CONTENT SECURITY FOR MOBILE TV
Good work must, in the long run, receive good rewards or it will cease to be good work.
—Charles Handy, Irish thinker and author
17.1 INTRODUCTION: PAY TV CONTENT SECURITY
Satellite and cable broadcast services have had a long history of providing pay-TV services. Pay TV is provided through encryption of signal at the “headend” (cable or satellite) and use of a decoder with decryption at the receiving end. A number of encryption systems are in use in broadcast systems worldwide. These include, among others, Viaccess, Nagra, Conax, Videoguard, Cryptoworks, Irdeto, and NDS. The encryption systems are proprietary but are applied as per the DVB standards that are widely used in the broadcast TV industry.
The following are the common standards for transmission:
• DVB-S—DVB standard for satellite broadcast using QPSK or 8PSK modulation,
• DVB-C—DVB standard for digital cable using 16QAM or 64QAM modulation, and
• DVB-T—DVB standard for terrestrial broadcast using COFDM modulation.
It would appear that, the DVB-H being an extension of the DVB-T standards, the same encryption systems could apply. However, the mobile environment is not ideally suited to DVB-based conditional access (CA) systems, as there is no room to carry the bandwidth-hungry stream of entitlement messages common in DVB-based CA systems. Mobile systems are characterized by low-bandwidth environments with occasional severed connections. Hence modifications to the conditional access systems are required, which we will see in the later sections.
In the DVB-based conditional access systems the content can be encrypted at the program elementary scheme (PES) or the transport stream (TS) level. This implies that a broadcast operator, for example, may encrypt any of the programs individually or all of the programs carried on a transmit stream. When the signal is delivered at the other end, the broadcaster supplies a decoder unit, which decrypts and provides an unencrypted signal to the user. Hence the encryption is essentially the property of the transmission operator. Once the content leaves the transmission system it is no longer encrypted and can be freely stored, viewed, and retransmitted.
Content owners are, however, more concerned regarding the content security of individual items, e.g., pictures, video, music, e-books, programs, and games. They are less concerned about the security of the transmission systems that protects the revenues of the pay-TV operators. The rampant piracy that was witnessed in the heyday of the Internet, with sharing of copyrighted videos and music, has driven the industry toward the digital rights management of content. This implies that the rights of viewing (or listening, reading, or forwarding) each item can be controlled by the license holders using, for example, a server that administers the rights. The rights can be administered in a number of ways, including:
• who can view the content,
• how many times the content can be viewed,
• at what time the rights to view content expire,
• in which geographical area the content can be viewed,
• on what devices the content can be viewed,
• restrictions on forwarding of content, and
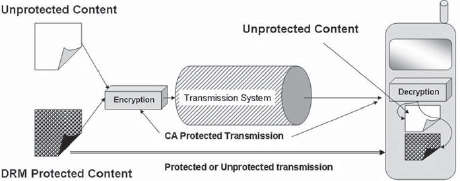
• renewal of rights through payment mechanisms (Fig. 17-1).
This mechanism of management of rights for content has given birth to the technology of digital rights management or DRM.
FIGURE 17-1 Conditional Access and Content Security. DRM provides rights management of content even after delivery.
It will be evident that in the case of mobile multimedia networks DRM is considered the most effective way to manage content security. The fact that mobile phones are now playing the roles of iPods, MP3 or MP4 players as Walkman phones, and other manifestations with large storage was a foregone conclusion. Hence it is not adequate (from the point of view of the entertainment or publishing industries) that the content be delivered using CA systems. They are also concerned that the content once stored (which inevitably it will be) should still be governed by the digital rights for viewing, listening, or sharing. The DRM technologies are here to ensure this and we will take a look at these technologies under Digital Rights Management and OMA. Users have become quite familiar with the term “DRM” since Apple introduced its music store iTunes service and the Apple’s proprietary DRM (Apple’s Fairplay DRM technology). DRM limited the number of machines to which a purchased item can be copied, the number of CDs that can be made, and to which devices it could be transferred (e.g., iPods, Macs).
17.1.1 Subscription Modes
Having observed the pay-TV industry over the past decade we see that the pay-TV services (digital satellite, DTH, digital terrestrial, and digital cable) can fall into a number of categories:
• subscription services,
• pay per view (PPV),
• impulse pay per view (IPPV).
Understanding the distinction is important from the point of view of payment mechanisms.
17.1.2 Subscription Services
Subscription services provide subscription to a particular channel (e.g., ABC News or HBO). The subscription can be for a particular period, from a month to a year or more. More often subscription services are offered as part of bouquets to which customers may subscribe. Subscription services are most common on pay-TV systems for satellite, DTH, cable, or terrestrial mainly because in most cases the systems are not interactive. It is not convenient for customers to go online and order each movie, video, or sports event separately. Hence, in that industry, subscription services that provide a stable environment for viewing as long as the customer keeps paying the bills are the most common.
Interactive networks on which online access to payment servers can be made available on a return path via GSM, CDMA, or the Internet (e.g., using mobiles) are game for richer services with higher potential revenues, such as PPV.
17.1.3 Pay per View
Pay-per-view services have made strong headway into the pay-TV industry, by which the customers can order specific shows or events such as sports events. Where return path or interactive services are not available a call center is often used with various payment mechanisms to order PPV events.
Near video on demand and impulse pay per view are variations on pay per view; in the former case the user merely selects from multiple channels of the same event running in a time-staggered manner and in the latter case (IPPV), the user can press an interactive button during an ongoing program or advertising to select an event to watch.
17.2 SECURITY IN MOBILE BROADCAST NETWORKS
17.2.1 Access Control and Content Security
We have seen that the traditional method enabling access to content has been conditional access. This type of access can be classified as “transmission system security” or “broadcast security” as opposed to content security, which is provided by DRM. Broadcast security is very common in the pay-TV industry, in which it is used by the operators to permit or deny access to specific channels or programs to the customers. Once access is provided, however, the customers can store and retrieve the content, forward it to others, make copies, or use it in any other manner. The access security provided at the broadcast level does not provide any useful mechanisms to control the use of the content once it is decrypted.
17.2.2 Unicast and Multicast Networks
The mobile TV and multimedia delivery networks can be classified into unicast and multicast networks (see Chap. 5). In unicast networks, a separate session is set up with each client mobile device. This gives the maximum flexibility in selection of channels and video on demand but has limitations in terms of scalability. On the other hand, in multicast networks the contents are multicast via multicast routers (in the case of IP networks) or broadcast using terrestrial or satellite technologies. Multicast or broadcast technologies can cater to an unlimited number of users without any additional burden on the networks. DVB-H, DVB-T, S-DMB, DAB-IP, and MBMS are examples of such networks. Owing to the receiving device being a mobile handset, which also has a connection to the mobile networks, such networks have the possibility of having interactive services.
Pure broadcast networks without a return path tend to have conditional access as the primary method of broadcast content security. On the other hand, networks with a return path have the flexibility to have keys delivered over the mobile and can use content and broadcast security using a DVB-CBMS or OMA-BCAST type of system in addition to the pure broadcast-based CA systems. We will be discussing the new content security mechanisms in this chapter.
As an example of a multicast and broadcast network for mobile phones, the MediaFLO network uses AES (Advanced Encryption Standard) encryption for broadcast multimedia services. The keys are transmitted using the mobile network directly to the users and will not use the broadcast network as in pay-TV broadcast systems.
17.3 CONDITIONAL ACCESS SYSTEMS FOR MOBILE TV
The conditional access or encryption in conventional pay-TV systems is usually provided based on the DVB Common Scrambling Algorithm. The DVB standard does not specify any particular conditional access system per se, but specifies the manner in which such encryption is applied to a DVB program stream. Further, using this algorithm, more than one encryption (CA) can be applied to the DVB stream, as a result of which it can be decoded by decoders supporting either type of encryption. This process, called simulcrypt, is useful in having a common uplink network and satellite for carriage even though the ground networks may be from different broadcasters and use different encryptions. For this reason the DVB systems are considered to provide an open platform for encryption systems.
The conditional access systems used for fixed applications are usually based on a specific algorithm and a set of keys required to carry out the decryption. The keys can be asymmetric or symmetric. A common scheme of implementation is to have symmetric encryption for the data stream using a scrambling keyword (e.g., Sk), which needs to be used by the transmitting end as well as for reception. In order to maintain the system security against hacking, the keyword Sk needs to be changed every 5–20 sec. The keyword is conveyed to the receiver by sending entitlement control messages (ECMs). These messages contain the current keyword Sk and are conveyed by using a service key (e.g., Kw) as scrambling key for the ECM. The service keys are also needed to be changed periodically (e.g., once a month). The information of the service key (Kw) is provided along with other information such as entitlement of channels for the customers by using another key (master key, Mk), which is supplied to each operator by the CA vendor and is network specific. The messages carrying the subscription information and the service keyword (Kw) are called the entitlement management messages (EMMs). The operation of the receiver is thus dependent on the reception of ECMs (which carry the program information and the current scrambling keyword) 3–20 times every minute (typical). The EMM frequency is lower (say, once in 10–20 min)and these messages carry the service key and subscriber entitlement information but need to be sent for all subscribers. The parameters are system specific and on them depends how long it will take to get a subscriber entitled to a new service (Fig. 17-2).
In traditional CA systems the receiving decrypter is expected to operate as a stand-alone requirement, i.e., it is dependent solely on the transmitted stream for reception of keys. It cannot (and is not designed to) access any external sources for the keys, such as the public key infrastructure (PKI). The PKI has been a standard feature in Internet-based encryption and authentication systems.
The challenges in the extension of the CA systems to the mobile environment now become apparent. First, the bandwidth available is always constrained so that heavy traffic of ECMs and EMMs cannot be supported nor can processing power be spared for the same in the mobile handsets. Second, mobile devices are liable to lose signals and roam out of the coverage area from time to time. Hence the system should be robust enough to bear loss in signals. Third, due to the very nature of the mobile phones as personal devices, users expect immediate authorization of services such as video on demand. In order to overcome these problems, most of the CA operators have come out with Subscriber Identity Module (SIM)-based CA systems. The SIM retains the keys and service entitlement information and reduces the overhead needed for the CA system to operate in the mobile environment. In cases in which the SIMs (or USIMs for 3G networks) are provided by mobile operators who happen to be independent of the broadcaster, the CA can be implemented through memory modules such as multimedia cards (MMCs). The modification of the CA mechanism by having the keys and algorithms stored in USIMs or CA-supplied MMCs has been the primary mechanism deployed in mobile CA systems. These mobile CA systems act as extensions of the traditional pay-TV network CAs and do not make use of any feature available for communication in a mobile phone, such as access to the PKI.
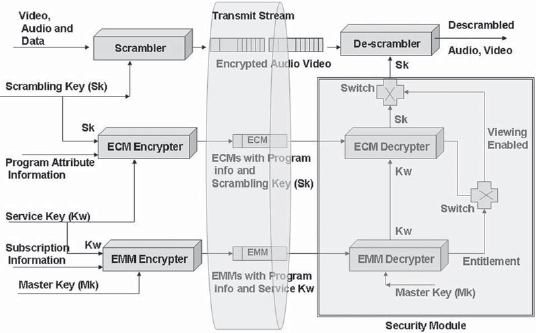
FIGURE 17-2 Model of a Conditional Access System
Mobile phones, being communication devices, can, however, have access to external servers and these principles are used in some schemes of authorization of content delivered to mobiles in the new technology of DRM.
17.4 EXAMPLES OF MOBILE CA SYSTEMS
The initial deployment of content protection in mobile TV networks has been via the use of the CA systems. Some examples are given below.
• S-DMB services in Korea were launched in 2005 using a mobile version of the Irdeto conditional access system called Irdeto Mobile.
• DVB-H: 3 Italia, which demonstrated its DVB-H service during the FIFA World Cup 2006, has launched its services based on a CA solution from Nagra.
17.5 DIGITAL RIGHTS MANAGEMENT AND OMA
The Open Mobile Alliance (OMA), which is an association of over 350 industry participants, has been concerned with the extension of CA systems in their present form to the mobile multimedia content industry. This is because, first, using different CA systems as they exist today will defeat the objectives of the mobile industry to keep the networks interoperable and facilitate roaming. If CA systems are embedded in phones (or even on USIMs) the roaming world will get fragmented. Second, “transmission security” is seen to suit only operators and does not satisfy the securing of content item by item, which is the objective of content owners, authors, and publishers. To overcome these shortcomings and foster greater use of mobile networks, the OMA has formulated the schemes of digital rights management by which the contents and its rights are considered two separate entities. The DRM defines these structures and how the rights are transferred and enforced.
17.5.1 DRM 1.0
The OMA DRM 1.0 was released in November 2002. Release 1 was always considered as interim until DRM 2.0 was finalized and released, which happened in December 2004. For all practical purposes it is release 2.0 that is used now. However, DRM 1.0 set the ball rolling by enhancing the definition of content by defining new media types.
In DRM, individual media objects such as images, audio, and video clips are encrypted by using a specified algorithm. The DRM content is associated with metadata (such as title, artist, duration, year of release) and delivery method. In DRM 1.0 there are three delivery methods:
• forward lock (compulsory or implicit),
• combined delivery, and
• separate delivery.
DRM 1.0 defines the new media types as “DRM content” (encrypted content with meta data), “rights,” and “DRM message.” The procedure of the download is not specified by DRM 1.0. The users can only consume the content as per the “rights” contained.
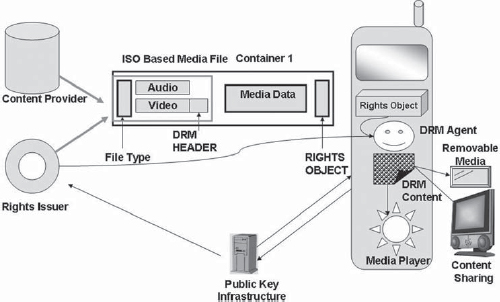
Figure 17-3 shows the “separate delivery” and the “combined delivery” methods. In combined delivery the delivery method is also sent along with the content. Alternative methods of delivery are the forward lock method (in which the rights are not conveyed and forward lock is implicit) and separate delivery (in which the delivery of rights is over a separate channel). DRM 1.0 does not contain tools for management of key transfer, which were left for later releases.
FIGURE 17-3 Content Handling in DRM 1.0
17.5.2 DRM 2.0
OMA DRM 2.0 provides for the use of the PKI for key management and provides for a higher level of security in end-to-end DRM systems. DRM 2.0 defines “actors,” which define various roles in the DRM management process. The following are the actors in the DRM 2.0 scheme:
• A DRM agent is a “trusted entity” placed in a device (e.g., a mobile phone), which is responsible for receiving DRM content and enforcing the rights.
• A content provider provides DRM content to various agents.
• A rights issuer delivers rights instructions or objects for the use of such content.
• A certification authority provides certificates to rights issuers and trusted agents to operate as per the PKI infrastructure. DRM 2.0 specifies the use of various protocols for operating in the PKI environment such as the 128-bit AES and RSA-PSS (signature algorithm). It specifies a DRM content format (DCF) for discrete objects such as pictures and a packetized data format for continuous video (e.g., in streaming video).
DRM 2.0 is a fairly complex standard with multiple options for passing of keys. In a typical implementation, the content is first encrypted using AES and a content encryption key (CEK). The CEK is wrapped using the rights objects key and placed along with the encrypted content in the DCF. The DCF is delivered to the DRM agent in the receiving device, which then decrypts the rights information using the PKI and the transmitted keys.
The DRM agent, as a trusted entity, is resident in the mobile phone and is responsible for delivering the decrypted content as per the rights.
While the transmission of content to the mobile phone using DRM protection is a one-time process, the user may consume the content (for example store and listen to songs or view videos) over a period of time. In case the rights expire the user can buy new rights from the rights issuer and the DRM agent can reauthorize the use of content using the PKI (Fig. 17-4).
17.5.3 Broadcast Level Security and OMA: OMA-BCAST
OMA DRM 2.0 is primarily meant for content security and rights management for downloadable objects. It is not scalable to provide broadcast mode content security as there are no mechanisms for continuous change of keys, a feature that is the hallmark of conditional access systems.
The Open Mobile Alliance has been working on a common standard for transport level security as well as content security under an initiative called OMA-BCAST. The OMA-BCAST has been conceived as a “broadcast-level” security system that can work for all standards of mobile TV and multimedia transmissions, including DVB-T-, DMB-, DVB-H-, 3 GPP-, and 3 GPP2-based systems. The advantage of OMA-BCAST as conceived by the Open Mobile Alliance would be that such systems can be used independent of the operator or networks. Using proprietary CA systems as is the common practice in the broadcast industry is seen as restricting features such as roaming across networks and interchangeable use of phones for different operators. Such interoperability and roaming features are common to the mobile world but unfamiliar in the TV broadcasting world.
Both DVB and OMA are working toward open standards for broadcast-level content security. Under DVB the Digital Video Broadcasting—Convergence of Broadcasting and Mobile Services (DVB-CBMS) initiative is progressing. The DVB-CBMS specifications were released in December 2005, while the OMA-BCAST specifications are set for 2007 release. The DVB-CBMS is at present focusing on providing an open framework for DVB-H systems for content security. The DVB-CBMS is supported by a number of operators and handset manufacturers, including Nokia. The recent implementations of the DVB-H systems and FIFA trials involving T-Mobile, Vodafone, E-Plus, and Orange were based on the use of DVB-CBMS as the content security system. Both DVB-CBMS and OMA-BCAST have common core architecture and four-level key structures. The DVB-CBMS release is based on a profile called 18Crypt. The 18Crypt profile is also an option in OMA-BCAST and is based on OMA DRM 2.0.
FIGURE 17-5 Content Security in the Mobile TV Industry
The OMA-BCAST as an umbrella standard is expected to provide content level security under OMA DRM 2.0 and broadcast security through extensions to the DRM for live TV. 18Crypt is set to emerge as a common profile for implementation of open content protection systems (Fig. 17-5).
17.5.4 Content Protection for Other Multimedia Transmission Systems
Multimedia transmission security as well as content security has been defined for other standards as well. For MBMS the content security has been defined as per OMA DRM 2.0 and transmission security as per the Secure Real-Time Transport Protocol.
17.5.5 An Example of Mobile DRM: NDS mVideoguard Mobile DRM
NDS, one of the major providers of CA systems for pay TV, has announced the mVideoguard system for conditional access as well as content protection using OMA DRM. The software is an integrated solution for electronic service guide, interactive TV, OMA digital rights management, DVB-CBMS, and mVideoguard conditional access. NDS is also providing packaged solutions with DibCom for mobile digital TV with DVB-H. Pantech Korea has also adapted the use of mVideoguard for its OMA DRM capabilities.
With the addition of OMA DRM capabilities to the mVideoguard, including OMA DRM versions 1.0 and 2.0 and DVB-CBMS based on 18Crypt as well as OSF solutions, mVideoguard has brought forth an open platform for DVB-H as well as DMB and DAB-IP systems.
17.5.6 OMA-BCAST vs CA Systems
There are some concerns over the use of a common open standard broadcast level CA system such as OMA-BCAST. In the case of individual CA systems the CA vendors are responsible for maintaining the integrity of the encryption system, including key distribution to handset manufacturers. Under the OMA framework, there is no single point of responsibility if a breach in security were to happen. However, this is predominantly the view of the CA manufacturers. The industry continues to work for open solutions. CA solutions do not by themselves provide a complete solution for protection of content and its consumption as per assignment of rights. Hence the DRM solutions, and in particular OMA DRM 2.0 and Windows Media DRM, are likely to emerge as winners.
17.6 CONTENT SECURITY AND TECHNOLOGY
17.6.1 Security for DMB Networks
DMB networks are an extension of the digital audio broadcasting (DAB) standards. These networks find considerable favor, as the spectrum for DAB is available in most countries. While Korea saw the first implementation of DMB technologies, with the launch of both S-DMB and T-DMB in 2005, DMB trials have been conducted in many countries and DMB networks are likely to see progressive deployments in 2007 and 2008. The beginning for Europe came recently when T-DMB services were launched in Italy in June 2006, coinciding with the FIFA World Cup 2006 games. DMB systems also assume importance owing to their use in China.
The technology used in DMB is the DAB physical layer and a multiplexing of various services using an ensemble multiplexer. The ensemble multiplexer does not follow the DVB multiplex schemes in order to enable applying DVB-based CA systems. However, the DMB uses MPEG-4 or H.264 coded programs carried in an MPEG-2 transport stream. Hence DVB-CA encryptions (as modified for mobiles for keys based in SIM) can be applied to the programs carried in the MPEG-2 transmission stream. The S-DMB system in Korea uses Irdeto PIsys Mobile as the conditional access system, while T-DMB services are present provided on a free-to-air basis. SK Telecom in Korea uses SK-DRM for its 3G network, which is based on the OMA DRM.
17.6.2 Security for DVB-H Networks
DVB-H is an extension of the DVB-T standard and can in fact operate on the same network in “shared multiplex” mode or “hierarchical” mode. DVB-T uses conventional conditional access systems for broadcast security, such as Nagra, Irdeto, and Viaccess. By itself, the DVB-T is a unidirectional transmission medium and the DVB-H streams can be carried in a similar manner and provided broadcast level security using a CA system modified for mobiles (e.g., keys and algorithms in the SIM/USIM or UICC card or in MMC/SDIO cards). Alternatively, use can be made of the underlying mobile communications, to have an open standard by negotiation of keys. This is the approach followed by the OMA systems.
17.6.3 DVB-H Conditional Access
DVB-H streams can be encrypted by a CA system and decrypted by keys stored in SIM or MMCs. This system was used in the DVB-H launch by 3 Italia, which used the Nagra encryption system.
IP datacast over DVB-H is an end-to-end broadcast system for delivery of various types of digital content using an underlying IP-based layer. A typical IP datacast system comprises a unidirectional DVB-H broadcast combined with a return bidirectional mobile connectivity. DVB-H using IP datacast is thus a fully interactive mobile TV broadcast system. It is thus a convergence of broadcast and mobile services and is appropriately termed DVB-H CBMS. The specifications of IP datacast are given by DVB Blue Book A098.Content can be delivered (and consumed by the terminal) using an IP datacast service by two methods, i.e., streaming and file download. The IP datacast over DVB-H specification has a provision of service purchase and protection. The IP datacast model of service protection is dependent on the underlying mobile network for encryption key management and thus differs from pure broadcast-based conditional access systems (CA systems) used in pay-TV broadcast applications.
Digita (Finland) has launched its trial services based on the MBS 3.0 broadcast solution from Nokia. This solution is a DVB-H CBMS-based content protection mechanism. It also features the open air interface.
The encryption and key management system is quite straightforward in DVB-CBMS systems and follows a four-layer architecture.
1. First of all a session is established between the headend and the mobile device, in which the metadata about the content may be exchanged. This is called the registration session. The registration can happen over either the interactive or the broadcast channel.
2. Thereafter the content is encrypted using a traffic encryption key (TEK) using symmetric encryption. This provides a broadcast level security and is done irrespective of whether the user has the rights to view the content.
3. As the encryption is symmetric, there is now a need for the TEK to be transmitted to the mobile device. This is done by using the key stream management (KSM) layer. The KSM layer transmits the keys using the broadcast channel. Reception of a TEK enables the receiver to decrypt the content.
4. Finally the user needs to have the rights to view the content. This is done by using the rights management layer. Keys received for the user as a result of purchase of rights (key management messages) are transmitted via the rights management layer via the interactive or the broadcast channel. Additional information such as a service entitlement key (SEK) may also be transmitted in the rights management layer (Fig. 17-6).
FIGURE 17-6 DVB-H CBMS Model (Source: DVB Blue Book 098)
17.7 MULTIMEDIA APPLICATIONS AND HIGH-CAPACITY SIMS
The growing use of multimedia handsets with mobile TV capabilities and associated content protection and conditional access requirements has focused attention on the requirement for high-capacity SIMs (USIMs or UICCs for 3G networks). The usage of the handset to store the content rights led to the well-known problem that when the user changed the handset the new handset had no record of the rights previously acquired by the customer. Earlier when the customers used to download music from the MusicMoto site of Motorola, it was authorized to play only on the first handset to which it was downloaded. A user changing a handset would need to get all rights reauthorized. The same is the case for personal information, e-mails, etc. Orange launched 128-Mbyte USIMs and moved to 512 Mbytes in 2006 (e.g., the LG 8210 handset). The main focus for multimedia applications is the support of cryptographic functions, including symmetric and asymmetric cryptography, interface to cell broadcast protocol (to receive content pushed by the cell operators), and SMS functions. The SIM interface has to be a high-speed interface as well to support the applications. The SIM functionality for 3GPP networks is primarily defined by TS 11.10-4. New functionalities are now being added to support the multimedia world with content protection-type applications (with backward compatibility). The high-capacity SIMs can be used to store the DRM-protected content, user rights, and digital certificates. This provides easy handset portability in today’s environment. The MMC Association announced its support for secureMMC version 2.0 as a basis for porting of DRM 2.0 in removable devices such as SIMs.
In the case of mobile TV, the high-capacity SIMs can be used to store the mobile TV service settings, including roaming operator information, TV content rights objects, the DRM 2.0 agent, and cryptographic keys.
17.8 EXAMPLES OF MOBILE BROADCAST CONTENT SECURITY
With the finalization of DRM 2.0 by the OMA, the stage was set for the availability of content protected by DRM 2.0. Some of the handsets, especially those designed for storage of music, have started coming with support for DRM 2.0. An example is the Sony Ericsson Walkman phone W850, which has a Walkman Player 2.0 with MP3, AAC, AAC+, eAAC+, and MP4a support. The phone has DRM 2.0 and full-length music download OTA features. Support for DRM 2.0 is also available in many tool sets for mobile TV such as Netfront.
DRM 2.0 is licensed software and owing to the license fees per handset and the proprietary systems available many of the online music stores have been using proprietary systems. For example, the RealNetworks, which supports in the online community Helix, has the Helix DRM 10 as the content security system. The Helix DRM DNA is the client that runs natively on mobile devices. The client provides support for 3GPP, 3 GPP2, RealAudio, and RealVideo formats on mobile phones. Helix DNA client has been shipped in more than 100,000,000 mobile phones. There are many other proprietary DRM systems in use. For example, Sprint uses Groove’s Mobile Solution. Sony Music BMG (sonymusic.com) uses XCP and Mediamax content protection.
17.8.1 Windows Media DRM
Windows Media players for video and audio are very common. A number of operators (particularly in the United States and Europe) have preferred the use of Windows Media or RealPlayers over other types of players in mobile phones and their networks. An example is the U.S. carrier Cingular, which launched its music download service mMode. The service is based on the use of Windows Media DRM, which gets downloaded onto the phones upon subscription to the service.
The content usage rules can differ from one content provider to another. As per the standard usage rules, users can burn digital downloads up to seven times for noncommercial use and listen to the music an unlimited number of times. The music files can be transferred to up to four additional devices (secondary devices). The music must be downloaded only in the United States. In addition the users are prohibited from sharing the content, uploading it to the net, or modifying it in any manner. Verizon also uses Windows DRM for its V CAST video streaming services. Windows DRM for portable devices is also known as Janus.
Major music stores now need the handsets or other downloading devices to support Windows DRM 10. Examples of such stores in the United States are Virgin Digital, Rhapsody to Go, AOL Music Now, and Napster to Go.
17.8.2 Korea DMB: Irdeto Mobile
The Korean S-DMB system is a pioneer in the family of DMB systems in terms of its early deployment and successful operation. The system uses Irdeto PIsys for its mobile conditional access system for access to mobile TV and multimedia services. PIsys encrypts the payload as well as the messages that are encrypted using 128-bit AES. The Irdeto Mobile Solution is available for S-DMB, DVB-H, and DVB-T systems and has been introduced by a number of operators globally. Irdeto Mobile is a modular system and also provides modules for DRM 2.0. Irdeto has developed bandwidth minimization techniques, one of which is the transport of EMMs using out-of-band channels such as mobile SMS in addition to the transmit stream (Fig. 17-7).
FIGURE 17-7 A Conceptual View of the Irdeto PIsys Mobile Solution
17.8.3 Nokia IP Datacasting (IPDC) E-Commerce System
Nokia provides a complete system for e-commerce based primarily on the Nokia IPDC 2.0 solutions platform for IP datacasting using the DVB-H broadcast platform. In the IPDC solution, the service protection is achieved by using IPsec encryption, which is done at the IP level. The IP encryption is carried out in the IPE10 IP encapsulator of Nokia on a session-by-session basis and a new key is generated for each session. The decryption information is stored in the Security Association file, which carries the DRM information and the rights object (i.e., whether the user can watch one particular program (VoD) or the program on a subscription basis). The e-commerce server of Nokia is the prime component from where the user can order the viewing rights and the rights data is pushed to the phone using WAP-Push technology. The DRM agent in the phone then permits the consumption of content as authorized. Having an e-commerce system provides a complete solution to content providers and content aggregators (Fig. 17-8).
FIGURE 17-8 Nokia e-commerce System
17.8.4 BT Movio: Safenet Fusion DRM
BT Movio is a DAB-IP service available to customers as well as other virtual network operators. The DRM solution selected by Movio is DRM Fusion from Safenet. The solution is interoperable and supports multiple DRM technologies. DRM Fusion has support for DRM 2.0 and Windows Media DRM 10 and can be used for live or on-demand services. It can be used for wireless as well as wireline applications. The DRM solution is end to end and has both client- and server-side components. It also has flexibility to have server-side enhancements so that proprietary clients are not needed on the wireless devices.
The Japanese market needs a mention as it has been a pioneer for 3G services through NTT DoCoMo’s FOMA network. FOMA handsets have been produced with Microsoft Media DRM 10 (e.g., F 902is). In addition they support SD binding DRM. Here SD refers to the SD memory card and the DRM is designed to place contents on the SD card in an encrypted fashion. Further, the keys for the SD binding are saved in such a manner that it is possible to specify and limit the devices on which they can be decrypted. A player from PacketVideo (pvPlayer) can play both types of content, i.e., WDRM 10 and SD binding.
17.9 MODELS FOR SELECTION OF CONTENT SECURITY
A number of different models are emerging for applying content security as the mobile operators and broadcasters move in to provide mobile TV services. Where such services are provided by mobile operators themselves, they use the SIM, USIM, or UICC, which is supplied by them and over which they have full control. This is also the case of broadcasters who provide the services in cooperation with a mobile operator as a partner.
On the other hand, independent broadcasters can still provide their own content security, which can be added onto the mobile phones using an MMC or SDIO card or UICC in a second SIM slot. Interactive services can still be provided by using their own servers, which are accessed by the mobile using the IP layer.
The industry, under the aegis of the OMA, is moving toward open solutions that can be deployed across networks and a range of mobile phones. This is expected to set the trend for medium-term developments in the industry.