CHAPTER
4
Risk Management
Risk management covers many functional areas in the employment world. Some of them are: compliance with federal employment laws, identification of workplace hazards and developing safety plans to protect employees and the public, and preparation of job descriptions to be used both as a communication tool and also as a means to address physical and mental requirements of each job. Risk management explores how technology can help manage the liability that comes with operating an employment organization. And, finally, risk management addresses the rapidly evolving field of social media, Internet, technology, and e-mail use. Eight percent of the PHR exam and 7 percent of the SPHR exam will focus on this area of knowledge.
Risk management addresses issues related to employees, customers, clients, the public, and vendors/suppliers. Risk management is the process of managing liabilities related to these populations in ways that will protect the employer organization and not be so heavy-handed that the organization can’t function well in performing its mission. HR professionals are the key to striking a balance in that delicate effort—developing, implementing/administering, and evaluating programs, procedures, and policies in order to provide a safe, secure working environment and to protect the organization from potential liability. Lots of exciting things to think about.
The official HRCI Risk Management functional area responsibilities and knowledge statements are as follows:
Responsibilities
• Ensure that workplace health, safety, security, and privacy activities are compliant with applicable federal laws and regulations.
• Conduct a needs analysis to identify the organization’s safety requirements.
• Develop/select and implement/administer occupational injury and illness prevention programs (i.e., OSHA, workers’ compensation).
![]()
• Establish and administer a return-to-work process after illness or injury to ensure a safe workplace (for example: modified duty assignment, reasonable accommodations, independent medical exam).
• Develop/select, implement, and evaluate plans and policies to protect employees and other individuals, and to minimize the organization’s loss and liability (for example: emergency response, workplace violence, substance abuse).
• Communicate and train the workforce on security plans and policies.
• Develop, monitor, and test business continuity and disaster recovery plans.
• Communicate and train the workforce on the business continuity and disaster recovery plans.
• Develop policies and procedures to direct the appropriate use of electronic media and hardware (for example: e-mail, social media, and appropriate website access).
• Develop and administer internal and external privacy policies (for example: identity theft, data protection, and workplace monitoring).
Knowledge of
• Applicable federal laws and regulations related to workplace health, safety, security, and privacy (for example: OSHA, Drug-Free Workplace Act, ADA, HIPAA, Sarbanes-Oxley Act)
• Occupational injury and illness prevention (safety) and compensation programs
• Investigation procedures of workplace safety, health, and security enforcement agencies
• Return to work procedures (for example: interactive dialog, job modification, accommodations)
• Workplace safety risks (for example: trip hazards, blood-borne pathogens)
• Workplace security risks (for example: theft, corporate espionage, sabotage)
• Potential violent behavior and workplace violence conditions
• General health and safety practices (for example: evacuation, hazard communication, ergonomic evaluations)
• Organizational incident and emergency response plans
• Internal investigation, monitoring, and surveillance techniques
• Employer/employee rights related to substance abuse
• Business continuity and disaster recovery plans (for example: data sharing, password usage, social engineering)
• Data integrity techniques and technology (for example: data sharing, password usage, social engineering)
• Technology and applications (for example: social media, monitoring software, biometrics)
• Financial management practices (for example: procurement policies, credit card policies and guidelines, expense policies)
Core Knowledge of
• Needs assessment and analysis
• Third-party or vendor selection, contract negotiation, and management, including development of requests for proposals (RFPs)
• Communication skills and strategies
• Organizational documentation requirements to meet federal and state guidelines
• Adult learning processes
• Motivation concepts and applications
• Training techniques
• Leadership concepts and applications
• Project management concepts and applications
• Diversity concepts and applications
• Human relations concepts and applications
• Ethical and professional standards
• Technology to support HR activities
• Qualitative and quantitative methods and tools for analysis, interpretation, and decision-making purposes
• Change management theory, methods, and application
• Job analysis and job description methods
• Employee records management
• Techniques for forecasting, planning, and predicting the impact of HR activities and programs across the functional areas
• Types of organizational structures
• Environmental scanning concepts and applications
• Methods for assessing employee attitudes, opinions, and satisfaction
• Budgeting, accounting, and financial
• Risk-management techniques
Key Legislation Governing Risk Management
Now that you’ve reviewed the Risk Management HRCI responsibilities and knowledge statements, we recommend that you review the federal laws that apply to Risk Management as outlined in Figure 4-1. It would be helpful to refer back to Chapter 2 on these specific laws prior to reading any further in this chapter. A great many of them impact organizational liability, requiring HR professionals to make plans to address how those liabilities will be managed properly.

Figure 4-1 Key federal laws impacting employer liability
NOTE If you are a federal contractor or subcontractor you will want to be very familiar with the Executive Order and legislation that govern how employers must comply when they are receiving certain amounts of federal revenues through goods and service contracts.
Cross-Reference to Other Legislation Requirements and Enforcement Agencies That Impact Risk Management
As you reference each of these pieces of legislation listed in Figure 4-1, you will understand how they individually bring liability for noncompliance to the workplace. There are some additional federal laws that aren’t highlighted in the figure. That is because they are special condition laws that don’t apply to all employers. If your organization is a federal contractor or subcontractor, for example, you most likely have to comply with Executive Order 11246, the Rehabilitation Act, and the Vietnam Era Veterans’ Readjustment Assistance Act in your affirmative action efforts. But those requirements don’t apply to every employer, or even most employers.1
Applicable Legal Cases Involving Risk Management
We suggest that you understand the nature of case law prior to reading the chapter to correlate the topics with the legalities involved. There is only one recent case that is related to risk management, the 1991 case involving Johnson Controls. For more information on this case, see Appendix D.
A very common type of employer liability is employee complaints of discrimination. Typically, these complaints arise because an employee feels mistreated by a decision made about his or her employment conditions. They include complaints of race, sex, religious, or age discrimination. Also common are complaints of national origin discrimination and pregnancy discrimination. But the most frequent of all complaints is that “my employer retaliated against me because I filed a complaint.” The retaliation charge is one that most judges don’t like to hear and have little patience for. If an employer doesn’t understand that things must change when settling an initial complaint, and then does something to retaliate against the complaining employee, it is likely to raise the ire of any judge you find yourself before.
Hazard (Risk) Identification and Communication
The process of protecting an organization from financial harm by identifying, analyzing, financing, and controlling risk is a shared responsibility among several areas in an organization. Risk is the threat of an event or action that will adversely affect an organization. Risk arises from missed opportunities as well as possible threats. HR is relied upon to be the keeper of accountability and the developer of policies and procedures in risk management.2 Effective risk management is a progression of actions that are taken with the purpose of minimizing losses or injuries within the organization. HR’s responsibilities fall within the following areas:
• Occupational safety and health
• Legal compliance
• Privacy
• Security
• Disaster recovery for business continuity
The identification of current and potential risks is an essential role for the Human Resource professional. Weighing in on the probability and acceptability of the risk is valuable to integrate with business decisions that are made with other business units. It is a goal for the HR professional to be consulted as a business partner within the organization. Focus should be on proactive and management.
Needs Analysis (Audits)
Conducting a comprehensive risk management needs analysis is an important activity. A comprehensive risk management assessment is a useful tool to uncover and identify risks. When you conduct a risk management needs assessment, you must start with identifying a number of areas and goals and use an appropriate method for audit.
Qualitative and quantitative methods and tools for analysis, interpretation, and decision-making purposes—such as metrics and measurements, costs-benefit analysis, and financial statement analysis—are frequently used in risk management.
There are numerous risks possible in the modern workplace. For HR, the focus is usually on things related to the employee’s body and its day-to-day exposures. Some HR risks include:
• Employee complaints of illegal discrimination (EEO issues)
• Employee complaints of illegal financial processes (Sarbanes-Oxley and SEC issues)
• Employee injuries on the job (workers’ compensation issues)
• Safety practices and procedures (OSHA/MSHA issues)
• Emergency plans for use in the event of fire, earthquake, tornado, flood, hurricane (OSHA/MSHA issues)
• Imbalance of compensation programs (equal pay issues)
• Loss of federal contract revenues by noncompliance with affirmative action requirements
• Responses to crisis conditions (embezzlement, production interruption, natural disaster, key person disappearance)
Recordkeeping Requirements
There is a saying among HR professionals: “If it isn’t documented, it didn’t happen.” Actually, many management attorneys agree with that sentiment. When employer meets employee in a courtroom, juries have a tendency to root for the little guy (the employee) and have little sympathy for the big guy (the employer). That means the employer must be ready to “prove” everything they claim during the course of defending themselves against claims such as wrongful termination, illegal discrimination, failure to (fill in the blank).
Documentation is so important that almost every management attorney will offer instructions to their clients about how to prepare documentation of actions involving employee treatment. The problem is that people are inherently lazy. It takes time and effort to prepare documentation. If there is a choice between spending a half hour writing up the conversation a supervisor just had about an employee performance problem or getting out of work early, the documentation will slide. Eventually, it will be forgotten. And, there will be nothing in the file to prove a supervisor had that conversation with that employee about that performance problem. Whatever the supervisor claims to recall will be suspect without the written document to demonstrate that the recollection is accurate.

NOTE One of the highest impact activities an HR professional can have on any organization is to teach managers and supervisors the proper way to prepare documentation.
Once prepared, it is usually dependent upon state laws and company policy whether or not the employee is given a copy. In some states, that is a requirement, while it is not in other states. Federal law doesn’t specify one way or the other. It is not necessary for an employee to sign documentation about a disciplinary conversation with the supervisor, but if you get an employee signature, it is a good practice to provide a copy of the document to that employee. Why isn’t it necessary to get an employee signature? Supervisor notes are made by the employer and don’t require employee agreement. Unless it is a contract with the employee, the supervisor is merely writing what happened from his/her perspective.
Generally speaking, documentation should include the following:
• The date of the event and when the documentation was prepared. (They should be the same in most situations. Supervisors should always prepare their notes for file soon after the event took place.)
• A description of what was said. It is not necessary to quote verbatim. It is important to capture the key thoughts, who agreed to what, and the details about any deficiencies or issues the supervisor pointed out. The level of detail depends on the topic and how important details were to the conversation.
• How the conversation ended. What action plan was agreed to by both people?
• Will there be a follow-up meeting?
These same guidelines should apply to HR professionals in their documentation of conversations they have with employees, supervisors, and managers. It may be necessary at a future date to show someone your notes about what was said on a particular occasion.
The thing about documentation is that you don’t know if it will be important until you reach the future when someone requests it. By the time you discover it is important, it’s too late to create it.
Here is a quick word about creating documentation after the fact. While it is always best to be able to say that your notes were made right after the event or conversation, it is also possible to create your notes in the days following that event. When you write notes after the fact, always put the date on them representing when you wrote them. If you had a conversation on January 2 with an employee but didn’t get around to writing your notes until three days later, mark your notes with the January 5 date. That way, there will be no question about the fact that you prepared them after the event. It could be beneficial if you stuck in a note saying what caused the delay in preparing the documentation.
Investigating Complaints
There are several ways in which HR professionals can manage the employee complaint process, and there are several reasons why you could be faced with the need for an investigation. It may become necessary because of a discrimination complaint, employee bad behavior (code of conduct violation, embezzlement), safety issue (serious employee injury or death), disagreement with the employee’s supervisor, and so on.
When you recognize the need for an investigation, you can take one of several approaches to getting that done:
• Investigate the complaint yourself. As an HR professional, investigations are often just another of the many responsibilities that come with the job.
• Hire an outside expert to conduct the complaint investigation. This might be a consultant specializing in the investigation of complaints of the type you face. It might also be an attorney who specializes in investigating complaints for clients. It is generally possible to protect files created by an outside legal counsel as attorney work product. The files are part of the legal advice provided to the client organization. You should be aware of any state or local requirements that investigators be licensed before performing such work. Using unlicensed investigators when a license is required could expose the organization to additional risks.
• Have your internal legal expert conduct the complaint investigation. It may or may not be possible to protect investigation materials from disclosure under attorney client privilege when you use your internal attorney. An argument is sometimes made that a lawyer who provides legal advice and is also a participant (investigator) in the same situation invalidates the claim to attorney-client privilege. You’ll have to talk with your own legal counsel to determine the best course of action for your organization.
The following steps should be taken in an investigation:
• Plan the investigation. Identify the key people involved (complainant, supervisor, witnesses, experts). Identify what is needed from each of them. What questions should be asked based about the complaint. Who saw what? Who did what? Is there any documentation available? Are there any videos or photos available?
• Interview the employee who filed the complaint. Determine the details. Be sure the complaint is in writing, naming names and being specific about what happened. Document the encounter.
• Interview the witnesses. Determine if they can corroborate the claims of the complaining employee. Find out if they have any documentation or other evidence to support their observations. That might include videos or photographs. Document each interview.
• Interview the accused. Explain the charges. Explain the documentation and witness testimony about what happened. Ask for comments from the accused in reaction to each of those pieces of input. Document the responses.
• Follow up on any questions remaining. Re-interview individuals if necessary.
• Make a determination and provide feedback to both the accused and the complaining employee.
Documentation of each step in the process is very important. Note that it will be difficult to protect the documents you create from disclosure requests in the event of a lawsuit at some point in the future. That means you should “write for the jury” by explaining everything in detail, especially the reasons you had for making the decisions you made as you progressed through the investigation. Make sure your written documentation can stand on its own if you are not available to testify about what you did in that investigation.
Communication Skills and Strategies
Not much happens properly within a modern workplace unless adequate communication systems are in place to help workers understand what work needs to be done, how safety enters into the process, when to stop a given procedure, and hundreds of other applications you can think of each day.
Successful communication depends on completing the Communication Cycle, which is shown in Figure 4-2.
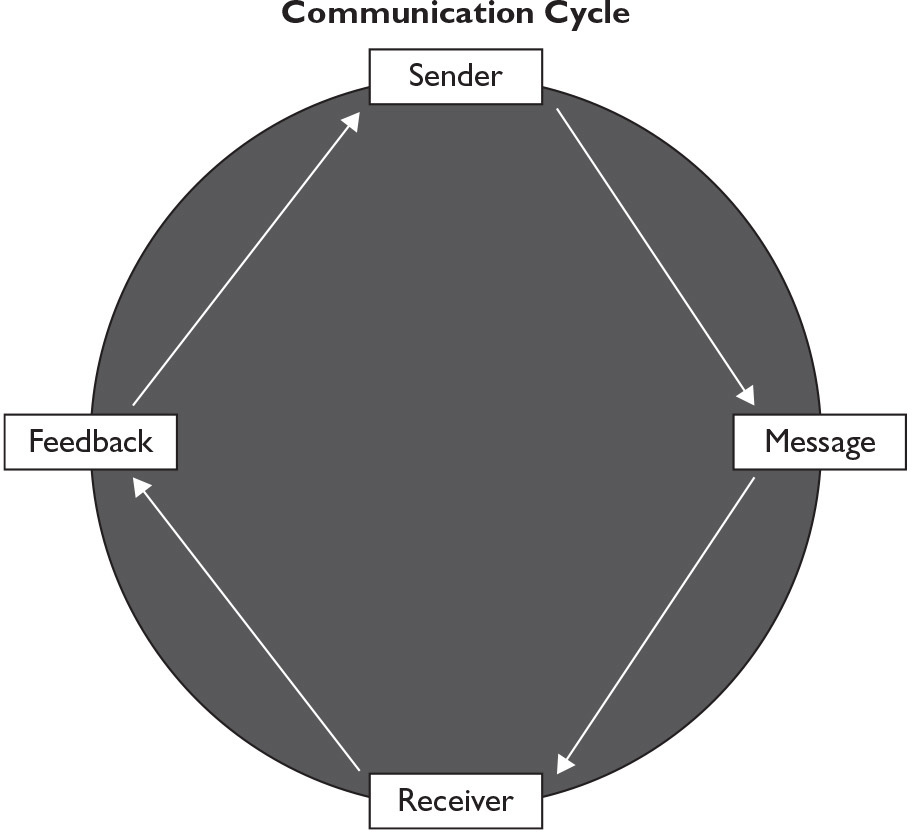
Figure 4-2 Communication cycle
When someone sends a message, it is generally received by the other person. However, the sender doesn’t really know that what was said has been understood unless there is some sort of feedback to indicate understanding.
Think about driving a car. When you step on the brakes, your brake light turns on to alert the driver behind you. When that message is received, the car behind begins to slow, giving you feedback that the message was received. If the car doesn’t slow, well… bad things happen.
Similar disasters can happen when communication between people goes awry. If your boss tells you not to send the announcement until later, and you understand the message to be, “Send the announcement, it will get there later,” the outcome won’t be what the boss wants and he may send you another message. When your doctor tells you take three pills twice a day and you hear, “Take three pills every two days,” things won’t go as planned in your recovery. Communication clarity matters.
One of the claims that invariably emerges from every complaint of sexual harassment is, “That isn’t what I meant at all.” Confusion in communication is reduced substantially when people insist upon getting feedback about what they have just said.
One tactic for making sure that the communication cycle is working as you want is to ask for feedback after you have given an important set of instructions. “Tell me what you are going to do…” Or, “What do you understand I just said?” Any number of other tests will solicit the feedback you want so that there is assurance your message got across as you wanted.
A second important part of communication is the realization that the sender controls intent, but the received controls the impact. Remember what accused parties usually say when confronted with a complaint that they sexually harassed someone? “That isn’t what I meant at all.” Well, it is often true. That isn’t what they intended the message to be. The receiver in our example heard something other than what the sender of the message intended. Incomplete or inaccurate communication can create very large liabilities for both individuals and organizations.
In the employment world, communication is critical to proper and successful running of the organization. Supervisors must successfully communicate to subordinates their task assignments, deadlines, expectations, methods, guidelines, and more.
Communication Methods
With today’s technology and real-time accessibility, a conscientious approach and clarity of message is vital. HR becomes a bridge communicating to various sectors within the organization and also outside the organization. Determining the most effective method to communicate can be just as important as what is communicated. Figure 4-3 illustrates the various communication methods for HR.
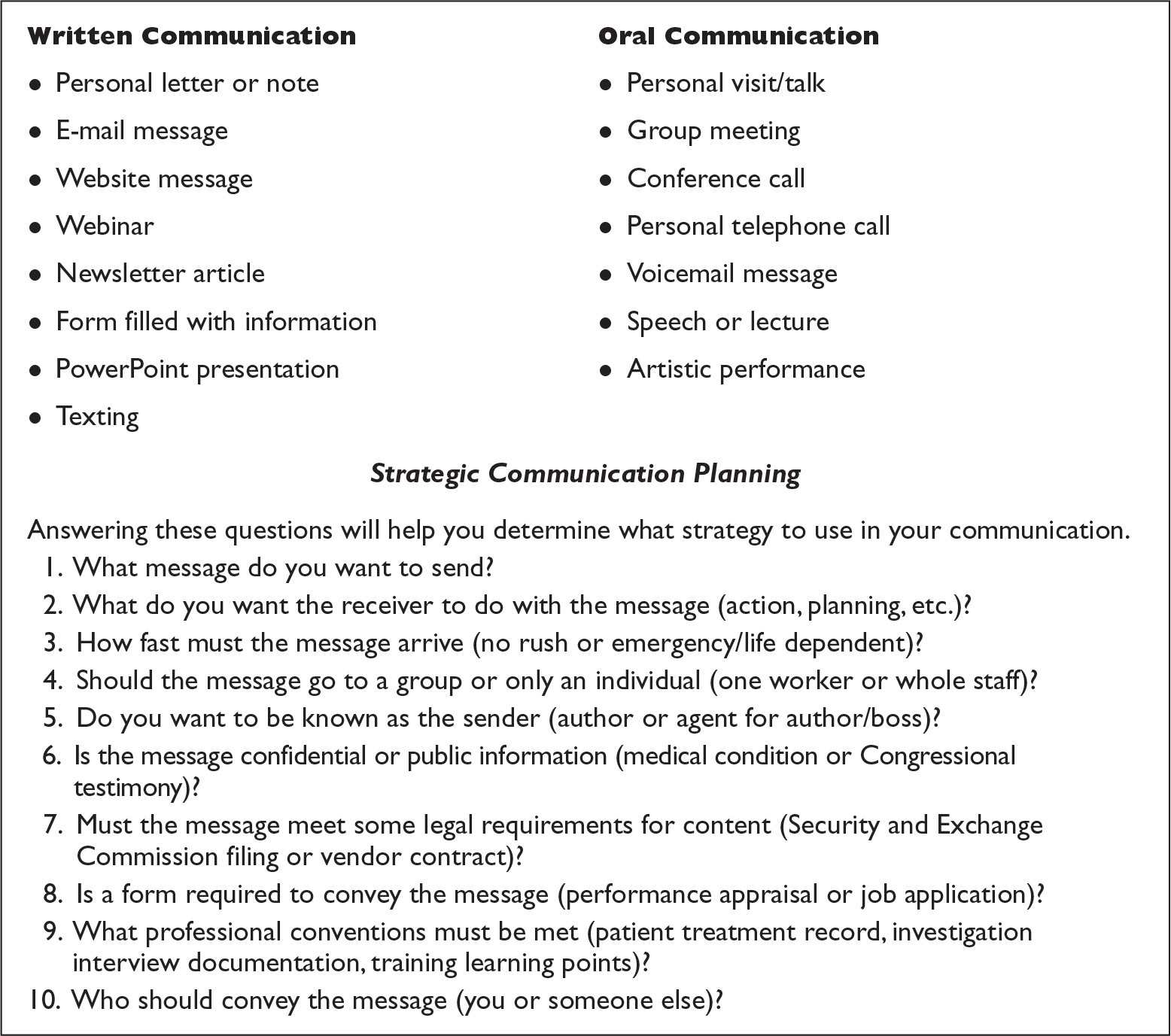
Figure 4-3 Communication methods
Strategy involves selecting the best tool for the job. In terms of communication strategy, how a message is to be communicated is often as important as what the message contains. Timing of a message can also be critical. Getting an e-mail message saying all performance appraisals were due last Thursday isn’t much help if you don’t get it on time to meet the deadline. When you are asked to provide some content to a bid proposal, delay can mean you lose business and the revenues associated with it. Picking the proper communication channel or media is often quite important.
Strategic Communication Planning
You can control the message in many different ways. What strategy you elect to use in conveying your message is dependent upon your answers to the key questions: Who, What, When, Where, Why? It’s not silly. And it’s not inane. These are important questions for anyone who doesn’t want to go through their professional career “winging it.” That cavalier approach won’t work for long in the role of an HR professional.
Ask yourself who should receive the message. What is the purpose of the message? When should your message arrive? Where will it be going? And, finally, why should the message be sent? If you can answer those questions you can select the best strategic communication process/media for your message.
Obviously, this analytical approach isn’t necessary for all messages. We send many messages every day as a matter of routine. Some, however, will require more thought. If you are involved in a merger or acquisition, a corporate downsizing, or introduction of a new vendor for your healthcare programs, some amount of thought should be put into what your message will be and how you will communicate it properly. Your employees will depend on your message being clear and easy to understand. Your executive team will be depending on you to accomplish the objective you have targeted. Success of your communication will depend a great deal on the strategy you select for its delivery.
Human Relations Concepts and Applications
Helping structure an organization’s policies and culture to make people feel welcome is a critical HR responsibility. If done properly, morale will remain high and risks can be controlled.
Job Analysis and Job Description Methods
As noted in Part I under Laws Affecting HR Management, the Americans with Disabilities Act (ADA) does not require employers to prepare job descriptions, but it does require that those who do shall review them for accuracy at least once each year. Federal contractors, subject to affirmative action obligations, must review their job descriptions every year. Therefore, most federal contractors are required to prepare and maintain proper job descriptions. If that requirement doesn’t apply to you, your organization may choose to have them or not have them. More information on job analysis appears in Chapter 9, “Compensation and Benefits.”
Preparing and Reviewing Job Descriptions
So, why should you write job descriptions for your organization? Job descriptions can:
• Identify key duties and responsibilities
• Communicate to incumbents their job content
• Communicate to job applicants the job content
• Communicate to job supervisors/managers what an incumbent should be doing
• Aid in organizational structuring to identify which jobs will perform which duties
• Provide input for evaluation of job value in compensation system
• Assist in determining how much incumbents should be paid
• Provide objective reference for preparation of work performance reviews or evaluations
• Assist in succession planning
• Provide reference for disability accommodation requests
Usually, job descriptions contain some typical subjects. They might be described as:
• List of duties and responsibilities
• Identification of the amount of time spent (by percentage) on each duty and/or responsibility
• List of knowledge categories required to perform the job
• List of skill categories required to perform the job
• List of ability categories required to perform the job
• List of physical requirements of the job
• List of mental requirements of the job
• Identification of qualifications not mentioned elsewhere in the job description (such as educational requirements, amount of specific experience required to be successful on the job)
Figure 4-4 is an example of a standard job description.
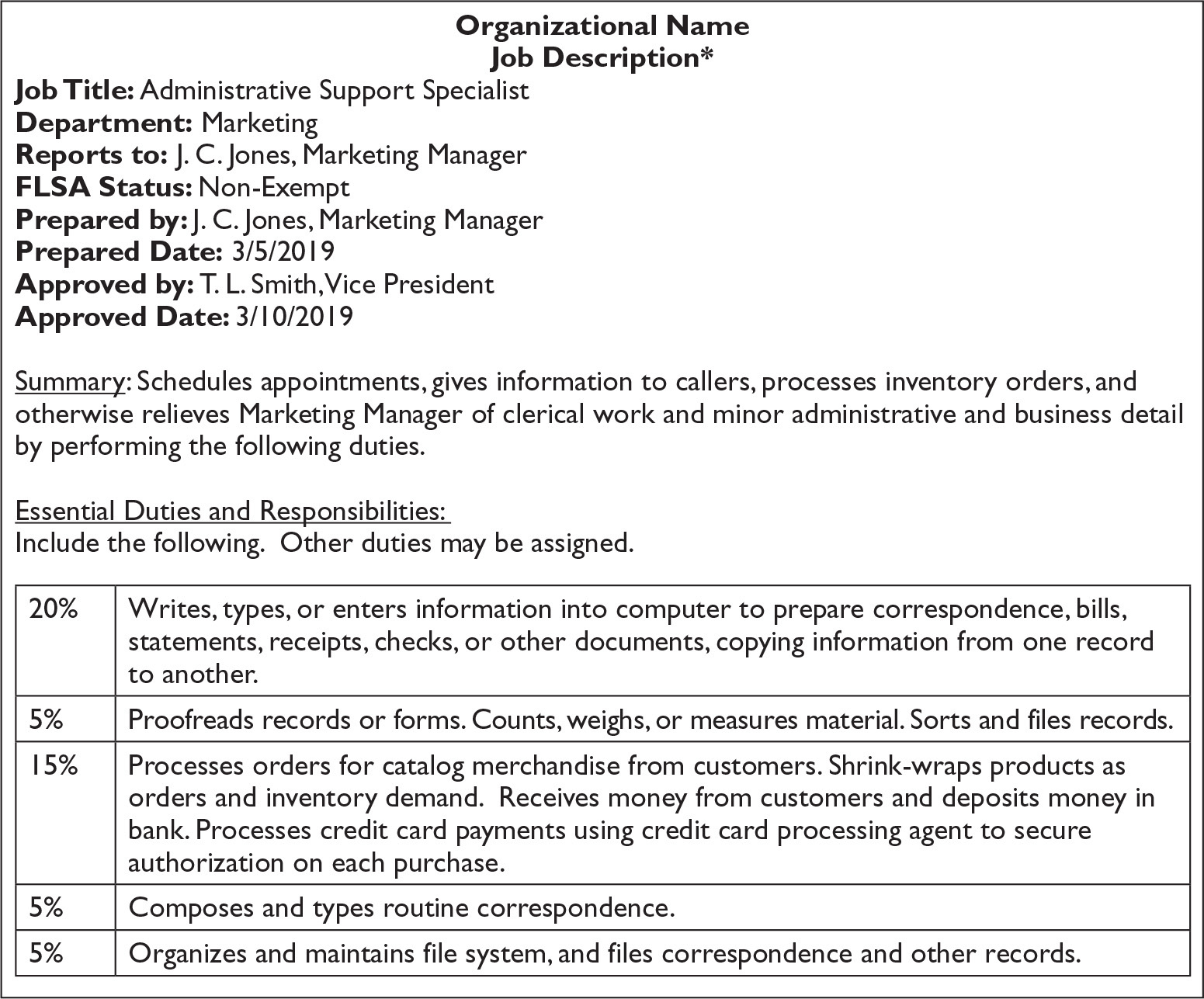

Figure 4-4 Job description example
NOTE Reviewing your job descriptions at least once each year is essential if you are to keep them representative of the actual job content and incumbent requirements. If you are a federal contractor, you must be prepared to attest that you have periodically reviewed your job descriptions to be sure they are accurate.
Job Analysis
When trying to determine the content of a job so a job description can be written, there are several approaches to the task:
• Observation A job analyst prepares lists of all activities and behaviors performed by an incumbent or group of incumbents, and then consolidates those lists of duties and responsibilities. Observation can involve time and motion studies. For accuracy of results, job analysts should be properly trained in the process rather than using untrained observers.
• Questionnaire A written questionnaire can be used to gather input from incumbents, supervisors, and managers about job content and incumbent requirements.
• Interview A job analyst interviews incumbent(s) to determine the job content, qualifications for successful incumbents, and the physical and mental requirements required of the job.
After a draft of the job description has been prepared, it should be shared with the incumbents, supervisors, and managers so they can have an opportunity to comment on the content. After considering the feedback received from the subject matter experts, a final description should be prepared and submitted for approval.
Each year, or at some more frequent schedule if the job is undergoing rapid changes, the incumbent and supervisor should be asked to submit their comments about changes needed in the written job description. Those changes should be worked into the description and resubmitted for approval.
There is more information about job descriptions and essential functions in Chapter 5, “Workforce Planning and Employment,” and Chapter 9, “Compensation and Benefits.”
Review of Job Descriptions
While job descriptions are not required, affirmative action compliance requires employers to review physical and mental job qualification standards annually. This review must be in writing and made available to Compliance Officers from the Office of Federal Contract Compliance Programs if requested during an audit of Affirmative Action Plans for the Disabled.3
Communication to Employees
Organizations live and die by communication. It is when people stop talking with one another that their organizations get into trouble and flounder. To prevent such a disastrous result, HR professionals should be alert to healthy communications within the organization and do all they can to foster those conversations.
Keys to Healthy Organizational Communication
Each of the following types of communication should be encouraged within any employment organization. It is incumbent upon the HR professional to be sure each type thrives and is reinforced and encouraged.
• Keep employees up to date on what is happening in the organization. Senior executives (and HR professionals) sometimes overlook how important it is to the average worker to understand what’s going on with the organization. If employees can be made to feel that they are given information about situations as developments occur, it will be easier for them to believe they really are contributing to the organizational success.
• Reinforce with employees why their jobs are important. When employees understand the “big picture” about where the organization is headed (and why), they will be more willing to keep their performance levels high. If they think they are being excluded from the “big picture,” their enthusiasm for the job will diminish.
• Deal effectively and immediately with rumors. Organizational effectiveness can be severely impacted by rumors working their way through the workforce. Rumors often start when people “suspect” something will happen, but don’t have confirmation that it is really true. Sometimes rumors are intentionally started in an effort to derail what is thought to be something bad for workers. It could be something to do with the organization, or something to do with individuals in the workgroup. Whenever untrue rumors take hold, managers should react quickly to address them openly and correct misunderstandings where they exist. If rumors deal with confidential issues, they should still be dealt with quickly and with as much openness as possible. You can always say, “We don’t have information about that yet, but as soon as we do, we’ll let you know.” Or, “These things are personal and hurtful to those involved. Consider how you would feel hearing something like this about yourself. Even though we can’t discuss them because of their personal nature, we hope you will not discuss things like this that can’t be confirmed as accurate.”
• Ask for feedback. Many employees would be willing to contribute ideas or suggestions if they thought there was a chance someone would actually listen. If we believe no one will listen, or worse, have actually been told to keep our ideas to ourselves, we are not very likely to be open with ideas in the future. HR managers should protect upward communication by requesting input from employees when it is appropriate. That may mean training managers and supervisors in how to request and accept employee feedback. You might have to prepare organizational leaders in how to behave when employee suggestions surface. Some of those ideas will be good ones. It is not necessary to have formal “Employee Suggestion Programs” for there to be requests for employee feedback. Feedback can be handled formally or informally, but if it is not handled at all, workers will become discouraged at not being able to contribute. Frustration will lead to dissatisfaction and lower production. Give folks the chance to contribute their ideas.
• Give feedback. Let your workers know how they are doing. If they are meeting your expectations, give them that acknowledgment. You don’t need a formal job performance appraisal system in order to provide that input to your employees. When something happens that you like, or there is a remarkable achievement, let employees know that you appreciate what they did. Likewise, when things go wrong that could have been handled differently, make suggestions for doing it differently next time. People have a need to understand where they fit into an organization and what their supervisors think of the contributions they are making.
HR Technology Activities
Besides the government, the HR function was notorious for being an intensive paper user. It was one of the first organizational functions to jump into the paperless movement via the development of technology, specifically human resource information systems and, soon after, applicant tracking systems. The cost savings of going digital and paperless were astounding. HR technology continues to develop and basically serves two purposes: as a repository of necessary information and as an aid to good decision making. Let’s review the various technology that exists today for HR.
Employee Records Management
These days, records management invokes thinking about not only the method of recordkeeping, but the safety of those records as well. For employers larger than 10 to 20 employees, keeping records manually is very difficult. That is particularly true with the reporting requirements that exist for federal contractors and subcontractors. A great deal of attention is given to record security, yet there are not many pieces of legislation that speak to employer obligations in that regard. Most of them on the books deal with medical information. (See Chapter 2, 1.14—The Fair Credit Reporting Act [CRA]; 1.18—The Health Insurance Portability and Accountability Act [HIPAA]; 2.1—Americans with Disabilities Act [ADA].) Today, hardly a week goes by that there isn’t news of another illegitimate access and release of private information from some database somewhere. From a risk management perspective, there are many commonsense protections that can be put in place to prevent the embarrassment of such disclosures and the expense of following up with people whose records have been jeopardized. It can be very costly to notify hundreds or thousands of employees that their records have been subject to theft. It erodes employee relations along with HR trust and credibility.
HR Information Systems (HRIS)
Employee records involve fields of data including those shown in Figure 4-5. This is not an exhaustive list. Many other records are maintained by some employers.
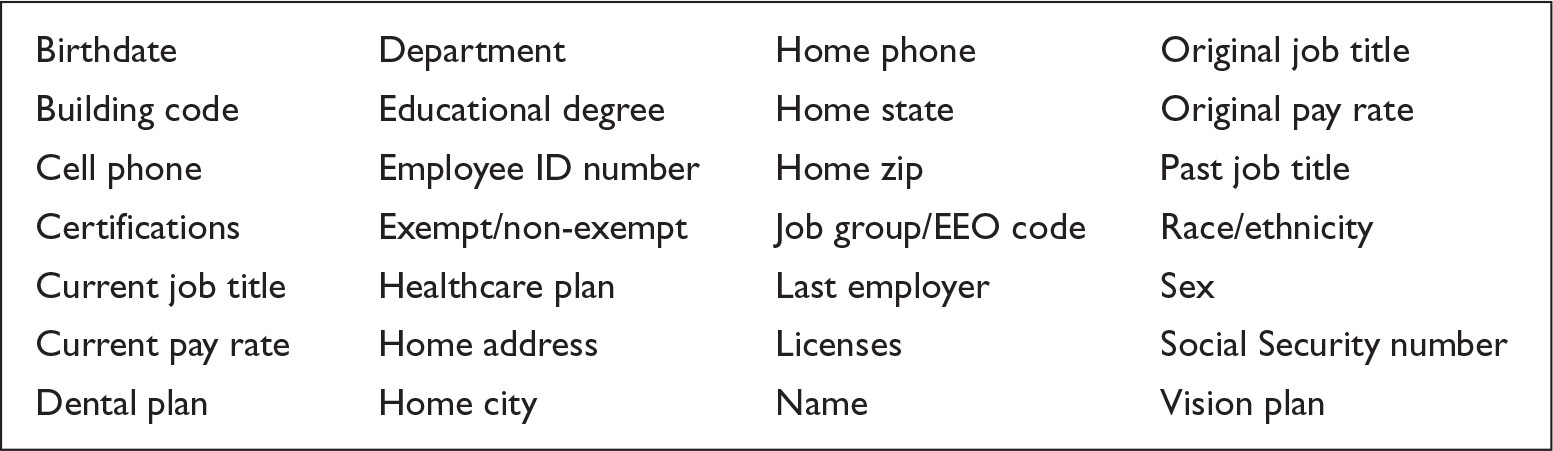
Figure 4-5 Types of data included in employee records
HRIS programs range from those serving employee groups up to 100 people to systems that can handle unlimited data fields and unlimited numbers of employees. Obviously, the prices of such software systems vary according to the capabilities they offer. PII (Personal Identity Information) is a crucial concern with HRIS and other systems in protecting employee data.
Employee Self-Service
There are many ways to offer employee self-service related to personal employee records. Some large employers use kiosks in central locations equipped with computer terminals that offer individual employees the opportunity to make changes to their employee records. Those changes might include marital status, health plan selections during open enrollment, addition of licenses or certifications, and more.
Employers often offer employee self-service through remote access and internal intranets so they can connect from the convenience of home during off-duty hours. It is obvious that such systems require security to assure that only authorized employees can gain access and that employees can only access their own personal record and not others. It’s not a good thing to have one employee searching through other employee records. In some cases, employers have even offered telephone access to employee data with the ability to make updates from the touch tone keypad. The latest hardware, offering touch screen technology, makes reviewing and updating employee records quick and easy.
It used to be that employers would default to using Social Security numbers as employee numbers in their HRIS, or even file folders. That is no longer such a good idea with identity theft on the rise. In some states, it is no longer permissible to print the entire Social Security number on paychecks for that same reason. Instead, consider using sequential numbers, 1 representing the first employee hired, and so on. Or you could use compound numbers such as 2013-1 to reflect the year and the hiring priority within the year. Another approach is to use the employee’s phone number as the employee number. Because Social Security numbers are used for so many sensitive purposes such as bank account reporting to the Internal Revenue Service, income tax filings, and payroll withholding reports, protecting them by not using them as employee ID numbers is a reasonable protection to take.
e-Learning
Only a few years ago, e-learning was not an option in the workplace. Learning was accomplished by attending a classroom session lasting from a few hours to several days, weeks, or months. Today, employees are able to log on to a computer access point and participate in training programs at their own pace, on their own schedule. These e-learning systems provide materials, review, and testing to assure the employee has accomplished specific learning objectives before moving to the next training step. They also offer an audit trail to report on who has participated in each program. That is handy when you have to be sure everyone has gone through specific training programs. There is no need for an instructor. Each individual works with the materials presented, and perhaps some reference materials, to meet the training objectives.
One of the more popular e-learning systems involves classroom-type groups with an instructor and a group of students, all participating remotely from anywhere in the world. There is no longer a need when using these systems for the group to collect into one physical setting. The savings on travel time alone has been significant for organizations using these types of learning programs. This approach is used by almost all of the major universities and colleges around the country.
Applicant Tracking Systems
For most small employers, an applicant tracking system consists of a file folder filled with job application forms. Larger employers are not able to operate with manual records any longer. During the great recession, with unemployment running up to double digits, an employer could count on receiving hundreds or thousands of job applications for every job opening announcement. Processing them manually was not feasible.
More and more, applicant tracking is accomplished on employer websites. People interested in a given job opening can submit their application information online and in some cases can even submit resume files and cover letters for consideration. These mechanized programs allow employers to sort through the massive amounts of data to find the few candidates who might be a good fit for the job opening.
Federal contractors with 50 or more employees and $50,000 or more in contracts are required to maintain applicant flow logs so they can perform analysis compared to new hire data.4 The objective, of course, is to determine if there are significant disparities among various groups for race and gender. Don’t forget that “race” includes all races. All people have a race, and all races are protected…not just minorities.
See more about applicant tracking systems in Chapter 5.
Techniques for Forecasting, Planning, and Predicting Impact of HR Activities
One of the largest challenges facing HR professionals is having the right people resources available for the organizational needs precisely when they will be needed. Forecasting can be accomplished in many ways but often relies on the professional experience of people with institutional knowledge about organizational history.
Mathematically Based Forecasting Techniques
In some situations it is possible to bring objective analysis to the forecasting effort. Using mathematical techniques can help create confidence in the forecast.
• Staffing ratios Compare the number of support personnel needed for each 10 production workers. This method can be used to estimate any support group requirements from accounting to HR to legal.
• Sales ratios Compare the number of employees required to support each different level of sales activity.
• Regression analysis Can be used much like the other ratio approaches to use various pieces of information to determine the likely workload and employee requirements based on sales, production levels, economic indicators, and so on. This method can get very complicated very quickly, but is aided somewhat by the availability of software aids within programs such as Microsoft Excel.
Judgment-Based Forecasting Techniques
Judgment requires experience and knowledge to be effective in forecasting. Some manners of judgment-based forecasting techniques are:
• Simple estimates Based on what input may be available to the HR manager, this is simply an approximate valuation for the number of people required based on what is known subjectively and objectively about the future.
• The Delphi Technique Using input from a group of individuals who are experts in the area of HR forecasting. Input is gathered through the use of questionnaires; it is compiled/aggregated and then the anonymous responses are recirculated to the experts for another set of opinions. It is a type of orchestrated survey system that seeks to reach a “correct” response through consensus.
• Focus group or panel estimates Using people gathered into a conference room setting, the group is asked to voice their opinions based on a set of facts given to them.
• Historically based estimates Using historical records, best judgments are made extrapolating history into the future.
Risk Management Techniques
There are four techniques for managing risk:
• Risk avoidance Eliminate the risk at any cost. For example: Terminate an employee who had a car accident in a company vehicle to avoid claims of negligent retention. Or do not permit public tours of the facilities because of the possibility for liability if a visitor gets hurt.
• Loss control Reduce the number of occasions that loss occurs. For example: At least once a month, an employee gets injured by slipping and falling when the bathroom floors are being washed. Control could be obtained by washing the floors at a time when employees would not be using the facilities.
• Risk retention For larger employers, this is common when they self-insure such things as workers’ compensation or other loss risks. This approach requires that a reserve fund be established to pay for any loss since the employer is self-insured under this model.
• Risk transfer Insuring against a particular loss will move the liability from the employer to an insurance carrier. For a fee, nearly everything is insurable. Employers are more frequently turning to insurance to prevent large financial losses due to things such as sexual harassment or supervisor misbehavior. Those types of policies carry very large deductibles (paid by the employer) before the insurance begins paying for additional loss.
Occupational Injury and Illness Prevention Programs
On January 26, 1989, OSHA published in the Federal Register5 a notice with general guidelines for voluntary adoption by employers. That set of guidelines was identified as standards 1910; 1910.1200; 1915; 1917; 1918; and 1926.
OSHA refers to these Injury and Illness Prevention Programs as Voluntary Protection Programs (VPP) because employers are not required to adopt them, but encouraged instead. The VPP is broken down into four sections, as noted in the following outline, and although not a requirement, it would benefit organizations to create and maintain policies and programs that correlate with the VPP outline.
Injury and Illness Prevention Programs
• Section 1: Management Leadership and Employee Involvement
• Written safety and health management system
• Management commitment and leadership
• Planning
• Authority and line accountability
• Contract employees
• Employee involvement
• Safety and health management system evaluation
• Section 2: Worksite Analysis
• Baseline hazard analysis
• Hazard analysis and significant changes
• Hazard analysis and routine activities
• Routine inspections
• Hazard reporting
• Hazard tracking
• Accident/incident investigations
• Trend analysis
• Section 3: Hazard Prevention and Control
• Disciplinary system
• Emergency procedures
• Preventative/predictive maintenance
• Personal Protective Equipment (PPE)
• Process safety management
• Occupational healthcare program
• Recordkeeping
• Section 4: Safety and Health Training
• Requirements for managers and employees
• Delivery systems
• Results measurement
A key component of any safety program, as listed in Section 3, is the provision of Personal Protective Equipment (PPE). This can be as simple as safety glasses and earplugs to hard hats, breathing apparatus, and hazmat suits. PPE is provided by the employer based on the job conditions and hazards faced in doing that work. Employers who are cavalier about these protection requirements are liable to find themselves in jail or paying a big fine if one of their workers is injured because of a bad decision on their part.
What are some of the consequences of failure to keep workers safe and free of injury?
• Employee injuries or death.
• Workers’ compensation costs increase due to experience modifications.
• Executives and management risk criminal prosecution for negligence or intentional acts.
• Company assessed financial penalties for workplace injuries.
• Company existence threatened because of marketplace reactions to accidents.
Safety programs should be part of a business’s strategic plan. Because of that level of importance, this topic is considered critical for SPHR certification.
General Health Practices
Policies will vary from employer to employer primarily because the health risks associated with employers vary widely. An accounting firm employee will face health risks that are quite different from those faced by Level 4 Containment Lab workers at the Centers for Disease Control, or even people in a local physician’s office. And, in all work locations, the objective is the same…protect workers from health risks whenever possible.
Personal Protective Equipment (PPE)
In high risk environments, Personal Protective Equipment (PPE) plays a key role in health protection. In some environments, full hazmat suits are a requirement. In other environments, a gauze mask may be appropriate because of the number of people coughing and sneezing. In a normal office environment, there may be no PPE requirements. Other examples of PPE include:
• Rubber/latex/nitrile gloves
• Protective aprons or overcoats
• Goggles or safety glasses
Workplace Environment Management
Developing a checklist for auditing the environment is something every HR professional should be able to do. There should be an identification of health hazards caused by the workplace, and those brought into the workplace by employees and visitors. On that list should be considerations such as those in an environmental hazard checklist of considerations and inspections. Here are some items you may find on such a checklist:
• Dust, debris, hazards (construction environment) Are these in the primary work site or are they intruding from outside the site. What mitigation options exist?
• Electrical and gas hazards Are there exposed electrical terminals? Are there devices used in the workplace that pose an electrical hazard? Is natural gas, propane gas, gasoline, or other fuel used in the workplace posing a hazard? What potential for leaking gas exists in the workplace? What mitigation options exist?
• Respiratory hazards Is there a risk of exhaust from gasoline engines entering the workplace? Is there a risk of carbon monoxide poisoning from gas heaters or other appliances? Could other substances such as refrigerant gasses like ammonia or Freon escape into the workplace? Is it possible for chlorine gas to find a way into the workplace and cause problems for workers? What mitigation options exist?
• Noise Are there machine noises in the workplace? Are other sources of noise generating potentially damaging noise? What mitigation options exist?
• Moisture Are there sources of water that could potentially cause flooding in the workplace? Are there misting sources in the workplace that could cause respiratory issues for workers? Might they cause slip and fall hazards? Could moisture cause skin reactions for workers? What mitigation options exist?
• Temperature Does the workplace experience extreme high or low temperatures. Is work done outside in direct sun without shade? Is work done in a refrigerated environment? What mitigation options exist?
• Ergonomic Does the work require constant movement in repetitive motion? Are there physical response requirements that demand fast reaction, or extreme extensions of limbs? Are long periods of sitting, standing, or walking required? What mitigation options exist?
ISO 14001 is known as a generic environmental management system standard, meaning that it is relevant to any organization seeking to improve and manage its environment more effectively.6 The International Standards Organization (ISO) develops and publishes organizational and product standards for the world stage. This includes:
• Single site to large multinational companies
• High-risk companies to low-risk service organizations
• Manufacturing and the service industries, including local governments
• All industry sectors including public and private sectors
• Original equipment manufacturers and their suppliers

NOTE The key for any employer is to perform an analysis of the workplace to determine what type of health hazards exist and then develop plans for dealing with those hazards.
General Safety Practices
Because all employers are accountable under federal law for maintaining a safe and healthy work environment (General Duty Clause), and in many industries, are required to have written safety programs called Injury and Illness Prevention Programs (IIPP), it is necessary to understand what key components exist within those programs.7
Evacuation Plans
A basic component of every safety plan is evacuation. Fire is a threat in nearly every workplace. And, although fire is likely the primary reason, it is not the only reason for having an evacuation plan for your work space.
Employer work spaces vary from single office facilities to multiple floors in high-rise buildings to entire campus installations composed of many buildings. In each case, employees should be provided with instructions about how to evacuate their work site and what to do following evacuation. Re-assembly areas should be designated in the evacuation plan and someone should be designated as the authority to verify that everyone successfully got out of the quarters. Figure 4-6 provides a sample evaluation plan.
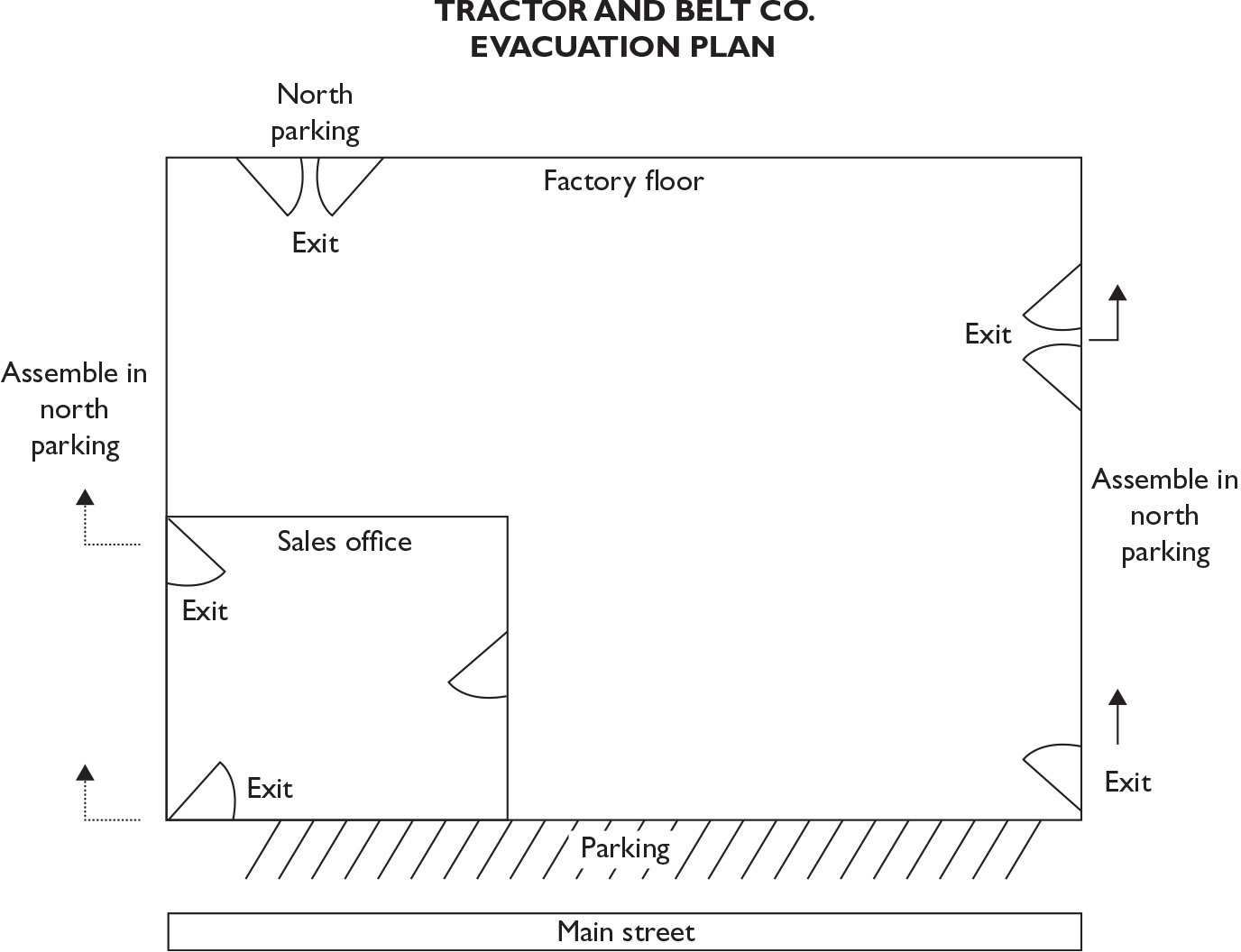
Figure 4-6 Sample evacuation plan
Once the plan has been properly drawn up, employees should be trained in how it should be implemented and the signals that will alert them to the need to evacuate.
Ergonomic Evaluations
These days, finding employees who have no need for ergonomic work stations is only a dream. Fortunately, these days, more and more resources are available to assist employers in prevention of injury due to ergonomic problems. Some of the areas for concern are:
• Repetitive motion injuries (wrists, hands, arms, legs, backs)
• Sitting (desk chairs, table height “standing” desks)
• Keyboard use, including use of the mouse (carpal tunnel syndrome, arm and shoulder ailments) (split keyboards, separate portions for each hand, wrist support pads for mouse and keyboard)
• Lifting, bending (cranes, exo-skeletons, robot substitute)
• Telephone use (neck pain, shoulder pain) (headset with microphone to avoid having to hold handset between ear and neck)
Safety Audit and Communication Plans
A good safety program will always have periodic inspections built into the program. As a function, “safety” can often be included in the Human Resources department. In some organizations, it is found in a department all its own (the Safety Department). Or, it can be located in another part of the organization such as Operations or Facilities Management.
It is a good idea to have each manager and supervisor perform monthly inspections of their individual and crew work areas. If there is a safety officer for the organization, that person should inspect every part of the physical facility at least once per quarter. Each inspection should be documented and notations made about the need for follow-up and problem correction. Part of every supervisor’s personal safety responsibility is to inspect the audit reports made by his or her subordinates. If nobody checks to be sure safety inspections were actually done, they will sometimes get “missed” because of other important things that demand a supervisor’s attention.
See Figure 4-7 for a sample Safety Inspection Report. It is necessary to create one inspection form for every type of work area and hazard present. Figure 4-8 illustrates a sample Safety Action Report.

Figure 4-7 Safety Inspection Report
Figure 4-8 Safety Action Report
Return to Work Policies
When choosing a policy, employers have a wide range of choices. On the one hand is a policy that says no one may return to work until they are 100 percent (100%) recovered and able to perform the full range of work duties their job requires. On the other hand is a policy that says, just as soon as an employee is able to perform some of the job functions, he or she should return to work, and the balance of their duties can be handled by others until they regain full recovery.
Modified Duty Assignments
Somewhere in the middle of that spectrum is a policy that says that once an employee is able to return to work, we will modify her job responsibilities on a temporary basis so we can get her back to work as early as possible. Some medical people suggest that returning to work early can aid in recovery. Because what we do in our job is so often integral to the person we see ourselves as being, assurances that the job will still be available to the employee can be psychologically beneficial.
In a Modified Duty Assignment, some tasks or duties will be forgiven or handed off to other employees for a period of time. If the employee has just returned from back surgery, waiving the need to lift objects that would be normal work tasks could be an example of modified duty.
Reasonable Accommodation
Reasonable accommodations can present an opportunity to get the employee back on the job with some alterations to the job that don’t relieve the employee of any duties or responsibilities. The same employee who had back surgery may find it necessary to alternate standing and sitting. Providing the opportunity for that to take place is an example of job accommodation. If frequent rest breaks are needed to help someone return to work, the employer could agree to allow the employee to take several additional breaks throughout the day. In many cases these accommodations are temporary and will go away in time. In other cases, the job accommodation may be a permanent thing. When an employee returns to work after having been diagnosed with diabetes, it may be that you are faced with an accommodation request to provide a firm schedule of meal and rest breaks so there are opportunities to take insulin injections and eat food at precise intervals throughout the day.
Independent Medical Exam
Of course, any injury or illness that requires medical attention will be followed closely by the employee’s own medical team. But, when the employee calls and say he is ready to return to work, what do you do?
First, if the absence has required medical attention, you should ask for a return to work release from the employee’s physician.
Second, you should make an appointment for the employee to visit a physician who is hired by the employer to evaluate the individual’s abilities to perform the specific job requirements. That means a physician who is an expert in occupational medicine. You should provide to that physician a copy of the employee’s job description, including a listing of the physical and mental requirements of the job.
If there is a difference of opinion between the two physicians, you can send the employee for a third evaluation, or you can simply elect to use the guidance from your employer’s medical expert. HR professionals should be cautioned that it is unwise to make conclusions of a medical nature if you are not a qualified physician yourself. Allow protocol and procedure to obtain the required expert input, and then rely on it for your decision making about the situation.
Plans to Protect Employees and Minimize Organization Liability
HR professionals are responsible for the workforce in many ways, including recruiting and counseling on employee management issues, record management, and the management of organizational liabilities related to employees. There are many disasters that can befall an employer. Airlines experience airplane crashes. Investment institutions experience embezzlement. Manufacturers experience product contamination or other defects. There may just be an accident that causes fire in the building. Who knows what will happen when they get up in the morning?
Emergency Response Plans
A primary safety axiom is that proper planning can save lives and property. It is a good idea to have a written plan specifying what actions will be taken in any of many various scenarios. There are some basic alternatives for dealing with a disaster, large or small.
This consideration goes beyond the Emergency Evacuation Plans discussed earlier in this chapter. Here we are talking about the entire universe of emergency planning. Evacuation is just one type of response to an emergency.
The first step toward having an emergency response plan is to conduct a risk assessment for your work location. Look at the physical facilities, emergency exits, fire suppression systems, electrical and gas shut-off access, hazardous materials used in the workplace, protective equipment needed for operations, employee training for special equipment, use of proper lock-out tag-out procedures when working on electrical equipment, and proper handling of carcinogenic substances such as copy machine toner. Answer hypothetical questions such as: “What would we do if someone with a gun walked through our front door?”
Engage key personnel in the development process. Ask people on the production line and in the office what they would do in some circumstances. Get input from experts and non-experts alike. Then list the responses that should happen for each emergency you listed.
Finally, once the plan is developed, be sure everyone in the workplace knows about it and what to do if an emergency happens.
Business Continuation
If there is a flood or fire and your workplace is destroyed, the computers, hard drives, on-site backup systems, and filing cabinets may no longer be available. How will you open your business tomorrow morning?
Employers must have a plan for how they will continue operating their organization. What about customer records, accounting records, client data, and payroll information?
This is an area of responsibility where HR professionals should work with others in the organization such as professionals in Information Technology (IT) and Accounting. It should be common practice for backups to be made of all technology systems, especially an HRIS system. And, those backups, or at least duplicates of them, should be stored off-site at some secure location. It is necessary for the survival of your organization that it be able to continue operations as quickly as possible with all the records it requires for that to happen.
What will your plan dictate regarding where employees should report to work after such a disaster? Do you plan to use e-mail, text messages, or a telephone tree to contact everyone and pass along instructions? How will you keep supervisors and managers informed? Who will handle media inquiries about the disaster and your plans for the future?
Password Usage
Some common mistakes are made by employees in handling passwords for computer program access. If you look around your workplace, you will likely find examples of these:
Password Problems
Here are some common problems found when analyzing password usage:
• Sticky pad note passwords Passwords written on sticky pad types of notes. This is for the convenience of the employee who can’t seem to remember his password. No effort is made to conceal the password. Sometimes this note is pressed to the computer monitor to make it even more available.
• Desk drawer passwords You will find some employees who make a list of their passwords and stick that list into their top desk drawer, or workbench drawer. Again, this is for convenience, but it is easily discoverable by anyone with dishonorable intentions.
• Personal information passwords Employees will often create passwords by using their birthday, their home street address, their child’s name, or their wedding anniversary. Any of these can be fairly easily discovered by looking elsewhere in the workstation. A family photo with a special date stamp, a diary with the password notations in the front or back, or some other personal notations will be available to anyone wishing to access the employee’s work information.
• Password binders What could be more handy for a thief than to have sitting in plain sight a binder labeled “Passwords”? With all the access points we must have in the HR world these days, it is common for people to keep binders and address books filled with passwords for each of those programs. But keeping the binder in plain sight shows a very low level of concern for security. Perhaps it could be locked up in a cabinet or desk drawer?
Password Examples
Passwords should be made of random or nonsensical characters. They should not be recognizable words.
Bad passwords might look something like this: Easter2015; Hellen1234; 1776July4th; InkPen; RadioKQRT; Mary7789; Phone593.
Strong passwords might look something like this: HyRtP73N; 84XcMH59; Ak9BrzE45. Some software today requires the use of symbols in passwords to add further complexity (for example, * & % $ # @ + = !). Use both upper- and lowercase letters interspersed with numerical characters.
Why Passwords Matter
HR professionals have many pieces of information entrusted to them. You know from Chapter 2 that you have a legal obligation to protect the privacy of employee data and medical information. If you take that responsibility seriously, you will treat passwords with the respect they deserve. The last thing you want to have to tell someone is, “I’m afraid someone has accessed your data file and taken a copy.”
Social Engineering
Social engineering refers to using electronic communications and the Internet to manipulate someone into compromising their organization’s cyber security by revealing critical information. With the role of Human Resources, personal identification information (referred to as PII) is the target. It is a term that describes a kind of intrusion that often involves tricking other people to break normal security procedures.
A social engineer runs what used to be called a “con game.” Social engineers often rely on the natural helpfulness of people as well as on their weaknesses. Virus writers use social engineering tactics to persuade people to run malware-laden e-mail attachments, phishers use social engineering to convince people to divulge sensitive information, and scareware vendors use social engineering to frighten people into running software that is useless at best and dangerous at worst. They might, for example, call the authorized employee with some kind of urgent problem that requires immediate network access. Appeals to vanity, appeals to authority, appeals to greed, and old-fashioned eavesdropping are other typical social engineering techniques. Social engineers may even be internal within an organization, searching wastebaskets for valuable information, or gaining access codes by looking over someone’s shoulder (shoulder surfing).
Security experts propose that as our culture becomes more dependent on information, social engineering will remain the greatest threat to any records and data system. Organizations need to raise the level of awareness of all their people about the dangers of social engineering, and keep it at a high level at all times. Con and scamming games are as old as civilization itself. The methods never really change because human nature never changes. Only the technology does.
Disaster Recovery
There are many resources for disaster recovery on the Internet. Here are some of those you may find useful:
• Federal Small Business Administration www.sba.gov/content/disaster-recovery-plan
• Federal Emergency Management Agency www.fema.gov/disaster-recovery-centers
• Federal Disaster Assistance Web Service www.disasterassistance.gov
Needless to say, every employer organization should have a disaster recovery plan. It should identify the types of disasters that might hit the organization (for example, earthquake, fire, flood, workplace violence), how each of those situations would be handled, who would be assigned to speak for the organization (to the employees and to the press), what should employees do following a disaster, how the organization could regain an ability to resume operations, and how employee injuries or fatalities should be handled. What alternate work site has been chosen to accommodate resumption of operations? Who will manage the business if the existing leaders are not available for some reason?
If you want a model of crisis management planning, look to the airline industry. They have worked through almost every possible scenario that could impact their business, and have developed plans for how each would be handled. They know it is possible for a disaster to happen in their business and they have prepared themselves for managing those possibilities.
If you would like to have a desk reference on the subject of disaster recovery, we suggest Manager’s Guide to Crisis Management, also published by McGraw-Hill, at www.mhprofessional.com/product.php?isbn=0071776133.
Workplace Violence
Like the other areas of risk management, the area of workplace violence demands planning. HR professionals will be required to have written workplace violence prevention programs in some states. Under the “General Duty Clause” of OSHA requirements, employers are responsible for providing a safe work environment. Preventing workplace violence would fall within that requirement.
Preventing workplace violence begins with identifying the types of violence that might occur in your workplace. Sources can come from inside or outside the organization. Retail establishments might consider robbery as a possible risk. The same could be said for banks or credit unions. Disgruntled customers or former employees can pose a risk.
Once identified, each risk should be addressed with an action plan detailing how the organization will respond if the violence actually happens. What will the business leaders do? What will the HR manager do? What are employees expected to do? Where should employees go in a violent event? How should they protect themselves if violence happens? Who will address the media? Who will coordinate with law enforcement?
Perhaps the most important consideration is employee communication. Keeping people informed as events unfold is a big part of keeping them safe and reassured. But making sure employees know where to go and what to do in advance depends on careful planning and training. HR professionals must allocate resources to those things or a disaster can result.
Budgeting, Accounting, and Financial
There is always a risk of employee theft. Embezzlement can happen in the smartest of organizations. If someone wants to game the system, it is only a matter of time before that happens. It is an area for more planning. The senior financial executive in the organization (Chief Financial Officer—CFO) should be involved with that planning effort.
There are commonsense things to consider when planning for financial security of the organization. For example, never allow a single person to have access to money or other resources without a second person involved in the transaction. When two or more people are required to access accounts, the likelihood of theft is reduced. Having a record of each financial transaction and who did it will serve as an audit trail so it will be possible to identify who is accessing funds for any purpose.
But oversight is going to remain a primary requirement. Frequent review by managers is important. When employees know they will be observed and their work reviewed, there is less chance they will try to take what they shouldn’t.
These types of financial risks can be significant depending on the employer. Planning should include identification of the type of risk that could occur, what action plans will be activated in each instance, and how the organization will recover from the problem after the fact.
In some situations, it will be necessary to inform federal agencies of the problem. This is often required when the employer is a publicly held entity. The Securities and Exchange Commission (SEC) and other federal agencies may have requirements that specifically address your type of organization. You should plan accordingly.
Substance Abuse
Substance abuse is a risk not only because it can harm employee health and personal life, but also because it can lead to problems such as embezzlement, workplace violence, and workplace injuries.
In some organizations, it is necessary to assure that you are maintaining a drug-free workplace. (See information about the Drug-Free Workplace Act in Chapter 2.) That can involve drug testing on either a regular or random basis. It can also require drug testing following accidents when an employee has been operating equipment or motor vehicles. Federal laws require drug testing for some truck drivers, train engineers, and airline pilots if they are involved in an accident.
If employees must be able to drive on their job, they must do so without impairment by drugs or alcohol, whether the drugs are prescription or illegal. It is up to the HR professional to establish systems necessary to assure that happens and can be verified.
Employers risk the torts of Negligent Hiring and Negligent Retention if they knowingly hire or keep on the payroll someone who is a drug or alcohol abuser who does harm to someone else while on the job. If the employee is involved in an automobile accident while under the influence on the job, the employer can be held accountable in some situations.
Policies must be developed that specify what will happen to employees if they fail to pass one or more drug tests. Sometimes, policies will provide for employees to use a leave of absence to address drug or alcohol dependence. Chapter 9, “Compensation and Benefits,” will explain more about the types of leaves of absence that can be used for this purpose and whether they provide for paid or unpaid time off. Will the employer sponsor employee participation in a rehabilitation program? Is there a state or local program that will help pay for the type of program? What will happen if the employee has another incident of involvement with drugs? How will someone who appears to be under the influence of drugs or alcohol be handled if they report to work while impaired?
Don’t forget to develop action plans for how you will handle the situation when one of your employees does become involved in an on-the-job incident because of drugs or alcohol.
Theft
There are lots of ways theft can happen in the workplace. Here are some examples:
• Embezzlement of funds
• Taking company equipment (for example, computers, printers, scanners, calculators)
• Taking company supplies (for example, paper, toner/ink, staplers, tape, batteries)
• Taking time (for example, long breaks for coffee and meals, wandering through the workplace chatting with other workers, playing games on the computer, texting and social media)
• Falsifying records (for example, time cards/payroll input, untrue overtime claim, extended time off for union activities, untrue sickness reports)
• Unauthorized credit card charges—claiming personal expense as company expense
• Copying employer software for personal use in violation of copyright law
HR professionals need to work with the accounting professionals to develop appropriate policies that explain how these things are unacceptable under the organization’s Code of Conduct. Policy should be clear about what will happen if an employee is discovered to have participated in these types of activities. And management should follow through with discipline according to that policy. Consistency in treatment is critical. Inconsistency can bring charges of illegal discrimination based on any number of classifications.
Sabotage
The term “sabotage” is believed to have originated in the fifteenth century.
Today, workplace sabotage includes such things as:
• Throwing items into machinery to destroy or disrupt production
• Removing parts of equipment to cause a shutdown
• Tampering with software or passwords for access to programs
• Attacking computer systems by hacking
• Destroying computer records
• Creating a false workload by filing inaccurate or false claims
Without a doubt, sabotage is a difficult problem to handle. HR professionals should approach such issues with basic investigative techniques. Conduct a proper investigation, and it is possible that some witnesses will surface, or the code of silence will be broken, and the truth will come out. When sabotage reaches the criminal vandalism level, always involve law enforcement with proper reports so they can conduct their own inquiries.
Social Media, Internet, and E-mail Use Policies
Social media is here to stay. There is no going back. According to one source, in February 2014 the membership and usage of some principal social media websites was very impressive8:
• eBay 120 million active users
• Facebook 1.23 billion users
• Instagram 150 million users
• LinkedIn 259 million users
• Pinterest 70 million users
• Skype 300 million users
• Twitter 240 million users
• YouTube 1 billion users (4 billion views per day)
This is just a sampling of websites involved in e-commerce and personal communication. Needless to say, with these membership and usage numbers growing each month, how employees use social media and e-commerce sites is an issue that employers must address in their policies and workplace practices. (Please note: These usage figures change daily. If you need exact usage figures, please conduct a current investigation to be sure you have the accurate data you need.)
Social Media
Social media embraces Internet sites that permit person-to-person communications or posting of general comments on almost any subject. Messages can be directed to a single individual or to the world at large. Also included are services such as YouTube.com that permit people to upload video files that can then be accessed by anyone with an interest. Consider a policy that explains to employees that they should have no expectation of privacy while in the workplace. Of course, careful review of all policies should involve your attorney before any announcements are made to employees.
Internet Access
When it is necessary for employees to have access to the Internet to conduct their business, there should be a written policy describing how that access is to be accomplished, and what websites are unacceptable. The policy should also provide for disciplinary activity for someone who engages in accessing Internet sites that are unacceptable. Unacceptable websites can include personal use of pornographic sites, political sites, gaming sites, shopping sites, or others. Use of company equipment and company time to access such sites could be cause for discipline as a misuse of work time and employer equipment.
E-mail Use
E-mail has grown to include texting as a means of written communication from one person to another. It is so common now that we’ve seen distracted people get into car accidents, walk into automobile traffic, and stumble into water fountains while concentrating on text messaging. Here, once again, employers should consider policy content that controls the use of organizational equipment and the limitation of personal use. But also consider the issue of employees using personal smart phones for texting and e-mail. If this happens during work time, it can be as big a problem as other non-work diversions. Policies should explain that work equipment is intended only for work applications.
Diversity Concepts and Applications
Diversity and inclusion practices embrace internal and external groups. Social media can be effectively used to reach out to groups you have found are underrepresented in your workforce, your vendor and supplier groups, or your customer and client groups. One example is found in how popular LinkedIn.com has become in the recruiting arena. It has been said that over half of white-collar workers are being placed through that website each year. Why not use those avenues of communication to increase diversity of the employee population?
Of course, the risk of liability for failing to treat people equally is that complaints about disparate treatment will be filed. When cases go directly to external enforcement agencies, the employer loses the ability to provide an early remedy, or explain to employees why the actions were not discriminatory.
Ethical and Professional Standards
The Society of Human Resource Management (SHRM) has compiled and published a Code of Ethics.9 It calls for HR professionals to set an example for others in their organization: “HR professionals are expected to exhibit individual leadership as a role model for maintaining the highest standards of ethical conduct.”
Privacy Issues
The United States Supreme Court has weighed in on the question of employee privacy when using employer-owned equipment intended for use as a business tool and not a private communication device. The Court has said, regarding public employees, they should have no expectation of privacy when the equipment is owned by the employer and they are directed to use it for work-related business only.10
Social media has become such a powerful influence in the lives of American citizens that private employers in some locations began asking job applicants for their Facebook passwords so a review of their Facebook content could be included in the background check. In 2012 Congress failed to pass the Password Protection Act, but that didn’t stop six states from passing their own legislation preventing employers from demanding such information.11
Another privacy issue for employers is embedded in the National Labor Relations Board ruling on employee freedom to engage in “concerted activities.” Late in 2012, the Board ruled that employees have a right to discuss employer policies and their personal treatment in a forum such as Facebook.12
Internal Privacy Issues
Privacy issues within an organization surround employee expectations and the type of business the organization conducts. Here are some reasons why you might want to explain to employees that they should have no expectation of privacy while at work:
• Security cameras monitor work areas as well as the grounds outside.
• Telephone calls are monitored and recorded for training and quality purposes.
• Computer use is monitored and reviewed for quality purposes.
• E-mails are subject to review at any time.
• Lockers and desks are employer property and subject to search at any time without notice.
• Personal bags and briefcases are subject to search when entering or leaving the building.
External Privacy Issues
When communicating with people and locations outside the employer’s organization, it is necessary to consider the possibility that those communications could be intercepted and read by unauthorized people. Today, there is a growing problem of “bad guys” stealing e-mail messages to mine personal data such as credit cards and Social Security numbers. One way to contain the problem is to use encryption for e-mail messages. That scrambles the message so it is not readable by anyone other than someone with the encryption tool needed to decode the message.
Electronic access to bank accounts, tax records, credit card merchant accounts, or other sensitive data are all at risk. Such data transfer processes should only be done with a secure link on the Internet. Credit card information should only be transmitted across secure connections. It is time to recognize that there are people sitting and watching electronic traffic. If they have an opportunity to steal such information for personal gain they will do so. It is incumbent upon the HR professional to assist the organization in constructing systems to prevent that from happening.
Protection of Data
Risks abound in the subject of data protection. Consider the types of data employers generally handle:
• Personal and private employee information (name, Social Security number, bank account number for payroll deposit, drivers license number, passport number, medical records, disability identification)
• Financial records belonging to customers (credit card number, credit card expiration date, credit card security code, bank account number for wire transfers)
• Financial records belonging to the employer’s organization (tax records, bank account numbers, accounting records including customer contact information)
The question becomes one of how to protect such information from unauthorized disclosure. Here are some considerations:
• Provide an audit trail in software so financial records can be checked.
• Require two people for authorization of transactions above a given dollar amount.
• Secure employee records with physical locks and sufficient password policy.
• Restrict access to customer records through sufficient password policy.
• If it is warranted, require a supervisor to input authorization on each occasion before an employee can gain access to sensitive record systems.
Ensuring that such policies and procedures are not only implemented but properly maintained by all people in the organization is something HR professionals can help with. The alternative is the unauthorized disclosure of employee personal information or customer financial information and the expense it will require to “clean up” after the fact. And that doesn’t include the loss of trust people will have in the organization having once experienced exposure that should not have happened. Typically, organizations that have had a breach of security and loss of personal or financial data will offer six to twelve months of credit report monitoring through one of the three major credit bureaus. Even with the expense that represents for thousands of people whose records may have been disclosed, often the basic security for the data systems doesn’t get changed and the same risk carries forward. Through proper attention to such matters, HR professionals can help their organizations avoid such catastrophes.
Password Protections, Monitoring Software, and Biometrics
Passwords are problematic because people generally treat them in a very cavalier manner. They are posted on notes under plastic desktop protectors or taped to the computer monitor in plain sight. Sometimes, a modicum of effort is made to hide them by putting the note inside the desk drawer or under a blotter.
Employers and HR professionals should have well-considered policies about passwords. The best systems have passwords controlled by a single coordinator who changes passwords on a regular basis or require users to create new passwords on a regular basis. Storing passwords is an issue that should be discussed with all departments. Proper handling can easily be the subject of a brief employee training program.
Monitoring software is available that will permit employers to track the type of usage on company PCs. Some of the types of tracking that can be done include:
• Websites visited
• Searches conducted
• Keystroke logging
• E-mail sent and received
• Document tracking
• Website blocking
• Application blocking
• Keyword blocking
All of these types of tracking can be performed remotely by supervisors or other authorized surveillance personnel. There are many such programs available for less than $100.

NOTE It is necessary to inform employees that such monitoring systems are being used and that they have no privacy when working on company equipment.
Biometrics is the use of personal biological characteristics to identify authorized personnel for system access. Biometrics can include retina scans, fingerprint scans, or palm print scans. The level of sophistication in this technology is increasing rapidly. A quick Internet search will unveil hundreds of websites that offer information or products related to biometric security systems. The federal government even has a website dedicated to the subject at www.biometrics.gov/.
Identity Theft
This is the result we wish to avoid. Identity theft is the generic term used to describe the situation when someone co-opts personal information such as credit card numbers and Social Security numbers to steal money from the person those things belong to. Often that happens without anyone being aware of it until the arrival of the next credit card statement. It should be noted, however, that banks and other credit card issuing organizations are becoming much more sophisticated about their monitoring of credit card purchases. They look for purchases that don’t belong in the individual’s buying pattern, or for charges made outside the country.
When someone has had their identity stolen, and their credit rating demolished, they will need to invest a significant amount of effort to set things right again. That can take months or years and some amount of money in correspondence and notary fees.
If employee information is jeopardized, a policy should be in place that specifies how the organization will respond to the problem. It should lay out the communication that will take place and any support that will be provided to employees who experience identity theft–type events as a result of the data loss.
Workplace Monitoring
Aside from the computer monitoring we have already discussed, there are some organizations that find it beneficial to monitor their workplace by using video equipment. Examples include gas stations, convenience stores, check cashing businesses, and banks. Monitoring is done for the benefit of employees as much as for the organization’s protection.
Of course, retail establishments are concerned about theft of products as well as robbery. “Shrinkage,” as product theft is called, costs retailers $119 billion in 2011 according to the RFID Journal. Radio Frequency Identification (RFID) is being used more and more to protect expensive products from pilferage. As the cost of those small devices decreases, they are finding their way into less expensive products. A transponder chip inserted into the packaging will trigger an alarm when exiting the store if it is not disarmed at the cash register first.
Policies should be in writing and clearly communicated to employees so they understand any monitoring that is conducted in the workplace.
Methods for Assessing Employee Attitudes, Opinions, and Satisfaction
Some risks can be reduced if employers are aware of them in advance. If employee attitudes are sliding from positive to negative, the employer would want to know that and have a chance to correct whatever problems exist before they become irreversible.
Small employer organizations can make use of PC-based software products that can perform surveys and survey reporting with some limitations. Larger organizations will likely want to use more sophisticated software or the help of external survey experts. Often these are members of the American Psychological Association (APA).
Most organizational success experts stress the importance of monitoring employee attitudes and opinions on a regular basis. Almost every large organization spends a great deal of energy and resources on monitoring customer satisfaction. But that’s only half of the equation. It takes satisfied customers to support an organization’s march into the future. However, it also takes satisfied employees as the other part of the equation. HR professionals can help their organizations understand the benefits and importance of budgeting for this important effort.
Use of Third Parties or Vendors
There will come a time in the professional life of every HR manager when there won’t be sufficient internal resources available to do the tasks required. It could be the need to do open benefits enrollment, affirmative action plan development, employee attitude surveys, or HR Information Systems (HRIS) implementation. It could be any number of other things.
When vendors are needed to perform a function or task, selecting them should be a serious undertaking. It is a multi-step process.
Developing Requests for Proposals (RFPs)
A Request for Proposals (RFP) is different from Requests for Information (RFI) or Requests for Quotation (RFQ).
RFI is a formal request for information about products or services available on the market that might fit the buyer’s needs. Think of them as “off the shelf” or “ready to wear.” There is little or no customization involved with an RFI. Examples are software packages that will track job applicants or an HRIS database for employee information.
An RFQ seeks pricing for a product or service that the buyer already understands. There is no need for the buyer to engage a vendor in discussions about how the request will be fulfilled. The basic information needed is a price for the deliverable. This can be useful when shopping for salary survey reports, or safety kits to be posted throughout the workplace.
The RFP is generally used for more complex products and services. When you need to have a vendor provide healthcare benefits programs or payroll services, you will want to publish an RFP and distribute it to vendors you believe would be able to respond adequately.
Contents of an RFP should include:
• Organization and project background This is a statement about the organizational history that brought about the need for this program or project. What generated the need?
• Work to be done A statement about what the project will entail. This is where a description of the product or service will be found. It can be brief or extensive depending on the complexity of the deliverable involved.
• Timelines and deadlines Clear expectations about milestones to be met during the project. Attach dates to each step or review point. Vendor responses should be based on these deadlines and expectations. If payments are to be made to the vendor at interim points along the way, that should be explained here.
• Vendor bid This is the statement of expense the vendor will provide. If necessary, the buyer may request more than a “bottom line number” for the cost statement. It might be that there are identifiable subdivisions of work that can be priced for budgeting purposes.
• Payment conditions Explain the number of days it will take to generate a check after a vendor invoice is received. Of course, this is something that should involve the Accounting department and any policy on the subject. Will there be monthly invoice requirements, one invoice at the end of the project, or only one invoice for delivery of the product being purchased?
• RFP evaluation criteria This is the statement about how the buyer will evaluate the RFP responses. Will there be interviews? Will there be follow-up questions requiring vendor response? Will a committee be making the decision or is that to be done by an individual? What will be taken into account for evaluating the RFPs? Cost will be one, but other factors could include the ability to meet the milestone dates, background and experience of the vendor and its staff, responses from references provided by the vendor, and the location of the vendor’s work site in relation to the buyer’s facilities. Almost any business criteria could be applied to evaluating vendor responses. But whatever they are should be included in the RFP document.
Contract Negotiation
If you are going to select a vendor or supplier without going through the RFP process, it will be necessary to reach agreement on the details of delivery and payment. These things are usually covered in an RFP.
When negotiating, first identify the legal requirements for the situation. Are there local or state laws that govern building permits, or zoning that will impact your project? Are there sales tax requirements that will be involved with the purchase? Your organization’s legal advisor or financial officer can be very helpful in identifying these requirements.
Next, prepare for your negotiating session(s):
• Prepare a list of topics you want to address. Identify the facts and figures associated with each topic. Know the details before you go into the meeting.
• Identify the facts that you think both parties might be able to agree on. List those that you think will be controversial.
• Highlight the items you believe are absolute requirements and those you would be willing to compromise on. Attach some cost estimates to each of the items so you will be ready to discuss the expenses if you do compromise.
• Meet the other side with respect. Treat the vendor, or others, as you want to be treated.
Contract Management
Once a contract has been negotiated and approved, someone should be designated as the contract manager. This should be a single person who will be responsible for following up to assure the contract requirements are met. These include verifying that the timeline is working as planned and that all deadlines or milestones are met. If contract changes are needed, work with the attorney to prepare an amendment and then implement the changes. Your organizational attorney will be of help in identifying how to oversee the contract’s implementation.
Chapter Review
In this chapter, we have identified how HR professionals can help their organization manage risks. There are risks to people and risks to budget. Some risks can be shifted away from the organization through insurance policies. Others must be managed and minimized. When HR professionals ask to be included in executive-level discussions, explaining how risks have been controlled is one way to gain that inclusion. Real contributions to business goals and financial bottom line will gain attention every time.
Questions
1. A hazard identification survey should be performed:
A. If there is an obvious problem or someone has filed a complaint
B. Every month in manufacturing organizations and every quarter for all other types of organizations
C. On a regular planned schedule that involves most management people
D. Only when the designated Safety Officer says it should be done
2. Hugo has just had a conversation with one of his subordinates about his performance. Now that it is over, Hugo should prepare documentation:
A. That must be approved by in-house counsel and the HR Manager
B. That is filed in the employee’s personnel folder
C. That is signed by the employee and sent to legal
D. That is at least four or five pages long with quotations from both supervisor and employee
3. Alexia has just received a complaint of discrimination from Marshall, one of her employees. She should now:
A. Determine if there is a prime facie case and investigate if there is
B. Determine if the complaint sounds reasonable and immediately call the employee’s supervisor to discuss things
C. Determine if the employee has a history of complaints and treat this one accordingly
D. Determine if the employee’s supervisor is going to be receptive to the complaint and an investigation before moving forward
4. Andre has just given instructions to his employee concerning a new sales order. This is not a routine order and there are a couple of unusual requirements. What should Andre do to be sure things will go the way he has instructed?
A. Tell the employee to check in after the order is completed to be sure it has been done properly.
B. Tell the employee that this customer is very important and if this order is done properly, there will be more orders to come in the future.
C. Give the employee a chance to explain his understanding of the instructions that have just been given. Because they are complicated, Andre should follow up with written instructions or checklist.
D. Andre should carefully supervise exactly how the employee works on the order, staying close and giving input all along the way.
5. Sylvia has just been asked to make a presentation to senior management about the new healthcare benefit program. To be sure it goes well Sylvia should:
A. Practice her presentation in front of a mirror and be sure she wears her best business suit on that day.
B. Prepare a brief summary sheet with key points about the new healthcare benefits that the managers can take back to their employee groups for discussion.
C. Make sure she has included the answers to the questions Who, What, When, Where, and Why in her presentation.
D. Ask the senior managers if any of them have already learned about the new program.
6. John is told he has been assigned the task of preparing written job descriptions for each job in the organization. He questions the idea that physical and mental requirements should be in writing. It sounds to John like the employer is more likely to be sued if those things are committed to paper. What would you tell John if you were his boss?
A. If physical and mental requirements have any possibility for excluding disabled people, John’s right. They shouldn’t be included in the description of job content.
B. Physical and mental job requirements should only be discussed if a disabled job candidate applies for the position. Otherwise, they should be left out of the description.
C. Actually, there should be two versions of every job description. One should have the mental and physical requirements and the other should not. The one without that content is what should be published announcing the opening.
D. Each job should have both physical and mental job requirements identified. Those requirements should be discussed with job candidates to determine if each candidate feels they can meet those requirements, or if they will need an accommodation of some sort.
7. Hilario has just been asked to prepare a written job description for a newly created position. Because this job has never existed before, can Hilario just make things up and correct them later?
A. Of course. The description can be updated after someone has been assigned to do it and discovers what responsibilities actually exist.
B. A job description should be prepared in advance, with help from the supervisor. It is up to the employer to determine job content. Listing those responsibilities is important because they can help in selecting a new employee for the new job.
C. In the beginning, it’s not too important to be accurate about the job content. It will develop over time and the description can be updated later.
D. When the supervisor isn’t sure what responsibilities will be assigned to the job, Hilario should reschedule development of the job description until the supervisor is more confident about the job content.
8. Lynell just got a call from a manager in Production asking if the rumor is true about a new policy on pension plans. As the HR Manager, what should Susan do about that phone call?
A. She should explain to senior management that the rumor is working its way through the organization. If it is true, she should encourage senior managers to move forward with announcements so the truth about new pension changes can be heard directly from the employer. If it is not true, Lynell should work with managers to communicate with employees that there is no foundation for the rumor.
B. Lynell should do nothing. It’s just one person who has raised the question. It will go away on its own without causing upset among the employees.
C. She should announce to all employees that the pension plan is being changed, or that the rumor is false.
D. Lynell should tell the production manager not to say anything about the pension issue until senior management is ready to unveil the changes.
9. Tobias has just been appointed the first HR Manager for his company. He wants to organize employee records as one of his first projects. He isn’t sure how to separate records into various categories of information. How would you advise Tobias?
A. All records for each employee should be consolidated into one file per person. That file should be kept in the HR office and secured in locked file cabinets.
B. Separate files should be created for each employee’s personnel records, medical records, and investigation files if necessary. All files should be secured in locked file cabinets.
C. The HR staff should only be concerned with personnel files. Medical records and investigation records should be handled by someone outside the HR organization.
D. According to the Employee Records Stability Act, employee files should contain personnel records and medical records but never investigation information. Securing them is a requirement.
10. Gary is converting paper records to a computerized Human Resource Information System (HRIS). He wants to make it easy for employees to update their personal records in the new system. What approach would you recommend he use?
A. It is a good idea to give a hard copy of their personal information to each employee so they can verify the accuracy of the data. Ask for feedback with corrections or additions.
B. Call each employee and review each personal data element to be sure they are all accurate. Take corrections over the telephone.
C. Send an e-mail to each employee with the employee’s personal information asking for corrections and additions.
D. Send out a notice to all employees that the new system is being created and ask anyone with questions to contact Gary.
11. Jerrod works for a federal contractor with 145 employees. He knows he should keep a log of job applicants, but his boss doesn’t want to give him the clerical support he needs to keep the log current. If you were Jerrod, what would you do?
A. Because the employer has fewer than 150 employees, it’s not an issue. He can ignore the log until he hires five more people.
B. The CEO should understand that federal regulations permit the Department of Labor to presume illegal discrimination if they don’t track applicants.
C. The CEO should understand that an applicant log is something that can be created at the end of the year and that’s when critical clerical support will be needed.
D. Because the employer hasn’t kept an applicant log up to now, Jerrod should wait until next year to start fresh with the new year.
12. Valerie has just begun work as HR Manager for a new non-profit organization. She has been tasked with developing many policies, including one on workplace safety. Valerie isn’t sure that she needs to be concerned about Injury and Illness Prevention Plans (IIPP). What would your advice to her be?
A. She is right. Non-profits don’t have to be concerned about meeting requirements for written IIPPs.
B. She should start creating her IIPP right away. Liability is present from day one of the employer’s operations.
C. She should develop a policy about safety, but there is no need for her to go to the trouble of creating an IIPP. That is just for government and for-profit companies.
D. She should take advantage of the 120-day grace period offered by OSHA rules and put creation of a safety program on her “To Do” list for later in the year.
13. If you are responsible for developing the safety plan for your organization, how would you be able to determine if everyone got out of your building in an emergency?
A. Always have the employee roster on your iPad and take that with you when you evacuate.
B. Have the Safety Officer check the number of people who made it to the gathering location away from the building.
C. Ask everyone who made it out if they know that the people they were talking to earlier were all present at the emergency gathering location.
D. Gather all evacuees in a predetermined location outside the building and have supervisors report on their group headcount.
14. Bill is going to return to work after a skiing accident had him recovering from a broken leg for six weeks. His doctor has written return to work instructions prohibiting Bill from standing for more than 30 minutes at a time. Because his job requires constant standing at the customer service counter, you have to determine whether to have him return to work or not.
A. You should have a frank discussion with Bill about what he can do and what he can’t do. From that conversation, you should determine if some accommodation can be made for the restrictions and how long that will need to last. Perhaps he can be reassigned to another job temporarily, or it might be that he can’t return until he can take on all of his responsibilities.
B. Sure, let Bill return to work and give him a stool to sit on while talking with customers. If he has to get something from the parts inventory, you can hire a temp to do the running for him.
C. You should have a frank discussion with Bill’s coworkers and tell them they will have to do more running to help Bill when parts are needed. They can object but you can require them to help out.
D. There is no way that Bill can return to work until he is able to perform all of the essential functions of his job, including walking to get parts when necessary.
15. Lanny supervises the accounting operations. He has several of the passwords he needs for software he uses on his job taped to his computer monitor. He knows that he shouldn’t do that but says he can’t remember them and doesn’t want to go digging for them every time he needs to do some work on the computer. What are you going to say to him?
A. Tell Lanny that he should put the note under the glass desktop protector. That way it won’t be obvious to anyone who looks at his computer monitor.
B. Tell Lanny that he can put the password list on the bottom of his keyboard. No one will think of looking there.
C. If he can’t remember the passwords, he should keep a list of them in a locked desk drawer.
D. Lanny should never write down his passwords. He should prove that he has them memorized before being allowed back into the software programs.
16. Monika works hard and parties hard. On Monday morning, she comes in to work and seems to be slurring her words and not really focusing on the things she looks at. The supervisor calls you to see what you recommend as the HR Manager. What will you tell the supervisor?
A. Tell the supervisor to take Monika home. She isn’t fit for duty and the organization doesn’t want the liability of having her at work.
B. Tell the supervisor that he should keep an eye on her to be sure she doesn’t get hurt. It should be just fine. Monika can handle this type of thing.
C. Tell the supervisor that we can’t get too personal with Monika by asking how she got stoned, so just send her to the break room for a half-hour to see how she feels after that.
D. Tell the supervisor we should get Monika to the company doctor for drug and alcohol screening. Be sure he takes her and doesn’t let her drive herself.
17. The accounting manager comes to you with a stack of printouts showing a long list of embezzlements by one of the employees. Best practices would suggest the following treatment.
A. Confirm that the data is accurate and shows employee theft. Notify senior management if necessary and obtain authorization to call in police for an arrest. Send the employee a letter confirming their employment termination.
B. Once the data has been confirmed, it should be used to confront the employee and demand repayment.
C. With the proof in hand, call the employee and the employee’s supervisor into a conference and terminate the employee on the spot. Send a letter confirming the termination.
D. Confront the employee and offer the opportunity to resign if the employee promises to repay the stolen funds.
18. Almost everyone in the Tiger Tooth Dental Office has and uses social media on their personal cell phones. Doctor Tiger has asked that employees only use their cell phones during breaks, lunch, or in emergencies. Sherlene can’t seem to restrain herself and the cell phone hardly ever leaves her hands. What would you advise Doctor Tiger to do?
A. Confiscate Sherlene’s cell phone. Tell her she can get it back at the end of the day.
B. Have Sherlene store her cell phone in the doctor’s private office and allow her to have it back at lunch and after work.
C. Make the Office Manager responsible for enforcing the policy and tell her that Sherlene will not be able to bring her cell phone to work if she doesn’t start abiding by the policy.
D. Explain to Sherlene that one more incident of her using her cell phone during work time will result in disciplinary action. Include the Office Manager in those discussions.
19. Alden has always considered himself a benevolent employer, trying to make decisions about employee issues in favor of the employees whenever he could. Yet in all the years he has been in business, he has never had a worker like Mickey. Mickey has been on the payroll for a little over two years and all of a sudden has started missing work two days a week. He has no more accrued sick time and has blown through all of his accrued vacation time. How should Alden handle the problem?
A. Talk with Mickey and try to determine what has suddenly changed in his life. If he is ill or has a family problem, it may be possible to offer a leave of absence so he can deal with whatever has happened.
B. Talk with Mickey and explain how important attendance is to personal performance. He can’t do his job if he isn’t here every day. Get a commitment from Mickey that he will not miss any more work days.
C. Talk with Mickey and tell him that he will be disciplined if he doesn’t end his attendance problem. Any more unauthorized time off and he might have all of his days free.
D. Talk with Mickey and explain that you are thinking of getting a replacement for him. As a matter of fact, you have already posted the job opening on Craig’s List. Tell him perfect attendance from now on is the only thing that can save his job.
20. Ivory wants to hire a benefits consultant to help assess the organization’s healthcare benefit options. Her boss tells her to draft an RFP to be used in obtaining input from other benefit consultants. Ivory has never prepared an RFP before. As her boss you should tell her:
A. Getting a list of qualifications and the bid amount are the two most important components of the RFP process.
B. Having responses include a list of deadlines that will be met for the project is something Ivory should not overlook.
C. It is important to begin by developing a list of criteria for evaluating each response from consultants.
D. If you have someone in mind for the work, write the RFP so only that person will qualify and be selected.
21. Doyle is wrestling with the idea of creating job descriptions for his organization. As the HR Manager, he is wondering how he can convince the line managers to invest the time it will require. How can job descriptions speak to risk management?
A. Used properly, they can help in employee selection (reduce turnover), assist in discussions about job accommodation requests (workers’ compensation), and help in performance management.
B. Used properly, job descriptions will give supervisors something to prove why they can’t accept a job accommodation request. There are too many actual requirements to be able to allow some of them to slide without getting done.
C. Used properly, supervisors will be able to talk with job candidates about the kinds of educational requirements needed in the job. A job description enables you to weed out unqualified people without wasting interview time.
D. Used properly, job descriptions will include a statement that says, “…and all other duties as may be assigned.” Supervisors should be pleased by that.
22. The AB Trucking company has never had a safety program until now. The CEO has said HR will develop one and make sure it is implemented the right way. What should the HR Manager include in the project outline for the safety program to succeed?
A. Supervisors should be required to spend a minimal amount of time or they won’t support the project.
B. The written program should include MSDS and an annual walkthrough by the CEO to reinforce the importance of safety.
C. The HR Manager should include all of the OSHA-specified content in the written IIPP. That will mean supervisors will have to spend time on safety issues.
D. Only the CEO can make safety a reality. It is up to the policy statements to carry the weight and produce the results.
23. Damion has just called saying he wants to file a complaint that he’s being discriminated against by his supervisor. What should you do if you are the HR Manager?
A. Give Damion the phone number for the EEOC. They are the experts in handling discrimination complaints. You couldn’t do as good a job if you handled it.
B. Ask Damion to explain what happened. Get him to describe the supervisor’s decision that caused him harm, and how that was linked to his membership in a protected group. Ask him how other people have been treated in similar circumstances.
C. Make some notes and explain to Damion that his accusations are very serious and you will get back to him after you talk with his supervisor. In the meantime, he should consider taking some time off.
D. It doesn’t matter how other people are treated, Damion has had such a difficult time. He should get some special recognition and a reward for turning in his supervisor.
24. For quality control purposes, you sit in on random interviews your recruiters conduct with finalists in the employment selection process. Your recruiter Samantha has just been asked, “I’m interested in a permanent job that will last for the rest of my career. Is this the job that will do that for me?” What would you like to hear Samantha say in a response?
A. Not a problem. We treat our people like members of a family. You won’t have anything to worry about.
B. The company’s not going anywhere and you can expect to be here for life.
C. We can’t guarantee lifetime employment.
D. We can’t give you promises, but you can expect that this job is going to last for a very long time.
25. Augustine filed a discrimination complaint saying her supervisor made sexual advances toward her. Now, her supervisor tells her she is being moved to a job at a different work location. She doesn’t like that much because it means a longer commute. Does she have any recourse?
A. Actually, she does. Making an employee move work locations against her wishes can be considered retaliation for having filed the complaint. The supervisor should have been moved instead. She should file a retaliation complaint.
B. Separating Augustine from her supervisor’s control is the best way to handle this situation. If it means she has to move, then at least she will be protected from him. She has no recourse.
C. Augustine’s supervisor is hopping mad to begin with. There is no way he will keep her in his group, so she is going to move one way or another. Augustine is just going to have to accept the move as a consequence of her complaint.
D. If there had been any openings for supervisors at other work locations, her supervisor would have been moved. She’ll just have to tough it out with the longer commute. Maybe later she can get a job at the original work location when something opens up.
Answers
1. C. Safety should be a concern and responsibility of every management person in the organization. There should be a plan or schedule for regular safety inspections and action plans should be developed for hazards discovered.
2. B. Unless state law or union agreement requires a copy be given to the employee, supervisor documentation is considered to be an employer-owned record of the conversation. It should be filed in the employee’s personnel file along with other performance-related documents such as appraisals and commendations. In some jurisdictions, a copy must be given to the employee if the employee signs the document.
3. A. If the complaint claims an employment penalty caused by membership in a protected group, and that people not in that group were given better treatment, the complaint seems valid on its surface (at first glance). It should be investigated to see if the facts support the employee’s charges.
4. C. Asking for feedback about the instructions is necessary to be sure Andre’s message has been received as it was intended. If Andre puts his instructions on paper as a follow-up, he can help the employee recall each unusual requirement for the order. Hovering over the employee as the order is processed would probably not be a good idea. Waiting until the order is completed means any problems would require that someone do the work all over again.
5. C. Both B and C are good answers, but for assurance that all the key information is conveyed successfully, each of the basic five questions should be addressed in her presentation. A simple fact sheet could be used if it contained the answers to all five of these questions.
6. D. Any employer subject to the Americans with Disabilities Act (ADA) would be well served to include physical and mental job requirements in each job description. When asked for a job accommodation, the job description can be helpful in determining how an accommodation will assist in accomplishing job responsibilities. While including them is not a federal requirement (nor is it required that job descriptions be created), stating the job requirements can be a good management tool.
7. B. If the supervisor doesn’t know what the new employee will be expected to do, how can someone be hired to do the job? The supervisor should decide what responsibilities will be assigned to the new position and help Hilario describe that in a written document. That will be an aid in selecting someone to fill the position.
8. A. Pension plans are important to employees. Any changes in those plans will be seen as having important personal impact by all affected workers. It is likely that the HR Manager will need to work with senior management to coordinate the announcement of any pension plan changes. Because the rumor exists, she should encourage a swift response with facts so workers will have accurate information.
9. B. There is no requirement for records to be locked up, but best practice says that it is a good idea. Medical records, including disability information, should be kept separate from personnel files. Investigation records should be created when necessary and kept separate from other employee records. Electronic files should be treated in the same way.
10. A. This is confidential information and it should probably not be transmitted by e-mail. Calling each employee will take a great deal of time and verbal corrections are subject to errors. By far, the best practice would be to send a confidential copy of the employee’s record for review with an invitation to submit corrections or additions.
11. B. Federal regulations (41 CFR 60-1.12(e)) provide, “Where the contractor has destroyed or failed to preserve records as required by this section, there may be a presumption that the information destroyed or not preserved would have been unfavorable to the contractor.” The CEO should be made aware that illegal discrimination can be expensive to remedy.
12. B. Liability exists from day one of operations. Non-profits are not exempt from OSHA rules, and there is no grace period offered by federal regulations.
13. D. The most reliable method is to have supervisors identify who among their group is present in the emergency evacuation location. Supervisors know who is working and who is off for vacation, illness, and so on. They should be able to accurately identify anyone missing from the muster point. If people are identified as missing, first responders should be notified.
14. A. It is important to engage Bill in a conversation about his medical restrictions and ask him how he thinks he can do the job within those restrictions. Seeking an honest outcome is the goal. Determining what to do with him before such a conversation will likely risk undesirable outcomes.
15. C. Passwords are sensitive enough that they deserve to be locked up all the time. Leaving them on the desk or monitor invites security problems.
16. D. Anyone who appears impaired physically or mentally should be taken to the employer’s physician for a drug and alcohol screen. They should not be permitted to remain at work until that has been accomplished. Depending on the outcome of the testing, the employer may decide on discipline or some other treatment. Under no circumstances should someone who is impaired be allowed to drive home or to the doctor. If the supervisor can’t take them, call a taxi.
17. A. It’s always a good idea to confirm the evidence is accurate before taking action. Embezzlement is a criminal problem and should be turned over to the local police. Arrange a meeting with the employee and have the police present. Explain the evidence and ask for the employee’s admission to the embezzlement. Ask the police to arrest the employee. If you have insurance covering such issues, you can file a claim for the missing funds.
18. D. When a policy is broken by employees, there should be proper progressive disciplinary procedures used to correct the situation. It is difficult to prevent people from bringing their cell phones to work. However, controlling how they are used during work time is a different matter.
19. A. Determining what is causing the attendance problem will help in determining how to manage it. Sick spouses, children, or even aging parents can suddenly create care-giving circumstances that hadn’t been anticipated. Attendance policies are important, but so are an employee’s personal needs. If it is possible, Alden should identify the root of the problem before taking action.
20. C. Listing evaluation criteria will include identifying milestones and costs as evaluation items. Determining how responses will be evaluated will make the sorting and selection of a benefit consultant easier and more accurate. Writing an RFP in such a way that only one consultant will qualify may be okay for this project, but the organization will soon get a reputation among vendors and service providers that will limit participation in future RFPs.
21. A. A properly developed job description is a good communication tool that helps with hiring and with firing. It helps defend the employer when essential duties may not be ignored during job accommodation discussions. It also helps physicians understand physical and mental job requirements when evaluating workers’ compensation issues or return to work.
22. C. A valid safety program will include all of the OSHA-specified content and involve supervisors directly in the process. Injuries and illnesses can make the supervisors’ job more difficult because of employee absences. Controlling workplace injury and illness is beneficial to everyone, employees and supervisors alike.
23. B. A prima facie case requires a statement of employment penalty, a statement of membership in a protected group, and a statement that people outside that group are treated differently in similar circumstances. Do everything possible to keep the complaint internal and not in a government enforcement agency such as the EEOC. Because the complaint is about Damion’s supervisor, talking with the supervisor initially is not a good idea.
24. C. Liability for oral contracts made by recruiters or other selecting managers can cost an employer a great deal of money. It is best to say, simply, we have no guarantees of long-term (or lifetime) employment.
25. A. Forcing an employee to endure additional penalties (moving to a job farther away) can be considered retaliation for the original complaint. If anyone moves, it should be the supervisor. Of course any action should depend upon the results of a thorough investigation, but imposing additional negative treatment on the employee is not a good idea.
Endnotes
1. Roughly 600,000 employers are federal contractors or subcontractors, subject to affirmative action requirements. According to the Bureau of the Census, there are more than 6,000,000 employers in the United States (organizations with payroll). Overall, there are nearly 28,000,000 non-employers in the United States. These are business firms with no payroll—nearly always, single entrepreneurs.
2. 29 CFR 1910.1200
3. 60-741.44(c)
4. 41 CFR 60–2.17(b)(2)
5. 54:3904–3916
6. “International Standards Organization” website as of July 11, 2013, www.iso.org/iso/home/standards/management-standards/iso14000.htm.
7. “How Many People Use the Top Social Media, Apps & Services,” July 14, 2013, Craig Smith, Digital Marketing Ramblings blog. Retrieved on February 8, 2014 from http://expandedramblings.com/index.php/resource-how-many-people-use-the-top-social-media/.
8. “SHRM Code of Ethics,” November 16, 2007, www.shrm.org/about/pages/code-of-ethics.aspx.
9. Public Employee Privacy Expectations, City of Ontario, California vs. Quon, No. 08–1332, June 17, 2010, www.supremecourt.gov/opinions/09pdf/08-1332.pdf.
10. States with laws barring employers from demanding social media account passwords from employees or job applicants as of January 2013 include: California, Delaware, Illinois, Maryland, Michigan, and New Jersey. Wired Magazine, www.wired.com/threatlevel/2013/01/password-protected-states/.
11. NLRB Case Ruling, Hispanics United of Buffalo, Inc. and Carlos Ortiz. Case 03–CA–027872.
