

Lab environment overview
This chapter describes the configuration of the IBM LinuxONE lab environment that was used for demonstrating FUJITSU Enterprise Postgres 12 use cases in this publication, which includes:
•A FUJITSU Enterprise Postgres Database that was installed on IBM LinuxONE in the following ways:
– Stand-alone IBM z/VM virtual servers running SUSE Enterprise Linux Server 12 SP4 and Red Hat Enterprise Linux Server 8.2 operating systems (OSs).
– High availability (HA) configurations of the same.
– Stand-alone and HA configurations, such as Red Hat OpenShift operators. This configuration leveraged Red Hat CoreOS.
•Implementing backups for FUJITSU Enterprise Postgres Database by using native database tools and with IBM Spectrum Protect.
•FUJITSU Enterprise Postgres integration with IBM LinuxONE hardware security module (HSM) for Transparent Data Encryption (TDE).
•Steps to install a stand-alone FUJITSU Enterprise Postgres 12 server on Red Hat Enterprise Linux Server 8 and SUSE Linux Enterprise Servers 12 SP4.
This chapter covers the following topics:
3.1 Overview
The lab environment that was configured for this publication included 22 Linux guests on four z/VM logical partitions (LPARs) running on two different types of IBM LinuxONE servers.
LPARs ARIES32, ARIES33, and ARIES34 were z/VM LPARs running on an IBM LinuxONE III multi-frame server. LPAR LEPUS23 was a z/VM LPAR running on an IBM LinuxONE Rockhopper II server. All four LPARs were running z/VM 7.1 as the first-level OS and hypervisor.
Across ARIES32, ARIES34, and LEPUS23, eight Linux guests were installed with Red Hat Enterprise Linux 8.2 and nine Linux guests were installed with SUSE Enterprise Linux Server 12 SP4. ARIES 33 consisted of seven Linux guests that were dedicated to hosting the Red Hat OpenShift environments that were configured with Red Hat CoreOS.
LPAR LEPUS23 was dedicated to hosting the management functions that are required for the various use cases, such as the Client App server, which was used to emulate client traffic to any of the FUJITSU Enterprise Postgres Database as needed.
Regarding HA and disaster recovery (DR) use cases, it was important to ensure that the lab environment delivered a valid and easily referenced HA configuration. The hardware partitioning capabilities that use PR/SM and z/VM deliver Evaluation Assurance Level (EAL) 5+ isolation to the virtual servers on an IBM LinuxONE.
EAL5+ isolation is equivalent to two physically separate mid-range or commodity servers that are deployed in independent racks. Viewed from the Linux OS, each guest can be treated as a separate physical serve with its own processor, memory, storage, and network resources. This isolation enabled the Lab environment to emulate FUJITSU Enterprise Postgres 12 servers being deployed on multiple IBM LinuxONE servers and across multiple data centers.
Figure 3-1 on page 83 demonstrates the layout for all guests that were deployed for this publication on different LPARs and IBM LinuxONE servers.

Figure 3-1 Linux guests layout
3.1.1 High availability lab environment for FUJITSU Enterprise Postgres 12 on Red Hat Enterprise Linux 8
Five Red Hat Enterprise Linux 8 guests were used to establish a HA lab for the FUJITSU Enterprise Postgres 12 databases, with a primary server running on LPAR ARIES32, and a secondary server running on LPAR ARIES34 to emulate two physically separate servers that used EAL5+ isolation.
The Arbitration Server that is used in maintaining HA database configurations must be deployed on an independent LPAR from that of both the primary and secondary databases to prevent a split-brain scenario, which is described in Chapter 5, “High availability and high reliability architectures” on page 165. The Arbitration Server was deployed on LEPUS23 on the second IBM LinuxONE server.
All use cases covering FUJITSU Enterprise Postgres 12 server’s HA, disaster preparedness, backup and recovery, and replication modes with Red Hat Enterprise Linux 8 were set up and run within the lab environment that is shown in Figure 3-2.

Figure 3-2 High availability lab environment with FUJITSU Enterprise Postgres 12 on Red Hat Enterprise Linux 8
Another secondary database server was also deployed on LPAR ARIES32 to use in horizontal scaling use cases.
3.1.2 High availability lab environment for FUJITSU Enterprise Postgres 12 on SUSE Linux Enterprise Server 12 SP4
Five SUSE Linux Enterprise Server 12 SP4 guests were used to establish a HA lab for FUJITSU Enterprise Postgres 12 with a primary server running on LPAR ARIES32 and a secondary server running on LPAR ARIES34 to emulate two physically separate servers that used EAL5+ isolation.
The Arbitration Server that was used in maintaining HA database configurations must be deployed on an independent LPAR from that of both the primary and secondary databases to prevent a split-brain scenario, which is described in Chapter 5, “High availability and high reliability architectures” on page 165. The Arbitration Server was deployed on LEPUS23 on the second IBM LinuxONE server.
All use cases covering FUJITSU Enterprise Postgres 12 server’s HA, disaster preparedness, backup and recovery, and replication modes with SUSE Linux Enterprise Server 12 SP4 were set up and run within the lab environment that is shown in Figure 3-3 on page 85.
Another secondary database server was also deployed on LPAR ARIES32 for use in horizontal scaling use cases.

Figure 3-3 High availability lab environment with FUJITSU Enterprise Postgres 12 on SUSE Linux Enterprise Server 12 SP4
For more information about the HA configurations that were used and supported on IBM LinuxONE, see Chapter 5, “High availability and high reliability architectures” on page 165.
3.1.3 Security feature lab environment for FUJITSU Enterprise Postgres 12 on Red Hat Enterprise Linux 8
Two Red Hat Enterprise Linux 8 guests with dedicated HSMs were used to establish a security feature lab environment for FUJITSU Enterprise Postgres 12 servers, with a primary server running on LPAR ARIES32 and a secondary server running on LPAR ARIES34.
Four CryptoExpress7S cards were dedicated to each Red Hat Enterprise Linux 8 guest. Each CryptoExpress7S card can be customized as two separated HSM engines with different types. In our lab environment, the four dedicated cards were configured as two EP11, four Common Cryptographic Architecture (CCA), and two accelerator engines, for each guest.
The use cases for FUJITSU Enterprise Postgres 12 server’s HSM-related security features with Red Hat Enterprise Linux 8 were set up and run on the lab environment that is shown in Figure 3-4 on page 86.
Although the HSM Accelerator engine was configured in this environment, FUJITSU Enterprise Postgres does not support or leverage this feature. The Accelerator is required for other functions that are performed at the z/VM and OS level, such as secure networking (TLS and Secure Sockets Layer (SSL)), and secure directory services connectivity.
|
Note: Because there is no material difference between a Red Hat Enterprise Linux server guest and a SUSE Linux guest when it comes to configuring and using the HSM, the lab environment and security use cases that are covered in this book refer only to Red Hat Enterprise Linux virtual servers.
|

Figure 3-4 Security feature lab environment for FUJITSU Enterprise Postgres 12 on Red Hat Enterprise Linux 8
In addition, five smart cards were used to load the HSM master keys for the EP11 certificate authority (CA), EP11 Admin, and the Trusted Key Entry (TKE) Administrator, with each smart card configured as follows:
•EP11 CA.
•EP11 CA backup (optional but recommended).
•EP11 Admin 1.
•EP11 Admin 2.
•TKE Administrator: Initially set up when the TKE was first used for generating CCA keys. Although only a single card was used for the lab environment, a backup card is recommended for client environments.
In a client environment, the number of smart cards that are used depends on the number of HSM engines that are required for HA in production/DR environments, and the requisite number of independent key parts for organizational security, for example, the minimum number of authorized individuals that are required to create/update MEKs on the HSM.
CryptoExpress7S feature configuration
Using the Cryptographic Management task on the IBM LinuxONE III Support Element (SE) GUI, a list of CryptoExpress feature cards that are installed on the IBM LinuxONE server with their configuration data is shown in Figure 3-5.

Figure 3-5 IBM LinuxONE III cryptographic management task GUI
Each row in the Cryptographic Card Data table shows a CryptoExpress coprocessor with a unique value for the physical channel identifier (PCHID) and number. Also shown are the configured operation types for each coprocessor. For example, the type of coprocessor whose number is '02 is configured as a CCA coprocessor.
The relationship between coprocessors and physical feature cards is indicated by the Card Location and Card Serial Number, where the same location and serial number indicate the same physical feature card. For example, coprocessors numbers 06 and 07 are on the same physical CryptoExpress7S card in B25BLG10, with the serial number YJ1093AABFVD.
When using the Cryptographic Configuration GUI task, the type of coprocessor can be changed by selecting the corresponding coprocessor from the list, and then clicking Crypto Type Configuration, as shown in Figure 3-6.

Figure 3-6 Cryptographic configuration GUI task
The correct configuration of coprocessor types for installed physical feature cards can achieve high resiliency, availability, and serviceability (RAS) at the hardware component level.
To showcase this RAS, four physical CryptoExpress7S cards from different locations, each with two coprocessors configured as different types, were selected for the lab environment. This level of redundant configuration ensured that an unplanned outage of any one physical card did not lead to a complete loss of any type of coprocessors.
For example, in the event of a loss of the CryptoExpress7S card at B17BLG20, the lab environment loses access to CCA coprocessor number 00 and accelerator number 01, but still has CCA coprocessor number 03 and accelerator number 04.
CryptoExpress card allocation to logical partitions
|
Note: During the initial build of our lab environment, some HSM configuration screen captures for LPARs ARIES32 and ARIES34 were not captured. As a result, a new LPAR ARIES22 was configured specifically to capture screen captures.
|
Assignment of the CryptoExpress cards to specific LPARs is initiated by clicking Change LPAR Cryptographic Controls task from the IBM LinuxONE III SE, selecting the LPAR (ARIES22) from the target object selection list, and clicking OK, as shown in Figure 3-7 on page 89.

Figure 3-7 Change LPAR Cryptographic Controls view
The Change LPAR Cryptographic Controls: ARIES22(Active) - ARIES2 opens (Figure 3-8). The first step to assigning HSMs to an LPAR is to configure cryptographic domains to the LPAR. Add a control or control and usage domain to the LPAR by selecting Assigned Domains → Select Actions.

Figure 3-8 Adding a domain to an LPAR view
Select Domain Type → Control and Usage to change Domain 10 to one of the usage domains of LPAR ARIES22 for cryptographic functions (Figure 3-9). An LPAR's control domains are the cryptographic domains for which remote secure administration functions can be established and administered from the LPAR.

Figure 3-9 Adding a domain to an LPAR
Assign coprocessors to the LPAR by selecting Select Actions in the Assigned Cryptos pane in the Change LPAR Cryptographic Controls: ARIES22(Active) - ARIES22 window (Figure 3-10).
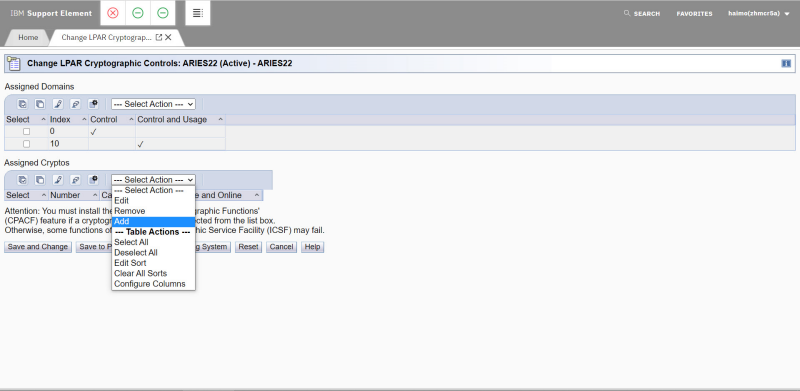
Figure 3-10 Adding crypto to LPAR-1
As shown in Figure 3-11, cryptos 0 - 7 were added to LPAR ARIES22 by selecting Candidate and Online in the Crypto type pane. Those crypto coprocessors will be assigned and brought online at the next activation of the LPAR. The Candidate option indicates that those crypto coprocessors will be assigned to the LPAR but must be activated manually when needed (for example, spare cards).

Figure 3-11 Adding crypto to LPAR-2
In the Change LPAR Cryptographic Controls: ARIES22(Active) - ARIES22 window, you can review the current assigned domains and crypto coprocessors to LPAR ARIES22 and modify the assignments as needed by clicking Select Action, and then clicking Edit, Remove, or Add under the Assigned Domains and Assigned Cryptos panes.
Click Save to Profiles to save any changes to the LPAR's profile, with the changes coming into effect when the LPAR is next activated or restarted. Clicking Change Running System applies the changes immediately without saving them to the LPAR's profile, which means these changes are when the LPAR is next activated or restarted.
For this environment, we clicked Save and Change as shown in Figure 3-12 to save the changes in LPAR ARIES22's profile and immediately applied the changes.

Figure 3-12 Save and Change to LPAR cryptographic control: 1 of 2
As shown in Figure 3-13, the newly added crypto coprocessors 00 - 07 were assigned to LPAR ARIES22 with a Stopped status, which means the coprocessors must be brought online manually before the OS can see and use them.

Figure 3-13 Save and Change to LPAR cryptographic control: 2 of 2
Select all the crypto coprocessors of LPAR ARIES22, click Configure On/Off task, and then select Select Action → Toggle All Online to simultaneously activate all coprocessors, as shown in Figure 3-14 on page 93.

Figure 3-14 Configuring LPAR crypto online: 1 of 2
Verify that the crypto ID, LPAR name and Desired Status are correct, as shown in Figure 3-15, and then to click OK.

Figure 3-15 Configuring LPAR crypto online: 2 of 2
Figure 3-16 shows cryptos 00 - 07 of LPAR ARIES22 all showing the Operating status and in the Online state.

Figure 3-16 Configuring LPAR crypto online
Figure 3-17 shows an example of the crypto and domain assign settings of LPAR ARIES 32, where cryptos 00 - 07 are assigned, but only 00 - 04 are in use. Domains 34, 44, and 54 are assigned as Control and Usage domains for the LPAR, and domain 34 is dedicated to our RHLE8 instance for the TDE use cases.

Figure 3-17 Crypto settings of LPAR ARIES32
3.1.4 Red Hat OpenShift lab environment for FUJITSU Enterprise Postgres 12
Seven Red Hat Enterprise Linux CoreOS (RHCOS) guests were set up for the use cases demonstrating FUJITSU Enterprise Postgres 12 databases that were deployed as Red Hat OpenShift Operators with the installation running on LPAR ARIES33 (Figure 3-18). For more information about containerization use cases, see Chapter 10, “FUJITSU Enterprise Postgres cluster on Red Hat OpenShift Container Platform” on page 373.

Figure 3-18 Red Hat OpenShift lab with FUJITSU Enterprise Postgres 12 on Red Hat Enterprise Linux CoreOS
3.1.5 Application development feature lab environment with FUJITSU Enterprise Postgres 12
One Red Hat Enterprise Linux 8 guest and one SUSE Linux Enterprise Server 12 SP4 guest is set up for use cases demonstrating FUJITSU Enterprise Postgres 12 server’s application development features and installation running on LPAR ARIES32. Our environment is shown in Figure 3-19.

Figure 3-19 Application development feature lab environment with FUJITSU Enterprise Postgres 12
3.1.6 Summary of lab environment
Our lab environment is summarized in Table 3-1 on page 97 and sorted by server name and LPAR.
Table 3-1 Lab environment summary by IBM LinuxONE servers and logical partitions.
|
IBM LinuxONE server
|
LPAR
|
Guest
|
Lab environment
|
|
IBM LinuxONE III Multi Frames
|
ARIES32
|
RDBKGR1
|
HA on Red Hat Enterprise Linux 8
|
|
RDBKGR2
|
|||
|
RDBKGR3
|
Application Development Feature on Red Hat Enterprise Linux 8
|
||
|
RDBKGR4
|
Security Feature on Red Hat Enterprise Linux 8
|
||
|
RDBKGS1
|
HA on SUSE Linux Enterprise Server 12 SP4
|
||
|
RDBKGS2
|
|||
|
RDBKGS3
|
Application Development Feature on SUSE Linux Enterprise Server 12 SP4
|
||
|
ARIES34
|
RDBKGR5
|
Security Feature on Red Hat Enterprise Linux 8
|
|
|
RDBKGR6
|
HA on Red Hat Enterprise Linux 8
|
||
|
RDBKGS5
|
Security Feature on SUSE Linux Enterprise Server 12 SP4
|
||
|
IBM LinuxONE Rockhopper II
|
LEPUS23
|
RDBKGR7
|
HA on Red Hat Enterprise Linux 8
|
|
RDBKGR8
|
|||
|
RDBKGS7
|
HA on SUSE Linux Enterprise Server 12 SP4
|
||
|
RDBKGS8
|
Table 3-2 summarizes our lab environment, which is sorted by the environment and type of server.
Table 3-2 Lab environment summary by lab environment
|
Lab environment
|
IBM LinuxONE server
|
LPAR
|
Guest
|
Environment highlights
|
|
HA on Red Hat Enterprise Linux 8
|
IBM LinuxONE III
Multi Frames
|
ARIES32
|
RDBKGR1
|
|
|
RDBKGR2
|
||||
|
ARIES34
|
RDBKGR6
|
|||
|
IBM LinuxONE Rockhopper II
|
LEPUS23
|
RDBKGR7
|
||
|
RDBKGR8
|
||||
|
HA on SUSE Linux Enterprise Server 12 SP4
|
IBM LinuxONE III
Multi Frames
|
ARIES32
|
RDBKGS1
|
|
|
RDBKGS2
|
||||
|
ARIES34
|
RDBKGS6
|
|||
|
IBM LinuxONE Rockhopper II
|
LEPUS23
|
RDBKGS7
|
||
|
RDBKGS8
|
||||
|
Security Feature on Red Hat Enterprise Linux 8
|
IBM LinuxONE III
Multi Frames
|
ARIES32
|
RDBKGR4
|
4x dedicated CryptoExpress7S cards customized as 8x separated HSM engines.
|
|
ARIES34
|
RDBKGR5
|
4x dedicated CryptoExpress7S cards customized as 8x separated HSM engines.
|
||
|
Security Feature on SUSE Linux Enterprise Server 12 SP4
|
IBM LinuxONE III
Multi Frames
|
ARIES32
|
RDBKGS4
|
|
|
ARIES34
|
RDBKGS5
|
|||
|
Application Development Feature on RHLE8
|
IBM LinuxONE III
Multi Frames
|
ARIES32
|
RDBKGR3
|
HA on SUSE Linux Enterprise Server 12 SP4.
|
|
Application Development Feature on SUSE Linux Enterprise Server 12 SP4
|
IBM LinuxONE III
Multi Frames
|
ARIES32
|
RDBKGS3
|
|
3.2 FUJITSU Enterprise Postgres 12 server installation on LinuxONE
In this section, we describe the steps to install a stand-alone FUJITSU Enterprise Postgres 12 Advanced Edition server on Red Hat Enterprise Linux 8 and SUSE Linux Enterprise Server 12 SP4 virtual machines (VMs) in IBM LinuxONE III.
3.2.1 Prerequisites
In this section, we describe the hardware and operating requirements for the installation.
Hardware prerequisites
•Memory: At least 512 MB of memory is required.
•HSM: If TDE is used with an HSM, then IBM Z Crypto Express adapter must support either the CCA coprocessor or the EP11 coprocessor.
•A minimum of 500 MB of disk space.
•Recommended file system: ext4.
|
Note: In the use cases that are described in this publication, it is presumed that the reader is familiar with the stand-alone installation steps that are described in this section.
|
OS prerequisites
Table 3-3 on page 99 provides the list of packages that are required for operations on Red Hat Enterprise Linux 8. Some of the packages are required for specific operations, as listed in the Description column.
Table 3-3 FUJITSU Enterprise Postgres 12 Advanced Edition prerequisite packages on Red Hat Enterprise Linux 8
|
Package name
|
Description
|
|
alsa-lib
|
|
|
audit-libs
|
|
|
cyrus-sasl-lib
|
|
|
pcp-system-tools
|
Required when using parallel scan.
|
|
glibc
|
|
|
libnsl2
|
|
|
libicu
|
Provides collation support.
|
|
Install 60.x.
|
|
|
libgcc
|
|
|
libmemcached
|
Required when using Pgpool-II.
|
|
libstdc++
|
|
|
libtool-ltdl
|
Required when using Open Database Connectivity (ODBC) drivers.
|
|
llvm
|
Version 8.0.x of llvm is required to run SQL with runtime compilation (just-in-time (JiT) compilation). Install llvm-libs from Application Streams.
FUJITSU Enterprise Postgres 12 uses runtime compilation by default. If you do not want to use runtime compilation, turn off the jit parameter in postgresql.conf. You do not need to install llvm if you turn off the jit parameter.
Installing llvm without turning off the jit parameter might result in an error when running SQL.
Note: If JIT compilation that uses llvm is performed on Red Hat Enterprise Linux 8, a verbose server message is logged one or more times on first query execution for each associated database connection:
<Message>
ORC error: No callback manager available for s390x-ibm-linux
This error message results from a known deficiency in one of the features of the LLVM library for IBM Z, but this feature is not used by the server and the error does not otherwise affect LLVM operation.
To prevent this message from being logged, JIT compilation can be disabled by turning of the value of the configuration variable jit.
|
|
ncurses-libs
|
|
|
net-tools
|
|
|
nss-softokn-freebl
|
|
|
opencryptoki
|
Required if TDE is used with an HSM. Install 3.12.1 or later into the default directory.
|
|
pam
|
Required when using PAM authentication.
|
|
perl-libs
|
Required when using PL/Perl. Install 5.26.
|
|
python3
|
Required when using PL/Python based on Python 3. Install 3.7.x.
|
|
redhat-lsb
|
|
|
libselinux
|
Required for sepgsql.
|
|
tcl
|
Required when using PL/Tcl. Install 8.6.
|
|
unzip
|
|
|
xz-libs
|
|
|
zlib
|
|
|
java-1.8.0-openjdk
|
Required when using database multiplexing and WebAdmin. Use build 1.8.0_222-b10 or later for the S390x architecture.
|
Table 3-4 provides the list of packages that are required for operations on SUSE 12. Some of the packages are required for specific operations, as listed in the Description column.
Table 3-4 FUJITSU Enterprise Postgres 12 Advanced Edition prerequisite packages on SUSE 12
|
Package name
|
Description
|
|
alsa-lib
|
|
|
audit-libs
|
|
|
dstat
|
Required when using parallel scan.
|
|
glibc
|
|
|
libgcc
|
|
|
libicu
|
Provides collation support. Install 52.
|
|
libmemcached
|
Required when using Pgpool-II.
|
|
libstdc++
|
|
|
libtool-ltdl
|
Required when using ODBC drivers.
|
|
llvm
|
Install Version 7.0.x of llvm to run SQL with runtime compilation (JiT compilation) and add the directory where the shared library libLLVM -*.so is located next to the environment variable LD_LIBRARY_PATH.
FUJITSU Enterprise Postgres 12 uses runtime compilation by default. If you do not want to use runtime compilation, turn off the jit parameter in postgresql.conf. You do not need to install llvm if you turn off the jit parameter.
Failure to install llvm without turning off the jit parameter might result in an error when run SQL.
|
|
LLVM-libs
|
Install version 7.0.x. (*1).
|
|
ncurses-libs
|
|
|
net-tools
|
|
|
nss-softokn-freebl
|
|
|
opencryptoki
|
Required if TDE is used with an HSM. Install 3.10 or later into the default directory.
|
|
pam
|
Required when using PAM authentication.
|
|
perl-libs
|
Required when using PL/Perl. Install 5.18.
|
|
python3
|
Required when using PL/Python based on Python 3. Install 3.7.x.
|
|
sysstat
|
Required when using the pgx_fjqssinf command. Set up the sar command after installation.
|
|
tcl
|
Required when using PL/Tcl. Install 8.6.
|
|
xz-libs
|
|
|
zlib
|
|
|
java-1.8.0-openjdk
|
Required when using database multiplexing and WebAdmin. Use build 1.8.0_181-b13 or later for the S390x architecture.
|
Next, we describe the step by step installation procedure on Red Hat Enterprise Linux 8 and SUSE Linux Enterprise Server 12.
3.3 Installing and configuring a stand-alone database instance on a Red Hat Enterprise Linux 8 guest
To install and configure a stand-alone database instance on a Red Hat Enterprise Linux 8 Linux guest, complete the following steps:
1. Run the following commands to install the international components for Unicode libraries through libicu. Also, install the library libns, which provides a transport layer interface to the networking services.
# yum install libnsl
# yum install libicu
2. Next, set up JAVA_HOME. For this example, we used OpenJDK Version 1.8.0 and used the following command:
#export JAVA_HOME="/usr/lib/jvm/java-1.8.0-openjdk-1.8.0.265.b01-0.el8_2.s390x/jre"
3. Mount the FUJITSU Enterprise Postgres 12 Advanced Edition ISO and start the installation as shown in Example 3-1.
Example 3-1 Mounting the ISO
#mount -t iso9660 -r -o loop /fep12iso/fsep12_ae_linux64.iso /mnt2
#cd /mnt2/SERVER/Linux/packages/r80s390x
# rpm -ivh FJSVfsep-SV-12-1200-0.el8.s390x.rpm
Verifying... ################################# [100%]
Preparing... ################################# [100%]
Updating / installing...
1:FJSVfsep-SV-12-1200-0.el8 ################################# [100%]
4. Install the WebAdmin component of the FUJITSU Enterprise Postgres, as shown in Example 3-2. WebAdmin provides an easy way to create and manage FUJITSU Enterprise Postgres clusters by using a GUI.
Example 3-2 Installing WebAdmin
#mount -t iso9660 -r -o loop /fep12iso/fsep12_ae_linux64.iso /mnt2
#cd /mnt2/WEBADMIN/Linux/packages/r80s390x
# rpm -ivh FJSVfsep-WAD-12-1200-0.el8.s390x.rpm
Verifying... ################################# [100%]
Preparing... ################################# [100%]
Updating / installing...
1:FJSVfsep-WAD-12-1200-0.el8 ################################# [100%]
5. This step is optional for a stand-alone installation because Mirroring Controller (MC) is required in HA implementations that have more than one database server that is configured as the primary and standby. Run the command shown in Example 3-3 if there is a requirement to convert this installation into a HA implementation in the future.
Example 3-3 Installing Mirroring Controller
#/opt/fsepv12server64/bin/mc_update_jre_env
INFO: /usr/lib/jvm/java-1.8.0-openjdk-1.8.0.265.b01-0.el8_2.s390x/jre/lib/s390x/server/libjvm.so is in use.
6. Create the database administrator user ID fsepuser, and set the password to fsepuser by using the following commands:
#useradd -m fsepuser
#passwd fsepuser
7. After the user ID is created, prepare the directories (see Example 3-4 on page 103) to store the FUJITSU Enterprise Postgres binary files, transaction logs, and backup files. Figure 3-20 shows the components that should be logically placed in directories and different types of storage devices for performance and reducing I/O bottlenecks.
|
Note: For more information about estimating disk space requirements, see Appendix E, “Estimating Database Disk Space Requirements” in FUJITSU Enterprise Postgres 12 Installation and Setup Guide for Server.
|

Figure 3-20 Server resource for FUJITSU Enterprise Postgres
Example 3-4 Preparing the directories
# mkdir -p /database/inst1
# chown -R fsepuser:fsepuser /database
# chmod 700 /database/inst1
# mkdir -p /transaction/inst1
# chown -R fsepuser:fsepuser /transaction
# chmod 700 /transaction/inst1
# mkdir -p /backup/inst1
# chown -R fsepuser:fsepuser /backup
# chmod 700 /backup/inst1
8. To enable communication, grant access to the ports 27500, 27515, 27516, 27540, and 27541 by editing the fsep.xml file (Example 3-5).
Port 27500 is used by FUJITSU Enterprise Postgres, ports 27515 and 27516 are used by WebAdmin, and ports 27540 and 27541 are used by the MC.
Example 3-5 Granting access to the ports
# vim /etc/firewalld/services/fsep.xml
# cat /etc/firewalld/services/fsep.xml
<?xml version="1.0" encoding="utf-8"?>
<service>
<short>FSEP12</short>
<description>FUJITSU Enterprise Postgres Database Server</description>
<port protocol="tcp" port="27500"/>
<port protocol="tcp" port="27515"/>
<port protocol="tcp" port="27516"/>
<port protocol="tcp" port="27540"/>
<port protocol="tcp" port="27541"/>
</service>
# firewall-cmd --reload
# firewall-cmd --get-services | grep fsep
# firewall-cmd --permanent --zone=public --add-service=fsep
# firewall-cmd --reload
# firewall-cmd --list-all | grep fsep
9. Configure the environment variables, as shown in Example 3-6.
Example 3-6 Configuring the environment variables
# su - fsepuser
$ PATH=/opt/fsepv12server64/bin:$PATH ; export PATH
$ MANPATH=/opt/fsepv12server64/share/man:$MANPATH ; export MANPATH
$ LD_LIBRARY_PATH=/opt/fsepv12server64/lib:$LD_LIBRARY_PATH ; export LD_LIBRARY_PATH
Example 3-7 Creating the database instance
$ initdb -D /database/inst1 --waldir=/transaction/inst1 --lc-collate="C" --lc-ctype="C" --encoding=UTF8
The files belonging to this database system will be owned by user "fsepuser".
This user must also own the server process.
The database cluster will be initialized with locales
COLLATE: C
CTYPE: C
MESSAGES: en_US.UTF-8
MONETARY: en_US.UTF-8
NUMERIC: en_US.UTF-8
TIME: en_US.UTF-8
The default text search configuration will be set to "english". (15541)
Data page checksums are disabled. (18153)
fixing permissions on existing directory /database/inst1 ... ok (15516)
fixing permissions on existing directory /transaction/inst1 ... ok (15516)
creating subdirectories ... ok (15516)
selecting dynamic shared memory implementation ... posix
selecting default max_connections ... 100
selecting default shared_buffers ... 128MB
selecting default time zone ... (19842)America/New_York
creating configuration files ... ok (15516)
running bootstrap script ... ok (15516)
performing post-bootstrap initialization ... ok (15516)
syncing data to disk ... ok (15516)
initdb: warning: enabling "trust" authentication for local connections
You can change this by editing pg_hba.conf or using the option -A, or
--auth-local and --auth-host, the next time you run initdb.
Success. You can now start the database server using:
pg_ctl -D /database/inst1 -l logfile start
11. Now that the first database instance is created, configure the instance to accept remote connections, as shown in Example 3-8. By default, FUJITSU Enterprise Postgres allows connections only from the local machine where the database server is installed. You also need to turn on the logging collector to capture the log messages into the log files. This parameter can be set only at the server start.
Example 3-8 Configuration file modifications
$ vim /database/inst1/postgresql.conf
listen_addresses = '*'
port = 27500
logging_collector = on
12. Configure the host-based authentication by setting up the pg_hba.conf file (Example 3-9). The parameters in pg_hba.conf control the authentication process in PostgreSQL and in FUJITSU Enterprise Postgres.
Example 3-9 Configuring host-based authentication
$ vim /database/inst1/pg_hba.conf
host all all xxx.xx.xx.0/24 trust
With this configuration, all the connections originating from the xxx.xx.xx.0 network can access the stand-alone database instance inst1. Make sure that you provide the accurate network range in place of xxx.xx.xx.0/24.
|
Note: FUJITSU Enterprise Postgres supports several authentication methods, including TRUST, IDENT, PEER, Generic Security Standard Application Programming Interface (GSSAPI), LDAP, Salted Challenge Response Authentication Mechanism (SCRAM), SHA-256, MD5, and password. For more information about host-based authentication methods, see 4.4, “FUJITSU Enterprise Postgres encryption on IBM LinuxONE with crypto cards” on page 126.
|
13. Start the database instance inst1 on the stand-alone database server. The command and output are shown in Example 3-10.
Example 3-10 Starting the database instance
$ pg_ctl start -D /database/inst1
waiting for server to start....2020-12-25 00:19:37.058 EST [2154304] LOG: starting PostgreSQL 12.1 on s390x-ibm-linux-gnu, compiled by gcc (GCC) 8.3.1 20190507 (Red Hat 8.3.1-4), 64-bit
2020-12-25 00:19:37.060 EST [2154304] LOG: listening on IPv4 address "0.0.0.0", port 27500
2020-12-25 00:19:37.060 EST [2154304] LOG: listening on IPv6 address "::", port 27500
2020-12-25 00:19:37.061 EST [2154304] LOG: listening on Unix socket "/tmp/.s.PGSQL.27500"
2020-12-25 00:19:37.067 EST [2154304] LOG: redirecting log output to logging collector process
2020-12-25 00:19:37.067 EST [2154304] HINT: Future log output will appear in directory "log".
done
server started
14. After the database instance starts, verify the connection by running the psql command-line user interface (CUI) from the stand-alone database server, as shown in Example 3-11. Enter the actual IP address of the stand-alone server in place of xxx.xx.xx.xxx in the psql command. Press the Enter key and wait for the postgres=# prompt.
Example 3-11 Verifying the connection
$ psql -h <xxx.xx.xx.xxx> -p 27500 -d postgres -U fsepuser
psql (12.1)
Type "help" for help.
postgres=#
The installation of stand-alone FUJITSU Enterprise Postgres 12 Advanced Edition on a Red Hat Enterprise Linux 8 Linux guest is complete.
3.4 Installing and configuring a stand-alone database instance on a SUSE Linux Enterprise Server 12 Linux guest
To install and configure a stand-alone database instance on a SUSE Linux Enterprise Server 12 Linux guest, complete the following steps:
Example 3-12 Installing Java
# zypper install java
Loading repository data...
Reading installed packages...
'java' not found in package names. Trying capabilities.
Resolving package dependencies...
The following 4 NEW packages are going to be installed:
java-1_8_0-openjdk java-1_8_0-openjdk-headless javapackages-tools libgif6
4 new packages to install.
Overall download size: 43.3 MiB. Already cached: 0 B. After the operation,
additional 56.7 MiB will be used.
Continue? [y/n/...? shows all options] (y): y
Retrieving package javapackages-tools-2.0.1-11.1.s390x
(1/4), 51.1 KiB (129.9 KiB unpacked)
Retrieving: javapackages-tools-2.0.1-11.1.s390x.rpm ......................[done]
Retrieving package libgif6-5.0.5-12.1.s390x
(2/4), 20.8 KiB ( 39.4 KiB unpacked)
Retrieving: libgif6-5.0.5-12.1.s390x.rpm .................................[done]
Retrieving package java-1_8_0-openjdk-headless-1.8.0.181-27.26.2.s390x
(3/4), 42.9 MiB ( 55.9 MiB unpacked)
Retrieving: java-1_8_0-openjdk-headless-1.8.0.181-27.26.2.s390x.rpm ......[done]
Retrieving package java-1_8_0-openjdk-1.8.0.181-27.26.2.s390x
(4/4), 370.8 KiB (647.2 KiB unpacked)
Retrieving: java-1_8_0-openjdk-1.8.0.181-27.26.2.s390x.rpm ...............[done]
Checking for file conflicts: .............................................[done]
(1/4) Installing: javapackages-tools-2.0.1-11.1.s390x ....................[done]
(2/4) Installing: libgif6-5.0.5-12.1.s390x ...............................[done]
(3/4) Installing: java-1_8_0-openjdk-headless-1.8.0.181-27.26.2.s390x <12%>==[-]
(3/4) Installing: java-1_8_0-openjdk-headless-1.8.0.181-27.26.2.s390x .................................................................................................................................................................[done]
Additional rpm output:
update-alternatives: using /usr/lib64/jvm/jre-1.8.0-openjdk/bin/java to provide /usr/bin/java (java) in auto mode
update-alternatives: using /usr/lib64/jvm/jre-1.8.0-openjdk to provide /usr/lib64/jvm/jre-openjdk (jre_openjdk) in auto mode
update-alternatives: using /usr/lib64/jvm/jre-1.8.0-openjdk to provide /usr/lib64/jvm/jre-1.8.0 (jre_1.8.0) in auto mode
(4/4) Installing: java-1_8_0-openjdk-1.8.0.181-27.26.2.s390x ..........................................................................................................................................................................[done]
2. Set up JAVA_HOME by using the following command. For this example, we used OpenJDK Version 1.8.0.
#export JAVA_HOME="/usr/lib64/jvm/java-1.8.0-openjdk-1.8.0/jre"
3. Mount the FUJITSU Enterprise Postgres 12 Advanced Edition ISO and start the installation, as shown in Example 3-13.
Example 3-13 Starting the installation
# mount -t iso9660 -r -o loop /fep12iso/fsep12_ae_linux64.iso /mnt2
# cd /mnt2/SERVER/Linux/packages/SUSE12s390x
# rpm -ivh FJSVfsep-SV-12-1200-0.s390x.rpm
Preparing... ################################# [100%]
Updating / installing...
1:FJSVfsep-SV-12-1200-0 ################################# [100%]
4. Install the WebAdmin component of FUJITSU Enterprise Postgres. WebAdmin provides an easy way to create and manage FUJITSU Enterprise Postgres clusters through a GUI. Follow the commands shown in Example 3-14 on page 107.
Example 3-14 Installing WebAdmin
# cd
# umount /mnt2
# mount -t iso9660 -r -o loop /fep12iso/fsep12_ae_linux64.iso /mnt2
# cd /mnt2/WEBADMIN/Linux/packages/SUSE12s390x/
# rpm -ivh FJSVfsep-WAD-12-1200-0.s390x.rpm
Preparing... ################################# [100%]
Updating / installing...
1:FJSVfsep-WAD-12-1200-0 ################################# [100%]
5. This step is optional for a stand-alone installation because MC is required in HA implementations with more than one database server that is configured as primary and standby. Run the commands that are shown in Example 3-15 if there is a requirement to convert this installation into a HA implementation in the future.
Example 3-15 Installing Mirroring Controller
# /opt/fsepv12server64/bin/mc_update_jre_env
INFO: /usr/lib64/jvm/java-1.8.0-openjdk-1.8.0/jre/lib/s390x/server/libjvm.so is in use.
6. Create the database admin user ID fsepuser and set the password by using the following commands:
#useradd -m -U fsepuser
#passwd fsepuser
7. After the user ID is created, the next step is to prepare the directories to store the FUJITSU Enterprise Postgres binary files, transaction logs, and backup (Example 3-16). Figure 3-21 shows the components that should be logically placed in directories, and the different types of storage devices for performance and reducing I/O bottlenecks.
|
Note: For more information about estimating disk space requirements, see Appendix E, “Estimating Database Disk Space Requirements” in FUJITSU Enterprise Postgres 12 Installation and Setup Guide.
|

Figure 3-21 Server resource for FUJITSU Enterprise Postgres
Example 3-16 Preparing the directories
# mkdir -p /database/inst1
# chown -R fsepuser:fsepuser /database
# chmod 700 /database/inst1
# mkdir -p /transaction/inst1
# chown -R fsepuser:fsepuser /transaction
# chmod 700 /transaction/inst1
# mkdir -p /backup/inst1
# chown -R fsepuser:fsepuser /backup
# chmod 700 /backup/inst1
8. To enable communication, grant access to ports 27500, 27515, 27516, 27540, and 27541, as shown in Example 3-17 on page 109. Port 27500 is used by FUJITSU Enterprise Postgres, ports 27515 and 27516 are used by WebAdmin, and ports 27540 and 27541 are used by MC.
Example 3-17 Enabling communication
# SUSEfirewall2 open EXT TCP 27500
# SUSEfirewall2 open EXT TCP 27515
# SUSEfirewall2 open EXT TCP 27516
# SUSEfirewall2 open EXT TCP 27540
# SUSEfirewall2 open EXT TCP 27541
# SUSEfirewall2 stop
<38>Feb 18 20:21:44 SuSEfirewall2[14092]: Firewall rules unloaded.
# SUSEfirewall2 start
<38>Feb 18 20:21:49 SuSEfirewall2[14126]: Setting up rules from /etc/sysconfig/SuSEfirewall2 ...
<38>Feb 18 20:21:49 SuSEfirewall2[14126]: using default zone 'ext' for interface eth0
<38>Feb 18 20:21:50 SuSEfirewall2[14126]: Firewall rules successfully set
9. Configure the environment variables, as shown in Example 3-18.
Example 3-18 Configuring the environment variables
# su - fsepuser
$ PATH=/opt/fsepv12server64/bin:$PATH ; export PATH
$ MANPATH=/opt/fsepv12server64/share/man:$MANPATH ; export MANPATH
$ LD_LIBRARY_PATH=/opt/fsepv12server64/lib:$LD_LIBRARY_PATH ; export LD_LIBRARY_PATH
Example 3-19 Creating the database instance
$ initdb -D /database/inst1 --waldir=/transaction/inst1 --lc-collate="C" --lc-ctype="C" --encoding=UTF8
The files belonging to this database system will be owned by user "fsepuser".
This user must also own the server process.
The database cluster will be initialized with locales
COLLATE: C
CTYPE: C
MESSAGES: en_US.UTF-8
MONETARY: en_US.UTF-8
NUMERIC: en_US.UTF-8
TIME: en_US.UTF-8
The default text search configuration will be set to "english". (15541)
Data page checksums are disabled. (18153)
fixing permissions on existing directory /database/inst1 ... ok (15516)
fixing permissions on existing directory /transaction/inst1 ... ok (15516)
creating subdirectories ... ok (15516)
selecting dynamic shared memory implementation ... posix
selecting default max_connections ... 100
selecting default shared_buffers ... 128MB
selecting default time zone ... (19842)America/New_York
creating configuration files ... ok (15516)
running bootstrap script ... ok (15516)
performing post-bootstrap initialization ... ok (15516)
syncing data to disk ... ok (15516)
initdb: warning: enabling "trust" authentication for local connections
You can change this by editing pg_hba.conf or using the option -A, or
--auth-local and --auth-host, the next time you run initdb.
Success. You can now start the database server using:
pg_ctl -D /database/inst1 -l logfile start
11. After the first database instance is created, configure the instance to accept remote connections (Example 3-20). By default, FUJITSU Enterprise Postgres allows connections only from the local machine on which the database server is installed. Turn on the logging collector to capture log messages into log files. This parameter can be set only at the server start.
Example 3-20 Configuring the instance to accept remote connections
$ vim /database/inst1/postgresql.conf
listen_addresses = '*'
port = 27500
logging_collector = on
12. Configure the host-based authentication by setting up the pg_hba.conf file, as shown in Example 3-21. The parameters in pg_hba.conf control the authentication process in PostgreSQL and in FUJITSU Enterprise Postgres.
Example 3-21 Configuring host-based authentication
$ vim /database/inst1/pg_hba.conf
host all all xxx.xx.xx.0/24 trust
With the configuration that is shown in Example 3-20 and Example 3-21, all the connections originating from the xxx.xx.xx.0 network can access the stand-alone database instance inst1. Ensure that you provided the correct network range in place of xxx.xx.xx.0/24.
|
Note: FUJITSU Enterprise Postgres supports several authentication methods, including TRUST, IDENT, PEER, GSSAPI, LDAP, SCRAM, SHA-256, MD5, and password. For more information about the host-based authentication method, see 4.4, “FUJITSU Enterprise Postgres encryption on IBM LinuxONE with crypto cards” on page 126.
|
13. Start the database instance inst1 on the stand-alone database server by running the command that is shown in Example 3-22.
Example 3-22 Starting the database instance
$ pg_ctl start -D /database/inst1
waiting for server to start....2021-02-18 20:26:09.272 EST [14680] LOG: starting PostgreSQL 12.1 on s390x-ibm-linux-gnu, compiled by gcc (SUSE Linux) 4.8.5, 64-bit
2021-02-18 20:26:09.272 EST [14680] LOG: listening on IPv4 address "0.0.0.0", port 27500
2021-02-18 20:26:09.272 EST [14680] LOG: listening on IPv6 address "::", port 27500
2021-02-18 20:26:09.273 EST [14680] LOG: listening on Unix socket "/tmp/.s.PGSQL.27500"
2021-02-18 20:26:09.279 EST [14680] LOG: redirecting log output to logging collector process
2021-02-18 20:26:09.279 EST [14680] HINT: Future log output will appear in directory "log".
done
server started
14. Verify the connection by starting the psql CUI from the stand-alone database server, as shown in Example 3-23. Enter the IP address of your stand-alone server in place of xxx.xx.xx.xxx in the psql command. Press the Enter key and wait for the postgres=# prompt.
Example 3-23 Verifying the connection
$ psql -h xxx.xx.xx.xxx -p 27500 -d postgres -U fsepuser
psql (12.1)
Type "help" for help.
postgres=#
15. To stop the instance, run the command that is shown in Example 3-24.
Example 3-24 Stopping the instance
$ pg_ctl stop -D /database/inst1
waiting for server to shut down.... done
server stopped
The installation of stand-alone FUJITSU Enterprise Postgres 12 Advanced Edition on a SUSE Linux Enterprise Server 12 Linux guest is complete.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
