In Chapter 11 a detailed planning process for an Office Communications Server 2007 deployment of a fictitious global company named Contoso was presented. It's been demonstrated how to use the Office Communications Server 2007 Planning Guide and the Office Communications Server 2007 Enterprise Voice Planning and Deployment Guide to design a multi-pool Office Communications Server 2007 deployment with several different scenarios enabled. The aim of the example in this chapter is to develop a deployment path for the entire Contoso architecture. The focus of this chapter will therefore be on the demonstration of all preparation steps that have to be taken before Contoso can be deployed, as well as on the deployment sequence. How to install every individual Office Communications Server 2007 Server role is explained in the various Office Communications Server 2007 deployment guides.
Contoso's deployment of Office Communications Server 2007 is a complex example of an Office Communications Server 2007 deployment created to show the possible difficulties administrators might face when designing the right deployment path for such architecture. In particular, when several scenarios are enabled at one time for such a deployment, the time required can be lowered by first doing all preparation steps—such as developing a server naming convention, preparing Domain Name System (DNS) entries, creating certificates, installing and configuring network interface cards (NICs)—and then proceeding with the actual deployment. This approach saves you from having to come back to the preparation of the environment after each step. The advantage in doing all the server preparation up front is that when you deploy server roles later in your deployment path (for example, when deploying the Edge Server after you have set up the pool), you don't have to ask DNS administrators to do further entries for the Edge Server deployment because you already spoke with them a few days earlier when you deployed the pool. In particular, in large customer environments where multiple administrators are involved, the deployment process will become much smoother. There might be several answers to the questions "Where should I start?" and "What should I do next?" However, in this chapter a deployment path for Contoso is shown that can be seen as the Best Practice guidance for similar Office Communications Server 2007 deployments.
At first, it is important to define the naming convention for all servers Contoso wants to deploy. To choose a naming convention that is easily understandable to all organizations involved in the deployment is essential because it decreases the possibility of miscommunication. As Table 12-1 shows, Contoso chooses a naming convention for its servers that easily identifies each of the Office Communications Server 2007 roles and their locations.
Table 12-1. Contoso's Server Naming Convention
Attribute | Naming Convention |
|---|---|
Server name | XXXYYYZZ |
Server-FQDN (fully qualified domain name) | xxxyyyzz.contoso.com |
XXX | Server roles are abbreviated as follows:
|
YYY | Server locations are abbreviated as follows: |
ZZ | Role number (if this is missing, the server is a Load Balancer) |
Note that some exceptions to this naming convention exist for non–Office Communications Server 2007 roles, such as Load Balancers.
Table 12-2 through Table 12-5 show the Server names, IP addresses, and FQDNs for the servers for the four Contoso sites.
Table 12-2. Contoso Server Names for Chicago
Server Role | Server Name | IP Address | Server FQDN |
|---|---|---|---|
Pool Name | CHIPOOL01 | 10.18.10.1 | chipool01.contoso.com |
Load Balancer virtual IP (VIP) for Office Communications Server 2007 Enterprise Edition (EE) Front End Servers | FRECHI | 10.18.10.1 | frechi.contoso.com |
EE expanded Front End Server | FRECHI01 | 10.18.10.2 | frechi01.contoso.com |
EE expanded Front End Server | FRECHI02 | 10.18.10.3 | frechi02.contoso.com |
EE expanded Front End Server | FRECHI03 | 10.18.10.4 | frechi03.contoso.com |
EE expanded Front End Server | FRECHI04 | 10.18.10.5 | frechi04.contoso.com |
EE expanded Front End Server | FRECHI05 | 10.18.10.6 | frechi05.contoso.com |
EE expanded Front End Server | FRECHI06 | 10.18.10.7 | frechi06.contoso.com |
Back End SQL cluster name | SQLCHI01 | 10.18.10.10 | sqlchi01.contoso.com |
Back End Nodes | BAECHI01 | 10.18.10.11 | baechi01.contoso.com |
Back End Nodes | BAECHI02 | 10.18.10.12 | baechi02.contoso.com |
Load Balancer VIP for Internet Information Services (IIS) | IISCHI | 10.18.10.15 | iischi.contoso.com |
IIS | IISCHI01 | 10.18.10.16 | iischi01.contoso.com |
IIS | IISCHI02 | 10.18.10.17 | iischi02.contoso.com |
Web Conferencing Server | WCSCHI01 | 10.18.10.20 | wcschi01.contoso.com |
Web Conferencing Server | WCSCHI02 | 10.18.10.21 | wcschi02.contoso.com |
Web Conferencing Server | WCSCHI03 | 10.18.10.22 | wcschi03.contoso.com |
Web Conferencing Server | WCSCHI04 | 10.18.10.23 | wcschi04.contoso.com |
A/V Conferencing Server | AVCCHI01 | 10.18.10.24 | avcchi01.contoso.com |
A/V Conferencing Server | AVCCHI02 | 10.18.10.25 | avcchi02.contoso.com |
A/V Conferencing Server | AVCCHI03 | 10.18.10.26 | avcchi03.contoso.com |
A/V Conferencing Server | AVCCHI04 | 10.18.10.27 | avcchi04.contoso.com |
Director Pool Name | CHIDIRPOOL | 10.18.10.32 | chidirpool.contoso.com |
Load Balancer VIP for Directors (internal-facing pool) | DIRCHI | 10.18.10.32 | dirchi.contoso.com |
Director (internal NIC) | DIRCHI01 | 10.18.10.30 | dirchi01.contoso.com |
Director (external NIC) | — | 10.18.10.130 | — |
Director (internal NIC) | DIRCHI02 | 10.18.10.31 | dirchi02.contoso.com |
Director (external NIC) | — | 10.18.10.131 | — |
Load Balancer VIP for Directors (external-facing Edge Server) | — | 10.18.10.33 | dirchiext.contoso.com |
Load Balancer VIP for Edge Access Server (internal) | CAWCHI | 192.168.10.40 | access.contoso.com |
Co-located Access Edge Server and Web Conferencing Edge Server (internal NIC) | CAWCHI01 | 192.168.10.41 | cawchi01.contoso.com |
Co-located Access Edge Server and Web Conferencing Edge Server (external NIC) | — | 64.65.66.3 | — |
Co-located Access Edge Server and Web Conferencing Edge Server (internal NIC) | CAWCHI02 | 192.168.10.42 | cawchi02.contoso.com |
Co-located Access Edge Server and Web Conferencing Edge Server (external NIC) | — | 64.65.66.4 | — |
Load Balancer VIP for Edge Access Server (external) | — | 64.65.66.1 | sip.contoso.com |
Load Balancer VIP for Edge Web Conferencing Server (external) | — | 64.65.66.2 | wcechi.contoso.com |
Load Balancer VIP for A/V Edge Server (internal) | AVECHI | 192.168.10.45 | avechi.contoso.com |
A/V Edge Server (internal NIC) | AVECHI01 | 192.168.10.46 | avechi01.contoso.com |
A/V Edge Server (external NIC) | — | 64.65.66.16 | — |
A/V Edge Server (internal NIC) | AVECHI02 | 192.168.10.47 | avechi02.contoso.com |
A/V Edge Server (external NIC) | — | 64.65.66.17 | — |
Load Balancer VIP for A/V Edge Server (external) | — | 64.65.66.15 | avechi.contoso.com |
Mediation Server (internal NIC) | MEDCHI01 | 10.18.10.50 | medchi01.contoso.com |
SIP/PSTN Gateway (external to Mediation Server) | — | 10.18.10.51 | gwychi01.contoso.com |
HTTP Reverse Proxy Server (internal NIC) | HTTCHI01 | 192.168.10.60 | httchi01.contoso.com |
HTTP Reverse Proxy Server (external NIC) | — | 64.65.66.30 | httchi01.contoso.com |
Table 12-3. Contoso Server Names for Paris
Server Role | Server Name | IP Address | Server FQDN |
|---|---|---|---|
Pool Name | PARPOOL01 | 10.17.10.1 | parpool01.contoso.com |
Load Balancer VIP for EE Front End Servers | FREPAR | 10.17.10.1 | frepar.contoso.com |
EE expanded Front End Server | FREPAR01 | 10.17.10.2 | frepar01.contoso.com |
EE expanded Front End Server | FREPAR02 | 10.17.10.3 | frepar02.contoso.com |
EE expanded Front End Server | FREPAR03 | 10.17.10.4 | frepar03.contoso.com |
EE expanded Front End Server | FREPAR04 | 10.17.10.5 | frepar04.contoso.com |
Back End SQL cluster name | SQLPAR01 | 10.17.10.10 | sqlpar01.contoso.com |
Back End Nodes | BAEPAR01 | 10.17.10.11 | baepar01.contoso.com |
Back End Nodes | BAEPAR02 | 10.17.10.12 | baepar02.contoso.com |
Load Balancer VIP for IIS | IISPAR | 10.17.10.15 | iispar.contoso.com |
IIS | IISPAR01 | 10.17.10.16 | iispar01.contoso.com |
IIS | IISPAR02 | 10.17.10.17 | iispar02.contoso.com |
Web Conferencing Server | WCSPAR01 | 10.17.10.20 | wcspar01.contoso.com |
Web Conferencing Server | WCSPAR02 | 10.17.10.21 | wcspar02.contoso.com |
A/V Conferencing Server | AVCPAR01 | 10.17.10.24 | avcpar01.contoso.com |
A/V Conferencing Server | AVCPAR02 | 10.17.10.25 | avcpar02.contoso.com |
Load Balancer VIP for Web Conferencing Server (internal) | WCEPAR | 192.167.10.40 | wcepar.contoso.com |
Web Conferencing Edge Server (internal NIC) | WCEPAR01 | 192.167.10.41 | wcepar01.contoso.com |
Web Conferencing Edge Server (external NIC) | — | 64.64.66.11 | — |
Web Conferencing Edge Server (internal NIC) | WCEPAR02 | 192.167.10.42 | wcepar02.contoso.com |
Web Conferencing Edge Server (external NIC) | — | 64.64.66.12 | — |
Load Balancer VIP for Web Conferencing Server (external) | — | 64.64.66.10 | wcepar.contoso.com |
Load Balancer VIP for A/V Edge Server (internal) | AVEPAR | 192.167.10.45 | avepar.contoso.com |
A/V Edge Server (internal NIC) | AVEPAR01 | 192.167.10.46 | avepar01.contoso.com |
A/V Edge Server (external NIC) | — | 64.64.66.16 | — |
A/V Edge Server (internal NIC) | AVEPAR02 | 192.167.10.47 | avepar02.contoso.com |
A/V Edge Server (external NIC) | — | 64.64.66.17 | — |
Load Balancer VIP for A/V Edge Server (external) | — | 64.64.66.15 | avepar.contoso.com |
HTTP Reverse Proxy Server (internal NIC) | HTTPAR01 | 192.167.10.60 | httpar01.contoso.com |
HTTP Reverse Proxy Server (external NIC) | — | 64.64.66.30 | httpar01.contoso.com |
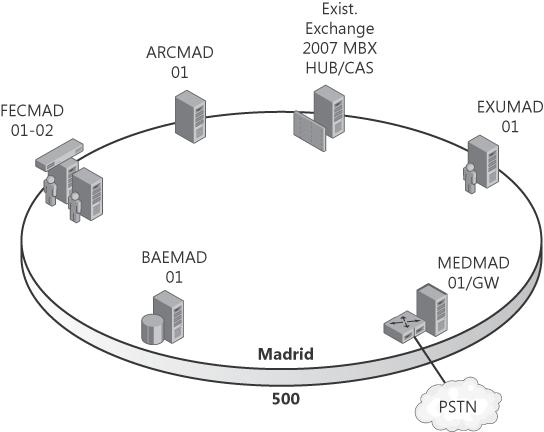
Table 12-4. Contoso Server Names for Madrid
Server Role | Server Name | IP Address | Server FQDN |
|---|---|---|---|
Pool Name | MADPOOL01 | 10.16.10.1 | madpool01.contoso.com |
Load Balancer VIP for EE Front End Servers | FREMAD | 10.16.10.1 | fremad.contoso.com |
EE consolidated Front End Server | FECMAD01 | 10.16.10.2 | fecmad01.contoso.com |
EE consolidated Front End Server | FECMAD02 | 10.16.10.3 | fecmad02.contoso.com |
Back End Nodes | BAEMAD01 | 10.16.10.11 | baemad01.contoso.com |
Mediation Server (internal NIC) | MEDMAD01 | 10.16.10.50 | medmad01.contoso.com |
SIP/PSTN Gateway (external to Mediation Server) | — | 10.16.10.51 | gwymad01.contoso.com |
Exchange Unified Messaging (UM) Server | EXUMAD01 | 10.16.10.70 | exumad01.contoso.com |
Archiving Server | ARCMAD01 | 10.16.10.80 | arcmad01.contoso.com |
Note
It is possible to install only one SQL database in Madrid and store Back End database data as well as the archiving data in the same database.
Table 12-5. Contoso Server Names for Singapore
Server Role | Server Name | IP Address | Server FQDN |
|---|---|---|---|
Pool Name | SPOPOOL01 | 10.15.10.1 | spopool01.contoso.com |
Load Balancer VIP for EE Front End Servers | FRESPO | 10.15.10.1 | frespo.contoso.com |
EE consolidated Front End Server | FECSPO01 | 10.15.10.2 | fecspo01.contoso.com |
EE consolidated Front End Server | FECSPO02 | 10.15.10.3 | fecspo02.contoso.com |
EE consolidated Front End Server | FECSPO03 | 10.15.10.4 | fecspo03.contoso.com |
EE consolidated Front End Server | FECSPO04 | 10.15.10.5 | fecspo04.contoso.com |
Back End Nodes | BAESPO01 | 10.15.10.11 | baespo01.contoso.com |
Load Balancer VIP for Web Conferencing Server (internal) | WCESPO | 192.165.10.41 | wcespo.contoso.com |
Web Conferencing Edge Server (internal NIC) | WCESPO01 | 192.165.10.41 | wcespo01.contoso.com |
Web Conferencing Edge Server (external NIC) | — | 64.62.66.11 | wcespo01.contoso.com |
Load Balancer VIP for A/V Edge Server (internal) | AVESPO | 192.165.10.46 | avespo.contoso.com |
A/V Edge Server (internal NIC) | AVESPO01 | 192.165.10.46 | avespo01.contoso.com |
A/V Edge Server (external NIC) | — | 64.62.66.16 | avespo01.contoso.com |
Each Contoso Server role requires dedicated server hardware, as described in the Office Communications Server 2007 Planning Guide. From a performance perspective, none of the server roles handling media should be installed on virtual machines. When preparing server hardware for an Office Communications Server 2007 deployment, the required number of NICs in each server should be checked. Table 12-6 through Table 12-23, found later in this chapter, show where Contoso needs multiple NICs, as required by the server roles.
Contoso decided to enable several scenarios with a high level of redundancy for its users. This resulted in a high number of individual servers and server roles needing to be deployed. Figure 12-1 through Figure 12-4 provide a graphical view of the target deployment for each of the Contoso sites.
Contoso will perform the Active Directory schema update as the initial step for its Office Communications Server 2007 deployment.
Contoso decided to install the entire Office Communications Server 2007 deployment in a single domain (Contoso.com) because domain controllers are available in each of the sites. The "Office Communications Server 2007 Active Directory Guide" explains in detail the steps that have to be taken to prepare Active Directory for an Office Communications Server 2007 deployment.
Important
Active Directory schema updates need to be well-controlled events by the Active Directory administrators because they can affect the entire enterprise's directory infrastructure. Therefore, it is understandable that the Active Directory preparation in an Office Communications Server 2007 deployment has to be coordinated with the Active Directory administrators. Depending on the enterprise and its business, there can be periods where an Active Directory schema update is not allowed by company policy and therefore the Office Communications Server 2007 deployment can be significantly delayed. The effects of such policies on the deployment schedule have to be incorporated into the deployment plan.
In large enterprises, the configurations of DNS, certificates, and firewalls are sometimes organizationally separated from the Office Communications Server 2007administrators who install and configure Office Communications Server 2007 and collaborate with other administrators in the company. Even the setup of servers can be performed by people other than the Office Communications Server 2007 administrators, so clear requirements have to be communicated to each organization within the enterprise to avoid interruptions of the deployment process because of missing prerequisites.
As part of Contoso's Office Communications Server 2007 planning process, the number of individual server roles has been identified as shown in Chapter 11. This allows Contoso to summarize all DNS and Firewall port requirements so that the preparation of the surrounding infrastructure can be done at one time before the actual deployment takes place. Table 12-6 through Table 12-23 summarize all preparations that need to be done for Contoso's Office Communications Server 2007 deployment. In addition to the summary views of the infrastructure requirements for each site, a detailed view with all the infrastructure requirements—including certificate requirements for Chicago—will be shown later in the chapter.
Table 12-6 provides a summary of Contoso's infrastructure requirements for Chicago.
Table 12-6. Summary of Chicago Infrastructure Requirements
Note that in Table 12-6, a total of seven IP addresses are used that point to the same two physical servers (the Access Edge Server and the Web Conferencing Edge Server). Here is a summary to further clarify the addressing scheme for these servers:
One IP address for the Access Edge VIP (externally) = 64.65.66.1
One IP address for the Access Edge VIP (internally) = 192.168.10.40
One IP address for the Web Conferencing Edge VIP (externally) = 64.65.66.2
Two IP addresses for the Web Conferencing Edge (externally) = 64.65.66.3 and 64.65.66.4 (these addresses are the node addresses and the VIPs point to them)
Two IP addresses for the Web Conferencing Edge (internally) = 192.168.10.41 and 192.168.10.42 (since no Load Balancing of the Web Conferencing Edge roles is allowed internally)
Table 12-7 through Table 12-9 provide detailed views of the infrastructure requirements for the Access Edge Server and Web Conferencing Edge Server arrays in the Chicago perimeter network. An array is a set of servers running the same server roles.
Table 12-7. Details for Chicago—External Load Balancer for Co-located Access Edge Servers and Web Conferencing Edge Servers
Role/Feature | Quantity/Value(s) | Location/Setting | Note/Example |
|---|---|---|---|
Load Balancer | |||
Access Edge Server | sip.contoso.com | Perimeter Network | Externally facing hardware Load Balancer with 2 VIPs. |
Web Conferencing Edge Server | wcechi.contoso.com | ||
VIPs | |||
Access Edge Server VIP (external) | (1) 64.65.66.1 | 100-Mb Full | Virtual IP Address on the external Load Balancer for array of Access Edge Servers. |
Web Conferencing Edge Server VIP (external) | (1) 64.65.66.2 | 100-Mb Full | Virtual IP Address on the external Load Balancer for array of Web Conferencing Edge Servers. |
Ports | |||
Firewall (external) |
5061 TCP | Inbound Bi-directional | Traffic from Internet → Access Edge Server external Load Balancer VIP (sip.contoso.com) and Web Conferencing Edge Server external Load Balancer VIP (wcechi.contoso.com). |
Traffic to/from Internet ↔ Access Edge Server external Load Balancer VIP (sip.contoso.com). | |||
Certificates | |||
Certificate Name (CN)/Subject Name (SN) | N/A | N/A | N/A |
DNS (Internal) | |||
(A) | N/A | N/A | N/A |
(A) | sip.contoso.com | 64.65.66.1 | |
(A) | wcechi.contoso.com | 64.65.66.2 | |
Table 12-8. Details for Chicago—Internal Load Balancer for Co-located Access Edge Servers and Web Conferencing Edge Servers
Table 12-9. Details for Chicago—Access Edge Servers and Web Conferencing Edge Servers
Table 12-10 through Table 12-12 provide detailed views of the infrastructure requirements for the A/V Edge Server arrays in the Chicago perimeter network.
Table 12-10. Details for Chicago—External Load Balancer for A/V Edge Servers
Table 12-11. Details for Chicago—Internal Load Balancer for A/V Edge Servers
Table 12-12. Details for Chicago—A/V Edge Servers
Table 12-13 provides a detailed view of the infrastructure requirements for the HTTP Reverse Proxy Server in the Chicago perimeter network.
Table 12-13. Details for Chicago—HTTP Reverse Proxy Server
Table 12-14 through Table 12-16 provide detailed views of the infrastructure requirements for the Director Servers in Chicago.
Table 12-14. Details for Chicago—External Load Balancer for Director Servers
Table 12-15. Details for Chicago—Internal Load Balancer for Director Servers
Role/Feature | Quantity/Value(s) | Location/Setting | Note/Example |
|---|---|---|---|
Load Balancer | |||
Director | dirchi.contoso.com | Internal network | Internally facing hardware Load Balancer with 1 VIP. |
VIPs | |||
Director VIP (internal) | (1) 10.18.10.32 | 100-Mb Full | Virtual IP Address on the internal-facing Load Balancer for array of Director Servers. |
Ports | |||
Firewall (internal) | N/A | N/A | N/A |
Certificates | |||
CN/SN | N/A | N/A | N/A |
DNS (Internal) | |||
(A) | dirchi.contoso.com | 10.18.10.32 | |
DNS (External) | |||
(A) | N/A | N/A | N/A |
Table 12-16. Details for Chicago—Director Server Array
Table 12-17 and Table 12-18 provide detailed views of the infrastructure requirements for the expanded Office Communications Server 2007 Enterprise Edition pool in Chicago.
Table 12-17. Details for Chicago—Internal Load Balancer for Office Communications Server 2007 Enterprise Edition Front End Server Pool
Table 12-18. Details for Chicago—Office Communications Server 2007 Enterprise Edition Front End Servers
Table 12-19 provides a detailed view of the infrastructure requirements for the Back End SQL cluster in the Chicago pool.
Table 12-19. Details for Chicago—Back End SQL Cluster
Role/Feature | Quantity/Value(s) | Location/Setting | Note/Example |
|---|---|---|---|
Server | |||
SQL Server 2005 Cluster | sqlchi01.contoso.com | Internal network | This is the virtual name for the SQL Server 2005 cluster. |
Node1 | BAECHI01 | Internal network | Domain member SQL Server (EE Pool back end). |
Node2 | BAECHI02 | Internal network | Domain member SQL Server (EE Pool back end). |
NICs | |||
|
Node2 (internal) | (1) 10.18.10.11 (1) 10.18.10.12 | 100-Mb Full 100-Mb Full | |
Ports | |||
Internal | N/A | ||
Certificates | |||
CN/SN | N/A | ||
DNS (Internal) | |||
(A) | sqlchi01.contoso.com | 10.18.10.10 | This is the internal FQDN of the SQL Server 2005 cluster. |
(A) | baechi01.contoso.com | 10.18.10.11 | This is the internal FQDN of the SQL Server 2005 Node1. |
(A) | baechi01.contoso.com | 10.18.10.12 | |
DNS (External) | |||
(A) | N/A | ||
Table 12-20 and Table 12-21 provide detailed views of the infrastructure requirements for the IIS Web Content Server array in Chicago.
Table 12-20. Details for Chicago—Internal Load Balancer for IIS Web Content Server Array
Role/Feature | Quantity/Value(s) | Location/Setting | Note/Example |
|---|---|---|---|
Load Balancer | |||
IIS Web Content Server | iischi.contoso.com | Hardware Load Balancer with 1 VIP. | |
VIPs | |||
EE Pool VIP (internal) | (1) 10.18.10.15 | 100-Mb Full | Virtual IP Address on the Load Balancer for the IIS Web content servers. |
Ports | |||
Firewall (internal) | N/A | N/A | N/A |
Certificates | |||
CN/SN | N/A | N/A | N/A |
DNS (Internal) | |||
(A) | iischi.contoso.com | 10.18.10.15 | |
DNS (External) | |||
(A) | N/A | N/A | N/A |
Table 12-21. Details for Chicago—IIS Web Content Server Array
Role/Feature | Quantity/Value(s) | Location/Setting | Note/Example |
|---|---|---|---|
Server | |||
IIS Web Content Server | |||
Node1 | IISCHI01 | Internal network | Domain member IIS Server (Web Content). |
Node2 | IISCHI02 | Internal network | Domain member IIS Server (Web Content). |
NICs | |||
Node1 (internal) | (1) 10.18.10.16 | 100-Mb Full | |
Node2 (internal) | (1) 10.18.10.17 | 100-Mb Full | |
Ports | |||
Internal | N/A | ||
Certificates | |||
N/A | |||
DNS (Internal) | |||
(A) | iischi01.contoso.com | 10.18.10.16 | |
(A) | iischi01.contoso.com | 10.18.10.17 | |
DNS (External) | |||
(A) | N/A | The IIS Web Content Server is not addressable externally. | |
Table 12-22 provides a detailed view of the infrastructure requirements for the Web Conferencing Server array in the Chicago pool.
Table 12-22. Details for Chicago—Web Conferencing Server Array
Table 12-23 provides a detailed view of the infrastructure requirements for the A/V Conferencing Server array in the Chicago pool.
Table 12-23. Details for Chicago—A/V Conferencing Server Array
Role/Feature | Quantity/Value(s) | Location/Setting | Note/Example |
|---|---|---|---|
Server | |||
Web Conferencing Server | Each node is a Domain member A/V Conferencing Server, and they are all configured identically. | ||
Node1 | AVCCHI01 | Internal network | |
Node2 | AVCCHI02 | Internal network | |
Node3 | AVCCHI03 | Internal network | |
Node4 | AVCCHI04 | Internal network | |
NICs | |||
Node1 (internal) | (1) 10.18.10.24 | 100-Mb Full | |
Node2 (internal) | (1) 10.18.10.25 | 100-Mb Full | |
Node3 (internal) | (1) 10.18.10.26 | 100-Mb Full | |
Node4 (internal) | (1) 10.18.10.27 | 100-Mb Full | |
Ports | |||
Internal | N/A | N/A | |
Certificates | |||
CN/SN | avcchi01.contoso.com | Exportable machine certificate: Used for Client/Server TLS/MTLS. | |
CN/SN | avcchi02.contoso.com | EKU: Server | Exportable machine certificate: Used for Client/Server TLS/MTLS. |
CN/SN | avcchi03.contoso.com | EKU: Server | Exportable machine certificate: Used for Client/Server TLS/MTLS. |
CN/SN | avcchi04.contoso.com | EKU: Server | Exportable machine certificate: Used for Client/Server TLS/MTLS. |
SAN | N/A | N/A | |
DNS (Internal) | |||
(A) | avcchi01.contoso.com | 10.18.10.24 | This is the internal FQDN of A/V Conferencing Server Node1. |
(A) | avcchi02.contoso.com | 10.18.10.25 | This is the internal FQDN of A/V Conferencing Server Node2. |
(A) | avcchi03.contoso.com | 10.18.10.26 | This is the internal FQDN of A/V Conferencing Server Node3. |
(A) | avcchi04.contoso.com | 10.18.10.27 | This is the internal FQDN of A/V Conferencing Server Node4. |
DNS (External) | |||
(A) | N/A | N/A | The A/V Conferencing Server Array servers are not addressable externally. |
Table 12-24 provides a detailed view of the infrastructure requirements for the Mediation Server in Chicago.
Table 12-24. Details for Chicago—Mediation Server
Table 12-25 contains the summary view of all infrastructure requirements for the deployment in Paris.
Table 12-25. Summary of Paris Infrastructure Requirements
Table 12-26 contains the summary view of all infrastructure requirements for the deployment in Madrid.
Table 12-26. Summary of Madrid Infrastructure Requirements
Server Role | Name | External DNS Name (IP Address) | Internal DNS Name (IP Address) | External Firewall Port (Direction) | Internal Firewall Port (Direction) |
|---|---|---|---|---|---|
EE Consolidated Pool | MADPOOL01 | N/A | madpool01.contoso.com (10.16.10.1) | N/A | N/A |
EE (Load Balancer) | FREMAD | N/A | fremad.contoso.com VIP = (10.16.10.1) | N/A | N/A |
_sipinternal._tcp.domain (SRV) 5061 madpool01.contoso.com | |||||
_sipinternaltls._tcp.domain (SRV) 5061 madpool01.contoso.com | |||||
EE Front End Servers | |||||
Node1 | FECMAD01 | N/A | fecmad01.contoso.com (10.16.10.2) | N/A | N/A |
Node2 | FECMAD02 | N/A | fecmad02.contoso.com (10.16.10.3) | N/A | N/A |
Mediation Server | MEDMAD01 | Session Initiation Protocol (SIP)/Public Switched Telephone Network (PSTN) Gateway (GW) (not in DNS) (10.16.10.51) | medchi01.contoso.com (10.16.10.50) | N/A | N/A |
SQL Server 2005 (non-clustered) | BAEMAD01 | N/A | baemad01.contoso.com (10.16.10.11) | N/A | N/A |
Exchange 2007 UM, Mailbox Server (MBX), Client Access Server (CAS), and Hub Transport Server (HUB) Server | EXUMAD01 | N/A | exumad01.contoso.com (10.16.10.70) | N/A | N/A |
Archiving Server | ARCMAD01 | N/A | arcmad01.contoso.com (10.16.10.80) | N/A | N/A |
Table 12-27 contains the summary view of all infrastructure requirements for the deployment in Singapore.
Table 12-27. Summary of Singapore Infrastructure Requirements
After preparing the server hardware and surrounding infrastructure—such as DNS and firewall configuration—Contoso can begin its Office Communications Server 2007 deployment. Contoso decides to start with the deployment in the Chicago headquarters and follows the deployment path presented in Table 12-28. For each server role deployment, Contoso reads the information in the corresponding Office Communications Server 2007 deployment guides.
Table 12-28. Deployment Path for Chicago
When configuring the Enterprise Voice Scenario in Chicago, Contoso configures Location Profiles, Phone Usages, and Routes that are needed later in the deployment process for the Madrid Enterprise Voice users together with the configuration for the Chicago Enterprise Voice users. The following sidebar explains Contoso's Enterprise Voice configuration.
The next location to be configured after the Chicago deployment in Contoso's Office Communications Server 2007 deployment is Paris. Contoso decides to deploy in the order described in Table 12-32.
Table 12-32. Deployment Path for Paris
After the Chicago and Paris deployments, Contoso proceeds with the Madrid deployment by following the deployment path described in Table 12-33.
Table 12-33. Deployment Path for Madrid
Step | Server | Action |
|---|---|---|
1 | BAEMAD01 | Install BAEMAD01. |
2 | FREMAD | Install pool Load Balancer. |
3 | FECMAD01 | Install FECMAD01. |
4 | Install one Office Communicator 2007 client to test. | |
5 | FECMAD02 | Install FECMAD02. |
6 | Test Office Communicator 2007 Client Instant Messaging access first with one or more Front End Servers offline and then with all of them online. | |
7 | MEDMAD01 | Install MEDMAD01. |
8 | Install the SIP/PSTN Gateway. | |
9 | Test the Office Communicator 2007 client by placing and receiving PSTN calls. | |
10 | EXUMAD01 | Install EXUMAD01. |
11 | Test Office Communicator 2007 client access and forward to VoiceMail. Test external access to VoiceMail. | |
12 | ARCMAD01 | Install ARCMAD01. |
13 | Test whether the Archiving Server works by using Office Communicator 2007 Instant Messaging. |
The last pool location for Contoso's Office Communications Server 2007 deployment is Singapore. Contoso decides to deploy Office Communications Server 2007 server roles in the order described in Table 12-34.
Table 12-34. Deployment Path for Singapore
Step | Server | Action |
|---|---|---|
1 | BAESPO01 | Install BAESPO01. |
2 | FRESPO | Install pool Load Balancer. |
3 | FECSPO01 | Install FECSPO01. |
4 | Install one Office Communicator 2007 client to test. | |
5 | FECSPO02 | Install FECSPO02. |
6 | FECSPO03 | Install FECSPO03. |
7 | FECSPO04 | Install FECSPO04. |
8 | Test Office Communicator 2007 Client Instant Messaging access first with one or more Front End Servers offline and then with all of them online. | |
9 | HTTSPO01 | Install HTTSPO01. |
10 | WCESPO01 | Install WCESPO01. |
11 | Test the Live Meeting 2007 client external Web Conferencing Server access. | |
12 | AVESPO01 | Install AVESPO01. |
13 | Test the Live Meeting 2007 client and Office Communicator 2007 external A/V Conferencing Server. |