Answers A, C, and E are correct. B is incorrect because data indicates that insider attacks are potentially more damaging than external attacks; for instance, insiders often have sufficient access to systems to inflict damage without password-cracking tools. D is incorrect because Cisco recommends exactly the opposite. When in doubt, read the manual!
Question 2
The correct answers are A, B, and C. Access control is considered a broad category of a network security policy and does not address specifics as to what types of devices it is applied to. This is why answers d and e are incorrect.
Question 3
Due Diligence—1, Due Care—2. Due diligence is more of a static, security preparation activity, whereas due care is a dynamic, ongoing process that involves day-to-day operations.
Question 4
Answers B, C, and D are correct. An axiom of network security is that production data traffic should never cross the cables of a hostile network. Putting a public server on an internal network segment shared by knowledge workers’ computers is lunacy—if the public server is compromised, it becomes a hostile system. The enemy is amongst us. Answer A is incorrect because even though the server is on a different switch port, the resulting segmentation is not proof against various types of switch infrastructure attacks (see also Chapter 10, “Protecting Switch Infrastructure”). Answer E is incorrect because, at a minimum, the server should be in a separate security zone. The IOS firewall cannot protect against insider attacks, which result from a compromised server.
Question 5
Answers A, D, and E are correct. Answers B and C are incorrect because they are examples of administrative controls.
Question 6
The correct answer is C. Answers A and D are made up and do not appear elsewhere in any network security context in this course. Answer B is deliberately misleading because management sounds like maintenance.
The correct answer is false. Scanners probe a network for vulnerabilities, whereas sensors monitor a network for signs of probes and attacks. IDSs and IPSs are sensors. (See also Chapter 8, “Network Security Using Cisco IOS IPS.”)
Question 8
False. Policies specify overall statements of direction including management’s position on security issues, but they don’t stipulate details of day-to-day operations. Procedures do.
Question 9
Cisco Security MARS—B; Cisco NAC Appliance—C; Cisco IPS Sensor—D; Cisco Security Management—A.
Question 10
False. This is a trick question. The concept of least privileges specifies that network security elements should have no more than the minimum privileges necessary to perform a task.
Question 11
Answers A and D are correct. This password protects the user mode on the router only. Furthermore, a security feature on Cisco routers refuses Telnet or SSH connections to the vtys if an enable password or enable secret has not also (but separately) been set. Answer B is incorrect per the preceding explanation. Answer C is incorrect because the enable password is set separately, and there is no automatic encryption of these passwords by default.
Question 12
True. The IOS enables you to create interim privilege levels (1–14) between user mode and enable mode where you can customize what commands are allowed to be issued at that level.
Question 13
False. Not all the files required to run the SDM are present. The sdm.tar file is missing.
The correct answer is A. The other answers don’t exist, are wrong, and moreover are tricky for someone who hasn’t studied the right command syntax.
Question 15
The correct answer is A. Answers b and c are incorrect because they specify authentication and accounting and not authorization. Answer D is just plain wrong.
Question 16
The correct answer is out-of-band. Care must be taken to ensure the integrity of the communication path between the syslog server and its clients; otherwise, data obtained might be legally inadmissible as evidence of a security breach.
Question 17
False. Although SNMP versions 1 and 2 are configurable by SDM, SNMP version 3 must be configured via CLI.
Question 18
The correct answer is B. A is incorrect because, even though the chosen fixes are automatically applied, the user has to decide which vulnerabilities have to be addressed in the first place, and this takes some knowledge. Answers C and D are incorrect because the definitions are incorrect.
Question 19
The answer is false. If you later want to undo some of the changes, you can run the Security Audit wizard again and select Undo Security configurations.
Question 20
The correct answers are A and B, respectively. Answers C, D, and E are incorrect because access to the virtual terminal lines, console port, and auxiliary ports have no effect on network access, only access to the router itself. Answer F is incorrect because CDP is enabled by default.
Answers A, B, C, and D are correct. Answer E is incorrect because the opposite is true; firewalls can even sanitize protocols in some cases.
Question 22
The correct answers are A, C, and E. ACLs cannot be used to mitigate tunneled applications because ACLs do not operate above the Transport layer. MAC address table overflow attacks cannot be mitigated against with ACLs either. (See Chapter 10, “Protecting Switch Infrastructure,” for details of how to mitigate this and other types of layer 2 attacks.)
Question 23
Question 24
The correct choices are A and C. The three main categories of actions that ZPF can take on traffic are inspect, drop, and pass.
Question 25
False. The class map IM_and_P2P_Traffic pictured filters on native IM and P2P traffic. Filtering services tunneled inside HTTP is outside the scope of this Exam Cram.
Question 26
The correct answers are D and E, respectively. Encryption can occur at other layers of the OSI model as well.
The correct answer is E. PKI defines a whole protocol for the secure issuance, exchange, revocation, destruction, storage, and backup of digital certificates and integral asymmetric keys used for device and individual authentication and encryption. Answers a through d are incorrect because PKI neither provides for encryption nor does it specify a specific cryptosystem. It simply makes the management of the credentials and keys used easier.
Question 28
Answer D is correct because Hashing Message Authentication Codes (HMACs) not only assure that the 1’s and 0’s haven’t changed in transit between the transmitter and the receiver (integrity), but that they uniquely and only came from the transmitter (origin authentication). Answers A, B, and C are incorrect for this reason. Answer E is incorrect because there is no guaranteed delivery provided by HMACs.
Question 29
Question 30
Answers A, B, and C are correct. Answer D is incorrect because a subordinate CA exists within a hierarchical CA model. Answer E is incorrect because this terminology doesn’t exist.
Question 31
Respectively, the answers are remote-access, IPSec, network, remote-access, SSL, and transport.
Question 32
The correct answers are D, E, and F. All three are supported on Cisco security appliances and PSKs, and RSA signatures only are supported on Cisco IOS routers. Answers A and B are incorrect because they use a mashup of existing terminology such as RSA and HMAC in an attempt to mislead. Answer C is incorrect because DH stands for Diffie-Hellman, and DH is not used for authentication in any case. It is used to create a shared encryption key in-band over a hostile network.
The correct answers are ESP and 50, respectively. Authentication Header (AH) is encapsulated in IP packets as protocol 51 traffic and does not provide encryption. Encapsulating Security Payload (ESP), on the other hand, provides for encryption of the payload and is encapsulated in IP packets as protocol 50.
NOTE
This might sound like trivia, but actually it is important to remember. Because ESP and AH don’t use TCP or UDP for transport, a packet might be dropped by a router that performs Port Address Translation (PAT). No port number = no translation.
Question 34
The correct answers are C, D, and E. Answer a is incorrect because the IP address specified in the crypto map is that of the remote peer. Answer B is incorrect because the transform set name, CantHackMe, is of local significance only. The transform set’s values and not its name are transmitted during quick mode.
Question 35
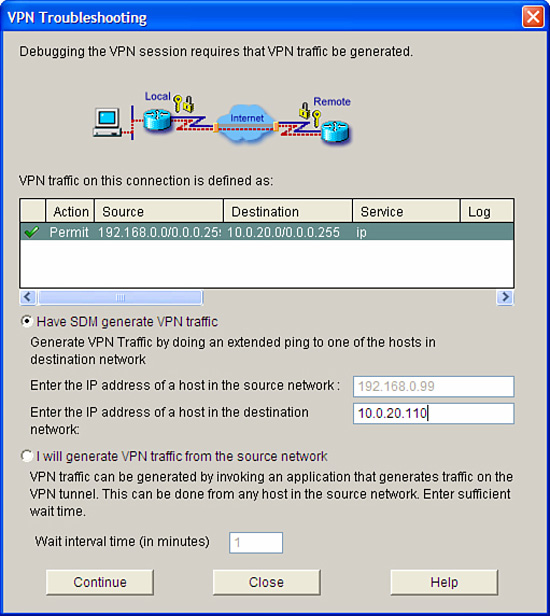
True. See the following figure and also Figure 7.19. You can have SDM generate VPN traffic or you can generate the VPN traffic from the source network yourself and ask SDM to wait a specific interval before it tests the status of the tunnel again.
The correct answers are B, D, and E. Answer A is incorrect because an IPS is deployed inline with traffic and does not simply monitor copies of the data flow in the way that an IDS does. Similarly, answer C is incorrect because an IPS sees all packets including the trigger packets in an attack.
Question 37
False. The Cisco IOS IPS is an inline network IPS.
Question 38
The correct answer is A. Curiously, this button does not launch a wizard where you can change the signatures. The word “rule” in this context means “policy.” Your intuition probably tells you that answer B would be correct, but this is not the case. This is something to watch for on the exam.
Question 39
The correct answer is C. Answer A is incorrect because this is what the Produce Verbose Alert action does. Answer B is incorrect because this is what the Request SNMP Trap action does. Answer D is incorrect because this is what the Log Victim Packets action does. These actions are in the “IPS Attack Responses” section of Chapter 8 and should all be memorized for the exam.
Question 40
The correct answers are A, B, D, and E. Answer C is incorrect because one of SDEE’s features is that it is not proprietary.
Question 41
The correct answers are C, D, and D, respectively. Answer A is incorrect because “host” in the context of Cisco’s Host Security Strategy refers to an endpoint. Answer B is incorrect because a network isn’t a software element. Answer e is incorrect because while drivers are software, they, like applications, function in the environment provided by the operating system.
The correct answers are: 1—A; 2—C; 3—B.
Question 43
The correct answer is C. Answer A is incorrect as it describes FCIP (Fiber Channel over IP). Answer B is incorrect as it describes Fiber Channel. Answer D is incorrect because it is a made-up answer that sounds like it might be right!
Question 44
Answer D is correct. The other choices are standards-based protocols and thus incorrect.
Question 45
The correct answers are A, C, and D. Answer B is incorrect because 802.1Q trunking is required to separate the VVLAN from the data VLAN for QoS and security reasons. Answer E is incorrect because SIP stands for Session Initiation Protocol and Cisco makes no specific recommendation about it in this context.
Question 46
The correct answers are B and C. Answer B is correct because this command manually enables trunking. Answer C is correct because this command turns off autonegotiation of trunks. Answer A is incorrect because this command specifies that this port should be in access mode (wrong!), but doesn’t turn off autonegotiation in any case (as with answer C). Answers D and E are incorrect because these commands don’t exist.
Question 47
The correct answers are A, B, and C. Answer D is incorrect because this feature doesn’t exist. Answer e is incorrect because PVST+ defines a protocol for rapid spanning tree convergence per VLAN and does not specifically mitigate an STP manipulation attack. It is a red herring and is found nowhere in this Exam Cram but is part of the CCNA curriculum.
False. Port security is only appropriate on access ports because, unlike trunks between switches, shutting down these ports only results in loss of connection to a finite number of attached stations. If this logic fails to sway you, you should know that port security can’t be configured on trunk ports because the IOS won’t let you.
Question 49
The correct answers are C, D, and E. Answer a and b are incorrect because poor cabling and EMI issues are more likely to cause much more general failures and certainly not broadcast storms.
Question 50
True. This is why you must take great care in making sure that putting this switch port in portfast mode doesn’t inadvertently create a topological loop.
