Office Communications Server 2007 defines three Edge Server roles. These server roles are referred to as Edge Servers because they are deployed in the network perimeter of an organization's network. These server roles enable an organization to expose Office Communications functionality across the corporate network boundary to remote employees, federated partners, and public IM connectivity users. Office Communications Server 2007 exposes the following edge server roles:
Access Edge Server
Web Conferencing Edge Server
A/V Edge Server
These server roles are explained in more detail in the following sections. Hardware and software requirements for Edge Servers are shown in Table 2-5.
Note
To get the most up-to-date information about Edge Servers, refer to http://www.microsoft.com/technet/prodtechnol/office/communicationsserver/evaluate/sysreqs/ocs-ee.mspx#EMD.
Table 2-5. Hardware and Software Requirements for Edge Servers
Component | Requirement |
|---|---|
Computer and processor | Dual processor, dual core with 3.0-GHz or faster processor |
Memory | 4 GB or more of RAM recommended |
Cache | 1 MB L2 per core recommended |
Hard disk | 2 SCSI hard drives with 18 GB of available hard disk space recommended |
Network | 2 1-GBit NICs: one NIC for the external edge, and the second NIC for the internal edge |
Operating system | Windows Server 2003 Standard Edition, Windows Server 2003 R2 Standard Edition, or higher |
Other | Active Directory directory service for Windows Server 2003 or Windows 2000 with Service Pack 3 required |
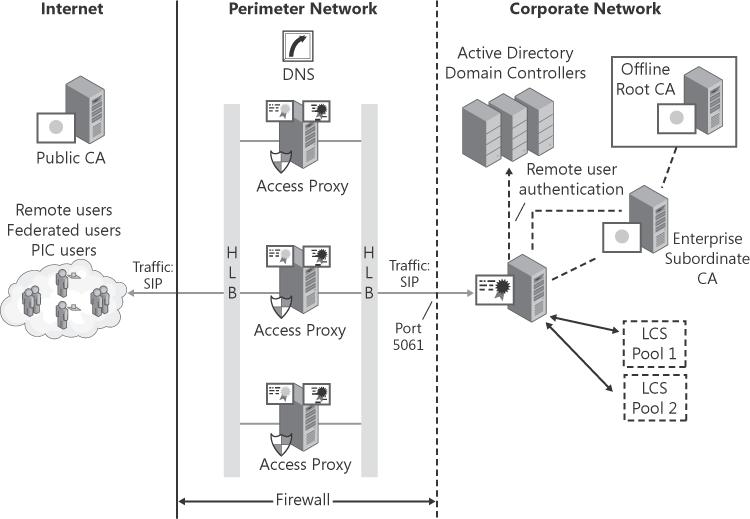
If you've deployed Live Communications Server 2005 SP1 and enabled remote user access, federation, or public IM connectivity, you're already familiar with this server role. In Live Communications Server 2005 SP1, this server role was called Access Proxy. It has been renamed to offer a consistent naming convention with the two new additions, the Web Conferencing Edge Server and the A/V Edge Server. Despite the name change, the Access Edge Server role serves the same function as Access Proxy.
The Access Edge Server must be deployed if you want to enable Federation, public IM connectivity, or remote user access. Because most organizations do not have Active Directory access from their network perimeter for security reasons, the Access Edge Server is deployed on a computer running Windows Server 2003 or Windows Server 2003 R2 in a workgroup environment. Therefore, it cannot authenticate users. Users are authenticated by the Director.
The Access Edge Server cannot be collocated on the same physical server with any other network perimeter service, such as Microsoft Internet Security and Acceleration (ISA) Server; however, it can be collocated on the same physical server with the Web Conferencing Edge Server and the A/V Edge Server. Scaling requirements for your organization might demand that you install these Edge Server roles on separate physical servers.
The Access Edge Server must be configured with two IP addresses. One IP address should be visible to the Internet, and the second IP address should be visible to the enterprise network.
The recommended configuration (for performance and ease of securing the server) is to install two network interface cards (NICs) and connect the Internet to one and the enterprise network to the other. If the Access Edge Server is protected by firewalls on both sides of the network perimeter, the internal firewall must be configured to open port 5061. This is necessary so that the Access Edge Server can connect to the Director in the corporate network, and vice versa. If you are configuring Federation or public IM connectivity, you must open port 5061 on the external firewall to allow connectivity from the Internet to the Access Edge Server. If remote user access is configured, you have the option to configure whichever port number you prefer because you control the clients connecting to your Access Edge Server, because these are internal users. The recommendation is to open port 5061 or 443. A best practice is to open port 443 because this allows your users to connect back to your Access Edge Server from another organization's network, because this port number is usually opened. This is particularly important for professionals, such as consultants, who work at customer sites.
To provide high availability, a bank of Access Edge Servers can be deployed. An HLB must be configured on both sides of the Access Edge Servers, as shown in Figure 2-10.
Similar to the Access Edge Server, the Web Conferencing Edge Server proxies Web conferencing media across the firewall to and from the Internet and the corporate network. Where the Access Edge Server proxies SIP traffic, the Web Conferencing Edge Server proxies PSOM traffic from a Web conferencing session. Similar to the Access Edge Server, the Web Conferencing Edge Server must be configured with two NICs: one network card connected to the Internet, and the other network card connected to the internal network. The network security administrator needs to open port 443 on the external NIC to allow users to connect from the Internet and open port 8057 on the internal NIC for Web Conferencing Servers to connect to it. This is because the Web Conferencing Edge Server never establishes a connection to the Web Conferencing Server directly. Only the Web Conferencing Server connects to the Web Conferencing Edge Server. This design has the advantage of reducing the number of vectors into the corporate network.
The Web Conferencing Edge Server role cannot be collocated with any other server role except the Access Edge Server and the A/V Edge Server.
To provide high availability, a bank of Web Conferencing Edge Servers can be deployed. An HLB must be configured on both sides of the Web Conferencing Edge Servers.
The Access Edge Server role and Web Conferencing Edge Server role can also be combined on the same physical servers in a bank. This configuration provides high availability while consolidating the number of Edge Servers required. This architecture is shown in Figure 2-11.
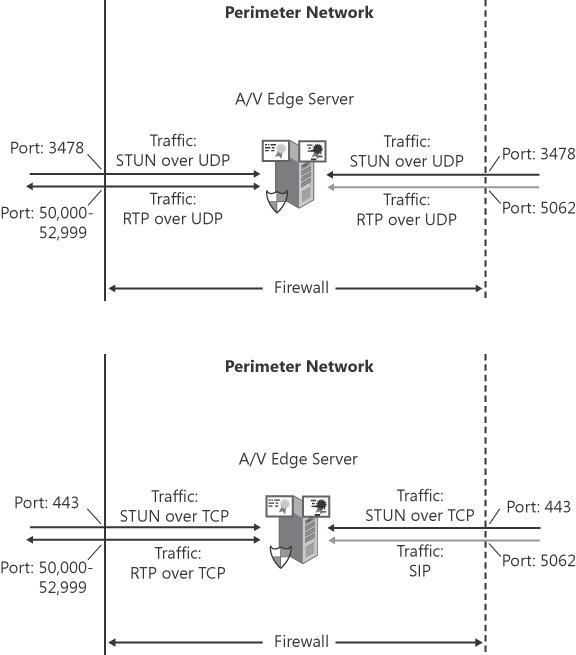
The A/V Edge Server enables audio and video traffic to traverse the corporate perimeter network. The A/V Edge Server serves as a meeting point for bridging users connecting from the Internet to an A/V Conferencing Server associated with the user's home server. Users connect to the A/V Edge Server, and the A/V Conferencing Server connects to the A/V Edge Server. The A/V Edge Server relays the Real-Time Protocol (RTP) traffic between the users and A/V Conferencing Server. Similar to the other Edge Server roles, the A/V Edge Server must be configured with two NICs: one network card connected directly to the Internet, and the other network card connected to the internal network. The A/V Edge Server uses the Information and Content Exchange (ICE) protocol to enable clients to traverse firewalls that might lie in between the end-user's client and the A/V Edge Server.
For A/V to work properly, the following ports need to be opened on the firewall adjacent to the external edge of the A/V Edge Server. Because User Datagram Protocol (UDP) is preferred for RTP traffic, Communicator will attempt to first connect to UDP port 3478. If Communicator fails to connect to UDP port 3478, it attempts to connect to the A/V Edge Server on TCP port 443. If successful, the A/V Edge Server negotiates with the client a port in the range 50,000 through 59,999 for the media stream.
Following is the set of ports to open on the A/V Edge Server external NIC:
STUN over UDP port 3478
RTP over UDP port range 50,000–59,999
STUN over TCP port 443
RTP over TCP port range 50,000–59,000
Here is the set of ports to open on the A/V Edge Server internal NIC:
STUN over TCP port 443
SIP port 5062
STUN over UDP port 3478
These sets of ports are shown in Figure 2-12.
To provide high availability, a bank of A/V Edge Servers can be deployed. An HLB must be configured on both sides of the A/V Edge Servers.