Chapter 16. Security Policy
Establishing a security policy is the starting point in designing a secure network. It is essential that a set of minimum security requirements be gathered, formalized and included as the basis of your security policy. This security policy must be enforceable by your organization and will create an additional cost to running and monitoring your network. This additional cost/benefit of a security policy must be understood and embraced by your organization’s management in order to enhance and maintain network and system security.
The lack of an accepted and well-thought-out security policy and guidelines document is one of the major security vulnerabilities in most companies today. This section discusses several Best Practices related to the production of such a document. The importance of a meaningful security policy cannot be over-emphasized.
16.1. Best Practice #1
Perform a threat analysis and risk analysis for your organization to determine the level of security that must be implemented.
First, identify all the threats to your network; second, determine threat categories; third, perform the risk assessment; and, fourth, recommend action. Risk assessment should be performed by constructing a “consequence” matrix vs. “likelihood” matrix[1] as shown in Figure 16.1.
1 NDIA, Undersea Warfare Systems Division, “INFOSEC Considerations for Submarine Systems Study, Technical Report II: Threat/Risk Decomposition”, 1998.
Figure 16.1. Risk rating matrix
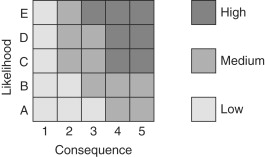
For each threat, construct a likelihood/consequence table. The “likelihood” rating for a threat can use categories such as A=remote, B=unlikely, C=likely, D=highly likely, and E=near certainty. The “Consequence” rating of the threat should use a point system where block 1 in the table=0–1 points, block 2=2–3 points, block 3=4–6 points, block 4=7–9 points, block 5=9–11 points. Points are assigned based upon your subjective assessment of a compromise in security as an impact on functioning of your organization and data compromise. For instance, 5 points=organization grinds to a halt, loss of mission-critical systems; 3 points=some application(s) don’t function, loss of non-mission-critical systems, but the organization can function; and 0 points=no loss of function. Data compromise points may be assigned as, for example, 2 points=compromise of sensitive data to people outside the organization; 1 point=compromise of sensitive data to people internal to the organization that should not have access; and 0 point=no compromise of data. This type of matrix will immediately highlight where to emphasize security. Also, a form should be created and filled out that:
- identifies the threat
- gives solutions to the threat
- shows the likelihood of the threat (i.e., A, B, etc.)
- gives the impact of the threat on an organization’s function and data
- shows the consequences of a compromise.
16.2. Best Practice #2
Define a security policy for the entire site and use it as a guide for the network security architecture.
Define a policy that includes sections for confidentiality, integrity, availability, accountability, assurance, and enforcement, as described in the following paragraphs. The policy should address as much as possible of what is included in these sections according to risk and affordability. The general security policy described in this section was developed from DoD 5200.28 and SECNA VINST 5239.3.
Confidentiality – The system must ensure the confidentiality of sensitive information by controlling access to information, services, and equipment. Only personnel who have the proper authorization and need-to-know can have access to systems and data. The system must include features and procedures to enforce access control policies for all information, services, and equipment comprising the system.
Integrity – The system must maintain the integrity (i.e., the absence of unauthorized and undetected modification) of information and software while these are processed, stored and transferred across a network or publicly accessible transmission media. Each file or data collection in the system must have an identifiable source throughout its life cycle. Also, the system must ensure the integrity of its mission-critical equipment. Automated and/or manual safeguards must be used to detect and prevent inadvertent or malicious destruction or modification of data.
Availability – The system must protect against denial of service threats. Protection must be proportionate to the operational value of the services and the information provided. This protection must include protection against environmental threats such as loss of power and cooling.
Accountability – The system must support tracing of all security relevant events, including violations and attempted violations of security policy to the individual subsystems and/or users including external connections. The system must enforce the following rules:
- Personnel and systems connecting to the system must be uniquely identifiable to the system and must have their identities authenticated before being granted access to sensitive information, services, or equipment.
- Each subsystem handling sensitive or mission-critical information must maintain an audit trail of security relevant events, including attempts by individual users or interfacing subsystems to gain access through interfaces not authorized for that particular purpose. This audit trail must be tamper-resistant and always active.
Assurance – The criticality and sensitivity of the information handled, equipment and services, and the need-to-know of personnel must be identified in order to determine the applicable security requirements. The security implementations chosen must provide adequate security protection commensurate with the criticality of the data, in accordance with the security policy.
Enforcement – The security policy must be enforced throughout the life cycle of the system. All implementations of system security functions including those implemented at the subsystem level must be evaluated to ensure that they adequately enforce the requirements derived from the security policy. Each platform must be evaluated to ensure that the installed system configuration enforces the stated security policy. As a result of this evaluation, an assessment of the vulnerability can be generated. This assessment must be evaluated by the security manager or system administrator to decide if any modifications to the system must be made so that it complies with the security policy. Security best practices must be employed throughout the life cycle of a system to ensure continued compliance with the stated security policy. New system projects must have information security representatives during the planning and preliminary design stages in order to implement security into the design.
16.3. Best Practice #3
Create a plan for implementing your security policy.
Once a security policy is established, an implementation plan should be created. Incremental, staged infrastructure improvements and new hires (if any) will help management plan for expenses and create a timetable for implementation.
The implementation plan should include the following steps:
- Defining implementation guidelines. These guidelines should specify the personnel to receive security alarms and what action is to be taken, chains of command for incident escalation, and reporting requirements.
- Educating staff, customers, etc. about the security policy.
- Purchasing any needed hardware/software and hiring anyneeded personnel.
- Installing and testing equipment/software.
