|
|
Firewall |
|
|
Perimeter |
|
|
Static and dynamic packet-filtering firewalls |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Protocol numbers of common protocols |
|
|
Cisco Common Classification Policy Language (C3PL) |
|
|
ZPF terms: zone, zone pair, class maps, policy maps, self zone |
|
Exam Topics Covered in This Chapter: |
|
|---|---|
|
|
Explain the functionality of standard, extended, and named IP ACLs used by routers to filter packets |
|
|
Configure and verify IP ACLs to mitigate given threats (filter IP traffic destined for Telnet, SNMP, and DDoS attacks) in a network using CLI |
|
|
Configure IP ACLs to prevent IP address spoofing using CLI |
|
|
Discuss the caveats to be considered when building ACLs |
|
|
Describe the operational strengths and weaknesses of the different firewall technologies |
|
|
Explain stateful firewall operations and the function of the state table |
|
|
Implement Zone Based Firewall using SDM |
Note
These exam topics are from cisco.com. Check there periodically for the latest exam topics and info.
At this juncture, it would be easy to say something like, “Now that we have secured the network perimeter (see Chapter 3, “Security at the Network Perimeter,” and Chapter 4, “Implementing Secure Management and Hardening the Router”), we can now implement firewall technologies on our router.” After all, everyone knows what a firewall is, right? Most people would be fine with this and just ... do it. But we’re not “most people.” To be totally comfortable with the subject of implementing IOS firewalls in support of a network security policy, we should start by defining what is meant by a firewall in the first place. This question will lead to more questions:
![]() Just what is a firewall?
Just what is a firewall?
![]() What types of firewalls are there?
What types of firewalls are there?
![]() Can any one definition suffice?
Can any one definition suffice?
![]() What kind of firewall technologies do I need to deploy to protect the perimeter?
What kind of firewall technologies do I need to deploy to protect the perimeter?
![]() What do I need firewalls for in the first place?
What do I need firewalls for in the first place?
This chapter answers these questions.
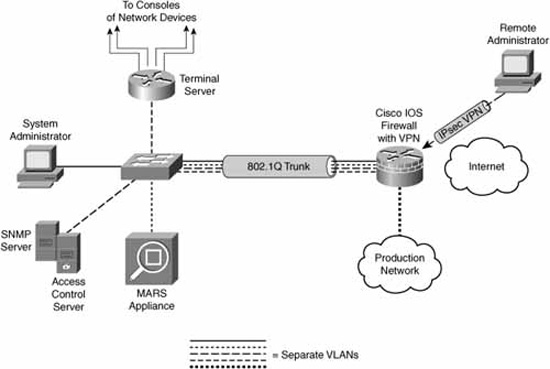
In Chapter 4, we introduced a reference design to give us a design context for secure management and reporting. For consistency, we will use the same reference architecture in this chapter as presented in Figure 5.1.
We will refer to this reference design from time to time when examining, defining, and implementing firewall technologies.