from megabytes to gigabytes. Regardless of the quota size, if e-mail is not properly managed, the quota will likely be exceeded.
Filing the Message
Knowing what to do with e-mail messages that need to be retained can help you be more productive and reduce risks to the company. The following sections analyze methods for filing, naming, and retaining e-mail messages. This includes reviewing e-mail management functionality offered in applications such as Microsoft Outlook and determining how it can benefit your organization, as well as using shared network drives and enterprise content management systems to manage e-mail messages.
PSSST! What you need to know about PST folders
E-mail messages (including attachments) that need to be retained should be properly filed in an established folder structure. Most users file e-mail in Personal Storage Table (PST) folders. PST is a file extension format controlled by Microsoft and used in its Outlook e-mail application.
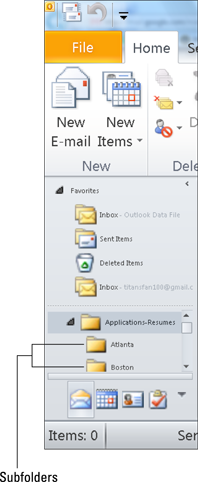
PST folders are visible in your Mail Folders pane in Outlook, as shown in Figure 6-1. Additional PST subfolders can be added to any of the default folders such as Deleted Items, Inbox, Drafts, and Sent Items, as shown in Figure 6-2.
PST folders can be created and structured to meet a user’s filing needs similar to the folder functionality that’s available with shared network drives and hard drives (as detailed in Chapter 5). After your PST folder structure has been developed, it allows you to conveniently click an e-mail and “drag and drop” it into a PST folder.
Work-arounds are available to the hard drive dilemma. PST files can be shared and accessed via your organization’s network drives. However, Microsoft has officially stated that it doesn’t support this approach due to the potential for the files to become corrupted. In addition, if you share your PST files, only one user at a time can access the information.

If you are concerned about backing up your PST files, you can download a Microsoft add-in that makes a copy of your PST files and saves them to a network drive. The download link is available at www.microsoft.com/en-us/download/details.aspx?id=9003.
Some organizational IT departments promote the use of PST folders because it reduces the amount of information on the e-mail server, and it allows employees to store more messages. However, in many cases, this methodology can be detrimental to your records and information management efforts. You should consider other e-mail message filing options in lieu of PST folders, as you discover in the next sections.
Figure 6-2: PST subfolders.
MSG can be good for your informational health
This section isn’t about food additives; it’s about a good option for filing e-mail messages. Another Microsoft file format is MSG. As you probably guessed, MSG stands for message. Most e-mail systems are configured (by default) to save e-mail messages to a hard drive or network drives as HTML (Hypertext Markup Language) files. In addition, this approach requires you to save any attachments separately. Using the MSG file extension allows you to save messages (plus attachments) as an e-mail to folders on hard drives and network drives.
You find several benefits to using the MSG file extension:
![]() Visibility: Applying the MSG extension to a message and saving it to a shared network drive allow other employees to search, retrieve, and view the e-mail. This promotes organizational knowledge sharing. In addition, it provides visibility to the subject matter in the event of a lawsuit or governmental inquiry.
Visibility: Applying the MSG extension to a message and saving it to a shared network drive allow other employees to search, retrieve, and view the e-mail. This promotes organizational knowledge sharing. In addition, it provides visibility to the subject matter in the event of a lawsuit or governmental inquiry.
![]() File backup: Saving e-mail messages by using the MSG file extension to a shared network drive ensures that the file is regularly backed up.
File backup: Saving e-mail messages by using the MSG file extension to a shared network drive ensures that the file is regularly backed up.
![]() Native format: When you retrieve an e-mail saved with an MSG file extension, it automatically invokes Microsoft Outlook, allowing you to work directly in the e-mail application. Messages saved with an MSG file extension keep the e-mail in its Microsoft Outlook format, retaining all the e-mail’s original metadata. This is important in the event that an e-mail has to be produced for a lawsuit or governmental inquiry.
Native format: When you retrieve an e-mail saved with an MSG file extension, it automatically invokes Microsoft Outlook, allowing you to work directly in the e-mail application. Messages saved with an MSG file extension keep the e-mail in its Microsoft Outlook format, retaining all the e-mail’s original metadata. This is important in the event that an e-mail has to be produced for a lawsuit or governmental inquiry.
Although using the MSG file extension approach does not provide drag-and-drop convenience, it does create consistency in the way that employees save electronic content. Saving a message by using the MSG extension is similar to saving a Microsoft Word document by using the DOC extension or a Microsoft Excel spreadsheet by using the XLS extension. Follow these steps to save an e-mail by using the MSG file extension:
1. Click the e-mail that you want to save.
Doing so highlights the e-mail.
2. Click the File tab and then select Save As.
The Save As screen appears.
3. Using the top panes of the Save As screen, select the network drive location where you want to save the file.
4. Click in the Save as Type drop-down menu.
The available file format types appear.
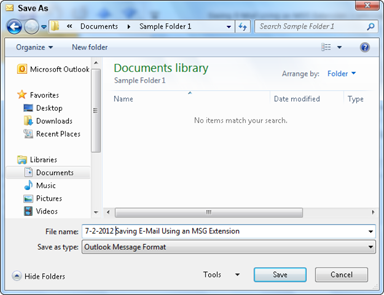
5. Choose the Outlook Message Format (*.msg) option from the Save as Type drop-down menu, as shown in Figure 6-3.
6. (Optional) Change the filename for the e-mail message in the File Name field, if desired.
7. Click Save.
Your e-mail message is saved in its new location in the new .msg format.
Figure 6-3: Using the MSG file extension to save e-mail.
Naming e-mail
E-mail messages and attachments should be named as you would any other electronic file you save — meaning that you should follow naming conventions designed so that you (or other employees) are able to retrieve the file at a moment’s notice without any fuss and bother. To ensure that e-mails can be quickly retrieved, it’s important to name the e-mail in a manner that allows its contents to be readily identified.
If you use PST folders to file your e-mail, the Subject line serves as your filename. However, sometimes the wording in the Subject line can be vague or cryptic, preventing you from easily identifying the e-mail’s contents. Microsoft Outlook allows you to easily edit the Subject line. Just follow these steps:
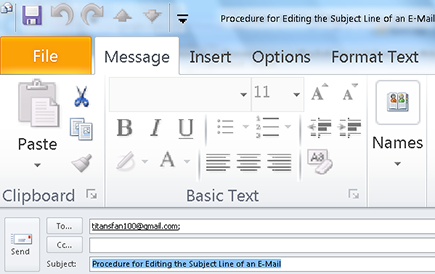
1. Open the e-mail whose Subject line you want to change, as shown in Figure 6-4.
2. Click the e-mail’s Subject line.
This highlights the current subject.
Figure 6-4: Highlighting the old Subject line.

3. Type the new subject in the highlighted Subject field.
The new subject overwrites the existing subject, as shown in Figure 6-5.
Figure 6-5: Coming up with a more informative Subject line.
4. Click the File tab and then select Close.
You can also click the X in the upper-right corner of the message window to save the change to the subject instead of clicking File and Close.
A message appears asking whether you want to save the change to the subject.
5. Click Yes.
Your e-mail has a new (and improved) Subject line.
If you’re saving files to a shared network drive by using an MSG extension, you have the ability to rename the file as you save it. Just do the following:
1. Click the e-mail that you want to save.
Doing so highlights the e-mail.
2. Click the File tab and then select Save As.
The Save As screen appears with the File Name box (containing the current name) highlighted.
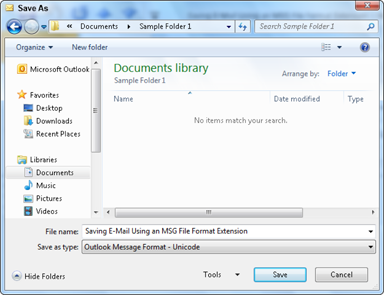
3. Type in the new name of the file.
Figure 6-6 gives an example of a more informative filename.
Figure 6-6: Naming files with an MSG file format extension.
4. Using the top panes of the Save As screen, select the network drive location where you want to save the file.
5. Click in the Save as Type drop-down menu.
The available file format types appear.
6. Choose the Outlook Message Format (*.msg) option from the Save as Type drop-down menu.
7. Click Save.
Using Software to Manage E-Mail
E-mail volume has increased at a staggering rate over the past decade and will continue to grow exponentially. It’s the number one information management challenge for most organizations. As the volume continues to increase, so does our need for finding more-effective ways to manage e-mail. The days where you could just use the functionality available in an e-mail application, PST folders, and shared network drives to manage e-mail are coming to an end.
Using software designed to specifically manage electronic content (including e-mail) is becoming more prevalent. This includes e-mail archiving, document management (DM), and enterprise content management (ECM) applications. When coupled with records management capabilities, these types of systems provide the ability to properly manage e-mail.
E-mail archiving systems
E-mail archiving software has been available for many years. It’s designed to extract e-mail messages and attachments, apply index values, and place the e-mail information in a read-only format in a separate database. The benefit of this approach is that it centralizes all e-mails, makes them accessible across the organization, and can assist in disaster recovery.
Optimizing with DM and ECM applications
A preferred option for managing your e-mails is to implement a document management (DM) or enterprise content management (ECM) system. These applications are designed to manage the life cycle of information. Using document and enterprise content management software provides the following benefits:
![]() Integration: Many DM and ECM applications integrate directly with e-mail systems such as Microsoft Outlook. This allows users to index and save e-mail to the software application while remaining in the e-mail system.
Integration: Many DM and ECM applications integrate directly with e-mail systems such as Microsoft Outlook. This allows users to index and save e-mail to the software application while remaining in the e-mail system.
![]() Metadata: Software provides the ability to assign additional metadata (index values) to an e-mail file. This allows significantly better search and retrieval capabilities.
Metadata: Software provides the ability to assign additional metadata (index values) to an e-mail file. This allows significantly better search and retrieval capabilities.
![]() Sharing: Enterprise content management systems are designed to make information available to the entire organization. This promotes knowledge sharing, better decision-making, and regulatory compliance.
Sharing: Enterprise content management systems are designed to make information available to the entire organization. This promotes knowledge sharing, better decision-making, and regulatory compliance.
![]() Records management: Document management and ECM systems equipped with records management functionality provide the ability to assign retention periods to e-mail based on content. This ensures that e-mail is only retained for a prescribed length of time and prevents the accumulation of unneeded information. DM and ECM applications can programmatically incorporate an organization’s record and information retention rules so that retention can be automatically managed.
Records management: Document management and ECM systems equipped with records management functionality provide the ability to assign retention periods to e-mail based on content. This ensures that e-mail is only retained for a prescribed length of time and prevents the accumulation of unneeded information. DM and ECM applications can programmatically incorporate an organization’s record and information retention rules so that retention can be automatically managed.
Note: The appendix, available online at www.dummies.com/go/records managefd, provides a listing of DM and ECM vendors and their contact information.

 The same concept applies to e-mail. E-mail is an electronic envelope that delivers digital content. Just like a paper envelope contains information such as a postmark (date sent) as well as the sender’s and recipient’s name, an e-mail envelope contains important information (metadata), some of which is readily visible, like sender, recipients, date and subject, and other information that is embedded in its properties.
The same concept applies to e-mail. E-mail is an electronic envelope that delivers digital content. Just like a paper envelope contains information such as a postmark (date sent) as well as the sender’s and recipient’s name, an e-mail envelope contains important information (metadata), some of which is readily visible, like sender, recipients, date and subject, and other information that is embedded in its properties. Prior to e-mail, many of us can remember the inbox that sat on our desk. If not managed, it could quickly fill up. The same holds true for our e-mail inbox. It’s essential to have a plan for dealing with incoming messages. Your inbox should not be used for storage or viewed as your “to-do” list; rather, think of it as a temporary processing location. After you have read an e-mail message you should take the “4D” approach — delete it, do it, delegate it, or defer it:
Prior to e-mail, many of us can remember the inbox that sat on our desk. If not managed, it could quickly fill up. The same holds true for our e-mail inbox. It’s essential to have a plan for dealing with incoming messages. Your inbox should not be used for storage or viewed as your “to-do” list; rather, think of it as a temporary processing location. After you have read an e-mail message you should take the “4D” approach — delete it, do it, delegate it, or defer it: You’ll soon encounter one major drawback to using PST folders: They typically store all information on your computer’s hard drive. Content located on a hard drive is only accessible if you have access to that specific computer. In addition, most hard drives do not have automatic backup capability, increasing the potential for lost information.
You’ll soon encounter one major drawback to using PST folders: They typically store all information on your computer’s hard drive. Content located on a hard drive is only accessible if you have access to that specific computer. In addition, most hard drives do not have automatic backup capability, increasing the potential for lost information.