|
True or false. An IDS is a passive technology that only reports when events trigger signatures, whereas an IPS not only reports but also blocks the intrusion. |
||||||||||||||||
|
2. |
Which in the following list are examples of where an IDS or IPS may be deployed? (Choose all that apply.)
|
|||||||||||||||
|
3. |
Match the list of IPS technologies below with the letter corresponding to the platform to which it belongs. Letters may be used more than once.
Choices: A. ASA 5500 Series Adaptive Security appliances B. Catalyst 6500 Series switches C. Cisco IOS router |
|||||||||||||||
|
4. |
Which of the following is part of Cisco’s suite of IPS Management Software? (Choose one correct answer.)
|
|||||||||||||||
|
5. |
Fill in the blank. Cisco _____ Agent is Cisco’s Host IPS (HIPS) software solution.
|
|||||||||||||||
|
6. |
Which of the following is not considered an advantage of Network IPS? (Choose all that apply.)
|
|||||||||||||||
|
7. |
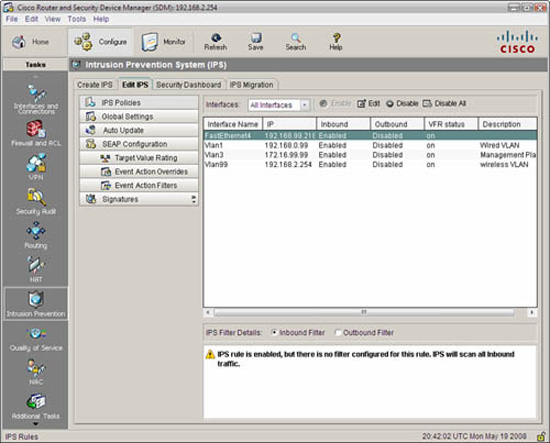
Review the information in Figure 8.27. Which of the following statements is correct about the information it contains? (Choose all that apply.) |
|||||||||||||||
|
8. |
Fill in the blanks in the following sentence with a choice from the list below. The IPS signature file that you download to your PC will end with a _____ file extension, whereas the file that you push to the IOS IPS will end with a _____ file extension. Both can be downloaded from Cisco.
|
|||||||||||||||
|
9. |
View the CLI output below of an incomplete IPS configuration. Which of the following statements best describes what is missing? ip ips config location flash:/ips/ retries 1
|
|||||||||||||||
|
10. |
True or false. SDEE is a push-logging protocol that can optionally use encryption, whereas syslog uses a pull-logging protocol. |
Answers to Exam Prep Questions
|
1. |
False. This is a bit of a trick question. What makes an IDS an intrusion detection system is that it might miss trigger packets from an attack because it is not inline to the traffic like an IPS. An IDS might be able to block attacks after they have started. |
|
2. |
The correct answers are A, B, and C. There is no IPS or IDS add-on module for the concentrator. |
|
3. |
The correct answers are: 1—A; 2—B; 3—C; 4—C. |
|
4. |
The correct answer is E. |
|
5. |
The correct answer is D. |
|
6. |
The correct answers are C and D. C is correct because one of the advantages of a network IPS is that you don’t have to deploy it on every end system in the network. D is also correct because one of the disadvantages of network IPS is that they are blind to encrypted data. Only a Host IPS (HIPS) can see the data in the encrypted data stream because they operate above the network and transport layers where encryption occurs. (Review Chapter 7, “Virtual Private Networks with IPsec,” if you’re not sure about this last point.) |
|
7. |
The correct answers are B and C. Answer A is incorrect because the notice in the bottom pane of the Edit IPS screenshot just means what it says—all inbound traffic will be scanned by the IPS since no filter is set. The word “inbound” is with respect to the interface itself and has nothing to do with zones and zone pairs and levels of trust. Answer D is incorrect because this screen is used to verify that IPS is enabled on the interfaces. You can see that all the interfaces have an IPS policy enabled in the inbound direction. |
|
8. |
The correct answer is A. When you elect to download the signature files from CCO in the course of configuring the IOS IPS, the Create IPS Wizard will ask you if you want to push the files to the router in addition to downloading them to your local PC. The file names that are pushed to the router are in the form of IOS-Sxxx-CLI.pkg, and the file names that are downloaded to your PC are in the form of sigv5-SDM-Sxxx.zip, where xxx is the version number of the signature set. |
|
9. |
The correct answer is D. Answers A and B are incorrect because the basic signature category is for Cisco IOS IPS routers, which have less than 128MB of DRAM. This doesn’t turn off the inline nature of the IPS either, so trigger packets (at least in the applied signatures) will not be missed. Answer C is incorrect because the word “retired” in the CLI output refers to whether retired signatures are used in a certain category. Answer E is incorrect because the IPS policy is only applied to interfaces and not globally to the entire device. Here is an example of a complete configuration. Note that the IPS policy sdm_ips_rule has been applied in the inbound direction to interfaces Vlan1 and FastEthernet4: ip ips config location flash:/ips/ retries 1 |
|
10. |
False. One of SDEE’s strengths is that it is a pull protocol that can optionally use HTTPS (vs. HTTP) for transport for encryption. Syslog is unencrypted, uses UDP port 514 for transport, and is a push protocol, meaning that a syslog server cannot query the IPS for alert message entries unlike SDEE. |