Chapter 1. Cybersecurity Fundamentals
This chapter covers the following topics:
• Introduction to Cybersecurity
• Threats, Vulnerabilities, and Exploits
• Intrusion Detection Systems and Intrusion Prevention Systems
• Cisco Security Management Appliance
• Cisco Identity Services Engine
• Security Cloud-Based Solutions
• The Principles of the Defense-in-Depth Strategy
• Confidentiality, Integrity, and Availability: The CIA Triad
• Personally Identifiable Information and Protected Health Information
• Principle of Least Privilege and Separation of Duties
• Playbooks, Runbooks, and Runbook Automation
Welcome to the start of your journey toward the CyberOps Associate certification! Cybersecurity programs recognize that organizations must be vigilant, resilient, and ready to protect and defend every ingress and egress connection as well as organizational data wherever it is stored, transmitted, or processed. In this chapter, you learn concepts of cybersecurity and information security. Then you learn the difference between cybersecurity threats, vulnerabilities, and exploits. You also explore the most common cybersecurity threats, as well as common software and hardware vulnerabilities. You learn the details about the confidentiality, integrity, and availability (CIA) triad. In addition, you learn about different cloud security and IoT security threats.
This chapter also describes the different types of network security devices and cloud services in the industry. It compares traditional firewalls and next-generation firewalls (NGFWs), as well as traditional intrusion prevention systems (IPS) and next-generation IPS (NGIPS). You learn details about the Cisco Web Security and Cisco Email Security solutions, as well as what advanced malware protection (AMP) is, what identity management systems are, how to use Cisco NetFlow, and details about data loss prevention (DLP).
The chapter concludes with an introduction to Digital Forensics and Incident Response (DFIR) and security operations. More details about each of these topics are covered throughout the rest of the book.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz allows you to assess whether you should read this entire chapter thoroughly or jump to the “Exam Preparation Tasks” section. If you are in doubt about your answers to these questions or your own assessment of your knowledge of the topics, read the entire chapter. Table 1-1 lists the major headings in this chapter and their corresponding “Do I Know This Already?” quiz questions. You can find the answers in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes and Review Questions.”
Table 1-1 “Do I Know This Already?” Foundation Topics Section-to-Question Mapping


Caution
The goal of self-assessment is to gauge your mastery of the topics in this chapter. If you do not know the answer to a question or are only partially sure of the answer, you should mark that question as wrong for purposes of the self-assessment. Giving yourself credit for an answer you correctly guess skews your self-assessment results and might provide you with a false sense of security.
1. Which of the following statements are true about cybersecurity practices?
a. Cybersecurity risk includes not only the risk of a data breach but also the risk of the entire organization being undermined via business activities that rely on digitization and accessibility.
b. The objective of cybersecurity is to protect each of us, our economy, our critical infrastructure, and our country from the harm that can result from inadvertent or intentional misuse, compromise, or destruction of information and information systems.
c. In the past, information security programs and policies were designed to protect the confidentiality, integrity, and availability of data within the confines of an organization. Cybersecurity is the process of protecting information by preventing, detecting, and responding to attacks.
d. All of these answers are correct.
2. Cybersecurity programs and policies expand and build on traditional information security programs but also include which of the following?
a. Cyber risk management and oversight
b. Threat intelligence
c. Threat hunting
d. All of these answers are correct.
3. Which of the following is a framework, developed by the United States government, that provides a common taxonomy, and one of the main goals is to address and manage cybersecurity risk in a cost-effective way to protect critical infrastructure?
a. The Forum of Incident Response and Security Teams (FIRST)
b. The Common Vulnerability Scoring System (CVSS)
c. NIST Cybersecurity Framework
d. The National Vulnerability Database (NVD)
4. Which of the following is a good definition of a vulnerability?
a. A weakness in the system design, implementation, software, or code, or the lack of a mechanism.
b. A common vulnerability and exposure (CVE)
c. Any potential danger to an asset
d. None of these answers are correct.
5. You are part of a vulnerability management team tasked to research information about a new vulnerability disclosed by Microsoft affecting numerous systems in your company. What database can you query to obtain more information about such a vulnerability?
a. NVD
b. CVSS
c. FIRST
d. None of these answers are correct.
6. Which of the following can be used to obtain proof-of-concept exploits against known vulnerabilities?
a. The Exploit Database by Offensive Security
b. The searchploit tool
c. GitHub
d. All of these answers are correct.
7. A number of standards are being developed for disseminating threat intelligence information. Which of the following standards is a language designed for sharing threat intelligence?
a. CWE
b. CVE
c. CVSS
d. STIX
8. Access control entries, which are part of an access control list, can classify packets by inspecting Layer 2 through Layer 4 headers for a number of parameters, including which of the following items?
a. Layer 2 protocol information such as EtherTypes
b. Layer 3 protocol information such as ICMP, TCP, or UDP
c. Layer 3 header information such as source and destination IP addresses
d. Layer 4 header information such as source and destination TCP or UDP ports
e. All of these answers are correct.
9. Which of the following is a methodology in which the intrusion detection device searches for a fixed sequence of bytes within the packets traversing the network using signatures?
a. Pattern matching and stateful pattern-matching recognition
b. Anomaly-based analysis
c. Snort-based analysis using AMP
d. NetFlow-based analysis
10. Which of the following is a solution that makes basic personal firewalls and HIPS obsolete?
a. CTA
b. CVSS
c. AMP for Endpoints
d. None of these answers are correct.
11. Which of the following protocols is used to redirect traffic from a network infrastructure device to the Cisco WSA for inspection?
a. WCCP
b. NetFlow
c. TLS
d. TAXII
12. Which of the following is the operating system used by the Cisco ESA and Cisco WSA?
a. Cisco IOS-XE
b. AsyncOS
c. Cisco FTD
d. Cisco NX-OS
13. Which of the following centralizes the management and reporting for one or more Cisco ESAs and Cisco WSAs?
a. Cisco SMA
b. Cisco FMC
c. Cisco Defense Orchestrator
d. Cisco DNAC
14. Which of the following is part of TrustSec?
a. Security group tags (SGTs)
b. Security group access control lists (SGACLs)
c. AnyConnect
d. All of these answers are correct.
15. Which of the following are examples of cloud-based security solutions?
a. Cisco Cloud Email Security (CES)
b. Cisco AMP Threat Grid
c. Umbrella (OpenDNS)
d. CloudLock
e. All of these answers are correct.
16. Which of the following are components of the 5-tuple in a NetFlow flow record?
a. Source port, destination port, source IP address, destination IP address, and protocol
b. TCP, UDP, ICMP, source IP address, destination IP address
c. Source IP address, destination IP address, source MAC address, destination MAC address, protocol
d. None of these answers are correct.
17. Which of the following is a technology that typically has the ability to detect any sensitive emails, documents, or information leaving your organization?
a. DLP
b. IDaaS
c. SaaS
d. IaaS
18. One of the primary benefits of a ____________ is that even if a single control (such as a firewall or IPS) fails, other controls can still protect your environment and assets.
a. DLP
b. AMP
c. CoPP
d. Defense-in-depth strategy
19. Which of the following is the component of the CIA triad that ensures that a system and its data have not been altered or compromised?
a. Integrity
b. Availability
c. Confidentiality
d. Nonrepudiation
20. Which of the following entities developed a tool to provide a repeatable and measurable process for organizations to measure their cybersecurity readiness?
a. FFIEC
b. FedRAMP
c. FIRST
d. ISO
21. Which of the following are considered personally identifiable information (PII)?
a. Individual’s name
b. Date of birth
c. Mother’s maiden name
d. All of these answers are correct.
22. Which of the following states that all users—whether they are individual contributors, managers, directors, or executives—should be granted only the level of privilege they need to do their jobs, and no more?
a. ISO privilege standard
b. NIST 800-61r2
c. CVSS
d. Principle of least privilege
23. Which of the following are best practices in the SOC?
a. Organizations should operate the SOC as a program rather than a single project.
b. Metrics must be established to measure the effectiveness of the SOC capabilities.
c. Analysts should collaborate with other groups such as public relations, legal, and IT.
d. All of these answers are correct.
24. Which of the following is a collection of procedures and operations performed by system administrators, security professionals, or network operators?
a. Separation of duties document
b. Vulnerability management SOP
c. Runbook
d. None of these answers are correct.
25. Which of the following refers to the way you document and preserve evidence from the time that you started the cyber forensics investigation to the time the evidence is presented at court or to your executives?
a. Best evidence
b. Chain of custody
c. Chain of trust
d. Web of trust
Foundation Topics
Introduction to Cybersecurity
The objective of cybersecurity is to protect each of us, our economy, our schools, our critical infrastructure, and any other organization from the harm that can result from inadvertent or intentional misuse, compromise, or destruction of information and information systems.
Cybersecurity risk includes not only the risk of a data breach but also the risk of the entire organization being undermined via business activities that rely on digitization and accessibility. As a result, learning how to develop an adequate cybersecurity program is crucial for any organization. Cybersecurity can no longer be something that you delegate to the information technology (IT) team. Everyone needs to be involved, including the board of directors.

Cybersecurity vs. Information Security (Infosec)
Many individuals confuse traditional information security with cybersecurity. In the past, information security programs and policies were designed to protect the confidentiality, integrity, and availability of data within the confines of an organization. Unfortunately, this is no longer sufficient. Organizations are rarely self-contained, and the price of interconnectivity is an increased level of exposure to attack. Every organization, regardless of size or geographic location, is a potential target. Cybersecurity is the process of protecting information by preventing, detecting, and responding to attacks.
Cybersecurity programs recognize that organizations must be vigilant, resilient, and ready to protect and defend every ingress and egress connection as well as organizational data wherever it is stored, transmitted, or processed. Cybersecurity programs and policies expand and build on traditional information security programs but also include the following:
• Cyber risk management and oversight
• Threat intelligence and information sharing
• Threat hunting (proactively looking for potential compromises and threats in your organization that have not been detected by your security products or technologies)
• Third-party organization, software, and hardware dependency management
• Incident response and resiliency
The NIST Cybersecurity Framework
The National Institute of Standards and Technology (NIST) is a well-known nonregulatory federal agency within the U.S. Commerce Department’s Technology Administration. NIST’s mission is to develop and promote measurement, standards, and technology to enhance productivity, facilitate trade, and improve quality of life. The Computer Security Division (CSD) is one of seven divisions within NIST’s Information Technology Laboratory. NIST’s Cybersecurity Framework is a collection of industry standards and best practices to help organizations manage cybersecurity risks. This framework is created in collaboration among the United States government, corporations, and individuals. The NIST Cybersecurity Framework can be accessed at www.nist.gov/cyberframework.
The NIST Cybersecurity Framework is developed with a common taxonomy, and one of the main goals is to address and manage cybersecurity risk in a cost-effective way to protect critical infrastructure. Although designed for a specific constituency, the requirements can serve as a security blueprint for any organization.
Additional NIST Guidance and Documents
Currently, there are more than 500 NIST information security–related documents. This number includes FIPS, the SP 800 & 1800 series, ITL bulletins, and NIST interagency reports:
• Federal Information Processing Standards (FIPS): This is the official publication series for standards and guidelines.
• Special Publication (SP) 800 series: This series reports on ITL research, guidelines, and outreach efforts in information system security and its collaborative activities with industry, government, and academic organizations. SP 800 series documents can be downloaded from https://csrc.nist.gov/publications/sp800.
• Special Publication (SP) 1800 series: This series focuses on cybersecurity practices and guidelines. SP 1800 series document can be downloaded from https://csrc.nist.gov/publications/sp1800.
• NIST Internal or Interagency Reports (NISTIR): These reports focus on research findings, including background information for FIPS and SPs.
• Information Technology Laboratory (ITL) bulletins: Each bulletin presents an in-depth discussion of a single topic of significant interest to the information systems community. Bulletins are issued on an as-needed basis.
From access controls to wireless security, the NIST publications are truly a treasure trove of valuable and practical guidance.
The International Organization for Standardization
The International Organization for Standardization (known as the ISO) is a network of the national standards institutes of more than 160 countries. The ISO has developed more than 13,000 international standards on a variety of subjects, ranging from country codes to passenger safety.
The ISO/IEC 27000 series (also known as the ISMS Family of Standards, or ISO27k for short) comprises information security standards published jointly by the ISO and the International Electrotechnical Commission (IEC).
The first six documents in the ISO/IEC 27000 series provide recommendations for “establishing, implementing, operating, monitoring, reviewing, maintaining, and improving an Information Security Management System”:
• ISO 27001 is the specification for an information security management system (ISMS).
• ISO 27002 describes the code of practice for information security management.
• ISO 27003 provides detailed implementation guidance.
• ISO 27004 outlines how an organization can monitor and measure security using metrics.
• ISO 27005 defines the high-level risk management approach recommended by ISO.
• ISO 27006 outlines the requirements for organizations that will measure ISO 27000 compliance for certification.
In all, there are more than 20 documents in the series, and several more are still under development. The framework is applicable to public and private organizations of all sizes. According to the ISO website, “the ISO standard gives recommendations for information security management for use by those who are responsible for initiating, implementing or maintaining security in their organization. It is intended to provide a common basis for developing organizational security standards and effective security management practice and to provide confidence in inter-organizational dealings.”
Threats, Vulnerabilities, and Exploits
The following sections describe the characteristics of threats, vulnerabilities, and exploits.
What Is a Threat?

A threat is any potential danger to an asset. If a vulnerability exists but has not yet been exploited—or, more importantly, it is not yet publicly known—the threat is latent and not yet realized. If someone is actively launching an attack against your system and successfully accesses something or compromises your security against an asset, the threat is realized. The entity that takes advantage of the vulnerability is known as the malicious actor, and the path used by this actor to perform the attack is known as the threat agent or threat vector.
What Is a Vulnerability?

A vulnerability is a weakness in the system design, implementation, software, or code, or the lack of a mechanism. A specific vulnerability might manifest as anything from a weakness in system design to the implementation of an operational procedure. The correct implementation of safeguards and security countermeasures could mitigate a vulnerability and reduce the risk of exploitation.
Vulnerabilities and weaknesses are common, mainly because there isn’t any perfect software or code in existence. Some vulnerabilities have limited impact and are easily mitigated; however, many have broader implications.
Vulnerabilities can be found in each of the following:
• Applications: Software and applications come with tons of functionality. Applications might be configured for usability rather than for security. Applications might be in need of a patch or update that may or may not be available. Attackers targeting applications have a target-rich environment to examine. Just think of all the applications running on your home or work computer.
• Operating systems: Operating system software is loaded on workstations and servers. Attackers can search for vulnerabilities in operating systems that have not been patched or updated.
• Hardware: Vulnerabilities can also be found in hardware. Mitigation of a hardware vulnerability might require patches to microcode (firmware) as well as the operating system or other system software. Good examples of well-known hardware-based vulnerabilities are Spectre and Meltdown. These vulnerabilities take advantage of a feature called speculative execution common to most modern processor architectures.
• Misconfiguration: The configuration file and configuration setup for the device or software may be misconfigured or may be deployed in an unsecure state. This might be open ports, vulnerable services, or misconfigured network devices. Just consider wireless networking. Can you detect any wireless devices in your neighborhood that have encryption turned off?
• Shrinkwrap software: This is the application or executable file that is run on a workstation or server. When installed on a device, it can have tons of functionality or sample scripts or code available.
Vendors, security researchers, and vulnerability coordination centers typically assign vulnerabilities an identifier that’s disclosed to the public. This is known as the Common Vulnerabilities and Exposures (CVE) identifier. CVE is an industry-wide standard. CVE is sponsored by US-CERT, the office of Cybersecurity and Communications at the U.S. Department of Homeland Security. Operating as DHS’s Federally Funded Research and Development Center (FFRDC), MITRE has copyrighted the CVE list for the benefit of the community to ensure it remains a free and open standard, as well as to legally protect the ongoing use of it and any resulting content by government, vendors, and/or users.
Figure 1-1 shows an example of a Cisco security advisory disclosing a vulnerability in Cisco products. This advisory includes a CVE ID and detailed information about the vulnerability severity, description, affected configuration, fixes, and other related vulnerability content.

Figure 1-1 A Cisco Security Advisory
MITRE maintains the CVE list and its public website, manages the CVE Compatibility Program, oversees the CVE numbering authorities (CNAs), and provides impartial technical guidance to the CVE Editorial Board throughout the process to ensure CVE serves the public interest.
The goal of CVE is to make it easier to share data across tools, vulnerability repositories, and security services. Figure 1-2 shows the CVE entry in MITRE’s CVE website for the vulnerability addressed in the security advisory shown in Figure 1-1.

Figure 1-2 MITRE’s CVE Example
The National Vulnerability Database (NVD) also maintains a detailed list of vulnerabilities disclosed in the industry. NVD can be accessed at https://nvd.nist.gov/, and an example of the same vulnerability report in NVD is shown in Figure 1-3.

Figure 1-3 The National Vulnerability Database
What Is an Exploit?

An exploit refers to a piece of software, a tool, a technique, or a process that takes advantage of a vulnerability that leads to access, privilege escalation, loss of integrity, or denial of service on a computer system. Exploits are dangerous because all software has vulnerabilities; hackers and perpetrators know that there are vulnerabilities and seek to take advantage of them. Although most organizations attempt to find and fix vulnerabilities, some organizations lack sufficient funds, processes, policies, and design practices for securing their networks. Sometimes no one may even know the vulnerability exists, and it is exploited. That is known as a zero-day exploit. Even when you do know there is a problem, you are burdened with the fact that a window exists between when a vulnerability is disclosed and when a patch is available to prevent the exploit. The more critical the server, the slower it is usually patched. Management might be afraid of interrupting the server or afraid that the patch might affect stability or performance. Finally, the time required to deploy and install the software patch on production servers and workstations exposes an organization’s IT infrastructure to an additional period of risk.
There are several places where people trade exploits for malicious intent. The most prevalent is the dark web. The dark web (or darknet) is an overlay of networks and systems that use the Internet but require specific software and configurations to access it. The dark web is just a small part of the deep web. The deep web is a collection of information and systems on the Internet that is not indexed by web search engines. Often people incorrectly confuse the term deep web with dark web.
Not all exploits are shared for malicious intent. For example, many security researchers share proof-of-concept (POC) exploits in public sites such as The Exploit Database (or Exploit-DB) and GitHub. The Exploit Database is a site maintained by Offensive Security where security researchers and other individuals post exploits for known vulnerabilities. The Exploit Database can be accessed at www.exploit-db.com. Figure 1-4 shows an example of a publicly available exploit in the Exploit Database.

Figure 1-4 The Exploit Database (Exploit-DB)
Note
A command-line tool called searchsploit enables you to download a copy of the Exploit Database so that you can use it on the go.
Risk, Assets, Threats, and Vulnerabilities
As with any new technology topic, to better understand the security field, you must learn the terminology that is used. To be a security professional, you need to understand the relationship between risk, threats, assets, and vulnerabilities.
Risk is the probability or likelihood of the occurrence or realization of a threat. There are three basic elements of risk: assets, threats, and vulnerabilities. To deal with risk, the U.S. federal government has adopted a Risk Management Framework (RMF). The RMF process is based on the key concepts of mission- and risk-based, cost-effective, and enterprise information system security. NIST Special Publication 800-37, “Guide for Applying the Risk Management Framework to Federal Information Systems,” transforms the traditional Certification and Accreditation (C&A) process into the six-step RMF. Let’s look at the various components associated with risk, which include assets, threats, and vulnerabilities.
An asset is any item of economic value owned by an individual or corporation. Assets can be real—such as routers, servers, hard drives, and laptops—or assets can be virtual, such as formulas, databases, spreadsheets, trade secrets, and processing time. Regardless of the type of asset discussed, if the asset is lost, damaged, or compromised, there can be an economic cost to the organization.
Note
No organization can ever be 100 percent secure. There will always be some risk left over. This is known as residual risk, which is the amount of risk left after safeguards and controls have been put in place to protect the asset.
A threat sets the stage for risk and is any agent, condition, or circumstance that could potentially cause harm, loss, or damage, or compromise an IT asset or data asset. From a security professional’s perspective, threats can be categorized as events that can affect the confidentiality, integrity, or availability of the organization’s assets. These threats can result in destruction, disclosure, modification, corruption of data, or denial of service. Examples of the types of threats an organization can face include the following:
• Natural disasters, weather, and catastrophic damage: Hurricanes, storms, weather outages, fires, floods, earthquakes, and other natural events compose an ongoing threat.
• Hacker attacks: An insider or outsider who is unauthorized and purposely attacks an organization’s infrastructure, components, systems, or data.
• Cyberattack: Attackers who target critical national infrastructures such as water plants, electric plants, gas plants, oil refineries, gasoline refineries, nuclear power plants, waste management plants, and so on. Stuxnet is an example of one such tool designed for just such a purpose.
• Viruses and malware: An entire category of software tools that are malicious and are designed to damage or destroy a system or data.
• Disclosure of confidential information: Anytime a disclosure of confidential information occurs, it can be a critical threat to an organization if such disclosure causes loss of revenue, causes potential liabilities, or provides a competitive advantage to an adversary. For instance, if your organization experiences a breach and detailed customer information is exposed (for example, personally identifiable information [PII]), such a breach could have potential liabilities and loss of trust from your customers. Another example is when a threat actor steals source code or design documents and sells them to your competitors.
• Denial-of-service (DoS) or distributed denial-of-service (DDoS) attacks: An attack against availability that is designed to bring the network, or access to a particular TCP/IP host/server, to its knees by flooding it with useless traffic. Today, most DoS attacks are launched via botnets, whereas in the past tools such as the Ping of Death or Teardrop may have been used. As with malware, hackers constantly develop new DoS tools so that Storm and Mariposa, for example, are replaced with other, more current threats.
Note
If the organization is vulnerable to any of these threats, there is an increased risk of a successful attack.
Threat Actors
Threat actors are the individuals (or a group of individuals) who perform an attack or are responsible for a security incident that impacts or has the potential of impacting an organization or individual. There are several types of threat actors:
• Script kiddies: These people use existing “scripts” or tools to hack into computers and networks. They lack the expertise to write their own scripts.
• Organized crime groups: The main purpose of these groups is to steal information, scam people, and make money.
• State sponsors and governments: These agents are interested in stealing data, including intellectual property and research-and-development data from major manufacturers, government agencies, and defense contractors.
• Hacktivists: These people carry out cybersecurity attacks aimed at promoting a social or political cause.
• Terrorist groups: These groups are motivated by political or religious beliefs.
Originally, the term hacker was used for a computer enthusiast. A hacker was a person who enjoyed understanding the internal workings of a system, computer, and computer network and who would continue to hack until he understood everything about the system. Over time, the popular press began to describe hackers as individuals who broke into computers with malicious intent. The industry responded by developing the word cracker, which is short for a criminal hacker. The term cracker was developed to describe individuals who seek to compromise the security of a system without permission from an authorized party. With all this confusion over how to distinguish the good guys from the bad guys, the term ethical hacker was coined. An ethical hacker is an individual who performs security tests and other vulnerability-assessment activities to help organizations secure their infrastructures. Sometimes ethical hackers are referred to as white hat hackers.
Hacker motives and intentions vary. Some hackers are strictly legitimate, whereas others routinely break the law. Figure 1-5 shows some of the most common categories used in the industry to identify hackers and their motives.


Figure 1-5 White, Black, and Gray Hackers

Threat Intelligence
Threat intelligence is referred to as the knowledge about an existing or emerging threat to assets, including networks and systems. Threat intelligence includes context, mechanisms, indicators of compromise (IoCs), implications, and actionable advice. Threat intelligence includes specifics on the tactics, techniques, and procedures of these adversaries. The primary purpose of threat intelligence is to inform business decisions regarding the risks and implications associated with threats.
Converting these definitions into common language could translate to threat intelligence being evidence-based knowledge of the capabilities of internal and external threat actors. This type of data can be beneficial for the security operations center (SOC) of any organization. Threat intelligence extends cybersecurity awareness beyond the internal network by consuming intelligence from other sources Internetwide related to possible threats to you or your organization. For instance, you can learn about threats that have impacted different external organizations. Subsequently, you can proactively prepare rather than react once the threat is seen against your network. Providing an enrichment data feed is one service that threat intelligence platforms would typically provide.
Figure 1-6 shows a five-step threat intelligence process for evaluating threat intelligence sources and information.

Figure 1-6 The Threat Intelligence Process
Many different threat intelligence platforms and services are available in the market nowadays. Cyber threat intelligence focuses on providing actionable information on adversaries, including IoCs. Threat intelligence feeds help you prioritize signals from internal systems against unknown threats. Cyber threat intelligence allows you to bring more focus to cybersecurity investigation because, instead of blindly looking for “new” and “abnormal” events, you can search for specific IoCs, IP addresses, URLs, or exploit patterns.
A number of standards are being developed for disseminating threat intelligence information. The following are a few examples:
![]()
• Structured Threat Information eXpression (STIX): This express language is designed for sharing cyberattack information. STIX details can contain data such as the IP addresses or domain names of command and control servers (often referred to C2 or CnC), malware hashes, and so on. STIX was originally developed by MITRE and is now maintained by OASIS. You can obtain more information at http://stixproject.github.io.
• Trusted Automated eXchange of Indicator Information (TAXII): This open transport mechanism standardizes the automated exchange of cyber threat information. TAXII was originally developed by MITRE and is now maintained by OASIS. You can obtain more information at http://taxiiproject.github.io.
• Cyber Observable eXpression (CybOX): This free standardized schema is used for specification, capture, characterization, and communication of events of stateful properties that are observable in the operational domain. CybOX was originally developed by MITRE and is now maintained by OASIS. You can obtain more information at https://cyboxproject.github.io.
• Open Indicators of Compromise (OpenIOC): This open framework is used for sharing threat intelligence in a machine-digestible format. Learn more at www.openioc.org.
• Open Command and Control (OpenC2): This language is used for the command and control of cyber-defense technologies. OpenC2 Forum was a community of cybersecurity stakeholders that was facilitated by the U.S. National Security Agency. OpenC2 is now an OASIS technical committee (TC) and specification. You can obtain more information at www.oasis-open.org/committees/tc_home.php?wg_abbrev=openc2.
It should be noted that many open-source and non-security-focused sources can be leveraged for threat intelligence as well. Some examples of these sources are social media, forums, blogs, and vendor websites.
Tip
You can obtain different examples of threat intelligence STIX documents at https://oasis-open.github.io/cti-documentation/stix/examples. The following GitHub repository includes thousands of references and resources related to threat intelligence, threat hunting, ethical hacking, penetration testing, digital forensics, incident response, vulnerability research, exploit development, reverse engineering, and more: https://github.com/The-Art-of-Hacking/h4cker.
![]()
Threat Intelligence Platform
Many organizations deploy their own threat intelligence platforms (TIPs) to aggregate, correlate, and analyze threat intelligence information from multiple sources in near real time. In order for analysts in the security operations center (SOC) to defend against today’s threats, TIPs need to scale and support the growing amount of threat intelligence data generated by a variety of resources (including system logs and threat intelligence feeds). Modern threat intelligence platforms provide and also use APIs to gather or exchange data.
Threat intelligence platforms support the following:
• Threat intelligence collection: Collecting and aggregating multiple data formats including CSV, STIX, XML, JSON, IODEK, OpenIOC, and proprietary threat intelligence feeds.
• Data correlation: Automatically analyzing and correlating threat intelligence data.
• Enrichment and contextualization: Provides enriched context around threats in order to enable SOC analysts and incident responders to have as much data as possible regarding the attack and the threat actor (adversary).
• Analyze: Automates the analysis of threat indicators to enable the identification of the adversary’s tactics, techniques, and procedures (TTPs). Often TIPs can leverage the adversary tactics and techniques included in MITRE’s ATT&CK framework (attack.mitre.org).
• Integrations with other security systems: Modern TIPs provide the ability to integrate with many different security solutions (including Security Information and Event Management [SIEM] and Security Orchestration Automation and Response [SOAR] solutions).
• Act: The threat intelligence platform should enable security professionals to create tools and applications that can help respond to and mitigate cybersecurity threats and attacks.
Vulnerabilities, Exploits, and Exploit Kits
Earlier in this chapter, you learned that a vulnerability is a weakness in the system design, implementation, software, or code, or the lack of a mechanism. The number of disclosed vulnerabilities continues to rise. You can keep up with vulnerability disclosures by subscribing to vulnerability feeds and searching public repositories such as the National Vulnerability Database (NVD). The NVD can be accessed at https://nvd.nist.gov.
Tip
Vulnerabilities are typically identified by a Common Vulnerabilities and Exposures (CVE) identifier. CVE is an identifier for publicly known security vulnerabilities. This is a standard created and maintained by MITRE and used by numerous organizations in the industry, as well as security researchers. You can find more information about the CVE specification and search the CVE list at https://cve.mitre.org.
There are many different software and hardware vulnerabilities and related categories.
The following are examples of injection-based vulnerabilities:
• SQL injection vulnerabilities
• HTML injection vulnerabilities
• Command injection vulnerabilities
Code injection vulnerabilities are exploited by forcing an application or a system to process invalid data. An attacker takes advantage of this type of vulnerability to inject code into a vulnerable system and change the course of execution. Successful exploitation can lead to the disclosure of sensitive information, manipulation of data, denial-of-service conditions, and more. Examples of code injection vulnerabilities include the following:
• SQL injection
• HTML script injection
• Dynamic code evaluation
• Object injection
• Remote file inclusion
• Uncontrolled format string
• Shell injection

SQL Injection
SQL injection (SQLi) vulnerabilities can be catastrophic because they can allow an attacker to view, insert, delete, or modify records in a database. In an SQL injection attack, the attacker inserts, or injects, partial or complete SQL queries via the web application. The attacker injects SQL commands into input fields in an application or a URL to execute predefined SQL commands.
Web applications construct SQL statements involving SQL syntax invoked by the application mixed with user-supplied data, as follows:
SELECT * FROM Users WHERE UserName LIKE ‘%Santos%’;
The actual SQL statement is not shown to the user. Typically, the application sends this portion to the database behind the scenes. The highlighted portion of the SQL statement is typically user input in a web form.
If an application does not sanitize user input, an attacker can supply crafted input in an attempt to make the original SQL statement execute further actions in the database. SQL injections can be done using user-supplied strings or numeric input. The following is an example of a basic SQL injection attack:
Santos’ OR 1=1;--
When the string Santos’ OR 1=1;-- is entered in a web form of a vulnerable application, it may cause the application to display all records in the database table to the attacker.
One of the first steps when finding SQL injection vulnerabilities is to understand when the application interacts with a database. This is typically done with web authentication forms, search engines, and interactive sites such as e-commerce sites.
SQL injection attacks can be divided into the following categories:
• In-band SQL injection: With this type of injection, the attacker obtains the data by using the same channel that is used to inject the SQL code. This is the most basic form of an SQL injection attack, where the data is dumped directly in a web application (or web page).
• Out-of-band SQL injection: With this type of injection, the attacker retrieves data using a different channel. For example, an email, a text, or an instant message could be sent to the attacker with the results of the query. Alternatively, the attacker might be able to send the compromised data to another system.
• Blind (or inferential) SQL injection: With this type of injection, the attacker does not make the application display or transfer any data; rather, the attacker is able to reconstruct the information by sending specific statements and discerning the behavior of the application and database.
To perform an SQL injection attack, an attacker must craft a syntactically correct SQL statement (query). The attacker may also take advantage of error messages coming back from the application and might be able to reconstruct the logic of the original query to understand how to execute the attack correctly. If the application hides the error details, the attacker might need to reverse engineer the logic of the original query.
HTML Injection
An HTML injection is a vulnerability that occurs when an unauthorized user is able to control an input point and able to inject arbitrary HTML code into a web application. Successful exploitation could lead to disclosure of a user’s session cookies; an attacker might do this to impersonate a victim or to modify the web page or application content seen by the victims.
HTML injection vulnerabilities can lead to cross-site scripting (XSS). You learn details about the different types of XSS vulnerabilities and attacks later in this chapter.

Command Injection
A command injection is an attack in which an attacker tries to execute commands that she is not supposed to be able to execute on a system via a vulnerable application. Command injection attacks are possible when an application does not validate data supplied by the user (for example, data entered in web forms, cookies, HTTP headers, and other elements). The vulnerable system passes that data into a system shell.
With command injection, an attacker tries to send operating system commands so that the application can execute them with the privileges of the vulnerable application. Command injection is not the same as code execution and code injection, which involve exploiting a buffer overflow or similar vulnerability.
Authentication-Based Vulnerabilities
An attacker can bypass authentication in vulnerable systems by using several methods.
The following are the most common ways to take advantage of authentication-based vulnerabilities in an affected system:

• Credential brute forcing
• Session hijacking
• Redirecting
• Exploiting default credentials
• Exploiting weak credentials
• Exploiting Kerberos vulnerabilities
Credential Brute-Force Attacks and Password Cracking
In a credential brute-force attack, the attacker attempts to log in to an application or a system by trying different usernames and passwords. There are two major categories of brute-force attacks:
• Online brute-force attacks: In this type of attack, the attacker actively tries to log in to the application directly by using many different combinations of credentials. Online brute-force attacks are easy to detect because you can easily inspect for large numbers of attempts by an attacker.
• Offline brute-force attacks: In this type of attack, the attacker can gain access to encrypted data or hashed passwords. These attacks are more difficult to prevent and detect than online attacks. However, offline attacks require significantly more computation effort and resources from the attacker.
The strength of user and application credentials has a direct effect on the success of brute-force attacks. Weak credentials are one of the major causes of credential compromise. The more complex and the longer a password (credential), the better. An even better approach is to use multifactor authentication (MFA). The use of MFA significantly reduces the probability of success for these types of attacks.
An attacker may feed to an attacking system a word list containing thousands of words in order to crack passwords or associated credentials. The following site provides links to millions of real-world passwords: http://wordlists.h4cker.org.
Weak cryptographic algorithms (such as RC4, MD5, and DES) allow attackers to easily crack passwords.
Tip
The following site lists the cryptographic algorithms that should be avoided and the ones that are recommended, as well as several other recommendations: www.cisco.com/c/en/us/about/security-center/next-generation-cryptography.html.
Attackers can also use statistical analysis and rainbow tables against systems that improperly protect passwords with a one-way hashing function. A rainbow table is a precomputed table for reversing cryptographic hash functions and for cracking password hashes. Such tables can be used to accelerate the process of cracking password hashes.
In addition to weak encryption or hashing algorithms, poorly designed security protocols such as Wired Equivalent Privacy (WEP) introduce avenues of attack to compromise user and application credentials. Also, if hashed values are stored without being rendered unique first (that is, without a salt), it is possible to gain access to the values and perform a rainbow table attack.
An organization should implement techniques on systems and applications to throttle login attempts and prevent brute-force attacks. Those attempts should also be logged and audited.
Session Hijacking
There are several ways an attacker can perform a session hijack and several ways a session token may be compromised:
• Predicting session tokens: If an attacker can predict session tokens, they can easily hijack the web session to further compromise the system or steal data.
• Session sniffing: This can occur through collecting packets of unencrypted web sessions.
• Man-in-the-middle (MITM) attack: With this type of attack, the attacker sits in the path between the client and the web server.
• Man-in-the-browser (MITB) attack: This attack is similar in approach to a man-in-the-middle attack; however, in this case, a browser (or an extension or a plug-in) is compromised and used to intercept and manipulate web sessions between the user and the web server.
If web applications do not validate and filter out invalid session ID values, they can potentially be used to exploit other web vulnerabilities, such as SQL injection (if the session IDs are stored on a relational database) or persistent XSS (if the session IDs are stored and reflected back afterward by the web application).
Default Credentials
A common adage in the security industry is, “Why do you need hackers if you have default passwords?” Many organizations and individuals leave infrastructure devices such as routers, switches, wireless access points, and even firewalls configured with default passwords.
Attackers can easily identify and access systems that use shared default passwords. It is extremely important to always change default manufacturer passwords and restrict network access to critical systems. A lot of manufacturers now require users to change the default passwords during initial setup, but some don’t.
Attackers can easily obtain default passwords and identify Internet-connected target systems. Passwords can be found in product documentation and compiled lists available on the Internet. An example is www.defaultpassword.com, but dozens of other sites contain default passwords and configurations on the Internet. It is easy to identify devices that have default passwords and that are exposed to the Internet by using search engines such as Shodan (www.shodan.io).
Insecure Direct Object Reference Vulnerabilities
Insecure Direct Object Reference vulnerabilities can be exploited when web applications allow direct access to objects based on user input. Successful exploitation could allow attackers to bypass authorization and access resources that should be protected by the system (for example, database records and system files). This vulnerability occurs when an application does not sanitize user input and does not perform appropriate authorization checks.
An attacker can take advantage of Insecure Direct Object Reference vulnerabilities by modifying the value of a parameter used to directly point to an object. To exploit this type of vulnerability, an attacker needs to map out all locations in the application where user input is used to reference objects directly. Example 1-1 shows how the value of a parameter can be used directly to retrieve a database record.
Example 1-1 A URL Parameter Used Directly to Retrieve a Database Record
https://store.h4cker.org/buy?customerID=1245
In this example, the value of the customerID parameter is used as an index in a table of a database holding customer contacts. The application takes the value and queries the database to obtain the specific customer record. An attacker may be able to change the value 1245 to another value and retrieve another customer record.
In Example 1-2, the value of a parameter is used directly to execute an operation in the system.
Example 1-2 Direct Object Reference Example
https://store.h4cker.org/changepassd?user=omar
In Example 1-2, the value of the user parameter (omar) is used to have the system change the user’s password. An attacker can try other usernames and see whether it is possible to modify the password of another user.
Mitigations for this type of vulnerability include input validation, the use of per-user or -session indirect object references, and access control checks to make sure the user is authorized for the requested object.

Cross-Site Scripting
Cross-site scripting (commonly known as XSS) vulnerabilities have become some of the most common web application vulnerabilities. XSS vulnerabilities are classified in three major categories:
• Reflected XSS
• Stored (persistent) XSS
• DOM-based XSS
Attackers can use obfuscation techniques in XSS attacks by encoding tags or malicious portions of the script using Unicode so that the link or HTML content is disguised to the end user browsing the site.
Tip
Dozens of examples of XSS vectors are listed at the GitHub repository https://github.com/The-Art-of-Hacking/h4cker, along with numerous other cybersecurity references.
Reflected XSS attacks (nonpersistent XSS) occur when malicious code or scripts are injected by a vulnerable web application using any method that yields a response as part of a valid HTTP request. An example of a reflected XSS attack is a user being persuaded to follow a malicious link to a vulnerable server that injects (reflects) the malicious code back to the user’s browser. This causes the browser to execute the code or script. In this case, the vulnerable server is usually a known or trusted site.
Examples of methods of delivery for XSS exploits are phishing emails, messaging applications, and search engines.
Stored, or persistent, XSS attacks occur when the malicious code or script is permanently stored on a vulnerable or malicious server, using a database. These attacks are typically carried out on websites hosting blog posts (comment forms), web forums, and other permanent storage methods. An example of a stored XSS attack is a user requesting the stored information from the vulnerable or malicious server, which causes the injection of the requested malicious script into the victim’s browser. In this type of attack, the vulnerable server is usually a known or trusted site.
The Document Object Model (DOM) is a cross-platform and language-independent application programming interface (API) that treats an HTML, XHTML, or XML document as a tree structure. DOM-based attacks are typically reflected XSS attacks that are triggered by sending a link with inputs that are reflected to the web browser. In DOM-based XSS attacks, the payload is never sent to the server. Instead, the payload is only processed by the web client (browser).
In a DOM-based XSS attack, the attacker sends a malicious URL to the victim, and after the victim clicks on the link, it may load a malicious website or a site that has a vulnerable DOM route handler. After the vulnerable site is rendered by the browser, the payload executes the attack in the user’s context on that site.
One of the effects of any type of XSS attack is that the victim typically does not realize that an attack has taken place. DOM-based applications use global variables to manage client-side information. Often developers create unsecured applications that put sensitive information in the DOM (for example, tokens, public profile URLs, private URLs for information access, cross-domain OAuth values, and even user credentials as variables). It is a best practice to avoid storing any sensitive information in the DOM when building web applications.
Successful exploitation could result in installation or execution of malicious code, account compromise, session cookie hijacking, revelation or modification of local files, or site redirection.
The results of XSS attacks are the same regardless of the vector. Even though XSS vulnerabilities are flaws in a web application, the attack typically targets the end user. You typically find XSS vulnerabilities in the following:
• Search fields that echo a search string back to the user
• HTTP headers
• Input fields that echo user data
• Error messages that return user-supplied text
• Hidden fields that may include user input data
• Applications (or websites) that display user-supplied data
Example 1-3 demonstrates an XSS test that can be performed from a browser’s address bar.
Example 1-3 XSS Test from a Browser’s Address Bar
javascript:alert(“omar_XSS_test"); javascript:alert(document.cookie);
Example 1-4 demonstrates an XSS test that can be performed in a user input field in a web form.
Example 1-4 XSS Test from a Web Form
<script>alert(“XSS Test")</script>

Cross-Site Request Forgery
Cross-site request forgery (CSRF or XSRF) attacks occur when unauthorized commands are transmitted from a user who is trusted by the application. CSRF attacks are different from XSS attacks because they exploit the trust that an application has in a user’s browser. CSRF vulnerabilities are also referred to as one-click attacks or session riding.
CSRF attacks typically affect applications (or websites) that rely on a user’s identity. Attackers can trick the user’s browser into sending HTTP requests to a target website. An example of a CSRF attack is a user authenticated by the application by a cookie saved in the browser unwittingly sending an HTTP request to a site that trusts the user, subsequently triggering an unwanted action.
Cookie Manipulation Attacks
Cookie manipulation attacks are often referred to as stored DOM-based attacks (or vulnerabilities). Cookie manipulation is possible when vulnerable applications store user input and then embed that input in a response within a part of the DOM. This input is later processed in an unsafe manner by a client-side script. An attacker can use a JavaScript string (or other scripts) to trigger the DOM-based vulnerability. Such scripts can write controllable data into the value of a cookie.
An attacker can take advantage of stored DOM-based vulnerabilities to create a URL that sets an arbitrary value in a user’s cookie. The impact of a stored DOM-based vulnerability depends on the role that the cookie plays within the application.
Race Conditions
A race condition occurs when a system or an application attempts to perform two or more operations at the same time. However, due to the nature of such a system or application, the operations must be done in the proper sequence to be done correctly. When an attacker exploits such a vulnerability, he has a small window of time between when a security control takes effect and when the attack is performed. The attack complexity in race conditions is very high. In other words, race conditions are very difficult to exploit.
Race conditions are also referred to as time of check to time of use (TOCTOU) attacks. An example of a race condition is a security management system pushing a configuration to a security device (such as a firewall or an intrusion prevention system) such that the process rebuilds access control lists (ACLs) and rules from the system. An attacker might have a very small time window in which it could bypass those security controls until they take effect on the managed device.
Unprotected APIs
Application programming interfaces (APIs) are used everywhere today. A large number of modern applications use some type of API to allow other systems to interact with the application. Unfortunately, many APIs lack adequate controls and are difficult to monitor. The breadth and complexity of APIs also make it difficult to automate effective security testing. There are a few methods or technologies behind modern APIs:
• Simple Object Access Protocol (SOAP): This standards-based web services access protocol was originally developed by Microsoft and has been used by numerous legacy applications for many years. SOAP exclusively uses XML to provide API services. XML-based specifications are governed by XML Schema Definition (XSD) documents. SOAP was originally created to replace older solutions such as the Distributed Component Object Model (DCOM) and Common Object Request Broker Architecture (CORBA). You can find the latest SOAP specifications at www.w3.org/TR/soap.
• Representational State Transfer (REST): This API standard is easier to use than SOAP. It uses JSON instead of XML, and it uses standards such as Swagger and the OpenAPI Specification (www.openapis.org) for ease of documentation and to encourage adoption.
• GraphQL: GraphQL is a query language for APIs that provides many developer tools. GraphQL is now used for many mobile applications and online dashboards. Many different languages support GraphQL. You can learn more about GraphQL at https://graphql.org/code.
SOAP and REST use the HTTP protocol; however, SOAP limits itself to a more strict set of API messaging patterns than REST.
An API often provides a roadmap that describes the underlying implementation of an application. This roadmap can give penetration testers valuable clues about attack vectors they might otherwise overlook. API documentation can provide a great level of detail that can be very valuable to a security professional, as well to attackers. API documentation can include the following:
• Swagger (OpenAPI): Swagger is a modern framework of API documentation and development that is the basis of the OpenAPI Specification (OAS). Additional information about Swagger can be obtained at https://swagger.io. The OAS specification is available at https://github.com/OAI/OpenAPI-Specification.
• Web Services Description Language (WSDL) documents: WSDL is an XML-based language that is used to document the functionality of a web service. The WSDL specification can be accessed at www.w3.org/TR/wsdl20-primer.
• Web Application Description Language (WADL) documents: WADL is an XML-based language for describing web applications. The WADL specification can be obtained from www.w3.org/Submission/wadl.
Return-to-LibC Attacks and Buffer Overflows
A return-to-libc (or ret2libc) attack typically starts with a buffer overflow. In this type of attack, a subroutine return address on a call stack is replaced by an address of a subroutine that is already present in the executable memory of the process. This is done to potentially bypass the no-execute (NX) bit feature and allow attackers to inject their own code.
Operating systems that support nonexecutable stack help protect against code execution after a buffer overflow vulnerability is exploited. However, a nonexecutable stack cannot prevent a ret2libc attack because in this attack, only existing executable code is used. Another technique, called stack-smashing protection, can prevent or obstruct code execution exploitation because it can detect the corruption of the stack and can potentially “flush out” the compromised segment.
Tip
The following video provides a detailed explanation of what buffer overflow attacks are: www.youtube.com/watch?v=1S0aBV-Waeo.
A technique called ASCII armoring can be used to mitigate ret2libc attacks. When you implement ASCII armoring, the address of every system library (such as libc) contains a NULL byte (0x00) that you insert in the first 0x01010101 bytes of memory. This is typically a few pages more than 16 MB and is called the ASCII armor region because every address up to (but not including) this value contains at least one NULL byte. When this methodology is implemented, an attacker cannot place code containing those addresses using string manipulation functions such as strcpy().
Of course, this technique doesn’t protect the system if the attacker finds a way to overflow NULL bytes into the stack. A better approach is to use the address space layout randomization (ASLR) technique, which mitigates the attack on 64-bit systems. When you implement ASLR, the memory locations of functions are random. ASLR is not very effective in 32-bit systems, though, because only 16 bits are available for randomization, and an attacker can defeat such a system by using brute-force attacks.

OWASP Top 10
The Open Web Application Security Project (OWASP) is a nonprofit charitable organization that leads several industrywide initiatives to promote the security of applications and software. The organization lists the top 10 most common vulnerabilities against application at the following address:
www.owasp.org/index.php/Category:OWASP_Top_Ten_Project
Tip
It is recommended that you become familiar and always keep up with the OWASP Top 10 list. OWASP not only defines each of the vulnerabilities but also provides a list of techniques to prevent and mitigate those vulnerabilities. OWASP also has local chapters around the world that are free and open to anyone. Many chapters also have meetings, presentations, and training that help the community. Information about the OWASP local chapters can be obtained at www.owasp.org/index.php/OWASP_Chapter.
Security Vulnerabilities in Open-Source Software
Security vulnerability patching for commercial and open-source software is one of the most important processes of any organization. An organization might use the following technologies and systems to maintain an appropriate vulnerability management program:
• Vulnerability management software and scanners, such as Qualys, Nexpose, and Nessus
• Software composition analysis tools, such as BlackDuck Hub, Synopsys Protecode (formerly known as AppCheck), FlexNet Code Insight (formerly known as Palamida), SourceClear, and WhiteSource
• Security vulnerability feeds, such as MITRE’s CVE list, NIST’s National Vulnerability Database (NVD), VulnDB, and Recorded Future
Network Security Systems
The Cisco CyberOps Associate Certification assumes that you have familiarity with routers, switches, firewalls, intrusion detection systems (IDSs), and intrusion prevention systems (IPSs). However, here is a quick refresh for your reference. Many network security devices have been invented throughout the years to enforce policy and maintain visibility of everything that is happening in the network. These network security devices include the following:
• Traditional firewalls
• Next-generation firewalls
• Personal firewalls
• Intrusion detection systems
• Traditional and next-generation intrusion prevention systems
• Anomaly detection systems
• Advanced malware protection (AMP)
• Web security appliances
• Email security appliances
• Identity management systems
Traditional Firewalls
Typically, firewalls are devices that are placed, or deployed, between a trusted and an untrusted network, as illustrated in Figure 1-7.

Figure 1-7 Traditional Firewall Deployment
In Figure 1-7, the trusted network is labeled as the “inside” network, and the untrusted network is labeled as the “outside” network. The untrusted network in this case is connected to the Internet. This is the typical nomenclature you’ll often see in Cisco and non-Cisco documentation. When firewalls are connected to the Internet, they are often referred to as Internet edge firewalls. A detailed understanding of how firewalls and their related technologies work is extremely important for all network security professionals. This knowledge not only helps you configure and manage the security of your networks accurately and effectively, but also allows you to gain an understanding of how to enforce policies and achieve network segmentation suitable for your environment.
Several firewall solutions offer user and application policy enforcement to supply protection for different types of security threats. These solutions often provide logging capabilities that enable security administrators to identify, investigate, validate, and mitigate such threats.
Additionally, several software applications can run on a system to protect only that host. These types of applications are known as personal firewalls. This section includes an overview of network firewalls and their related technologies. Later in this chapter, you will learn the details about personal firewalls.
![]()
Network-based firewalls provide key features that are used for perimeter security, such as Network Address Translation (NAT), access control lists, and application inspection. The primary task of a network firewall is to deny or permit traffic that attempts to enter or leave the network based on explicit preconfigured policies and rules. Firewalls are often deployed in several other parts of the network to provide network segmentation within the corporate infrastructure and also in data centers. The processes used to allow or block traffic may include the following:
• Simple packet-filtering techniques
• Application proxies
• Network Address Translation
• Stateful inspection firewalls
• Next-generation context-aware firewalls
Packet-Filtering Techniques
The purpose of packet filters is simply to control access to specific network segments by defining which traffic can pass through them. They usually inspect incoming traffic at the transport layer of the Open Systems Interconnection (OSI) model. For example, packet filters can analyze Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) packets and compare them against a set of predetermined rules called access control lists. They inspect the following elements within a packet:
• Source address
• Destination address
• Source port
• Destination port
• Protocol
![]()
ACLs are typically configured in firewalls, but they also can be configured in network infrastructure devices such as routers, switches, wireless LAN controllers (WLCs), and others.
Each entry of an ACL is referred to as an access control entry (ACE). These ACEs can classify packets by inspecting Layer 2 through Layer 4 headers for a number of parameters, including the following:
• Layer 2 protocol information such as EtherTypes
• Layer 3 protocol information such as ICMP, TCP, or UDP
• Layer 3 header information such as source and destination IP addresses
• Layer 4 header information such as source and destination TCP or UDP ports
After an ACL has been properly configured, you can apply it to an interface to filter traffic. The firewall or networking device can filter packets in both the inbound and outbound direction on an interface. When an inbound ACL is applied to an interface, the security appliance analyzes packets against the ACEs after receiving them. If a packet is permitted by the ACL, the firewall continues to process the packet and eventually passes the packet out the egress interface.
The big difference between a router ACL and a Cisco ASA (a stateful firewall) ACL is that only the first packet of a flow is subjected by an ACL in the security appliance (stateful firewall). After that, the connection is built, and subsequent packets matching that connection are not checked by the ACL. If a packet is denied by the ACL, the security appliance discards the packet and generates a syslog message indicating that such an event has occurred.
If an outbound ACL is applied on an interface, the firewall processes the packets by sending them through the different processes (NAT, QoS, and VPN) and then applies the configured ACEs before transmitting the packets out on the wire. The firewall transmits the packets only if they are allowed to go out by the outbound ACL on that interface. If the packets are denied by any one of the ACEs, the security appliance discards the packets and generates a syslog message indicating that such an event has occurred.
Following are some of the important characteristics of an ACL configured on a Cisco ASA or on a Cisco IOS zone-based firewall:
• When a new ACE is added to an existing ACL, it is appended to the end of the ACL.
• When a packet enters the firewall, the ACEs are evaluated in sequential order. Hence, the order of an ACE is critical. For example, if you have an ACE that allows all IP traffic to pass through, and then you create another ACE to block all IP traffic, the packets will never be evaluated against the second ACE because all packets will match the first ACE entry.
• There is an implicit deny at the end of all ACLs. If a packet is not matched against a configured ACE, it is dropped and a syslog is generated.
• Each interface is assigned a security level. The higher the security level, the more secure. In traditional Cisco ASA firewalls, the security levels go from 0 (less secure) to 100 (more secure). By default, the outside interface is assigned a security level of 0, and the inside interface is assigned a security level of 100. In the Cisco ASA, by default, you do not need to define an ACE to permit traffic from a high-security-level interface to a low-security-level interface. However, if you want to restrict traffic flows from a high-security-level interface to a low-security-level interface, you can define an ACL. If you configure an ACL to a high-security-level interface to a low-security-level interface, it disables the implicit permit from that interface. All traffic is now subject to the entries defined in that ACL.
• Also in the Cisco ASA, an ACL must explicitly permit traffic traversing the security appliance from a lower- to a higher-security-level interface of the firewall. The ACL must be applied to the lower-security-level interface.
• The ACLs (Extended or IPv6) must be applied to an interface to filter traffic that is passing through the security appliance.
• You can bind one extended and one EtherType ACL in each direction of an interface at the same time.
• You can apply the same ACL to multiple interfaces. However, this is not considered to be a good security practice because overlapping and redundant security policies can be applied.
• You can use ACLs to control traffic through the security appliance, as well as to control traffic to the security appliance. The ACLs controlling traffic to the appliance are applied differently than ACLs filtering traffic through the firewall. The ACLs are applied using access groups. The ACLs controlling traffic to the security appliance are called controlled plane ACLs.
• When TCP or UDP traffic flows through the security appliance, the return traffic is automatically allowed to pass through because the connections are considered established and bidirectional.
• Other protocols such as ICMP are considered unidirectional connections; therefore, you need to allow ACL entries in both directions. There is an exception for the ICMP traffic when you enable the ICMP inspection engine.
The Cisco ASA supports five different types of ACLs to provide a flexible and scalable solution to filter unauthorized packets into the network:
• Standard ACLs
• Extended ACLs
• IPv6 ACLs
• EtherType ACLs
• Webtype ACLs
Standard ACLs
Standard ACLs are used to identify packets based on their destination IP addresses. These ACLs can be used in scenarios such as split tunneling for the remote-access virtual private network (VPN) tunnels and route redistribution within route maps for dynamic routing deployments (OSPF, BGP, and so on). These ACLs, however, cannot be applied to an interface for filtering traffic. A standard ACL can be used only if the security appliance is running in routed mode. In routed mode, the Cisco ASA routes packets from one subnet to another subnet by acting as an extra Layer 3 hop in the network.
![]()
Extended ACLs
Extended ACLs, the most commonly deployed ACLs, can classify packets based on the following attributes:
• Source and destination IP addresses
• Layer 3 protocols
• Source and/or destination TCP and UDP ports
• Destination ICMP type for ICMP packets
An extended ACL can be used for interface packet filtering, QoS packet classification, packet identification for NAT and VPN encryption, and a number of other features. These ACLs can be set up on the Cisco ASA in the routed and the transparent mode.
EtherType ACLs
EtherType ACLs can be used to filter IP and non-IP-based traffic by checking the Ethernet type code field in the Layer 2 header. IP-based traffic uses an Ethernet type code value of 0x800, whereas Novell IPX uses 0x8137 or 0x8138, depending on the Netware version.
An EtherType ACL can be configured only if the security appliance is running in transparent mode. Just like any other ACL, the EtherType ACL has an implicit deny at the end of it. However, this implicit deny does not affect the IP traffic passing through the security appliance. As a result, you can apply both EtherType and extended ACLs to each direction of an interface. If you configure an explicit deny at the end of an EtherType ACL, it blocks IP traffic even if an extended ACL is defined to pass those packets.
Webtype ACLs
A Webtype ACL allows security appliance administrators to restrict traffic coming through the SSL VPN tunnels. In cases where a Webtype ACL is defined but there is no match for a packet, the default behavior is to drop the packet because of the implicit deny. On the other hand, if no ACL is defined, the security appliance allows traffic to pass through it.
An ACL Example
Example 1-5 shows the command-line interface (CLI) configuration of an extended ACL. The ACL is called outside_access_in, and it is composed of four ACEs. The first two ACEs allow HTTPS traffic destined for 10.10.20.111 from devices in the outside interface, whereas the last two ACEs allow SMTP access to 10.10.20.112. Adding remarks to an ACL is recommended because it helps others recognize its function. In Example 1-5 the system administrator has added the ACL remark: “ACL to block inbound traffic except HTTPS and SMTP.”
Example 1-5 Configuration Example of an Extended ACL
ASA# configure terminal ASA(config)# access-list outside_access_in remark ACL to block inbound traffic except HTTPS and SMTP ASA(config)# access-list outside_access_in extended permit tcp any host 10.10.20.111 eq https ASA(config)# access-list outside_access_in extended permit tcp any host 10.10.20.111 eq https ASA(config)# access-list outside_access_in extended permit tcp any host 10.10.20.112 eq smtp ASA(config)# access-list outside_access_in extended permit tcp any host 10.10.20.112 eq smtp
Always remember that there is an implicit deny at the end of any ACL.
The Understanding Cisco Cybersecurity Operations Fundamentals (200-201 CBROPS) exam does not require you to know details about how to configure access control lists in different Cisco devices. However, it is good for you to become familiar with the high-level concepts of traditional ACLs and the benefits of modern access control policies that are present in next-generation firewalls. For instance, traditional packet filters do not commonly inspect additional Layer 3 and Layer 4 fields such as sequence numbers, TCP control flags, and TCP acknowledgment (ACK) fields. The firewalls that inspect such fields and flags are referred to as stateful firewalls. You learn how stateful firewalls operate later in this chapter in the “Stateful Inspection Firewalls” section. In addition, next-generation firewalls allow you to create more granular policies that are related to applications, users, and other context to better defend your organization.
Various packet-filtering firewalls can also inspect packet header information to find out whether the packet is from a new or an existing connection. Simple packet-filtering firewalls have several limitations and weaknesses:
• Their ACLs or rules can be relatively large and difficult to manage.
• They can be deceived into permitting unauthorized access of spoofed packets. Attackers can orchestrate a packet with an IP address that is authorized by the ACL.
• Numerous applications can build multiple connections on arbitrarily negotiated ports. This makes it difficult to determine which ports are selected and used until after the connection is completed. Examples of these types of applications are multimedia applications such as streaming audio and video applications. Packet filters do not understand the underlying upper-layer protocols used by these types of applications, and providing support for these types applications is difficult because the ACLs need to be manually configured in packet-filtering firewalls.
Application Proxies
![]()
Application proxies, or proxy servers, are devices that operate as intermediary agents on behalf of clients that are on a private or protected network. Clients on the protected network send connection requests to the application proxy to transfer data to the unprotected network or the Internet. Consequently, the application proxy (sometimes referred to as a web proxy) sends the request on behalf of the internal client. The majority of proxy firewalls work at the application layer of the OSI model. Most proxy firewalls can cache information to accelerate their transactions. This is a great tool for networks that have numerous servers that experience high usage. Additionally, proxy firewalls can protect against some web-server-specific attacks; however, in most cases, they do not provide any protection against the web application itself.
![]()
Network Address Translation
Several Layer 3 devices can supply Network Address Translation (NAT) services. The Layer 3 device translates the internal host’s private (or real) IP addresses to a publicly routable (or mapped) address.
Cisco uses the terminology of “real” and “mapped” IP addresses when describing NAT. The real IP address is the address that is configured on the host, before it is translated. The mapped IP address is the address to which the real address is translated.
Tip
Static NAT allows connections to be initiated bidirectionally, meaning both to the host and from the host.
Figure 1-8 demonstrates how a host on the inside of a firewall with the private address of 10.10.10.123 is translated to the public address 209.165.200.227.

Figure 1-8 NAT Example
NAT is often used by firewalls; however, other devices such as routers and wireless access points provide support for NAT. By using NAT, the firewall hides the internal private addresses from the unprotected network and exposes only its own address or public range. This enables a network professional to use any IP address space as the internal network. A best practice is to use the address spaces that are reserved for private use (see RFC 1918, “Address Allocation for Private Internets”). Table 1-2 lists the private address ranges specified in RFC 1918.
Table 1-2 RFC 1918 Private Address Ranges

It is important to think about the different private address spaces when you plan your network (for example, the number of hosts and subnets that can be configured). Careful planning and preparation lead to substantial time savings if changes are encountered down the road.
Tip
The white paper titled “A Security-Oriented Approach to IP Addressing” provides numerous tips on planning and preparing your network IP address scheme. You can find this whitepaper here: www.cisco.com/web/about/security/intelligence/security-for-ip-addr.html.
![]()
Port Address Translation
Typically, firewalls perform a technique called Port Address Translation (PAT). This feature, which is a subset of the NAT feature, allows many devices on the internal protected network to share one IP address by inspecting the Layer 4 information on the packet. This shared address is usually the firewall’s public address; however, it can be configured to any other available public IP address. Figure 1-9 shows how PAT works.

Figure 1-9 PAT Example
As illustrated in Figure 1-9, several hosts on a trusted network labeled “inside” are configured with an address from the network 10.10.10.0 with a 24-bit subnet mask. The Cisco ASA performs PAT for the internal hosts and translates the 10.10.10.x addresses into its own address (209.165.200.228). In this example, Host A sends a TCP port 80 packet to the web server located in the “outside” unprotected network. The Cisco ASA translates the request from the original 10.10.10.8 IP address of Host A to its own address. It does this by randomly selecting a different Layer 4 source port when forwarding the request to the web server. The TCP source port is modified from 1024 to 1188 in this example.
Static Translation
![]()
A different methodology is used when hosts in the unprotected network need to initiate a new connection to specific hosts behind the NAT device. You configure the firewall to allow such connections by creating a static one-to-one mapping of the public (mapped) IP address to the address of the internal (real) protected device. For example, static NAT can be configured when a web server resides on the internal network and has a private IP address but needs to be contacted by hosts located in the unprotected network or the Internet. Figure 1-8 demonstrated how static translation works. The host address (10.10.10.123) is statically translated to an address in the outside network (209.165.200.227, in this case). This allows the outside host to initiate a connection to the web server by directing the traffic to 209.165.200.227. The device performing NAT then translates and sends the request to the web server on the inside network.
Firewalls like the Cisco ASA, Firepower Threat Defense (FTD), Cisco IOS zone-based firewalls, and others can perform all these NAT operations. Address translation is not limited to firewalls, however. Nowadays, all sorts of lower-end network devices such as simple small office or home office (SOHO) and wireless routers can perform different NAT techniques.
Stateful Inspection Firewalls
Stateful inspection firewalls provide enhanced benefits when compared to simple packet-filtering firewalls. They track every packet passing through their interfaces by ensuring that they are valid, established connections. They examine not only the packet header contents but also the application layer information within the payload. Subsequently, different rules can be created on the firewall to permit or deny traffic based on specific payload patterns. A stateful firewall monitors the state of the connection and maintains a database with this information, usually called the state table. The state of the connection details whether such a connection has been established, closed, reset, or is being negotiated. These mechanisms offer protection for different types of network attacks.
![]()
Demilitarized Zones
Firewalls can be configured to separate multiple network segments (or zones), usually called demilitarized zones (DMZs). These zones provide security to the systems that reside within them with different security levels and policies between them. DMZs can have several purposes; for example, they can serve as segments on which a web server farm resides or as extranet connections to a business partner. Figure 1-10 shows a firewall with a DMZ.

Figure 1-10 DMZ Example
DMZs minimize the exposure of devices and clients on your internal network by allowing only recognized and managed services on those hosts to be accessible from the Internet. In Figure 1-10, the DMZ hosts web servers that are accessible by internal and Internet hosts. In large organizations, you can find multiple firewalls in different segments and DMZs.
Firewalls Provide Network Segmentation
Firewalls can provide network segmentation while enforcing policies between those segments. In Figure 1-11, a firewall segments and enforces policies between three networks in the overall corporate network. The first network is the finance department, the second is the engineering department, and the third is the sales department.

Figure 1-11 Firewall Providing Network Segmentation
![]()
Application-Based Segmentation and Micro-segmentation
Another dilemma is the machine-to-machine communication between different systems and applications. How do you also segment and protect that in an effective manner?
In today’s virtualized and containerized environments, traffic between applications may never leave a physical device or server, as illustrated in Figure 1-12.

Figure 1-12 Virtual Machine Traffic Never Leaving the Physical Server
This is why micro-segmentation is currently so popular. A solution of the past was to include virtual firewalls between virtual machines (VMs), as shown in Figure 1-13.

Figure 1-13 Virtual Firewalls for Segmentation
Machine-to-machine (or application-to-application) communication also needs to be segmented within an organization. For instance, do your Active Directory (AD) servers need to communicate with Network Time Protocol (NTP) servers? What is their relationship and data interaction?
Micro-segmentation features provided by modern solutions like Cisco Application Centric Infrastructure (ACI) offer a new level of segmentation capabilities. Cisco ACI allows organizations to automatically assign endpoints to logical security zones called endpoint groups (EPGs). EPGs are used to group VMs within a tenant and apply filtering and forwarding policies to them. These EPGs are based on various network-based or VM-based attributes.
A micro-segment in ACI is also often referred to as μSeg EPGs. You can group endpoints in existing application EPGs into new micro-segment (μSeg) EPGs and configure network or VM-based attributes for those μSeg EPGs. With these μSeg EPGs, you can apply dynamic policies. You can also apply policies to any endpoints within the tenant. For instance, let’s say that you want to assign web servers to an EPG and then apply similar policies. By default, all endpoints within an EPG can communicate with each other. You also can restrict access if this web EPG contains a mix of production and development web servers. To accomplish this, you can create a new EPG and automatically assign endpoints based on their VM name attribute, such as prod-xxxx or dev-xxx.
Micro-segmentation in Cisco ACI can be accomplished by integrating with vCenter or Microsoft System Center Virtual Machine Manager (SCVMM), Cisco ACI API (controller), and leaf switches.
Applying attributes to μSeg EPGs enables you to apply forwarding and security policies with greater granularity than you can to EPGs without attributes. Attributes are unique within the tenant.
High Availability
Firewalls such as the Cisco ASA provide high availability features such as the following:
• Active-standby failover
• Active-active failover
• Clustering
Active-Standby Failover
In an active-standby failover configuration, the primary firewall (when operational) is always active, and the secondary is in standby mode. When the primary firewall fails, the secondary firewall takes over. Figure 1-14 shows a pair of firewalls in an active-standby failover configuration.
The configuration and stateful network information is synchronized from the primary firewall to the secondary.

Figure 1-14 Firewalls in Active-Standby Failover Mode
Active-Active Failover
In an active-active failover configuration, both of the firewalls are active. If one fails, the other will continue to pass traffic in the network. Figure 1-15 shows a pair of firewalls in an active-active failover configuration.

Figure 1-15 Firewalls in Active-Active Failover Mode
Clustering Firewalls
Firewalls such as the Cisco ASA and Firepower Threat Defense can also be clustered to provide next-generation firewall protection in large and highly scalable environments. Figure 1-16 shows a cluster of three Cisco ASAs. One of the main reasons to cluster firewalls is to increase packet throughput and to scale in a more efficient way.

Figure 1-16 Cisco ASAs in a Cluster
In Figure 1-16, the Cisco ASAs have 10 Gigabit Ethernet interfaces in an EtherChannel configuration to switches in both inside and outside networks. An EtherChannel involves bundling together two or more interfaces to scale and achieve bigger bandwidth.
Firewalls in the Data Center
Firewalls can also be deployed in the data center. The placement of firewalls in the data center will depend on many factors, such as how much latency the firewalls will introduce, what type of traffic you want to block and allow, and in what direction the traffic will flow (either north to south or east to west).
In the data center, traffic going from one network segment or application of the data center to another network segment or application within the data center is often referred to as east-to-west (or west-to-east) traffic. This is also known as lateral traffic. Figure 1-17 demonstrates east-west traffic.

Figure 1-17 Data Center East-West Traffic
Similarly, traffic going to and from the data center and the rest of the corporate network is often referred to as north-to-south (or south-to-north) traffic. Figure 1-18 demonstrates north-south traffic.

Figure 1-18 Data Center North-South Traffic
Another example of advanced segmentation and micro-segmentation in the data center is the security capabilities of the Cisco ACI, which is a software-defined networking (SDN) solution that has a robust policy model across data center networks, servers, storage, security, and services. This policy-based automation helps network administrators achieve micro-segmentation through the integration of physical and virtual environments under one policy model for networks, servers, storage, services, and security. Even if servers and applications are “network adjacent” (that is, on the same network segment), they will not communicate with each other until a policy is configured and provisioned. This is why Cisco ACI is very attractive to many security-minded network administrators. Another major benefit of Cisco ACI is automation. With such automation, you can reduce application deployment times from weeks to minutes. Cisco ACI policies are enforced and deployed by the Cisco Application Policy Infrastructure Controller (APIC).
Virtual Firewalls
Firewalls can also be deployed as VMs. An example of a virtual firewall is the Cisco FTDv. These virtual firewalls are often deployed in the data center to provide segmentation and network protection to virtual environments. They are typically used because traffic between VMs often does not leave the physical server and cannot be inspected or enforced with physical firewalls.
Tip
The Cisco ASA also has a featured called virtual contexts. This is not the same as the virtual firewalls described previously. In the Cisco ASA security context feature, one physical appliance can be “virtualized” into separate contexts (or virtual firewalls). Virtual firewalls such as the Cisco ASAv run on top of VMware or KVM on a physical server such as the Cisco UCS.
Figure 1-19 shows two virtual firewalls providing network segmentation between several VMs deployed in a physical server.

Figure 1-19 Virtual Firewalls Example
Deep Packet Inspection
Several applications require special handling of data packets when they pass through firewalls. They include applications and protocols that embed IP addressing information in the data payload of the packet or open secondary channels on dynamically assigned ports. Sophisticated firewalls and security appliances such as the Cisco ASA, Cisco FTD, and Cisco IOS zone-based firewall offer application inspection mechanisms to handle the embedded addressing information to allow the previously mentioned applications and protocols to work. Using application inspection, these security appliances can identify the dynamic port assignments and allow data exchange on these ports during a specific connection.
With deep packet inspection (DPI), firewalls can look at specific Layer 7 payloads to protect against security threats. You can also configure these devices to deny specific FTP commands, HTTP content types, and other application protocols.
Next-Generation Firewalls
The proliferation of mobile devices and the need to connect from any place are radically changing the enterprise security landscape. Social networking sites such as Facebook and Twitter long ago moved beyond mere novelty sites for teens and geeks and have become vital channels for communicating with groups and promoting brands.
Security concerns and fear of data loss are leading reasons why some businesses don’t embrace social media, but many others are adopting social media as a vital resource within the organization. Some of the risks associated with social media can be mitigated through the application of technology and user controls. However, there’s no doubt that criminals have used social media networks to lure victims into downloading malware and handing over login passwords.
Before today’s firewalls grant network access, they need to be aware of not only the applications and users accessing the infrastructure but also the device in use, the location of the user, and the time of day. Such context-aware security requires a rethinking of the firewall architecture. Context-aware firewalls extend beyond the next-generation firewalls on the market today. They provide granular control of applications, comprehensive user identification, and location-based control. The Cisco Firepower Threat Defense is an example of a next-generation firewall.
The Cisco Firepower firewalls provide a comprehensive set of features and next-generation security capabilities. For example, they provide capabilities such as simple packet filtering (normally configured with access control lists) and stateful inspection. The Cisco FTD software also provides support for application inspection/awareness. It can listen in on conversations between devices on one side and devices on the other side of the firewall. The benefit of listening in is so that the firewall can pay attention to application layer information.
The Cisco FTD also supports Network Address Translation, the capability to act as a Dynamic Host Configuration Protocol (DHCP) server or client, or both. The Cisco FTD also can be implemented as a traditional Layer 3 firewall, which has IP addresses assigned to each of its routable interfaces. The other option is to implement a firewall as a transparent (Layer 2) firewall, in which the actual physical interfaces receive individual IP addresses, but a pair of interfaces operate like a bridge. The Cisco ASA and Cisco FTD firewalls are often used as a head-end or remote-end device for VPN tunnels for both remote-access VPN users and site-to-site VPN tunnels. They support IPsec and SSL-based remote-access VPNs. The SSL VPN capabilities include support for clientless SSL VPN and the full AnyConnect SSL VPN tunnels.
Tip
The Cisco Firepower Threat Defense (FTD) is unified software that includes Cisco ASA features, legacy FirePOWER Services, and new features. Cisco spells the word FirePOWER (uppercase POWER) when referring to the Cisco ASA FirePOWER Services module. The word Firepower (lowercase power) is used when referring to all other software, such as FTD, Firepower Management Center (FMC), and Firepower appliances. Cisco is always adding new models to its firewall portfolio. To get the latest information about the Cisco firewall solutions, go to www.cisco.com/c/en/us/products/security/firewalls/index.html.
Intrusion Detection Systems and Intrusion Prevention Systems
Intrusion detection systems (IDSs) are devices that detect (in promiscuous mode) attempts from an attacker to gain unauthorized access to a network or a host, to create performance degradation, or to steal information. They also detect DDoS attacks, worms, and virus outbreaks. Figure 1-20 shows how an IDS device is configured to promiscuously detect security threats.

Figure 1-20 IDS Example
In this figure, a compromised host sends a malicious packet to a series of hosts in the 10.10.20.0/24 network. The IDS device analyzes the packet and sends an alert to a monitoring system. The malicious packet still successfully arrives at the 10.10.20.0/24 network.
Intrusion prevention system (IPS) devices, on the other hand, are capable of not only detecting all these security threats but also dropping malicious packets inline. IPS devices may be initially configured in promiscuous mode (monitoring mode) when you are first deploying them in the network. This is done to analyze the impact to the network infrastructure. Then they are deployed in inline mode to be able to block any malicious traffic in your network.
Figure 1-21 shows how an IPS device is placed inline and drops the noncompliant packet while sending an alert to the monitoring system.

Figure 1-21 IPS Example
A few different types of IPSs exist:
• Traditional network-based IPSs (NIPSs)
• Next-generation IPS systems (NGIPSs)
• Host-based IPSs (HIPSs)
Examples of legacy NIPSs are the Cisco IPS 4200 sensors and the Catalyst 6500 IPS module. These devices have been in the end-of-life (EoL) stage for quite some time. Examples of NGIPSs are the Cisco Firepower IPS systems.
The legacy Cisco ASA 5500 Series FirePOWER Services provide intrusion prevention, firewall, and VPN services in a single, easy-to-deploy platform. Intrusion prevention services enhance firewall protection by looking deeper into the flows to provide protection against threats and vulnerabilities. The Cisco Firepower Threat Defense provides these capabilities in a combined software package.
Network-based IDSs and IPSs use several detection methodologies, such as the following:
• Pattern matching and stateful pattern-matching recognition
• Protocol analysis
• Heuristic-based analysis
• Anomaly-based analysis
• Global threat correlation capabilities
Pattern Matching and Stateful Pattern-Matching Recognition
Pattern matching is a methodology in which the intrusion detection device searches for a fixed sequence of bytes within the packets traversing the network. Generally, the pattern is aligned with a packet that is related to a specific service or, in particular, associated with a source and destination port. This approach reduces the amount of inspection made on every packet. However, it is limited to services and protocols that are associated with well-defined ports. Protocols that do not use any Layer 4 port information are not categorized. Examples of these protocols are Encapsulated Security Payload (ESP), Authentication Header (AH), and Generic Routing Encapsulation (GRE).
This tactic uses the concept of signatures. A signature is a set of conditions that point out some type of intrusion occurrence. For example, if a specific TCP packet has a destination port of 1234 and its payload contains the string ff11ff22, a signature can be configured to detect that string and generate an alert.
Alternatively, the signature could include an explicit starting point and endpoint for inspection within the specific packet.
Here are some of the benefits of the plain pattern-matching technique:
• Direct correlation of an exploit
• Trigger alerts on the pattern specified
• Traffic inspections across different services and protocols
One of the main disadvantages is that pattern matching can lead to a considerably high rate of false positives, which are alerts that do not represent a genuine malicious activity. In contrast, any alterations to the attack can lead to overlooked events of real attacks, which are normally referred as false negatives.
To address some of these limitations, a more refined method was created. This methodology is called stateful pattern-matching recognition. This process dictates that systems performing this type of signature analysis must consider the chronological order of packets in a TCP stream. In particular, they should judge and maintain a stateful inspection of such packets and flows.
Here are some of the advantages of stateful pattern-matching recognition:
• The capability to directly correlate a specific exploit within a given pattern
• Support for all nonencrypted IP protocols
Systems that perform stateful pattern matching keep track of the arrival order of nonencrypted packets and handle matching patterns across packet boundaries.
However, stateful pattern-matching recognition shares some of the same restrictions as the simple pattern-matching methodology, which was discussed previously, including an uncertain rate of false positives and the possibility of some false negatives. Additionally, stateful pattern matching consumes more resources in the IPS device because it requires more memory and CPU processing.
Protocol Analysis
Protocol analysis (or protocol decode-base signatures) is often referred to as an extension to stateful pattern recognition. A network-based intrusion detection system (NIDS) accomplishes protocol analysis by decoding all protocol or client/server conversations. The NIDS identifies the elements of the protocol and analyzes them while looking for an infringement. Some intrusion detection systems look at explicit protocol fields within the inspected packets. Others require more sophisticated techniques, such as examination of the length of a field within the protocol or the number of arguments. For example, in SMTP, the device may examine specific commands and fields such as HELO, MAIL, RCPT, DATA, RSET, NOOP, and QUIT. This technique diminishes the possibility of encountering false positives if the protocol being analyzed is properly defined and enforced. However, the system can generate numerous false positives if the protocol definition is ambiguous or tolerates flexibility in its implementation.
Heuristic-Based Analysis
A different approach to network intrusion detection is to perform heuristic-based analysis. Heuristic scanning uses algorithmic logic from statistical analysis of the traffic passing through the network. Its tasks are CPU and resource intensive, so it is an important consideration while planning your deployment. Heuristic-based algorithms may require fine-tuning to adapt to network traffic and minimize the possibility of false positives. For example, a system signature can generate an alarm if a range of ports is scanned on a particular host or network. The signature can also be orchestrated to restrict itself from specific types of packets (for example, TCP SYN packets). Heuristic-based signatures call for more tuning and modification to better respond to their distinctive network environment.
Anomaly-Based Analysis
A different practice keeps track of network traffic that diverges from “normal” behavioral patterns. This practice is called anomaly-based analysis. The limitation is that what is considered to be normal must be defined. Systems and applications whose behavior can be easily considered as normal could be classified as heuristic-based systems.
However, sometimes it is challenging to classify a specific behavior as normal or abnormal based on different factors, which include the following:
• Negotiated protocols and ports
• Specific application changes
• Changes in the architecture of the network
A variation of this type of analysis is profile-based detection. This analysis allows systems to orchestrate their alarms on alterations in the way that other systems or end users interrelate on the network.
Another kind of anomaly-based detection is protocol-based detection. This scheme is related to, but not to be confused with, the protocol-decode method. The protocol-based detection technique depends on well-defined protocols, as opposed to the protocol-decode method, which classifies as an anomaly any unpredicted value or configuration within a field in the respective protocol. For example, a buffer overflow can be detected when specific strings are identified within the payload of the inspected IP packets.
Tip
A buffer overflow occurs when a program attempts to stock more data in a temporary storage area within memory (buffer) than it was designed to hold. This might cause the data to incorrectly overflow into an adjacent area of memory. An attacker could thus craft specific data inserted into the adjacent buffer. Subsequently, when the corrupted data is read, the target computer executes new instructions and malicious commands.
Traditional IDS and IPS provide excellent application layer attack-detection capabilities. However, they do have a weakness. For example, they cannot detect DDoS attacks where the attacker uses valid packets. IDS and IPS devices are optimized for signature-based application layer attack detection. Another weakness is that these systems utilize specific signatures to identify malicious patterns. Yet, if a new threat appears on the network before a signature is created to identify the traffic, it could lead to false negatives. An attack for which there is no signature is called a zero-day attack.
Although some IPS devices do offer anomaly-based capabilities, which are required to detect such attacks, they need extensive manual tuning and have a major risk of generating false positives.
You can use more elaborate anomaly-based detection systems to mitigate DDoS attacks and zero-day outbreaks. Typically, an anomaly detection system monitors network traffic and alerts or reacts to any sudden increase in traffic and any other anomalies. You can also use NetFlow as an anomaly detection tool. NetFlow is a Cisco proprietary protocol that provides detailed reporting and monitoring of IP traffic flows through a network device, such as a router, switch, or the Cisco ASA.
Global Threat Correlation Capabilities
![]()
Cisco NGIPS devices include global correlation capabilities that utilize real-world data from Cisco Talos. Cisco Talos is a team of security researchers who leverage big-data analytics for cybersecurity and provide threat intelligence for many Cisco security products and services. Global correlation allows an IPS sensor to filter network traffic using the “reputation” of a packet’s source IP address. The reputation of an IP address is computed by Cisco threat intelligence using the past actions of that IP address. IP reputation has been an effective means of predicting the trustworthiness of current and future behaviors from an IP address.
Next-Generation Intrusion Prevention Systems
As a result of the Sourcefire acquisition, Cisco expanded its NGIPS portfolio with high-performance IPS appliances and virtual appliances that can be deployed in virtualized environments. By deploying these virtual appliances, security administrators can maintain network visibility that is often lost in virtual environments.
Firepower Management Center
Cisco Firepower Management Center (FMC) provides a centralized management and analysis platform for the Cisco NGIPS appliances, the legacy Cisco ASA with FirePOWER Services, and Cisco FTD. It provides support for role-based policy management and includes a fully customizable dashboard with advanced reports and analytics.
Advanced Malware Protection
![]()
Cisco provides advanced malware protection capabilities for endpoint and network security devices. In the following sections, you learn the details about AMP for Endpoints and the integration of AMP in several Cisco security products.
AMP for Endpoints
Numerous antivirus and antimalware solutions on the market are designed to detect, analyze, and protect against both known and emerging endpoint threats. Before diving into these technologies, you should understand viruses and malicious software (malware).
The following are the most common types of malicious software:
• Computer virus: This malicious software infects a host file or system area to produce an undesirable outcome such as erasing data, stealing information, or corrupting the integrity of the system. In numerous cases, these viruses multiply again to form new generations of themselves.
• Worm: This virus replicates itself over the network, infecting numerous vulnerable systems. In most cases, a worm executes malicious instructions on a remote system without user interaction.
• Mailer or mass-mailer worm: A type of worm that sends itself in an email message. Examples of mass-mailer worms are Loveletter.A@mm and W32/SKA.A@m (a.k.a. the Happy99 worm), which sends a copy of itself every time the user sends a new message.
• Logic bomb: This type of malicious code is injected into a legitimate application. An attacker can program a logic bomb to delete itself from the disk after it performs the malicious tasks on the system. Examples of these malicious tasks include deleting or corrupting files or databases and executing a specific instruction after certain system conditions are met.
• Trojan horse: This type of malware executes instructions to delete files, steal data, or otherwise compromise the integrity of the underlying operating system. Trojan horses typically use a form of social engineering to fool victims into installing such software on their computers or mobile devices. Trojans can also act as backdoors.
• Backdoor: This piece of malware or a configuration change allows an attacker to control the victim’s system remotely. For example, a backdoor can open a network port on the affected system so that the attacker can connect to and control the system.
• Exploit: This malicious program is designed to exploit, or take advantage of, a single vulnerability or set of vulnerabilities.
• Downloader: This piece of malware downloads and installs other malicious content from the Internet to perform additional exploitation on an affected system.
• Spammer: This malware sends spam, or unsolicited messages sent via email, instant messaging, newsgroups, or any other kind of computer or mobile device communications. Spammers send these unsolicited messages with the primary goal of fooling users into clicking malicious links, replying to emails or other messages with sensitive information, or performing different types of scams. The attacker’s main objective is to make money.
• Key logger: This piece of malware captures the user’s keystrokes on a compromised computer or mobile device. A key logger collects sensitive information such as passwords, personal identification numbers (PINs), personally identifiable information (PII), credit card numbers, and more.
• Rootkit: This set of tools is used by an attacker to elevate privilege to obtain root-level access to be able to completely take control of the affected system.
• Ransomware: This type of malware compromises a system and then demands that the victim pay a ransom to the attacker for the malicious activity to cease or for the malware to be removed from the affected system. Examples of ransomware are Nyeta, NotPetya, WannaCry, Sodinokibi, BadRabbit, and CryptoWall; they all encrypt the victim’s data and demand that the user pay a ransom for the data to be decrypted and accessible again.
The following are just a few examples of the commercial and free antivirus software options available today:
• Avast
• AVG Internet Security Bitdefender Antivirus Free
• Kaspersky Anti-Virus
• McAfee AntiVirus
• Sophos Antivirus
• Norton AntiVirus
• ClamAV
• Immunet AntiVirus
There are numerous other antivirus software companies and products.
Tip
ClamAV is an open-source antivirus engine sponsored and maintained by Cisco and non-Cisco engineers. You can download ClamAV from www.clamav.net. Immunet is a free community-based antivirus software maintained by Cisco Sourcefire. You can download Immunet from www.immunet.com.
Personal firewalls and host-based intrusion prevention systems (HIPSs) are software applications that you can install on end-user machines or servers to protect them from external security threats and intrusions. The term personal firewall typically applies to basic software that can control Layer 3 and Layer 4 access to client machines. HIPS provides several features that offer more robust security than a traditional personal firewall, such as host intrusion prevention and protection against spyware, viruses, worms, Trojans, and other types of malware.
Today, more sophisticated software makes basic personal firewalls and HIPS obsolete. For example, Cisco Advanced Malware Protection (AMP) for Endpoints provides granular visibility and control to stop advanced threats missed by other security layers. Cisco AMP for Endpoints takes advantage of telemetry from big data, continuous analysis, and advanced analytics provided by Cisco threat intelligence to be able to detect, analyze, and stop advanced malware across endpoints.
Cisco AMP for Endpoints provides advanced malware protection for many operating systems, including Windows, Mac OS X, Android, and Linux.
Attacks are getting very sophisticated and can evade detection of traditional systems and endpoint protection. Today, attackers have the resources, knowledge, and persistence to beat point-in-time detection. Cisco AMP for Endpoints provides mitigation capabilities that go beyond point-in-time detection. It uses threat intelligence from Cisco to perform retrospective analysis and protection. Cisco AMP for Endpoints also provides device and file trajectory capabilities to allow a security administrator to analyze the full spectrum of an attack. Device trajectory and file trajectory support the following file types in the Windows and macOS operating systems:
• MSEXE
• MSCAB
• MSOLE2
• ZIP
• ELF
• MACHO
• MACHO_UNIBIN
• SWF
• JAVA
AMP for Networks
Cisco AMP for Networks provides next-generation security services that go beyond point-in-time detection. It provides continuous analysis and tracking of files and also retrospective security alerts so that a security administrator can take action during and after an attack. The file trajectory feature of Cisco AMP for Networks tracks file transmissions across the network, and the file capture feature enables a security administrator to store and retrieve files for further analysis.
The network provides unprecedented visibility into activity at a macro-analytical level. However, to remediate malware, in most cases you need to be on the host. This is why AMP has the following connectors: AMP for Networks, AMP for Endpoints, and AMP for Content Security Appliances.
You can install AMP for Networks on any Cisco Firepower security appliance right alongside the firewall and IPS; however, there are dedicated AMP appliances as well. When it comes down to it, though, AMP appliances and Firepower appliances are actually the same. They can all run the same services. Are you thoroughly confused? Stated a different way, Cisco AMP for Networks is the AMP service that runs on the appliance examining traffic flowing through a network. It can be installed in a standalone form or as a service on a Firepower IPS or even a Cisco ASA with FirePOWER Services.
AMP for Networks and all the AMP connectors are designed to find malicious files, provide retrospective analysis, illustrate trajectory, and point out how far malicious files may have spread.
The AMP for Networks connector examines, records, tracks, and sends files to the cloud. It creates an SHA-256 hash of the file and compares it to the local file cache. If the hash is not in the local cache, it queries the Firepower Management Center. The FMC has its own cache of all the hashes it has seen before, and if it hasn’t previously seen this hash, the FMC queries the cloud. Unlike with AMP for Endpoints, when a file is new, it can be analyzed locally and doesn’t have to be sent to the cloud for all analysis. Also, the file is examined and stopped in flight, as it is traversing the appliance.
Figure 1-22 illustrates the many AMP for Networks connectors sending the file hash to the FMC, which in turn sends it to the cloud if the hash is new. The connectors could be running on dedicated AMP appliances, as a service on a Cisco next-generation IPS, on an ASA with FirePOWER Services, or on the next-generation firewall known as Firepower Threat Defense .

Figure 1-22 AMP Connectors Communicating to the FMC and the Cloud
It’s very important to note that only the SHA-256 hash is sent unless you configure the policy to send files for further analysis in the Cisco AMP Threat Grid.
AMP can also provide retrospective analysis. The AMP for Networks appliance keeps data from what occurred in the past. When a file’s disposition is changed, AMP provides an historical analysis of what happened, tracing the incident/infection. With the help of AMP for Endpoints, retrospection can reach out to that host and remediate the bad file, even though that file was permitted in the past.
Web Security Appliance
![]()
For an organization to be able to protect its environment against web-based security threats, security administrators need to deploy tools and mitigation technologies that go far beyond traditional blocking of known bad websites. Today, you can download malware through compromised legitimate websites, including social media sites, advertisements in news and corporate sites, and gaming sites. Cisco has developed several tools and mechanisms to help customers combat these threats, including and Cisco Web Security Appliance (WSA), Cisco Security Management Appliance (SMA), and Cisco Cloud Web Security (CWS). These solutions enable malware detection and blocking, continuous monitoring, and retrospective alerting.
A Cisco WSA uses cloud-based intelligence from Cisco to help protect an organization before, during, and after an attack. This “life cycle” is referred to as the attack continuum. The cloud-based intelligence includes web (URL) reputation and zero-day threat intelligence from the Talos Cisco security intelligence and research group. This threat intelligence helps security professionals stop threats before they enter the corporate network and also enables file reputation and file sandboxing to identify threats during an attack. Retrospective attack analysis allows security administrators to investigate and provide protection after an attack, when advanced malware might have evaded other layers of defense.
A Cisco WSA can be deployed in explicit proxy mode or as a transparent proxy, using the Web Cache Communication Protocol (WCCP). In explicit proxies, clients are aware of the requests that go through a proxy. Alternately, in transparent proxies, clients are not aware of a proxy in the network; the source IP address in a request is that of the client. In transparent proxies, configuration is needed on the client. WCCP was originally developed by Cisco, but several other vendors have integrated this protocol into their products to allow clustering and transparent proxy deployments on networks using Cisco infrastructure devices (routers, switches, firewalls, and so on).
Figure 1-23 illustrates a Cisco WSA deployed as an explicit proxy.
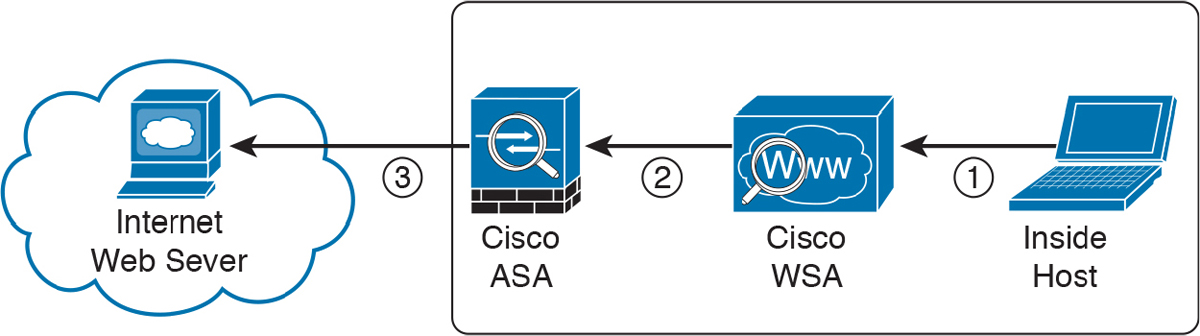
Figure 1-23 WSA Explicit Proxy Configuration
The following steps are illustrated in Figure 1-23:
1. An internal user makes an HTTP request to an external website. The client browser is configured to send the request to the Cisco WSA.
2. The Cisco WSA connects to the website on behalf of the internal user.
3. The firewall (Cisco ASA) is configured to allow only outbound web traffic from the Cisco WSA, and it forwards the traffic to the web server.
Figure 1-24 shows a Cisco WSA deployed as a transparent proxy.
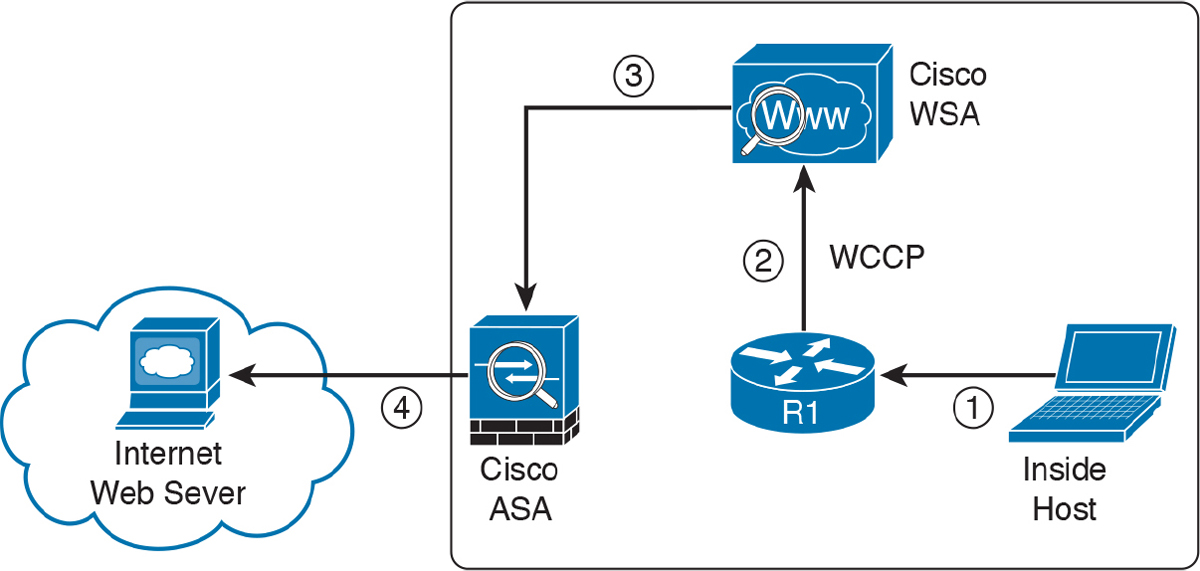
Figure 1-24 WSA Transparent Proxy Configuration
The following steps are illustrated in Figure 1-24:
1. An internal user makes an HTTP request to an external website.
2. The internal router (R1) redirects the web request to the Cisco WSA, using WCCP.
3. The Cisco WSA connects to the website on behalf of the internal user.
4. The firewall (Cisco ASA) is configured to allow only outbound web traffic from the WSA. The web traffic is sent to the Internet web server.
Figure 1-25 demonstrates how the WCCP registration works. The Cisco WSA is the WCCP client, and the Cisco router is the WCCP server.

Figure 1-25 WCCP Registration
During the WCCP registration process, the WCCP client sends a registration announcement (“Here I am”) every 10 seconds. The WCCP server (the Cisco router, in this example) accepts the registration request and acknowledges it with an “I see you” WCCP message. The WCCP server waits 30 seconds before it declares the client as “inactive” (engine failed). WCCP can be used in large-scale environments. Figure 1-26 shows a cluster of Cisco WSAs, where internal Layer 3 switches redirect web traffic to the cluster.

Figure 1-26 Cisco WSA Cluster
The Cisco WSA runs the Cisco AsyncOS operating system. Cisco AsyncOS supports numerous features, including the following, that help mitigate web-based threats:
• Real-time antimalware adaptive scanning: The Cisco WSA can be configured to dynamically select an antimalware scanning engine based on URL reputation, content type, and scanner effectiveness. Adaptive scanning is a feature designed to increase the “catch rate” of malware embedded in images, JavaScript, text, and Adobe Flash files. Adaptive scanning is an additional layer of security on top of Cisco WSA web reputation filters that include support for Sophos, Webroot, and McAfee.
• Layer 4 traffic monitor: The Cisco WSA is used to detect and block spyware. It dynamically adds IP addresses of known malware domains to databases of sites to block.
• Third-party DLP integration: The Cisco WSA redirects all outbound traffic to a third-party DLP appliance, allowing deep content inspection for regulatory compliance and data exfiltration protection. It enables an administrator to inspect web content by title, metadata, and size, and to even prevent users from storing files to cloud services such as Dropbox and Google Drive.
• File reputation: Using threat information from Cisco Talos, this file reputation threat intelligence is updated every 3 to 5 minutes.
• File sandboxing: If malware is detected, the Cisco AMP capabilities can put files in a sandbox to inspect the malware’s behavior and combine the inspection with machine-learning analysis to determine the threat level. Cisco Cognitive Threat Analytics (CTA) uses machine-learning algorithms to adapt over time.
• File retrospection: After a malicious attempt or malware is detected, the Cisco WSA continues to cross-examine files over an extended period of time.
• Application visibility and control: The Cisco ASA can inspect and even block applications that are not allowed by the corporate security polity. For example, an administrator can allow users to use social media sites such as Facebook but block micro-applications such as Facebook games.
Email Security Appliance
Users are no longer accessing email only from the corporate network or from a single device. Cisco provides cloud-based, hybrid, and on-premises solutions based on the Email Security Appliance (ESA) that can help protect any dynamic environment. This section introduces these solutions and technologies and explains how users can use threat intelligence to detect, analyze, and protect against both known and emerging threats.
The following are the most common email-based threats:
• Spam: These unsolicited email messages advertise a service, a scam (typically), or a message with malicious intent. Email spam continues to be a major threat because it can be used to spread malware.
• Malware attachments: These threats are email messages containing malicious software (malware).
• Phishing: This threat is an attacker’s attempt to fool a user into thinking that the email communication comes from a legitimate entity or site, such as a bank, social media website, online payment processor, or even the corporate IT department. The goal of a phishing email is to steal a user’s sensitive information, such as user credentials, bank account information, and so on.
• Spear phishing: This threat involves phishing attempts that are more targeted. Spear-phishing emails are directed to specific individuals or organizations. For instance, an attacker might perform a passive reconnaissance on an individual or organization by gathering information from social media sites (for example, Twitter, LinkedIn, and Facebook) and other online resources. Then the attacker might tailor a more directed and relevant message to the victim to increase the probability that the user will be fooled into following a malicious link, clicking an attachment containing malware, or simply replying to the email and providing sensitive information. Another phishing-based attack, called whaling, specifically targets executives and high-profile users.
![]()
The Cisco ESA runs the Cisco AsyncOS operating system. Cisco AsyncOS supports numerous features that help mitigate email-based threats. The following are examples of the features supported by the Cisco ESA:
• Access control: This feature controls access for inbound senders, according to a sender’s IP address, IP address range, or domain name.
• Antispam: Multilayer filters are based on Cisco SenderBase reputation and Cisco antispam integration. The antispam reputation and zero-day threat intelligence are fueled by the Cisco security intelligence and research group named Talos.
• Network antivirus: Network antivirus capabilities are provided at the gateway. Cisco partnered with Sophos and McAfee, supporting their antivirus scanning engines.
• Advanced Malware Protection (AMP): This tool allows security administrators to detect and block malware and perform continuous analysis and retrospective alerting.
• Data loss prevention (DLP): This feature enables administrators to detect any sensitive emails and documents leaving the corporation. The Cisco ESA integrates RSA email DLP for outbound traffic.
• Email encryption: This feature enables administrators to encrypt outgoing mail to address regulatory requirements. The administrators can configure an encryption policy on the Cisco ESA and use a local key server or hosted key service to encrypt the message.
• Email authentication: A few email authentication mechanisms include Sender Policy Framework (SPF), Sender ID Framework (SIDF), and DomainKeys Identified Mail (DKIM) verification of incoming mail, as well as DomainKeys and DKIM signing of outgoing mail.
• Outbreak filters: These filters provide preventive protection against new security outbreaks and email-based scams using Cisco Talos threat intelligence information.
The Cisco ESA acts as the email gateway for an organization, handling all email connections, accepting messages, and relaying messages to the appropriate systems. The Cisco ESA can service email connections from the Internet to users inside a network and from systems inside the network to the Internet. Email connections use Simple Mail Transfer Protocol (SMTP). The ESA services all SMTP connections, by default acting as the SMTP gateway.
Tip
Mail gateways are also known as mail exchangers (MX).
The Cisco ESA uses listeners to handle incoming SMTP connection requests. A listener defines an email processing service that is configured on an interface in the Cisco ESA. Listeners apply to email entering the appliance from either the Internet or internal systems.
The following listeners can be configured:
• Public listeners for email coming in from the Internet.
• Private listeners for email coming from hosts in the corporate (inside) network. (These emails are typically from internal groupware, Exchange, POP, or IMAP email servers.)
Cisco ESA listeners are often referred to as SMTP daemons, and they run on specific Cisco ESA interfaces. When a listener is configured, the following information must be provided:
• Listener properties such as a specific interface in the Cisco ESA and the TCP port that will be used. The listener properties must also indicate whether the listener is public or private.
• The hosts that are allowed to connect to the listener, using a combination of access control rules. An administrator can specify which remote hosts can connect to the listener.
• The local domains for which public listeners accept messages.
Cisco Security Management Appliance
Cisco Security Management Appliance (SMA) is a Cisco product that centralizes the management and reporting for one or more Cisco ESAs and Cisco WSAs. Cisco SMA enables you to consistently enforce policy and enhance threat protection. Figure 1-27 shows a Cisco SMA that is controlling Cisco ESAs and Cisco WSAs in different geographic locations (New York, Raleigh, Paris, and London).

Figure 1-27 Cisco SMA
The Cisco SMA can be deployed with physical appliances or as virtual appliances.
Cisco Identity Services Engine
![]()
The Cisco Identity Services Engine (ISE) is a comprehensive security identity management solution designed to function as a policy decision point for network access. It allows security administrators to collect real-time contextual information from a network, its users, and devices. Cisco ISE is the central policy management platform in the Cisco TrustSec solution. It supports a comprehensive set of AAA (authentication, authorization, and accounting), posture, and network profiler features in a single device. Cisco ISE provides the AAA functionality of legacy Cisco products such as the Cisco Access Control Server (ACS).
Cisco ISE allows security administrators to provide network guest access management and wide-ranging client provisioning policies, including 802.1X environments. The support of TrustSec features such as security group tags (SGTs) and security group access control lists (SGACLs) make the Cisco ISE a complete identity services solution. Cisco ISE supports policy sets, which let a security administrator group sets of authentication and authorization policies.
Cisco ISE provides Network Admission Control (NAC) features, including posture policies, to enforce configuration of end-user devices with the most up-to-date security settings or applications before they enter the network. The Cisco ISE supports the following agent types for posture assessment and compliance:
• Cisco NAC Web Agent: A temporary agent that is installed in end-user machines at the time of login. The Cisco NAC Web Agent is not visible on the end-user machine after the user terminates the session.
• Cisco NAC Agent: An agent that is installed permanently on a Windows or Mac OS X client system.
• Cisco AnyConnect Secure Mobility Client: An agent that is installed permanently on a Windows or Mac OS X client system.
Cisco ISE provides a comprehensive set of features to allow corporate users to connect their personal devices—such as mobile phones, tablets, laptops, and other network devices—to the network. Such a bring-your-own-device (BYOD) system introduces many challenges in terms of protecting network services and enterprise data. Cisco ISE provides support for multiple mobile device management (MDM) solutions to enforce policy on endpoints. ISE can be configured to redirect users to MDM onboarding portals and prompt them to update their devices before they can access the network. Cisco ISE can also be configured to provide Internet-only access to users who are not compliant with MDM policies.
Cisco ISE supports the Cisco Platform Exchange Grid (pxGrid), a multivendor, cross-platform network system that combines different parts of an IT infrastructure, such as the following:
• Security monitoring
• Detection systems
• Network policy platforms
• Asset and configuration management
• Identity and access management platforms
Cisco pxGrid has a unified framework with an open application programming interface designed in a hub-and-spoke architecture. pxGrid is used to enable the sharing of contextual-based information from a Cisco ISE session directory to other policy network systems, such as Cisco IOS devices and the Cisco ASA.
The Cisco ISE can be configured as a certificate authority (CA) to generate and manage digital certificates for endpoints. Cisco ISE CA supports standalone and subordinate deployments.
Cisco ISE software can be installed on a range of physical appliances or on a VMware server (Cisco ISE VM). The Cisco ISE software image does not support the installation of any other packages or applications on this dedicated platform.
Security Cloud-Based Solutions
![]()
Several cloud-based security solutions are also available in the market. For example, Cisco provides the following cloud-based security services:
• Cisco Cloud Email Security (CES)
• Cisco AMP Threat Grid
• Cisco Threat Awareness Service
• Umbrella (formerly OpenDNS)
• Stealthwatch Cloud
• CloudLock
The following sections describe these cloud-based security services.
Cisco Cloud Email Security
Cisco Cloud Email Security (CES) provides a cloud-based solution that allows companies to outsource the management of their email security. The service provides email security instances in multiple Cisco data centers to enable high availability.
The Cisco Hybrid Email Security solution combines both cloud-based and on-premises ESAs. This hybrid solution helps Cisco customers reduce their onsite email security footprint and outsource a portion of their email security to Cisco, while still allowing them to maintain control of confidential information within their physical boundaries. Many organizations must comply with regulations that require them to keep sensitive data physically on their premises. The Cisco Hybrid Email Security solution allows network security administrators to remain compliant and to maintain advanced control with encryption, DLP, and onsite identity-based integration.
Cisco AMP Threat Grid
![]()
Cisco acquired a security company called Threat Grid that provides cloud-based and on-premises malware analysis solutions. Cisco integrated Cisco AMP and Threat Grid to provide a solution for advanced malware analysis with deep threat analytics. The Cisco AMP Threat Grid integrated solution analyzes millions of files and correlates them with hundreds of millions of malware samples. This provides a look into attack campaigns and how malware is distributed. This solution provides a security administrator with detailed reports of indicators of compromise and threat scores that help prioritize mitigations and recover from attacks.
Cisco AMP Threat Grid crowdsources malware from a closed community and analyzes all samples using highly secure proprietary techniques that include static and dynamic analysis. These are different from traditional sandboxing technologies. The Cisco AMP Threat Grid analysis exists outside the virtual environment, identifying malicious code designed to evade analysis.
A feature in Cisco AMP Threat Grid called Glovebox helps you interact with the malware in real time, recording all activity for future playback and reporting. Advanced malware uses numerous evasion techniques to determine whether it is being analyzed in a sandbox. Some of these samples require user interaction. Glovebox dissects these samples without infecting your network while the samples are being analyzed. Glovebox is a powerful tool against advanced malware that allows analysts to open applications and replicate a workflow process, see how the malware behaves, and even reboot the virtual machine.
Umbrella (OpenDNS)
![]()
Cisco acquired a company called OpenDNS that provides DNS services, threat intelligence, and threat enforcement at the DNS layer. OpenDNS has a global network that delivers advanced security solutions (as a cloud-based service) regardless of where Cisco customer offices or employees are located. This service is extremely easy to deploy and easy to manage. Cisco has also incorporated the innovative advancements to threat research and threat-centric security that OpenDNS has developed to block advanced cybersecurity threats with other security and networking products. Millions of people use OpenDNS, including thousands of companies, from Fortune 500 enterprises to small businesses.
OpenDNS provides a free DNS service for individuals, students, and small businesses. You can just configure your endpoint (laptop, desktop, mobile device, server, or your DHCP server) to point to OpenDNS servers: 208.67.222.222 and/or 208.67.220.220.
OpenDNS also provides the following premium services:
• Cisco Umbrella: This enterprise advanced network security service protects any device, anywhere. This service blocks known malicious sites from being “resolved” in DNS. It provides an up-to-the-minute view and analysis of at least 2 percent of the world’s Internet activity to stay ahead of attacks. This service provides threat intelligence by seeing where attacks are being staged on the Internet.
• Investigate: This premium service provides information on where attacks are forming, allowing you to investigate incidents faster and prioritize them better. With the Investigate service, you can see up-to-the-minute threat data and historical context about all domains on the Internet and respond quickly to critical incidents. It provides a dynamic search engine and a RESTful API that you can use to automatically bring critical data into the security management and threat intelligence systems deployed in your organization. It also provides predictive threat intelligence using statistical models for real-time and historical data to predict domains that are likely malicious and could be part of future attacks.
Stealthwatch Cloud
![]()
Stealthwatch Cloud is a Software as a Service cloud solution. You can use Stealthwatch Cloud to monitor many different public cloud environments, such as Amazon’s AWS, Google Cloud Platform, and Microsoft Azure. All of these cloud providers support their own implementation of NetFlow:
• In Amazon AWS, the equivalent of NetFlow is called VPC Flow Logs. You can obtain detailed information about VPC Flow Logs in AWS at https://docs.aws.amazon.com/vpc/latest/userguide/flow-logs.html.
• Google Cloud Platform also supports VPC Flow Logs (or Google-branded GPC Flow Logs). You can obtain detailed information about VPC Flow Logs in Google Cloud Platform at https://cloud.google.com/vpc/docs/using-flow-logs.
• In Microsoft’s Azure, traffic flows are collected in Network Security Group (NSG) flow logs. NSG flow logs are a feature of Network Watcher. You can obtain additional information about Azure’s NSG flow logs and Network Watcher at https://docs.microsoft.com/en-us/azure/network-watcher/network-watcher-nsg-flow-logging-overview.
CloudLock
![]()
Cisco acquired a company called CloudLock that creates solutions to protect customers against data breaches in any cloud environment and application (app) through a highly configurable cloud-based data loss prevention (DLP) architecture. CloudLock has numerous out-of-the-box policies and a wide range of automated, policy-driven response actions, including the following:
• File-level encryption
• Quarantine
• End-user notifications
These policies are designed to provide common data protection and help with compliance. CloudLock also can monitor data at rest within platforms via an API and provide visibility of user activity through retroactive monitoring capabilities. This solution helps organizations defend against account compromises with cross-platform User and Entity Behavior Analytics (UEBA) for Software as a Service (SaaS), Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Identity as a Service (IDaaS) environments. CloudLock uses advanced machine learning to be able to detect anomalies and to identify activities in different countries that can be whitelisted or blacklisted in the platform. CloudLock Apps Firewall is a feature that discovers and controls malicious cloud apps that may be interacting with the corporate network.
Cisco NetFlow
![]()
NetFlow is a Cisco technology that provides comprehensive visibility into all network traffic that traverses a Cisco-supported device. Cisco invented NetFlow and is the leader in IP traffic flow technology. NetFlow was initially created for billing and accounting of network traffic and to measure other IP traffic characteristics such as bandwidth utilization and application performance. NetFlow has also been used as a network capacity planning tool and to monitor network availability. Nowadays, NetFlow is used as a network security tool because its reporting capabilities provide nonrepudiation, anomaly detection, and investigative capabilities. As network traffic traverses a NetFlow-enabled device, the device collects traffic flow data and provides a network administrator or security professional with detailed information about such flows.
NetFlow provides detailed network telemetry that can be used to see what is actually happening across the entire network. You can use NetFlow to identify DoS attacks, quickly identify compromised endpoints and network infrastructure devices, and monitor network usage of employees, contractors, or partners. NetFlow is also often used to obtain network telemetry during security incident response and forensics. You can also take advantage of NetFlow to detect firewall misconfigurations and inappropriate access to corporate resources.
NetFlow supports both IP Version 4 (IPv4) and IP Version 6 (IPv6).
There’s also the Internet Protocol Flow Information Export (IPFIX), which is a network flow standard led by the Internet Engineering Task Force (IETF). IPFIX was designed to create a common, universal standard of export for flow information from routers, switches, firewalls, and other infrastructure devices. IPFIX defines how flow information should be formatted and transferred from an exporter to a collector. IPFIX is documented in RFC 7011 through RFC 7015 and RFC 5103. Cisco NetFlow Version 9 is the basis and main point of reference for IPFIX. IPFIX changes some of the terminologies of NetFlow, but in essence they are the same principles of NetFlow Version 9.
Traditional Cisco NetFlow records are usually exported via UDP messages. The IP address of the NetFlow collector and the destination UDP port must be configured on the sending device. The NetFlow standard (RFC 3954) does not specify a specific NetFlow listening port. The standard or most common UDP port used by NetFlow is UDP port 2055, but other ports, such as 9555, 9995, 9025, and 9026, can also be used. UDP port 4739 is the default port used by IPFIX.
A flow in NetFlow is a unidirectional series of packets between a given source and destination. In a flow, the same source and destination IP addresses, source and destination ports, and IP protocol are shared. This is often referred to as the 5-tuple.
Note
You will learn additional details about NetFlow in Chapter 10, “Network Infrastructure Device Telemetry and Analysis.”
Data Loss Prevention
![]()
Data loss prevention is the ability to detect any sensitive emails, documents, or information leaving your organization. Several products in the industry inspect for traffic to prevent data loss in an organization. Several Cisco security products integrate with third-party products to provide this type of solution. For example, the Cisco ESA integrates RSA email DLP for outbound email traffic. Also, the Cisco Cloud Email Service and the Cisco Hybrid Email Security solution allow network security administrators to remain compliant and to maintain advanced control with encryption, DLP, and onsite identity-based integration. Another product family that integrates with other DLP solutions is the Cisco WSA, which redirects all outbound traffic to a third-party DLP appliance, allowing deep content inspection for regulatory compliance and data exfiltration protection. It enables an administrator to inspect web content by title, metadata, and size and even to prevent users from storing files to cloud services such as Dropbox and Google Drive.
Cisco CloudLock is also another DLP solution. CloudLock is designed to protect organizations of any type against data breaches in any type of cloud environment or application (app) through a highly configurable cloud-based DLP architecture.
CloudLock is an API-driven solution that provides a deep level of integration with monitored SaaS, IaaS, PaaS, and IDaaS solutions. It provides advanced cloud DLP functionality that includes out-of-the-box policies designed to help administrators maintain compliance. Additionally, CloudLock can monitor data at rest within platforms via APIs and provide a comprehensive picture of user activity through retroactive monitoring capabilities. Security administrators can mitigate risk efficiently using CloudLock’s configurable, automated response actions, including encryption, quarantine, and end-user notification.
Data loss doesn’t always take place because of a complex attack carried out by an external attacker; many data loss incidents have been carried out by internal (insider) attacks. Data loss can also happen because of human negligence or ignorance—for example, an internal employee sending sensitive corporate email to a personal email account or uploading sensitive information to an unapproved cloud provider. This is why maintaining visibility into what’s coming as well as leaving the organization is so important.
![]()
The Principles of the Defense-in-Depth Strategy
If you are a cybersecurity expert, or even an amateur, you probably already know that when you deploy a firewall or an intrusion prevention system or install antivirus or advanced malware protection on your machine, you cannot assume you are now safe and secure. A layered and cross-boundary “defense-in-depth” strategy is what is needed to protect your network and corporate assets. One of the primary benefits of a defense-in-depth strategy is that even if a single control (such as a firewall or IPS) fails, other controls can still protect your environment and assets. Figure 1-28 illustrates this concept.

Figure 1-28 Defense in Depth
The following are the layers illustrated in the figure:
• Nontechnical activities such as appropriate security policies and procedures, and end-user and staff training.
• Physical security, including cameras, physical access control (such as badge readers, retina scanners, and fingerprint scanners), and locks.
• Network security best practices, such as routing protocol authentication, control plane policing (CoPP), network device hardening, and so on.
• Host security solutions such as advanced malware protection (AMP) for endpoints, antiviruses, and so on.
• Application security best practices such as application robustness testing, fuzzing, defenses against cross-site scripting (XSS), cross-site request forgery (CSRF) attacks, SQL injection attacks, and so on.
• The actual data traversing the network. You can employ encryption at rest and in transit to protect data.
Tip
Each layer of security introduces complexity and latency, while requiring that someone manage it. The more people are involved, even in administration, the more attack vectors you create, and the more you distract your people from possibly more important tasks. Employ multiple layers, but avoid duplication—and use common sense.
The first step in the process of preparing your network and staff to successfully identify security threats is achieving complete network visibility. You cannot protect against or mitigate what you cannot view/detect. You can achieve this level of network visibility through existing features on network devices you already have and on devices whose potential you do not even realize. In addition, you should create strategic network diagrams to clearly illustrate your packet flows and where, within the network, you could enable security mechanisms to identify, classify, and mitigate the threats. Remember that network security is a constant war. When defending against the enemy, you must know your own territory and implement defense mechanisms.
Tip
Defense in depth in the cloud has different aspects to be considered such as security at the compute level (physical server security, hypervisor security, virtual machine security, and container security), at the application level, and protecting data at rest. Data at rest refers to the data that is not being transferred over a network (data that is “not moving” or “in transit”). It includes data that resides in every form of databases, file systems, memory of all types, networked storage like SAN, software-defined storage, and so on.
When applying defense-in-depth strategies, you can also look at a roles-based network security approach for security assessment in a simple manner. Each device on the network serves a purpose and has a role; subsequently, you should configure each device accordingly. You can think about the different planes as follows:
• Management plane: This is the distributed and modular network management environment.
• Control plane: This plane includes routing control. It is often a target because the control plane depends on direct CPU cycles.
• User/data plane: This plane receives, processes, and transmits network data among all network elements.
• Services plane: This is the Layer 7 application flow built on the foundation of the other layers.
• Policies: The plane includes the business requirements. Cisco calls policies the “business glue” for the network. Policies and procedures are part of this section, and they apply to all the planes in this list.
![]()
Software-defined networking introduced the notion of a centralized controller. The SDN controller has a global view of the network, and it uses a common management protocol to configure the network infrastructure devices. The SDN controller can also calculate reachability information from many systems in the network and pushes a set of flows inside the switches. The flows are used by the hardware to do the forwarding. Here you can see a clear transition from a distributed “semi-intelligent brain” approach to a “central and intelligent brain” approach.
Tip
An example of an open-source implementation of SDN controllers is the Open vSwitch (OVS) project using the OVS Database (OVSDB) management protocol and the OpenFlow protocol. Another example is the Cisco Application Policy Infrastructure Controller (Cisco APIC). Cisco APIC is the main architectural component and the brain of the Cisco Application Centric Infrastructure (ACI) solution. A great example of this is Cisco ACI, which is discussed in the next section of the chapter.
SDN changed a few things in the management, control, and data planes. However, the big change was in the control and data planes in software-based switches and routers (including virtual switches inside of hypervisors). For instance, the Open vSwitch project started some of these changes across the industry.
SDN provides numerous benefits in the area of the management plane. These benefits are in both physical switches and virtual switches. SDN is now widely adopted in data centers. A great example of this is Cisco ACI.
You should also view security in two different perspectives, as illustrated in Figure 1-29:
• Operational (reactive) security
• Proactive security

Figure 1-29 Reactive vs. Proactive Security
You should have a balance between proactive and reactive security approaches. Prepare your network, staff, and organization as a whole to better identify, classify, trace back, and react to security incidents. In addition, proactively protect your organization while learning about new attack vectors, and mitigate those vectors with the appropriate hardware, software, and architecture solutions.
![]()
Confidentiality, Integrity, and Availability: The CIA Triad
Confidentiality, integrity, and availability are often referred to as the CIA triad. This model was created to define security policies. In some cases, you might also see this model referred to as the AIC triad (availability, integrity, and confidentiality) to avoid confusion with the United States Central Intelligence Agency.
The idea is that confidentiality, integrity, and availability should be guaranteed in any system that is considered secured.
Confidentiality
The ISO 27000 standard has a very good definition: “confidentiality is the property, that information is not made available or disclosed to unauthorized individuals, entities, or processes.” One of the most common ways to protect the confidentiality of a system or its data is to use encryption. The Common Vulnerability Scoring System (CVSS) uses the CIA triad principles within the metrics used to calculate the CVSS base score.
Note
You will learn more about CVSS throughout the following chapters, and you can obtain more information about CVSS at www.first.org/cvss/specification-document.
Integrity
Integrity is the ability to make sure that a system and its data have not been altered or compromised. It ensures that the data is an accurate and unchanged representation of the original secure data. Integrity applies not only to data, but also to systems. For instance, if a threat actor changes the configuration of a server, firewall, router, switch, or any other infrastructure device, it is considered that this person impacted the integrity of the system.
Availability
Availability means that a system or application must be “available” to authorized users at all times. According to the CVSS version 3 specification, the availability metric “measures the impact to the availability of the impacted component resulting from a successfully exploited vulnerability. While the Confidentiality and Integrity impact metrics apply to the loss of confidentiality or integrity of data (e.g., information, files) used by the impacted component, this metric refers to the loss of availability of the impacted component itself, such as a networked service (e.g., web, database, email). Since availability refers to the accessibility of information resources, attacks that consume network bandwidth, processor cycles, or disk space all impact the availability of an impacted component.”
A common example of an attack that impacts availability is a DoS attack.
![]()
Risk and Risk Analysis
According to the Merriam-Webster online dictionary, risk is “the possibility that something bad or unpleasant will happen.” In the world of cybersecurity, risk can be defined as the possibility of a security incident (something bad) happening. There are many standards and methodologies for classifying and analyzing cybersecurity risks. The Federal Financial Institutions Examination Council (FFIEC) developed the Cybersecurity Assessment Tool (Assessment) to help financial institutions identify their risks and determine their cybersecurity preparedness. This guidance/tool can be useful for any organization. The FFIEC tool provides a repeatable and measurable process for organizations to measure their cybersecurity readiness.
According to the FFIEC, the assessment consists of two parts:
• Inherent Risk Profile and Cybersecurity Maturity: The Inherent Risk Profile identifies the institution’s inherent risk before implementing controls. Cybersecurity includes domains, assessment factors, components, and individual declarative statements across five maturity levels to identify specific controls and practices that are in place. Although management can determine the institution’s maturity level in each domain, the assessment is not designed to identify an overall cybersecurity maturity level.
• The International Organization for Standardization (ISO) 27001: This is the international standard for implementing an information security management system (ISMS). ISO 27001 is heavily focused on risk-based planning to ensure that the identified information risks (including cyber risks) are appropriately managed according to the threats and the nature of those threats. ISO 31000 is the general risk management standard that includes principles and guidelines for managing risk. It can be used by any organization, regardless of its size, activity, or sector. Using ISO 31000 can help organizations increase the likelihood of achieving objectives, improve the identification of opportunities and threats, and effectively allocate and use resources for risk treatment.
The ISO/IEC 27005 standard is more focused on cybersecurity risk assessment. It is titled “Information technology—Security techniques—Information security risk management.”
The following is according to ISO’s website:
The standard doesn’t specify, recommend or even name any specific risk management method. It does however imply a continual process consisting of a structured sequence of activities, some of which are iterative:
• Establish the risk management context (e.g. the scope, compliance obligations, approaches/methods to be used and relevant policies and criteria such as the organization’s risk tolerance or appetite);
• Quantitatively or qualitatively assess (i.e. identify, analyze and evaluate) relevant information risks, taking into account the information assets, threats, existing controls and vulnerabilities to determine the likelihood of incidents or incident scenarios, and the predicted business consequences if they were to occur, to determine a ‘level of risk;’
• Treat (i.e. modify [use information security controls], retain [accept], avoid and/or share [with third parties]) the risks appropriately, using those ‘levels of risk’ to prioritize them;
• Keep stakeholders informed throughout the process; and
• Monitor and review risks, risk treatments, obligations and criteria on an ongoing basis, identifying and responding appropriately to significant changes.
There are also standards to score the overall “risk” of a vulnerability. The most commonly used is the Common Vulnerability Scoring System developed by the Forum of Incident Response and Security Teams (FIRST). CVSS is a standards-based scoring method that conveys vulnerability severity and helps determine the urgency and priority of response. CVSS is used by many Product Security Incident Response Teams (PSIRTs), vulnerability coordination centers, security researchers, and consumers of security vulnerability information.
There are also several additional scoring systems:
• Common Weakness Scoring System (CWSS): A methodology for scoring software weaknesses. CWSS is part of the Common Weakness Enumerator (CWE) standard. More information about CWSS is available at http://cwe.mitre.org/cwss.
• Common Misuse Scoring System (CMSS): A standardized way to measure software feature misuse vulnerabilities. More information about CMSS is available at http://scap.nist.gov/emerging-specs/listing.html#cmss.
• Common Configuration Scoring System (CCSS): More information about CCSS can be found at http://csrc.nist.gov/publications/nistir/ir7502/nistir-7502_CCSS.pdf.
Personally Identifiable Information and Protected Health Information
Many regulations as well as the United States government require organizations to identify personally identifiable information (PII) and protected health information (PHI) and handle them in a secure manner. Unauthorized release or loss of such data could result in severe fines and penalties for the organization. Given the importance of PII and PHI, regulators and the government want to oversee the usage more efficiently. This section explains what PII and PHI are.
PII
![]()
According to the Executive Office of the President, Office of Management and Budget (OMB), and the U.S. Department of Commerce, Office of the Chief Information Officer, PII refers to “information which can be used to distinguish or trace an individual’s identity.” The following are a few examples:
• An individual’s name
• Social security number
• Biological or personal characteristics, such as an image of distinguishing features, fingerprints, X-rays, voice signature, retina scan, and the geometry of the face
• Date and place of birth
• Mother’s maiden name
• Credit card numbers
• Bank account numbers
• Driver license number
• Address information, such as email addresses or street addresses, and telephone numbers for businesses or personal use
PHI
![]()
The Health Insurance Portability and Accountability Act (HIPAA) requires health-care organizations and providers to adopt certain security regulations for protecting health information. The Privacy Rule calls this information “protected health information,” or PHI. This information includes, but is not limited to, the following:
• An individual’s name (that is, patient’s name)
• All dates directly linked to an individual, including date of birth, death, discharge, and administration
• Telephone and fax numbers
• Email addresses and geographic subdivisions such as street addresses, ZIP codes, and county
• Medical record numbers and health plan beneficiary numbers
• Certificate numbers or account numbers
• Social security number
• Driver license number
• Biometric identifiers, including voice or fingerprints
• Photos of the full face or recognizable features
• Any unique number-based code or characteristic
• The individual’s past, present, and future physical or mental health or condition
• The provision of health care to the individual, or the past, present, or future payment for the provision of health care to the individual
Principle of Least Privilege and Separation of Duties
Two additional key concepts in information security are the principle of least privilege and separation of duties. This section defines these two key concepts.
![]()
Principle of Least Privilege
The principle of least privilege states that all users—whether they are individual contributors, managers, directors, or executives—should be granted only the level of privilege they need to do their jobs, and no more. For example, a sales account manager really has no business having administrator privileges over the network, or a call center staff member over critical corporate financial data.
The same concept of principle of least privilege can be applied to software. For example, programs or processes running on a system should have the capabilities they need to “get their job done,” but no root access to the system. If a vulnerability is exploited on a system that runs “everything as root,” the damage could extend to a complete compromise of the system. This is why you should always limit users, applications, and processes to access and run as the least privilege they need.
Tip
Somewhat related to the principle of least privilege is the concept of “need to know,” which means that users should get access only to data and systems that they need to do their job, and no other.
![]()
Separation of Duties
Separation of duties is an administrative control dictating that a single individual should not perform all critical- or privileged-level duties. Additionally, important duties must be separated or divided among several individuals within the organization. The goal is to safeguard against a single individual performing sufficiently critical or privileged actions that could seriously damage a system or the organization as a whole. For instance, security auditors responsible for reviewing security logs should not necessarily have administrative rights over the systems. Another example is that a network administrator should not have the ability to alter logs on the system. This is to prevent such individuals from carrying out unauthorized actions and then deleting evidence of such action from the logs (in other words, covering their tracks).
Think about two users having two separate keys to open a safety deposit box. Separation of duties is similar to that concept, where the safety deposit box cannot be opened by a user without the other key.
![]()
Security Operations Centers
Security operations centers (SOCs) are facilities where an organization’s assets, including applications, databases, servers, networks, desktops, and other endpoints, are monitored, assessed, and protected.
Tip
Computer Security Incident Response Team (CSIRT) analysts typically work in SOCs utilizing many tools to monitor events from numerous systems (firewalls, applications, IPSs, DLPs, endpoint security solutions, and so on). Typically, these logs are aggregated in a Security Information and Event Manager (SIEM) system. Modern SOCs also use Security Orchestration, Automation, and Response (SOAR) systems that extend beyond traditional SIEMs. You learn more details about how SOC analysts use SIEM and SOAR implementations in Chapter 7, “Introduction to Security Operations Management,” Chapter 8, “Fundamentals of Intrusion Analysis,” Chapter 12, “Challenges in the Security Operations Center (SOC),” Chapter 13, “The Art of Data and Event Analysis,” and Chapter 14, “Classifying Intrusion Events into Categories.”
Establishing SOC capabilities requires careful planning. The planning phase helps you decide on and formalize yourself with the objectives that justify having an SOC, and to develop a roadmap you can use to track your progress against those predefined objectives. The success of any security program (including the SOC) depends on proper planning. There are always challenges that are specific to an organization, and these challenges are introduced because of issues related to governance, collaboration, lack of tools, lack of automation, lack of threat intelligence, skill sets, and so on. Such challenges must be identified and treated, or at least acknowledged, at an early stage of an SOC establishment program. SOCs are created to be able to address the following challenges:
• How can you detect a compromise in a timely manner?
• How do you triage a compromise to determine the severity and the scope?
• What is the impact of the compromise to your business?
• Who is responsible for detecting and mitigating a compromise?
• Who should be informed or involved, and when do you deal with the compromise once detected?
• How and when should you communicate a compromise internally or externally, and is that needed in the first place?
To build and operate an effective SOC, you must have the following:
• Executive sponsorship.
• SOC operating as a program. Organizations should operate the SOC as a program rather than a single project. Doing so depends on the criticality and the number of resources required to design, build, and operate the various services offered by the SOC. Having a clear SOC service strategy with clear goals and priorities will shape the size of the SOC program, timeline, and the number of resources required to deliver the program objectives.
• A governance structure. Metrics must be established to measure the effectiveness of the SOC capabilities. These metrics should provide sufficient and relevant visibility to the organization’s management team on the performance of the SOC and should identify areas where improvements and investments are needed.
• Effective team collaboration.
• Access to data and systems.
• Applicable processes and procedures.
• Team skill sets and experience.
• Budget (for example, will it be handled in-house or outsourced?).
![]()
Playbooks, Runbooks, and Runbook Automation
Organizations need to have capabilities to define, build, orchestrate, manage, and monitor the different operational processes and workflows. This is achieved by implementing playbooks, runbooks and runbook automation (RBA). A runbook is a collection of procedures and operations performed by system administrators, security professionals, or network operators. According to Gartner, “the growth of RBA has coincided with the need for IT operations executives to enhance IT operations efficiency measures.” Gartner, Inc., is an American research and advisory firm providing information technology–related insight for IT and other business leaders.
Here are some of the metrics to measure effectiveness:
• Mean time to repair (MTTR)
• Mean time between failures (MTBF)
• Mean time to discover a security incident
• Mean time to contain or mitigate a security incident
• Automation of the provisioning of IT resources
Many different commercial and open-source RBA solutions are available in the industry. An example of a popular open-source RBA solution is Rundeck (http://rundeck.org/). Rundeck can be integrated with configuration management platforms such as Chef, Puppet, and Ansible.
Tip
Playbooks are also extremely beneficial for all SOCs. You can navigate and become familiar with several open-source examples of playbooks that are derived from standard incident response policies and industry best practices at www.incidentresponse.com/playbooks/.
![]()
Digital Forensics
The United States Computer Emergency Response Team (CERT) defines cyber forensics as follows:
If you manage or administer information systems and networks, you should understand cyber forensics. Forensics is the process of using scientific knowledge for collecting, analyzing, and presenting evidence to the courts. (The word forensics means “to bring to the court.”) Forensics deals primarily with the recovery and analysis of latent evidence. Latent evidence can take many forms, from fingerprints left on a window to DNA evidence recovered from blood stains to the files on a hard drive.
Cyber forensics is often referred to as digital forensics or computer forensics. The two primary objectives in digital forensics are to find out what happened and to collect data in a manner that is acceptable to the court.
Note
Many in the industry also combine the terms digital forensics and incident response (DFIR). If you see the term or acronym DFIR used in documents, standards, and articles, you know that the practices of incident response and digital forensics (which go hand-in-hand) are combined.
Any device that can store data is potentially the object of digital forensics, including, but not limited to, the following:
• Computers (servers, desktop machines, and so on)
• Smartphones
• Tablets
• Network infrastructure devices (routers, switches, firewalls, intrusion prevention systems)
• Network management systems
• Printers
• IoT devices
![]()
Chain of custody is critical to forensics investigations. Chain of custody is the way you document and preserve evidence from the time that you started a cyber forensics investigation to the time the evidence is presented at court or to your executives (in the case of an internal investigation). It is extremely important to be able to show clear documentation of the following:
• How the evidence was collected
• When it was collected
• How it was transported
• How is was tracked
• How it was stored
• Who had access to the evidence and how it was accessed
Tip
If you fail to maintain proper chain of custody, it is likely you cannot use that evidence in court. It is also important to know how to dispose of evidence after an investigation.
When you collect evidence, you must protect its integrity. This involves making sure that nothing is added to the evidence and that nothing is deleted or destroyed (this is known as evidence preservation).
Tip
A method often used for evidence preservation is to work only with a copy of the evidence—in other words, not work directly with the evidence itself. This involves creating an image of any hard drive or any storage device.
Several forensics tools are available on the market. The following are two of the most popular:
• Guidance Software’s EnCase (www.guidancesoftware.com/)
• AccessData’s Forensic Toolkit (http://accessdata.com/)
Tip
Several open-source tools and Linux distributions can be used for digital forensics. Examples include Security Onion, CAINE, and SIFT. I have included numerous examples of tools for evidence collection, log analysis, memory analysis and other digital forensics tasks at the following GitHub repository: https://github.com/The-Art-of-Hacking/h4cker/tree/master/dfir
Another methodology used in evidence preservation is to use write-protected storage devices. In other words, the storage device you are investigating should immediately be write-protected before it is imaged and should be labeled to include the following:
• Investigator’s name
• Date when the image was created
• Case name and number (if applicable)
Additionally, you must prevent electronic static or other discharge from damaging or erasing evidentiary data. Special evidence bags that are antistatic should be used to store digital devices. It is very important that you prevent electrostatic discharge (ESD) and other electrical discharges from damaging your evidence. Some organizations even have cyber forensic labs that control access to only authorized users and investigators. One method often used involves constructing what is called a Faraday cage. This cage is often built out of a mesh of conducting material that prevents electromagnetic energy from entering into or escaping from the cage. Also, this prevents devices from communicating via Wi-Fi or cellular signals.
What’s more, transporting the evidence to the forensics lab or any other place, including the courthouse, has to be done very carefully. It is critical that the chain of custody be maintained during this transport. When you transport the evidence, you should strive to secure it in a lockable container. It is also recommended that the responsible person stay with the evidence at all times during transportation.
Note
Chapter 8, “Fundamentals of Intrusion Analysis,” covers the details of the incident response process, the operations of a SOC, and post-breach incident response. Chapter 9, “Introduction to Digital Forensics,” covers the details about the science of digital forensics.
Exam Preparation Tasks
Review All Key Topics
Review the most important topics in the chapter, noted with the Key Topic icon in the outer margin of the page. Table 1-3 lists a reference of these key topics and the page numbers on which each is found.
![]()
Table 1-3 Key Topics for Chapter 1



Define Key Terms
Define the following key terms from this chapter, and check your answers in the glossary:
network firewalls
Security Information and Event Manager (SIEM)
Security Orchestration, Automation, and Response (SOAR)
Review Questions
The answers to these questions appear in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes and Review Questions.” For more practice with exam format questions, use the exam engine on the website.
1. Explain the features of a traditional stateful firewall.
2. List a commercial tool used in digital forensics.
3. Describe some of the benefits of NetFlow.
4. What is DLP?
5. Stateful and traditional firewalls can analyze packets and judge them against a set of predetermined rules called access control lists. Which elements within a packet do they inspect?
6. What is a specification that provides a methodology for scoring software weaknesses?
7. List an open-source SDN solution.
8. Which of the following is true about heuristic-based algorithms?
a. Heuristic-based algorithms may require fine-tuning to adapt to network traffic and minimize the possibility of false positives.
b. Heuristic-based algorithms do not require fine-tuning.
c. Heuristic-based algorithms support advanced malware protection.
d. Heuristic-based algorithms provide capabilities for the automation of IPS signature creation and tuning.
9. Describe the use of DMZs.
10. Which of the following has the most storage requirements?
a. NetFlow
b. Syslog
c. Full packet captures
d. IPS signatures
11. Which of the following statements are true about application proxies? (Choose two.)
a. Application proxies, or proxy servers, are devices that operate as intermediary agents on behalf of clients that are on a private or protected network.
b. Clients on the protected network send connection requests to the application proxy to transfer data to the unprotected network or the Internet.
c. Application proxies can be classified as next-generation firewalls.
d. Application proxies always perform Network Address Translation.
12. Which of the following statements are true when referring to Network Address Translation? (Choose two.)
a. NAT can only be used in firewalls.
b. Static NAT does not allow connections to be initiated bidirectionally.
c. Static NAT allows connections to be initiated bidirectionally.
d. NAT is often used by firewalls; however, other devices such as routers and wireless access points provide support for NAT.
