Appendix A
Practice Exam
This appendix contains a full-length practice exam designed to be similar to the CompTIA Cybersecurity Analyst (CySA+) exam. The questions are balanced among the CySA+ domains, and the question content is similar to what you will find on the exam.
Our recommendation is that you save this exam until you have completed your first round of studying and then attempt the exam in a single sitting to simulate the real exam experience.
After grading your exam, you may use it to highlight areas of study that you should revisit before taking the real exam. You will find the answers and explanations to this exam listed in Appendix B.
Good luck with the practice test and best wishes for success on the CySA+ exam!
Exam Questions
- Tom is preparing to build a credit card processing system. As he creates his design, he realizes that the operating environment will not allow him to include one of the PCI DSS required elements. What type of control should Tom discuss implementing?
- Technical control
- Operational control
- Administrative control
- Compensating control
- Shane administers a Linux server running Apache. During the middle of his workday, tweets start to appear in his Twitter feed about compromises of Apache servers due to a flaw that had not been previously reported. What type of threat is this?
- A local exploit
- Advanced persistent threat
- A zero-day exploit
- A zero-knowledge threat
- Juan is analyzing systems on his network for known indicators of compromise. What term best describes the work he is performing?
- Threat hunting
- Vulnerability scanning
- Intrusion prevention
- Data mining
- Which one of the following controls may be used to attract the attention of intruders who gain access to a network segment so that they are distracted from high-value targets and may be monitored?
- MAC
- Honeypot
- Intrusion prevention system
- Rogue AP
- While engaging in an attack, the attacker sends an email message to the targeted victim that contains malicious software as an attachment. What phase of the Cyber Kill Chain is occurring?
- Weaponization
- Delivery
- Action on Objectives
- Reconnaissance
- Betsy receives many requests from IT staff members for remote access to internal systems through the DMZ. What type of system might Betsy place in the DMZ to accommodate these requests?
- Jump box
- Virtual machine
- Honeypot
- Firewall
- Karen is configuring the host firewall on a web server that allows both encrypted and unencrypted web connections. It also must allow SSH access for users to securely drop off files. Which one of the following ports should not be open on the host firewall?
- 22
- 80
- 443
- 1433
- Jacob has been tasked with using NetFlow to monitor network traffic flows in his organization, but the systems he is using are unable to keep up with the volume of data. What is his best option to deal with the traffic without adding new hardware while retaining visibility into the entire network?
- Switch to RMON monitoring
- Use flow sampling
- Decrease the number of flows allowed for each user
- Use packet shaping to reduce traffic rates to one that the flow collector can keep up with
- Brooke is helping her organization implement a new cloud service. She is configuring the operating system on a server built in the cloud provider's environment. What cloud service model is in use?
- PaaS
- FaaS
- SaaS
- IaaS
- Barry joins a hotel wireless network and opens a web browser. No matter which page he visits, he is redirected to a web page requesting him to provide his name and room number. What type of network access control is the hotel using?
- In-band
- Out-of-band
- 802.1x
- Agent-based
- Charles has been asked to secure the wired network that is normally a suite of offices that will be temporarily used by a visiting team from another company. If he wants to continue to allow members of his team to use the jacks, what technical means can he use to do this while also verifying the security posture of the systems that connect?
- NAC
- MAC filtering
- Port security
- HIPS
- Which one of the following components is built into most modern computer systems and is used to store disk encryption keys?
- HSM
- Trusted foundry
- Root of trust
- TPM
- Which media disposition is typically the most expensive option from NIST's options in NIST SP 800-88?
- Clearing
- Purging
- Destruction
- Obliteration
- What type of firewall is able to incorporate contextual information about the user and application when making permit/deny decisions?
- NGFW
- Perimeter firewall
- Stateful inspection
- Packet filter
- During a network attack simulation exercise, which team is responsible for securing the targeted environment?
- Red
- White
- Blue
- Black
- Laura is investigating a potential security breach within her organization. She believes that an attacker stole a file containing employee information. Which information security tenet would this attack violate?
- Confidentiality
- Integrity
- Availability
- Nonrepudiation
- Which of the following incident response activities should not happen during the eradication phase of incident response?
- Sanitization
- Reconstruction/re-imaging
- Secure disposal
- Segmentation
- Karen is conducting a risk analysis for her organization and identifies that one potential threat is a widespread power outage that disrupts service to her organization's datacenters. How should Karen classify this threat?
- Accidental
- Adversarial
- Structural
- Environmental
- Which of the following is not a law?
- HIPAA
- PCI DSS
- FERPA
- SOX
- Which of the following is not typically involved in the initial phases of a CSIRT activation?
- Technical staff
- CSIRT leader
- Law enforcement
- First responder
- Which one of the following activities would not normally occur during the attack phase of a penetration test?
- System browsing
- Network reconnaissance
- Escalating privileges
- Gaining access
- Bob is evaluating the risk to his organization from advanced persistent threat (APT) attackers. He assesses the likelihood of this risk occurring to be medium and the impact high. How would this risk be categorized under most organizations' risk evaluation matrices?
- Low risk
- Moderate risk
- Semi-moderate risk
- High risk
- Which of the following is not a common network issue?
- Bandwidth consumption
- Beaconing
- Link aggregation
- Unexpected traffic
- Richard wants to build DDoS detection capability into his network. Which of the following tools is not appropriate for that task?
- Network bandwidth monitoring tools
- IPS
- Active performance monitoring tools
- Network fuzzers
- Which one of the following technologies is commonly used to integrate software as a service (SaaS) productivity platforms?
- API
- SOAR
- SCAP
- CI/CD
- What concern may make active monitoring less attractive in some heavily used networks?
- Active monitoring can't monitor busy networks.
- Active monitoring bypasses IPSs.
- Active monitoring consumes additional bandwidth.
- Active monitoring requires SNMP to be enabled.
- What security tool generated the output shown here?

- Nessus
- Traceroute
- Nmap
- Syslog
- Which one of the following analysis techniques requires samples of known malicious activity to identify future instances of the same activity?
- Signature analysis
- Trend analysis
- Behavioral analysis
- Anomaly analysis
- Fiona is investigating the misuse of her company's network and needs to capture network traffic for analysis. She wants to use a dedicated open source tool that is designed for packet capture and analysis. Which one of the following tools best meets her needs?
- Nessus
- Nmap
- Wireshark
- Nikto
- Bill is analyzing a system that is experiencing strange symptoms. He would like a list of the open network connections on that system. Which one of the following tools would be helpful in this scenario?
- Traceroute
- Netstat
- Tcpdump
- Wireshark
- Which of the following is not a reason to avoid imaging live systems?
- The drive may be modified by the forensic tool.
- The drive contents may change during the imaging process.
- Unallocated space will not be included.
- Capturing memory contents is more difficult.
- Which incident response phase includes filing catch-up change requests in the organization's change control process?
- Eradication
- Containment
- Recovery
- Postincident activities
- Brian is a new hire to his company as a threat hunter and he is beginning by developing scenarios of potential attacks. What threat hunting activity is Brian performing?
- Reducing the attack surface area
- Establishing the hypothesis
- Profiling threat actors
- Gathering evidence
- Rodney's company wants to prevent phishing attacks from resulting in account compromise. Which of the following solutions will provide the most effective solution?
- Implement context-aware authentication.
- Use enhanced password requirements.
- Add token-based authentication.
- Set a shorter password lifespan.
- The group of developers that Cynthia is part of tests each software component or function before integrating it into larger software modules. What is this process called?
- Code segmentation
- Unit testing
- UAT
- Fagan inspection
- At what stage in the incident response process does a CSIRT move from primarily passive to primarily active work?
- Preparation
- Detection and Analysis
- Containment, Eradication, and Recovery
- Postincident Activity
- Howard is analyzing the logs from his firewall and sees that the same IP address attempted blocked connections to the same server many different times. What is the most likely explanation for this activity?
- Denial-of-service attack
- Port scan
- SQL injection
- Cross-site scripting
- Ron is reviewing Cisco router logs from his organization and would like an easy way to filter the logs down to those that are most critical. What Cisco log level represents an emergency situation?
- 0
- 1
- 6
- 7
- Angela wants to search for rogue devices on her network. Which of the following techniques will best help her identify systems if she has a complete hardware and systems inventory?
- MAC address vendor checking
- Site surveys
- Traffic analysis for unexpected behavior
- MAC address verification
- What type of control can be put in place and documented if an existing security measure is too difficult to implement or does not fully meet security requirements?
- Cost limiting
- Administrative
- Compensating
- Break-fix
- What security tool generated the output shown here?

- Wireshark
- Nessus
- Nmap
- Nexpose
- Tom would like to use nmap to perform service fingerprinting and wants to request banner information from scanned services. What flag should he use?
-oG-sS-b-sV
Use the following scenario for questions 43–45. Insecure, Inc. has experienced multiple data breaches over the past 6 months and has recently hired Cynthia, a new information security officer. Cynthia's first task is to review Insecure, Inc.'s defenses with the goal of identifying appropriate defenses to put in place.
Cynthia knows that her new employers had two major breaches. Breach A occurred when an employee took home a USB external drive with sensitive customer information as well as corporate planning data for the following year. The employee left the drive in their car, and the car was broken into overnight. In the morning, the drive was gone. Insecure, Inc. is uncertain about the fate of the drive and is concerned that customer data as well as their top-secret plans to best their competitors may have been exposed.
Breach B was caused when Insecure, Inc.'s new web application was attacked by unknown attackers who used a SQL injection attack to insert new data into their e-commerce application. Insecure, Inc.'s website was quickly deluged with deal seekers, who put in hundreds of orders for Insecure's newly inexpensive products—the attackers had managed to change the price for almost every product they sold. Insecure, Inc. managed to cancel most of the orders before they shipped, but they have had to deal with angry customers since the event.
Using this information, your task is to help Cynthia recommend the best defensive strategy for each of the following questions.
- Cynthia wants to ensure that data cannot be lost in the same way as the loss that occurred during Breach A. Which of the following would make a lost drive not a major concern?
- Encrypt the drive with SHA1.
- Encrypt the drive with AES256.
- Encrypt the drive with DES.
- Encrypt the drive with MD5.
- If Cynthia wants to address the human side of the issues she has discovered, what solution would best help prevent future issues?
- Policy and awareness training
- Dual control and cross training
- Cross training and an awareness program
- Implementing a continuous improvement program
- What technical solution can Cynthia use to detect and possibly stop both SQL injection attacks and denial-of-service attacks against her web applications?
- An IDS
- A PRNG
- DLP
- An IPS
- Kevin ran a port scan on a system and determined that it is listening on port 1433. What type of server is Kevin most likely scanning?
- Web server
- Database server
- AAA server
- Email server
- Phil ran a port scan on a server and discovered the following results:

Which one of the services running on this server can Phil be confident is using encryption?
- SSH
- HTTP
- MySQL
- SMTP
- What requirement of shared authentication is a key differentiator from SSO?
- It requires authentication for each site.
- It uses the same authentication key for each site.
- Shared authentication provides end-to-end encryption.
- The shared authentication standard is an open standard.
- NIST's data impact rating scale describes what category of data impact as “Sensitive personally identifiable information (PII) of taxpayers, employees, beneficiaries, etc., was accessed or exfiltrated”?
- Confidentiality breach
- Privacy breach
- Proprietary breach
- Integrity loss
- Tara ran an nmap scan against a server and received the following results:

Of the services listed, which port is most unusual to find on a web server?
- 53
- 80
- 443
- 8080
- What Windows tool provides detailed data, including counters, that can measure information about a system like energy consumption, disk usage, and network activity?
- Winmon
- Perfmon
- Sysctl
- Resmon
- Kyle used nslookup to determine the IP address for
nytimes.comand received the following results:
What is the IP address of the server that answered Kyle's request?
- 172.30.0.2
- 151.101.1.164
- 151.101.65.164
- 151.101.193.164
- A part of his forensic investigation, Alex signs and notes in his log when the drive copy he prepared is transferred to legal counsel. What is this process known as?
- Handoff documentation
- Chain-of-custody tracking
- Asset tracking
- Forensic certification
- Ryan uses the following command as part of his forensic image preparation:
root@demo:~# md5sum image1.raw441fb68910e08fd0ed2db3bdb4e49233 image1.rawWhat task has he performed?
- Encryption
- Image creation
- Hashing
- Secure wipe
- Ryan uses the following command later in his forensic investigation and receives the response shown. What has occurred?
root@demo:~# md5sum -c image1.md5 image1v2.md5image1.raw: FAILEDmd5sum: WARNING: 1 computed checksum did NOT matchimage1.raw: OK- The hash was miscalculated.
- No hash was created.
- The files are the same.
- The files are different.
- Ed is preparing an incident response report, and he discovers that some systems were not properly configured to use NTP. What critical element of incident reports may suffer based on this?
- The root cause analysis
- The chronology of events
- The postrecovery validation report
- The documentation of specific actions taken to remediate issues
- Which one of the following criteria would normally be considered least important when making decisions about the scope of vulnerability scanning programs?
- Regulatory requirements
- Data classification
- Operating system type
- Corporate policy
- Bernie is designing a PCI DSS–compliant vulnerability management program for his business. Who may conduct the internal scans required by the standard?
- Scans must be conducted by an approved scanning vendor (ASV).
- Scans must be conducted by an internal audit group or an ASV.
- Scans must be conducted by a PCI DSS–certified individual.
- Scans may be conducted by any qualified individual.
- Which one of the following elements of the Security Content Automation Protocol (SCAP) provides a standard nomenclature for describing security-related software flaws?
- CVSS
- CPE
- CVE
- OVAL
- Which of the following is not a Linux memory forensic tool?
- fmem
- LiME
- The Volatility Framework
- DumpIt
- What step is missing from the vulnerability management life cycle shown here?
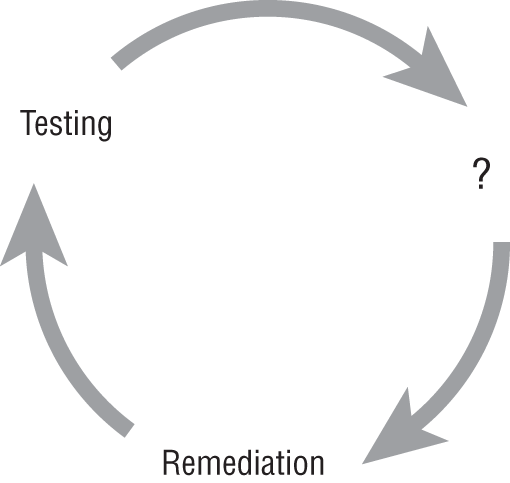
- Assessment
- Detection
- Patching
- Scanning
- The NIST Cybersecurity framework includes three major measures. Which three major measures are included in the measures that allow an organization to evaluate which tier they are at?
- Risk management process, integrated risk management program, external participation
- Risk management program, risk tolerance, controls structure
- Risk management process, incident response program, external data sources
- Risk management program, vulnerability management program, external data sources
- Bryan is preparing to conduct a vulnerability scan and wishes to use credentialed scanning for maximum effectiveness. What type of account should Bryan use to perform this scanning in a secure manner?
- Domain administrator
- Root user
- Local administrator
- Read-only user
- Gary is the cybersecurity manager for a federal government agency subject to FISMA. He is evaluating the potential confidentiality impact of a system and decides that the unauthorized disclosure of information stored on the system could have a serious adverse impact on citizens served by his agency. How should Gary rate the confidentiality impact?
- Low
- Moderate
- High
- Critical
- What major Kerberos-centric concern faces administrators of an Active Directory forest or domain if the AD server itself is compromised?
- All Kerberos tickets will be invalidated.
- Attackers can create a “golden ticket.”
- There is no way to notify users of the issue.
- Previously issued user tickets will be exposed.
- Which of the following is not a common attack against LDAP servers?
- Exploiting of insecure binding
- Directory harvesting
- LDAP injection
- Silver ticket attacks
- Oliver is developing a prioritization scheme for vulnerability remediation. Which one of the following is not generally accepted as an important criterion for prioritizing remediation?
- Vulnerability severity
- Age of vulnerability
- Criticality of system
- Difficulty of remediation
- What regulatory schemes specifically require the use of vulnerability scanning?
- FISMA and PCI DSS
- PCI DSS and HIPAA
- HIPAA and GLBA
- GLBA and FISMA
- What type of term describes review of code by running it?
- The Run/Test method
- Runtime inspection
- Static code analysis
- Dynamic code analysis
- After completing a vulnerability scan, Bob received a report of a blind SQL injection vulnerability. Bob worked with the application developer to inspect the vulnerability and determined that the attack was not possible. What type of error occurred?
- True positive
- True negative
- False positive
- False negative
- Which of the following types of staff are not frequently part of a CSIRT?
- Technical subject matter experts
- IT support staff
- Legal counsel
- Comptrollers
- Which of the following is not well suited to identifying network scans and probes?
- IPS
- SNMP traps
- Firewall
- SIEM
- Olivia has requested that her development team run their web application security testing tools against their web applications, despite the fact that they just installed the most recent patches. What is this type of testing called?
- Regression testing
- Patch state validation
- WAV testing
- HTTP checking
- What type of testing directly targets error handing paths, particularly those that are rarely used or might otherwise be missed during normal testing?
- Fuzzing
- Mutation testing
- Fault injection
- Fagan inspection
- Which of the following pieces of information does Windows not capture by default about USB devices when they are plugged in?
- The capacity of the device
- The device name
- The device serial number
- The unit's vendor ID
- What type of process is shown here?

- A Waterfall SDLC
- Mutation testing
- Dynamic code analysis
- Fagan inspection
- When searching a Windows system for forensic data, where can point-in-time details of prior actions taken on the machine sometimes be found?
- The Windows Registry
- Autorun keys
- Hibernation files
- Volume shadow copies
- Harry identified the following vulnerability in one of his systems:

He would like to search network traffic to identify connection attempts that might have attempted to exploit this vulnerability. What port would traffic exploiting this vulnerability most likely use?
- 22
- 80
- 443
- 1521
- Erik identified the following vulnerability in one of his systems:

What technique would be the most effective way to combat this vulnerability?
- Firewall rule
- Input validation
- Honeypot
- Patching
- Bonnie ran a vulnerability scan against one of her servers and received a report that the server contains buffer overflow vulnerabilities in the operating system. Which one of the following would be the most effective defense?
- Input validation
- Firewall
- Operating system patching
- Intrusion prevention system
- Which one of the following protocols would not generate a network vulnerability report if run on a production system?
- SSLv2
- SSLv3
- TLS 1.1
- All three would generate a vulnerability.
- Ben identified the following vulnerability in one of his systems:

What technique would be the most effective way to combat this vulnerability?
- Firewall rule
- Input validation
- Honeypot
- Patching the operating system
- Chelsea's company runs an industrial control system (ICS) from a vendor that no longer provides support. The system has a newly discovered vulnerability to buffer overflow attacks. What would be the best way to defend this system?
- Apply a patch
- Rewrite the code
- Place it on a segmented network
- Use encryption
- What component of a virtualized infrastructure is responsible for ensuring that software running on one virtualized system does not receive access to areas of memory that are reserved for use by another virtualized system?
- Hypervisor
- Virtual guest
- Virtual host
- Physical hardware
- Frank received a phone call from a user who is traveling and accessing the Wi-Fi network at a hotel. The user tried to access a corporate website and received an error message that the certificate was invalid. No other users are receiving this error. What is the most likely explanation for this error message?
- The company's website is using an expired certificate.
- The company's website has an incorrect certificate installed.
- The hotel uses a captive portal.
- Another user on the hotel network is attempting to eavesdrop on the connection.
