Chapter 9. Asset Threats, Response, and Management
The following exam domain is partially covered in this chapter:
Domain 5—Protection of Information Assets
This chapter covers the following topics:
![]() Security Controls: These controls play a key role in preventing attackers from successfully attacking an organization.
Security Controls: These controls play a key role in preventing attackers from successfully attacking an organization.
![]() Attack Methods and Techniques: Auditors should understand the techniques and methods used by attackers.
Attack Methods and Techniques: Auditors should understand the techniques and methods used by attackers.
![]() Prevention and Detection Tools and Techniques: Implementing basic controls such as logging, auditing, and security information and event management (SIEM) can help prevent and detect common attack patterns.
Prevention and Detection Tools and Techniques: Implementing basic controls such as logging, auditing, and security information and event management (SIEM) can help prevent and detect common attack patterns.
![]() Problem and Incident Management Practices: It is not a matter of if but when a security breach will occur. Incident response and forensics should be documented and tested.
Problem and Incident Management Practices: It is not a matter of if but when a security breach will occur. Incident response and forensics should be documented and tested.
It is a sad fact that things will go wrong and that an organization must be prepared to deal with problems. While the first step is to obviously have security controls in place to address issues, it’s just as important to think like an attacker to understand how various attacks can occur. If an auditor understands common attack vectors, it’s easier to understand what types of controls can be used to prevent these attacks. Luckily, a host of tools are available for detecting common attack patterns by using intrusion detection systems or reviewing of the logs.
The final component of being prepared is to have a plan in place to deal with problems, incidents, and breaches. Plans must be tested. When a breach occurs, you must know how to protect evidence. Before an incident ever occurs, it should be clear who is responsible for specific activities and what must occur from a forensic standpoint to make sure that evidence will be admissible in court.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz allows you to assess whether you should read this entire chapter thoroughly or jump to the “Exam Preparation Tasks” section. If you are in doubt about your answers to these questions or your own assessment of your knowledge of the topics, read the entire chapter. Table 9-1 lists the major headings in this chapter and their corresponding “Do I Know This Already?” quiz questions. You can find the answers at the bottom of the page following the quiz and in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes and Review Questions.”
Table 9-1 “Do I Know This Already?” Section-to-Question Mapping
Foundation Topics Section |
Questions Covered in This Section |
Security Controls |
1–2 |
Attack Methods and Techniques |
3–8 |
Prevention and Detection Tools and Techniques |
9 |
Problem and Incident Management Practices |
10 |
Caution
The goal of self-assessment is to gauge your mastery of the topics in this chapter. If you do not know the answer to a question or are only partially sure of the answer, you should mark that question as incorrect for purposes of the self-assessment. Giving yourself credit for an answer you correctly guess skews your self-assessment results and might provide you with a false sense of security.
1. Which of the following is similar to SIEM except that it focuses specifically on database access and activity?
a. NAC
b. NetFlow
c. DAM
d. SNMP
2. Which of the following is not a concern when hosting data in the cloud?
a. Regulatory issues related to data type
b. Encryption
c. Disaster recovery plan of the cloud provider
d. Reduction in workforce
3. Which of the following terms is used to describe obtaining personal information about an individual under false pretenses?
a. Pretexting
b. Smishing
c. Whaling
d. Phishing
4. Which of the following attacks best describes the removal of small amounts of money over a long period of time?
a. Man-in-the-middle
b. Salami attack
c. Integer overflow
d. TOCTOU
5. Which attack is also known as a race condition?
a. Man-in-the-middle
b. Salami attack
c. Integer overflow
d. TOCTOU
6. Which of the following is a social engineering attack that is used to target a specific group of people?
a. Phishing
b. Spear phishing
c. Whaling
d. Integer overflow
7. What attack technique does not provide the attacker access but blocks others?
a. Session hijacking
b. Password cracking
c. Hijacking
d. DoS
8. Which of the following presents itself as one thing but in reality does something else?
a. Trojan
b. Virus
c. Worm
d. TOCTOU
9. Which of the following are used to scan for deviations to normal trends?
a. Audit-reduction tools
b. Trend- or variance-detection tools
c. Attack-detection tools
d. IDSs
10. What type of forensic analysis allows a malicious program to execute in a sandbox?
a. Dynamic analysis
b. Static analysis
c. Reverse engineering
d. Passive analysis
Security Controls
Security controls are safeguards or countermeasures that are used to avoid, detect, or minimize security risks to an enterprise. NIST speaks of three categories of security controls: technical, administrative, and physical. Each category of control can be broken down by functionality (for example, preventive, detective, corrective, deterrent, recovery, compensating). The idea is to use controls to restrict access to only authorized users and for only authorized data. Chapter 8, “Protection of Assets,” discusses physical controls, and the following sections describe technical and administrative controls.
Technical Controls
Technical controls include various technical measures, such as firewalls, identification/authentication systems, intrusion detection systems, and file encryption, among others. Controls are an important concept, and auditors typically review and test controls to verify that they are providing adequate protection for the enterprise.
Cloud Computing
One area of concern is the technical controls used to protect data in the cloud. An auditor may be tasked with providing stakeholders with an assessment of the effectiveness of a cloud computing service provider’s internal controls and security. As part of this, the auditor needs to identify internal control deficiencies within the customer organization. For example, is encryption being used? If so, what is its strength? Is the data encrypted at rest or also while in transit? An auditor should also consider how data is stored. Is the data on a private server, or is it in the cloud shared with other organizations?
Operating Systems
For data not stored in the cloud, there is still more work to be done. End user workstations and operating systems are under constant threat of attack. Just take a moment to think of your own computer system. You have many services turned on and have multiple applications (for example, iTunes, Microsoft Office, Java, Adobe Flash, QuickTime) present. This makes for a large attack surface.
An important part of implementing technical controls is hardening the OS. This process is accomplished by turning off, removing, and deleting unused components. An auditor should verify that controls have been implemented to protect operating systems. Figure 9-1 shows an example of Bastille Linux, which can be used to harden Linux systems. The following are some of the guidelines for OS hardening:
![]() NSA security configuration guidance: www.iad.gov/iad/library/ia-guidance/security-configuration/
NSA security configuration guidance: www.iad.gov/iad/library/ia-guidance/security-configuration/
![]() Center for Internet Security benchmarks: www.cisecurity.org/cis-benchmarks/
Center for Internet Security benchmarks: www.cisecurity.org/cis-benchmarks/
![]() Security Technical Implementation Guides (STIGs): http://iase.disa.mil/stigs/Pages/index.aspx
Security Technical Implementation Guides (STIGs): http://iase.disa.mil/stigs/Pages/index.aspx
Answers to the “Do I Know This Already?” Quiz:
1. C;
2. D;
3. A;
4. B;
5. D;
6. B;
7. D;
8. A;
9. B;
10. A
Regardless of what standard or approach you use to harden the OS, the idea is to remove or disable items that are not needed. For example, you would want to turn off the following services and applications unless absolutely necessary: Telnet, FTP, rlogin, TFTP, LPD, CDE, NetBIOS, and even HTTP if it’s not used. An auditor should also verify that network resources are secured. Table 9-2 provides some examples of best practices that are based on PCI-DSS standard.
Table 9-2 Best Practices Examples
Item |
Recommendation |
Logs |
Mandatory log monitoring. |
Patching |
Patching all systems and applications. |
Vulnerability assessment |
Establish a process to identify newly discovered security vulnerabilities. |
Encryption |
Enforce encryption for data at rest and data in transit. |
User Accounts |
Remove inactive user accounts at least every 90 days. |
Passwords |
Remove default passwords and require unique passwords for all users. |
Databases
Databases are high-value assets for most organizations. SQL injection is one common attack vector. It’s basically an input problem and typically makes the OWASP top 10 security concerns, as shown in Figure 9-2.
One way to deal with this type of input problem is to use defense-in-depth, which begins by filtering traffic before it ever enters the network. A web application firewall (WAF) can help. A WAF is the next advancement in firewall design. A WAF analyzes web traffic and can be used to filter out SQL injection attacks, malware, cross-site scripting (XSS), and cross-site request forgery (XSRF). (XSS and XSRF are discussed later in the chapter.) WAFs require a high degree of application awareness as they have the ability to analyze web traffic and look for items such as malicious XML constructs and SQL injection commands.
Traditional end point solutions such as anti-malware have also advanced as endpoint detection and response (EDR) is now being used by many as an additional defense to protect endpoint systems. This emerging technology describes a category of tools that focus on detecting, investigating, and mitigating suspicious activities and issues on hosts and client systems.
Another item that can be used to help defend against SQL inject attacks is database activity monitoring (DAM). DAM systems emerged as companies began to face more threats, such as SQL injection, than in the past. In addition, they assist with compliance so that companies can track what activity occurs within databases. Laws and regulations such as HIPAA and PCI-DSS have increased this demand. A DAM system basically monitors a database and analyzes the types of activity that are occurring. You can think of DAM as being similar to security information and event management (SIEM) except that an SIEM correlates and analyzes events from multiple sources, whereas DAM focuses specifically on database access and activity.
Note
CISA exam candidates should have knowledge of security options such as SIEM, DAM, IDSs, and firewalls.
Protecting a database is not just about preventing and detecting problems. Backups are also a concern. Over the past few years, ransomware has grown to be a huge problem, and part of its success is related to the fact that some organizations don’t have database backups. That’s where database shadowing comes in. A database shadowing system uses two physical disks to write the data to. It creates good redundancy by duplicating the database sets to mirrored servers. Therefore, this is an excellent way to provide fault tolerance and redundancy. Shadowing mirrors changes to the database as they occur.
Virtualization
Virtualized servers have many advantages. One of the biggest is server consolidation. Virtualization allows you to host many virtual machines on one physical server. This reduces deployment time and makes better use of existing resources. Some controls are based on the type of virtualized system being used. A Type 1 hypervisor runs on bare metal and does not have an underlying OS. A Type 2 hypervisor system has an underlying OS. A hypervisor is the computer software or hardware that creates and runs a virtual machine.
Virtualized systems are just as vulnerable to attack as standalone machines. Also, malware has the potential to migrate from one virtual machine to another. This problem, referred to as VM escape, means the attacker is able to run malware or code on a virtual machine that allows an operating system running within it to break out and interact directly with the hypervisor. This can be especially problematic when a single platform is hosting multiple companies’ virtual machines (VMs) or when VMs of different security levels are used.
Securing virtual servers requires the same focus on defense-in-depth that is used for physical systems. Some basic items to review for securing virtual systems are listed in Table 9-3.
Table 9-3 Common Security Controls for Virtual Systems
Security Control |
Comments |
Antivirus |
Antivirus must be present on the host and all VMs. |
Authentication |
Use strong access control. |
Encryption |
Use encryption for sensitive data in storage or transit. |
Hardening |
All VMs should be hardened so that nonessential services are removed. |
Physical controls |
Controls should be implemented to limit who has access to the data center. |
Remote access services should be restricted when not needed. When required, use encryption. |
|
Resource access |
Use administrative accounts only as needed. |
Administrative Controls
From an auditing perspective, a big concern is the presence of policies that specify the approved/prohibited activities of employees. For example, years ago it was easy for an organization to control the message of the organization. Today, it’s easy for information to spread via instant messaging, message boards, blogs, and social networking. These technologies have the ability to introduce risk to the enterprise.
Although instant messaging (IM) is not as popular as it once was, it is still used and available in many home and corporate settings. IM allows two-way communication in near real time. It enables business users to collaborate, hold informal chat meetings, and share files and information. An auditor should understand that IM programs are not all the same. Some have added encryption, central logging, and user access controls and are aimed at corporate clients, while others operate without such controls. Without adequate controls, IM products are highly vulnerable to malware and can be used for data exfiltration. Sensitive information can be transmitted without the company’s knowledge. An auditor should seek answers to the following questions:
![]() Is the IM solution a critical business requirement?
Is the IM solution a critical business requirement?
![]() What IM product is used? Is it just one, or are multiple applications permitted?
What IM product is used? Is it just one, or are multiple applications permitted?
![]() Is encryption used?
Is encryption used?
![]() Is IM just for internal use?
Is IM just for internal use?
![]() Is IM used for external clients?
Is IM used for external clients?
![]() Is the company subject to regulatory compliance requirements for IM? If so, how is data logged and recorded?
Is the company subject to regulatory compliance requirements for IM? If so, how is data logged and recorded?
![]() Are users allowed to transfer files and applications? If so, are any mechanisms in place to control this activity?
Are users allowed to transfer files and applications? If so, are any mechanisms in place to control this activity?
![]() Are virus scanning, file scanning, and content-filtering applications used?
Are virus scanning, file scanning, and content-filtering applications used?
![]() How many employees are expected to use the system over the next 24 to 36 months?
How many employees are expected to use the system over the next 24 to 36 months?
![]() Is the IM application available to everyone or only to specific users?
Is the IM application available to everyone or only to specific users?
![]() Does the IM solution use filters on specific words to flag for profanity or inappropriate content?
Does the IM solution use filters on specific words to flag for profanity or inappropriate content?
![]() Does the organization provide user training for secure use of IM?
Does the organization provide user training for secure use of IM?
Blogs, message boards, and websites can be as concerning as IM. It’s relatively easy for an individual to set up a blog or a domain that disparages or slanders an organization or that even leaks sensitive information (see Figure 9-3). Starting in 2015, a new sucks top-level domain was created. It is difficult for an organization to get a damaging blog or website taken down, and often it’s up to the courts to determine whether a case involves trademark violation or is protected free speech.
Finally, social media has grown immensely in popularity and brought new problems. Workplace social media policies are becoming more common as a growing number of people are sharing, liking, and posting every aspect of their life. Organizations have taken action against employees who post damaging information on social media. For example, Burger King fired a worker who posted pictures of himself standing in bins of lettuce, and Taco Bell fired an employee over a picture posted on Facebook that showed the employee licking a tall stack of taco shells. Figure 9-4 shows an example of a social media page used to show pictures of credit cards people have shared online. Employees can post any number of items on social media. Many of which should clearly not be posted.
Companies should have policies that specify what employees should or should not post on their personal social media pages. These policies should address issues such as the following:
![]() What is considered appropriate online activity
What is considered appropriate online activity
![]() Whether social media use is allowed while at work
Whether social media use is allowed while at work
![]() What is considered confidential information
What is considered confidential information
![]() The consequences of employees’ actions online violating policy
The consequences of employees’ actions online violating policy
Figure 9-5 shows a site (http://blog.hirerabbit.com) that lists 5 good examples of corporate social media policy.
Attack Methods and Techniques
Without security measures and controls in place, an enterprise might be subjected to an attack. Some common attack methods are discussed next. These techniques can be social, technical, or physical. Let’s look at some examples of social attacks first.
Social Engineering and Nontechnical Attacks
Social engineering predates the computer era. For many years, scams have used the art of manipulation to trick victims into providing private information or improper access. Social-engineering attacks work because they attack a weak link—people.
Social-engineering attacks can be launched in person, on the phone, or via computer. Attacks carried out in person can be as easy as attackers disguising themselves as repair persons or vending machine employees. Attackers may use the phone to call the help desk and ask to have a password reset or seek to gain other privileged information. The low-ranking help desk employee might be bullied, feel scared, or feel coerced into giving out a password or other important information.
Email attacks are also commonly used for social engineering. These typically occur by means of the attacker spoofing a trusted party, such as eBay, Gmail, PayPal, Morgan Stanley, and so on. The attacker sends an official-sounding email, asking the user to verify a password, click a link, or open an attachment. If this type of attack targets a random group of people, it is known as phishing. Spear phishing is a targeted attack, and whaling is the term used for pulling in a big fish. Pretexting is a social attack that involves obtaining personal information about an individual under false pretenses. Pretexting is usually done when an individual wants more information about a certain individual to investigate his or her activities, such as to sue that person, to steal his or her assets, or to obtain credit in his or her name. Pretexters use a variety of techniques, but they are all simple variations of social-engineering techniques. A pretexter might, for example, spoof your caller ID and call your cell phone provider to ask for a reprint of a bill. Or a pretexter might call your bank to obtain a replacement for a lost checkbook, or even contact your credit card provider. In most cases, pretexting is illegal, and there are laws against pretending to be someone else to gain personal information. If you have never seen how easily someone can launch this type of attack, check out www.youtube.com/watch?v=PWVN3Rq4gzw.
Note
Spoofing can be used with domain names, email addresses, media access control (MAC) addresses, and even IP addresses.
Dumpster diving is another attack that requires no technical skill. Dumpster divers simply dig through the trash, looking for key pieces of information. Sensitive information should be shredded, but this doesn’t always happen. Sticky notes and other small pieces of trash can provide critical pieces of information to those seeking to gain sensitive information. As long as no trespassing takes place, dumpster diving is usually not illegal.
Sniffing
A network sniffer, such as Wireshark, is a software tool that captures and displays network traffic. By using a sniffer, an attacker can potentially capture all the information transported by the network. Many sniffers can reassemble packets and create entire messages, including user IDs and passwords. This vulnerability is particularly acute in environments where network connections are easily accessible to outsiders. For example, an attacker could put a laptop or a portable computer in your wiring closet and attach it to your network. Figure 9-6 shows Wireshark running.
Man-in-the-Middle Attacks and Hijacking
A technique attackers can use that is similar to sniffing is hijacking. Hijacking occurs when an attacker pretends to be a trusted party. For example, with session hijacking, a legitimate user logs on to a service or an application and then an attacker takes control of the session. The attacker gets an authenticated connection and the ability to masquerade as the victim.
A man-in-the-middle (MITM) attack occurs when an attacker secretly relays and possibly alters the communication between two parties, as shown in Figure 9-7. Packet replay is a similar technique that an attacker can use to gain access. For example, the attacker might sniff an authentication session on the network and replay it later to try to gain unauthorized access.
Denial of Service
A denial of service (DoS) attack does not give an attacker access; instead, it blocks legitimate users from using resources they have access to. While DoS attacks are not as prominent as ransomware, point-of-sale attacks, or retail data breaches, they can affect a large number of users. What keeps these attacks popular is that they are easy to launch and difficult to defend against. DoS attacks target availability, and they provide an easy way for an attacker to disrupt services. Denial-of-service attacks consume resources or flood the network to the point that legitimate access is not possible.
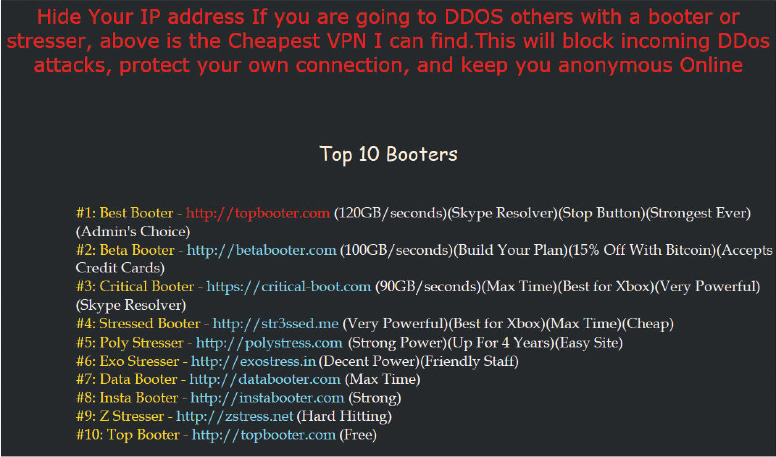
Distributed DoS (DDoS) attacks work in much the same manner, except that they are launched from many more devices and add a layer between the attacker and the victim. Anyone can launch a DDoS attack against your company. Figure 9-8 shows the top 10 DDoS attack sites.
Some DoS/DDoS attack tools and techniques include the following:
![]() Ping of death: A DoS attack that employs an oversized IP packet.
Ping of death: A DoS attack that employs an oversized IP packet.
![]() Smurf: A DoS attack that involves sending a message to the broadcast address of a subnet or network so that every node on the network produces one or more response packets.
Smurf: A DoS attack that involves sending a message to the broadcast address of a subnet or network so that every node on the network produces one or more response packets.
![]() Syn flood: A DoS attack that manipulates the standard three-way handshake used by TCP.
Syn flood: A DoS attack that manipulates the standard three-way handshake used by TCP.
![]() hping: A tool that is not strictly a DDoS tool but provides a range of functionality by sending large volumes of TCP traffic to a target while spoofing the source IP addresses, making it appear to be random or even to originate from a specific, user-defined source.
hping: A tool that is not strictly a DDoS tool but provides a range of functionality by sending large volumes of TCP traffic to a target while spoofing the source IP addresses, making it appear to be random or even to originate from a specific, user-defined source.
![]() Slowloris: A tool that causes a DoS condition for a server by using a very slow HTTP request. Sending HTTP headers to the target site in tiny chunks as slowly as possible forces the server to continue to wait for the headers to arrive.
Slowloris: A tool that causes a DoS condition for a server by using a very slow HTTP request. Sending HTTP headers to the target site in tiny chunks as slowly as possible forces the server to continue to wait for the headers to arrive.
![]() R U Dead Yet? (RUDY): A DDoS tool that knocks systems offline by using long-form field HTTP POST submissions.
R U Dead Yet? (RUDY): A DDoS tool that knocks systems offline by using long-form field HTTP POST submissions.
![]() Low Orbit Ion Cannon (LOIC): An open source network stress testing and DoS attack application that is written in C#.
Low Orbit Ion Cannon (LOIC): An open source network stress testing and DoS attack application that is written in C#.
![]() High Orbit Ion Cannon (HOIC): An open source network stress testing and DoS attack tool capable of attacking as many as 256 URLs at the same time.
High Orbit Ion Cannon (HOIC): An open source network stress testing and DoS attack tool capable of attacking as many as 256 URLs at the same time.
Botnets
Botnets have in many ways replaced DoS attack tools as they are much more functional. Botnets can be used for DoS but also other activities, such as pump-and-dump financial schemes, extortion, fake/counterfeit software distribution, ransomware, and other malicious activities.
A botnet is a network of compromised computers that can be accessed remotely and used for malicious activity. An attacker infects scores of computers that then just wait until commanded to action by the attacker. These compromised machines can communicate with each other or with a bot herder and can act in a coordinated way, based on commands (see Figure 9-9).
Figure 9-9 Botnet Communication
The hackers who create botnets must make sure that the bots can receive their instructions. If the communication channels can be shut down, the botnet can be disabled. Therefore, actively controlling botnets is of critical importance, as is protecting a botnet from attempts to hijack or shut it down. Botnets generally make use of one of three types of command and control (C&C) structures:
![]() Centralized C&C: This approach relies on a single centralized resource to communicate with all infected systems. Each infected system is issued new instructions directly from the central control point.
Centralized C&C: This approach relies on a single centralized resource to communicate with all infected systems. Each infected system is issued new instructions directly from the central control point.
![]() Decentralized C&C: The advantage of this approach is that it overcomes the weakness of centralized C&C: its single point of failure. With a decentralized design, each bot acts as both a client and a server. This lack of centralized C&C and the many-to-many communication makes this form of botnet much more difficult to shut down.
Decentralized C&C: The advantage of this approach is that it overcomes the weakness of centralized C&C: its single point of failure. With a decentralized design, each bot acts as both a client and a server. This lack of centralized C&C and the many-to-many communication makes this form of botnet much more difficult to shut down.
![]() Hybrid botnets: Hybrid botnets use a mix of centralized C&C and decentralized C&C.
Hybrid botnets: Hybrid botnets use a mix of centralized C&C and decentralized C&C.
Malware
Malware comes in a variety of forms. Sometimes malware targets unknown vulnerabilities. These are known as zero-day attacks because they are not known by anti-malware vendors and so the software cannot defend against them. There is a growing market in zero-day exploits, and entire websites have been set up to market and sell them to the highest bidder.
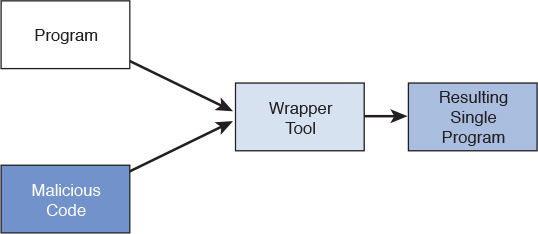
A very common type of malware is viruses. Viruses require some type of human interaction. One early type of virus was the macro virus, which targets Office documents. Some viruses have the ability to mutate and are known as polymorphic. Worms require no interaction and can self-replicate. Trojans are yet another type of malware. Think of a Trojan as something you think you want but really do not. A Trojan masks itself as a legitimate program to a user, such as a .pdf, .ppt, .docx, or other file type. Hackers use droppers or wrappers to combine malware with a legitimate program. An example of a wrapper is shown in Figure 9-10. When a user clicks on or runs a program that has been wrapped, malicious code may be installed.
Wireless and Bluetooth
An organization’s electronic equipment (wireless keyboards, mouse devices, monitors, and so on) transmits a wide range of electronic signals. One such technology is Bluetooth, which is designed as a short-range wireless system used in a personal area network (PAN), or a network of devices close to a single individual. Bluetooth was originally designed to be broadcast about 3 meters. However, attackers can launch attacks from much greater distances if they use long-range antennas.
When Bluetooth devices are first configured, they are placed in Discovery mode so others can identify them. While in Discovery mode, a Bluetooth device broadcasts its physical address and allows other devices to see it and potentially connect. Discovery mode is required for initial paring. During this time, attackers can attempt to pair to a device to gain access. Whenever possible, a device should have Discovery mode turned off.
Note
Attacks are much easier when Bluetooth devices remain in Discovery mode.
With the right software, an attacker can then launch the following types of attacks:
![]() Bluejacking: This Bluetooth attack is launched by sending unsolicited messages to nearby Bluetooth devices.
Bluejacking: This Bluetooth attack is launched by sending unsolicited messages to nearby Bluetooth devices.
![]() Bluesnarfing: This attack is any unauthorized access to or theft of information from a Bluetooth connection. Attackers might target information such as email, contact lists, calendars, and text messages.
Bluesnarfing: This attack is any unauthorized access to or theft of information from a Bluetooth connection. Attackers might target information such as email, contact lists, calendars, and text messages.
![]() Bluebugging: This type of attack allows an attacker to take over a mobile phone. Attackers can potentially eavesdrop on phone conversations, carry out call forwarding, send messages, and more.
Bluebugging: This type of attack allows an attacker to take over a mobile phone. Attackers can potentially eavesdrop on phone conversations, carry out call forwarding, send messages, and more.
Figure 9-11 shows an example of Ubertooth, a Bluetooth hacking tool.
802.11 wireless connections are also an area of concern. While wireless access points may support one of three wireless encryption standards—Wired Equivalent Privacy (WEP), Wi-Fi Protected Access (WPA), or WPA2—this does not mean encryption will always be used. Many access points have no encryption at all. You can look for unsecured access points by performing a site survey or by using one of multiple websites that list access points and the types of encryption used. Figure 9-12 shows the Wigle website and a map of some identified wireless points. The act of looking for wireless access points is known as war driving, and sites such as Wigle depend on others to war drive and upload their data to the Wigle database.
While open access points may have few controls in place to prevent someone from gaining access, access points that use WEP are not much better.
An IV is simply a random number that’s used along with a secret key for data encryption. If these random numbers are pulled from a small range of numbers or are not truly random, they repeat over time; it’s possible that these values can be easily recovered, guesses, or calculated. WEP suffers from a flaw in the implementation of the RC4 cipher used. The 802.11 standard does not specify how to generate IVs, and cracking WEP typically doesn’t require more than a few minutes’ work.
WPA, which was designed as a stopgap measure, uses the Temporal Key Integrity Protocol (TKIP) and a 64-bit message integrity check (MIC) to improve security. While more secure than WEP, WPA can be targeted for attack with tools such as Aircrack, which is one of the most popular tools for targeting WEP and WPA.
WPA2 is the newest wireless standard and uses AES to protect data. An auditor should ensure that an organization’s wireless technology uses layers of defense—such as WPA2, MAC filtering, wireless IDS, non-broadcast of the service set ID (SSID), and other security measures—to build defense-in-depth.
Tip
CISA exam candidates should understand that wireless access points should be secured to the highest level of encryption possible.
SQL Injection
What if a database is the target of an attack? If a database does not have the proper security controls in place, an attacker can create queries against the database to get it to disclose unauthorized information. This type of attack is generally known as SQL injection. A SQL injection attack is carried out when an attacker uses a series of malicious SQL queries to directly manipulate the SQL database. SQL injection is not a database issue as much as an application issue. It occurs because of poor input validation. It’s sad but true that there are hundreds if not thousands of websites that are vulnerable to SQL injection and have not been secured.
SQL injection attacks can be launched from the any query field on a webpage, from within application fields, or through queries and searches. There are Internet sites that list websites vulnerable to SQL injection. One example is shown in Figure 9-13.
Once a SQL injection attack is launched, the attacker typically seeks to enumerate the database and then extract password hashes or steal credit card or other personally identifiable information (PII). Malformed input may cause the database to become unstable or leak information. Attackers use logic such as a single quote (‘) to test a database for vulnerabilities. Responses such as the one shown in the following code give feedback the attackers need that the database is vulnerable to attack:
Microsoft OLE DB Provider for ODBC Drivers error '80040e14'
[Microsoft][ODBC SQL Server Driver][SQL Server]Syntax error converting
the nvarchar value 'sa_login' to a column of data
type int. /index.asp, line 5
Buffer Overflow
A buffer overflow occurs when a software application somehow writes data beyond the allocated end of a buffer in memory. Buffer overflows are commonly found in programming languages that don’t do good bounds testing. If an attacker can launch a buffer overflow attack, there is a possibility the attacker will be able to load malicious code and force the application to run it. This malicious code could do any number of things, such as open a command prompt or pass shell access back to the attacker.
The best defense against buffer overflow attacks is to put controls in code when it is designed. Building secure code is less costly than attempting to secure an application after it has been developed and released. A range of tools can be used to analyze code. One example is Microsoft Attack Surface Analyzer, which is described in Figure 9-14.
Good coding is what is needed to prevent these types of vulnerabilities. Auditors should be included in the design and build process to ensure that the proper testing of controls will be included in the build process. For precompiled applications, and situations where the source code is not available, another approach is black-box testing or fuzzing. An auditor can use fuzzing tools to enter random values into input fields to see if an application will crash or hang, as shown in Figure 9-15.
Tip
CISA exam candidates should understand that fuzzing is an automated software testing technique that involves providing invalid, unexpected, or random data as inputs to a computer program to see if the program will crash or hang.
XSS and XSRF
Cross-site scripting (XSS) attacks are injection attacks targeted against dynamically generated web pages in which malicious scripts are injected into the otherwise benign and trusted web content. XSS allows an attacker to forcibly load any website when unsuspecting users visit malicious web pages. The attacker can then steal usernames and passwords typed into HTML forms or cookies—or compromise any confidential information on the screen. Situational awareness requires users to use caution when clicking on links in emails or clicking on links at suspicious sites.
Cross-site request forgery (XSRF) is a client-side attack that occurs when a malicious website tricks users into unknowingly loading a URL from a site at which they’re already authenticated, thus making use of their authenticated status.
Logic Bombs, Rounding Down, and Asynchronous Attacks
Imagine that a company’s programmer is able to access and change applications at will. What if this person could change the company’s payroll application? The programmer might not destroy the code but might add a few lines to the code to have it checked for his employee number each week before printing checks. If his employee ID is verified, the program prints checks as normal. If his employee ID is not found, each check is printed but is made out to a random dollar amount. This is a logic bomb, designed to detonate sometime after the perpetrator leaves. A logic bomb can cause a great deal of damage: Because it is buried deeply in the code, it is unlikely to be detected before it becomes active.
Similar to a logic bomb is a trap door, a shortcut created by a programmer during development. It acts as a hidden access point in the software or application and can aid in the testing process. When testing is completed, the trap door should be removed. A trap door that isn’t removed can act as a hidden shortcut for attackers.
An asynchronous attack is a complex attack that targets timing. These attacks are also known as time-of-check, time-of-use (TOCTOU) attacks, or race conditions, because the attacker is racing to make a change to the object after it has been changed and just before it’s used by the system. For example, if a program creates a data file to hold the amount a customer owes, and the attacker can replace the value before the program reads it, the attacker can successfully manipulate the program. An IS auditor is likely to need the help of a programmer or an IT specialist to evaluate this complex attack.
Some attacks are launched for financial reasons. For example, rounding-down attack involves skimming off small amounts of money by rounding down the last few digits. For example, the amount $5,239,812.33 might be rounded down to $5,239,812.30. Similar to this attack is the salami technique, which slices off small amounts of money so that the last few digits are truncated. For example, $5,239,812.33 might become $5,239,812.00. Both the rounding-down technique and the salami technique work under the assumption that small amounts will not be missed; over a period of time, this can add up to big profits for the attacker. This type of attack can be seen in movies such as Superman III and Office Space.
Integer Overflow
Integer overflow occurs when a program or an application attempts to store a number in a variable that is larger than that variable’s type can handle. Consider the situation where an allocated buffer can hold a value up to 65,535. If the maximum size is exceeded, the value essentially wraps around to 0. The result can cause some unusual behavior if the resulting value is used in a computation. Years ago this type of attack could be exploited in arcade games such as Pac-Man. Pac-Man used an 8-bit counter, and players who were good enough to complete all 255 levels could roll over the counter and crash the game.
Password Attacks
Common attacks against access control are dictionary attacks, hybrid attacks, brute-force attacks, and rainbow tables. Unfortunately, many passwords are based on weak dictionary words. Dictionary attacks exploit this fact and use a predefined dictionary to look for a match between a hashed password and a hashed value in the dictionary. Many dictionary files are available online. Although passwords are commonly stored in a hashed format, password-cracking programs use a technique called comparative analysis. Each potential password found in a dictionary list is encrypted and compared to the encrypted password. If a match is obtained, the password has been discovered. If it’s not obtained, the program continues on to the next word, computes its hashed value, and compares it to the hashed password.
Another type of password cracking method is the hybrid attack, used to target individuals who use variations of a common word. For example, consider the word password. Hybrid password cracking would process the word as Password, password, PASSWORD, PassWord, PaSSword, and so on. Hybrid password cracking also attempts to add common prefixes, suffixes, and extended characters to try to crack the password. For example, the word password would also be tried as 123password, abcpassword, drowssap, p@ssword, pa55w0rd, and so on. These various attempts increase the odds of successfully cracking an ordinary word. An example of a password cracking tool is John the Ripper (see www.openwall.com/john/).
Yet another type of password attack is a brute-force attack, which attempts to use every possible combination of letters, numbers, and characters. Depending on the length and complexity of the original password, this attack can take hours, days, months, or years.
Finally, a rainbow table is a precomputed table for finding password hashes. Tables are usually used in recovering a plaintext password up to a certain length and consisting of a limited set of characters. Instead of computing each hash one at a time and then comparing, a rainbow table is filled with precomputed hashed passwords. This form of time–memory trade-off requires that a rainbow table be generated for all possibilities within a given range, such as 1- to 14-character alphanumeric passwords. Then, if any password is a match that’s 14 characters or less, it is found in just a few seconds. Rainbow tables are incorporated into many password cracking programs.
An advancement on rainbow tables is the thunder table. Imagine that you have a 14-character rainbow table and use it against five password hashes. If it is successful against four of the passwords but not the fifth one, the historic approach would have been to brute-force the remaining one. As we have discussed, brute-force attacks take time. Thunder tables can be used to reduce that amount of time. Thunder tables contain additional data that lists all attempts for which rainbow tables failed. Therefore, a thunder table knows which brute-force values to check and which ones it should not spend time trying. Figure 9-16 shows an example of an online password cracking program.
Prevention and Detection Tools and Techniques
Part of the internal audit function is a review of prevention and detection controls to ensure normal and efficient functioning of the enterprise’s activities. These controls include those that are responsible for logging, monitoring, and real-time analysis of security alerts. Some of these controls can be thought of as administrative. For example, an auditor should verify that each individual’s responsibility is clearly defined. Policies should require that employees be trained and aware of proper procedure. Users need to know why logging off before leaving for the day is a requirement, how social engineers con employees out of information or access, and how to practice safe computing. The end user also should be made aware of keystroke logging, email scanning, and Internet acceptable use policies (AUPs). Employees should know they will be held accountable. Auditing is a good way to determine whether repetitive mistakes are being made or if someone is trying to gain unauthorized access. As a detective control, auditing provides a means of uncovering suspicious activity.
Audit and Log Review
From a control standpoint, an IS auditor needs to examine log-retention policies to make sure they comply with local, state, or federal laws. If possible, audit records should be transferred to a centralized location. This makes auditing and analysis easier for the appropriate administrator, and it makes log tampering harder for the malicious user because logs are not kept on the local system. Strong access controls to the logs, encryption, and integrity checks should also be considered. The idea behind integrity checks is to have a means of detecting log tampering. One good approach is for an auditor to periodically check the logs to make sure no one has attempted to exceed access privileges or gain access during unusual hours. Any control or procedure that bypasses normal security measures should be examined closely. For example, bypass label processing can be used to bypass the normal process of reading a file security label. Because most access controls are based on security labels, this means normal security control could be bypassed.
Manual analysis of logs is time-consuming and tedious. It’s best to use automated tools for log analysis. Although the CISA exam does not expect you to know the names of specific tools, you do need to know the types of tools that can be used when working with log files. Attack-detection tools are audit tools that look for known attack signatures. For example, Bob normally is able to log in on the first attempt, but now he has attempted to log in 5,000 times. This type of activity should be flagged for analysis.
Trend- or variance-detection tools are similar to attack-detecting tools except that they scan for deviations from normal trends. For example, there could be a problem if Bob normally logs in at 9 a.m. but now is attempting to log in at 4 a.m. Finally, audit-reduction tools reduce the volume of information to be examined to ease manual analysis.
The bottom line on auditing logs is that you need to strike a balance because a system that produces auditing information takes a hit in performance as the number of auditable events increases. One widely used tool is Syslog, a standard Linux service that uses UDP to send log messages within a network. Syslog provides a wide range of system info, which makes it an important part of network monitoring.
One big question is how much should be logged? Reducing auditable events raises performance but reduces the amount of usable information. Even if performance were not a factor and you could audit every conceivable event, there would still be a huge burden on the analysis side. It would be impossible to review so much information. This means that collecting the information in the first place would be of little or no value. The art of auditing is best accomplished by balancing a required number of metrics to log and measure that against the time and effort required to periodically review the logged data. This entire process should be documented and policy driven.
NetFlow is another tool that can be used to collect and analyze network traffic statistics. It uses multiple sources of internal and external information and processes it in real time to detect threats. The key is to use existing network infrastructure that’s already inline and available. Two other technologies an auditor should understand are network access control (NAC) and security information and event management (SIEM). NAC is a technology for unifying endpoint security technology that can be used for network security enforcement. SIEM is used for real-time analysis of security alerts generated by network hardware and applications.
Security Testing Techniques
While IT auditing is generally concerned with reviewing policies and procedures that have been implemented to protect confidentiality, integrity, and availability of data, there is also a need to have an understanding of other types of security testing techniques. An organization’s policies and procedures should set the tone for good security practices and should assign responsibility for a secure infrastructure. Policies on logical access control should be designed so that least privilege is established and users are granted access to only the minimum level of access needed to perform their assigned tasks. Two techniques for this are vulnerability scanning and penetration testing.
Vulnerability Scanning
Vulnerability scanning typically involves using software tools to scan a network, devices, and applications for vulnerabilities. Some of these tools are commercial and require an annual subscription; others are open source and don’t cost anything to acquire initially. These tools can be run against a single computer or against a range of network addresses. Nessus is an example of a well-known vulnerability scanning tool. Nessus is now both an open source and a commercial tool.
Vulnerability scanning tools can be used to run regularly scheduled scans or can be used if a target system or network has been patched or changed due to upgrades. Periodic network assessments should review a list of best practices to make sure security best practices are being followed. Table 9-4 presents a basic checklist of these items.
Table 9-4 Network Assessment Checklist
Item |
Finding |
Strong authentication used? |
Yes/No |
Intrusion detection in place and tuned? |
Yes/No |
Firewalls deployed and properly configured? |
Yes/No |
Encryption used? |
Yes/No |
Antivirus present and updated? |
Yes/No |
Patch management used? |
Yes/No |
Application controls in place? |
Yes/No |
Penetration Testing
Penetration testing is more in-depth than vulnerability scanning. Penetration testing is adversarial in nature. It examines what an attacker can see, what the attacker can access, how that information can be leveraged, and whether anyone would notice. Penetration testing is the process of evaluating an organization’s security measures by using the same tools and techniques a criminal hacker (cracker) would use. The big difference is that penetration testing is done with the enterprise’s permission. This type of security evaluation is also known as a pen test, ethical hacking, or a red team activity. The organization’s security team might or might not be made aware of a pending test. In a blind test, the pen test team has no knowledge of the internal network. A double-blind test is similar, but with the added requirement that the internal security employees have no knowledge of the test.
During a pen test, operational control of computers might be the target, or the goal might simply be to plant a flag or download usernames and passwords to prove that vulnerabilities exist. A pen test can also be conducted internally, examining the security of the internal or external network; these attacks seek to gain control from outside the organization’s security perimeter. After the test methodology is determined, the pen test team is responsible for determining the weaknesses; technical, administrative, or physical flaws; and vulnerabilities. Recommendations for addressing security shortcomings should be included. Test results should be delivered in a comprehensive report to management.
Several good documents detail ways to conduct penetration testing. The Open Source Security Testing Methodology Manual (OSSTMM) is one. It is a peer-reviewed methodology for performing security tests, and you can find it at www.osstmm.org. Another is NIST-800-42. Table 9-5 lists the different stages of penetration testing, per NIST.
Table 9-5 The NIST Four-Stage Pen Test Methodology
Stage |
Description |
Planning |
At this stage, a signed letter of authorization is obtained. The rules of engagement are established here. The team must have goals, know the time frame, and know the limits and boundaries. |
Discovery |
This stage is divided into two distinct phases: Passive: This phase is concerned with information gathered in a very covert manner. Examples of passive information gathering include surfing the organization’s website to mine valuable information and reviewing job openings to gain a better understanding of the technologies and equipment used by the organization. Active: This phase of the test is split between network scanning and host scanning. As individual networks are enumerated, they are further probed to discover all hosts, determine their open ports, and attempt to pinpoint the OS. Nmap is a popular scanning program. |
Attack |
At this stage, the pen testers attempt to gain access, escalate their privilege, browse the system, and expand their influence. |
Reporting |
In this final stage, documentation is used to compile the final report. This report serves as the basis for corrective action, which can range from nothing more than enforcing existing policies to closing unneeded ports and adding patches and service packs. |
NIST 800-115 is another document to review. This is just one of several documents available to help guide you through an assessment. Find out more at http://csrc.nist.gov/publications/PubsSPs.html.
Note
To learn more about ethical hacking and pen testing, consider reading Certified Ethical Hacker (CEH) Version 9 Cert Guide by one of the authors of this book, Michael Gregg.
Throughout the pen test process, the security team should be in close contact with management to keep them abreast of any findings. The team should never exceed its level of authorization or attempt any type of test that has not been previously approved in writing. There shouldn’t be any big surprises at the conclusion of the pen tests. Leading a pen test team is a huge undertaking that requires managerial, technical, and project-management skills.
Note
During a pen test, team members try to exploit potential vulnerabilities. If vulnerabilities are discovered that cannot be removed, the team should look for ways to implement compensating controls.
Problem and Incident Management Practices
If one thing is a given in life, it’s that things will go wrong. Problem and incident management procedures can be thought of as pre-disaster planning.
Tracking Change
One way to prevent problems before they occur is to have a good change management program. Change management is a structured process whose purpose is to control modifications made to systems and programs. Without effective change-management procedures, unauthorized changes to software could endanger the security of an organization. During an audit, controls to prevent unauthorized changes should be verified. Some common change controls include the following:
![]() Separation of duties: Development, administration, and operation duties should be performed by different individuals.
Separation of duties: Development, administration, and operation duties should be performed by different individuals.
![]() Controlling the development environment: Software developers should have access restricted to a controlled area used only for code development.
Controlling the development environment: Software developers should have access restricted to a controlled area used only for code development.
![]() Restricting access: Access to source code should be restricted to only individuals who have a valid need for it.
Restricting access: Access to source code should be restricted to only individuals who have a valid need for it.
Fraud Risk Factors
Fraud risk factors are events or conditions that indicate an incentive or pressure to commit fraud or provide an opportunity to commit fraud. Fraud can be caused by insiders or outsiders. When there is no internal audit function, it is unlikely that incorrect or inappropriate transactions will be spotted or corrected.
Insiders
Errors can result from honest mistakes or intentional fraud. One of the basic tests to help identify or eliminate a suspect is means, opportunity, and motive (MOM). Also known as the crime triangle, MOM demonstrates why insiders pose a greater threat to security than outsiders. Insiders possess the means and opportunity to launch an attack, whereas outsiders might have only a motive.
Outsiders
The percentage of insider threats compared to outsider threats is the subject of ongoing debate. Regardless of who is responsible for an attack, admitting to falling prey to computer crime can have a negative impact on an organization’s image, can make the company appear vulnerable, or can even motivate additional attacks. However, data breaches often must be reported. Some laws and regulations require reporting, including PCI-DSS, HIPAA, SOX, and the EU Privacy Shield. Some of the individuals responsible for computer crimes include the following:
![]() Hackers: Hackers typically try to overcome the technical and physical barriers that restrict their access to information and systems. They may be driven by many factors, such as money, prestige, thrill, or activism.
Hackers: Hackers typically try to overcome the technical and physical barriers that restrict their access to information and systems. They may be driven by many factors, such as money, prestige, thrill, or activism.
![]() Script kiddies: A script kiddie is a young or inexperienced attacker who uses only well-known vulnerabilities and scripts to launch attacks. Tool sets such as Kali Linux make it easy for anyone to hack. Script kiddies do not have any serious programming skills or an in-depth understanding of networks or operating systems.
Script kiddies: A script kiddie is a young or inexperienced attacker who uses only well-known vulnerabilities and scripts to launch attacks. Tool sets such as Kali Linux make it easy for anyone to hack. Script kiddies do not have any serious programming skills or an in-depth understanding of networks or operating systems.
![]() Criminal hackers: These hackers seek to cash in, do damage, or perform other illegal activities. They may be technically proficient or may just download a crimeware kit that’s readily available on the dark web.
Criminal hackers: These hackers seek to cash in, do damage, or perform other illegal activities. They may be technically proficient or may just download a crimeware kit that’s readily available on the dark web.
![]() Phreakers: These hackers of yesterday are interested in breaking into telecommunication and PBX systems. In the past, their motive might have been to exploit systems for free phone calls, for illegal use, or to provide telecommunication access to others for a profit. Phreakers can access telecommunication equipment, reprogram it, and spoof caller ID or send fake text messages, which is known as smishing.
Phreakers: These hackers of yesterday are interested in breaking into telecommunication and PBX systems. In the past, their motive might have been to exploit systems for free phone calls, for illegal use, or to provide telecommunication access to others for a profit. Phreakers can access telecommunication equipment, reprogram it, and spoof caller ID or send fake text messages, which is known as smishing.
![]() Terrorists: These individuals might be funded by other countries, covert organizations, or industries. Their goal is to conduct acts of terror, and their activities can range from using social media to gain followers, launch a DoS attack, deface a website, or potentially even compromise critical infrastructure, such as nuclear power plants, electric plants, water plants, gas refineries, and so on. Figure 9-17 shows a Shodan search for automated gas pump controls. Shodan allows anyone to search for industrial control systems or other types of critical infrastructure.
Terrorists: These individuals might be funded by other countries, covert organizations, or industries. Their goal is to conduct acts of terror, and their activities can range from using social media to gain followers, launch a DoS attack, deface a website, or potentially even compromise critical infrastructure, such as nuclear power plants, electric plants, water plants, gas refineries, and so on. Figure 9-17 shows a Shodan search for automated gas pump controls. Shodan allows anyone to search for industrial control systems or other types of critical infrastructure.
Incident Response
To be able to respond to security incidents, organizations need to have incident response and incident handling policies in place. These policies should dictate how the organization handles various types of incidents. Most companies set up a Computer Security Incident Response Team (CSIRT). A very early example of incident response occurred, 1988 in response to the Morris worm, which knocked out more than 10 percent of the systems connected to the Internet. Having an incident response team in place, along with the policies needed to function, can give an organization an effective and efficient means of reducing the potential impact of these situations. These procedures should also give management sufficient information to decide on an appropriate course of action. By having these procedures in place, an organization can maintain or restore business continuity, defend against future attacks, and deter attacks by prosecuting violators.
Incident response team members need diverse skill sets. Members should come from various departments throughout the organization, such as the following:
![]() Information security
Information security
![]() Legal
Legal
![]() Human resources
Human resources
![]() Public relations
Public relations
![]() Physical security
Physical security
![]() Network and system administration
Network and system administration
![]() IS auditing
IS auditing
Being a diverse group better prepares an incident response team to deal with the many types of incidents that can occur. Per ISACA, auditors should ensure that an organization has documented incident response plans in place to deal with these common types of security incidents:
![]() Malware infections
Malware infections
![]() Trojans
Trojans
![]() Website attacks
Website attacks
![]() Unauthorized access
Unauthorized access
![]() Hardware theft and physical intrusion
Hardware theft and physical intrusion
![]() Unauthorized software
Unauthorized software
![]() Denial of service
Denial of service
![]() Slander and media misinformation
Slander and media misinformation
![]() Proper forensic response and investigation practices
Proper forensic response and investigation practices
Documentation to address common types of potential incidents is critical because investigating computer crime is complex and involved. Missteps can render evidence useless and unusable in a court of law. Team members must therefore be knowledgeable about the proper procedures and have training on how to secure and isolate the scene to prevent contamination. That is the role of computer forensics.
Whatever the motive or reason, the response should always be the same. Security breaches should be investigated in a structured, methodical manner. Most companies would not operate a business without training their employees how to respond to fires, but many companies do not build good incident response and investigation procedures.
Note
Honeypots can be used to learn more about what hackers do during an attack. A honeypot is a fake system used to jail an attacker and learn more about his or her activities so you are better prepared during a real attack.
The first step is the analysis of the event. An event is a noticeable occurrence. For example, say that an IDS alert was tripped. This requires an investigation because it must be determined whether the event was an incident. An incident is an adverse event or series of events that violates law, policy, or procedure.
Emergency Incident Response Team
The emergency incident response team, which investigates incidents, needs a variety of skills, including the following:
![]() Recognition skills and abilities
Recognition skills and abilities
![]() Technical skills and abilities
Technical skills and abilities
![]() Investigative and response skills
Investigative and response skills
The individuals in charge of an incident must be able to recognize that something has happened. For example, this could be that an IDS has tripped. Recognition is not enough; those responsible must also have the ability to look at logs and event records and perform incident analysis. Skills are also needed to properly investigate an incident.
There should be a variety of individuals on an incident response team. For example, if an employee is thought to have been hacking, the manager may want to fire the person but will most likely have to consult the legal department and human resources. This means the team needs to include employees from many different parts of the company. While all members of the team may not be involved in every single incident, there will be a need to have contacts in many different departments, and these individuals should understand that they may be called on as needed. This team also must know how to contain damage and determine how to proceed.
Incident Response Process
Incident response requires organizations to define the specific steps that will be carried out when an incident takes place. Good incident response procedures give the organization an effective and efficient means of dealing with an incident in a manner that reduces the potential impact. These procedures should also provide management with sufficient information to decide on an appropriate course of action. By having these procedures in place, the organization can maintain or restore business continuity, defend against future attacks, and deter attacks by prosecuting violators.
The primary goal of incident response is to contain the damage, find out what happened, and prevent it from reoccurring. Crime can be greatly reduced by eliminating any one of the three sides of the crime triangle commonly referred to as means opportunity, and motive. (see Figure 9-18).
The steps to emergency response are many and follow a structured approach such as the format shown here:
Step 1. Planning and preparation: The organization must establish policies and procedures to address potential security incidents.
Step 2. Identification and evaluation: Automated systems should be used to determine whether an event occurred. Was an event real, not a false positive? The tools used for identification include IDSs, IPSs, firewalls, audits, logging, and observation.
Step 3. Containment and mitigation: Preplanning, training, and the use of predeveloped procedures are key to this step. The incident response plan should dictate what action is required. The incident response team must have had the required level of training to properly handle response.
Step 4. Eradication and recovery: Containing the problem is not enough; it must be removed, and steps must be taken to return to normal business processes.
Step 5. Investigate and closure: What happened? When the investigation is complete, a report, either formal or informal, must be prepared. This is needed to evaluate any needed changes to the IR policies.
Step 6. Lessons learned: At this final step, all those involved must review what happened and why. Most importantly, necessary changes must be put in place to prevent future problems. Learning from what happened will help prevent it from happening again.
Note
Management needs to make a decision about whether law enforcement should be called in during a security breach. There are reasons both for and against calling in law enforcement.
Incident Response and Results
Incident response procedures must be of such detail that specific types of incidents are documented and advice given about what the proper response would be. Documentation to address each of these potential incidents is critical because investigating computer crime is complex and involved. Missteps can render evidence useless and unusable in a court of law. This means that team members must be knowledgeable about the proper procedures and trained on how to secure and isolate the scene to prevent contamination. Table 9-6 outlines some sample response strategies.
Table 9-6 Sample Escalation and Response Procedures
Incident |
Response Procedure |
Possible data theft |
Contact legal department, make forensic image, secure evidence |
External hacker attack |
Capture logs, monitor activities, gather evidence, contact management |
Unauthorized use of computer resources |
Gather evidence, make forensic image, analyze data, review corporate policy |
In the end, incident response is about learning. Results of your findings should be fed back into the system to make changes or improve the environment so that the same incident isn’t repeated. Tasks you might end up doing as a result of an attack include the following:
![]() Figuring out how the attack occurred and looking for ways to prevent it from happening again
Figuring out how the attack occurred and looking for ways to prevent it from happening again
![]() Upgrading tools or software in response to finding out what the team lacked that prevented effective response to the incident
Upgrading tools or software in response to finding out what the team lacked that prevented effective response to the incident
![]() Finding things that went wrong and making changes to the incident response plan to improve operations during the next incident
Finding things that went wrong and making changes to the incident response plan to improve operations during the next incident
Although no one ever wants to end up in court or to take incident response to the next level, this is not always how it works out. All incident response must be handled meticulously so you can be prepared for whatever unfolds in an investigation. Sometimes the forensic skill level required mandates that the forensic analysis be handed off to a more skilled forensics lab. The next section discusses what happens in forensic labs.
Note
Ultimately, incident response is about learning. An incident response team needs to answer questions such as the following: What happened? How did it happen? Can we prevent it from happening again? How can we better prepare and respond for the next time? and What did we learn?
Forensic Investigation
Forensics and incident response are very closely related except that incident response is most closely associated with getting systems back up and running, while forensics is more closely associated with capturing information in such a way that it is acceptable. Computer forensics is the systematic step-by-step examination and analysis of data that is stored, retrieved, or processed on computer systems in a legal, approved way so that the evidence can be used in court, if needed. Computers are a part of just about all crimes today. Consider the following ways that computers may be involved in crimes:
![]() Computers used in a crime: Criminals may use computers as a tool much as they would use a crowbar or gun. For example, whereas in the past a criminal might have used the post office for extortion or fraud, he might now use a computer and email to achieve the same goal.
Computers used in a crime: Criminals may use computers as a tool much as they would use a crowbar or gun. For example, whereas in the past a criminal might have used the post office for extortion or fraud, he might now use a computer and email to achieve the same goal.
![]() Computers targeted as a crime: Crimes may be directed at computers. For example, LulzSec targeted MasterCard and Visa in 2010 with an extended DDoS attack.
Computers targeted as a crime: Crimes may be directed at computers. For example, LulzSec targeted MasterCard and Visa in 2010 with an extended DDoS attack.
![]() Computers are incidental in a crime: Sometimes a computer may aid a criminal in some way. For example, a criminal might keep a list of earnings from illegal gambling in an Excel spreadsheet instead of in a spiral notebook.
Computers are incidental in a crime: Sometimes a computer may aid a criminal in some way. For example, a criminal might keep a list of earnings from illegal gambling in an Excel spreadsheet instead of in a spiral notebook.
The chain of custody helps protect the integrity and reliability of evidence by providing an evidence log that shows every access to evidence, from collection to appearance in court. Forensic specialists must know how to record evidence at the scene by taking photographs, documenting their activities in an investigator’s notebook, interviewing suspects and witnesses, and knowing the proper procedures for collecting or seizing suspected systems or media. Doing all this correctly protects the chain of custody and the legality of the evidence.
Although law enforcement has been practicing forensics for a long time, the computer forensics field is relatively new to the corporate sector. Many IS auditors are not highly skilled in auditing this important field. An IS auditor must look carefully at the policies and procedures that detail forensic activities during an audit. Such policies might address computers, but other devices could be subject to forensic analysis, including cell phones, tablets, digital cameras, and USB thumb drives. Any existing policy must specify how evidence is to be handled. Mishandling can cost companies millions.
Forensics Steps
Because electronic information can be changed easily, a rigid methodology should be followed in handling electronic evidence:
1. Identify and acquire: The information must be identified and retrieved. Once in the custody of an investigator, a copy is usually created. Standard practice dictates making a bit-level copy, which is an exact duplicate of the original data. This enables the investigator to examine the copy while leaving the original copy intact.
2. Preserve and authenticate: Preservation is the act of maintaining the evidence in an unchanged state. This process requires that an investigator show that the data is unchanged and has not been tampered with. Authentication can be accomplished through the use of integrity checks and hashes such as MD5 and SHA.
3. Analyze, record, and present: An investigator must be careful to examine the data and ensure that any activity is documented. The investigator usually extracts evidence by examining drive slack space, file slack space, hidden files, swap data, Internet cache, and other locations, such as the recycle bin. Specialized tools are available for this activity. All the activities of an investigator must be recorded to ensure that the information will be usable in court, if needed.
Because the collection of electronic information is an important concern, the International Organization on Computer Evidence (IOCE) was appointed to develop international principles for procedures related to digital evidence. The goal was to develop standards and practices that many countries and states would recognize as legal to allow digital evidence collected by one state to be used in the courts of another state. (See https://archives.fbi.gov/archives/about-us/lab/forensic-science-communications/fsc/april2000/swgde.htm.)
![]() When dealing with digital evidence, all the generally accepted forensic and procedural principles must be applied.
When dealing with digital evidence, all the generally accepted forensic and procedural principles must be applied.
![]() Upon seizing digital evidence, actions taken should not change that evidence.
Upon seizing digital evidence, actions taken should not change that evidence.
![]() When it is necessary for a person to access original digital evidence, that person should be trained for the purpose.
When it is necessary for a person to access original digital evidence, that person should be trained for the purpose.
![]() All activity related to the seizure, access, storage, or transfer of digital evidence must be fully documented, preserved, and available for review.
All activity related to the seizure, access, storage, or transfer of digital evidence must be fully documented, preserved, and available for review.
![]() An individual is responsible for all actions taken with respect to digital evidence while the digital evidence is in his or her possession.
An individual is responsible for all actions taken with respect to digital evidence while the digital evidence is in his or her possession.
![]() Any agency responsible for seizing, accessing, storing, or transferring digital evidence is responsible for compliance with these principles.
Any agency responsible for seizing, accessing, storing, or transferring digital evidence is responsible for compliance with these principles.
Other Forensic Types
While the discussion so far has been about computer forensics, there are other forensics types, including network forensics and software forensics.
Network forensics involves the examination of network traffic and can be used to examine traffic as it passes over a network. Common tools used for network forensics include Wireshark, RSA NetWitness, and NetworkMiner. Regardless of what tool is used, the idea is to examine network traffic. Network forensics might be used to look for the exfiltration of data, track the activity of botnets, or detect employee Internet misuse.
Software forensics involves the examination of software. Maybe you have found what may be a malicious application or even a Trojan. Software forensics can help analyze the software’s purpose and actions. Software forensics can be carried out in one of two ways: dynamic or static forensic analysis.
With dynamic forensic analysis, the idea is to have the software run or execute in a controlled environment or sandbox to learn more about its activity. This is tricky because if the malware gets out of its sandbox, it might infect the entire organization. One approach is to use a virtualized system that has been isolated to perform this task. Another approach is to upload the suspected malware to an online sandbox. ThreatExpert, as shown in Figure 9-19, is an example of such a service.
Static forensic analysis overcomes the worry of allowing the potential malware to spread because the application is not executed. Static analysis involves disassembling or decompiling the application to examine the inner workings of the code. The creators of malware don’t make this activity easy, and there are many things they do, such as using encryption, to make analysis more difficult. An example of a static analysis tool is IDA Pro, shown in Figure 9-20.
Computer Crime Jurisdiction
The unpleasant truth is that even after conducting incident response and forensics, it is difficult to track and prosecute computer criminals. This is due in part to the international nature of computer crime. Unlike conventional crimes that occur in one location, computer crimes might originate in China, use a compromised computer network located in Singapore, and target a computer network located in the United States. Each country’s conflicting views on what constitutes cybercrime and how or even if the hackers should be punished can cause legal nightmares. It is hard to apply national borders to a medium such as the Internet that is essentially borderless.
If computer crime prosecution is possible, the presentation of evidence in court has to meet specific standards. Evidence is every type of proof legally presented at trial used to convince the judge and/or jury of alleged facts. Computer evidence is very volatile, and if it’s not handled correctly, it can be considered hearsay. This should drive home the fact that crimes involving computers must be handled in a very specific way so the chain of custody is protected.
Chapter Summary
This chapter discusses asset threat, response, and management. The threats to organizations can be physical, technical, or social. This chapter focuses on the technical and social threats. Organizations face a large number of potential technical threats, such as MITM, DoS, sniffing, XSS, and botnets. Social threats involve people and include phishing, smishing, and other forms of social engineering.
Dealing with these threats requires that policy be developed for incident response as well as forensic response, and these policies must be tested and verified before bad events occur so that when they do, steps such as chain of custody and proper handling of data are performed in such a way that any evidence will be admissible in court.
Exam Preparation Tasks
As mentioned in the section “How to Use This Book” in the Introduction, you have a couple choices for exam preparation: the exercises here; Chapter 10, “Final Preparation;” and the exam simulation questions on the book’s companion web page (www.informit.com/title/9780789758446).
Review All the Key Topics
Review the most important topics in this chapter, noted with the Key Topic icon in the outer margin of the page. Table 9-7 lists these key topics and the page number on which each is found.
Table 9-7 Key Topics in Chapter 9
Key Topic Element |
Description |
Page Number |
Best practices examples |
393 |
|
Common security controls for virtual systems |
395 |
|
Section |
Social engineering and nontechnical attacks |
399 |
Section |
Wireless and Bluetooth |
405 |
The NIST four-stage pen test methodology |
417 |
Complete Tables from Memory
Print a copy of Appendix B, “Memory Tables” (found on the companion web page), or at least the section for this chapter, and complete the tables from memory. Appendix C, “Memory Tables Answer Key,” also on the companion web page, includes completed tables you can use to check your work.
Define Key Terms
Define the following key terms from this chapter and check your answers against the glossary:
assessment
audit
backdoor
blackbox testing
botnet
buffer overflow
cracker
cross-site request forgery (XSRF)
ethical hacker
exploit
file infector
fuzzing
gray box testing
honeypot
Internet packet spoofing (IP spoofing)
MAC filtering
macro infector
macro virus
man-in-the-middle (MITM) attack
media access control (MAC)
multipartite virus
penetration test
phreaker
polymorphic virus
rounding down
service set ID (SSID)
smurf attack
social engineering
SYN flood attack
virus scanning
war driving
white box testing
Wi-Fi Protected Access (WPA)
Wired Equivalent Privacy (WEP)
zero-day exploit
Review Questions
1. When responding to a potential computer crime, what should an auditor do first?
a. Seek to identify the attacker
b. Remove the device from the network
c. Ensure that the evidence remains unchanged
d. Contact the police
2. While reviewing her email, an auditor notices that one email message contains an obscured link. Which of the following is not the appropriate action?
a. Inform IT
b. Open the link
c. Delete the email
d. Mark the email source as spam
3. When examining change management, an auditor should not be concerned with which of the following?
a. Restricted access controls.
b. Separation of duties.
c. Controls in the development environment.
d. Access to source code by developers.
4. To aid in the successful completion of the company’s first penetration test, an auditor should recommend which of the following?
a. SOX
b. NIST 800-42
c. PCI-DSS
d. SSAE-16
5. Which of the following activities would an auditor most like to see carried out on a weekly basis?
a. Penetration testing
b. Change management
c. Vulnerability assessment
d. Rotation of duties
6. Which of the following would an auditor expect to see as the first step in the incident response process?
a. Recovery
b. Mitigation
c. Planning and preparation
d. Identification
7. As an auditor, how would you describe a penetration test in which the structure of the network is unknown and the test team has no prior knowledge of the infrastructure?
a. Double-blind
b. Blind
c. Zero proof
d. Unknown
8. You have been invited to a postmortem review of a recent malware attack. The attacker was able to exploit the fact that the victim was connected to a legitimate site and a malicious site at the time the attack was carried out. Which of the following best describes this situation?
a. XSS
b. XSRF
c. Buffer overflow
d. TOCTOU
9. An auditor has been asked to attend an application acquisition meeting for commercial off-the-shelf (COTS) software. Which of the following would be the best recommendation for testing and evaluating a compiled existing application?
a. Fuzzing
b. Code review
c. Reverse engineering
d. Decompiling
10. From an audit perspective, which of the following would be the best technique to use to scan for deviations from normal activity?
a. Bypass label processing
b. Use attack detection tools
c. Use trend variance detection tools
d. Use audit reduction tools
Suggested Reading and Resources
![]() The five steps of incident response: https://digitalguardian.com/blog/five-steps-incident-response
The five steps of incident response: https://digitalguardian.com/blog/five-steps-incident-response
![]() Forensic tools for auditors: http://whitecollarinv.com/wp-content/uploads/2010/03/ForensicToolsTechniquesforIA4-19.ppt
Forensic tools for auditors: http://whitecollarinv.com/wp-content/uploads/2010/03/ForensicToolsTechniquesforIA4-19.ppt
![]() Common hacking techniques: https://fossbytes.com/hacking-techniques/
Common hacking techniques: https://fossbytes.com/hacking-techniques/
![]() IT security audits: www.tracesecurity.com/services/it-security-audit
IT security audits: www.tracesecurity.com/services/it-security-audit
![]() Chain of custody: https://ovc.ncjrs.gov/sartkit/develop/issues-coc.html
Chain of custody: https://ovc.ncjrs.gov/sartkit/develop/issues-coc.html
![]() ITIL incident management: www.bmc.com/guides/itil-incident-management.html
ITIL incident management: www.bmc.com/guides/itil-incident-management.html
![]() Risk factors that increase employee fraud: www.facilitiesnet.com/facilitiesmanagement/article/Three-Risk-Factors-That-Increase-Employee-Fraud--10923
Risk factors that increase employee fraud: www.facilitiesnet.com/facilitiesmanagement/article/Three-Risk-Factors-That-Increase-Employee-Fraud--10923
![]() Social Media Policy Examples: http://blog.hirerabbit.com/5-terrific-examples-of-company-social-media-policies/
Social Media Policy Examples: http://blog.hirerabbit.com/5-terrific-examples-of-company-social-media-policies/
![]() Top 10 DoS attack sites: http://top10stressers.com/
Top 10 DoS attack sites: http://top10stressers.com/