

Using quantum-safe cryptography
In this chapter, various use cases are introduced to illustrate the threats that many organizations face with the rise of quantum computing for use cases that are related to confidentiality, integrity, authentication, and nonrepudiation.
Across these use cases, the challenges are addressed and how the quantum-safe capabilities that are provided with IBM z16 can help to overcome these challenges and ensure the security of sensitive and valuable data into the future.
Also, each use case includes applications for quantum-safe encryption capabilities across different industries and the specific enhancements with IBM z16 that enable these adoption patterns.
This chapter includes the following topics:
3.1 Protecting sensitive data
Classical cryptographic algorithms are widely used to protect data that is at rest and in flight. Cryptographic algorithms are used for having the capabilities of secrecy, integrity, authentication, and nonrepudiation.
Organizations use symmetric keys and public key encryption for data protection schemes. Most organizations encrypt sensitive data to protect it against insider threats, unauthorized user access, and accidental data exposures.
An organization’s data is at risk on the internet and communication network when Shor’s quantum algorithms are used to break public key encryption schemes. Suppose that a cybercriminal gets access to a powerful quantum computer, they can decrypt lost or harvested confidential data by determining encryption keys.
In highly regulated industries, organizations must protect subject data rights to personally identifiable information (PII) or personal health information (PHI) and comply with standards, such as GDPR, NIST, ISO, SOX, CCPA, and PCI. Data privacy and security are critical to avoid penalties and the cost of data breaches because digital trust and brand reputation are at stake. Organizations need quantum-safe encryption to protect their sensitive data and maintain the confidentiality of trade secrets in the quantum era.
3.1.1 Problem statement
An organization’s long-lasting data can be at risk from “harvest now, decrypt later” attacks. These attacks are carried out offline or as passive attacks on confidentiality versus as an online attack against a security protocol. That is, an adversary might carry out the attack by collecting data or public information today and later attempt to recover the secret key that is used to encrypt the data. This process might be done by mounting a brute force attack to find the secret key. The the private key that is used in a key negotiation step also might be derived by attacking Rivest, Shamir, Adleman (RSA) or Elliptic Curve Cryptography (ECC) if a public key protocol was used for secret key establishment. The bad actor’s goal is to find the secret key that was used to encrypt the data.
Organizations must start the use of quantum-safe methods to protect their data now so that more vulnerable data is not produced. Several symmetric algorithms are not secure when Grover’s algorithm is used to search the key space.
Organizations can mitigate the risk by switching to strong encryption algorithms, such as AES, and ensuring the AES key length is at least 256 bits. As discussed in “Cryptographic vulnerabilities possible with quantum computers” on page 9, organizations should not continue to encrypt their sensitive data by using algorithms, such as 2TDEA or 3TDEA, whose strength is not sufficient in the quantum computing era. These algorithms for new encryption use cases must be retired or no longer used when possible.
3.1.2 Solving this challenge by using IBM z16 capabilities
Organizations must be concerned about data protection today. Even though the threat of a quantum computer might be in the future, organizations must ensure that they are not continuing to create encrypted data by using methods that are not quantum-safe, especially for long-lasting data.
It is essential to understand data classification and where potential exposures exist. It is also critically important to have a plan for retiring versions of your data that were protected by using the retired algorithms. If that data remains in systems, an attacker might find it and break it without attacking the version that is newly protected with the newer algorithm.
In 2.2.3, “Building your inventory” on page 23, we discussed creating a data inventory and a cryptographic inventory. These security assets help organizations identify which data is encrypted and which encryption methods were used.
The inventories must be reviewed to highlight weak or vulnerable encryption cryptography that is used in the enterprise to protect data. IBM provides tools to help create the cryptographic inventory, such as ADDI, CAT, zERT, and the Crypto Statistics Monitoring tool, as described in “Establishing a cryptographic inventory” on page 58.
After the vulnerable data assets are identified, a data protection strategy is created. The strategy is informed by using knowledge about how the data must be protected.
IBM z16 offers several features that can be used to protect the data, such as pervasive encryption. This encryption feature uses AES encryption with 256 bits. Its internal key management support uses quantum-safe protections with a hybrid key exchange mechanism that uses CRYSTALS-Kyber and Elliptic Curve Diffie Hellman (ECDH) and dual-signing scheme that uses CRYSTALS-Dilithium and Elliptic Curve Digital Signature Algorithm (ECDSA). The pervasive encryption features include Linux on IBM Z protected key dm-crypt, z/OS data set encryption, coupling facility encryption, and IBM z/VM encryption.
IBM z16 also provides quantum-safe APIs that can be used to protect data. The APIs are available through ICSF. IBM z16 provides quantum-safe key management APIs and lifecycle management support for the organization to generate the encryption keys and also encryption APIs that can be used to encrypt the data (see Figure 3-1).

Figure 3-1 Data encryption process
The following process is used to encrypt data on the IBM z16 as shown in Figure 3-1 on page 29:
1. The Requester calls ICSF to generate an AES 256-bit CIPHER key. The Requester is a component that uses the quantum-safe APIs, such as an application or key management tool.
2. ICSF sends a request to Crypto Express8S (CEX8S) to generate a secure key.
3. CEX8S returns the secure key to ICSF.
4. ICSF returns the key to the Requester.
5. The Requester calls ICSF to add a key record to the CKDS that contains the key, which later is referenced by its associated key label.
6. The Requester calls ICSF to encrypt data by using the key label.
7. ICSF retrieves CIPHER key from the key data set. If requested, the secure key is converted to a protected key. A secure key request, including the key and data, are sent to the CEX8S. Protected key requests (including the key and data) are sent to CPACF.
8. The crypto engine (CPACF or CEX8S) returns the ciphertext to ICSF.
9. ICSF returns ciphertext to the Requester.
3.1.3 Industry applications
In highly regulated industries, organizations must provide data security and protection to meet the privacy regulations and compliance requirements that are outlined in their data retention policies. Examples are healthcare and insurance organizations with patient health information (PHI) in electronic medical records (EMR) that must be protected. These and other organizations must encrypt and store confidential documents for a long period.
Information that requires special attention includes tax documents, legal agreements, trade secrets, and clinical trials. Customer data and PII must be protected. Financial and banking organizations must protect customer data in mortgage and loan processing applications. They must also safeguard banking (PAN data) or payment card (IBM PIN® data). Organizations must ensure that their data is being protected by using quantum-safe encryption methods.
3.2 Use case: Sharing keys securely
This use case describes the requirement for organizations with confidential information, such as intellectual property, to share their sensitive data with Business Partners and third parties by establishing keys with traditional key exchange protocols.
In addition, the threat that quantum computing has on these processes are explained in-depth and how IBM z16 capabilities can overcome these challenges. The quantum-safe capabilities in the IBM z16 can help ensure that partnering organizations securely share their intellectual property and proprietary information to avoid information disclosure and protect it from competitors to avoid reputation damage, profit loss, and brand impact.
Across many industries, organizations use their valuable information, sensitive data, and intellectual property to compete and succeed in a global market. These digital assets oftentimes constitute over 80% of the organization’s total value.
Organizations that have strategic relationships with each other, such as Business Partners, often need to share this valuable information to collaborate and develop solutions and products. As important as it is to enable this collaboration and allow for sharing of information, it is equally important that this valuable information stays out of the hands of competitors and adversaries. The unintended disclosure of an organization’s intellectual property and sensitive information can result in irreversible damage to the organization’s reputation, along with profit loss and long-lasting brand impact.
Traditionally, organizations keep their sensitive information and digital assets protected by encrypting their data within their data boundaries. The ability to share these encrypted assets with partners implicates a need to securely share keys with their partners so that they can also access the data. This process is referred to as a key exchange and often used a key agreement protocol. The details of a hybrid key agreement scheme are described in this section.
3.2.1 Problem statement
In the past, this key exchange process was used by partnering organizations in a way that allowed them to securely derive the same encryption key over a public, insecure channel. Regardless of who was eavesdropping on the public channel (whether a competing organization or a bad actor), the mutually derived encryption key maintained its confidentiality because of the ability to establish a secure connection over this public, insecure channel by way of key exchange schemes.
Traditionally, the ECDH key agreement protocol is a method that is used to derive keys for a key exchange process. This key agreement scheme allows two business parties, each with their own ECC key pair (consisting of a private and public key) to establish a shared secret by using an insecure channel, and it begins with each party sharing their public keys.
However, a key agreement scheme solves one piece of the key exchange puzzle. To create a truly secure key exchange protocol, you must also solve the “trust” problem that is associated with exchanging keys.
Although the public key can be shared over an insecure channel, a mechanism must be in place to ensure that the key that is labeled as party A’s public key really belongs to party A and the key labeled party B’s public key really belongs to party B to avoid a man-in-the-middle attack.
This problem can be addressed by cryptography; however, this use case focuses on the key establishment piece of the key exchange puzzle. For our example, we assume that a trust mechanism is in place.
If party A and party B wanted to participate in a key exchange process to obtain a shared key, they each generate their ECC public-private key pair and share their public keys with each other. Each party can use the ECDH protocol to derive the same shared key.
For example, party A uses their private key in combination with party B’s public key in the protocol, while party B uses their private key in combination with party A’s public key. The result is that both parties now have the same shared secret. This method of key exchange to derive the same shared secret historically was considered secure because neither party had to share their private key to perform the key exchange.
Traditionally, this use of public key cryptography for key exchange was considered sufficiently secure. The only means for a cybercriminal to derive the shared secret key was to obtain one of the party’s private keys.
Although the public and private keys in an ECC key pair are mathematically related, it takes a conventional computer millions of years to derive the private key from one party’s public key because of the significant computational capacity that is required to perform this operation. However, the rise of quantum computing brings about many challenges to keeping the shared secret key secure.
Although specific symmetric key algorithms, such as AES with 256-bit encryption keys, are considered quantum-safe, the method of sharing those keys in a key exchange by way of public key cryptography is no longer considered to be quantum-safe, which results in the vulnerability of these symmetric keys.
After quantum computers have the computing power to perform Shor’s Algorithm, an adversary with access to a quantum computer can solve the elliptic curve discrete logarithm problem exponentially faster than a conventional computer. As a result, the private key of one party can be derived from their public key in only a matter of hours.
After the key is in the hands of an adversary, the same shared key that is derived by the two parties might be generated with the ECDH key exchange scheme. Then, the bad actor can access the organization’s valuable information.
To make matters worse, data that is encrypted today by using symmetric keys that are exchanged between two parties by way of public key cryptography is still not safe, even in the absence of quantum computers of sufficient scale.
Because the encrypted data, along with the public key, can be harvested today, an adversary with access to a quantum computer in the future can perform Shor’s algorithm to break this public key cryptographic algorithm to expose the sensitive data.
3.2.2 Solving this challenge with IBM z16 capabilities
Valuable information and digital assets that partnering organizations share with each other are no longer secure because of methods that are used by adversaries to harvest the encrypted data now.
IBM z16 provides quantum-safe capabilities to circumvent this security challenge and allow for the secure key exchange between two parties in a quantum-safe manner. With IBM z16, organizations have a reliable method to securely share encryption keys between parties through a hybrid key exchange scheme.
Although traditional key exchange schemes relied on public key cryptography alone to derive a shared secret, a hybrid key exchange scheme relies on classical cryptography (such as ECDH) and a quantum-safe cryptographic algorithm (such as CRYSTALS-Kyber). ECDH is a key agreement protocol and CRYSTALS-Kyber is a key encapsulation mechanism.
When used together, organizations have an efficient way to securely exchange keys, even in the face of high-powered quantum computers. This secure exchange is made possible with the introduction of quantum-safe APIs within the Crypto Express8S feature (CEX8S). This feature is provided with IBM z16 to securely derive quantum-safe encryption keys by using the hybrid key exchange mechanism that is performed in the CEX8S by using the CCA API or the Enterprise PKCS#11 API.
When two Business Partners (party A and party B) take advantage of this hybrid key exchange scheme on IBM z16, they can safely derive keys that are used to protect their shared sensitive information (see Figure 3-2).

Figure 3-2 Key and data setup for hybrid key exchange - CCA example
By using this capability, party A generates an ECC key pair and a quantum-safe CRYSTALS-Kyber key pair. Party B must generate an ECC key pair and an AES CIPHER key. The two parties then exchange their public keys.
Party B then uses CEX8S APIs to generate a random 32-byte secret and encrypt it with party A’s CRYSTAL-Kyber public key and an AES key that is owned by Party B. The secret that is protected with the CRYSTAL-Kyber public key is transmitted to party A. Although it is being sent over an insecure channel, not even a quantum computer can break this algorithm because it is considered to be quantum-safe (see “New algorithms to counter CRQC attacks” on page 11).
After party A receives the wrapped secret, they then use their CRYSTALS-Kyber private key to recover the 32-byte secret from party B. Now that both parties have each other’s ECC public key and the 32-byte secret, they can each use the ECDH key agreement protocol to create a shared secret just as they do in the classical key exchange process (see “Quantum-safe hybrid key exchange” on page 113).
However, this shared secret is used with the mutually known 32-byte secret in the key material creation process to compute the same shared key by using ECDH. This 32-byte secret is protected with the quantum-safe Kyber algorithm. By using the CEX8S APIs, the secret information is protected by the hardware security module and never appears outside in the clear in the memory of the host computer.
After this shared secret key is derived by both parties, it can be used to encrypt either party’s data, and the data itself can be shared between parties (see Figure 3-3). Even in the presence of a quantum computer with sufficient computing power, the key cannot be derived. Although a quantum computer might derive either party’s ECC private key, the 32-byte secret that is used in the ECDH protocol cannot be exposed because it was protected by using a CRYSTALS-Kyber key.

Figure 3-3 Hybrid key agreement process - CCA example
3.2.3 Industry applications
This section describes how organizations across many different industries with a need to share encryption keys securely with partners by using traditional key exchange mechanisms might be vulnerable to CRQC attacks.
It also outlines how they can benefit from the hybrid key exchange schemes that are provided with IBM z16 to ensure data confidentiality, even in the presence of sufficiently capable quantum computers.
Pharmaceuticals
The pharmaceutical industry is an example of the need to securely share intellectual property and research findings with Business Partners to drive success. The process of developing new drugs and making them publicly available in the marketplace is lengthy and costly.
On average, it takes at least 10 years for a new drug to become available in the market, with six to seven of those years being dedicated to performing clinical trials. A study that was conducted by Tufts Center for the Study of Drug Development1 estimated that it costs pharmaceutical companies $2.6 billion to develop a new medication gaining marketing approval.
Pharmaceutical companies that are vying to successfully complete clinical trials for their new drug have only a 12% success rate. Even if a newly developed drug passes all required steps to bring it to market, pharmaceutical companies face heavy competition with each other.
To create efficiencies in the drug development process to lower costs and increase the likelihood that a drug passes clinical trials, pharmaceutical companies can benefit greatly from collaborating with each other and other technology organizations. An example of this collaboration within the pharmaceutical industry was the agreement between Pfizer and BioNTech to begin developing a vaccine for COVID-19. One year later, the BioNTech, Pfizer vaccine was approved for use worldwide.
Part of this collaboration requires the need to safely share intellectual property and research findings with each other. Their data must be protected from unintended disclosure by competitors and adversaries to avoid reputation damage, profit loss, and brand impact.
Although the rise of quantum computing undoubtedly benefits pharmaceutical companies regarding drug development, it also brings about challenges for them about collaborating with each other and sharing their intellectual property in a secure manner.
If an adversary with access to a quantum computer can break the encryption algorithms that are used to protect shared information, they can publicly expose a pharmaceutical company’s research findings that can result in a significant advantage for their competitors to release a similar drug.
By taking advantage of the quantum-safe capabilities with IBM z16, these organizations can use the benefits that quantum computers can provide in Research and Development while also ensuring that intellectual property that is shared between companies remains secure.
Government bodies
Government bodies often partner with other government agencies and the private sector to create efficiencies in their operations. For example, information sharing programs are used that are dedicated to saving government resources through partnerships between various federal, state, and municipal government agencies. As part of these information sharing programs, the previously mentioned agencies are entitled to exchange taxpayer information with each other.
This example the need to facilitate the sharing of confidential information between partnering agencies. Although safeguards exist to protect the confidentiality of taxpayers’ information, the threat of quantum computing presents challenges for maintaining this confidentiality in the future.
Government bodies greatly benefit from the capabilities that are provided with IBM z16 to enable secure information sharing with partners. By using quantum-safe hybrid key exchange schemes, government agencies can maintain the confidentiality of their citizens’ information as it is shared to ensure that not even a quantum computer can intercept the information and break the encryption algorithms that are used to protect it.
Banking
In financial services, such as banking, a significant need exists to protect business-critical data in the face of quantum computing. Although many examples exist of data that requires protection in banking, a simple example to illustrate is in the case of credit card information.
Banks are required to comply with the Payment Card Industry Data Security Standard (PCI DSS) for protection of customer’s sensitive payment card information. As a result, security protocols are in place to protect their sensitive data as it is transmitted between point-of-sale (POS) terminals and the bank. This process typically is done by encrypting the data that is in transit between the two parties.
PCI DSS implies is that both parties must have a shared symmetric key that is used to encrypt the customer data at the POS and then decrypt it when in the hands of the bank. Even when quantum-safe symmetric key algorithms are used, such as AES (assuming 256-bit keys) for this encryption and decryption, the problem is that the shared keys are typically exchanged through classical public key cryptography schemes alone that are not quantum-safe. For example, they might use ECDH as their key agreement protocol to derive their symmetric encryption key.
As a result, the protection of their customers’ sensitive payment card information can potentially be exposed if a cybercriminal harvests the encrypted data now to decrypt in the future after they obtain access to a quantum computer of sufficient scale.
Therefore, banks and other organizations that deal with sensitive payment card information can benefit greatly by using the hybrid key exchange schemes that are available with IBM z16. By doing so, they securely derive a shared encryption key that cannot be derived in the face of high-powered quantum computers.
Automotive and aerospace
Similar to the pharmaceutical industry, automotive and aerospace companies must protect their intellectual property from unintended information disclosure from their competitors to avoid reputation damage, profit loss, and brand impact. They also must collaborate with Business Partners to develop the latest cutting-edge capabilities in their respective industries.
To enable this collaboration, they must share their intellectual property and proprietary research findings with each other in a way that is secure and cannot be exposed to bad actors and competitors. This sharing also is done by way of encrypting confidential data in transit by using mutually derived encryption keys.
Because these keys are shared between partnering organizations by using traditional public key cryptography alone, it can be concluded that quantum computers eventually can expose the organizations’ confidential information that is shared between parties by breaking the traditional public key algorithms that are used today.
Therefore, the quantum-safe key exchange mechanisms that are available with IBM z16 can be used. As a result, automotive and aerospace companies can be assured that the intellectual property they are exchanging with partners is never exposed in the clear to avoid unintended information disclosure.
3.3 Use case: Message integrity and secure logging
This use case addresses the problem of ensuring the integrity of messages and logs in the presence of quantum computers and how capabilities that are provided with IBM z16 can solve these challenges.
Organizations that send messages and digital assets to other parties, such as legal documents, audit logs, financial statements, and historical records, traditionally ensured the integrity of their messages by using digital signatures.
By using digital signatures, organizations can ensure that the receiver of a message or document knows whether the message is genuine and untampered. This feature makes it possible to prevent legal and documentation fraud.
However, with the rise of quantum computing, adversaries with access to a quantum computer of sufficient scale can undetectably rewrite history and modify documents, messages, and logs, and claim that the tampered message was indeed the original message the organization sent.
This section addresses how IBM z16 capabilities can overcome this security challenge.
Although digital signatures can serve multiple purposes, the focus of this use case is on message integrity. Digital signatures can also help achieve identity authentication, or proof of authorship, as described in 3.4, “Proof of authorship” on page 42.
3.3.1 Problem statement
In the past, organizations relied on digital signatures to ensure the integrity of messages, digital documents, and logs used for auditing purposes. Traditionally, when an organization sent a digitally signed message or document to another party, the other party verified the digital signature to ensure that the document or message was genuine and was not modified by an adversary. By using digital signatures, organizations avoided advanced legal and documentation fraud.
Digital signatures rely on public key cryptography. ECDSA is one example of a popular cryptographic algorithm that is used for digital signatures.
For an organization to send a message or document to another party and ensure it was not tampered with in-transit, they digitally sign the document by using ECDSA, for example. The process begins with the organization generating an ECC key pair (consisting of a private and public key). They then use the ECDSA signing algorithm to generate a digital signature.
As part of the algorithm’s signing process, a cryptographic hash of the message, document, or log is first calculated by using a hash algorithm, such as SHA-256. Because the hash generation is a one-way function, meaning the hash value is unique to the exact contents of the message or document, any effort to modify the message or document results in a different, inconsistent hash value.
Following the hash value generation, it is signed by using the organization’s private key, to which only they have access. The signed hash is then appended to the document or message and is sent to the party it was intended for, along with the organization’s public key.
The retrieving party can verify the integrity of the message or document by using ECDSA and the public key that was shared:
1. The party generates their own hash of the document or message by using the same hash function that was used to sign it.
2. They then use the shared public key to verify the signed hash that was appended to the document or message.
3. As part of the ECDSA verification process, the newly computed hash value is compared with the decrypted hash value that was appended to the document.
If the two hashes match, the party can be assured that the message was not tampered with in-transit and the contents of the message or document are exactly what the original organization sent.
If the hashes do not match, the receiving party can conclude that the message was tampered with because the hash that they generated differs only from the appended hash if the message’s contents was changed in-transit.
When digital signatures are used, the receiving party can reliably determine the integrity of the message because they assume that only the original organization includes the mathematically related private key that was used to sign the hash and nobody else. This assumption can be made because of the mathematical complexity of the elliptic-curve discrete logarithm problem.
The only way for an adversary to obtain the original organization’s private key is to derive it from the associated public key by solving this mathematical problem. However, it is not feasible for a conventional computer to solve this problem because it likely takes millions of years. As a result, it traditionally was accepted that the appended signed hash is the hash value that was generated from the original message or document. Therefore, the integrity can be determined by comparing the receiver’s hash output with the appended hash value.
With the rise of quantum computing, eventually it will be possible for a quantum computer of sufficient scale to solve this once considered complex problem in only a matter of hours by using Shor’s algorithm.
An adversary with access to a quantum computer might take an entity’s public key and derive the associated private key. After it is in the hands of an adversary, they can alter the contents of the message or document undetectably.
When the organization sends the message to the intended party, the adversary can run a “man in the middle” attack to intercept the original message, modify its contents, re-create a new hash value, and then, sign this new hash by using the organization’s private key. This newly signed message is then forwarded to the intended party. The party has no way of ensuring its integrity because the hash value that was generated is identical to the newly appended hash value.
This ability to undetectably modify messages, documents, and logs by using quantum computers can result in disastrous consequences, especially when considering the various regulations, such as eIDAS (in the EU), and UETA and E-SIGN (in the US) that allows digital signatures to have equal legal status to traditional “wet” signatures. In addition, adversaries might tamper with potentially life-saving messages that are used in the automobile industry and messages that are used for international government communication.
3.3.2 Solving the integrity challenge with IBM z16 capabilities
The challenge of ensuring message, document, and log integrity in the face of quantum computing can be alleviated by using the dual digital signature schemes that are made possible with IBM z16. For more information about for the procedures that are used to enable these dual digital signature schemes, see “Quantum-safe digital signatures” on page 107.
By using this IBM z16 capability, organizations can ensure message integrity by digitally signing their messages and documents by using a classical cryptographic algorithm and a quantum-safe cryptographic algorithm.
For example, a dual digital signature can be generated by using a classical cryptographic algorithm, such as ECDSA, with a quantum-safe cryptographic algorithm, such as CRYSTALS-Dilithium. IBM z16 enables this through enhancements in the Crypto Express8S (CEX8S) features to provide quantum-safe algorithm APIs.
As in the past, it is important to continue the use of a classical cryptographic signature algorithm, such as ECDSA, to comply with the various standards and compliance requirements mandating the use of approved signing algorithms. However, with the use of a classical cryptographic algorithm for digital signatures, it is also crucial to begin safeguarding information with a quantum-safe cryptographic scheme to ensure that message integrity is maintained in the face of CRQC attacks.
To ensure that message integrity is maintained in the future, an organization can use IBM z16 to digitally sign their out-bound messages and documents by using two digital signatures. This process is explained next (for more information, see “Quantum-safe digital signatures” on page 107).
An organization that wants to ensure the integrity of its messages begins by generating a hash of its message by using a cryptographic hash algorithm, such as SHA-256.
Then, the organization generates two key pairs. For example, they might generate an ECC public key pair and a quantum-safe CRYSTALS-Dilithium key pair (ICSF supports the CRYSTALS-Dilithium signature algorithm on the CCA and PKCS#11 APIs for IBM z16).
The organization then signs this hash with ECDSA by using their ECC private key, which results in an ECC signature. With generating that ECC signature, the organization also signs the same hash by using their CRYSTALS-Dilithium private key to generate a quantum-safe signature. The result is that two signatures exist for the single hash of the message, and both signatures are appended to the message for verification purposes.
Anyone who wants to verify that the message was not modified or tampered with in-transit uses the CRYSTALS-Dilithium public key to verify the Dilithium signature and the ECC public key to verify the ECC signature. As part of the verification process, the receiving party generates the hash value of the message and passes the hash value and the suitable digital signature to the signature verification function for each signature algorithm. If the ECC signature verifies and the CRYSTALS-Dilithium signature verifies, the party can be assured that the message was not tampered with by a bad actor, and thus, message integrity is maintained.
As shown in Figure 3-4, success indicates message integrity and authorship by the owner of the public key.
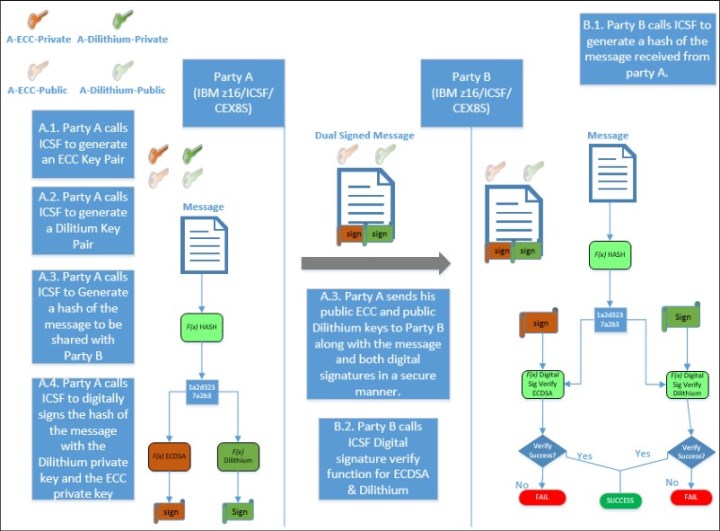
Figure 3-4 Validating the authenticity (proof of authorship) and integrity of a message
This dual digital signature scheme that is enabled with IBM z16 solves the challenge of ensuring message integrity, even if an adversary can access a quantum computer that can run Shor’s algorithm.
Suppose that the adversary ran a man-in-the-middle attack to intercept the original message, modify its contents and then, re-create a new hash value. Although they can sign the new hash by using the organization’s ECC private key that they derived by using Shor’s algorithm, they have no way of signing the same hash by using the organization’s CRYSTALS-Dilithium private key because it is quantum-safe.
A single ECC signature is of no value because the integrity verification works only if a valid ECC signature and a valid Dilithium signature with the message are available.
3.3.3 Industry applications
This section describes the wide range of applications that quantum-safe digital signatures have across different industries. Also discussed is how financial services organizations, automotive companies, software vendors, and even law firms might all benefit from the dual digital signature schemes that are enabled with IBM z16 to ensure that their communications and data were not tampered with or targeted by adversaries with access to quantum computers.
Banking
In the banking industry, digital signatures prove to be a vital necessity in securing financial transactions and messages between banks. Society for Worldwide Interbank Financial Telecommunication (SWIFT) was created in the 1970s to enable banks across the world to share information about financial transactions with each other. These high-value electronic transactions and messages can be shared between banks over the SWIFT network, which relies on public key infrastructure to digitally sign and encrypt messages.
The growing presence of quantum computing throughout the world threatens the long-term security of these types of banking transactions. Relying on traditional public key cryptography alone for securing these interbank transactions poses a vulnerability in message integrity because adversaries with access to quantum computers can inevitably forge transactions and messages.
The banking industry might also be one of the first targets of CRQC attacks because of the profit potential for cybercriminals. Adopting quantum-safe dual digital schemes in the banking industry is a must to secure interbank financial transactions in the future.
Automotive industry
In the automotive industry, manufacturers are constantly innovating new ways of improving driver safety. One of these innovations is the rise of vehicle-to-vehicle (V2V) communication that aims to make driving safer by allowing vehicles to communicate with each other to prevent crashes, traffic, and so on.
Quantum computing poses security challenges for this V2V communication in which messages between vehicles might be tampered with by bad actors. Messages that are transmitted between vehicles that are digitally signed by using traditional public key cryptography alone, such as RSA or ECDSA, no longer guarantee the integrity of these V2V messages when quantum computers of sufficient scale are available to bad actors.
Adversaries might manipulate messages to create life-threatening situations on highways and in busy cities. By taking advantage of the dual digital signing schemes that are available with IBM z16, vehicle manufacturers can use quantum-safe digital signing to thwart message tampering attacks and make driving safer.
Software vendors
In software development, vendors aim to secure software distribution by using digital signatures that are based on public key cryptography.
For example, updates to a software release are often digitally signed by using RSA or ECDSA encryption algorithms to ensure that customers can verify whether the software was tampered with before installation. Oftentimes, these software updates require automatic digital signature verification before installing the update.
The traditional algorithms that are used today for digitally signing software were reliable in ensuring its integrity; however, with the rise of quantum computing, integrity is no longer guaranteed because bad actors can tamper with the software undetectably.
This tampering can result in a customer installing malware on their systems. Therefore, it is critical that software vendors implement quantum-safe dual digital signature schemes in their products.
Legal industry
In the legal industry, regulations, such as eIDAS (in the EU) and UETA and E-SIGN (in the US) allow digital signatures to have equal legal status to traditional “wet” signatures.
Historically, confidential legal documents that use digital signature capabilities were not forged because the integrity of these documents was ensured through verification of the digital signatures by the receiving party.
However, quantum computers that can quickly derive the private keys serving as the underpinnings of these digital signatures eventually will make it possible to manipulate and tamper with legal documents by forging digital signatures.
To avoid advanced legal fraud and impersonation attacks in this era where digital signatures serve as legal evidence, it is critical that law firms begin safeguarding their legal documents and communications with quantum-safe dual digital signature schemes that are available with IBM z16.
3.4 Proof of authorship
Organizations that made their valuable assets digitally accessible, such as legal documents, financial statements, historical records, and license code, often ensured nonrepudiation such that the public can trace back these digital assets to the original creator.
Proof of authorship was achieved by using digital signatures where anyone can verify the authenticity of a digitally signed document or digital asset. Digital signatures also make it impossible for any unknown entity to disseminate information or assets to the public and claim it came from someone else, which ensures responsibility for the distribution of digital information.
In the legal industry, various regulations are in place that allow digital signatures to have equal legal status to traditional “wet” signatures. Because legal documents might feature long lifetimes, the signatures on them might need to be secure for decades.
With the rise of quantum computing, adversaries with access to a quantum computer of sufficient scale can manipulate legal history by forging digital signatures. As a result, the legal underpinnings of digitalization are now vulnerable.
This use case illustrates how organizations can avoid advanced legal fraud and impersonation attacks by using the quantum-safe capabilities that are available on IBM z16.
3.4.1 Problem statement
Organizations traditionally made their digital assets public while ensuring proof of authorship and nonrepudiation. Anyone accessing or viewing these digital assets can verify exactly from who it came, which is made possible by using digital signatures.
Nonrepudiation and proof of authorship are ensured because these digital signatures are generated by using a private key that is only known by the signer. As a result, the signer has no means of repudiating their signature that is added to the document.
If a dispute occurs, proof of authorship enables the document’s authorship to be supported by evidence, being the holder of the private key.
Digital signatures
Digital signatures are made possible with the use of public key cryptography. One example of a popular cryptographic algorithm for digital signatures is ECDSA. Organizations that wanted to digitally sign a document so that the public can trust that it came from them begins by generating an ECC key pair that consists of a private and public key.
They then use the ECDSA signing algorithm to digitally sign their document. The algorithm works by first calculating a cryptographic hash of the document by using a cryptographic hash algorithm, such as SHA-256. This hash is unique to the exact contents of the document.
If the document was modified, the resulting hash output is different. As part of the signing algorithm, the hash value then is signed by using the signer’s private key, which only they can access. The signed hash is appended to the document and made publicly available along with the signer’s public key.
Now that the document is digitally signed, anyone who wants to access the document can verify its authenticity by using ECDSA and the public key. The receiver uses the public key that they received to verify the signed hash that is appended to the document.
They also generate a hash output of the same document by using the same hash function that was used to sign the document. The algorithm then compares the hash value that the receiver computed with the decrypted hash value that was appended to the document. If the two hashes match, the public key sender is verified as the true author of the document because it is assumed that only they have the mathematically related private key.
Elliptic-curve discrete logarithm problem
The strength of these digital signatures for proving authorship of a digital asset is a result of the mathematical complexity of the elliptic-curve discrete logarithm problem. The only way to derive the private key from the associated public key is to solve this mathematical problem, which is not feasible for conventional computers because it likely takes millions of years to solve the elliptic-curve discrete logarithm problem.
Therefore, it was always assumed that the private key holder is the author of the digitally signed document, which is how proof of authorship can be ensured. As a result, public key cryptography alone was considered secure for digital signatures.
With the rise of quantum computing, it eventually will be possible for a quantum computer of sufficient scale to solve this once considered complex problem in only a matter of hours by using Shor’s algorithm. An adversary with access to a quantum computer might take an entity’s public key and derive the associated private key, which can have disastrous consequences.
By using that entity’s private key, the adversary can forge their digital signature to manipulate legal history and claim that the digital assets they create were authored by the entity whose private key they possess.
Making matters worse, many legal documents (and the signatures on them) are in public records; therefore, an adversary can easily obtain them and attack the cryptography with a quantum computer. No “hacking” is necessary to get to the data to be attacked. Documents, messages, certificates, software, and transactions all can be forged. Therefore, an identity over the internet is no longer guaranteed.
3.4.2 Solving this challenge with IBM z16 capabilities
Capabilities that are provided by IBM z16 allow organizations to solve this challenge that is faced today with the threat of quantum computing by using dual digital signature schemes and quantum-safe key generation. For more information about enabling these dual digital signature schemes, see “Quantum-safe digital signatures” on page 107.
With IBM z16, it is possible for organizations to digitally sign their valuable assets by using a classical cryptographic algorithm and a quantum-safe cryptographic algorithm. The ability to use a quantum-safe cryptographic algorithm, such as CRYSTALS-Dilithium, with a classical cryptographic algorithm, such as ECDSA, is supported by the quantum-safe algorithm APIs within the new Crypto Express cards (CEX8S) that was provided with IBM z16.
The value in the use of this dual digital signature scheme is two-fold: First, as in the past, it is important to use a classical cryptographic signature algorithm, such as ECDSA, because various standards and compliance requirements exist that require standards-approved signing algorithms.
Uncertainty also exists about how those standards might change in the future with the rise of quantum computing. Although newly developed algorithms might be considered “quantum-safe,” it is never guaranteed that these algorithms are not to be found insecure.
Therefore, as a minimum security measure, it is beneficial to continue the use of these classical signature schemes to thwart attacks from conventional computers. Also, to begin safeguarding valuable information in the future, even in the face of high-powered quantum computers, it is important to buttress this protection with a known quantum-safe cryptographic signature scheme with IBM z16.
To maintain proof of authorship and nonrepudiation for an organization’s digital assets, they use IBM z16 to create two digital signatures that public entities can verify (see Figure 3-4 on page 40):
1. A hash of their document is generated by using a cryptographic hash algorithm, such as SHA-256.
2. The organization generates two key pairs. For example, they might generate an ECC public key pair and a CRYSTALS-Dilithium key pair (ICSF supports the CRYSTALS-Dilithium signature algorithm on the CCA and PKCS#11 APIs for IBM z16).
3. The organization signs this hash with ECDSA; for example, by using their ECC private key, which results in an ECC signature. Along with generating that ECC signature, the organization also signs the same hash by using their CRYSTALS-Dilithium private key to generate a quantum-safe signature.
This process results in having two signatures for the single hash of the message, and both signatures are appended to the digital document for verification.
Anyone who wants to verify that this organization authored the document uses the CRYSTALS-Dilithium public key to verify the Dilithium signature and the ECC public key to verify the ECC signature. If both signatures are successfully verified, the verifying party can be assured that the document was authored by the organization.
The threat that is created by quantum computers of sufficient scale to forge digital signatures is negated because both signatures must verify.
Even if an adversary with access to a quantum computer can run Shor’s algorithm to derive the ECC private key by using the related public key, they cannot forge the organization’s signature because they cannot derive their CRYSTALS-Dilithium private key.
Suppose a cybercriminal with access to a quantum computer can create a fake document and sign it with the derived ECC private key. The ECC signature is created, but the adversary does not have the CRYSTALS-Dilithium private key to create a Dilithium signature.
A single ECC signature is of no value because the verification works only if a valid ECC signature and Dilithium signature exists with the document.
For more information, see “Quantum-safe digital signatures” on page 107.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
